c9b9417c5dbb1cf66f68e89af7b719eb.ppt
- Количество слайдов: 45

CMGT 442 Information Systems Risk Management Philip Robbins – November 28, 2012 (Week 3) University of Phoenix Mililani Campus

Objectives: Week 3 • - Risk Assessment (Part 2) Review Week 1 & 2: Concepts LT Activity: Week 3 & Week 4 Article Readings Discuss Homework Assignments & Class Videos Week 3: Quantitative Risk Analysis vs. Qualitative Risk Assessments Review NIST SP 800 -39 Review Week 3: Questions Assignments: IDV & LT Papers Quiz #3
Learning Team Activity • Activity: Review Week 3 & 4 ‘Article’ Readings - 15 minutes: Read Articles - 10 minutes: Answer article questions - 10 minutes: Present your article to the class - Submit for credit.

LT Activity: Week 3 Article Readings • Barr (2011). Federal Business Continuity Plans - Do you think the private sector must employ something similar to the Federal Government’s Continuity of Operations Process (COOP) as an integral part of their enterprise risk management plan? • Ledford (2012). FISMA - Do you think the Federal Information Security Management Act (FISMA) might provide the basis for a standard framework for enterprise risk management adaptable to the private sector?

LT Activity: Week 4 Article Readings • Ainworth (2009). The BCP Process - Might an effective risk management plan be considered a process that may restore all systems, businesses, processes, facilities, and people? • Barr (2011). Good Practice for Information Security - What changes would you recommend for the Information Security Forum’s 2007 Standard? - Which of these changes must be incorporated into the enterprise’s risk management plan?

REVIEW: IDV Assignments #1 & #2 #1: Risks associated with an industry. #2: Organization that has recently been compromised. - Focus on risks from Information Systems and how we manage those risks. - This involves understanding what Information Systems are and how they work. - Risks are all around you. (Class Videos)

Break? • This is probably time for a break…

QUICK REVIEW: Week 1 • What is Information Systems Risk Management? - Information Systems Risk Management is the process of identifying, assessing, and reducing (mitigating) risks to an acceptable level.

QUICK REVIEW: Week 2 • What are the components of Information Systems Risk? - Threats & Threat Agents - Vulnerabilities (Weakness) - Controls (Safeguards) - Impact
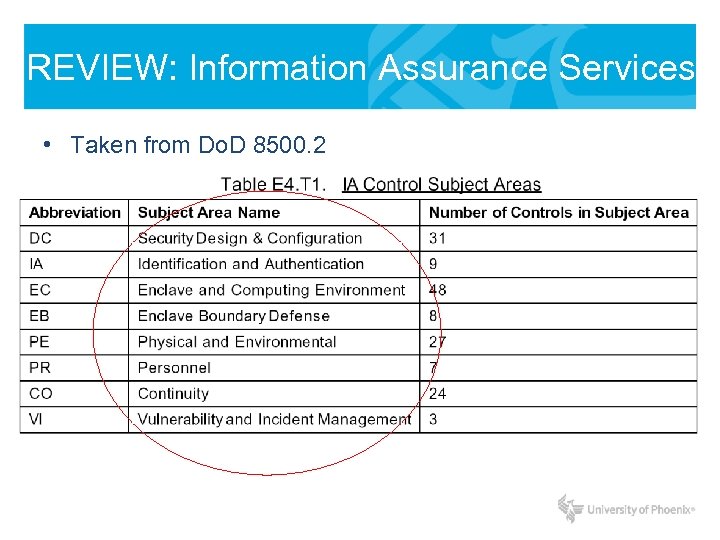
REVIEW: Information Assurance Services • Taken from Do. D 8500. 2
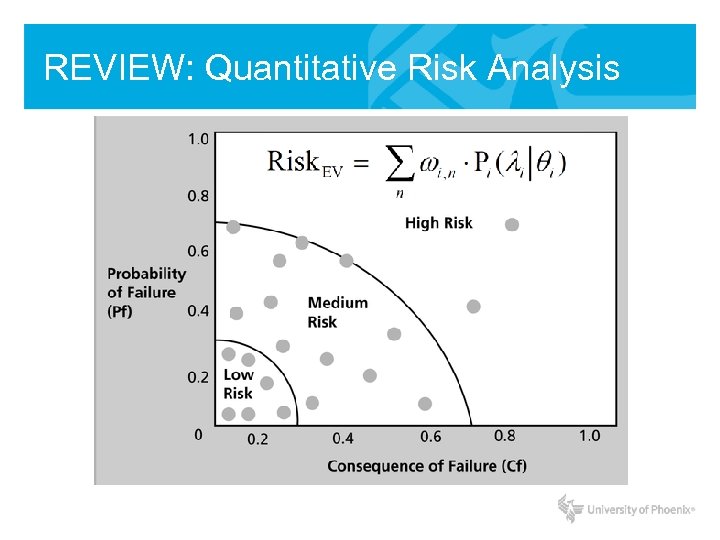
REVIEW: Quantitative Risk Analysis
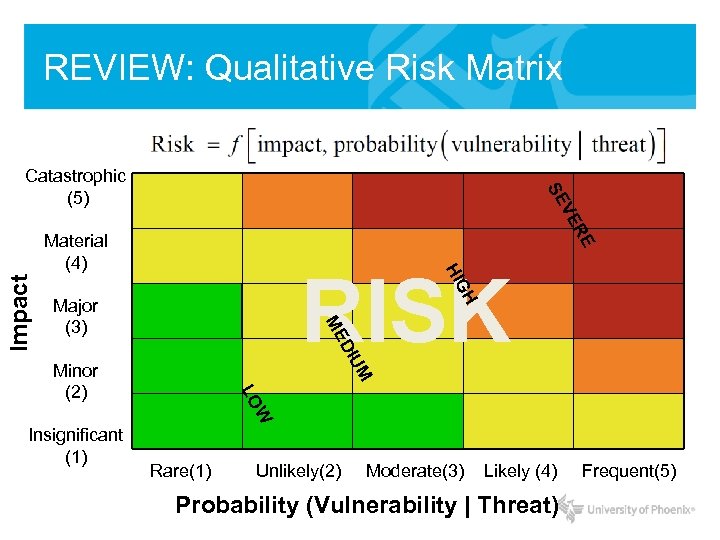
REVIEW: Qualitative Risk Matrix R VE SE Catastrophic (5) GH HI RISK Major (3) ME UM DI Impact E Material (4) W Insignificant (1) LO Minor (2) Rare(1) Unlikely(2) Moderate(3) Likely (4) Probability (Vulnerability | Threat) Frequent(5)
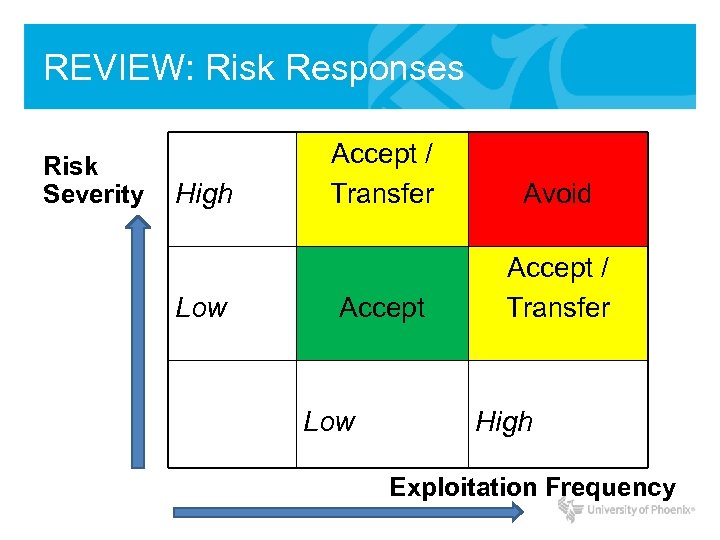
REVIEW: Risk Responses Risk Severity High Low Accept / Transfer Avoid Accept / Transfer Low High Exploitation Frequency

REVIEW: Risk Responses • Risk Avoidance – Halt or stop activity causing risk • Risk Transference – Transfer the risk (i. e. buy insurance) • Risk Mitigation – Reduce impact with controls/safeguards • Risk Acceptance – Understand consequences and accept risk

REVIEW: Total vs. Residual Risk • When a company chooses not to implement a safeguard (if they accept the risk) then they accept the total risk. • The leftover risk after applying countermeasures is called the residual risk. • No matter what controls you place to protect an asset, it will never be 100% secure. • Risk is never zero, thus, there is always some form of residual risk.

Week 3: Risk Assessment (Part 2) • Objectives - What is Quantitative Risk Analysis? - What is Qualitative Risk Assessment? - Positives (pros) and Negatives (cons) of each. - Which method is preferred?

Value of Information and Assets • Risk Management • It’s important to understand the value of your information and information systems. • So what is my information worth? - Value can be measured both Quantitatively and Qualitatively.

Two Types of Approaches • Quantitative Analysis • Qualitative Assessment - Tangible impacts can be measured Quantitatively in lost revenue, repair costs, or resources. - Other impacts (i. e. loss of public confidence or credibility, etc. ) can be qualified in terms of High, Medium, or Low impacts.
Let’s start • …with Quantitative analysis. - Warning: There is MATH… much more math. =(

Quantitative Analysis • Quantitative analysis attempts to assign real values to all elements of the risk analysis process. - Asset value - Safeguards / Controls - Threat frequency - Probability of incident

Quantitative Analysis • • • - Purely Quantitative Risk Analysis is impossible. There always unknown values. There always “Qualitative” values. What is the value of a reputation? …but what if you focused on Information Security Services as a unit of measurement? • Quantitative analysis can be automated with software and tools. - Requires large amounts of data to be collected.

Quantitative Analysis: Step-by-Step 1. Assign value to your information. 2. Estimate cost for each asset and threat combination. 3. Perform a Threat Analysis – determine the probability of exploitation. 4. Derive the overall loss potential per year. 5. Reduce, Transfer, Avoid, or Accept the Risk.
Step 1: Assign Value to Assets • What is my information assets worth? - What is my costs to obtain? - How much money does an asset bring in? - What is its value to my competitors? - How much would it cost to re-create? - Are there possible legal liabilities to account for?

Step 2: Estimate Loss Potential • For each threat, we need to determine how much a successful compromise could cost: - Physical damage Loss of productivity Cost for repairs Amount of Damage - “Single Loss Expectancy” per asset and threat* • Example: if you have a virus outbreak and each outbreak costs $50 K in lost revenue and repair costs. Your SLE = $50 K

Step 2: Estimate of Loss potential • When determining SLE, you may hear the term EF (exposure factor). • Loss then becomes a percentage of the assets value (AV). - This is where EF comes in… SLE = AV X EF

Step 3: Perform a Threat Analysis • Figure out the likelihood of a threat incident. - Analyze vulnerabilities and rate of exploits. - Analyze probabilities of threats to your location and systems. - Review historical records of incidents. • Annualized Rate of Occurrence (ARO) Example: If the chance of a virus outbreak in any month is = 75%, then ARO =. 75 * 12 (1 year) = 9 occurrences per year

Step 4: Derive the ALE Derive the Annual Loss Expectancy ALE = SLE * ARO • Example: Cost of a virus outbreak is $50 K (SLE) X 9 occurrences per year (ARO) ---------------------------------$450 K cost total (ALE)

Step 5: Risk Response • Risk Avoidance – Halt or stop activity causing risk • Risk Transference – Transfer the risk (i. e. buy insurance) • Risk Mitigation – Reduce impact with controls/safeguards • Risk Acceptance – Understand consequences and accept risk

Reducing Risk • When deciding whether to implement controls, safeguards, or countermeasures: you SHOULD be concerned about saving costs. • It doesn’t make sense to spend more to protect an asset that’s worth less! • So how do we determine if it’s worth it? …

Reducing Risk • Reducing risks through controls / safeguards / countermeasures makes sense when: • If the cost (per year) of a countermeasure is more than the ALE, don’t implement it.

Definitions • The Annualized Rate of Occurrence (ARO) is the likelihood of a risk occurring within a year. • The Single Loss Expectancy (SLE) is the dollar value of the loss that equals the total cost of the risk. • The ALE is calculated by multiplying the ARO by the SLE: ALE = ARO x SLE

Review of Quantitative Analysis • Assign value to information & assets: Asset Value (AV) • Estimate: Single Loss Expectancy (SLE) • Estimate: Likelihood of Threats (ARO) • Calculate: Annual Loss Expectancy (ALE) • Risk Response: Reduce, Transfer, Avoid or Accept.

Class Exercise: Quantitative Analysis • You own a data warehouse valued at $1, 000 USD (information & infrastructure included). • If the threat of a fire breaking out were to occur, it is expected that 40% of warehouse (including the data) would be damaged/lost. • The chance of a fire breaking out for this type of warehouse is known to be 8% annually.
Let’s move on to • …Qualitative assessments.

Qualitative Risk Assessment • Instead of assigning specific values… • We walk through different scenarios, rank and prioritize based on threats and counter measures. • Techniques includes: - Judgment - Best practices - Intuition (gut feelings) - Experience

Qualitative Assessments • Specific techniques include: - Delphi method (opinions provided anonymously) - Brainstorming - Storyboarding - Focus groups - Surveys - Questioners - Interviews / one-on-one meetings … very subjective
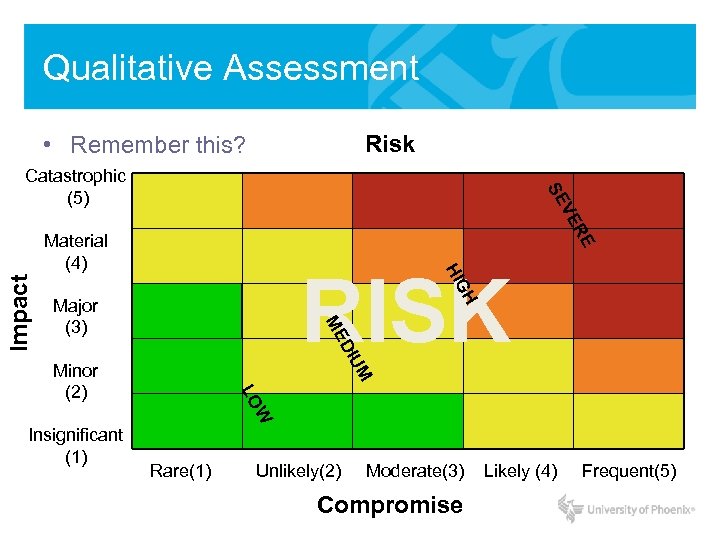
Qualitative Assessment Risk • Remember this? R VE SE Catastrophic (5) GH HI RISK Major (3) ME UM DI Impact E Material (4) W Insignificant (1) LO Minor (2) Rare(1) Unlikely(2) Moderate(3) Compromise Likely (4) Frequent(5)
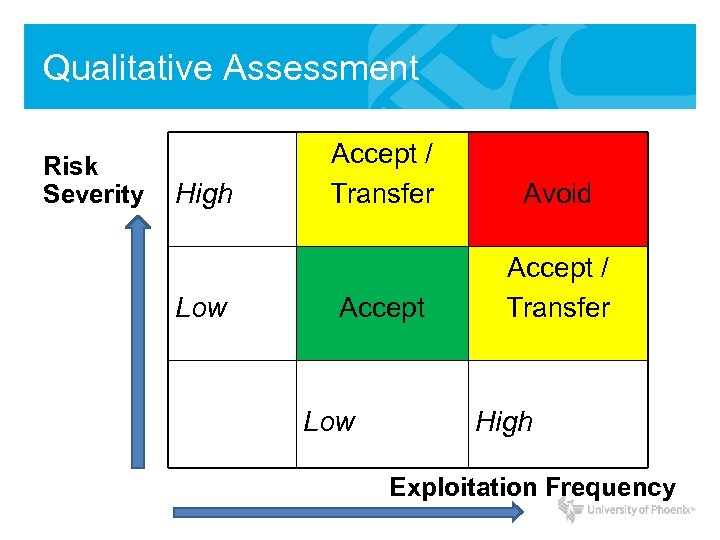
Qualitative Assessment Risk Severity High Low Accept / Transfer Avoid Accept / Transfer Low High Exploitation Frequency
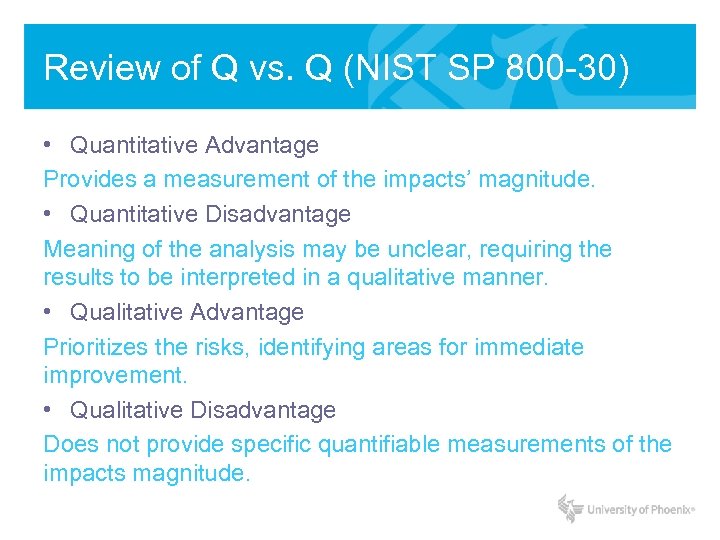
Review of Q vs. Q (NIST SP 800 -30) • Quantitative Advantage Provides a measurement of the impacts’ magnitude. • Quantitative Disadvantage Meaning of the analysis may be unclear, requiring the results to be interpreted in a qualitative manner. • Qualitative Advantage Prioritizes the risks, identifying areas for immediate improvement. • Qualitative Disadvantage Does not provide specific quantifiable measurements of the impacts magnitude.
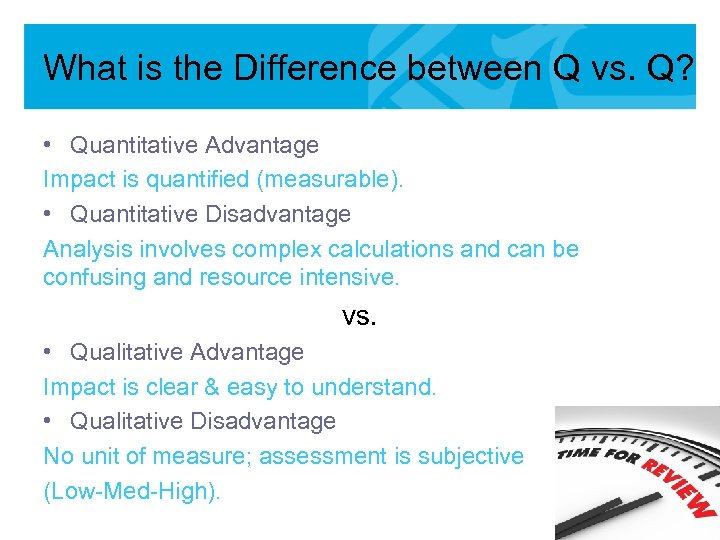
What is the Difference between Q vs. Q? • Quantitative Advantage Impact is quantified (measurable). • Quantitative Disadvantage Analysis involves complex calculations and can be confusing and resource intensive. vs. • Qualitative Advantage Impact is clear & easy to understand. • Qualitative Disadvantage No unit of measure; assessment is subjective (Low-Med-High).
What is the Difference between Q vs. Q? • Which approach is preferred when it comes to Information Systems Risk Management? • Why? - Let’s discuss…

Break? • This is probably time for a break…
Quiz: Week 3 • 10 -15 minutes

IDV and LT Assignments for Week #3 • Laptops at UOPX - Explain your thought process behind risk management as a new information system is introduced to an existing network. • Constraints involved with Information Sharing - Identify and discuss the risk components involved and possible constraints that may add to your risk. - Outlined formats are OK.
Week 3 Review Questions We’ll review these questions & more next week to prep for the final exam…
c9b9417c5dbb1cf66f68e89af7b719eb.ppt