d4d8903bc73135df257a5debb2e0452d.ppt
- Количество слайдов: 36

COMP 2221 Networks in Organisations Richard Henson November 2012

Week 7: Windows Services… n Objectives: Ø Explain the mechanism for control of user and system settings on networked machines Ø Explain the role of the registry in desktop configuration, usability, and security Ø Explain the mechanisms typical TCP/IP-based network services Ø Use appropriate software tools for network services, system/network monitoring and troubleshooting
Rapid Boot-up with Windows 7 (1) n Huge improvements in time to logon screen… Ø 32 -bit colour animation appears at an early stage » driven by the CPU (& using Intel EFI) n graphics card not yet initiated… Ømeanwhile, operating system's kernel and critical device drivers are loading into memory in the background…
Rapid Boot-up with Windows 7 (2) n Early stage of boot process bound to i/o: Øloading the kernel Ødevice driver files Øother system component files n Dimensions of the boot animation limited to a small region of the screen Øavoids i/o delay loading animation images during the early stage of boot…
Rapid Boot-up with Windows 7 (3) n Changes to the boot “architecture” Ø Windows 7 animation happens as the process moves along » contrast with Vista, where the pear animation comes only after the boot sequence is complete… Ø fewer transitions in graphics mode during initialisation of the graphics subsystem and Windows shell » again, c. f. Vista, where screen flashes black a few times. . n Sound plays BEFORE user login starts…

BUT… n The user in an organisation then needs to log on… Øendless loading of policy files… Øsubsequent configuration to accommodate settings into the local registry…

Policy Files: Controlling User and System Settings… n Arguably the most important part of a network manager’s job Ø get it right: happy users, happy managers Ø get it wrong: frustrated users, angry managers

Even at remote locations (!) n General principle of no access at all without logon… n Policies determine the desktops and services available when users logon right access the (enterprise) network
User/System Policy Settings ØDifferent types of system? » different registry settings needed ØSystem settings for computer may need to be changed for particular users » e. g. lower screen refresh rate required for epileptics

Groups and Group Policy n Convenient for users to be put into groups ØSettings for group provides particular access to data & services n Problems… Øuser in wrong group(s) Øgroup has wrong settings
Users and Convenience n Windows Networks provide storage space on Server for user data: Ømandatory profiles » no storage for desktop settings all same desktop settings! Øroaming profiles » desktop settings preserved on Server between user sessions n n but takes extra space and makes logon even longer!

The all-important Registry n n Hierarchical store of system and user settings Five basic subtrees: Ø HKEY_LOCAL_MACHINE : local computer info. Does not change no matter which user is logged on Ø HKEY_USERS : default user settings Ø HKEY_CURRENT_USER : current user settings Ø HKEY_CLASSES_ROOT : software config data Ø HKEY_CURRENT_CONFIG : “active” hardware profile n Each subtree contains one or more subkeys

Location… n C: windowssystem 32config n Six files (no extensions): Ø Software Ø System – hardware settings Ø Sam, Security » not viewable through regedt 32 Ø Default – default user Ø Sysdiff – HKEY USERS subkeys n Also: ntuser. dat file Ø user settings that override default user

Emergency Recovery if Registry is damaged n Backup registry files created during textbased part of windows installation Øalso stored in: » C: windowssystem 32config » distinguished by. sav suffix Øonly used to update registry if “R” option is chosen during a windows recovery/reinstall

Emergency Recovery if registry completely ruined… n Another NEVER UPDATED backup is saved to C: windowsrepair Øcontains no user and software settings Øreboots back to the point: » “Windows is now setting up”
Backing up the Registry n Much forgotten… Ø can be copied to tape, USB stick CD/DVD, or disk Ø rarely more than 100 Mb n Two options; Ø Use third-party backup tool » e. g http: //www. acronis. co. uk Ø Use windows “backup” » not recommended by experts! » already there & it does work! » when choosing backup options, “system state” should be selected

Editing “Live” Registry Settings n Registry data that is loaded into memory can also be overwritten by data: Ø from local profiles (ntconfig. pol) Ø downloaded across the network… n Contents should not be changed manually unless you really know what you are doing!!! n Special command line tool available for editing individual system settings: Ø REGEDT 32

Policy Files n Collection of registry settings in a text file Ø downloaded from the domain controller during logon Ø settings depend on the user or group logging on n Can overwrite: Ø local machine registry settings Ø current user registry settings n Policies should therefore only be created and used by those who know what they are doing!!!

Group Policy Files n Local Computer (local policy) Øread from local machine n Domain Controllers (domain policy) Ødownloaded across the network n Read by CPU on local machine during logon procedure Øsubsequently written to registry Øcontrol user desktop
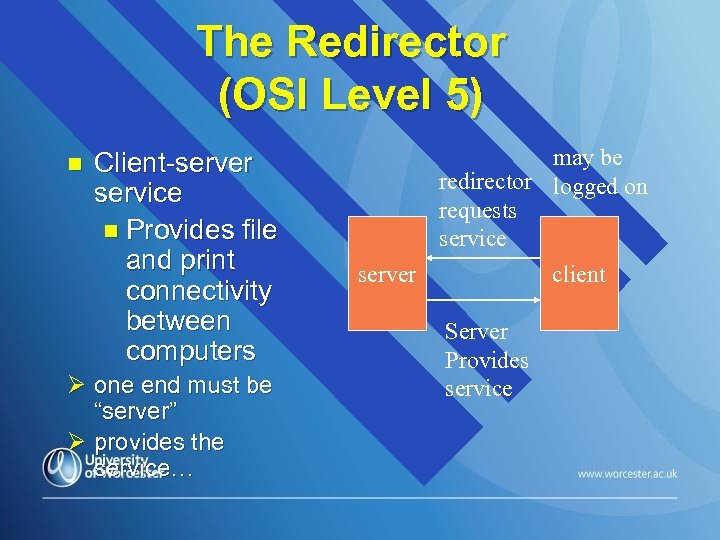
The Redirector (OSI Level 5) n Client-server service n Provides file and print connectivity between computers Ø one end must be “server” Ø provides the service… may be redirector logged on requests service server client Server Provides service

Redirector (“Workstation” i. e. client-end) n Implemented as a file system driver Øonly called if local file system cannot find the file or service Øsends request to active directory to locate the data object via Transport Driver Interface (TDI) » communicates directly with transport protocols » allows independence of networking components in OSI layers 2 -4
Redirector (Workstation Service) n Adherence to OSI layers… Ø Can independently add or remove: » transport protocols (layers 3 & 4) » network cards (layers 1 & 2) without reconfiguring the whole system n Completely transparent in redirection of i/o calls not serviced locally Ø esp. important when applications are being used

Server Service n Server end of redirector: Ø implemented as a file system driver Ø communicates with lower layers via TDI n n Supplies the network connections requested by the client redirector Receives requests via adapter card drivers, transport protocol (e. g. TCP/IP), and TDI
Running Client-Server Applications n Client process & server process provide a mechanism for: Ø pipes to link processes that need bi-directional communication Ø mailslots to link processes only requiring onedirectional communication Ø running Winsock to manage the communication channel Ø RPCs (Remote Procedure Calls) allowing distributed applications to call procedures anywhere on the network
File and Print Sharing n Shared resource access requires use of Ø redirector Ø server service… n Multiple UNC Provider allows connection to a resource on any computer that supports UNC Universal Naming Convention) names Ø Files \servershared folder[sub-folder]filename) Ø Printers \servershared printer n Multiple Provider Router supports multiple redirectors

Network Binding n n Binding is about linking network components working at different OSI levels together to enable communication Windows binding is about linking the redirector & server service with the transport protocol and (via NDIS) adapter card drivers Ø happens automatically when: » there is a change of protocol, or protocol settings » different network adapter drivers are installed » existing adapter card settings are altered

WINS (Windows Internet Names Service) n Client-server protocol like DNS, DHCP Ø used on first Windows TCP/IP networks to enable computer devices to communicate using IP Ø manages a dynamic database of IP addresses and local network (Net. BIOS) names Ø clients request IP addresses for particular Net. BIOS names Ø WINS server provides that information n Historical, but NETBIOS names still used in some places

Terminal Services n Allows any PC running a version of Windows to remotely run a Windows server Øuses a copy of the server’s desktop on the client machine n Client tools must be installed first, but the link can run with very little bandwidth Ø possible to remotely manage a server thousands of miles away using a phone connection…

More about the www service n Provided by Microsoft’s Web Server (IIS) Ø links to TCP port 80 Ø can also provide: » ftp service (port 21) » smtp service (port 25) n Purpose of www service: Ø Works with http protocol make html pages available: » across the network as an Intranet » across trusted external users/domains as an Extranet

Features of IIS n Provides server end program execution environment: Ø runs server-scripts n n n Sets up its own directory structure on the Server for developing Intranets, Extranets, etc. Sets up communication via TCP port 80 in response to client request Client end: Ø browser HTML display environment on client
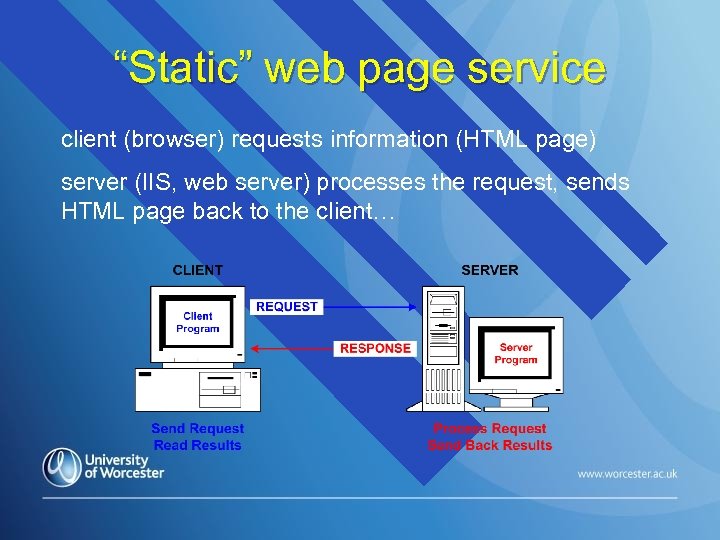
“Static” web page service client (browser) requests information (HTML page) server (IIS, web server) processes the request, sends HTML page back to the client…

More Features of IIS n Access to any client-server service can be restricted using username/password security at the server end Øor could bypass security with “anonymous login » uses a “guest” account – access granted only to files that make up the Intranet » prevents worries about hacking in through guessing passwords of existing users
Client-Server Web Applications n n Associated with “dynamic” web pages Web servers provides a server-side environment that can allow browser data to query remote online databases using SQL… Ø processing takes place at the server end Ø centralised and secure! n Some recent challenges to client-server applications Ø apps using local processing, even storage (!) Ø again…issue of availability v security
Troubleshooting Resources n Task Manager Ø Applications tab just gives the name and status of each application that is loaded into memory Ø Processes tab: » all system processes » Memory usage of each » % CPU time for each » Total CPU time since boot up Ø Performance tab » Total no. of threads, processes, handles running » % CPU usage n n Kernel mode User mode » Physical memory available/usage » Virtual memory available/usage
Troubleshooting Resources n Event viewer Ø System events recorded into “event log” files » Three by default: system, auditing, application » customisable Ø Three types of events: » Information » Warning » Error Ø More information for each event obtained by double-clicking Ø Event management also required… » E. g. new files daily, old ones archived? dumped? when? » how often to check event files? » Important to detect security issues and potential failures
Troubleshooting Resources n System Monitor (perfmon. msc) Ø monitor many aspects of system performance Ø e. g. capture, filter, or analyses frames or packets sent over the network, or capture data from hardware devices » either display current data graphically, in real-time » or log data at regular intervals to get a longer term picture Ø Alerts » notify when a particular threshold value has been reached n System Recovery… Ø If a fatal error occurs: » immediate dump of system memory is made n can be used for identifying the cause of the problem » alerts are sent to users » system is restarted automatically
d4d8903bc73135df257a5debb2e0452d.ppt