 Comprehensive Intelligence Analysis and Alert System (CIAAS)
Comprehensive Intelligence Analysis and Alert System (CIAAS)
 Characteristics
Characteristics
 Sources of Information
Sources of Information
 The Problems
The Problems
 Human Analysts
Human Analysts
 Human Analysts
Human Analysts
 Requirements
Requirements
 The Approach
The Approach
 Challenges
Challenges
 e. Cognition™ Active Knowledge Network Technology
e. Cognition™ Active Knowledge Network Technology
 e. Cognition™ - Emulating the Cognitive Model
e. Cognition™ - Emulating the Cognitive Model
 Extract Knowledge in Diversified Forms
Extract Knowledge in Diversified Forms
 Use It For Diversified Purposes
Use It For Diversified Purposes
 Integrate Knowledge Domains
Integrate Knowledge Domains
 Diversified Disciplines Aggregates new pieces of information to existing knowledge Modeling Automatically draws inferences Network inferencing Integrates information from diverse sources and formats Data miner Performs Analysis (including temporal) Analyzer Inherent simulation capabilities Simulator
Diversified Disciplines Aggregates new pieces of information to existing knowledge Modeling Automatically draws inferences Network inferencing Integrates information from diverse sources and formats Data miner Performs Analysis (including temporal) Analyzer Inherent simulation capabilities Simulator
 Diversified Interfaces
Diversified Interfaces
 Advantages
Advantages
 Example – Crime Analysis Automation
Example – Crime Analysis Automation
 The Demo
The Demo
 Searching In an Ocean of Information
Searching In an Ocean of Information
 Some Details
Some Details
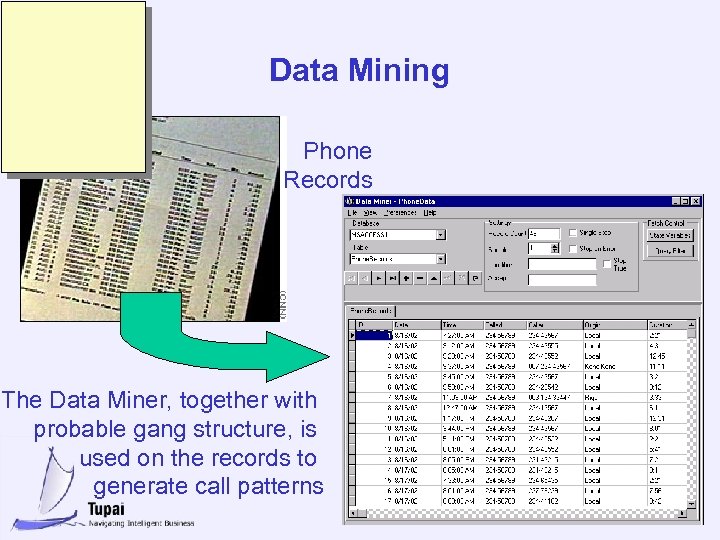 Data Mining Phone Records The Data Miner, together with probable gang structure, is used on the records to generate call patterns
Data Mining Phone Records The Data Miner, together with probable gang structure, is used on the records to generate call patterns
 Using Probabilities
Using Probabilities
 Time Series Analysis
Time Series Analysis
 Reversing the Use
Reversing the Use
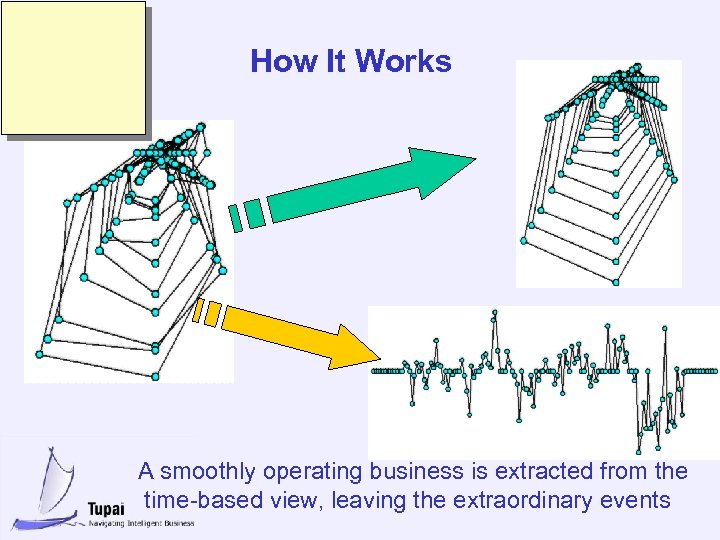 How It Works A smoothly operating business is extracted from the time-based view, leaving the extraordinary events
How It Works A smoothly operating business is extracted from the time-based view, leaving the extraordinary events
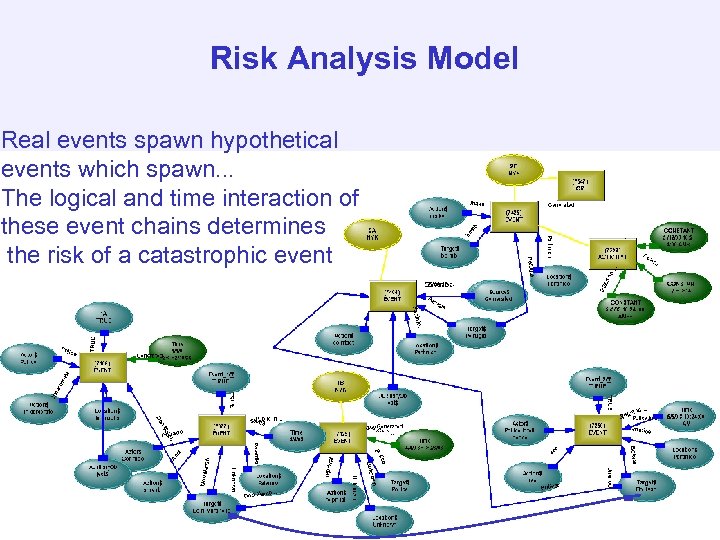 Risk Analysis Model Real events spawn hypothetical events which spawn. . . The logical and time interaction of these event chains determines the risk of a catastrophic event
Risk Analysis Model Real events spawn hypothetical events which spawn. . . The logical and time interaction of these event chains determines the risk of a catastrophic event
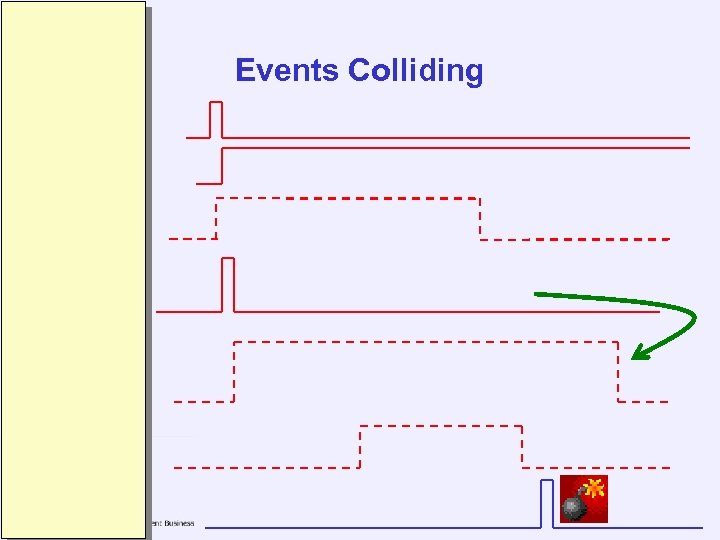 Events Colliding
Events Colliding