39ca6cc1f124a3eefce64a413b30858a.ppt
- Количество слайдов: 55
 CNIT 221 Security Module 3 2 City College of San Francisco Spring 2007 © 2004, Cisco Systems, Inc. All rights reserved. © 2005 Cisco Systems, Inc. All rights reserved. 1 1
CNIT 221 Security Module 3 2 City College of San Francisco Spring 2007 © 2004, Cisco Systems, Inc. All rights reserved. © 2005 Cisco Systems, Inc. All rights reserved. 1 1
 Network Security 2 Module 3 – Encryption and VPN Technology © 2005 Cisco Systems, Inc. All rights reserved. 2
Network Security 2 Module 3 – Encryption and VPN Technology © 2005 Cisco Systems, Inc. All rights reserved. 2
 Learning Objectives – 3. 1 Encryption Basics – 3. 2 Integrity Basics – 3. 3 Implementing Digital Certificates – 3. 4 VPN Topologies – 3. 5 VPN Technologies – 3. 6 IPSec © 2005 Cisco Systems, Inc. All rights reserved. 3
Learning Objectives – 3. 1 Encryption Basics – 3. 2 Integrity Basics – 3. 3 Implementing Digital Certificates – 3. 4 VPN Topologies – 3. 5 VPN Technologies – 3. 6 IPSec © 2005 Cisco Systems, Inc. All rights reserved. 3
 Module 3 – Encryption and VPN Technology 3. 1 Encryption Basics © 2005 Cisco Systems, Inc. All rights reserved. 4
Module 3 – Encryption and VPN Technology 3. 1 Encryption Basics © 2005 Cisco Systems, Inc. All rights reserved. 4
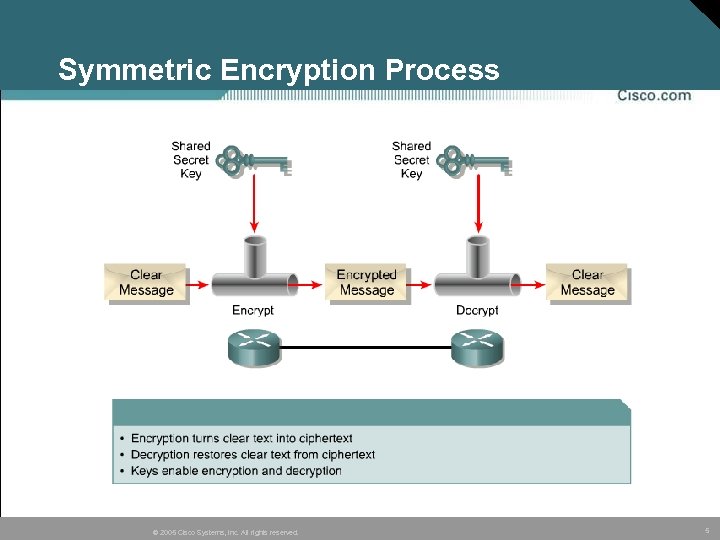 Symmetric Encryption Process © 2005 Cisco Systems, Inc. All rights reserved. 5
Symmetric Encryption Process © 2005 Cisco Systems, Inc. All rights reserved. 5
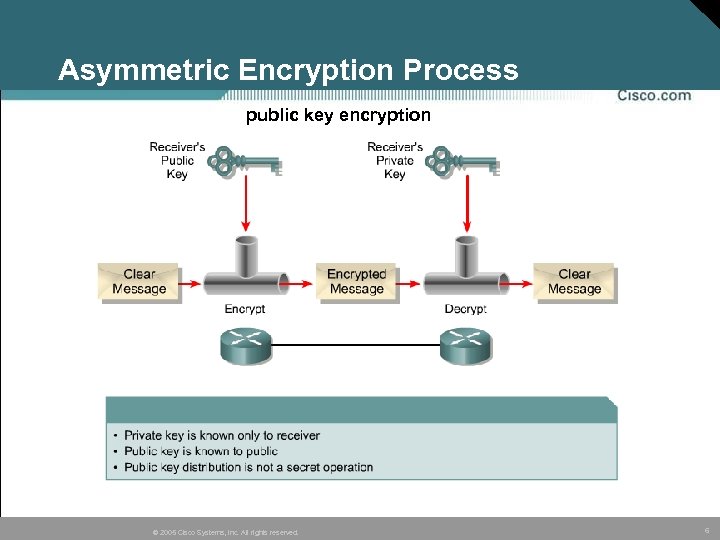 Asymmetric Encryption Process public key encryption © 2005 Cisco Systems, Inc. All rights reserved. 6
Asymmetric Encryption Process public key encryption © 2005 Cisco Systems, Inc. All rights reserved. 6
 Asymmetric Encryption • Some of the more common public key algorithms are the Rivest-Shamir-Adleman (RSA) algorithm and the El Gamal algorithm. – public key encryption algorithms are typically used in applications using digital signatures and key management. © 2005 Cisco Systems, Inc. All rights reserved. 7
Asymmetric Encryption • Some of the more common public key algorithms are the Rivest-Shamir-Adleman (RSA) algorithm and the El Gamal algorithm. – public key encryption algorithms are typically used in applications using digital signatures and key management. © 2005 Cisco Systems, Inc. All rights reserved. 7
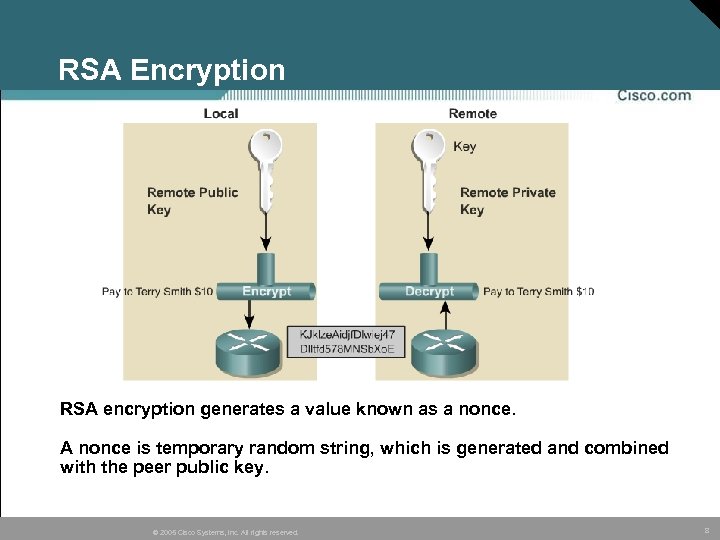 RSA Encryption RSA encryption generates a value known as a nonce. A nonce is temporary random string, which is generated and combined with the peer public key. © 2005 Cisco Systems, Inc. All rights reserved. 8
RSA Encryption RSA encryption generates a value known as a nonce. A nonce is temporary random string, which is generated and combined with the peer public key. © 2005 Cisco Systems, Inc. All rights reserved. 8
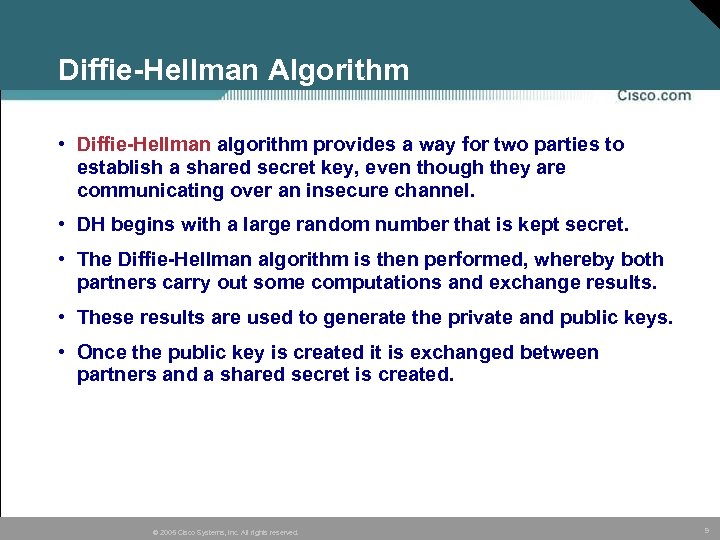 Diffie-Hellman Algorithm • Diffie-Hellman algorithm provides a way for two parties to establish a shared secret key, even though they are communicating over an insecure channel. • DH begins with a large random number that is kept secret. • The Diffie-Hellman algorithm is then performed, whereby both partners carry out some computations and exchange results. • These results are used to generate the private and public keys. • Once the public key is created it is exchanged between partners and a shared secret is created. © 2005 Cisco Systems, Inc. All rights reserved. 9
Diffie-Hellman Algorithm • Diffie-Hellman algorithm provides a way for two parties to establish a shared secret key, even though they are communicating over an insecure channel. • DH begins with a large random number that is kept secret. • The Diffie-Hellman algorithm is then performed, whereby both partners carry out some computations and exchange results. • These results are used to generate the private and public keys. • Once the public key is created it is exchanged between partners and a shared secret is created. © 2005 Cisco Systems, Inc. All rights reserved. 9
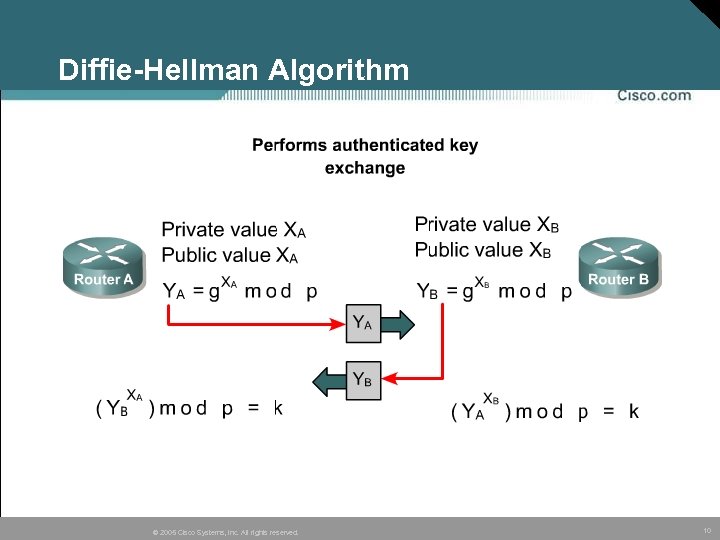 Diffie-Hellman Algorithm © 2005 Cisco Systems, Inc. All rights reserved. 10
Diffie-Hellman Algorithm © 2005 Cisco Systems, Inc. All rights reserved. 10
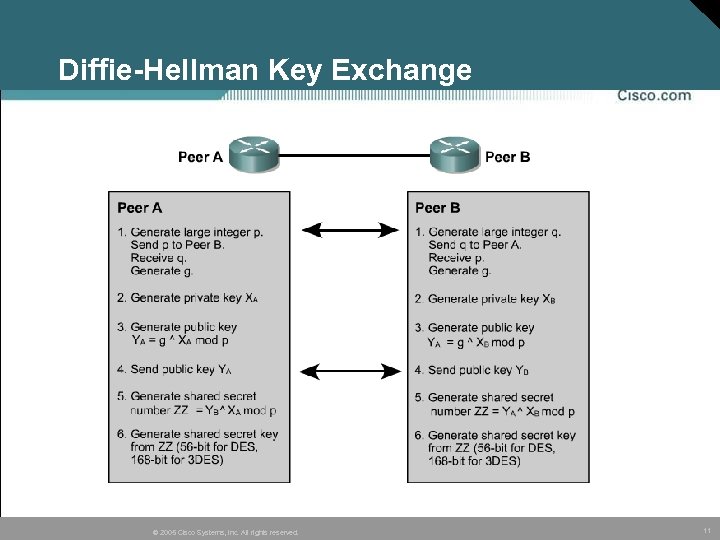 Diffie-Hellman Key Exchange © 2005 Cisco Systems, Inc. All rights reserved. 11
Diffie-Hellman Key Exchange © 2005 Cisco Systems, Inc. All rights reserved. 11
 Module 3 – Encryption and VPN Technology 3. 2 Integrity Basics © 2005 Cisco Systems, Inc. All rights reserved. 12
Module 3 – Encryption and VPN Technology 3. 2 Integrity Basics © 2005 Cisco Systems, Inc. All rights reserved. 12
 Integrity and Hashing • To guard against traffic being intercepted and modified, each message has a hash attached to it. • A hash is a method of verifying that the contents of a transmission are the same at both ends of the path, similar to a checksum. • A hash is a fixed-size string generated from the packet. • The hash guarantees the integrity of the original message. • Two common hashing algorithms are Message Digest (MD) and Secure Hash Algorithm (SHA). © 2005 Cisco Systems, Inc. All rights reserved. 13
Integrity and Hashing • To guard against traffic being intercepted and modified, each message has a hash attached to it. • A hash is a method of verifying that the contents of a transmission are the same at both ends of the path, similar to a checksum. • A hash is a fixed-size string generated from the packet. • The hash guarantees the integrity of the original message. • Two common hashing algorithms are Message Digest (MD) and Secure Hash Algorithm (SHA). © 2005 Cisco Systems, Inc. All rights reserved. 13
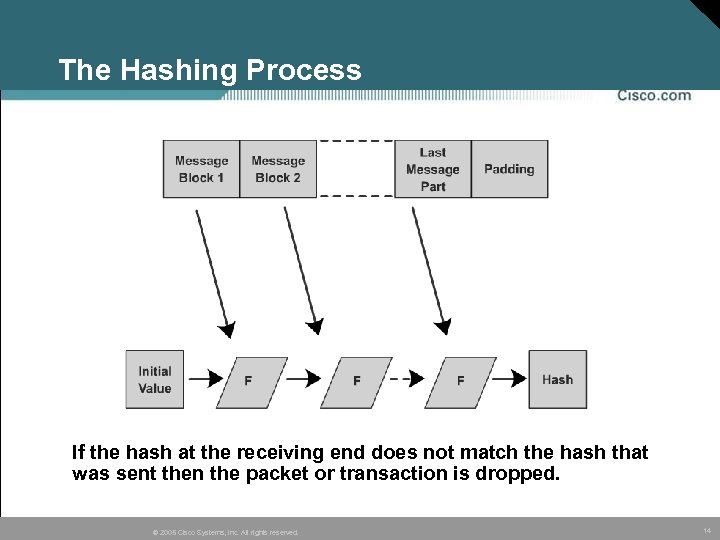 The Hashing Process If the hash at the receiving end does not match the hash that was sent then the packet or transaction is dropped. © 2005 Cisco Systems, Inc. All rights reserved. 14
The Hashing Process If the hash at the receiving end does not match the hash that was sent then the packet or transaction is dropped. © 2005 Cisco Systems, Inc. All rights reserved. 14
 Hashed Method Authentication Code • A Hashed Message Authentication Code (HMAC) guarantees the integrity of the message. • HMAC is similar to the hash process discussed earlier except that HMAC combines a secret key with the message. • There are two common hashing algorithms: –HMAC-MD 5 uses a 128 -bit shared secret key. –HMAC-SHA-1 uses a 160 -bit secret key. © 2005 Cisco Systems, Inc. All rights reserved. 15
Hashed Method Authentication Code • A Hashed Message Authentication Code (HMAC) guarantees the integrity of the message. • HMAC is similar to the hash process discussed earlier except that HMAC combines a secret key with the message. • There are two common hashing algorithms: –HMAC-MD 5 uses a 128 -bit shared secret key. –HMAC-SHA-1 uses a 160 -bit secret key. © 2005 Cisco Systems, Inc. All rights reserved. 15
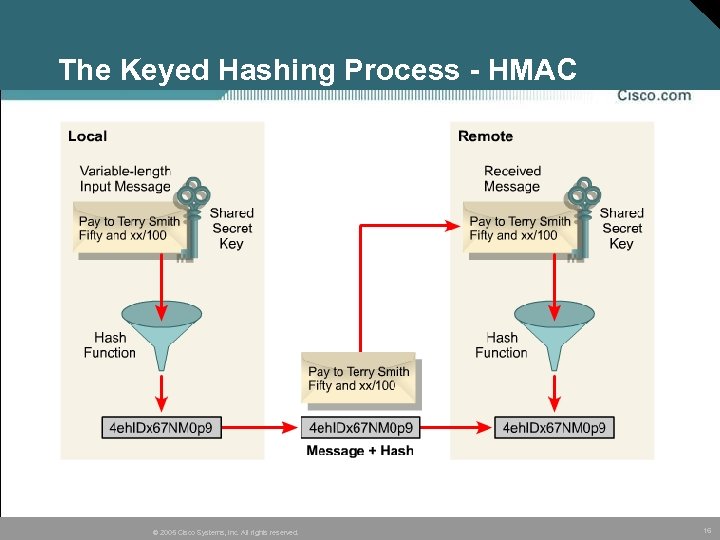 The Keyed Hashing Process - HMAC © 2005 Cisco Systems, Inc. All rights reserved. 16
The Keyed Hashing Process - HMAC © 2005 Cisco Systems, Inc. All rights reserved. 16
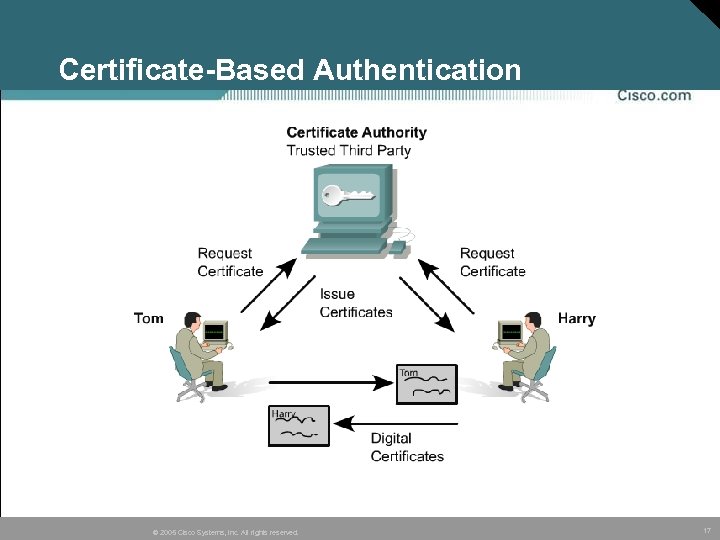 Certificate-Based Authentication © 2005 Cisco Systems, Inc. All rights reserved. 17
Certificate-Based Authentication © 2005 Cisco Systems, Inc. All rights reserved. 17
 Digital Certificates • A digital signature, or digital certificate, is an encrypted hash that is appended to a document. • Digital certs are used to confirm the identity of the sender and the integrity of the document. • A digital certificate contains information to identify a user or device, such as the name, serial number, company, department or IP address as well as copy of the entity’s public key. • A Certificate Authority (CA) signs the certificate. – The CA is a third party that is explicitly trusted by the receiver to validate identities and to create digital certificates © 2005 Cisco Systems, Inc. All rights reserved. 18
Digital Certificates • A digital signature, or digital certificate, is an encrypted hash that is appended to a document. • Digital certs are used to confirm the identity of the sender and the integrity of the document. • A digital certificate contains information to identify a user or device, such as the name, serial number, company, department or IP address as well as copy of the entity’s public key. • A Certificate Authority (CA) signs the certificate. – The CA is a third party that is explicitly trusted by the receiver to validate identities and to create digital certificates © 2005 Cisco Systems, Inc. All rights reserved. 18
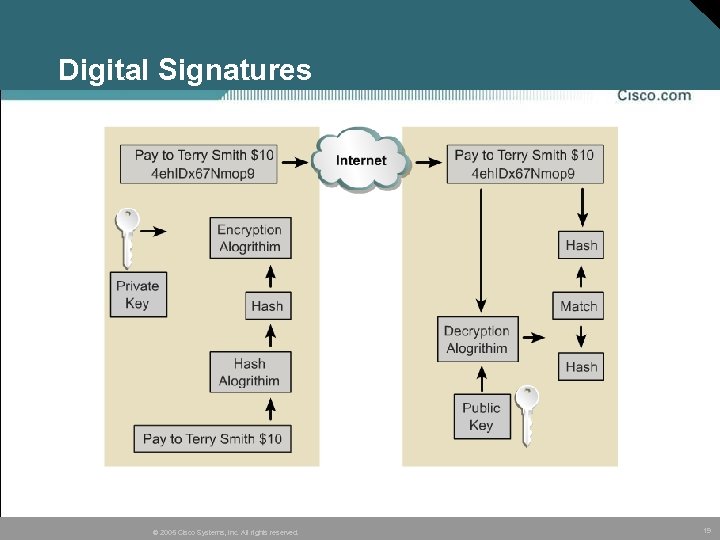 Digital Signatures © 2005 Cisco Systems, Inc. All rights reserved. 19
Digital Signatures © 2005 Cisco Systems, Inc. All rights reserved. 19
 Module 3 – Encryption and VPN Technology 3. 3 Implementing Digital Certificates © 2005 Cisco Systems, Inc. All rights reserved. 20
Module 3 – Encryption and VPN Technology 3. 3 Implementing Digital Certificates © 2005 Cisco Systems, Inc. All rights reserved. 20
 Simple Certificate Enrollment Protocol (SCEP) • The Simple Certificate Enrollment Protocol (SCEP) is a Cisco, Verisign, Entrust, Microsoft, Netscape, and Sun Microsystems initiative that provides a standard way of managing the certificate life cycle. • SCEP provides manual authentication and authentication based on pre-shared secret keys. • Manual authentication uses an MD 5 fingerprint • Pre-shared key authentication challenges the user for password. –The user then uses the pre-shared key as the password. © 2005 Cisco Systems, Inc. All rights reserved. 21
Simple Certificate Enrollment Protocol (SCEP) • The Simple Certificate Enrollment Protocol (SCEP) is a Cisco, Verisign, Entrust, Microsoft, Netscape, and Sun Microsystems initiative that provides a standard way of managing the certificate life cycle. • SCEP provides manual authentication and authentication based on pre-shared secret keys. • Manual authentication uses an MD 5 fingerprint • Pre-shared key authentication challenges the user for password. –The user then uses the pre-shared key as the password. © 2005 Cisco Systems, Inc. All rights reserved. 21
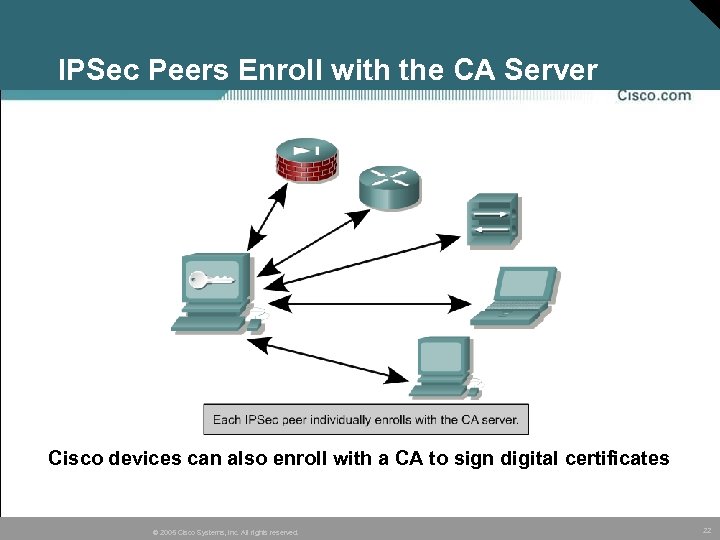 IPSec Peers Enroll with the CA Server Cisco devices can also enroll with a CA to sign digital certificates © 2005 Cisco Systems, Inc. All rights reserved. 22
IPSec Peers Enroll with the CA Server Cisco devices can also enroll with a CA to sign digital certificates © 2005 Cisco Systems, Inc. All rights reserved. 22
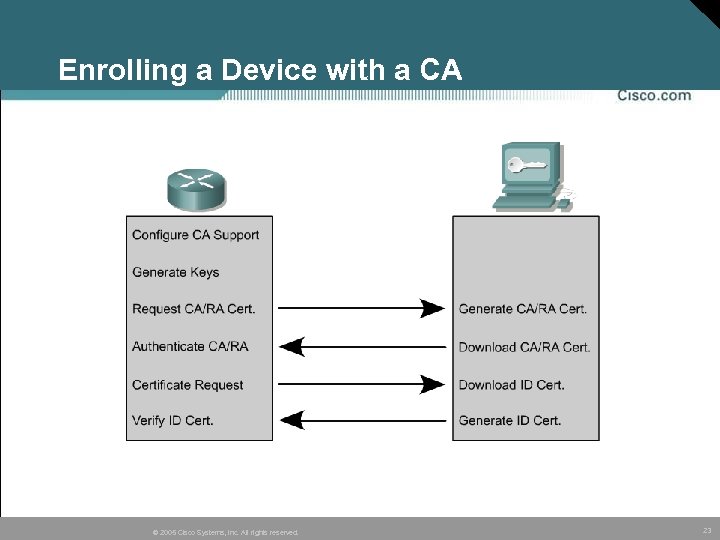 Enrolling a Device with a CA © 2005 Cisco Systems, Inc. All rights reserved. 23
Enrolling a Device with a CA © 2005 Cisco Systems, Inc. All rights reserved. 23
 Module 3 – Encryption and VPN Technology 3. 4 VPN Topologies © 2005 Cisco Systems, Inc. All rights reserved. 24
Module 3 – Encryption and VPN Technology 3. 4 VPN Topologies © 2005 Cisco Systems, Inc. All rights reserved. 24
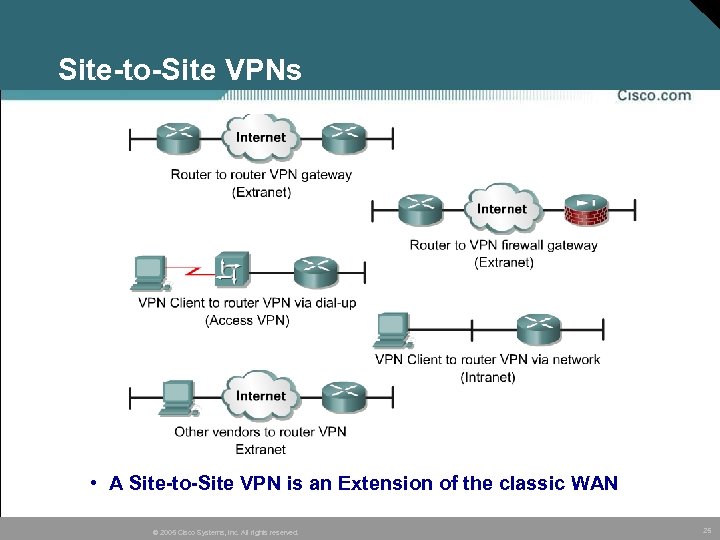 Site-to-Site VPNs • A Site-to-Site VPN is an Extension of the classic WAN © 2005 Cisco Systems, Inc. All rights reserved. 25
Site-to-Site VPNs • A Site-to-Site VPN is an Extension of the classic WAN © 2005 Cisco Systems, Inc. All rights reserved. 25
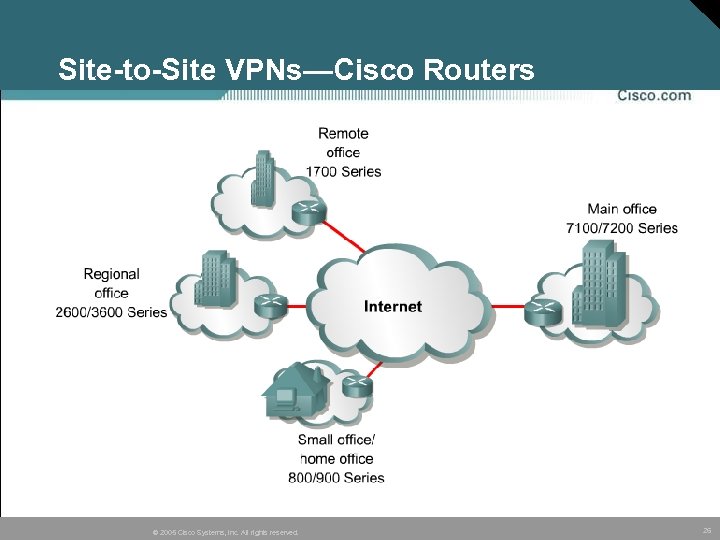 Site-to-Site VPNs—Cisco Routers © 2005 Cisco Systems, Inc. All rights reserved. 26
Site-to-Site VPNs—Cisco Routers © 2005 Cisco Systems, Inc. All rights reserved. 26
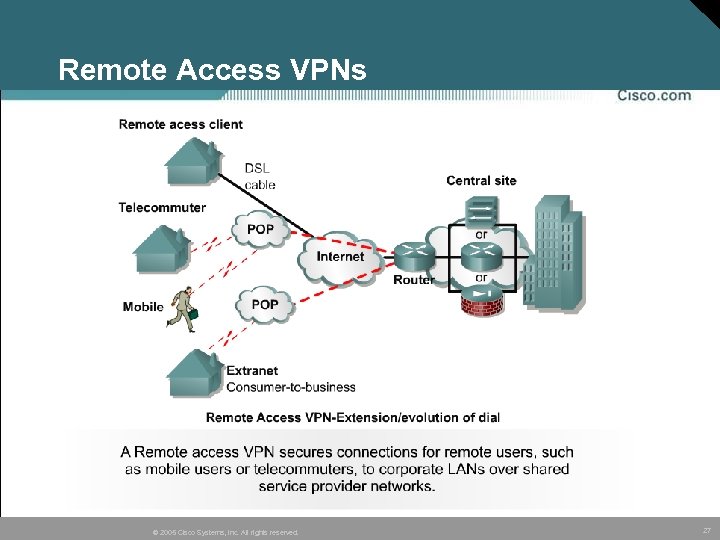 Remote Access VPNs © 2005 Cisco Systems, Inc. All rights reserved. 27
Remote Access VPNs © 2005 Cisco Systems, Inc. All rights reserved. 27
 Module 3 – Encryption and VPN Technology 3. 5 VPN Technologies © 2005 Cisco Systems, Inc. All rights reserved. 28
Module 3 – Encryption and VPN Technology 3. 5 VPN Technologies © 2005 Cisco Systems, Inc. All rights reserved. 28
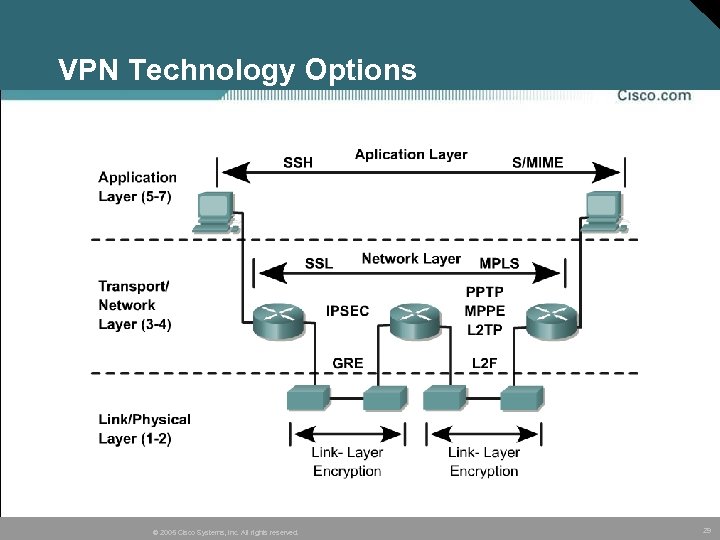 VPN Technology Options © 2005 Cisco Systems, Inc. All rights reserved. 29
VPN Technology Options © 2005 Cisco Systems, Inc. All rights reserved. 29
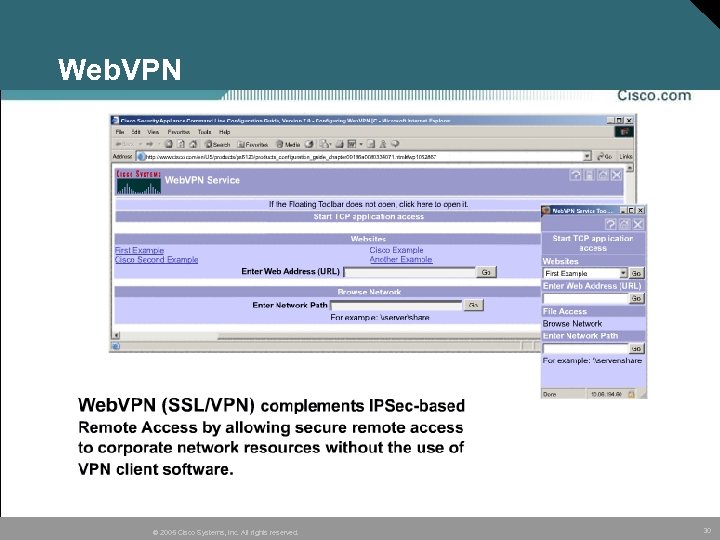 Web. VPN © 2005 Cisco Systems, Inc. All rights reserved. 30
Web. VPN © 2005 Cisco Systems, Inc. All rights reserved. 30
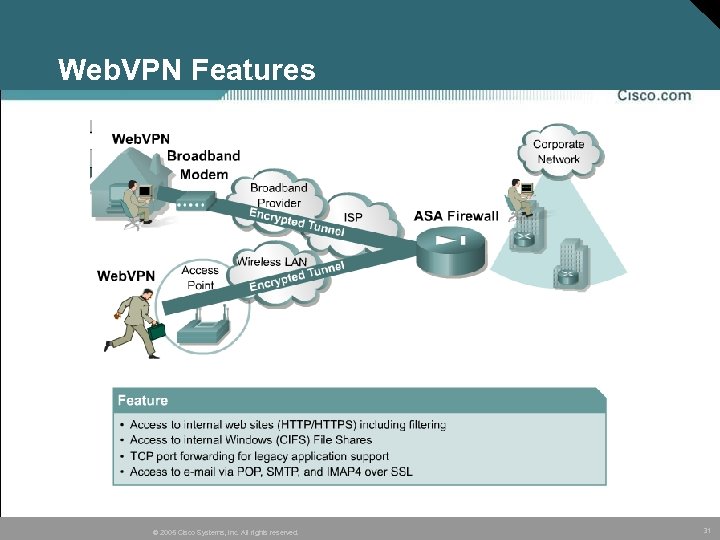 Web. VPN Features © 2005 Cisco Systems, Inc. All rights reserved. 31
Web. VPN Features © 2005 Cisco Systems, Inc. All rights reserved. 31
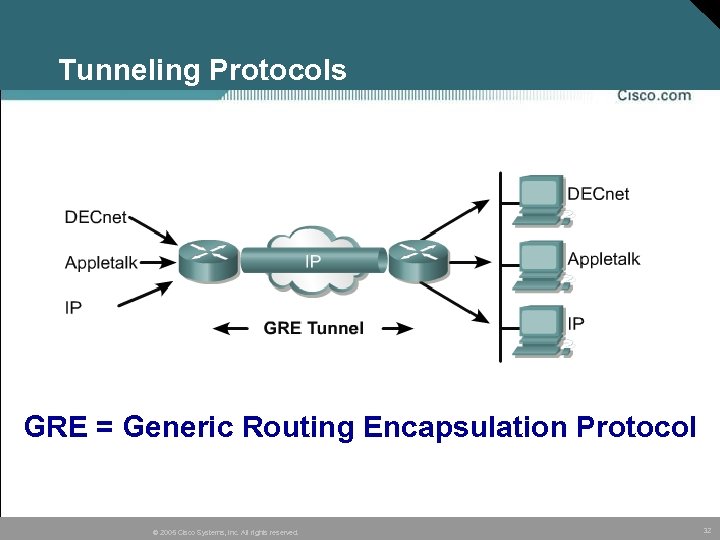 Tunneling Protocols GRE = Generic Routing Encapsulation Protocol © 2005 Cisco Systems, Inc. All rights reserved. 32
Tunneling Protocols GRE = Generic Routing Encapsulation Protocol © 2005 Cisco Systems, Inc. All rights reserved. 32
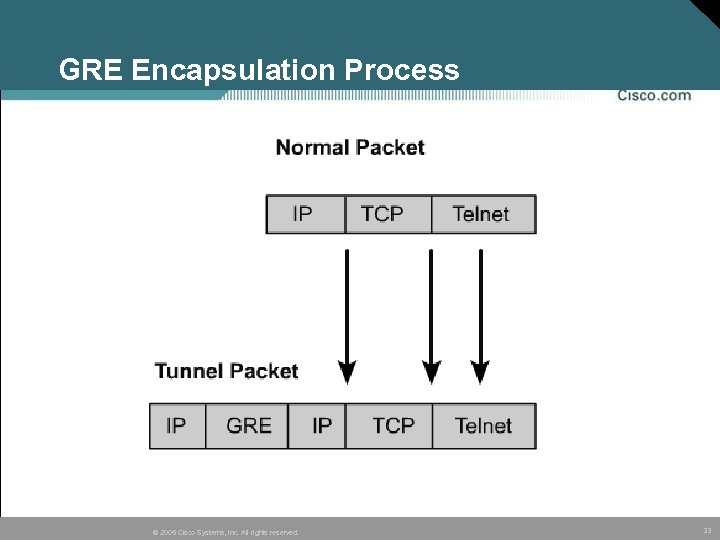 GRE Encapsulation Process © 2005 Cisco Systems, Inc. All rights reserved. 33
GRE Encapsulation Process © 2005 Cisco Systems, Inc. All rights reserved. 33
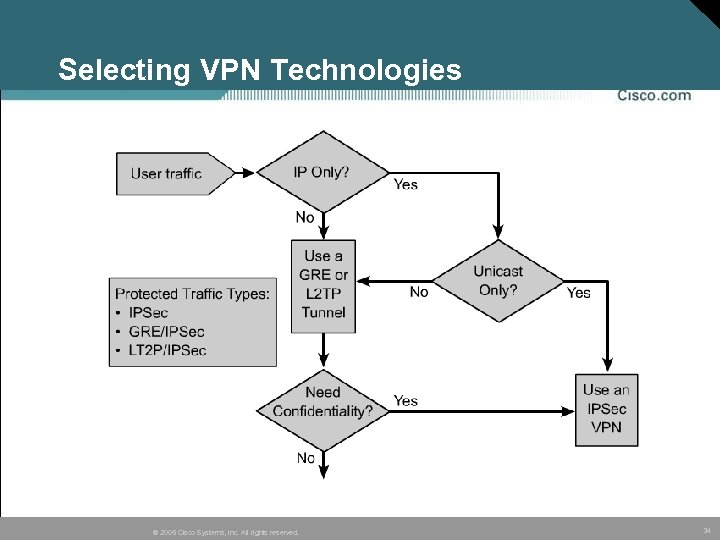 Selecting VPN Technologies © 2005 Cisco Systems, Inc. All rights reserved. 34
Selecting VPN Technologies © 2005 Cisco Systems, Inc. All rights reserved. 34
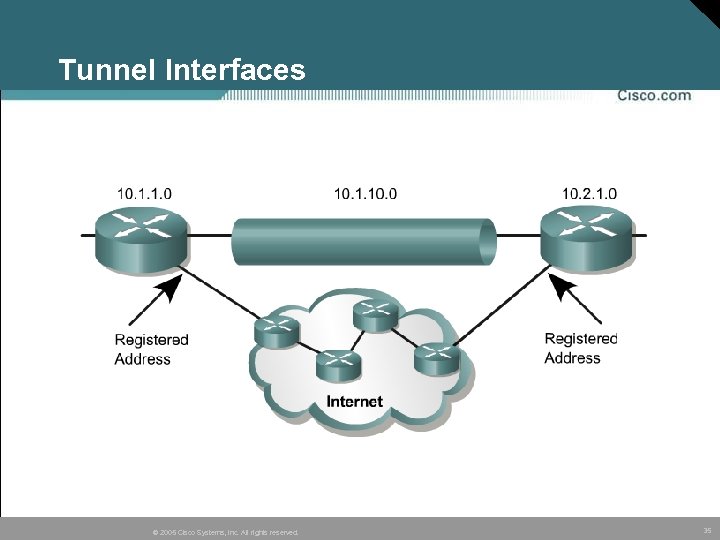 Tunnel Interfaces © 2005 Cisco Systems, Inc. All rights reserved. 35
Tunnel Interfaces © 2005 Cisco Systems, Inc. All rights reserved. 35
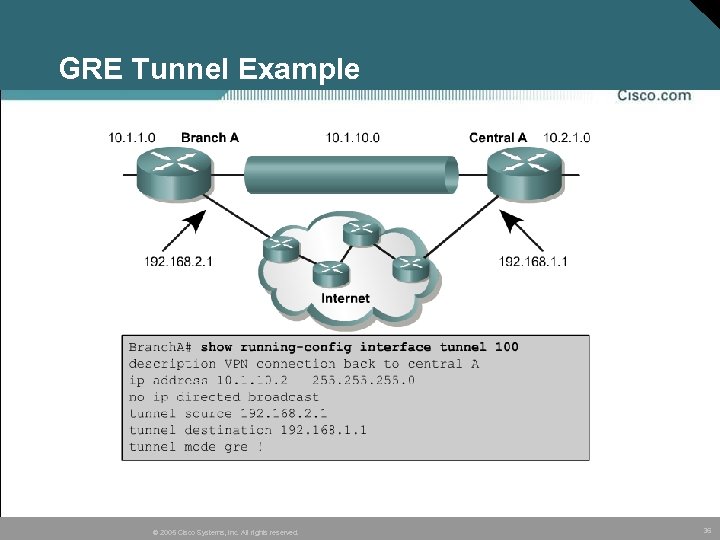 GRE Tunnel Example © 2005 Cisco Systems, Inc. All rights reserved. 36
GRE Tunnel Example © 2005 Cisco Systems, Inc. All rights reserved. 36
 Module 3 – Encryption and VPN Technology 3. 6 VPN © 2005 Cisco Systems, Inc. All rights reserved. 37
Module 3 – Encryption and VPN Technology 3. 6 VPN © 2005 Cisco Systems, Inc. All rights reserved. 37
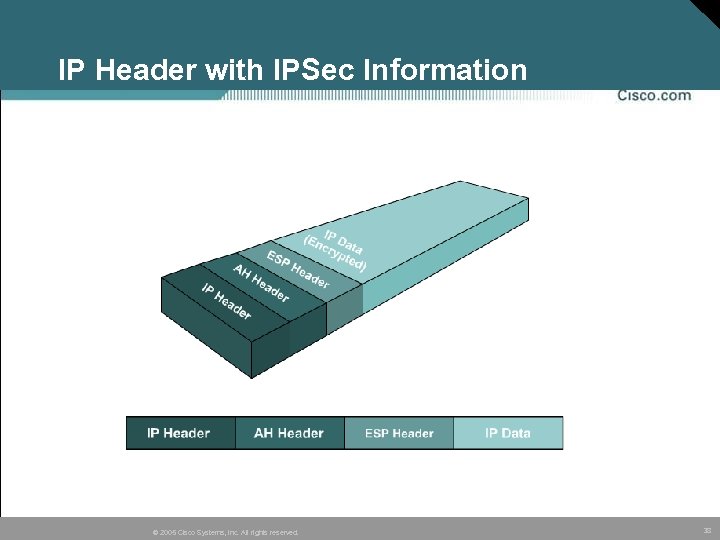 IP Header with IPSec Information © 2005 Cisco Systems, Inc. All rights reserved. 38
IP Header with IPSec Information © 2005 Cisco Systems, Inc. All rights reserved. 38
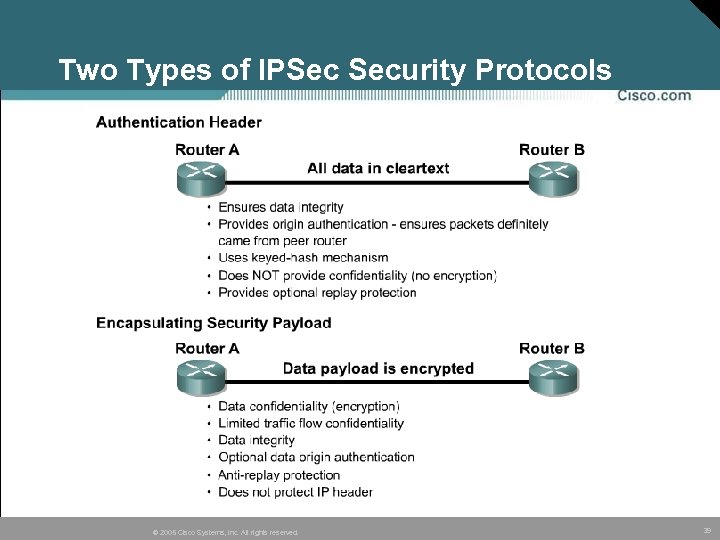 Two Types of IPSec Security Protocols © 2005 Cisco Systems, Inc. All rights reserved. 39
Two Types of IPSec Security Protocols © 2005 Cisco Systems, Inc. All rights reserved. 39
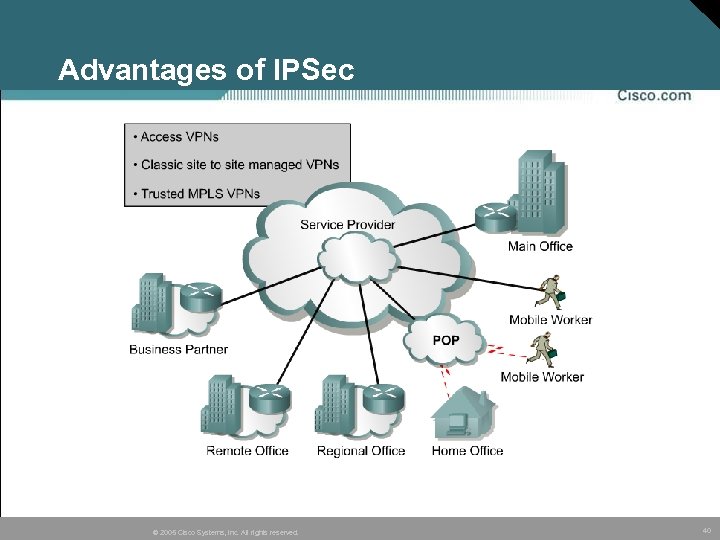 Advantages of IPSec © 2005 Cisco Systems, Inc. All rights reserved. 40
Advantages of IPSec © 2005 Cisco Systems, Inc. All rights reserved. 40
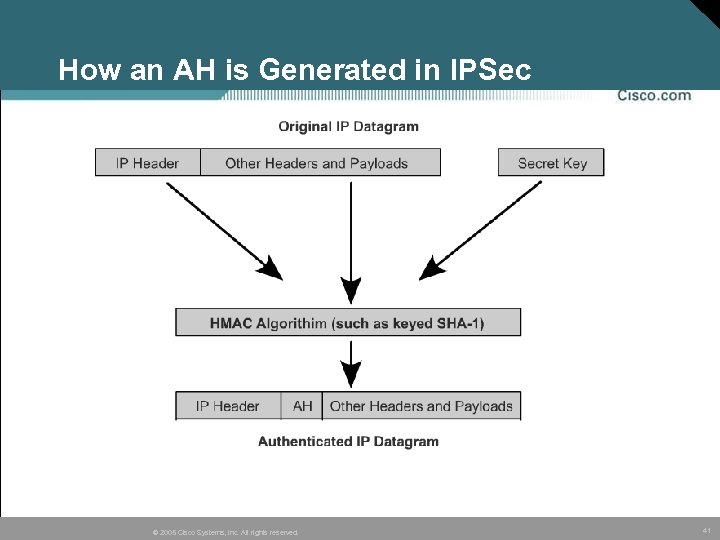 How an AH is Generated in IPSec © 2005 Cisco Systems, Inc. All rights reserved. 41
How an AH is Generated in IPSec © 2005 Cisco Systems, Inc. All rights reserved. 41
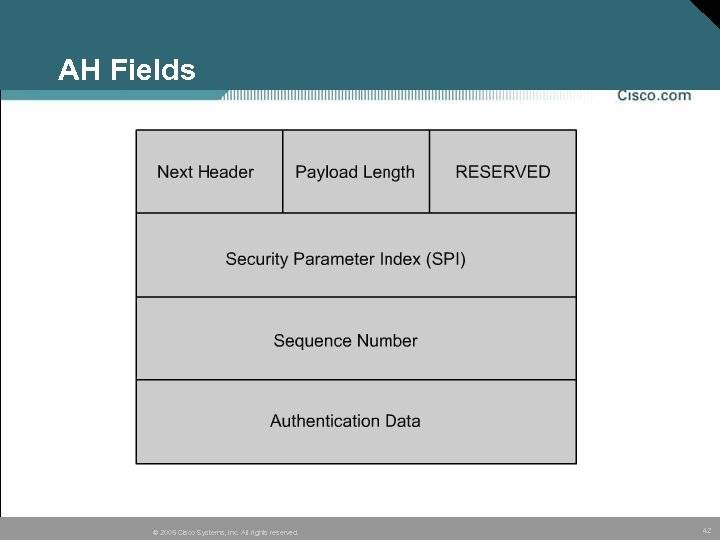 AH Fields © 2005 Cisco Systems, Inc. All rights reserved. 42
AH Fields © 2005 Cisco Systems, Inc. All rights reserved. 42
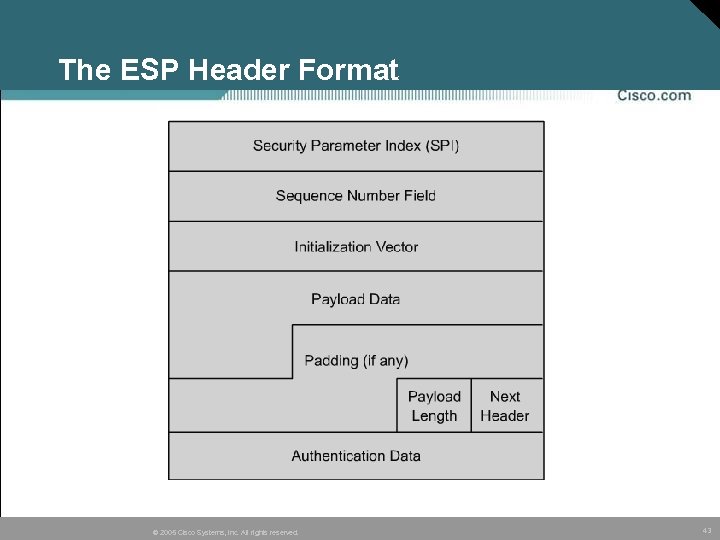 The ESP Header Format © 2005 Cisco Systems, Inc. All rights reserved. 43
The ESP Header Format © 2005 Cisco Systems, Inc. All rights reserved. 43
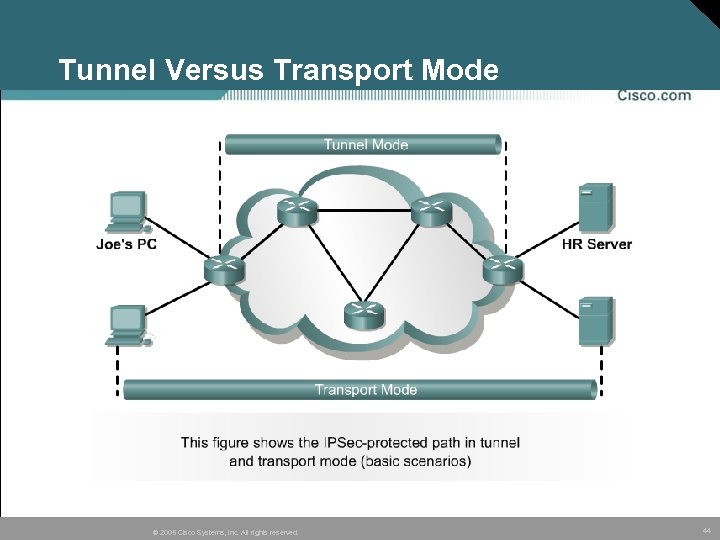 Tunnel Versus Transport Mode © 2005 Cisco Systems, Inc. All rights reserved. 44
Tunnel Versus Transport Mode © 2005 Cisco Systems, Inc. All rights reserved. 44
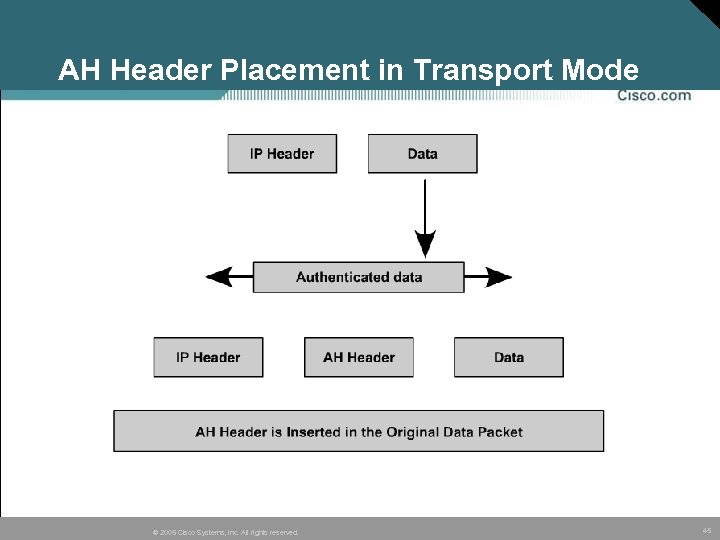 AH Header Placement in Transport Mode © 2005 Cisco Systems, Inc. All rights reserved. 45
AH Header Placement in Transport Mode © 2005 Cisco Systems, Inc. All rights reserved. 45
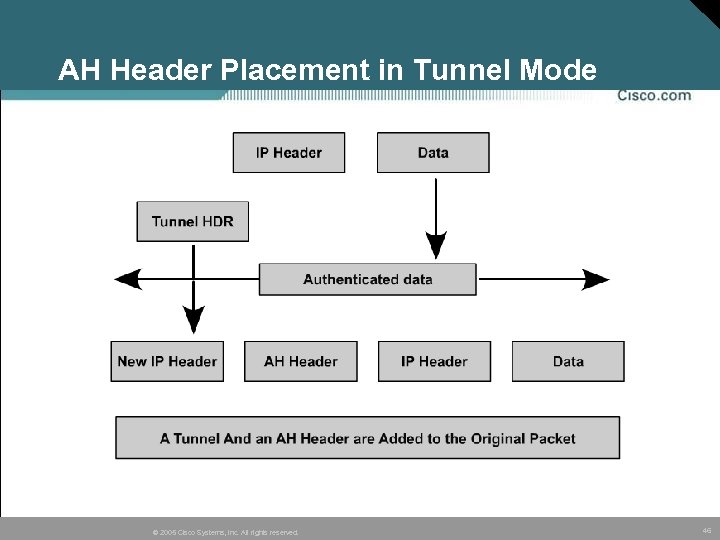 AH Header Placement in Tunnel Mode © 2005 Cisco Systems, Inc. All rights reserved. 46
AH Header Placement in Tunnel Mode © 2005 Cisco Systems, Inc. All rights reserved. 46
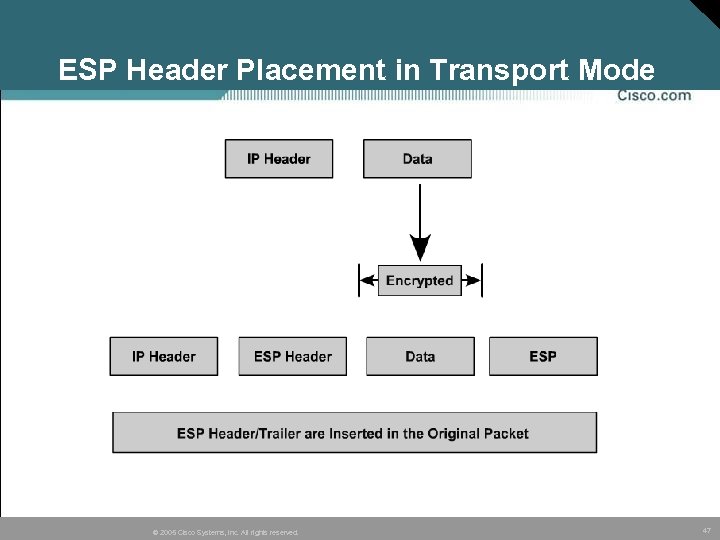 ESP Header Placement in Transport Mode © 2005 Cisco Systems, Inc. All rights reserved. 47
ESP Header Placement in Transport Mode © 2005 Cisco Systems, Inc. All rights reserved. 47
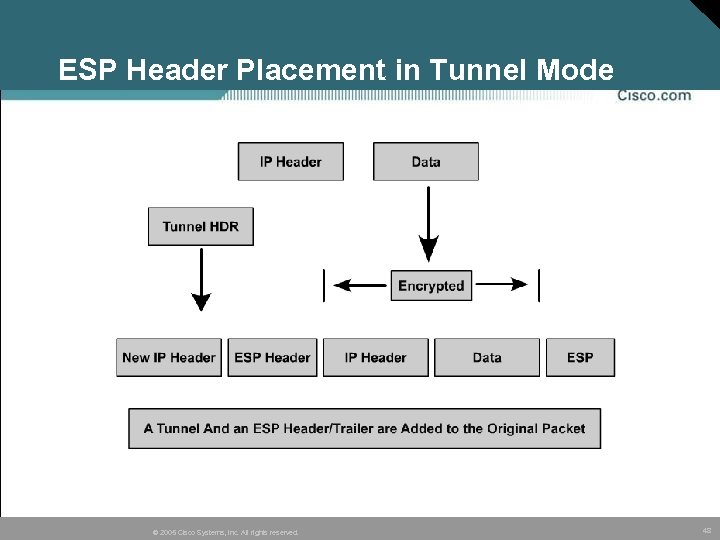 ESP Header Placement in Tunnel Mode © 2005 Cisco Systems, Inc. All rights reserved. 48
ESP Header Placement in Tunnel Mode © 2005 Cisco Systems, Inc. All rights reserved. 48
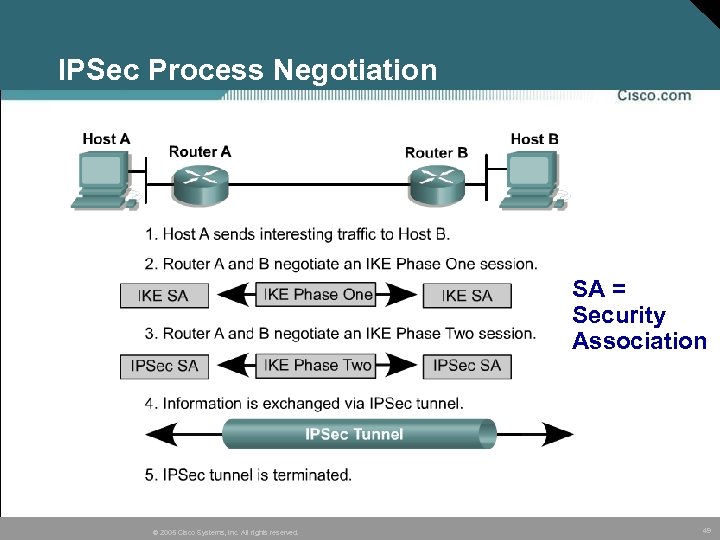 IPSec Process Negotiation SA = Security Association © 2005 Cisco Systems, Inc. All rights reserved. 49
IPSec Process Negotiation SA = Security Association © 2005 Cisco Systems, Inc. All rights reserved. 49
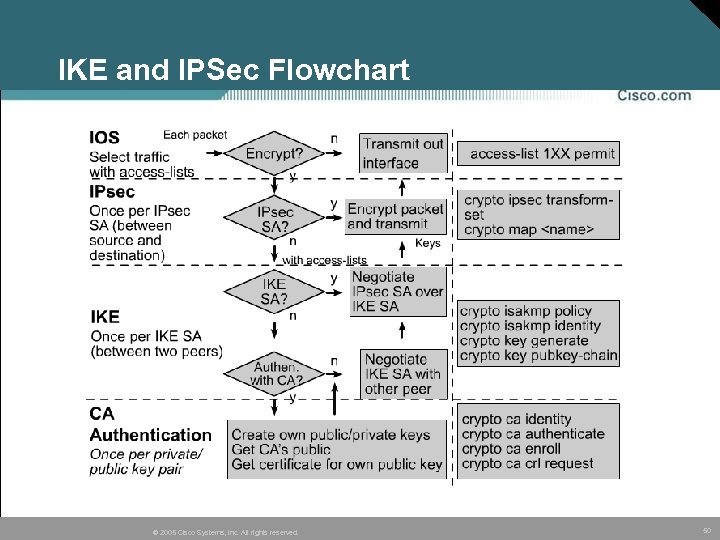 IKE and IPSec Flowchart © 2005 Cisco Systems, Inc. All rights reserved. 50
IKE and IPSec Flowchart © 2005 Cisco Systems, Inc. All rights reserved. 50
 Configuration crypto isakmp policy 10 encr 3 des IKE Phase 1 = IKE SA hash sha authentication pre-share group 2 IKE Phase 2 = IPSec SA ! crypto isakmp key
Configuration crypto isakmp policy 10 encr 3 des IKE Phase 1 = IKE SA hash sha authentication pre-share group 2 IKE Phase 2 = IPSec SA ! crypto isakmp key
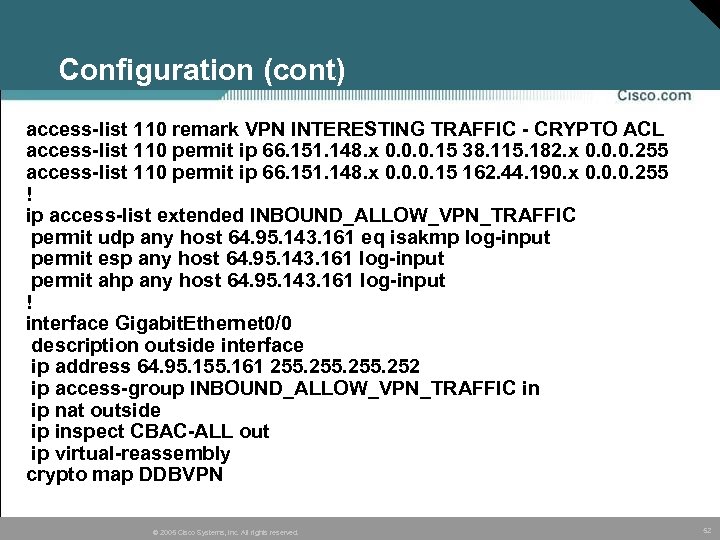 Configuration (cont) access-list 110 remark VPN INTERESTING TRAFFIC - CRYPTO ACL access-list 110 permit ip 66. 151. 148. x 0. 0. 0. 15 38. 115. 182. x 0. 0. 0. 255 access-list 110 permit ip 66. 151. 148. x 0. 0. 0. 15 162. 44. 190. x 0. 0. 0. 255 ! ip access-list extended INBOUND_ALLOW_VPN_TRAFFIC permit udp any host 64. 95. 143. 161 eq isakmp log-input permit esp any host 64. 95. 143. 161 log-input permit ahp any host 64. 95. 143. 161 log-input ! interface Gigabit. Ethernet 0/0 description outside interface ip address 64. 95. 155. 161 255. 252 ip access-group INBOUND_ALLOW_VPN_TRAFFIC in ip nat outside ip inspect CBAC-ALL out ip virtual-reassembly crypto map DDBVPN © 2005 Cisco Systems, Inc. All rights reserved. 52
Configuration (cont) access-list 110 remark VPN INTERESTING TRAFFIC - CRYPTO ACL access-list 110 permit ip 66. 151. 148. x 0. 0. 0. 15 38. 115. 182. x 0. 0. 0. 255 access-list 110 permit ip 66. 151. 148. x 0. 0. 0. 15 162. 44. 190. x 0. 0. 0. 255 ! ip access-list extended INBOUND_ALLOW_VPN_TRAFFIC permit udp any host 64. 95. 143. 161 eq isakmp log-input permit esp any host 64. 95. 143. 161 log-input permit ahp any host 64. 95. 143. 161 log-input ! interface Gigabit. Ethernet 0/0 description outside interface ip address 64. 95. 155. 161 255. 252 ip access-group INBOUND_ALLOW_VPN_TRAFFIC in ip nat outside ip inspect CBAC-ALL out ip virtual-reassembly crypto map DDBVPN © 2005 Cisco Systems, Inc. All rights reserved. 52
 VPN 3005 Concentrator © 2005 Cisco Systems, Inc. All rights reserved. 53
VPN 3005 Concentrator © 2005 Cisco Systems, Inc. All rights reserved. 53
 VPN Hardware Clients © 2005 Cisco Systems, Inc. All rights reserved. 54
VPN Hardware Clients © 2005 Cisco Systems, Inc. All rights reserved. 54
 © 2005, Cisco Systems, Inc. All rights reserved. © 2005 Cisco Systems, Inc. All rights reserved. 55 55
© 2005, Cisco Systems, Inc. All rights reserved. © 2005 Cisco Systems, Inc. All rights reserved. 55 55


