aceca9de5c2092cb2bc8ee6a6237f86b.ppt
- Количество слайдов: 37
 Computer and Network Security Introduction Dr. Ron Rymon Efi Arazi School of Computer Science IDC, Herzliya. 2010/11
Computer and Network Security Introduction Dr. Ron Rymon Efi Arazi School of Computer Science IDC, Herzliya. 2010/11
 Today’s Lecture ¨ Introduction ¨ A Few Nightmare Scenarios ¨ Statistics and Impact ¨ Course Plan and Administrativia ¨ Models of Computer Security
Today’s Lecture ¨ Introduction ¨ A Few Nightmare Scenarios ¨ Statistics and Impact ¨ Course Plan and Administrativia ¨ Models of Computer Security
 What do we mean by “Computer Security”?
What do we mean by “Computer Security”?
 Examples Threats Attacks Security Mechanisms Security Needs and Services
Examples Threats Attacks Security Mechanisms Security Needs and Services
 Our Security Needs/Threats ¨ ¨ ¨ ¨ ¨ Confidentiality of information stored on computers Confidentiality of information communications Control of our computers and networks Ensuring the integrity of information Identifying/authenticating communication partners Protecting information services (enterprise, www) Protecting information and people privacy Protecting digital rights and property Protecting computer-operated physical infrastructure ¨ … and more as computers take greater role in our lives – hand-held devices, electronic voting, electronic payment, border control, job entry, etc.
Our Security Needs/Threats ¨ ¨ ¨ ¨ ¨ Confidentiality of information stored on computers Confidentiality of information communications Control of our computers and networks Ensuring the integrity of information Identifying/authenticating communication partners Protecting information services (enterprise, www) Protecting information and people privacy Protecting digital rights and property Protecting computer-operated physical infrastructure ¨ … and more as computers take greater role in our lives – hand-held devices, electronic voting, electronic payment, border control, job entry, etc.
 The Adversaries ¨ For Profit – Organized crime – Fraudsters – Information thieves – Marketers – Spies (military, commercial) – Enemy states & terrorists ¨ Vandals – Commercial and political reasons – Mostly, nut cases and irresponsible kids (“script kiddies”) ¨ Joy riders – Technically skilled – Psychologically challenged – Again, mostly kids ¨ Insiders! ¨ Good hackers vs. Bad hackers (Crackers)
The Adversaries ¨ For Profit – Organized crime – Fraudsters – Information thieves – Marketers – Spies (military, commercial) – Enemy states & terrorists ¨ Vandals – Commercial and political reasons – Mostly, nut cases and irresponsible kids (“script kiddies”) ¨ Joy riders – Technically skilled – Psychologically challenged – Again, mostly kids ¨ Insiders! ¨ Good hackers vs. Bad hackers (Crackers)
 Their Tools of the Trade ¨ ¨ ¨ ¨ Viruses, worms, etc. Password cracking Intrusion and penetration attacks Eavesdropping attacks (esp. wireless) Communication hijacking attacks Denial of service attacks OS/Application vulnerability attacks Trojan horses, viruses/worms, spyware, keyloggers Server and access point impersonation Phishing and phraud Clickjacking Social Engineering More….
Their Tools of the Trade ¨ ¨ ¨ ¨ Viruses, worms, etc. Password cracking Intrusion and penetration attacks Eavesdropping attacks (esp. wireless) Communication hijacking attacks Denial of service attacks OS/Application vulnerability attacks Trojan horses, viruses/worms, spyware, keyloggers Server and access point impersonation Phishing and phraud Clickjacking Social Engineering More….
 Our Tools of the Trade ¨ ¨ ¨ ¨ Encryption Anti-virus software Spam filters Firewalls Intrusion detection/prevention software Strong authentication Access control Authorization management Application security gateways and filters Patch management systems Electronic signatures Disaster Recovery … and more… ¨ EDUCATION!!
Our Tools of the Trade ¨ ¨ ¨ ¨ Encryption Anti-virus software Spam filters Firewalls Intrusion detection/prevention software Strong authentication Access control Authorization management Application security gateways and filters Patch management systems Electronic signatures Disaster Recovery … and more… ¨ EDUCATION!!
 Security and People ¨ People, not technology, are often the weakest link – Create awareness and educate people that security matters – Create business processes that enhance security • accurate provisioning, password mgmt, stronger authentication, segregation of duty ¨ Security solutions shall be tied to business processes – “Treat security as an important part of doing business. It is not less important than features and performance” (Bill Gates) – “The missing component in most security products is what Global 5000 buyers most want, the ability to manage business risk, innovation, and agility. Despite this, security suppliers continue to focus their efforts on honing technical access controls “ (Aberdeen, Mar 2004) ¨ Corporate governance: Security is as enterprise management issue – New executives: Chief Security Officer & Chief Compliance Officer – Business managers in all ranks are asked to assume security responsibility
Security and People ¨ People, not technology, are often the weakest link – Create awareness and educate people that security matters – Create business processes that enhance security • accurate provisioning, password mgmt, stronger authentication, segregation of duty ¨ Security solutions shall be tied to business processes – “Treat security as an important part of doing business. It is not less important than features and performance” (Bill Gates) – “The missing component in most security products is what Global 5000 buyers most want, the ability to manage business risk, innovation, and agility. Despite this, security suppliers continue to focus their efforts on honing technical access controls “ (Aberdeen, Mar 2004) ¨ Corporate governance: Security is as enterprise management issue – New executives: Chief Security Officer & Chief Compliance Officer – Business managers in all ranks are asked to assume security responsibility
 A Few Nightmare Scenarios
A Few Nightmare Scenarios
 Nightmare Scenario #1: Information stolen from our systems ¨ 2000 – hacker breaks CDUniverse, steals 300, 000 credit card numbers ¨ 2002 – hacker steals 1 MM credit cards from merchants that didn’t patch ¨ 2007 – hacker steals millions of credit cards & personal info from TJMaxx ¨ 2001 – hacker pre-announces JDS earnings ¨ 1/2002, hacker penetrates financial software maker Online Resources; then uses this to hack into a NY bank and steal account data; then extorts the bank ¨ 2004 – Code of Win 2 K and NT stolen from Microsoft partner ¨ 2004 – Code of Cisco IOS stolen ¨ 2006 - 25% of companies reported attempted penetration (really, close to 100%) ¨ 2006 – 25% of computers believed infected ¨ ¨ 2007 - Theft of laptops and PDAs is top security concern for CIOs 2008 – Identity theft is top concern for individuals (1 in 6 Americans last year!) 2009 – Data Leakage is a key concern for security and compliance officers 2010 – Where are our (virtualized) systems? Who has access to them? ¨ 70% of all cases are “internal work” – profit, revenge, and ignorance
Nightmare Scenario #1: Information stolen from our systems ¨ 2000 – hacker breaks CDUniverse, steals 300, 000 credit card numbers ¨ 2002 – hacker steals 1 MM credit cards from merchants that didn’t patch ¨ 2007 – hacker steals millions of credit cards & personal info from TJMaxx ¨ 2001 – hacker pre-announces JDS earnings ¨ 1/2002, hacker penetrates financial software maker Online Resources; then uses this to hack into a NY bank and steal account data; then extorts the bank ¨ 2004 – Code of Win 2 K and NT stolen from Microsoft partner ¨ 2004 – Code of Cisco IOS stolen ¨ 2006 - 25% of companies reported attempted penetration (really, close to 100%) ¨ 2006 – 25% of computers believed infected ¨ ¨ 2007 - Theft of laptops and PDAs is top security concern for CIOs 2008 – Identity theft is top concern for individuals (1 in 6 Americans last year!) 2009 – Data Leakage is a key concern for security and compliance officers 2010 – Where are our (virtualized) systems? Who has access to them? ¨ 70% of all cases are “internal work” – profit, revenge, and ignorance
 Nightmare Scenario #2: Our communication can be exposed ¨ In 16 th century, Mary Queen of Scots loses her head when her coded messages are deciphered ¨ In WWII, many German U-boats were destroyed once the British were able to decipher their Enigma messages ¨ Today, encryption mechanisms (VPNs, SSL, etc. ) are very strong, usually rendering eavesdropping ineffective ¨ Still, some cases surface from time to time – Wi-Fi networks originally unsecured and being targeted – US Carnivore/Echelon sift through millions of emails/phone calls – Al-Qaeda members caught using Swisscom GSM chips – Tempest attacks, capturing electromagnetic radiation – Cloning encryption cards for satellite-based entertainment systems – Chinese using supercomputers to break American satellite communication
Nightmare Scenario #2: Our communication can be exposed ¨ In 16 th century, Mary Queen of Scots loses her head when her coded messages are deciphered ¨ In WWII, many German U-boats were destroyed once the British were able to decipher their Enigma messages ¨ Today, encryption mechanisms (VPNs, SSL, etc. ) are very strong, usually rendering eavesdropping ineffective ¨ Still, some cases surface from time to time – Wi-Fi networks originally unsecured and being targeted – US Carnivore/Echelon sift through millions of emails/phone calls – Al-Qaeda members caught using Swisscom GSM chips – Tempest attacks, capturing electromagnetic radiation – Cloning encryption cards for satellite-based entertainment systems – Chinese using supercomputers to break American satellite communication
 Nightmare Scenario #3: Control of our computers is taken ¨ First viruses (e. g. , Jerusalem) were spreading slowly ¨ Code Red (2001) leaves back door on infected machines – infected 359, 000 IIS servers in 14 hours, 2000 per minute at the peak ¨ SQL Slammer (2003) generated huge traffic from infected network ¨ In 2004, there were 112, 000 known viruses ¨ Today, most malware is commercially motivated – Professional and uses multiple infection mechanisms (“time to infection” is down to FIVE minutes in 2008) – Soldiers in the botnets army… (~25% of all computers are infected) – Steal information, e. g. , identity, passwords, credit cards… – Serve for commercial spam ¨ Many recent attacks aimed at virtualization platforms ¨ Next, significant risk to mobile devices, VOIP systems
Nightmare Scenario #3: Control of our computers is taken ¨ First viruses (e. g. , Jerusalem) were spreading slowly ¨ Code Red (2001) leaves back door on infected machines – infected 359, 000 IIS servers in 14 hours, 2000 per minute at the peak ¨ SQL Slammer (2003) generated huge traffic from infected network ¨ In 2004, there were 112, 000 known viruses ¨ Today, most malware is commercially motivated – Professional and uses multiple infection mechanisms (“time to infection” is down to FIVE minutes in 2008) – Soldiers in the botnets army… (~25% of all computers are infected) – Steal information, e. g. , identity, passwords, credit cards… – Serve for commercial spam ¨ Many recent attacks aimed at virtualization platforms ¨ Next, significant risk to mobile devices, VOIP systems
 Nightmare Scenario #4: Website defacing ¨ Some are political protests – 2000 - Pro-Israeli and Pro-Palestinian (e-Jihad) hackers deface sites – 2000 - Hamas site and Al Qaeda site visitors diverted to porn sites – 2001 - Chinese posted picture of downed pilot on US Govt sites – 2003 - web sites defaced by anti/pro war in Iraq – 2008 – CERN site was defaced after the big bang experiment t an ay d o T ev el ¨ Businesses are also affected – 1999 - NASDAQ and AMEX sites are defaced – 2001 - British Telecom defaced by hackers complaining about service – 2002 – RIAA site is defaced and provides pirated music for download R t o N ¨ Massive defacing – 2001 - hacker group defaces 679 sites in 1 minute – 2003 - Blackhat defacing competition: winner must deface 6000 sites asap ¨ 2007 – US government sites pointing to Viagra and porn sites
Nightmare Scenario #4: Website defacing ¨ Some are political protests – 2000 - Pro-Israeli and Pro-Palestinian (e-Jihad) hackers deface sites – 2000 - Hamas site and Al Qaeda site visitors diverted to porn sites – 2001 - Chinese posted picture of downed pilot on US Govt sites – 2003 - web sites defaced by anti/pro war in Iraq – 2008 – CERN site was defaced after the big bang experiment t an ay d o T ev el ¨ Businesses are also affected – 1999 - NASDAQ and AMEX sites are defaced – 2001 - British Telecom defaced by hackers complaining about service – 2002 – RIAA site is defaced and provides pirated music for download R t o N ¨ Massive defacing – 2001 - hacker group defaces 679 sites in 1 minute – 2003 - Blackhat defacing competition: winner must deface 6000 sites asap ¨ 2007 – US government sites pointing to Viagra and porn sites
 Nightmare Scenario #5: Service interruptions ¨ ¨ ¨ 1996 - Panix (ISP) suffers a Do. S SYN attack 1999 - Melissa crashes e-mail servers (replicates to Outlook contacts) 2000 - Mafiaboy attack crashes Yahoo, CNN, Amazon for 3 hours 2003 - RIAA site is attacked 2004 - My. Doom (email virus) attacks Microsoft, SCO sites 2007 - Estonia infrastructure attacked by Russian hackers ¨ 27% of companies running web services reported Do. S attacks ¨ The Knesset, Israeli PM and other ministries are constantly attacked ¨ Today, the main concern is around Vo. IP, wireless infrastructure. ¨ What is next? Power plants? Other forms of Cyber-Terrorism?
Nightmare Scenario #5: Service interruptions ¨ ¨ ¨ 1996 - Panix (ISP) suffers a Do. S SYN attack 1999 - Melissa crashes e-mail servers (replicates to Outlook contacts) 2000 - Mafiaboy attack crashes Yahoo, CNN, Amazon for 3 hours 2003 - RIAA site is attacked 2004 - My. Doom (email virus) attacks Microsoft, SCO sites 2007 - Estonia infrastructure attacked by Russian hackers ¨ 27% of companies running web services reported Do. S attacks ¨ The Knesset, Israeli PM and other ministries are constantly attacked ¨ Today, the main concern is around Vo. IP, wireless infrastructure. ¨ What is next? Power plants? Other forms of Cyber-Terrorism?
 Nightmare Scenario #6: Fraud and Identity Theft ¨ FTC Survey (2003) – 4. 6% of consumers defrauded in 2003 (12. 7% in past 5 years) – Mostly credit cards, but also bank accounts, loans, mortgage apps. . . – Total ID Fraud estimated at $50 B a year ¨ Internet payment fraud is rampant – 20 times the “normal” rate; typically identity theft – Used to be easy to change fields (e. g. price) in web forms ¨ Fraudulent merchants and con-artists defraud users – Phishing rampant everywhere – Fraudulent porn services “re-used” credit card numbers ¨ Identity theft becomes one of biggest problems (2007) – Fraudsters and mafia stealing “whole identities” – Use to buy, take loans, sell houses, etc. , ruining victim’s credit history ¨ Who is that merchant I am going to to buy from? difficult to authenticate…
Nightmare Scenario #6: Fraud and Identity Theft ¨ FTC Survey (2003) – 4. 6% of consumers defrauded in 2003 (12. 7% in past 5 years) – Mostly credit cards, but also bank accounts, loans, mortgage apps. . . – Total ID Fraud estimated at $50 B a year ¨ Internet payment fraud is rampant – 20 times the “normal” rate; typically identity theft – Used to be easy to change fields (e. g. price) in web forms ¨ Fraudulent merchants and con-artists defraud users – Phishing rampant everywhere – Fraudulent porn services “re-used” credit card numbers ¨ Identity theft becomes one of biggest problems (2007) – Fraudsters and mafia stealing “whole identities” – Use to buy, take loans, sell houses, etc. , ruining victim’s credit history ¨ Who is that merchant I am going to to buy from? difficult to authenticate…
 Nightmare Scenario #7: E-Mail Blues ¨ It used to be many forms of Viruses. Worms, Trojans spread via mail – Attract download software/applet (some pretend to help against a virus) – Phishing grows quickly – Spoof sender address and identity – Huge economic cost due to destruction, traffic, cleanup costs – At its peak, 8% of emails were My. Doom ¨ Today, Spam makes up >80% of email traffic – Started with Internet – economic model of direct marketing fails – Spoofing mail address, headers, names, etc – Cause significant economic damage ¨ Unprotected e-mail became almost unusable for simple e-mail users ¨ Proposed solutions are both technological and legal – New comprehensive email solutions include: anti-virus/worms, fraud, spam, content policy, privacy, and confidentiality – Microsoft initiative, Challenge-response mechanisms, Caller-ID
Nightmare Scenario #7: E-Mail Blues ¨ It used to be many forms of Viruses. Worms, Trojans spread via mail – Attract download software/applet (some pretend to help against a virus) – Phishing grows quickly – Spoof sender address and identity – Huge economic cost due to destruction, traffic, cleanup costs – At its peak, 8% of emails were My. Doom ¨ Today, Spam makes up >80% of email traffic – Started with Internet – economic model of direct marketing fails – Spoofing mail address, headers, names, etc – Cause significant economic damage ¨ Unprotected e-mail became almost unusable for simple e-mail users ¨ Proposed solutions are both technological and legal – New comprehensive email solutions include: anti-virus/worms, fraud, spam, content policy, privacy, and confidentiality – Microsoft initiative, Challenge-response mechanisms, Caller-ID
 Current Statistics and Impact
Current Statistics and Impact
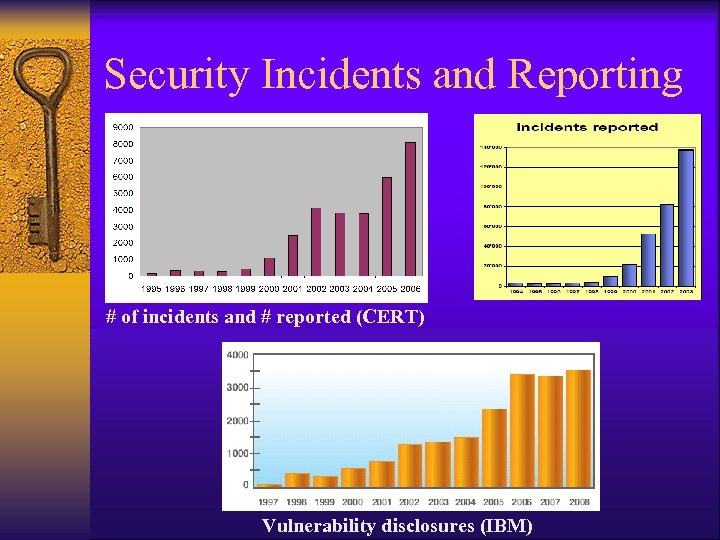 Security Incidents and Reporting # of incidents and # reported (CERT) Vulnerability disclosures (IBM)
Security Incidents and Reporting # of incidents and # reported (CERT) Vulnerability disclosures (IBM)
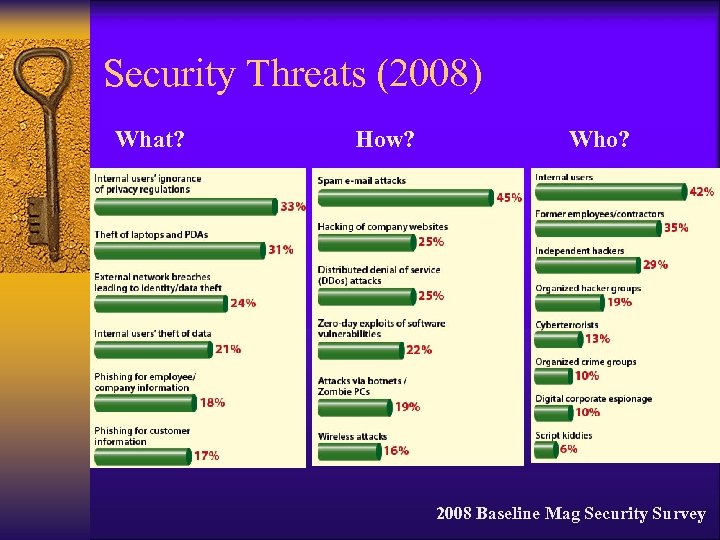 Security Threats (2008) What? How? Who? 2008 Baseline Mag Security Survey
Security Threats (2008) What? How? Who? 2008 Baseline Mag Security Survey
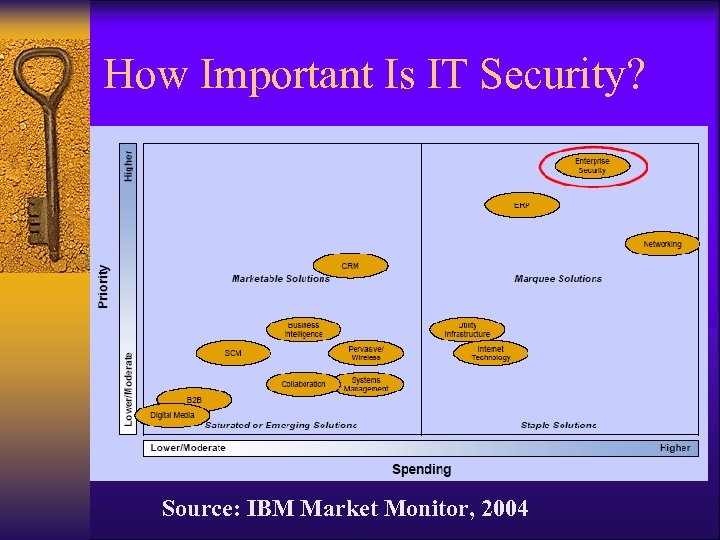 How Important Is IT Security? Source: IBM Market Monitor, 2004
How Important Is IT Security? Source: IBM Market Monitor, 2004
 Course Plan and Administrativia
Course Plan and Administrativia
 Course Plan ¨ Cryptography – history, conventional, public-key, key dist/mgmt ¨ Identity Authentication – Signatures, challenge-response, identity authentication ¨ Securing Communications Protocols – IPSec, VPNs, Web security (SSL), Wi. Fi Security ¨ Access Control – Kerberos, Firewalls, PKI ¨ Malicious Code and Intruders – Viruses, Worms, Intrusion detection, Spyware ¨ Application Security – Email security, Spam, Vo. IP, Cellphones ¨ Market Trends: Guest Presentations
Course Plan ¨ Cryptography – history, conventional, public-key, key dist/mgmt ¨ Identity Authentication – Signatures, challenge-response, identity authentication ¨ Securing Communications Protocols – IPSec, VPNs, Web security (SSL), Wi. Fi Security ¨ Access Control – Kerberos, Firewalls, PKI ¨ Malicious Code and Intruders – Viruses, Worms, Intrusion detection, Spyware ¨ Application Security – Email security, Spam, Vo. IP, Cellphones ¨ Market Trends: Guest Presentations
 Course Materials ¨ Course site – http: //www 1. idc. ac. il/compsec ¨ Most course material is from current sources – News, Industry (analysts, conferences, vendors), Academic – Subject-specific books ¨ Main Textbook – “Network Security Essentials: Applications and Standards” / William Stallings (old edition OK) ¨ Highly recommended – Applied Cryptography / Bruce Schneier
Course Materials ¨ Course site – http: //www 1. idc. ac. il/compsec ¨ Most course material is from current sources – News, Industry (analysts, conferences, vendors), Academic – Subject-specific books ¨ Main Textbook – “Network Security Essentials: Applications and Standards” / William Stallings (old edition OK) ¨ Highly recommended – Applied Cryptography / Bruce Schneier
 Administrativia ¨ Lecturer: Dr. Ron Rymon ¨ Teaching Assistant: Ilan Atias ¨ Lectures: Sunday 9: 15 -11: 45 am, C 109 ¨ Secondary slot: Tue evening, 6 pm (if needed) ¨ Office Hours: by appointment ¨ Credits: 3 ¨ Open to CS MSc, and BSc (2 nd and 3 rd year) students ¨ Grade: 70% exam, 30% other (project, in-class quizes, homework) – Must pass the exam – Must turn in all work, in time
Administrativia ¨ Lecturer: Dr. Ron Rymon ¨ Teaching Assistant: Ilan Atias ¨ Lectures: Sunday 9: 15 -11: 45 am, C 109 ¨ Secondary slot: Tue evening, 6 pm (if needed) ¨ Office Hours: by appointment ¨ Credits: 3 ¨ Open to CS MSc, and BSc (2 nd and 3 rd year) students ¨ Grade: 70% exam, 30% other (project, in-class quizes, homework) – Must pass the exam – Must turn in all work, in time
 Models of Computer Security
Models of Computer Security
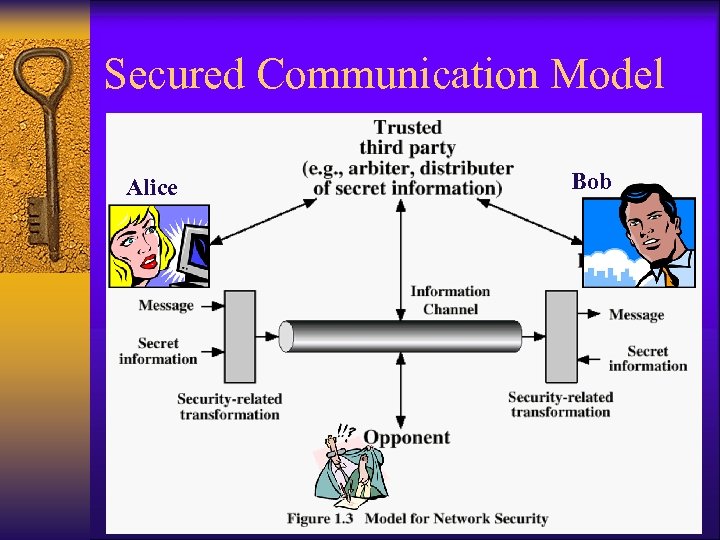 Secured Communication Model Alice Bob
Secured Communication Model Alice Bob
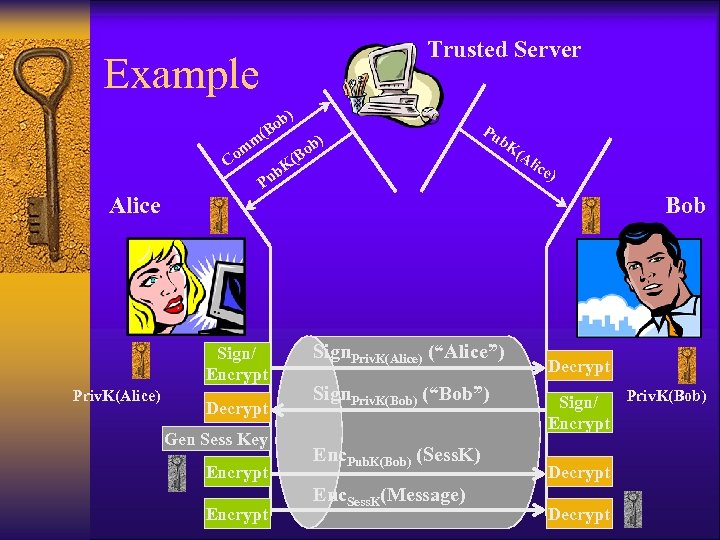 Trusted Server Example ) ( m om b Bo C Alice Pu b. K (A Decrypt Gen Sess Key Encrypt lic e ) P Sign/ Encrypt Priv. K(Alice) Bo ( K ub b) Bob Sign. Priv. K(Alice) (“Alice”) Sign. Priv. K(Bob) (“Bob”) Enc. Pub. K(Bob) (Sess. K) Enc. Sess. K(Message) Decrypt Priv. K(Bob) Sign/ Encrypt Decrypt
Trusted Server Example ) ( m om b Bo C Alice Pu b. K (A Decrypt Gen Sess Key Encrypt lic e ) P Sign/ Encrypt Priv. K(Alice) Bo ( K ub b) Bob Sign. Priv. K(Alice) (“Alice”) Sign. Priv. K(Bob) (“Bob”) Enc. Pub. K(Bob) (Sess. K) Enc. Sess. K(Message) Decrypt Priv. K(Bob) Sign/ Encrypt Decrypt
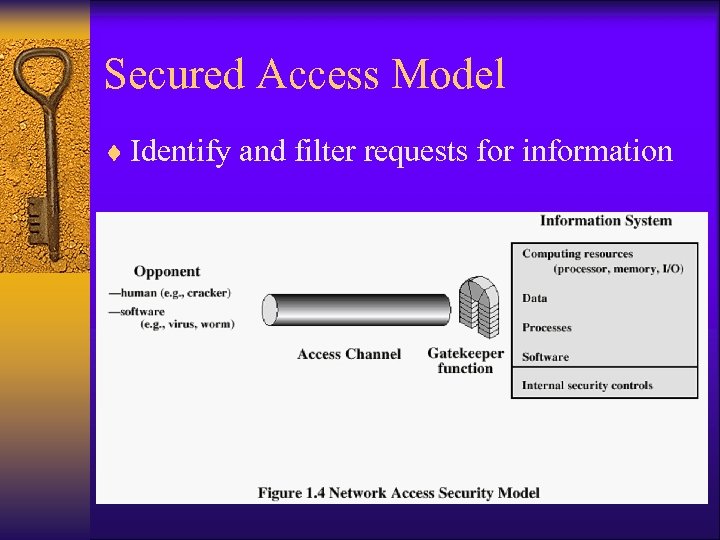 Secured Access Model ¨ Identify and filter requests for information
Secured Access Model ¨ Identify and filter requests for information
 Access Control Model ¨ Authentication – Must provide credentials to access a resource • E. g. , password, fingerprint, identification card ¨ Authorization – Must be authorized to gain access to specific data, other computing resources. • E. g. , file systems, firewalls, application authorization model • Various levels of granularity
Access Control Model ¨ Authentication – Must provide credentials to access a resource • E. g. , password, fingerprint, identification card ¨ Authorization – Must be authorized to gain access to specific data, other computing resources. • E. g. , file systems, firewalls, application authorization model • Various levels of granularity
 ITU/IETF X. 800: Security Threats, Attacks, Services, and Mechanisms ¨ Security Threat: A potential attack on systems or on information security needs ¨ Security Attack: An attempt to compromise the security of systems or information – Example: Eavesdropping on communication ¨ Security Service: Use of one or more mechanisms to enhance the security of a system or application – Example: Confidentiality of communications ¨ Security Mechanism: A specific method to detect, prevent, or recover from an attack, and to provide the required service – Example: Encryption software
ITU/IETF X. 800: Security Threats, Attacks, Services, and Mechanisms ¨ Security Threat: A potential attack on systems or on information security needs ¨ Security Attack: An attempt to compromise the security of systems or information – Example: Eavesdropping on communication ¨ Security Service: Use of one or more mechanisms to enhance the security of a system or application – Example: Confidentiality of communications ¨ Security Mechanism: A specific method to detect, prevent, or recover from an attack, and to provide the required service – Example: Encryption software
 Attacks: The X. 800 Threat Model
Attacks: The X. 800 Threat Model
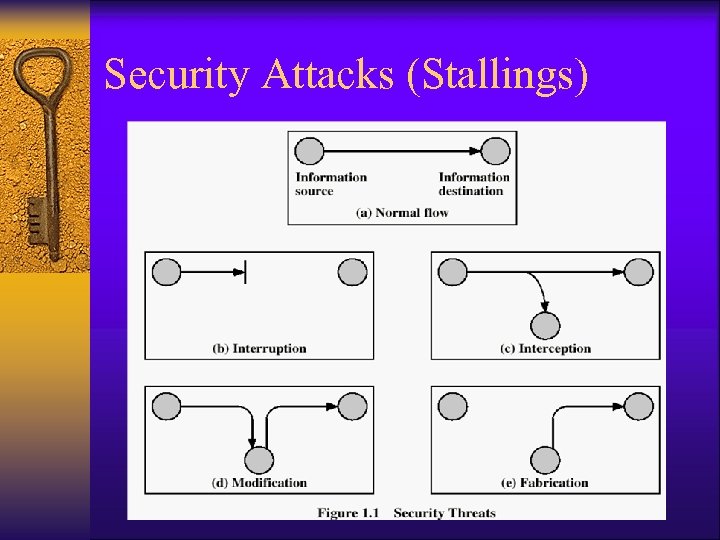 Security Attacks (Stallings)
Security Attacks (Stallings)
 Examples of Attacks ¨ Attacks can be Active, e. g. , intrusion, or Passive, e. g, eavesdropping ¨ Examples of attacks: – – – Intrusion Eavesdropping Impersonation Viruses / Worms Denial of service Man-in-the-middle Reflection attack Replay attack Password cracking Data/code modification Fraudulent attribution Repudiation
Examples of Attacks ¨ Attacks can be Active, e. g. , intrusion, or Passive, e. g, eavesdropping ¨ Examples of attacks: – – – Intrusion Eavesdropping Impersonation Viruses / Worms Denial of service Man-in-the-middle Reflection attack Replay attack Password cracking Data/code modification Fraudulent attribution Repudiation
 X. 800 Security Services ¨ Authentication – Identify peers, Source authentication for data ¨ Access Control – Who can access to what ¨ Data Confidentiality – Connection, Connectionless (system), Traffic, Privacy ¨ Data Integrity – With or without recovery ¨ Non-repudiation – Origin, Destination, Both ¨ Availability – A service on its own, or a property of other services
X. 800 Security Services ¨ Authentication – Identify peers, Source authentication for data ¨ Access Control – Who can access to what ¨ Data Confidentiality – Connection, Connectionless (system), Traffic, Privacy ¨ Data Integrity – With or without recovery ¨ Non-repudiation – Origin, Destination, Both ¨ Availability – A service on its own, or a property of other services
 Security Mechanisms ¨ Specific use of certain algorithms, protocols, and procedures to provide one or more security services ¨ Examples – Authentication – use password, fingerprint, magnetic card – Access Control – specify access rights based on the user id, role/group to specific transactions and/or specific content – Data Confidentiality – encrypt information using a specific algorithm – Data Integrity – detect and prevent unauthorized change to content – Non-Repudiation – use electronic signature to ensure authenticity – Availability – increase resiliency, filter malicious traffic ¨ Many security mechanisms use Cryptography as an underlying technology
Security Mechanisms ¨ Specific use of certain algorithms, protocols, and procedures to provide one or more security services ¨ Examples – Authentication – use password, fingerprint, magnetic card – Access Control – specify access rights based on the user id, role/group to specific transactions and/or specific content – Data Confidentiality – encrypt information using a specific algorithm – Data Integrity – detect and prevent unauthorized change to content – Non-Repudiation – use electronic signature to ensure authenticity – Availability – increase resiliency, filter malicious traffic ¨ Many security mechanisms use Cryptography as an underlying technology
 Next Class: Steganography and History of Cryptography
Next Class: Steganography and History of Cryptography


