f090fd6c8b28f5b48301845541cbe9a4.ppt
- Количество слайдов: 82
COBIT® Presentation Package The COBIT® framework explained in a complete Power. Point presentation, to be used by professors in information systems management, information security management, auditing, information systems auditing and/or accounting information systems © ITGI 2004 - not for commercial use. 1

Disclaimer The IT Governance Institute® (ITGI), Information Systems Audit and Control Association® (ISACA®) [the “Owner(s)”] and the authors have designed and created COBIT® in Academia™ and its related publications, titled COBIT® Presentation Package, COBIT® Student Book, COBIT® Case Study and COBIT® Caselets (the “Work”), primarily as an educational resource for assurance professionals. The Owners make no claim that use of any of the Work will assure a successful outcome. The Work should not be considered inclusive of any proper information, procedures and tests or exclusive of other information, procedures and tests that are reasonably directed to obtaining the same results. In determining the propriety of any specific information, procedure or test, the assurance professional should apply his/her own professional judgement to the specific circumstances presented by the particular systems or information technology environment. © ITGI 2004 - not for commercial use. 2

Disclosure Copyright © 2004 IT Governance Institute. All rights reserved. This publication is intended solely for academic use and shall not be used in any other manner (including for any commercial purpose). Reproductions of selections of this publication are permitted solely for the use described above and must include the following copyright notice and acknowledgement: “Copyright © 2004 IT Governance Institute. All rights reserved. Reprinted by permission. ” COBIT in Academia may not otherwise be used, copied, or reproduced, in any form by any means (electronic, mechanical, photocopying, recording or otherwise), without the prior written permission of the IT Governance Institute. Any modification, distribution, performance, display, transmission, or storage, in any form by any means (electronic, mechanical, photocopying, recording or otherwise) of COBIT in Academia is strictly prohibited. No other right or permission is granted with respect to this work. COBIT in Academia ISBN 1 -893209 -96 -2 © ITGI 2004 - not for commercial use. 3

Acknowledgements Development Team Ø Erik Guldentops, CISA, CISM, University of Antwerp Management School, Belgium (Chair) Ø Roger Debreceny, Ph. D. , FCPA, University of Hawaii, USA Ø Steven De Haes, University of Antwerp Management School, Belgium (Project Manager) Ø Roger Lux, Farmers Insurance Group, USA Ø John Mitchell, CISA, CIA, CFE, LHS Business Control, UK Ø Ed O’Donnell, Ph. D. , Arizona State University, USA Ø Scott Summers, Ph. D. , Brigham Young University, USA Ø Wim Van Grembergen, Ph. D. , University of Antwerp Management School, Belgium © ITGI 2004 - not for commercial use. 4

Acknowledgements Review Team Rob Nehmer, Ph. D. , Quinnipiac University, USA Malcolm Pattinson, CISA, University of South Australia, Australia Elaine Mauldin, CPA, University of Missouri-Columbia, USA Faye Borthick, Ph. D. , CISA, CPA, AMA, CDP, Georgia State University, USA Ø José Roberto Alpizar Fallas, CPA, Universidad de Costa Rica, Costa Rica Ø Ø © ITGI 2004 - not for commercial use. 5

Purpose of This Document This COBIT Presentation Package, developed in collaboration with a group of international academics and practitioners, is a product of the IT Governance Institute (www. itgi. org). It provides a complete Power. Point presentation explaining all the core elements of the COBIT framework, which can be used by professors in information systems management, information security management, auditing, information systems auditing and/or accounting information systems. Professors can use the complete set, make extractions if they want to focus on specific parts, or can even add their own materials and examples in accordance with their needs. There are some speaker notes included in the package, but it is advisable to use the COBIT Student Book (included in COBIT in Academia) as guidance and source material to prepare this presentation. The IT Governance Institute also developed three other components that are part of COBIT in Academia. The COBIT Student Book explains and illustrates all the COBIT components. The COBIT Case Study: TIBO can be used by students to apply the COBIT knowledge in a real-life situation and the COBIT Caselets provides some minicases for smaller COBIT exercises. © ITGI 2004 - not for commercial use. 6
COBIT Introduction Why does IT need an IT control framework? Who needs an IT control framework? How and why is COBIT used? © ITGI 2004 - not for commercial use. 7
Why does IT need a control framework? Do any of these conditions sound familiar? Ø Increasing pressure to leverage technology in business strategies Ø Growing complexity of IT environments Ø Fragmented IT infrastructures Ø Communication gap between business and IT managers Ø IT service levels that are disappointing from internal IT functions and from increasingly outsourced IT providers Ø IT costs perceived to be out of control Ø Marginal ROI/productivity gains on technology investments Ø Impaired organisational flexibility and nimbleness to change Ø User frustration leading to ad hoc solutions © ITGI 2004 - not for commercial use. 8

Why does IT need a control framework? Ø Increasing dependence on information and the systems that deliver this information Ø Increasing vulnerabilities and a wide spectrum of threats, such as cyberthreats and information warfare Ø Scale and cost of the current and future investments in information and information systems Ø The need to comply with regulations Ø The potential for technologies to dramatically change organisations and business practices, create new opportunities and reduce costs Ø Recognition by many organisations of the potential benefits that technology can yield Successful organisations understand manage the risks associated with implementing new technologies. © ITGI 2004 - not for commercial use. 9
Why does IT need a control framework? To ensure that Ø IT provides value i Cost, time and functionality are as expected Ø IT does not provide surprises i Risks are mitigated Ø IT pushes the envelope i New opportunities and innovations for process, product and services management needs to get IT under control. © ITGI 2004 - not for commercial use. 10

Who needs a control framework? Ø Board and Executive • To ensure management follows and implements the strategic direction for IT Ø Management • To make IT investment decisions • To balance risk and control investment • To benchmark existing and future IT environment Ø Users • To obtain assurance on security and control of products and services they acquire internally or externally Ø Auditors • To substantiate opinions to management on internal controls • To advise on what minimum controls are necessary © ITGI 2004 - not for commercial use. 11
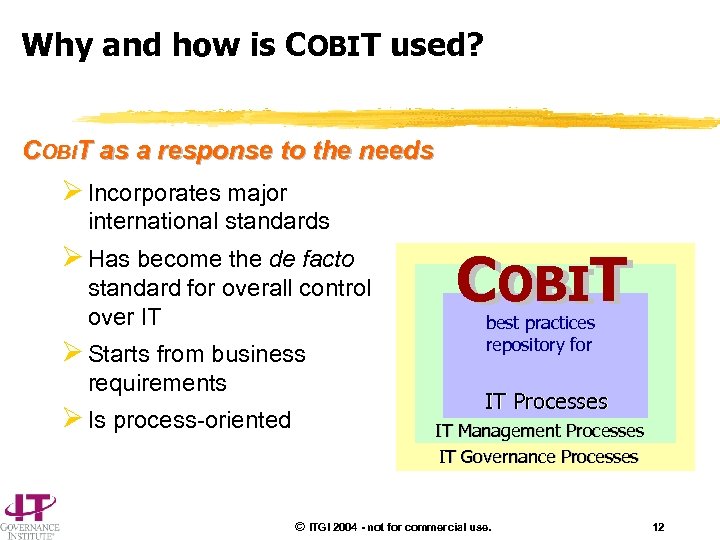
Why and how is COBIT used? COBIT as a response to the needs Ø Incorporates major international standards Ø Has become the de facto standard for overall control over IT Ø Starts from business requirements Ø Is process-oriented COBIT Cobi. T COBIT best practices repository for IT Processes IT Management Processes IT Governance Processes © ITGI 2004 - not for commercial use. 12

Why and how is COBIT used? Testimonials from Case Studies Ø Helps substantially increase acceptance and reduce time to implement IT governance program Ø Provides a guide formal audits/reviews Ø Helps use results of audits as an opportunity to plan improvements Ø Is a strong factor in achieving primary goals for IT governance: transform organisational practices and pursue improved processes Ø Provides economical continuous improvement framework Ø Provides a credible source for management's decision on controls Ø Impresses and helps IT operations managers with its ability to assist in understanding what auditors want Ø Is ideal for business management to communicate requirements and concerns Ø Is recognised as a reliable source reference that ensures identification of all major risk areas Ø Improves communications and relations with IT management © ITGI 2004 - not for commercial use. 13

Why and how is COBIT used? Results from Surveys Ø Ø Ø To improve audit approach/programmes To support audit work with detailed audit guidelines To provide guidance for IT governance As a valuable benchmark for IS/IT control To improve IS/IT controls To standardise audit approach/programmes © ITGI 2004 - not for commercial use. 14
The COBIT Framework The COBIT framework explained: Ø Business focus Ø Process orientation Ø IT resources © ITGI 2004 - not for commercial use. 15
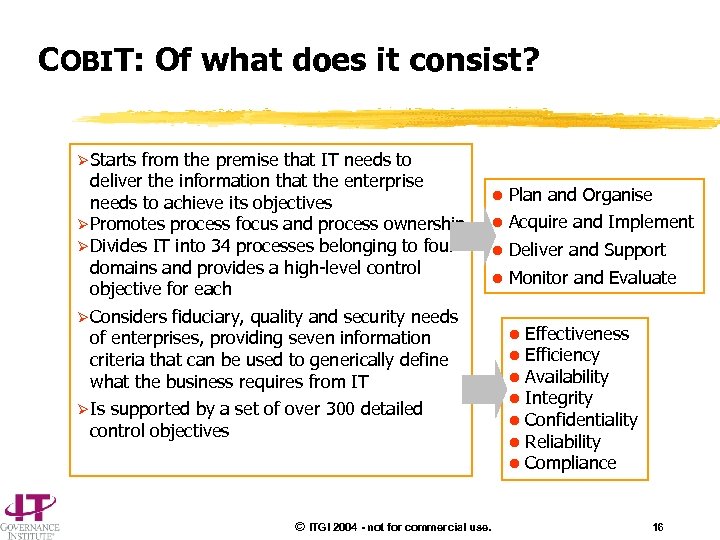
COBIT: Of what does it consist? Ø Starts from the premise that IT needs to deliver the information that the enterprise needs to achieve its objectives Ø Promotes process focus and process ownership Ø Divides IT into 34 processes belonging to four domains and provides a high-level control objective for each Ø Considers fiduciary, quality and security needs of enterprises, providing seven information criteria that can be used to generically define what the business requires from IT Ø Is supported by a set of over 300 detailed control objectives © ITGI 2004 - not for commercial use. l Plan and Organise l Acquire and Implement l Deliver and Support l Monitor and Evaluate l Effectiveness l Efficiency l Availability l Integrity l Confidentiality l Reliability l Compliance 16
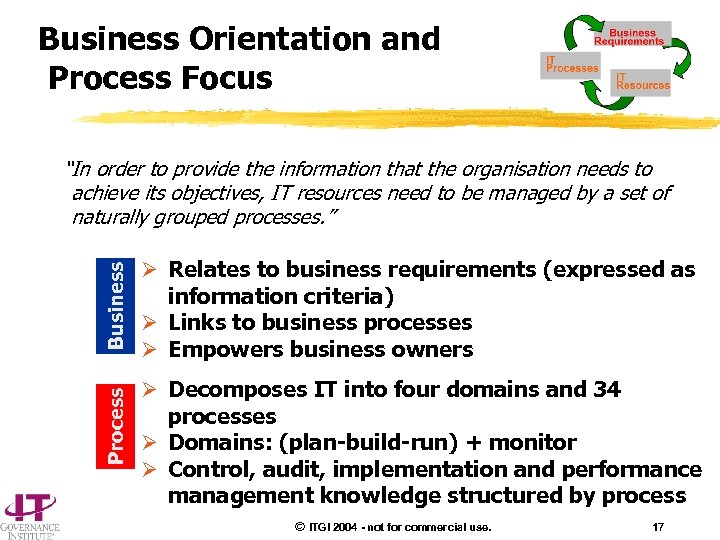
Business Orientation and Process Focus Process Business “In order to provide the information that the organisation needs to achieve its objectives, IT resources need to be managed by a set of naturally grouped processes. ” Ø Relates to business requirements (expressed as information criteria) Ø Links to business processes Ø Empowers business owners Ø Decomposes IT into four domains and 34 processes Ø Domains: (plan-build-run) + monitor Ø Control, audit, implementation and performance management knowledge structured by process © ITGI 2004 - not for commercial use. 17
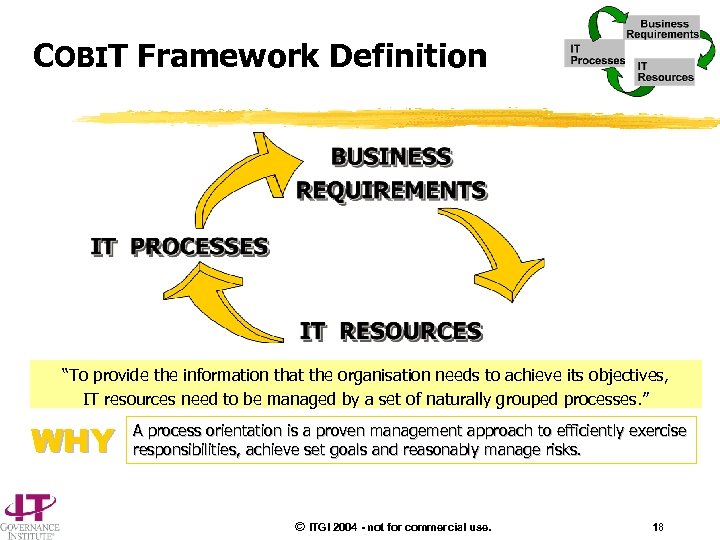
COBIT Framework Definition “To provide the information that the organisation needs to achieve its objectives, IT resources need to be managed by a set of naturally grouped processes. ” WHY A process orientation is a proven management approach to efficiently exercise responsibilities, achieve set goals and reasonably manage risks. © ITGI 2004 - not for commercial use. 18
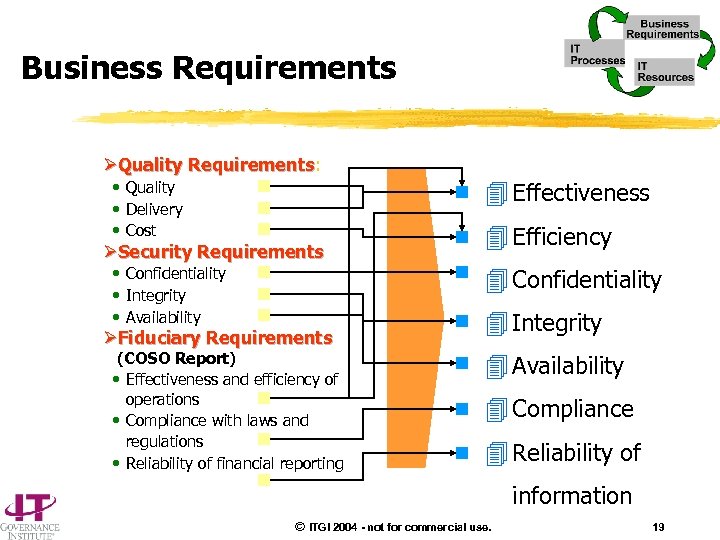
Business Requirements ØQuality Requirements: Requirements • Quality • Delivery • Cost ØSecurity Requirements • Confidentiality • Integrity • Availability ØFiduciary Requirements (COSO Report) • Effectiveness and efficiency of operations • Compliance with laws and regulations • Reliability of financial reporting 4 Effectiveness 4 Efficiency 4 Confidentiality 4 Integrity 4 Availability 4 Compliance 4 Reliability of information © ITGI 2004 - not for commercial use. 19
Business Requirements Effectiveness –Deals with information being relevant and pertinent to the business process as well as being delivered in a timely, correct, consistent and usable manner Efficiency –Concerns the provision of information through the optimal (most productive and economical) usage of resources Confidentiality –Concerns protection of sensitive information from unauthorised disclosure Integrity –Relates to the accuracy and completeness of information as well as to its validity in accordance with the business‘s set of values and expectations Availability –Relates to information being available when required by the business process, and hence also concerns the safeguarding of resources Compliance –Deals with complying with those laws, regulations and contractual arrangements to which the business process is subject, i. e. , externally imposed business criteria Reliability of information–Relates to systems providing management with appropriate information for it to use in operating the entity, providing financial reporting to users of the financial information, and providing information to report to regulatory bodies with regard to compliance with laws and regulations © ITGI 2004 - not for commercial use. 20
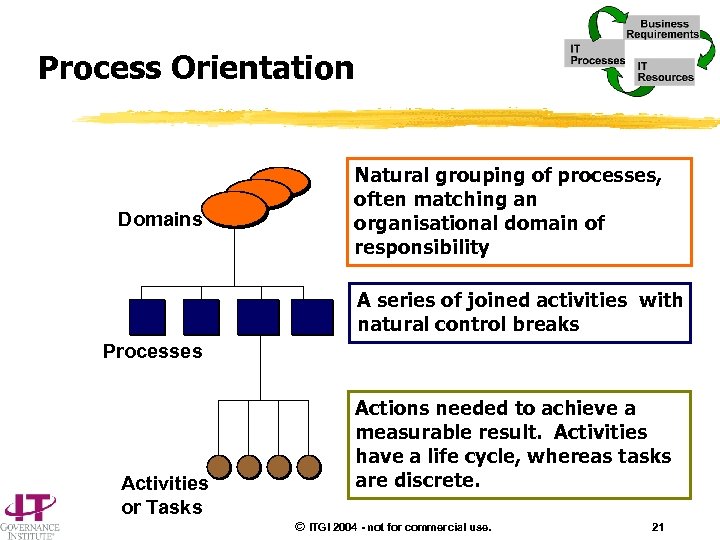
Process Orientation Domains Natural grouping of processes, often matching an organisational domain of responsibility A series of joined activities with natural control breaks Processes Activities or Tasks Actions needed to achieve a measurable result. Activities have a life cycle, whereas tasks are discrete. © ITGI 2004 - not for commercial use. 21
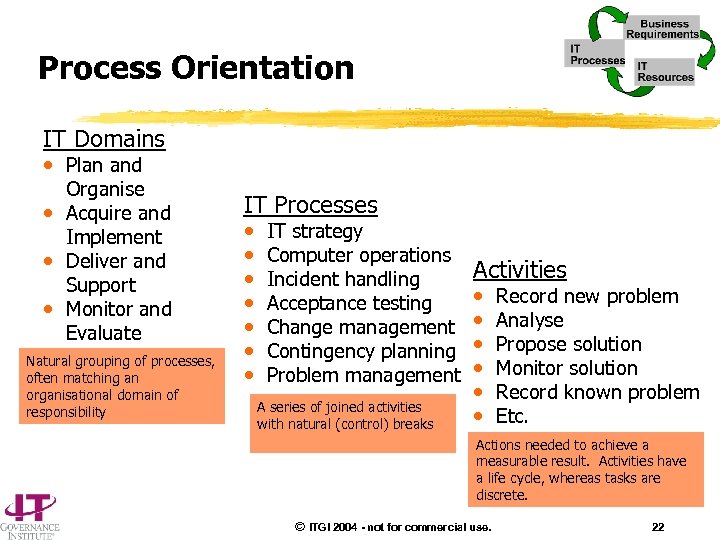
Process Orientation IT Domains • Plan and Organise • Acquire and Implement • Deliver and Support • Monitor and Evaluate Natural grouping of processes, often matching an organisational domain of responsibility IT Processes • • IT strategy Computer operations Incident handling Acceptance testing Change management Contingency planning Problem management A series of joined activities with natural (control) breaks Activities • • • Record new problem Analyse Propose solution Monitor solution Record known problem Etc. Actions needed to achieve a measurable result. Activities have a life cycle, whereas tasks are discrete. © ITGI 2004 - not for commercial use. 22

Process Orientation Domains Plan and Organise Description Ø This domain covers strategy and tactics, and concerns the identification of how IT can best contribute to the achievement of the business objectives. Furthermore, the realisation of the strategic vision needs to be planned, communicated and managed for different perspectives. Finally, a proper organisation as well as technological infrastructure must be put in place. Topics Ø Strategy and tactics Ø Vision planned Ø Organisation and infrastructure Questions Ø Ø Ø Are IT and the business strategy aligned? Is the enterprise achieving optimum use of its resources? Does everyone in the organisation understand the IT objectives? Are IT risks understood and being managed? Is the quality of IT systems appropriate for business needs? © ITGI 2004 - not for commercial use. 23

Process Orientation Plan and Organise Ø PO 1 Define a strategic information technology plan Ø PO 2 Define the information architecture Ø PO 3 Determine the technological direction Ø PO 4 Define the IT organisation and relationships Ø PO 5 Manage the investment in information technology Ø PO 6 Communicate management aims and direction Ø PO 7 Manage human resources Ø PO 8 Ensure compliance with external requirements Ø PO 9 Assess risks Ø PO 10 Manage projects . Ø PO 11 Manage quality © ITGI 2004 - not for commercial use. 24
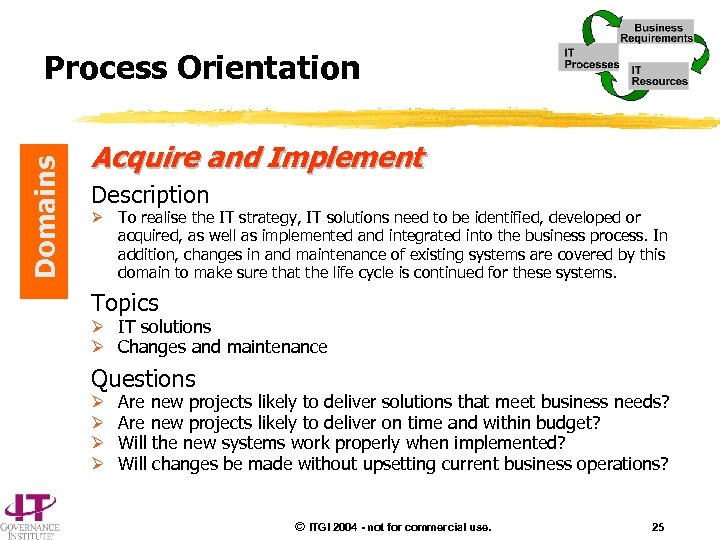
Domains Process Orientation Acquire and Implement Description Ø To realise the IT strategy, IT solutions need to be identified, developed or acquired, as well as implemented and integrated into the business process. In addition, changes in and maintenance of existing systems are covered by this domain to make sure that the life cycle is continued for these systems. Topics Ø IT solutions Ø Changes and maintenance Questions Ø Ø Are new projects likely to deliver solutions that meet business needs? Are new projects likely to deliver on time and within budget? Will the new systems work properly when implemented? Will changes be made without upsetting current business operations? © ITGI 2004 - not for commercial use. 25
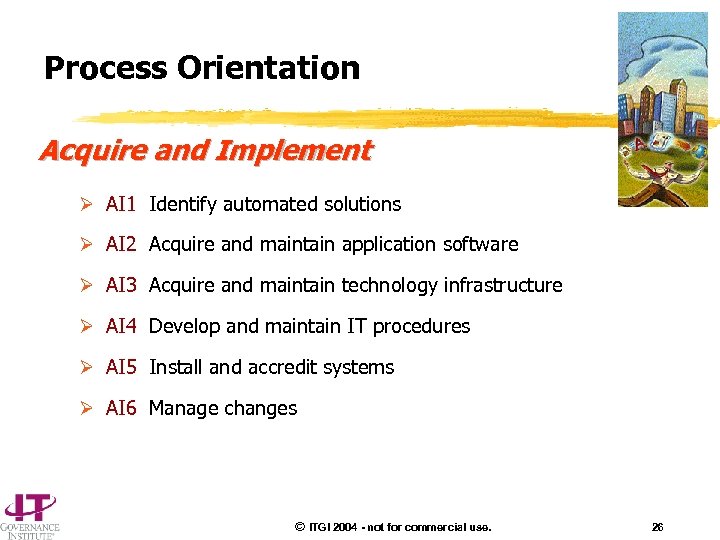
Process Orientation Acquire and Implement Ø AI 1 Identify automated solutions Ø AI 2 Acquire and maintain application software Ø AI 3 Acquire and maintain technology infrastructure Ø AI 4 Develop and maintain IT procedures Ø AI 5 Install and accredit systems Ø AI 6 Manage changes © ITGI 2004 - not for commercial use. 26

Process Orientation Domains Deliver and Support Description Ø This domain is concerned with the actual delivery of required services, which range from traditional operations over security and continuity aspects to training. To deliver services, the necessary support processes must be set up. This domain includes the actual processing of data by application systems, often classified under application controls. Topics Ø Delivery of required services Ø Setup of support processes Ø Processing by application systems Questions Ø Ø Are IT services being delivered in line with business priorities? Are IT costs optimised? Is the work force able to use the IT systems productively and safely? Are adequate security, integrity and availability in place? © ITGI 2004 - not for commercial use. 27
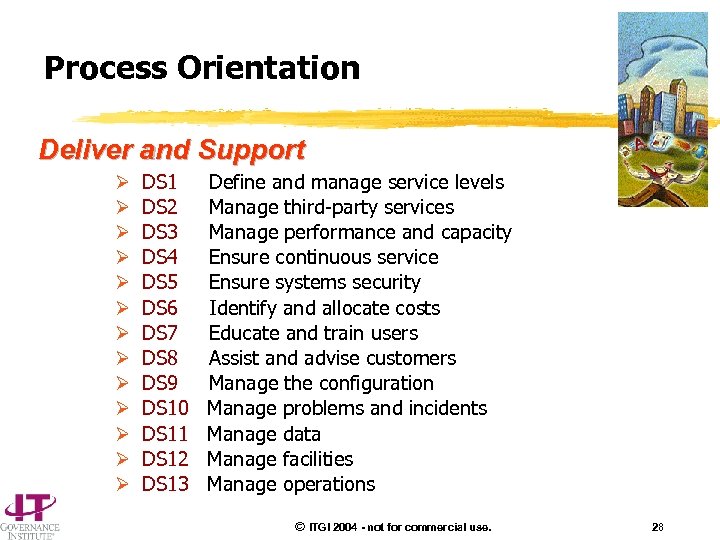
Process Orientation Deliver and Support Ø Ø Ø Ø DS 1 Define and manage service levels DS 2 Manage third-party services DS 3 Manage performance and capacity DS 4 Ensure continuous service DS 5 Ensure systems security DS 6 Identify and allocate costs DS 7 Educate and train users DS 8 Assist and advise customers DS 9 Manage the configuration DS 10 Manage problems and incidents DS 11 Manage data DS 12 Manage facilities DS 13 Manage operations © ITGI 2004 - not for commercial use. 28

Process Orientation Domains Monitor and Evaluate Description Ø All IT processes need to be regularly assessed over time for their quality and compliance with control requirements. This domain thus addresses management’s oversight of the organisation’s control process and independent assurance provided by internal and external audit or obtained from alternative sources. Topics Ø Assessment over time, delivering assurance Ø Management’s oversight of the control system Ø Performance measurement Questions Ø Can IT’s performance be measured and can problems be detected before it is too late? Ø Is independent assurance needed to ensure critical areas are operating as intended? © ITGI 2004 - not for commercial use. 29
Process Orientation Monitor and Evaluate ØM 1 Monitor the process ØM 2 Assess internal control adequacy ØM 3 Obtain independent assurance ØM 4 Provide for independent audit © ITGI 2004 - not for commercial use. 30

IT Resources Data: Data objects in their widest sense, i. e. , external and internal, structured and nonstructured, graphics, sound, etc. Application Systems: Understood to be the sum of manual and programmed procedures Technology: Covers hardware, operating systems, database management systems, networking, multimedia, etc. Facilities: Resources to house and support information systems People: Staff skills, awareness and productivity to plan, organise, acquire, deliver, support, monitor and evaluate information systems and services © ITGI 2004 - not for commercial use. 31
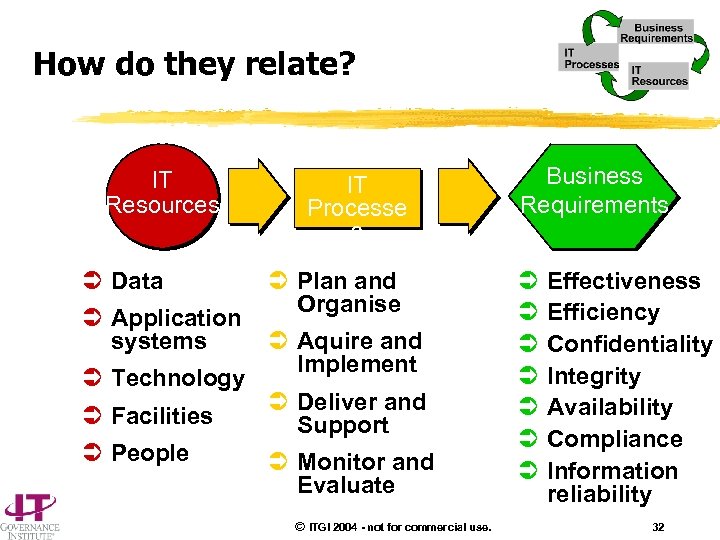
How do they relate? IT Resources Ü Data Ü Application systems Ü Technology Ü Facilities Ü People IT Processe s Ü Plan and Organise Ü Aquire and Implement Ü Deliver and Support Ü Monitor and Evaluate © ITGI 2004 - not for commercial use. Business Requirements Ü Ü Ü Ü Effectiveness Efficiency Confidentiality Integrity Availability Compliance Information reliability 32
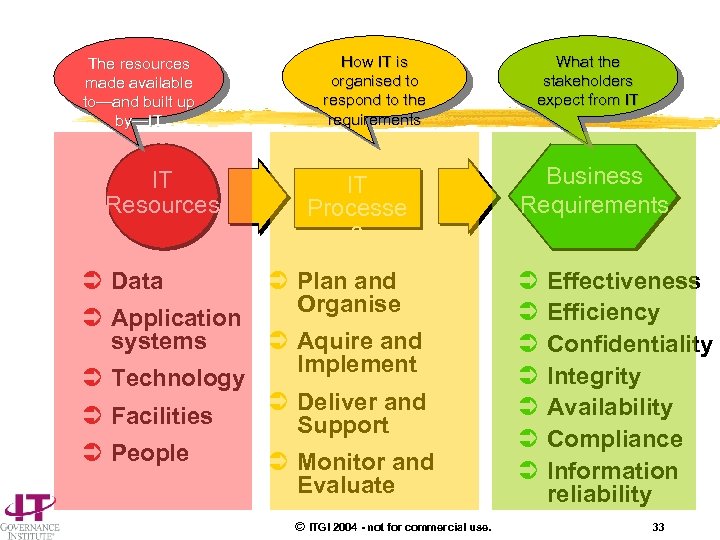
The resources made available to—and built up by—IT IT Resources Ü Data Ü Application systems Ü Technology Ü Facilities Ü People How IT is organised to respond to the requirements IT Processe s Ü Plan and Organise Ü Aquire and Implement Ü Deliver and Support Ü Monitor and Evaluate © ITGI 2004 - not for commercial use. What the stakeholders expect from IT Business Requirements Ü Ü Ü Ü Effectiveness Efficiency Confidentiality Integrity Availability Compliance Information reliability 33
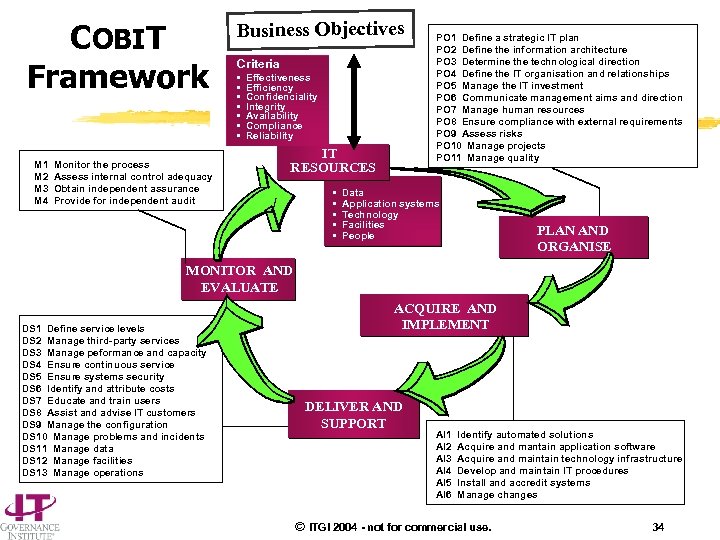
COBIT Framework M 1 M 2 M 3 M 4 Monitor the process Assess internal control adequacy Obtain independent assurance Provide for independent audit Business Objectives Criteria • • Effectiveness Efficiency Confidenciality Integrity Availability Compliance Reliability IT RESOURCES • • • PO 1 Define a strategic IT plan PO 2 Define the information architecture PO 3 Determine the technological direction PO 4 Define the IT organisation and relationships PO 5 Manage the IT investment PO 6 Communicate management aims and direction PO 7 Manage human resources PO 8 Ensure compliance with external requirements PO 9 Assess risks PO 10 Manage projects PO 11 Manage quality Data Application systems Technology Facilities People PLAN AND ORGANISE MONITOR AND EVALUATE DS 1 Define service levels DS 2 Manage third-party services DS 3 Manage peformance and capacity DS 4 Ensure continuous service DS 5 Ensure systems security DS 6 Identify and attribute costs DS 7 Educate and train users DS 8 Assist and advise IT customers DS 9 Manage the configuration DS 10 Manage problems and incidents DS 11 Manage data DS 12 Manage facilities DS 13 Manage operations ACQUIRE AND IMPLEMENT DELIVER AND SUPPORT AI 1 AI 2 AI 3 AI 4 AI 5 AI 6 Identify automated solutions Acquire and mantain application software Acquire and maintain technology infrastructure Develop and maintain IT procedures Install and accredit systems Manage changes © ITGI 2004 - not for commercial use. 34
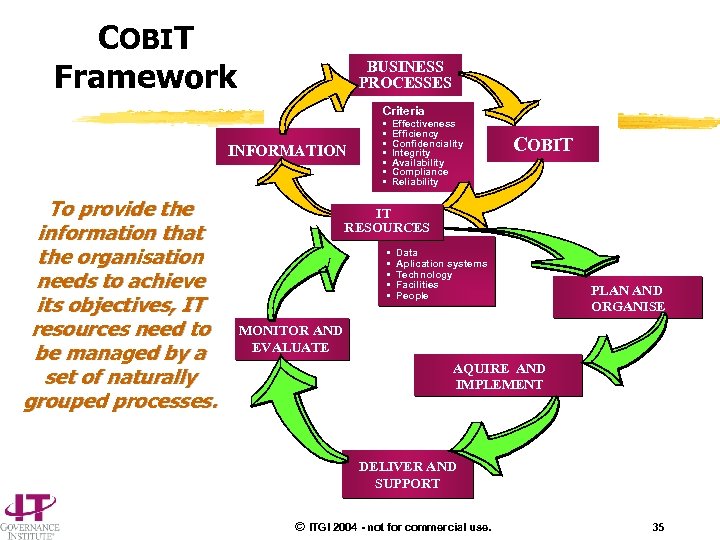
COBIT Framework BUSINESS PROCESSES Criteria INFORMATION To provide the information that the organisation needs to achieve its objectives, IT resources need to be managed by a set of naturally grouped processes. • • Effectiveness Efficiency Confidenciality Integrity Availability Compliance Reliability COBIT IT RESOURCES • • • Data Aplication systems Technology Facilities People PLAN AND ORGANISE MONITOR AND EVALUATE AQUIRE AND IMPLEMENT DELIVER AND SUPPORT © ITGI 2004 - not for commercial use. 35
COBIT Framework Summarising up to now Ø IT is indispensable for the survival and growth of enterprises. Ø Management is responsible for control. Ø That responsibility needs a framework: h. Business requirements can be expressed as information criteria. h. IT is generally organised in a set of processes. h. IT needs a set of resources. Ø COBIT is an internationally accepted standard. To provide the information that the organisation needs to achieve its objectives, IT resources need to be managed by a set of naturally grouped processes. © ITGI 2004 - not for commercial use. 36
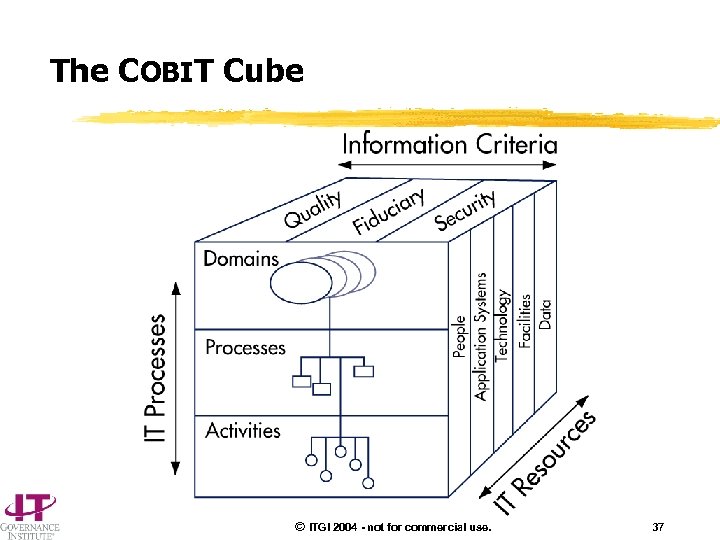
The COBIT Cube © ITGI 2004 - not for commercial use. 37
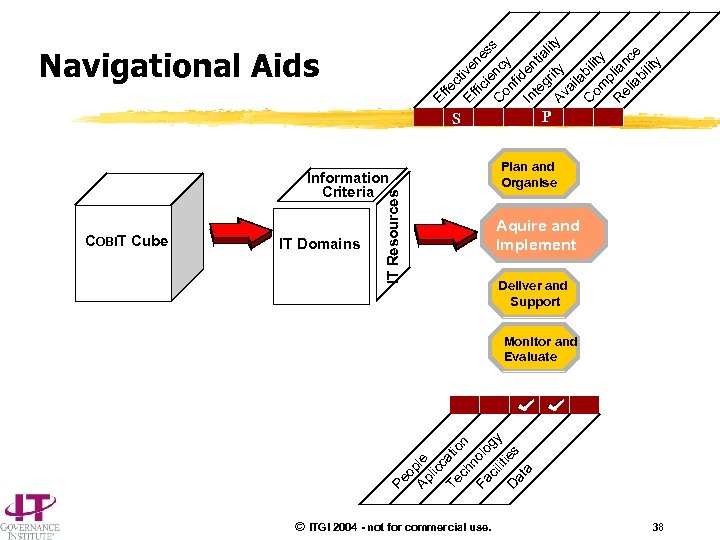
iv fic ene s ie C nc s on y fi In den te gr tiali Av ity ty ai la C bili om ty p R lian el ia ce bi lit y Ef Ef fe ct Navigational Aids P S IT Domains Plan and Organise Aquire and Implement Deliver and Support Monitor and Evaluate Pe o Ap ple lic c Te atio ch n n Fa olo g ci lit y ie D at s a COBIT Cube IT Resources Information Criteria © ITGI 2004 - not for commercial use. 38
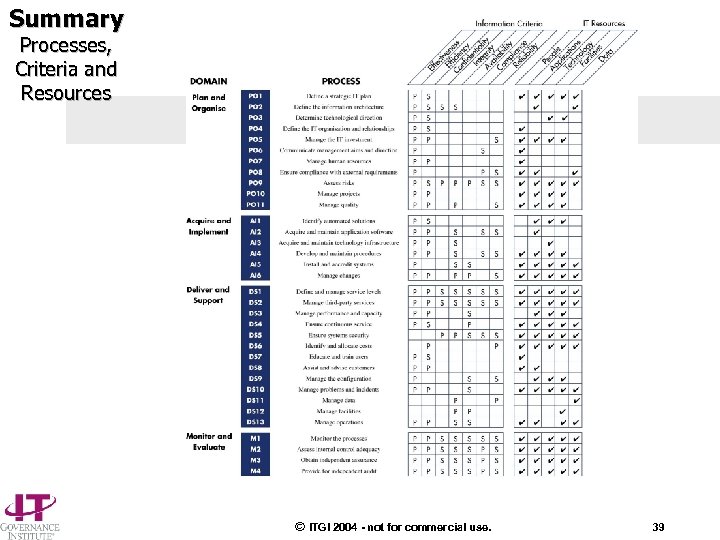
Summary Processes, Criteria and Resources © ITGI 2004 - not for commercial use. 39
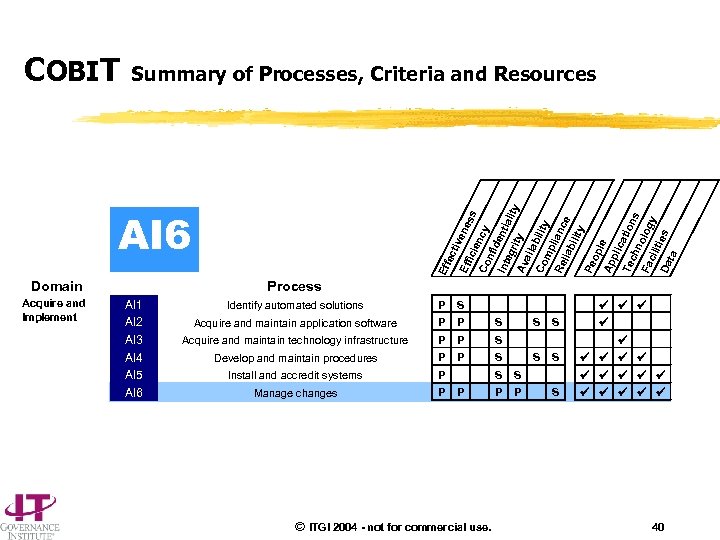
COBIT Summary of Processes, Criteria and Resources Eff ec ti ve ne Eff ss ici en c Co nfi y de nti Int ali eg ty r Av ity ail a Co bility mp Re lianc lia bil e ity Pe op le Ap pli ca t Te ch ions no log Fa cil itie y s Da ta AI 6 Domain Acquire and Implement Process AI 1 AI 2 AI 3 AI 4 AI 5 AI 6 Identify automated solutions P S Acquire and maintain application software P P S Acquire and maintain technology infrastructure P P S Develop and maintain procedures P P S Install and accredit systems P Manage changes P S S S P © ITGI 2004 - not for commercial use. P S S 40

Assignment The most important COBIT processes “For a business with which you are familiar, what would be the most important IT processes? Why? ” © ITGI 2004 - not for commercial use. 41

Important COBIT Products Control Objectives— “Minimum controls are. . . ” Management Guidelines— “Here is how you measure…” Audit Guidelines— “Here is how you audit. . . ” © ITGI 2004 - not for commercial use. 42

Control and Control Objective Definitions Definition of Control The policies, procedures, practices and organisational structures designed to provide reasonable assurance that business objectives will be achieved and undesired events will be prevented or detected and corrected Definition of IT Control Objective A statement of the desired result or purpose to be achieved by implementing control practices in a particular IT activity © ITGI 2004 - not for commercial use. 43

Control Objectives and Control Practices ØHigh-level control objective • One per process ØDetailed control objectives • Three to 30 per process ØControl practices • Five to seven per control objective © ITGI 2004 - not for commercial use. 44
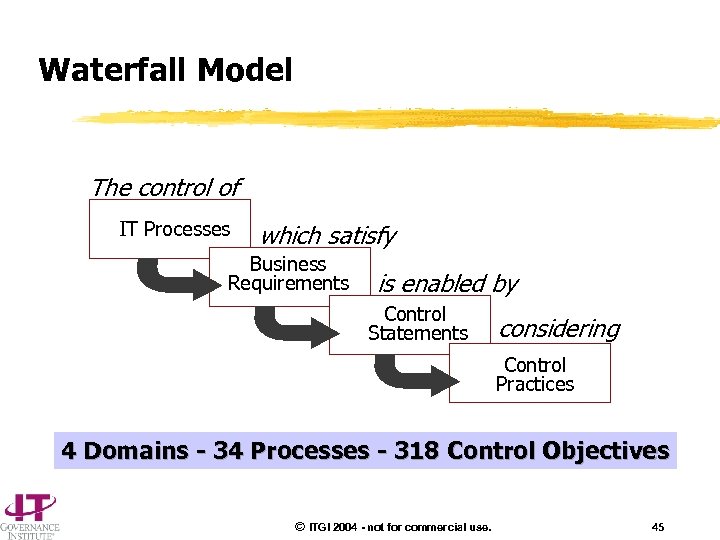
Waterfall Model The control of IT Processes which satisfy Business Requirements is enabled by Control Statements considering Control Practices 4 Domains - 34 Processes - 318 Control Objectives © ITGI 2004 - not for commercial use. 45

High-level Control Objective AI 6 Manage changes Managing changes to computer programs is required to ensure processing integrity between versions, and for consistency of results period to period. Change must be formally managed via change control request, impact assessment, documentation, authorisation, release, and distribution policies and procedures. © ITGI 2004 - not for commercial use. 46
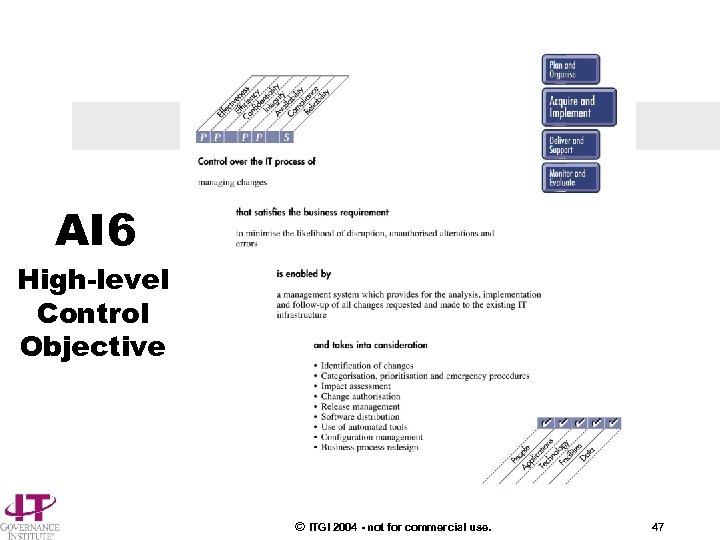
AI 6 High-level Control Objective © ITGI 2004 - not for commercial use. 47

Detailed Control Objectives AI 6 Manage Changes 6. 1 Change request initiation and control IT management should ensure that all requests for changes, system maintenance and supplier maintenance are standardised and are subject to formal change management procedures. Changes should be categorised and prioritised, and specific procedures should be in place to handle urgent matters. Change requesters should be kept informed about the status of their request. 6. 2 Impact assessment A procedure should be in place to ensure that all requests for change are assessed in a structured way for all possible impacts on the operational system and its functionality. 6. 3 Control of changes IT management should ensure that change management and software control and distribution are properly integrated with a comprehensive configuration management system. The system used to monitor changes to application systems should be automated to support the recording and tracking of changes made to large, complex information systems. 6. 4 Emergency changes IT management should establish parameters defining emergency changes and procedures to control these changes when they circumvent the normal process of technical, operational and management assessment prior to implementation. The emergency changes should be recorded and authorised by IT management prior to implementation. © ITGI 2004 - not for commercial use. 48

Detailed Control Objectives AI 6 Manage Changes (continued) 6. 5 Documentation and procedures The change process should ensure that, whenever system changes are implemented, the associated documentation and procedures are updated accordingly. 6. 6 Authorised maintenance IT management should ensure that maintenance personnel have specific assignments and their work is properly monitored. In addition, their system access rights should be controlled to avoid risks of unauthorised access to automated systems. 6. 7 Software release policy IT management should ensure that the release of software is governed by formal procedures —ensuring sign-off, packaging, regression testing, handover, etc. 6. 8 Distribution of software Specific internal control measures should be established to ensure distribution of the correct software element to the right place, with integrity, in a timely manner and with adequate audit trails. © ITGI 2004 - not for commercial use. 49

COBIT AI 6 Detailed Control Objectives © ITGI 2004 - not for commercial use. 50
Control Practices Translate COBIT’s control objectives into detailed, implementable practices and provide the business argumentation for implementation, from a value and a risk perspective Ø Control practices are key control mechanisms that support the: • Achievement of control objectives • Prevention, detection and correction of undesired events Ø Control practices achieve that through: • Responsible use of resources • Appropriate management of risk • Alignment of IT with business © ITGI 2004 - not for commercial use. 51

Control Practices AI 6 Manage change AI 6. 4 Emergency changes IT management should establish parameters defining emergency changes and procedures to control these changes when they circumvent the normal process of technical, operational and management assessment prior to implementation. The emergency changes should be recorded and authorised by IT management prior to implementation. 1. Management defines parameters, characteristics and Controlling emergency changes by 2. 3. 4. 5. procedures that identify and declare emergencies. All emergency changes are documented, if not before, then after, implementation. All emergency changes are tested, if not before, then after, implementation. All emergency changes are formally authorised by the system owner and management before implementation. Before and after images as well as intervention logs are retained for subsequent review. implementing the control practices will : p Ensure that emergency procedures are used in declared emergencies only p Ensure that urgent changes can be implemented without compromising integrity, availability, reliability, security, confidentiality or accuracy Control Practices Why do it? © ITGI 2004 - not for commercial use. 52

Important COBIT Products Control Objectives— “Minimum controls are. . . ” Management Guidelines – “Here is how you measure…” Audit Guidelines— “Here is how you audit. . . ” © ITGI 2004 - not for commercial use. 53
IT Governance Model IT governance helps ascertain how automated systems: • Simplify operations • Cut costs • Increase revenue Needs an IT control framework © ITGI 2004 - not for commercial use. 54
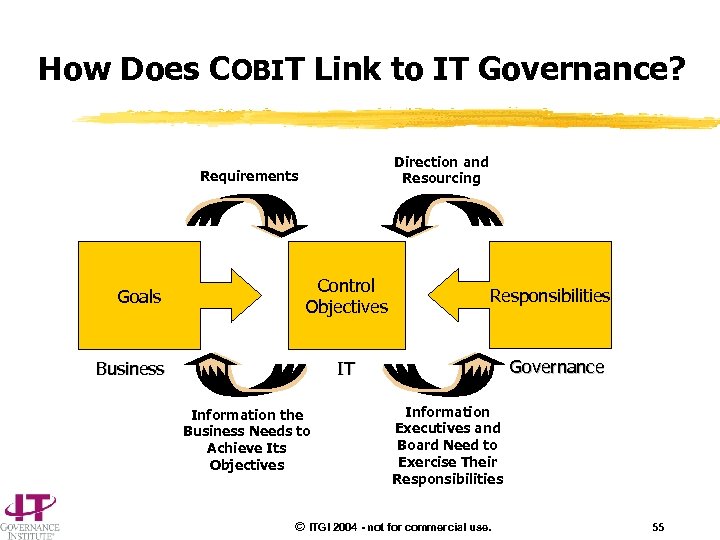
How Does COBIT Link to IT Governance? Direction and Resourcing Requirements Goals Control Objectives Business Responsibilities Governance IT Information the Business Needs to Achieve Its Objectives Information Executives and Board Need to Exercise Their Responsibilities © ITGI 2004 - not for commercial use. 55
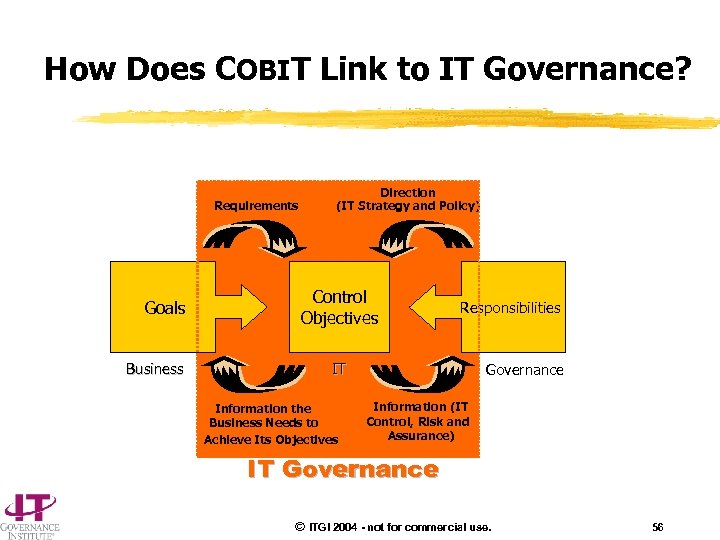
How Does COBIT Link to IT Governance? Requirements Goals Business Direction (IT Strategy and Policy) Control Objectives Responsibilities IT Information the Business Needs to Achieve Its Objectives Governance Information (IT Control, Risk and Assurance) IT Governance © ITGI 2004 - not for commercial use. 56
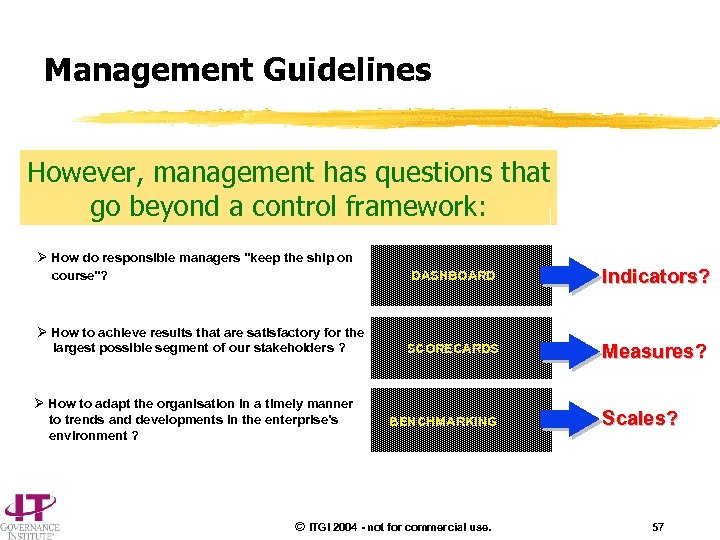
Management Guidelines However, management has questions that go beyond a control framework: Ø How do responsible managers "keep the ship on course"? Ø How to achieve results that are satisfactory for the largest possible segment of our stakeholders ? Ø How to adapt the organisation in a timely manner to trends and developments in the enterprise's environment ? DASHBOARD Indicators? SCORECARDS Measures? BENCHMARKING © ITGI 2004 - not for commercial use. Scales? 57
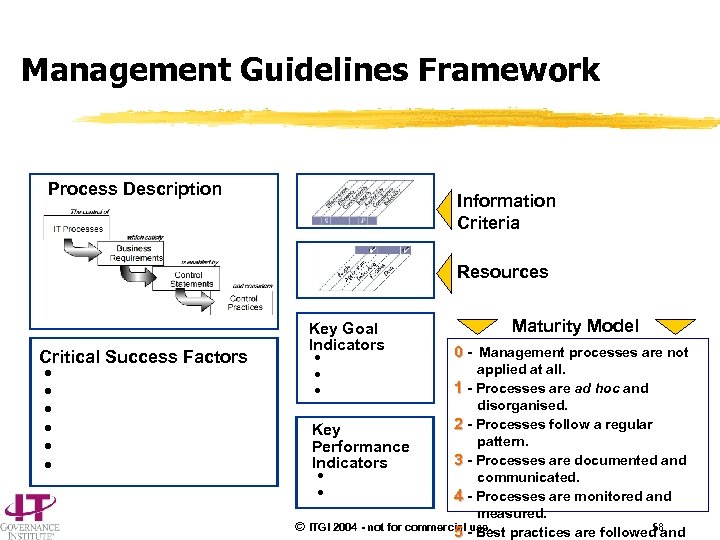
Management Guidelines Framework Process Description Information Criteria Resources Critical Success Factors h h h Key Goal Indicators h h h Maturity Model 0 - Management processes are not applied at all. 1 - Processes are ad hoc and disorganised. 2 - Processes follow a regular Key pattern. Performance 3 - Processes are documented and Indicators communicated. h h 4 - Processes are monitored and measured. © ITGI 2004 - not for commercial - Best practices are followed and use. 58 5
Key Goal Indicators Definitions l l l Describe the outcome of the process (i. e. , measurable after the fact); are measures of “what, ” and may describe the impact of not reaching the process goal Are indicators of the success of the process and its business contribution Focus on the customer and financial dimensions of the balanced scorecard © ITGI 2004 - not for commercial use. 59

Key Goal Indicators Examples l l l Increased level of service delivery Number of customers and cost per customer served Availability of systems and services Absence of integrity and confidentiality risks Cost-efficiency of processes and operations Confirmation of reliability and effectiveness Adherence to development cost and schedule Cost-efficiency of the process Staff productivity and morale Number of timely changes to processes and systems Improved productivity (e. g. , delivery of value per employee) © ITGI 2004 - not for commercial use. 60
Key Performance Indicators Definitions l l l Are measures of “how well” the process is performing Predict the probability of success or failure Focus on the process and learning dimensions of the balanced scorecard Are expressed in precise, measurable terms Should help in improving the IT process © ITGI 2004 - not for commercial use. 61
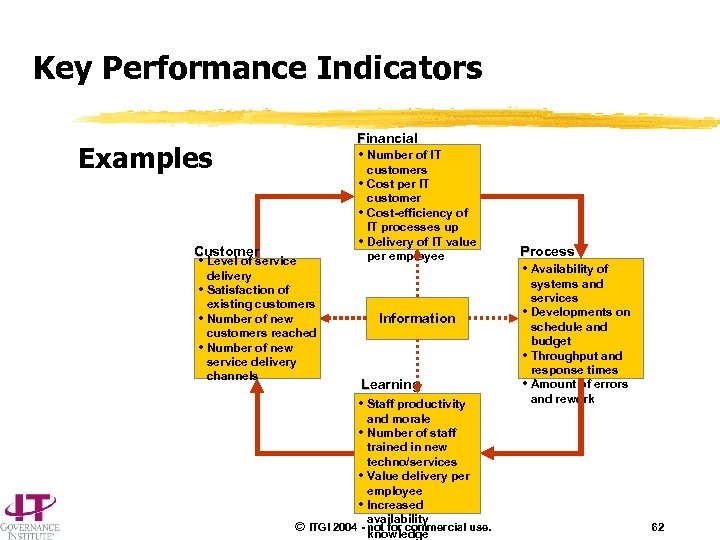
Key Performance Indicators Financial F Examples • Number of IT • • • Customer • Level of service • • • delivery Satisfaction of existing customers Number of new customers reached Number of new service delivery channels customers Cost per IT customer Cost-efficiency of IT processes up Delivery of IT value per employee Information Process • Availability of • • Learning • Staff productivity and morale • Number of staff trained in new techno/services • Value delivery per employee • Increased availability © ITGI 2004 - not for commercial use. knowledge • systems and services Developments on schedule and budget Throughput and response times Amount of errors and rework 62
Critical Success Factors Definitions l l l Are the most important things to do to increase the probability of success of the process Are observable—usually measurable—characteristics of the organisation and process Focus on obtaining, maintaining and leveraging capability, skills and behaviour © ITGI 2004 - not for commercial use. 63
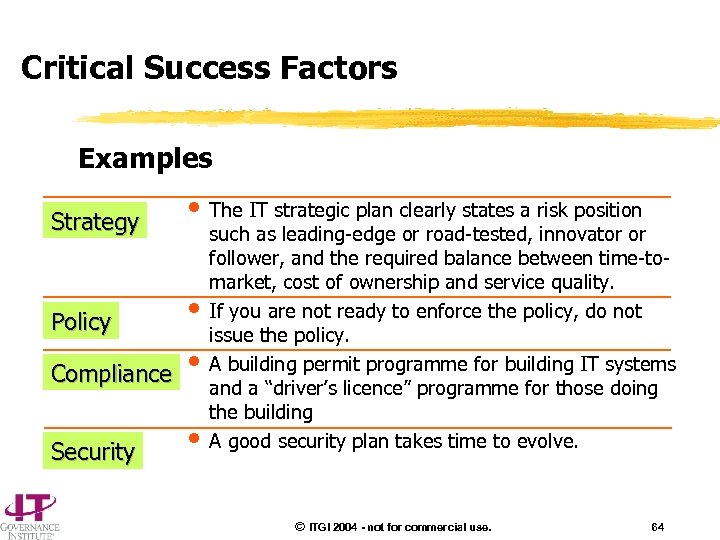
Critical Success Factors Examples Strategy • The IT strategic plan clearly states a risk position Policy • Compliance • Security • such as leading-edge or road-tested, innovator or follower, and the required balance between time-tomarket, cost of ownership and service quality. If you are not ready to enforce the policy, do not issue the policy. A building permit programme for building IT systems and a “driver’s licence” programme for those doing the building A good security plan takes time to evolve. © ITGI 2004 - not for commercial use. 64

Maturity Models Definitions l Refer to business requirements (KGIs) and the enabling aspects (KPIs) at the different levels l Are a scale that lend themselves to pragmatic comparison, where the difference can be made measurable in an easy manner l Are recognisable as a profile of the enterprise in relation to IT governance and control l Assist in determining as-is and to-be positions relative to IT governance and control maturity and analyse the gap l Are not industry-specific nor generally applicable. The nature of the business determines what is an appropriate level. © ITGI 2004 - not for commercial use. 65
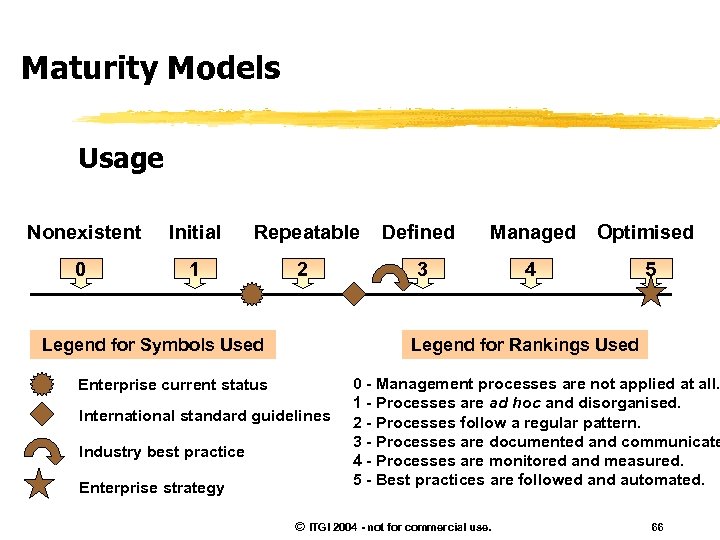
Maturity Models Usage Nonexistent Initial Repeatable Defined Managed Optimised 0 1 2 3 4 5 Legend for Symbols Used Legend for Rankings Used Enterprise current status International standard guidelines Industry best practice Enterprise strategy 0 - Management processes are not applied at all. 1 - Processes are ad hoc and disorganised. 2 - Processes follow a regular pattern. 3 - Processes are documented and communicate 4 - Processes are monitored and measured. 5 - Best practices are followed and automated. © ITGI 2004 - not for commercial use. 66

AI 6 Management Guideline © ITGI 2004 - not for commercial use. 67

AI 6 Management Guideline © ITGI 2004 - not for commercial use. 68

Important COBIT Products Control Objectives— “Minimum controls are. . . ” Management Guidelines— “Here is how you measure… Audit Guidelines— “Here is how you audit. . . ” © ITGI 2004 - not for commercial use. 69

Objectives of Auditing Ø Provide management with reasonable assurance that control objectives are being met Ø Where there are significant control weaknesses, substantiate the resulting risks Ø Advise management on corrective actions “Am I all right? And, if not, how do I fix it? ” © ITGI 2004 - not for commercial use. 70
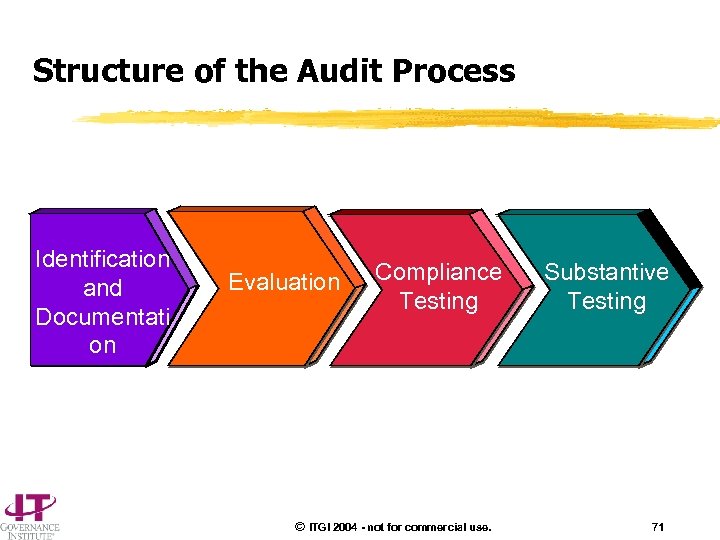
Structure of the Audit Process Identification and Documentati on Evaluation Compliance Testing © ITGI 2004 - not for commercial use. Substantive Testing 71
An IT process is audited by: • Obtaining an understanding of business requirements-related risks, and relevant control measures • Evaluating the appropriateness of stated controls • Assessing compliance by testing whether the stated controls are working as prescribed, consistently and continuously • Substantiating the risk of the control objectives not being met by using analytical techniques and/or consulting alternative sources © ITGI 2004 - not for commercial use. 72

COBIT Audit Guidelines One Generic Guideline and 34 Process-oriented Guidelines Ø A generic guideline identifies various tasks to be performed in assessing any control objective within a process. This generic guideline is a model for all control objectives. Ø Others are specific, process-oriented task suggestions to provide management assurance that a control exists and has a reasonable level of effectiveness. © ITGI 2004 - not for commercial use. 73

Generic Audit Guideline (1 of 4) Obtaining an Understanding The audit steps to be performed to document the activities underlying the control objectives as well as to identify the control measures/procedures put in place Ø Interview appropriate management and staff to obtain and gain an understanding of: • Business requirements and associated risks • Organisation structure • Roles and responsibilities • Policies and procedures • Laws and regulations • Control measures in place • Management reporting (status, performance, actions) Ø Document the process-related IT resources particularly affected by the process under review. Ø Confirm the understanding of the process under review, the control implications, e. g. , by a process walkthrough. © ITGI 2004 - not for commercial use. 74

Generic Audit Guideline (2 of 4) Evaluating the Controls The audit steps to be performed, in light of assessing the effectiveness of control measures in place or the degree to which the control objective is achieved Ø Evaluate the appropriateness of control measures for the process under review by considering identified criteria and industry standard practices and applying professional judgement. Determine whether: • Documented processes exist. • Appropriate deliverables exist. • Responsibility and accountability are clear and effective. • Compensating controls exist, where necessary. Ø Conclude the degree to which the control objective is met. © ITGI 2004 - not for commercial use. 75

Generic Audit Guideline (3 of 4) Assessing Compliance The audit steps to be performed to ensure that the control measures established are working as prescribed, consistently and continuously Ø Obtain direct or indirect evidence for selected items/periods to ensure that the procedures have been complied with for the period under review, using both direct and indirect evidence. Ø Perform a limited review of the adequacy of the process deliverables. Ø Determine the level of substantive testing and additional work needed to provide assurance that the IT process is adequate. © ITGI 2004 - not for commercial use. 76

Generic Audit Guideline (4 of 4) Substantiating the Risk The audit steps to be performed to substantiate the risk of the control objective not being met by using analytical techniques and/or consulting alternative sources Ø Document the control weaknesses and resulting threats and vulnerabilities. Ø Identify and document the actual and potential impact. © ITGI 2004 - not for commercial use. 77

AI 6 Audit Guideline © ITGI 2004 - not for commercial use. 78

AI 6 Audit Guideline © ITGI 2004 - not for commercial use. 79

AI 6 Audit Guideline © ITGI 2004 - not for commercial use. 80

How Audit Guidelines and Control Objectives Are Linked Ø Obtaining an understanding • Collect background information referencing business drivers, risks, infrastructure, etc. Ø Evaluating the appropriateness Control objectives translated to verify whether they are addressed and take into account the appropriateness for the enterprise and management claims about their presence Ø Assessing compliance Control objectives translated to test and/or measure whether controls in support of the control objectives are present as claimed and whether they operate satisfactorily Ø Substantiating the risk • Illustrate missed business objectives, losses, etc. , due to absence of adequate control. © ITGI 2004 - not for commercial use. 81
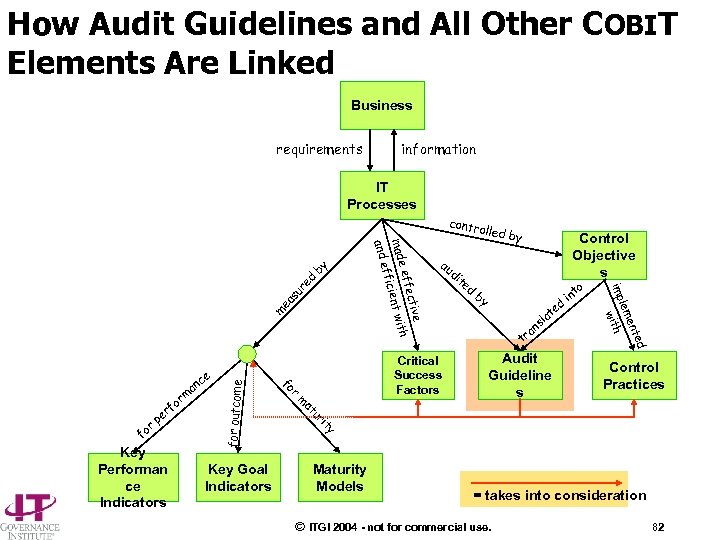
How Audit Guidelines and All Other COBIT Elements Are Linked Business requirements information IT Processes d re su d by an tr d te a sl Audit Guideline s to in ed ent lem h wit m ea te imp for outcome di Control Objective s Control Practices y it Key Goal Indicators au by ur at Key Performan ce Indicators m pe r r fo r an rm fo olled Critical Success Factors fo ce ctive effe h made cient wit ffi and e by contr Maturity Models = takes into consideration © ITGI 2004 - not for commercial use. 82
f090fd6c8b28f5b48301845541cbe9a4.ppt