dde884df6517db5dff621d5af0aefe23.ppt
- Количество слайдов: 24
 Cloud Operating System Unit 13 Cloud System Management II M. C. Chiang Department of Computer Science and Engineering National Sun Yat-sen University Kaohsiung, Taiwan, ROC
Cloud Operating System Unit 13 Cloud System Management II M. C. Chiang Department of Computer Science and Engineering National Sun Yat-sen University Kaohsiung, Taiwan, ROC
 Outline q Data Management v Data Integration v Data Security v Data Redundancy v Data Ownership q Network Management v Open. Stack Nova-Network v Open. Stack Quantum v Network Security q Summary 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -2
Outline q Data Management v Data Integration v Data Security v Data Redundancy v Data Ownership q Network Management v Open. Stack Nova-Network v Open. Stack Quantum v Network Security q Summary 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -2
 Data Management q What can be taken as data? v Uploaded files (Documents, Videos, Music) v Program Codes v User personal information (Name, Age, Location, etc. ) v User surfing history v etc. 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -3
Data Management q What can be taken as data? v Uploaded files (Documents, Videos, Music) v Program Codes v User personal information (Name, Age, Location, etc. ) v User surfing history v etc. 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -3
 Data Integration q There are no existing standards for moving data in the cloud. q The methods of each manufacture’s cloud data storage is different. q Here are some issues for enterprises to treat their data for integration: v Backup v Data movement (from/to) the Cloud 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -4
Data Integration q There are no existing standards for moving data in the cloud. q The methods of each manufacture’s cloud data storage is different. q Here are some issues for enterprises to treat their data for integration: v Backup v Data movement (from/to) the Cloud 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -4
 Data Security (1) q Data security can be considered from three aspects: v Physical Layer n n Touchable things such as machines, devices. As mentioned in “IDC Management”. v Network Layer n n The behaviors through network. This will be discussed later. v Management Layer n 3/18/2018 Can data be recognized by the Cloud? Cloud Operating System - Unit 12: Cloud Management U 12 -5
Data Security (1) q Data security can be considered from three aspects: v Physical Layer n n Touchable things such as machines, devices. As mentioned in “IDC Management”. v Network Layer n n The behaviors through network. This will be discussed later. v Management Layer n 3/18/2018 Can data be recognized by the Cloud? Cloud Operating System - Unit 12: Cloud Management U 12 -5
 Data Security (2) q With the rise of cloud computing, there are some new problems. v Data analysis n Google advertisement, e. g. , the righ side of the letter when using Gmail. v Mash-up authorization n n 3/18/2018 Facebook utilizes both sensitive and non-sensitive data to present to other users. Third-party applications on Facebook can also utilize the data. Cloud Operating System - Unit 12: Cloud Management U 12 -6
Data Security (2) q With the rise of cloud computing, there are some new problems. v Data analysis n Google advertisement, e. g. , the righ side of the letter when using Gmail. v Mash-up authorization n n 3/18/2018 Facebook utilizes both sensitive and non-sensitive data to present to other users. Third-party applications on Facebook can also utilize the data. Cloud Operating System - Unit 12: Cloud Management U 12 -6
 Data Security (3) v Increased authentication demands n Pros l l l n Software piracy becomes difficult. Centralize monitoring on software. Prevents sensitive data spread on untrustworthy clients. Cons l Phishing for stealing access credentials. v Cost-effective defense n n 3/18/2018 Cloud Computing encourages single points of failure. Protect productivity and trust from attackers. Cloud Operating System - Unit 12: Cloud Management U 12 -7
Data Security (3) v Increased authentication demands n Pros l l l n Software piracy becomes difficult. Centralize monitoring on software. Prevents sensitive data spread on untrustworthy clients. Cons l Phishing for stealing access credentials. v Cost-effective defense n n 3/18/2018 Cloud Computing encourages single points of failure. Protect productivity and trust from attackers. Cloud Operating System - Unit 12: Cloud Management U 12 -7
 Data Security (4) q Data shouldn’t be recognized by the Cloud provider/maintainer. q The simplest way to protect the data is performing encryption. v AES v RSA v Blowfish v IDEA 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -8
Data Security (4) q Data shouldn’t be recognized by the Cloud provider/maintainer. q The simplest way to protect the data is performing encryption. v AES v RSA v Blowfish v IDEA 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -8
 Data Security – Examples (1) q Amazon S 3 v 2011/10/04 announced v Encryption n When writing the object, add an additional request header. v Decryption n Automatically happens when the data retrieved. v Encryption Algorithm n 3/18/2018 AES-256 Cloud Operating System - Unit 12: Cloud Management U 12 -9
Data Security – Examples (1) q Amazon S 3 v 2011/10/04 announced v Encryption n When writing the object, add an additional request header. v Decryption n Automatically happens when the data retrieved. v Encryption Algorithm n 3/18/2018 AES-256 Cloud Operating System - Unit 12: Cloud Management U 12 -9
 Data Security – Examples (2) q Google Docs v Google Docs doesn’t provide any server side encryption methods. v For data security, users can n n encrypt the document before uploading set the group who can view the document v Encrypted document can not be viewed on Google Docs. 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -10
Data Security – Examples (2) q Google Docs v Google Docs doesn’t provide any server side encryption methods. v For data security, users can n n encrypt the document before uploading set the group who can view the document v Encrypted document can not be viewed on Google Docs. 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -10
 Data Security – Before Using the Cloud q Users should confirm service providers’ response for the following three questions v Are files transferred securely to/from the servers? v Are files stored on the servers encrypted by default? v How will the provider react to the file request from law? n 3/18/2018 If the provider could decrypt the file, what will the provider do? Cloud Operating System - Unit 12: Cloud Management U 12 -11
Data Security – Before Using the Cloud q Users should confirm service providers’ response for the following three questions v Are files transferred securely to/from the servers? v Are files stored on the servers encrypted by default? v How will the provider react to the file request from law? n 3/18/2018 If the provider could decrypt the file, what will the provider do? Cloud Operating System - Unit 12: Cloud Management U 12 -11
 Data Redundancy q The idea is simple; copy multiple data across different “zones”. q Example: The Ring in Open. Stack v Review: n Ring records the physical address of data. v When creating a ring, administrator must supply how many replicas through the zones, and the minimum interval of copying data in command. 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -12
Data Redundancy q The idea is simple; copy multiple data across different “zones”. q Example: The Ring in Open. Stack v Review: n Ring records the physical address of data. v When creating a ring, administrator must supply how many replicas through the zones, and the minimum interval of copying data in command. 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -12
 Data Ownership q Cloud service provider provides a free/non-free disk space and computing ability for users to handle the data. q After all, who owns the data? v Provider? n I provide the disk space!! v User? n 3/18/2018 I upload the data!! Cloud Operating System - Unit 12: Cloud Management U 12 -13
Data Ownership q Cloud service provider provides a free/non-free disk space and computing ability for users to handle the data. q After all, who owns the data? v Provider? n I provide the disk space!! v User? n 3/18/2018 I upload the data!! Cloud Operating System - Unit 12: Cloud Management U 12 -13
 Network Management Network is a fundamental part of Cloud Computing. q Network is an infrastructure which is q v easy to access v stable v high transfer rate v low latency for users. q Network in a cloud can be classified into two parts. v Internal network v External network 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -14
Network Management Network is a fundamental part of Cloud Computing. q Network is an infrastructure which is q v easy to access v stable v high transfer rate v low latency for users. q Network in a cloud can be classified into two parts. v Internal network v External network 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -14
 Open. Stack Nova-Network q Open. Stack network controller (nova-network) q The operations: v Allocate fixed IP addresses. v Configuring VLANs for projects. v Configuring networks for compute nodes. 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -15
Open. Stack Nova-Network q Open. Stack network controller (nova-network) q The operations: v Allocate fixed IP addresses. v Configuring VLANs for projects. v Configuring networks for compute nodes. 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -15
 Open. Stack Nova-Network - Concepts q Fixed IPs v An IP address will be assigned to an instance after instance creation. v The assigned IP will be remained until the instance is explicitly terminated. q Floating IPs v An IP address can be dynamically associated with an instance. v An IP address can be disassociated and associated with an instance at any time. 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -16
Open. Stack Nova-Network - Concepts q Fixed IPs v An IP address will be assigned to an instance after instance creation. v The assigned IP will be remained until the instance is explicitly terminated. q Floating IPs v An IP address can be dynamically associated with an instance. v An IP address can be disassociated and associated with an instance at any time. 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -16
 Fixed IPs Implementation (1) q There are three strategies available for implementing fixed IPs. v Flat Mode n The simplest networking mode. v Flat DHCP Mode n Similar to flat mode. v VLAN DHCP Mode n 3/18/2018 The default networking mode. Cloud Operating System - Unit 12: Cloud Management U 12 -17
Fixed IPs Implementation (1) q There are three strategies available for implementing fixed IPs. v Flat Mode n The simplest networking mode. v Flat DHCP Mode n Similar to flat mode. v VLAN DHCP Mode n 3/18/2018 The default networking mode. Cloud Operating System - Unit 12: Cloud Management U 12 -17
 Fixed IPs Implementation (2) v Flat Mode n n By default, all instances attach to the same bridge (br 100). Before the instance is booted, the network configuration will be injected into the instance. So far, this only works on linux-style systems. The network configuration is in /etc/networking/interfaces. v Flat DHCP Mode n n 3/18/2018 Nova will attempt to bridge into an ethernet device. A DHCP server (dnsmasq) will respond to instance’s dhcpdiscover operation. Cloud Operating System - Unit 12: Cloud Management U 12 -18
Fixed IPs Implementation (2) v Flat Mode n n By default, all instances attach to the same bridge (br 100). Before the instance is booted, the network configuration will be injected into the instance. So far, this only works on linux-style systems. The network configuration is in /etc/networking/interfaces. v Flat DHCP Mode n n 3/18/2018 Nova will attempt to bridge into an ethernet device. A DHCP server (dnsmasq) will respond to instance’s dhcpdiscover operation. Cloud Operating System - Unit 12: Cloud Management U 12 -18
 Fixed IPs Implementation (3) v VLAN DHCP Mode n n n 3/18/2018 Requires a switch which supports host-managed vlan tagging. A vlan will be created with a range of private ips. Cloudpipe helps user access the instances. Nova generates a key and certificate for user. One vpn per project. Illustration is shown in next page. Cloud Operating System - Unit 12: Cloud Management U 12 -19
Fixed IPs Implementation (3) v VLAN DHCP Mode n n n 3/18/2018 Requires a switch which supports host-managed vlan tagging. A vlan will be created with a range of private ips. Cloudpipe helps user access the instances. Nova generates a key and certificate for user. One vpn per project. Illustration is shown in next page. Cloud Operating System - Unit 12: Cloud Management U 12 -19
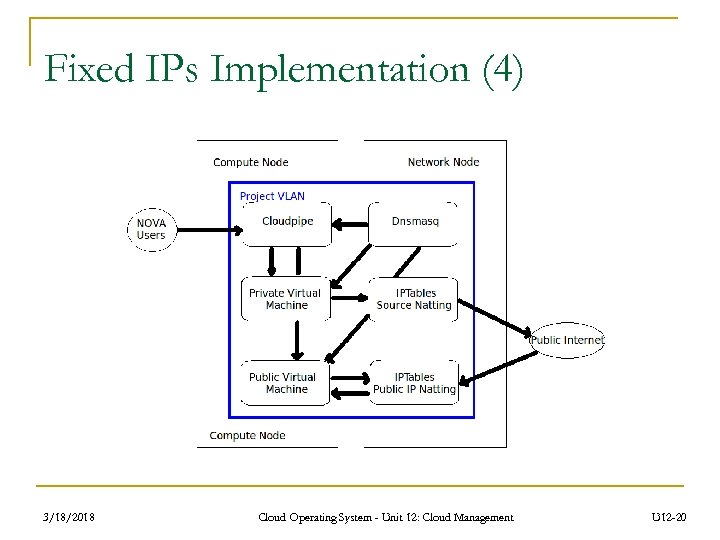 Fixed IPs Implementation (4) 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -20
Fixed IPs Implementation (4) 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -20
 Open. Stack Quantum (1) q Isolated from Nova to serve “Network Connectivity as a Service”. q Help user to establish their own network services. q Three components: v REST API Layer n Directly connect to Nova. v Authentication and Authorization Layer v Pluggable Backend 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -21
Open. Stack Quantum (1) q Isolated from Nova to serve “Network Connectivity as a Service”. q Help user to establish their own network services. q Three components: v REST API Layer n Directly connect to Nova. v Authentication and Authorization Layer v Pluggable Backend 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -21
 Open. Stack Quantum (2) q REST API Layer v Implement Quantum API and redirect API requests to where they should. q Authentication and Authorization Layer v Validate API requests and ensure them from the authorized users. q Pluggable Backend v Enhance REST API Layer. 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -22
Open. Stack Quantum (2) q REST API Layer v Implement Quantum API and redirect API requests to where they should. q Authentication and Authorization Layer v Validate API requests and ensure them from the authorized users. q Pluggable Backend v Enhance REST API Layer. 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -22
 Network Security q Even though it might be safe in the cloud, but the network is complicated. q The traditional methods still work for cloud. v Sniffer v ARP Poison v XSS v SQL Injection v etc. 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -23
Network Security q Even though it might be safe in the cloud, but the network is complicated. q The traditional methods still work for cloud. v Sniffer v ARP Poison v XSS v SQL Injection v etc. 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -23
 Summary q Users should confirm the agreement before using the service. q Quantum helps users to create the ideal network. 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -24
Summary q Users should confirm the agreement before using the service. q Quantum helps users to create the ideal network. 3/18/2018 Cloud Operating System - Unit 12: Cloud Management U 12 -24


