acbe5ddbcffc9bcebffcbf69e914cae7.ppt
- Количество слайдов: 22
 CNIC Grid CA/SDG CA Self Audit Kejun (Kevin) Dong (kevin@cnic. ac. cn) Computer Network Information Center (CNIC) Chinese Academy of Sciences APGrid. PMA F 2 F Meeting @ ASGC March 08, 2010
CNIC Grid CA/SDG CA Self Audit Kejun (Kevin) Dong (kevin@cnic. ac. cn) Computer Network Information Center (CNIC) Chinese Academy of Sciences APGrid. PMA F 2 F Meeting @ ASGC March 08, 2010
 Overview • CNIC Grid CA/SDG CA • Self Audit • Conclusion
Overview • CNIC Grid CA/SDG CA • Self Audit • Conclusion
 CNIC Grid CA • CNIC is an institute of CAS • CNIC Grid CA – The security infrastructure of CNIC Grid – Root CA • CNIC Grid CA Repository – – http: //ca. grid. cn/ CP/CPS Introduction Manual • CA Certificate – 20 years validity --- 2006 -2 -27 2026 -2 -27 – Only issues sub-CA certificate and CA servers and operators certificates
CNIC Grid CA • CNIC is an institute of CAS • CNIC Grid CA – The security infrastructure of CNIC Grid – Root CA • CNIC Grid CA Repository – – http: //ca. grid. cn/ CP/CPS Introduction Manual • CA Certificate – 20 years validity --- 2006 -2 -27 2026 -2 -27 – Only issues sub-CA certificate and CA servers and operators certificates
 SDG CA • Scientific Data Grid (SDG) – Scientific Data Grid (SDG) is an application grid based on scientific data resources sharing and collaboration. • SDG CA – the SDG security infrastructure – The subordinate CA of CNIC Grid CA • SDG CA Repository CP/CPS – – http: //ca. sdg. grid. cn/ CP/CPS Introduction Manual • SDG CA Certificate – 20 years validity --- 2006 -2 -27 2016 -2 -27 • Type of certificates – Person – Host – Service Approved by APGrid. PMA in July 2006
SDG CA • Scientific Data Grid (SDG) – Scientific Data Grid (SDG) is an application grid based on scientific data resources sharing and collaboration. • SDG CA – the SDG security infrastructure – The subordinate CA of CNIC Grid CA • SDG CA Repository CP/CPS – – http: //ca. sdg. grid. cn/ CP/CPS Introduction Manual • SDG CA Certificate – 20 years validity --- 2006 -2 -27 2016 -2 -27 • Type of certificates – Person – Host – Service Approved by APGrid. PMA in July 2006
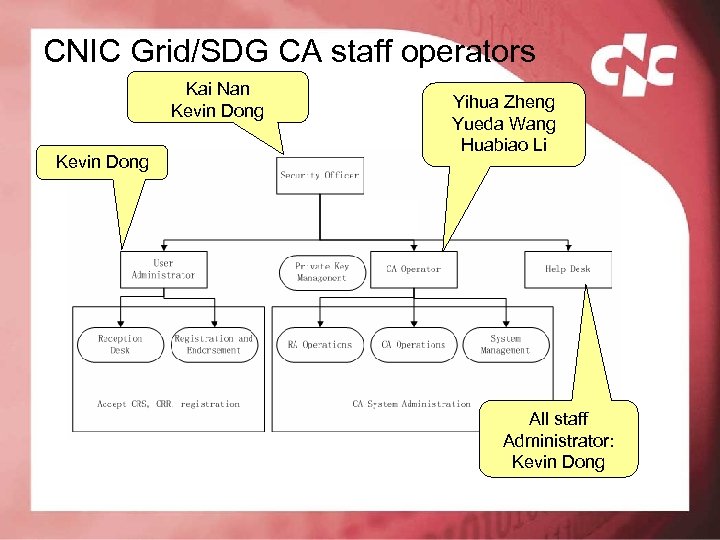 CNIC Grid/SDG CA staff operators Kai Nan Kevin Dong Yihua Zheng Yueda Wang Huabiao Li All staff Administrator: Kevin Dong
CNIC Grid/SDG CA staff operators Kai Nan Kevin Dong Yihua Zheng Yueda Wang Huabiao Li All staff Administrator: Kevin Dong
 Hardware • CA server – DELL GX 620 P 4 CPU 3. 20 GHz, Red Hat Linux AS 4 – Offline, no connection to any other network – UPS is supplied • RA server – DELL GX 620 P 4 CPU 3. 20 GHz, Red Hat Linux AS 4 – connected to the Internet • Only the necessary ports for RA operation are opened. Other ports are filtered by the firewall. – UPS is supplied • Web server (repository) – The same machine as RA Server – connected to the Internet • Same as RA Server – UPS is supplied
Hardware • CA server – DELL GX 620 P 4 CPU 3. 20 GHz, Red Hat Linux AS 4 – Offline, no connection to any other network – UPS is supplied • RA server – DELL GX 620 P 4 CPU 3. 20 GHz, Red Hat Linux AS 4 – connected to the Internet • Only the necessary ports for RA operation are opened. Other ports are filtered by the firewall. – UPS is supplied • Web server (repository) – The same machine as RA Server – connected to the Internet • Same as RA Server – UPS is supplied
 Sofeware • Open. CA • Cert. Utitily Tool – Generate CSR
Sofeware • Open. CA • Cert. Utitily Tool – Generate CSR
 Physical Access • CA room – Located in the CNIC machine room. – Limited person can enter. • Security Officer • CA Operators • Other CNIC administrators – Doors equipped with fingerprint recognition system. – Monitored by the CCTV • Physical access – The CA operator is not allowed to access the CA machines alone and need to do so with the other CA operator. – If the CA operator needs to access the CA machines alone, he must notify the fact to the user administrator by Emails before and after entering the room. – All events about the access to the machines must be recorded in the paper sheets prepared in the room. The events include the names of CA operators, date and time of entering/leaving the room, and the purpose of the access to the machine. – The filled sheets will be kept in the dedicated safe box.
Physical Access • CA room – Located in the CNIC machine room. – Limited person can enter. • Security Officer • CA Operators • Other CNIC administrators – Doors equipped with fingerprint recognition system. – Monitored by the CCTV • Physical access – The CA operator is not allowed to access the CA machines alone and need to do so with the other CA operator. – If the CA operator needs to access the CA machines alone, he must notify the fact to the user administrator by Emails before and after entering the room. – All events about the access to the machines must be recorded in the paper sheets prepared in the room. The events include the names of CA operators, date and time of entering/leaving the room, and the purpose of the access to the machine. – The filled sheets will be kept in the dedicated safe box.
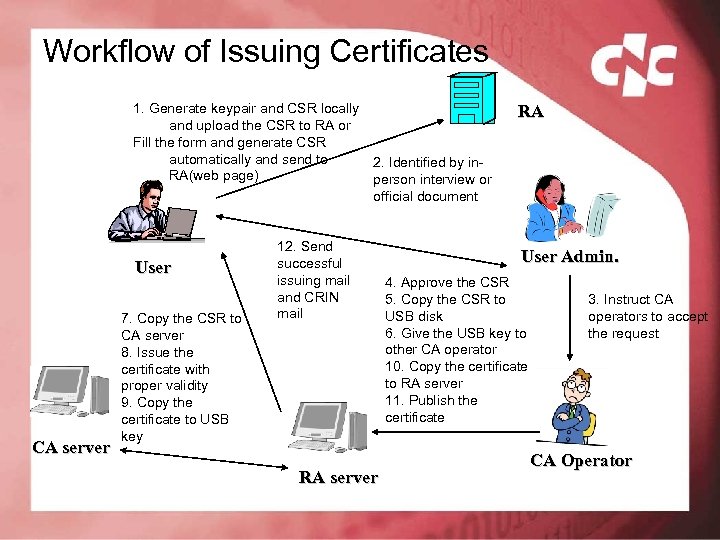 Workflow of Issuing Certificates 1. Generate keypair and CSR locally and upload the CSR to RA or Fill the form and generate CSR automatically and send to 2. Identified by in. RA(web page) person interview or official document User CA server 7. Copy the CSR to CA server 8. Issue the certificate with proper validity 9. Copy the certificate to USB key 12. Send successful issuing mail and CRIN mail RA server RA User Admin. 4. Approve the CSR 5. Copy the CSR to USB disk 6. Give the USB key to other CA operator 10. Copy the certificate to RA server 11. Publish the certificate 3. Instruct CA operators to accept the request CA Operator
Workflow of Issuing Certificates 1. Generate keypair and CSR locally and upload the CSR to RA or Fill the form and generate CSR automatically and send to 2. Identified by in. RA(web page) person interview or official document User CA server 7. Copy the CSR to CA server 8. Issue the certificate with proper validity 9. Copy the certificate to USB key 12. Send successful issuing mail and CRIN mail RA server RA User Admin. 4. Approve the CSR 5. Copy the CSR to USB disk 6. Give the USB key to other CA operator 10. Copy the certificate to RA server 11. Publish the certificate 3. Instruct CA operators to accept the request CA Operator
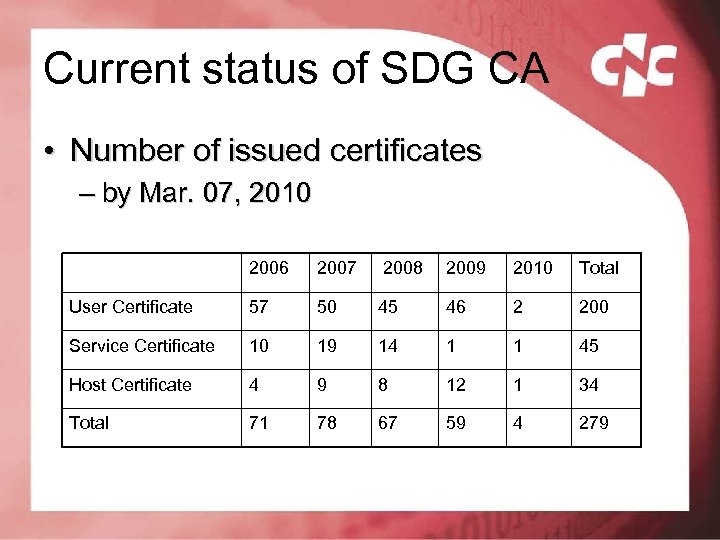 Current status of SDG CA • Number of issued certificates – by Mar. 07, 2010 2006 2007 2008 2009 2010 Total User Certificate 57 50 45 46 2 200 Service Certificate 10 19 14 1 1 45 Host Certificate 4 9 8 12 1 34 Total 71 78 67 59 4 279
Current status of SDG CA • Number of issued certificates – by Mar. 07, 2010 2006 2007 2008 2009 2010 Total User Certificate 57 50 45 46 2 200 Service Certificate 10 19 14 1 1 45 Host Certificate 4 9 8 12 1 34 Total 71 78 67 59 4 279
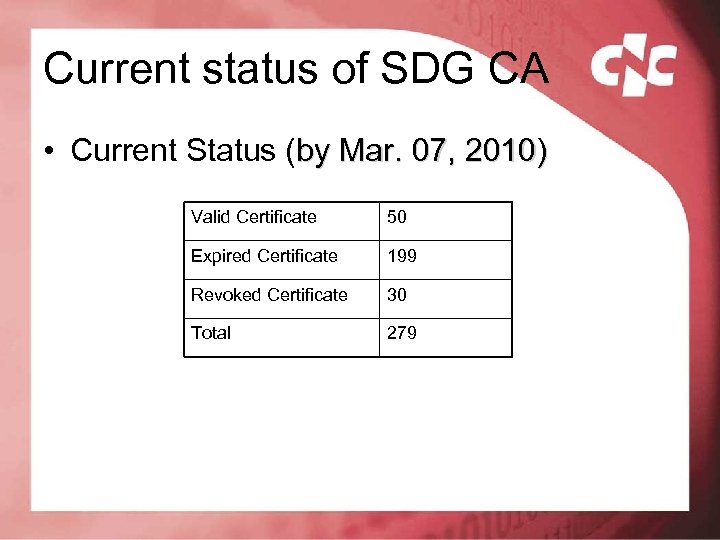 Current status of SDG CA • Current Status (by Mar. 07, 2010) Valid Certificate 50 Expired Certificate 199 Revoked Certificate 30 Total 279
Current status of SDG CA • Current Status (by Mar. 07, 2010) Valid Certificate 50 Expired Certificate 199 Revoked Certificate 30 Total 279
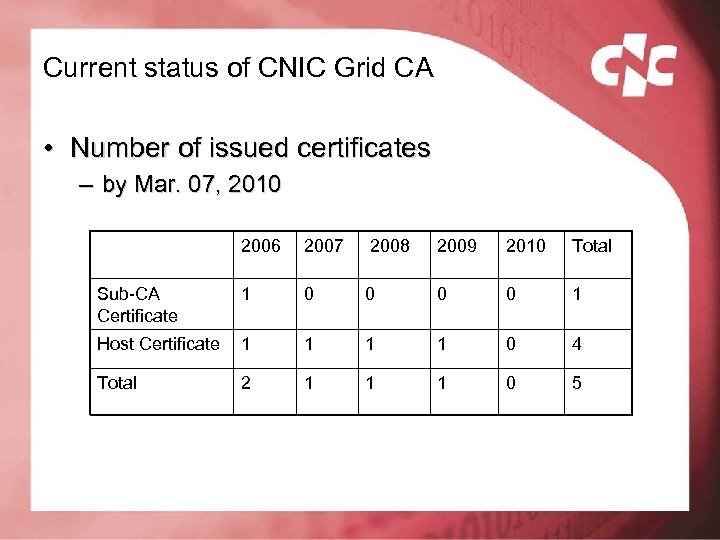 Current status of CNIC Grid CA • Number of issued certificates – by Mar. 07, 2010 2006 2007 2008 2009 2010 Total Sub-CA Certificate 1 0 0 1 Host Certificate 1 1 0 4 Total 2 1 1 1 0 5
Current status of CNIC Grid CA • Number of issued certificates – by Mar. 07, 2010 2006 2007 2008 2009 2010 Total Sub-CA Certificate 1 0 0 1 Host Certificate 1 1 0 4 Total 2 1 1 1 0 5
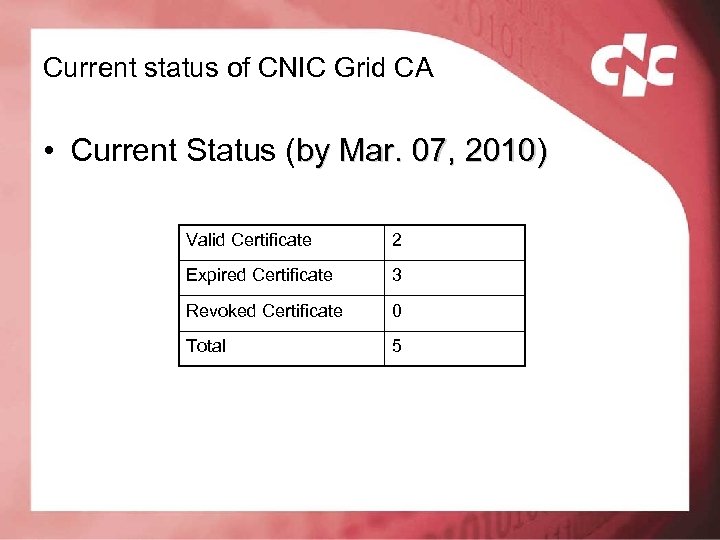 Current status of CNIC Grid CA • Current Status (by Mar. 07, 2010) Valid Certificate 2 Expired Certificate 3 Revoked Certificate 0 Total 5
Current status of CNIC Grid CA • Current Status (by Mar. 07, 2010) Valid Certificate 2 Expired Certificate 3 Revoked Certificate 0 Total 5
 Self Audit • SDG CA – CP/CPS 1. 8 ->1. 9 – CRL Profile 1. 3 ->1. 4 • CNIC Grid CA – CP/CPS 1. 4 ->1. 5 – CRL Profile 1. 2 ->1. 3 • Auditing. Spreadsheet. xls – IGTF classic profile: IGTF-AP-classic-4 -2 – Special thanks to Yoshio
Self Audit • SDG CA – CP/CPS 1. 8 ->1. 9 – CRL Profile 1. 3 ->1. 4 • CNIC Grid CA – CP/CPS 1. 4 ->1. 5 – CRL Profile 1. 2 ->1. 3 • Auditing. Spreadsheet. xls – IGTF classic profile: IGTF-AP-classic-4 -2 – Special thanks to Yoshio
 Summary • Marks – A: 66 – B: 3 – C: 2 – D: 0
Summary • Marks – A: 66 – B: 3 – C: 2 – D: 0
 RA - (4) • RA should ensure that the requester is appropriately authorized by the owner of the associated FQDN or the responsible administrator of the machine to use the FQDN identifiers asserted in the certificate. – In section 4. 3. 1, the role to ensure the FQDN will be defined in CP/CPS. –B
RA - (4) • RA should ensure that the requester is appropriately authorized by the owner of the associated FQDN or the responsible administrator of the machine to use the FQDN identifiers asserted in the certificate. – In section 4. 3. 1, the role to ensure the FQDN will be defined in CP/CPS. –B
 RA - (6) • The CA or RA should have documented evidence on retaining the same identity over time. – It is obvious that the DN is unique for a person because the email or FQDN is included. Now it is defined in section 3. 2. 3 –C
RA - (6) • The CA or RA should have documented evidence on retaining the same identity over time. – It is obvious that the DN is unique for a person because the email or FQDN is included. Now it is defined in section 3. 2. 3 –C
 CA - (16) • The on-line CA architecture must provide for a log of issued certificates and revocations. The log should be tamperprotected. – The logs are available and archived. We will make logs tamper-protected. –C
CA - (16) • The on-line CA architecture must provide for a log of issued certificates and revocations. The log should be tamperprotected. – The logs are available and archived. We will make logs tamper-protected. –C
 CA - (27), (32) • The authority must publish CRLs, and these CRLs should be compliant with RFC 5280. – In section 2 and section 4. 9. 8, "the repository of certificates and CRLs are available at http: //ca. sdg. grid. cn/" though RFC 5280 is not explicitly defined in CP/CPS. The RFC 5280 will be defined in the CP/CPS. –B
CA - (27), (32) • The authority must publish CRLs, and these CRLs should be compliant with RFC 5280. – In section 2 and section 4. 9. 8, "the repository of certificates and CRLs are available at http: //ca. sdg. grid. cn/" though RFC 5280 is not explicitly defined in CP/CPS. The RFC 5280 will be defined in the CP/CPS. –B
 CA - (45) • Identity validation records must be kept at least as long as there are valid certificates based on such a validation. – The identity validation records are kept at least as long as there are valid certificates based on such a validation. But it is not mentioned in CP/CPS. We will add in section 5. 4. 3. –B
CA - (45) • Identity validation records must be kept at least as long as there are valid certificates based on such a validation. – The identity validation records are kept at least as long as there are valid certificates based on such a validation. But it is not mentioned in CP/CPS. We will add in section 5. 4. 3. –B
 Conclusion • Positive • Update of CP/CPS and CRL profile – Done – Release soon
Conclusion • Positive • Update of CP/CPS and CRL profile – Done – Release soon
 Thanks!
Thanks!


