87a5b8cb037c584d540d3f4e2893bfec.ppt
- Количество слайдов: 22
 Computational Policies in a Need to Share Environment Tim Finin University of Maryland, Baltimore County Sem. Grail workshop, Redmond WA, 21 June 2007
Computational Policies in a Need to Share Environment Tim Finin University of Maryland, Baltimore County Sem. Grail workshop, Redmond WA, 21 June 2007
 Introduction • Comments on the role of and requirements for computational policies in today’s environment – Web, 9/11, pervasive computing, … • Ideas in development in collaboration with colleagues from UT Dallas, GMU, and MIT
Introduction • Comments on the role of and requirements for computational policies in today’s environment – Web, 9/11, pervasive computing, … • Ideas in development in collaboration with colleagues from UT Dallas, GMU, and MIT
 Background • We’ve been working on computational policies since about 1999 – Started with XML encoded horn clauses for supply chain mgmt & pervasive computing • Moved policy research to the Semantic Web in ~2002 – Lalana Kagal developed Rei in her dissertation • Applications have varied – Also enhanced P 3 P, service matching and selection, collaborative teams, RDF store access, and distributed router configuration.
Background • We’ve been working on computational policies since about 1999 – Started with XML encoded horn clauses for supply chain mgmt & pervasive computing • Moved policy research to the Semantic Web in ~2002 – Lalana Kagal developed Rei in her dissertation • Applications have varied – Also enhanced P 3 P, service matching and selection, collaborative teams, RDF store access, and distributed router configuration.
 Policy-based Automated Wide-Area Network Configuration and Management Goal: self configuring network routers running in a coalition environment demonstrating constraints on border gateway protocol
Policy-based Automated Wide-Area Network Configuration and Management Goal: self configuring network routers running in a coalition environment demonstrating constraints on border gateway protocol
 General approach • A computational policy describes a system’s actions or behavior • “Describes” can be – Specifies: whenever X, do Y – Constrains: doing X is permitted – Advises: whenever X, doing Y is preferred to doing Z • Public policies and common policies foster interoperability and cooperation
General approach • A computational policy describes a system’s actions or behavior • “Describes” can be – Specifies: whenever X, do Y – Constrains: doing X is permitted – Advises: whenever X, doing Y is preferred to doing Z • Public policies and common policies foster interoperability and cooperation
 Some lessons learned • Most of the work in developing a policy is in developing the domain ontology – Often the constraints are simple, e. g. , “For faculty use only” • Sharing policies means sharing domain models – The Semantic Web offers a sound and practical approach for shared domain models
Some lessons learned • Most of the work in developing a policy is in developing the domain ontology – Often the constraints are simple, e. g. , “For faculty use only” • Sharing policies means sharing domain models – The Semantic Web offers a sound and practical approach for shared domain models
 Some lessons learned • Several approaches to encoded the rules or constraints part of policies – Descriptions of permitted, forbidden and obliged classes of actions (KAOS) – Using rule extensions to RDF (Rei, Rein) • Some approaches are problematic – E. g. , uncertainty, probabilities, defaults • But OWL can do the heavy lifting in reasoning about the terms – Is Mary a full-time faculty member from a highereducational institution? What’s the evidence?
Some lessons learned • Several approaches to encoded the rules or constraints part of policies – Descriptions of permitted, forbidden and obliged classes of actions (KAOS) – Using rule extensions to RDF (Rei, Rein) • Some approaches are problematic – E. g. , uncertainty, probabilities, defaults • But OWL can do the heavy lifting in reasoning about the terms – Is Mary a full-time faculty member from a highereducational institution? What’s the evidence?
 New Requirements • 9/11 and related events illustrated problems in how sensitive information is managed • Managing information and services on the Web with appropriate security and privacy and simplicity is increasingly important and challenging • Autonomous devices like mobile phones, routers and medical equipment need access too.
New Requirements • 9/11 and related events illustrated problems in how sensitive information is managed • Managing information and services on the Web with appropriate security and privacy and simplicity is increasingly important and challenging • Autonomous devices like mobile phones, routers and medical equipment need access too.
 Need to Know, Need to Share • Traditional information security frameworks are based on “need to know” Unless you can prove that you have a prearranged right to this information, you can’t have it • The 9/11 commission recommended moving from this to “need to share” I think this information may be important for you to accomplish your mission and would like to share it with you
Need to Know, Need to Share • Traditional information security frameworks are based on “need to know” Unless you can prove that you have a prearranged right to this information, you can’t have it • The 9/11 commission recommended moving from this to “need to share” I think this information may be important for you to accomplish your mission and would like to share it with you
 Need to Know, Need to Share • Traditional information security frameworks are based on “need to know” Unless you can prove that you have a prearranged right to access this information, you can’t have it • The 9/11 commission recommended moving from this to “need to share” I think this information may be important for you to accomplish your mission and would like to share it with you
Need to Know, Need to Share • Traditional information security frameworks are based on “need to know” Unless you can prove that you have a prearranged right to access this information, you can’t have it • The 9/11 commission recommended moving from this to “need to share” I think this information may be important for you to accomplish your mission and would like to share it with you
 Just a slogan? • For “need to share” to be more than just a political slogan, we need to understand what it might mean technically • … and to explore its feasibility and desirability • … and the risks and benefits
Just a slogan? • For “need to share” to be more than just a political slogan, we need to understand what it might mean technically • … and to explore its feasibility and desirability • … and the risks and benefits
 Required Capabilities • • Semantic Interoperability Unknown principals Context Speech acts and negotiation Adjustable privacy Usage control, enforcement, accountability Explanations and provenance Ramifications
Required Capabilities • • Semantic Interoperability Unknown principals Context Speech acts and negotiation Adjustable privacy Usage control, enforcement, accountability Explanations and provenance Ramifications
 Semantic Interoperability • Having a shared policy requires that the parties agree on – The semantics of the policy language (e. g. , is everything not explicitly forbidden allowed? ) – The semantics of the domain ontology (e. g. , who’s a faculty member? ) • The Semantic Web is a big win here.
Semantic Interoperability • Having a shared policy requires that the parties agree on – The semantics of the policy language (e. g. , is everything not explicitly forbidden allowed? ) – The semantics of the domain ontology (e. g. , who’s a faculty member? ) • The Semantic Web is a big win here.
 Unknown Principles • Standard access control is based on authentication – I have a list of who can do what. Just prove to me which of these people you are • In open environments (Web, pervasive computing) this won’t work • We can control access based on their (provable) attributes – Prove you’re a current UMBC student to use the printer
Unknown Principles • Standard access control is based on authentication – I have a list of who can do what. Just prove to me which of these people you are • In open environments (Web, pervasive computing) this won’t work • We can control access based on their (provable) attributes – Prove you’re a current UMBC student to use the printer
 Context • What’s forbidden in a normal situation may be allowed in a life-threatening emergency • Context descriptions (e. g. , tags) can identify the current situation • Policy rules can be conditioned by context – E. g. , as guards on rules or by enabling/ disabling policy modules
Context • What’s forbidden in a normal situation may be allowed in a life-threatening emergency • Context descriptions (e. g. , tags) can identify the current situation • Policy rules can be conditioned by context – E. g. , as guards on rules or by enabling/ disabling policy modules
 Adjustable privacy • One way to enforce privacy is to not divulge information • Another is to provide general answers • Where’s John? – [47. 670412403362256, -122. 12013959884644] – In Redmond – In Washington state – On travel • Policies can control the granularity of answers given to different queries
Adjustable privacy • One way to enforce privacy is to not divulge information • Another is to provide general answers • Where’s John? – [47. 670412403362256, -122. 12013959884644] – In Redmond – In Washington state – On travel • Policies can control the granularity of answers given to different queries
 Usage control and accountability • Enforcing policies can be a difficult issue in open, distributed systems • MIT’s policy aware approach is exploring accountability for use – Policy violations can be detected in logs • There’s lots more to usage constraints – E. g. , DRM policies constrain how often you can perform certain operations on an object • Systems need to reason about there own behavior as well as that of others
Usage control and accountability • Enforcing policies can be a difficult issue in open, distributed systems • MIT’s policy aware approach is exploring accountability for use – Policy violations can be detected in logs • There’s lots more to usage constraints – E. g. , DRM policies constrain how often you can perform certain operations on an object • Systems need to reason about there own behavior as well as that of others
 Explanations and provenance • Explaining why a policy decision holds or doesn’t hold can be important – Explaining why a constraint does not hold continues to be a difficult task • The explanation may involve provenance, citing the source for the facts and policy constraints used
Explanations and provenance • Explaining why a policy decision holds or doesn’t hold can be important – Explaining why a constraint does not hold continues to be a difficult task • The explanation may involve provenance, citing the source for the facts and policy constraints used
 Utility and Ramifications • In some environments, the utility of data may be a factor in whether to share or not – This requires reasoning about the requestor’s tasks, the data’s relevance to them and the availability of alternate data • This may also require Bayesian reasoning – What’s the likelihood that the patient might have diabetes? • In general, a system might reason about the risks and benefits of sharing vs. . not sharing the data
Utility and Ramifications • In some environments, the utility of data may be a factor in whether to share or not – This requires reasoning about the requestor’s tasks, the data’s relevance to them and the availability of alternate data • This may also require Bayesian reasoning – What’s the likelihood that the patient might have diabetes? • In general, a system might reason about the risks and benefits of sharing vs. . not sharing the data
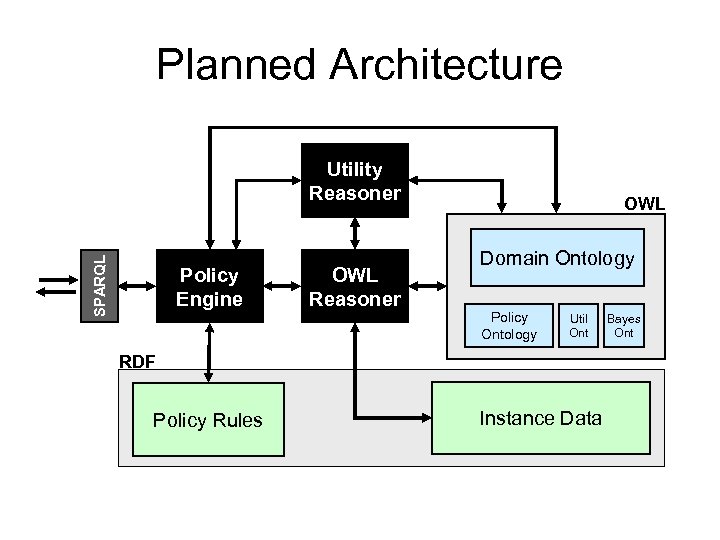 Planned Architecture SPARQL Utility Reasoner Policy Engine OWL Reasoner OWL Domain Ontology Policy Ontology Util Ont RDF Policy Rules Instance Data Bayes Ont
Planned Architecture SPARQL Utility Reasoner Policy Engine OWL Reasoner OWL Domain Ontology Policy Ontology Util Ont RDF Policy Rules Instance Data Bayes Ont
 Conclusion • Managing information in open, distributed environments with appropriate security and privacy is increasingly important • Computational policies can help • Semantic Web technologies offer a way to share common policy concepts, policies, and domain models • Other representation and reasoning components will be needed for many application domains.
Conclusion • Managing information in open, distributed environments with appropriate security and privacy is increasingly important • Computational policies can help • Semantic Web technologies offer a way to share common policy concepts, policies, and domain models • Other representation and reasoning components will be needed for many application domains.
 http: //ebiquity. umbc. edu/
http: //ebiquity. umbc. edu/


