239896132f0e683caafa7dfd966d60f8.ppt
- Количество слайдов: 16

Combating e-Crime in a rapidly evolving digital market Annual Future of Security in Banking & Financial Services March 2011

Combating e-Crime AGENDA • • • EVOLUTION ENTERPRISE STRATEGIES TOOLS The evolution of cyber crime – a Suncorp perspective Building an enterprise financial crime solution Multi-layered defence strategies Essential tools and the future Questions

Cyber Crime Evolution AGENDA EVOLUTION ENTERPRISE STRATEGIES TOOLS Cyber Crime (n): Offences against computers and computer systems and technology enabled crime Source: House Standing Committee on Communications 2010

Cyber Crime Evolution AGENDA EVOLUTION OLD WORLD ENTERPRISE STRATEGIES NEW WORLD • Hacking • Denial of Service Attacks • Internet Banking Fraud • Card Skimming • Terminal Tampering • Wire Intercepts • Phone Banking • Vishing • Porting TOOLS
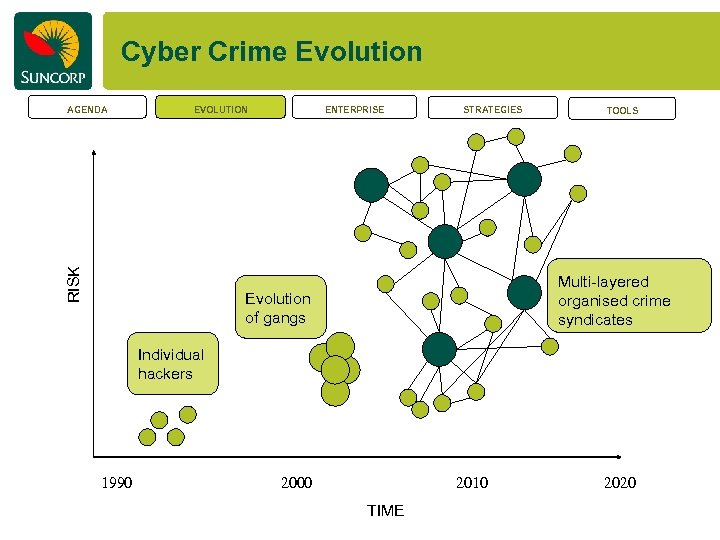
Cyber Crime Evolution EVOLUTION RISK AGENDA ENTERPRISE STRATEGIES TOOLS Multi-layered organised crime syndicates Evolution of gangs Individual hackers 1990 2000 2010 TIME 2020
Enterprise Financial Crime Solution AGENDA EVOLUTION ENTERPRISE STRATEGIES TOOLS We wanted to produce a system which provided detection capability across: – – – AML/CTF (including sanction monitoring) Internet Banking Fraud Phone Banking Fraud Cheque Fraud Branch Transaction Fraud Merchant Fraud and – Internal Fraud • Near real time coverage • Leverage data elements across multiple channels • Increase amount of data elements • Deliver single platform efficiencies • Increase data history holdings to improve analytical effectiveness • Move away from Black Box reliance to fluid analytics

Enterprise Financial Crime Solution AGENDA EVOLUTION ENTERPRISE STRATEGIES TOOLS Fraud management for Suncorp – a hands on approach • Seized control back from Business Technology. – Uplift in effectiveness – Control timeliness • Employed analysts who have the skills and drive to pro-actively detect fraud. • Own, know and understand our data.

Multi-layered Defence Strategies ENTERPRISE STRATEGIES High Tech Crime Operations / Aus. Cert Interbank e-Crime Collaborative Strategic EVOLUTION Operational AGENDA 3 rd Party Intelligence Sharing TOOLS
Multi-layered Detection Strategies AGENDA EVOLUTION ENTERPRISE STRATEGIES TOOLS The Irony! TXN Classic e-fraud is the easiest to detect of all frauds Data is Key • Transaction attributes • IP attributes • Packet Information • Receiver Information
Multi-layered Detection strategies AGENDA EVOLUTION ENTERPRISE STRATEGIES TOOLS Why is it ironic? Internet Banking Fraud normally contains the following traits: • The transfer is from a different IP address • The transfer is going into a new account • The transfer is often larger than normal What’s beginning to develop? • 2 Factor bypass • Proxying through customers PC

Multi-layered Detection strategies AGENDA EVOLUTION ENTERPRISE STRATEGIES Current multi-layered detection strategies Accumulative risk scoring on below • The transfer is from a different IP address • The transfer is going into a new account • The transfer is often larger than normal Strategies to combat recent developments Reliance on the Profile (normality) Packet comparison Industry IP Sharing TOOLS
What tools are essential for the future AGENDA EVOLUTION ENTERPRISE Main Threats to consider STRATEGIES TOOLS/FUTURE
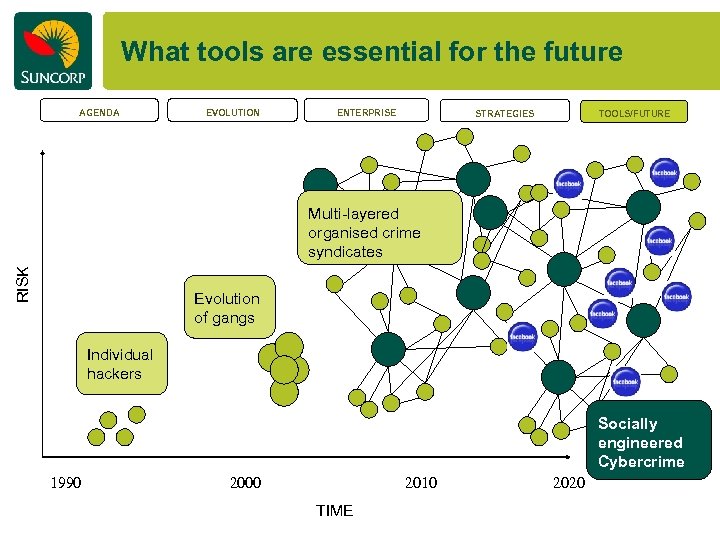
What tools are essential for the future AGENDA EVOLUTION ENTERPRISE STRATEGIES TOOLS/FUTURE RISK Multi-layered organised crime syndicates Evolution of gangs Individual hackers Socially engineered Cybercrime 1990 2000 2010 TIME 2020

Essential tools for the future EVOLUTION Fluid analytics which can model on the fly Intervention in only highrisk transactions ENTERPRISE Real Time Fraud Intervention AGENDA STRATEGIES TOOLS/FUTURE Real time intelligence sharing Detect more complex fraud indicators such as authentication bypass

E-crime in a rapidly evolving digital market Questions?

239896132f0e683caafa7dfd966d60f8.ppt