6e8339a859e7cd4282d24674287e5cbf.ppt
- Количество слайдов: 45
 Closing the Loop Towards a theory for High Confidence Cyber Physical Systems for Societal Systems Songhwai Oh (Seoul Natl. ), Saurabh Amin, Alvaro Cardenas (Fuji Res. ), Luca Schenato (Padova), Bruno Sinopoli (CMU), and Shankar Sastry University of California Berkeley CA 94720
Closing the Loop Towards a theory for High Confidence Cyber Physical Systems for Societal Systems Songhwai Oh (Seoul Natl. ), Saurabh Amin, Alvaro Cardenas (Fuji Res. ), Luca Schenato (Padova), Bruno Sinopoli (CMU), and Shankar Sastry University of California Berkeley CA 94720
 Outline • Tech Push and Applications Pull: instrumenting the World • Expanding the Vision: Heterogeneous Sensor Webs and Societal Scale Cyber Physical Systems • Closing the loop for Societal Scale Cyber Physical Systems (fault tolerant and robust) – Industrial Automation – Buildings • Trustworthy Cyber Physical Systems
Outline • Tech Push and Applications Pull: instrumenting the World • Expanding the Vision: Heterogeneous Sensor Webs and Societal Scale Cyber Physical Systems • Closing the loop for Societal Scale Cyber Physical Systems (fault tolerant and robust) – Industrial Automation – Buildings • Trustworthy Cyber Physical Systems
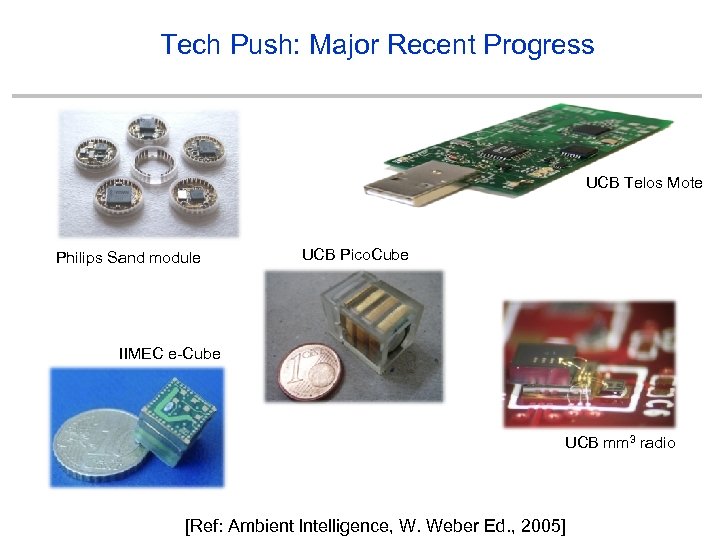 Tech Push: Major Recent Progress UCB Telos Mote Philips Sand module UCB Pico. Cube IIMEC e-Cube UCB mm 3 radio [Ref: Ambient Intelligence, W. Weber Ed. , 2005]
Tech Push: Major Recent Progress UCB Telos Mote Philips Sand module UCB Pico. Cube IIMEC e-Cube UCB mm 3 radio [Ref: Ambient Intelligence, W. Weber Ed. , 2005]
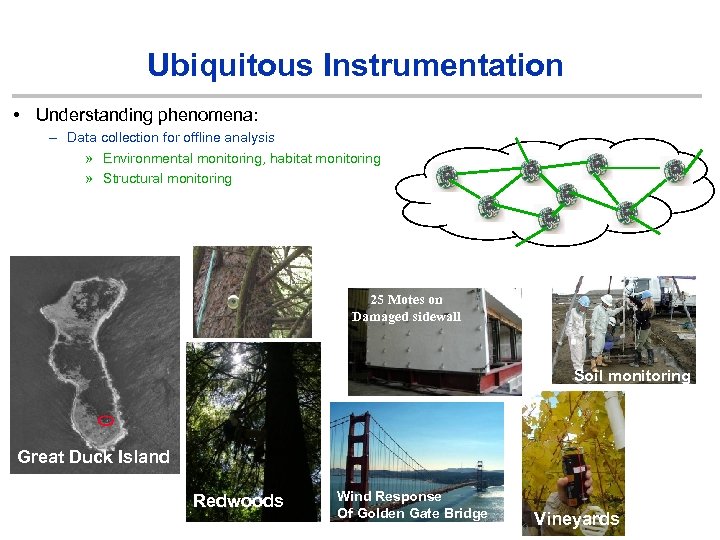 Ubiquitous Instrumentation • Understanding phenomena: – Data collection for offline analysis » Environmental monitoring, habitat monitoring » Structural monitoring 25 Motes on Damaged sidewall Soil monitoring Great Duck Island Redwoods Wind Response Of Golden Gate Bridge Vineyards
Ubiquitous Instrumentation • Understanding phenomena: – Data collection for offline analysis » Environmental monitoring, habitat monitoring » Structural monitoring 25 Motes on Damaged sidewall Soil monitoring Great Duck Island Redwoods Wind Response Of Golden Gate Bridge Vineyards
 Sensor Webs Everywhere • Understanding phenomena: – Data collection for offline analysis » Environmental monitoring, habitat monitoring » Structural monitoring • Detecting changes in the environment: – Thresholds, phase transitions, anomaly detection » Security systems, surveillance, health care » Wildfire detection » Fault detection, threat detection Intel Research Health Care Fire Response
Sensor Webs Everywhere • Understanding phenomena: – Data collection for offline analysis » Environmental monitoring, habitat monitoring » Structural monitoring • Detecting changes in the environment: – Thresholds, phase transitions, anomaly detection » Security systems, surveillance, health care » Wildfire detection » Fault detection, threat detection Intel Research Health Care Fire Response
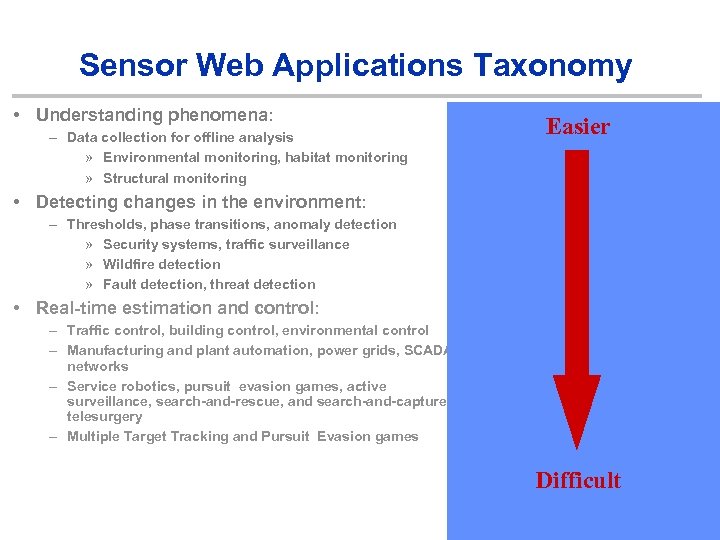 Sensor Web Applications Taxonomy • Understanding phenomena: – Data collection for offline analysis » Environmental monitoring, habitat monitoring » Structural monitoring • Detecting changes in the environment: Easier Building Comfort, Smart Alarms – Thresholds, phase transitions, anomaly detection » Security systems, traffic surveillance » Wildfire detection » Fault detection, threat detection • Real-time estimation and control: – Traffic control, building control, environmental control – Manufacturing and plant automation, power grids, SCADA networks – Service robotics, pursuit evasion games, active surveillance, search-and-rescue, and search-and-capture, telesurgery – Multiple Target Tracking and Pursuit Evasion games Difficult
Sensor Web Applications Taxonomy • Understanding phenomena: – Data collection for offline analysis » Environmental monitoring, habitat monitoring » Structural monitoring • Detecting changes in the environment: Easier Building Comfort, Smart Alarms – Thresholds, phase transitions, anomaly detection » Security systems, traffic surveillance » Wildfire detection » Fault detection, threat detection • Real-time estimation and control: – Traffic control, building control, environmental control – Manufacturing and plant automation, power grids, SCADA networks – Service robotics, pursuit evasion games, active surveillance, search-and-rescue, and search-and-capture, telesurgery – Multiple Target Tracking and Pursuit Evasion games Difficult
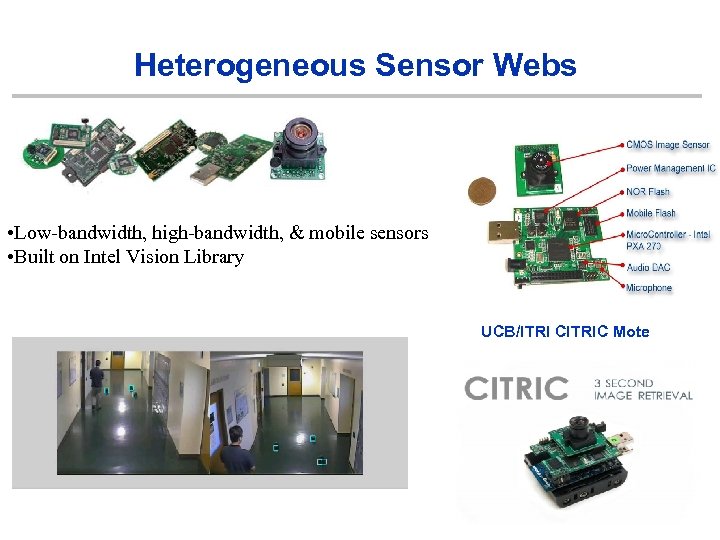 Heterogeneous Sensor Webs • Low-bandwidth, high-bandwidth, & mobile sensors • Built on Intel Vision Library UCB/ITRI CITRIC Mote
Heterogeneous Sensor Webs • Low-bandwidth, high-bandwidth, & mobile sensors • Built on Intel Vision Library UCB/ITRI CITRIC Mote
 Major Progress but True Immersion not yet in Reach Artificial Skin Smart Objects Interactive Surfaces “Microscopic” Health Monitoring Courtesy of Jan Rabaey
Major Progress but True Immersion not yet in Reach Artificial Skin Smart Objects Interactive Surfaces “Microscopic” Health Monitoring Courtesy of Jan Rabaey
 “Societal Scale Cyber Physical Systems ” • Characteristics – Ubiquitous, Pervasive, Disappearing, Perceptive, Ambient – Always Connectable, Reliable, Scalable, Adaptive, Flexible • The Emerging Service Models – Intelligent data access and extraction – Immersion-based work and play – Environmental control, energy management and safety in “highperformance” homes – Automotive and avionic safety and control – Management of metropolitan traffic flows – Distributed health monitoring – Power distribution with decentralized energy generation
“Societal Scale Cyber Physical Systems ” • Characteristics – Ubiquitous, Pervasive, Disappearing, Perceptive, Ambient – Always Connectable, Reliable, Scalable, Adaptive, Flexible • The Emerging Service Models – Intelligent data access and extraction – Immersion-based work and play – Environmental control, energy management and safety in “highperformance” homes – Automotive and avionic safety and control – Management of metropolitan traffic flows – Distributed health monitoring – Power distribution with decentralized energy generation
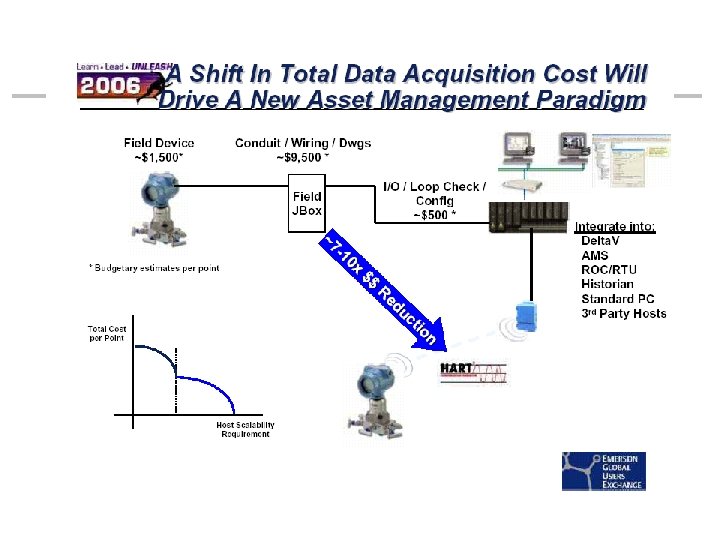
 Industrial Automation • Motivation: Cost reduction – More than 85% reduction in cost compared to wired systems (case study by Emerson) – SCADA (Supervisory Control And Data Acquisition) • Reliability is the number one issue – Robust estimation: Estimation of parameters of interest from noisy measurements with high fidelity in the presence of unreliable communication – Real-time control: A must for missioncritical systems
Industrial Automation • Motivation: Cost reduction – More than 85% reduction in cost compared to wired systems (case study by Emerson) – SCADA (Supervisory Control And Data Acquisition) • Reliability is the number one issue – Robust estimation: Estimation of parameters of interest from noisy measurements with high fidelity in the presence of unreliable communication – Real-time control: A must for missioncritical systems

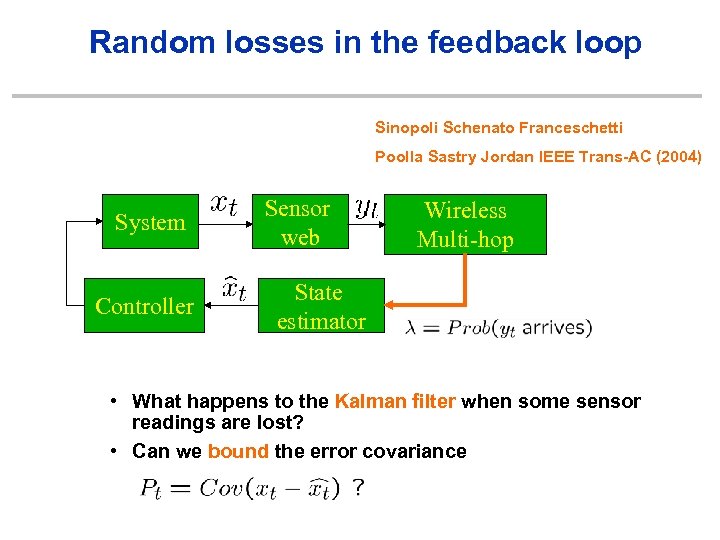 Random losses in the feedback loop Sinopoli Schenato Franceschetti Poolla Sastry Jordan IEEE Trans-AC (2004) System Controller Sensor web Wireless Multi-hop State estimator • What happens to the Kalman filter when some sensor readings are lost? • Can we bound the error covariance
Random losses in the feedback loop Sinopoli Schenato Franceschetti Poolla Sastry Jordan IEEE Trans-AC (2004) System Controller Sensor web Wireless Multi-hop State estimator • What happens to the Kalman filter when some sensor readings are lost? • Can we bound the error covariance
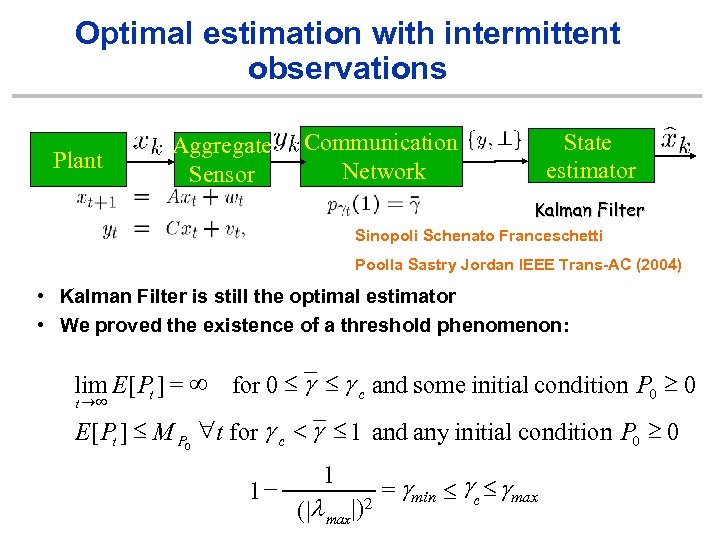 Optimal estimation with intermittent observations Plant Aggregate Sensor State estimator Communication Network Kalman Filter Sinopoli Schenato Franceschetti Poolla Sastry Jordan IEEE Trans-AC (2004) • Kalman Filter is still the optimal estimator • We proved the existence of a threshold phenomenon: lim E[ Pt ] = ¥ for 0 £ g c and some initial condition P 0 ³ 0 t ®¥ E[ Pt ] £ M P 0 "t for g c < g £ 1 and any initial condition P 0 ³ 0 1 - 1 ( |l max|)2 = gmin £ gc £ gmax
Optimal estimation with intermittent observations Plant Aggregate Sensor State estimator Communication Network Kalman Filter Sinopoli Schenato Franceschetti Poolla Sastry Jordan IEEE Trans-AC (2004) • Kalman Filter is still the optimal estimator • We proved the existence of a threshold phenomenon: lim E[ Pt ] = ¥ for 0 £ g c and some initial condition P 0 ³ 0 t ®¥ E[ Pt ] £ M P 0 "t for g c < g £ 1 and any initial condition P 0 ³ 0 1 - 1 ( |l max|)2 = gmin £ gc £ gmax
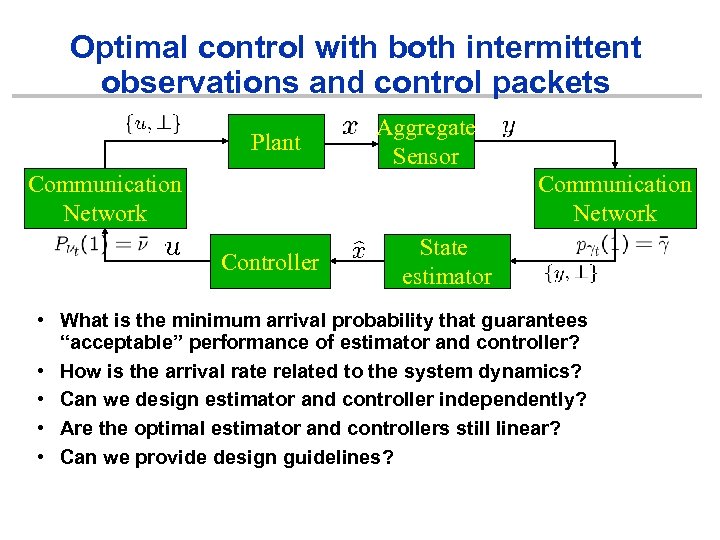 Optimal control with both intermittent observations and control packets Plant Aggregate Sensor Communication Network Controller State estimator • What is the minimum arrival probability that guarantees “acceptable” performance of estimator and controller? • How is the arrival rate related to the system dynamics? • Can we design estimator and controller independently? • Are the optimal estimator and controllers still linear? • Can we provide design guidelines?
Optimal control with both intermittent observations and control packets Plant Aggregate Sensor Communication Network Controller State estimator • What is the minimum arrival probability that guarantees “acceptable” performance of estimator and controller? • How is the arrival rate related to the system dynamics? • Can we design estimator and controller independently? • Are the optimal estimator and controllers still linear? • Can we provide design guidelines?
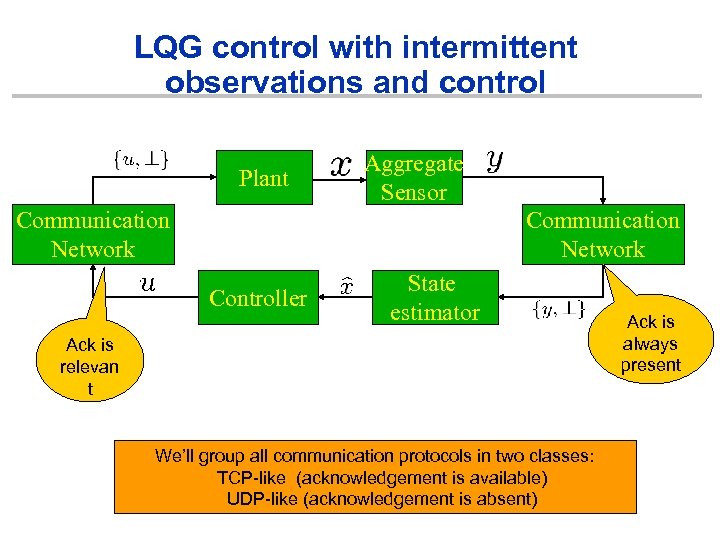 LQG control with intermittent observations and control Plant Aggregate Sensor Communication Network Controller State estimator Ack is relevan t We’ll group all communication protocols in two classes: TCP-like (acknowledgement is available) UDP-like (acknowledgement is absent) Ack is always present
LQG control with intermittent observations and control Plant Aggregate Sensor Communication Network Controller State estimator Ack is relevan t We’ll group all communication protocols in two classes: TCP-like (acknowledgement is available) UDP-like (acknowledgement is absent) Ack is always present
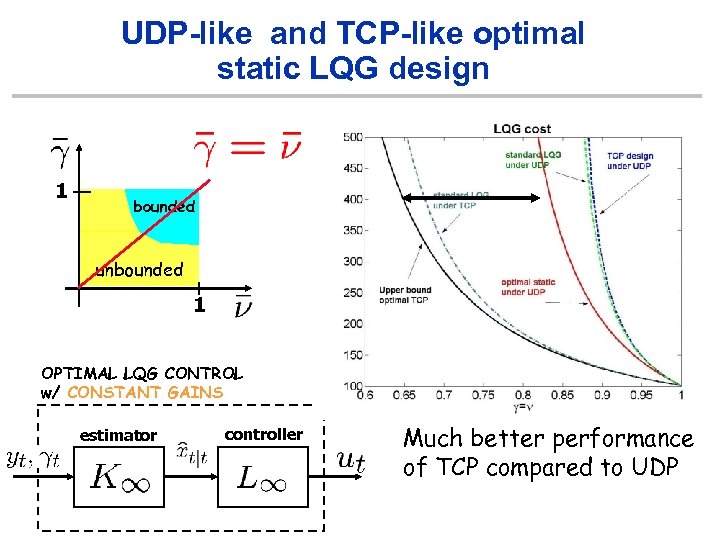 UDP-like and TCP-like optimal static LQG design 1 bounded unbounded 1 OPTIMAL LQG CONTROL w/ CONSTANT GAINS estimator controller Much better performance of TCP compared to UDP
UDP-like and TCP-like optimal static LQG design 1 bounded unbounded 1 OPTIMAL LQG CONTROL w/ CONSTANT GAINS estimator controller Much better performance of TCP compared to UDP
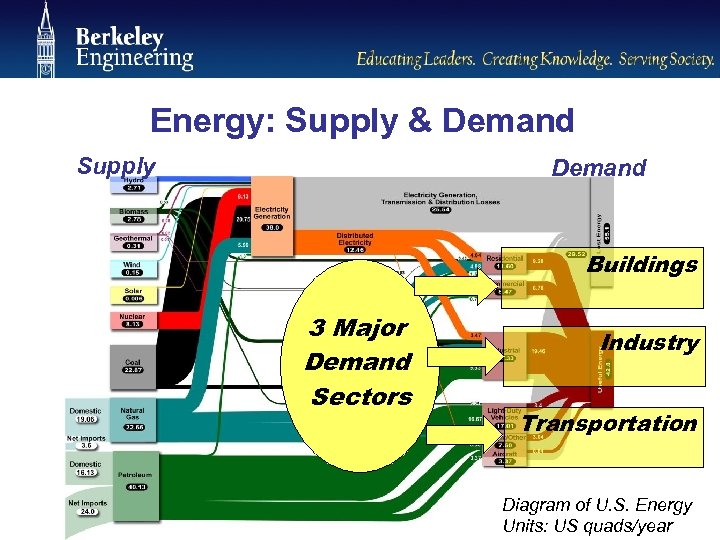 Energy: Supply & Demand Supply Demand Buildings 3 Major Demand Sectors Industry Transportation Diagram of U. S. Energy Units: US quads/year
Energy: Supply & Demand Supply Demand Buildings 3 Major Demand Sectors Industry Transportation Diagram of U. S. Energy Units: US quads/year
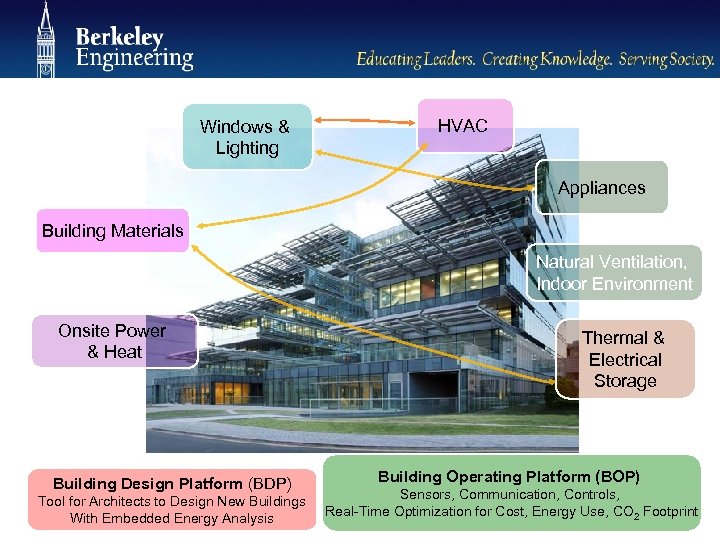 Windows & Lighting HVAC Appliances Building Materials Natural Ventilation, Indoor Environment Onsite Power & Heat Building Design Platform (BDP) Tool for Architects to Design New Buildings With Embedded Energy Analysis Thermal & Electrical Storage Building Operating Platform (BOP) Sensors, Communication, Controls, Real-Time Optimization for Cost, Energy Use, CO 2 Footprint
Windows & Lighting HVAC Appliances Building Materials Natural Ventilation, Indoor Environment Onsite Power & Heat Building Design Platform (BDP) Tool for Architects to Design New Buildings With Embedded Energy Analysis Thermal & Electrical Storage Building Operating Platform (BOP) Sensors, Communication, Controls, Real-Time Optimization for Cost, Energy Use, CO 2 Footprint
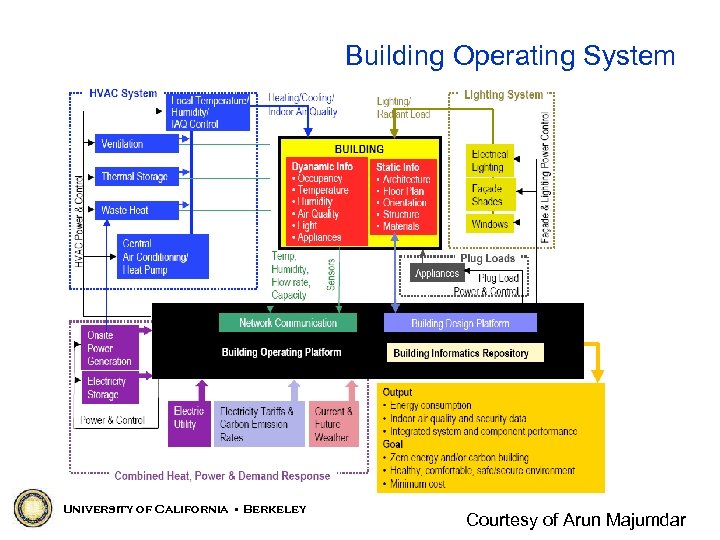 Building Operating System University of California • Berkeley Courtesy of Arun Majumdar
Building Operating System University of California • Berkeley Courtesy of Arun Majumdar
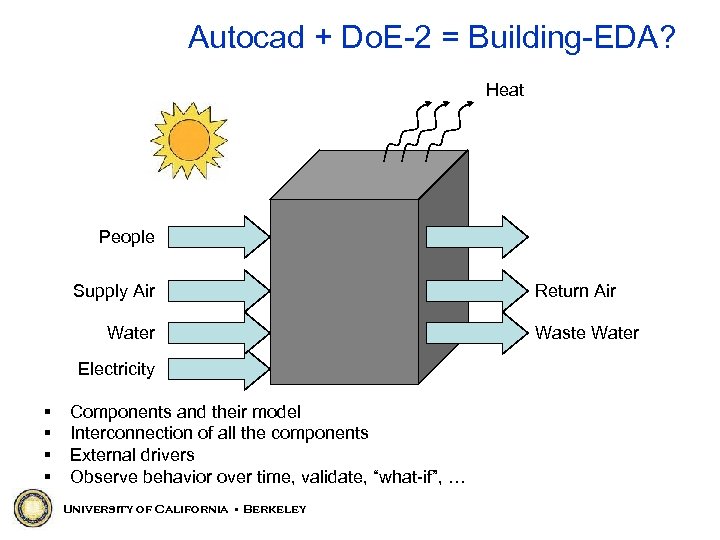 Autocad + Do. E-2 = Building-EDA? Heat People Supply Air Water Electricity § § Components and their model Interconnection of all the components External drivers Observe behavior over time, validate, “what-if”, … University of California • Berkeley Return Air Waste Water
Autocad + Do. E-2 = Building-EDA? Heat People Supply Air Water Electricity § § Components and their model Interconnection of all the components External drivers Observe behavior over time, validate, “what-if”, … University of California • Berkeley Return Air Waste Water
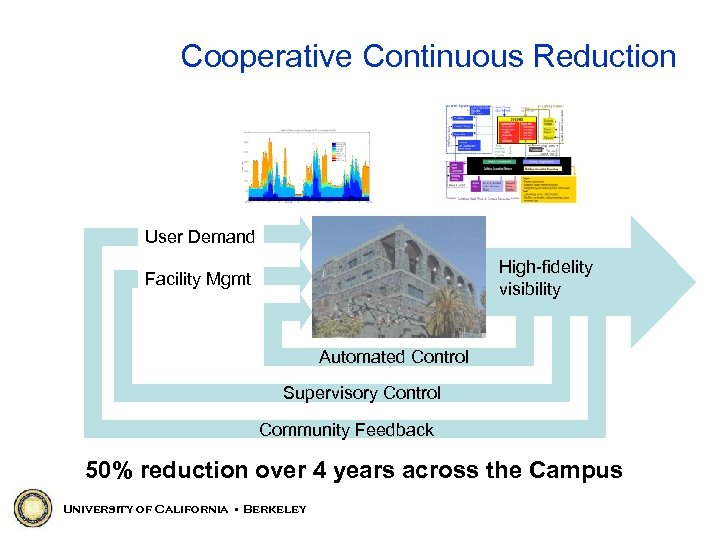 Cooperative Continuous Reduction User Demand High-fidelity visibility Facility Mgmt Automated Control Supervisory Control Community Feedback 50% reduction over 4 years across the Campus University of California • Berkeley
Cooperative Continuous Reduction User Demand High-fidelity visibility Facility Mgmt Automated Control Supervisory Control Community Feedback 50% reduction over 4 years across the Campus University of California • Berkeley
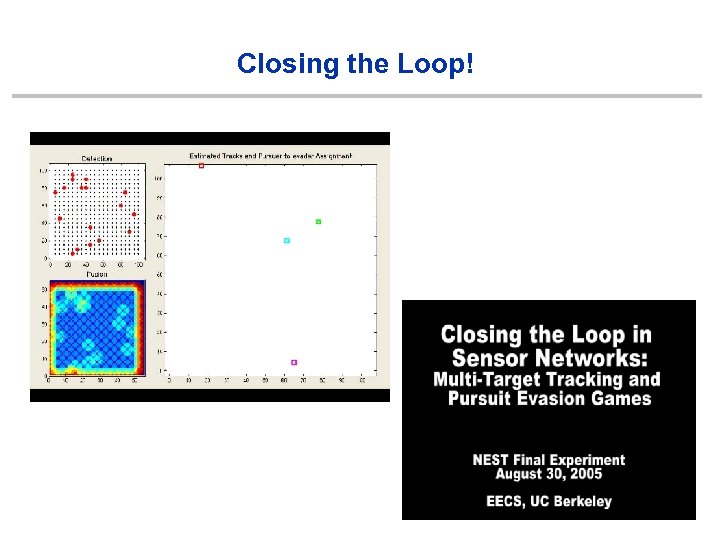 Closing the Loop!
Closing the Loop!
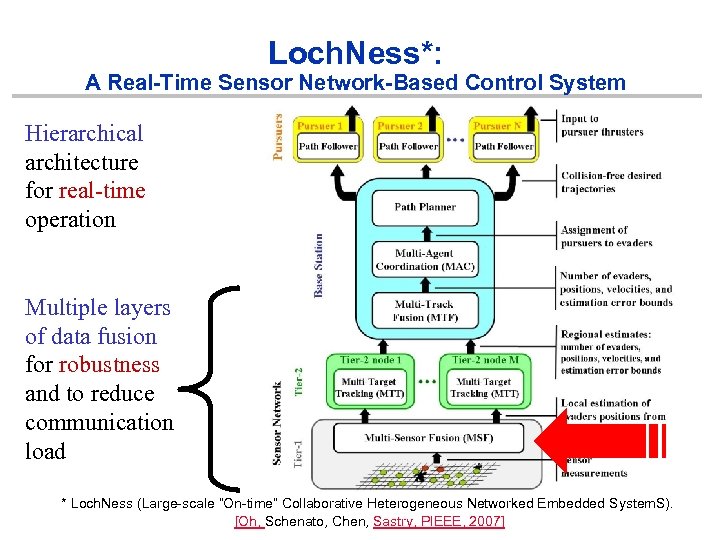 Loch. Ness*: A Real-Time Sensor Network-Based Control System Hierarchical architecture for real-time operation Multiple layers of data fusion for robustness and to reduce communication load * Loch. Ness (Large-scale “On-time” Collaborative Heterogeneous Networked Embedded System. S). [Oh, Schenato, Chen, Sastry, PIEEE, 2007]
Loch. Ness*: A Real-Time Sensor Network-Based Control System Hierarchical architecture for real-time operation Multiple layers of data fusion for robustness and to reduce communication load * Loch. Ness (Large-scale “On-time” Collaborative Heterogeneous Networked Embedded System. S). [Oh, Schenato, Chen, Sastry, PIEEE, 2007]
 Multi-Target Tracking (MTT) Problem • Given – – Multiple dynamics and measurement models Sensor and clutter (false alarms) models Target appearance and disappearance models Set of noisy unlabeled observations Y • Find – Number of targets – States of all targets • Requires solutions to both – Data association – State estimation Joint Work with Songhwai Oh and Stuart Russell
Multi-Target Tracking (MTT) Problem • Given – – Multiple dynamics and measurement models Sensor and clutter (false alarms) models Target appearance and disappearance models Set of noisy unlabeled observations Y • Find – Number of targets – States of all targets • Requires solutions to both – Data association – State estimation Joint Work with Songhwai Oh and Stuart Russell
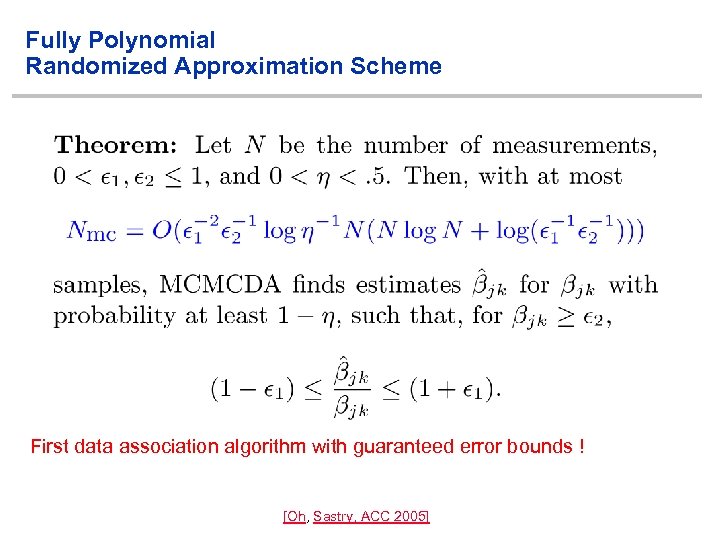 Fully Polynomial Randomized Approximation Scheme First data association algorithm with guaranteed error bounds ! [Oh, Sastry, ACC 2005]
Fully Polynomial Randomized Approximation Scheme First data association algorithm with guaranteed error bounds ! [Oh, Sastry, ACC 2005]
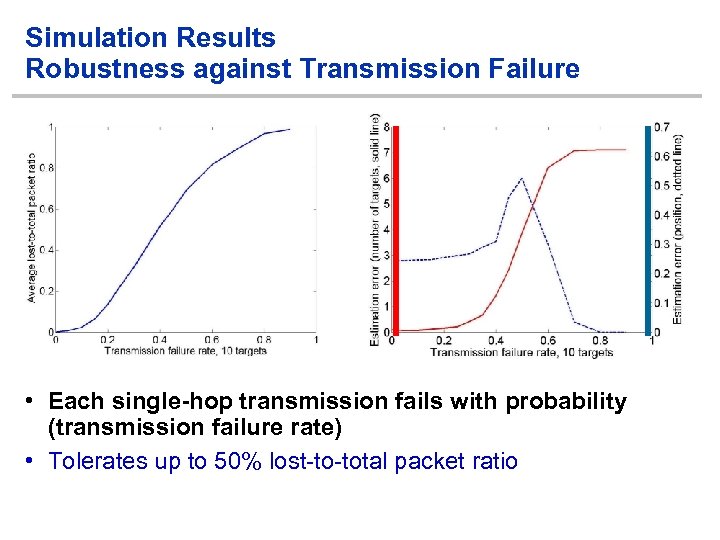 Simulation Results Robustness against Transmission Failure • Each single-hop transmission fails with probability (transmission failure rate) • Tolerates up to 50% lost-to-total packet ratio
Simulation Results Robustness against Transmission Failure • Each single-hop transmission fails with probability (transmission failure rate) • Tolerates up to 50% lost-to-total packet ratio
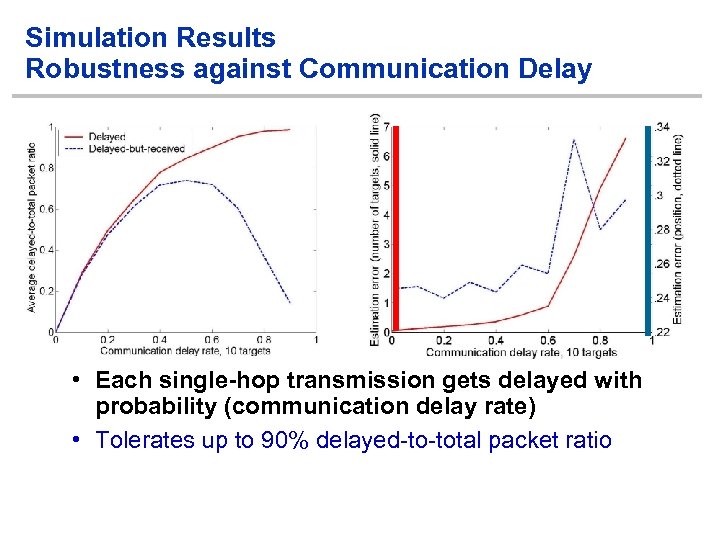 Simulation Results Robustness against Communication Delay • Each single-hop transmission gets delayed with probability (communication delay rate) • Tolerates up to 90% delayed-to-total packet ratio
Simulation Results Robustness against Communication Delay • Each single-hop transmission gets delayed with probability (communication delay rate) • Tolerates up to 90% delayed-to-total packet ratio
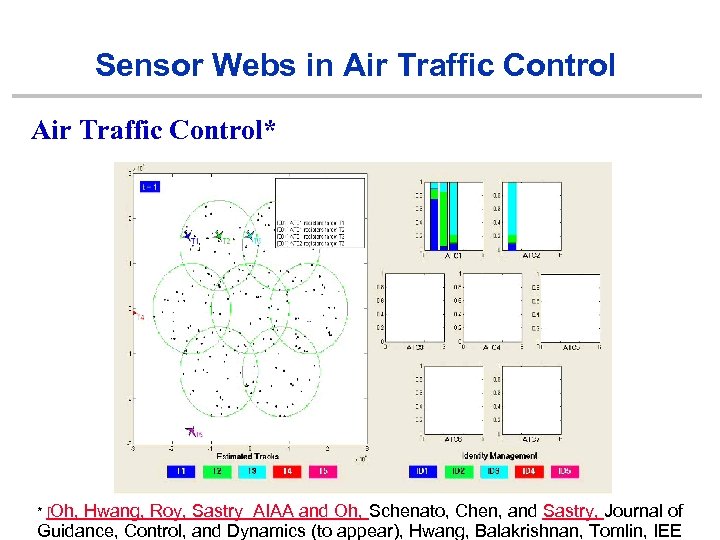 Sensor Webs in Air Traffic Control* * [Oh, Hwang, Roy, Sastry AIAA and Oh, Schenato, Chen, and Sastry, Journal of Guidance, Control, and Dynamics (to appear), Hwang, Balakrishnan, Tomlin, IEE
Sensor Webs in Air Traffic Control* * [Oh, Hwang, Roy, Sastry AIAA and Oh, Schenato, Chen, and Sastry, Journal of Guidance, Control, and Dynamics (to appear), Hwang, Balakrishnan, Tomlin, IEE
 Vulnerabilities of Cyber-physical systems • • Controllers are computers Networked Commodity IT solutions New functionalities (smart infrastructures) Many devices (sensor webs) Highly skilled IT global workforce (creating attacks is easier) Cybercrime Jt work with Saurabh Amin and Alvaro Cardenas
Vulnerabilities of Cyber-physical systems • • Controllers are computers Networked Commodity IT solutions New functionalities (smart infrastructures) Many devices (sensor webs) Highly skilled IT global workforce (creating attacks is easier) Cybercrime Jt work with Saurabh Amin and Alvaro Cardenas
 Vulnerabilities can be Exploited 2008 Huntington Beach offshore oil platforms 2007 Tehama-Colusa Canal 2000 Maroochy Shire sewage control system. 2007 Cal-ISO power marketing operations
Vulnerabilities can be Exploited 2008 Huntington Beach offshore oil platforms 2007 Tehama-Colusa Canal 2000 Maroochy Shire sewage control system. 2007 Cal-ISO power marketing operations
 Vulnerabilities can be Exploited
Vulnerabilities can be Exploited
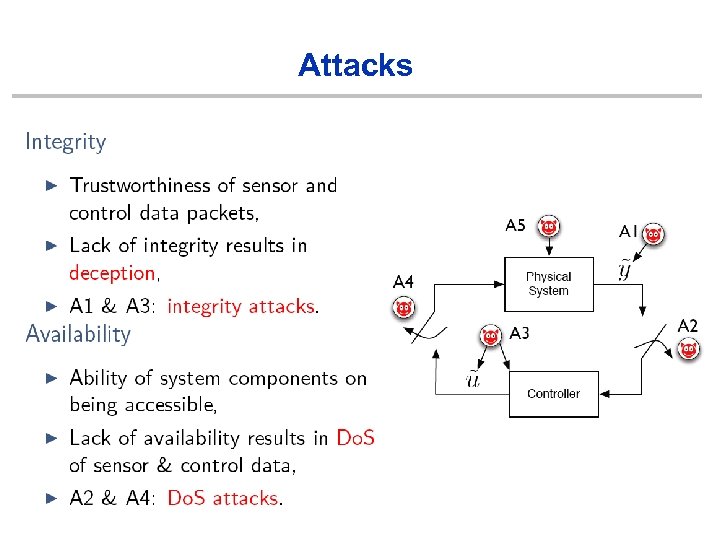 Attacks
Attacks
 Secure Control: What is New and Fundamentally Different? • • So security is important; but are there new research problems, or can problems be solved with – – Traditional IT security? Fault-tolerant control? Trust and Adversary Model Prevention – Authentication, access control, software security, trusted computing, white listing • Detection – Intrusion detection systems, anomaly detection • Resiliency – Separation of duty, least privilege principle
Secure Control: What is New and Fundamentally Different? • • So security is important; but are there new research problems, or can problems be solved with – – Traditional IT security? Fault-tolerant control? Trust and Adversary Model Prevention – Authentication, access control, software security, trusted computing, white listing • Detection – Intrusion detection systems, anomaly detection • Resiliency – Separation of duty, least privilege principle
 CPS Security vs. Traditional Security • • What is new and fundamentally different in control systems security? – Model interaction with the physical world By modeling the interaction with the physical world we can obtain 3 new research directions – – – Threat assessment: how attacker may manipulate control variables to achieve goals and study consequences to the physical system Attack-detection by using models of the physical system: Study stealthy attacks (undetected attacks), Ensure safety of any automated response mechanism Attack-resilient control algorithms
CPS Security vs. Traditional Security • • What is new and fundamentally different in control systems security? – Model interaction with the physical world By modeling the interaction with the physical world we can obtain 3 new research directions – – – Threat assessment: how attacker may manipulate control variables to achieve goals and study consequences to the physical system Attack-detection by using models of the physical system: Study stealthy attacks (undetected attacks), Ensure safety of any automated response mechanism Attack-resilient control algorithms
 Our Results in these 3 New Research Topics • • • Threat assessment of control systems – – Ad Hoc Networks 2009 Journal of Critical Infrastructure Protection 2009 Detecting attacks to control systems – – Work in progress Power grid, chemical reactor etc. Resilient control algorithms – HSCC 2009 We focus on “Detection” in the remaining part of this presentation
Our Results in these 3 New Research Topics • • • Threat assessment of control systems – – Ad Hoc Networks 2009 Journal of Critical Infrastructure Protection 2009 Detecting attacks to control systems – – Work in progress Power grid, chemical reactor etc. Resilient control algorithms – HSCC 2009 We focus on “Detection” in the remaining part of this presentation
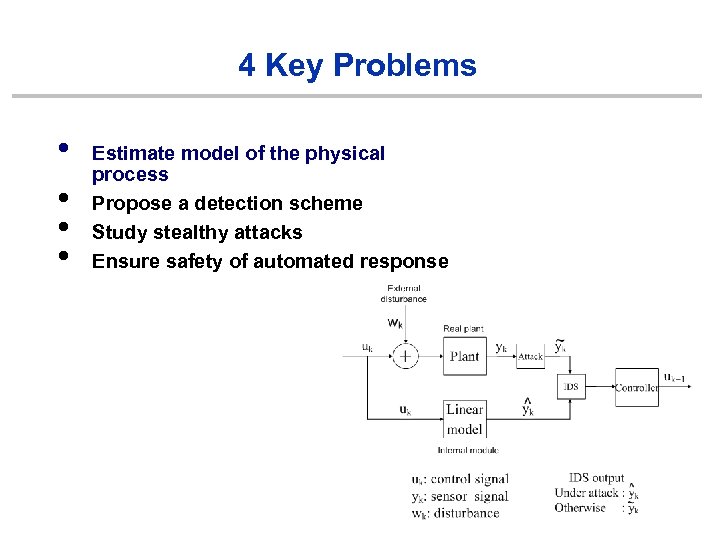 4 Key Problems • • Estimate model of the physical process Propose a detection scheme Study stealthy attacks Ensure safety of automated response
4 Key Problems • • Estimate model of the physical process Propose a detection scheme Study stealthy attacks Ensure safety of automated response
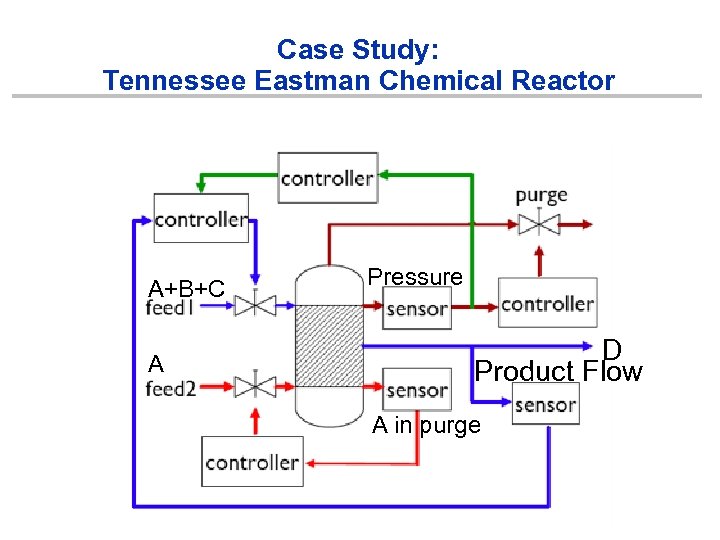 Case Study: Tennessee Eastman Chemical Reactor A+B+C A Pressure D Product Flow A in purge
Case Study: Tennessee Eastman Chemical Reactor A+B+C A Pressure D Product Flow A in purge
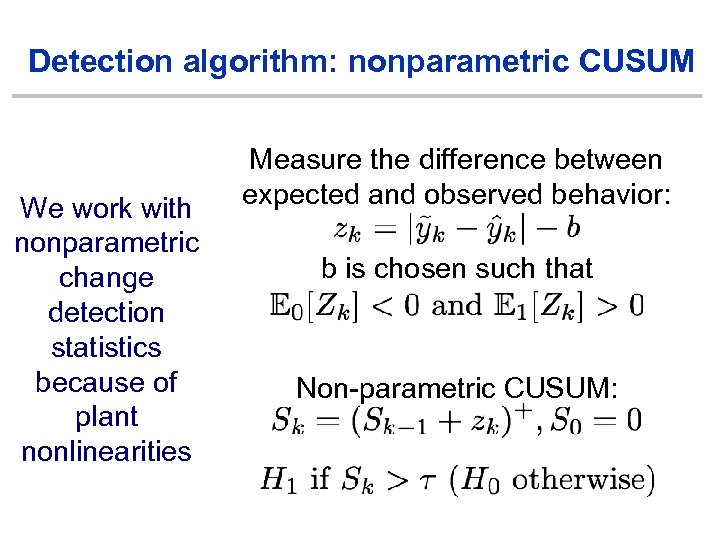 Detection algorithm: nonparametric CUSUM We work with nonparametric change detection statistics because of plant nonlinearities Measure the difference between expected and observed behavior: b is chosen such that Non-parametric CUSUM:
Detection algorithm: nonparametric CUSUM We work with nonparametric change detection statistics because of plant nonlinearities Measure the difference between expected and observed behavior: b is chosen such that Non-parametric CUSUM:
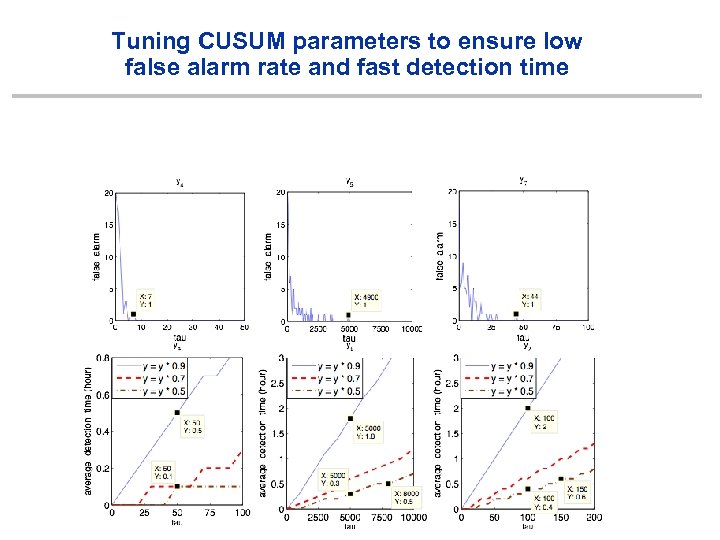 Tuning CUSUM parameters to ensure low false alarm rate and fast detection time
Tuning CUSUM parameters to ensure low false alarm rate and fast detection time
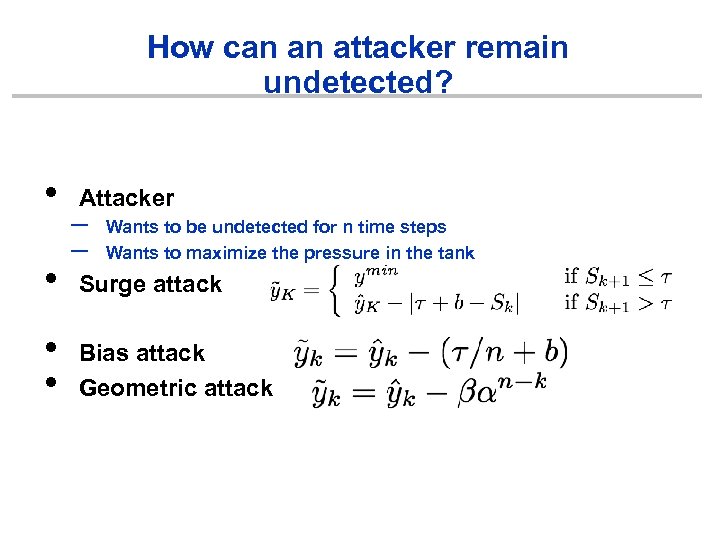 How can an attacker remain undetected? • • Attacker – – Wants to be undetected for n time steps Wants to maximize the pressure in the tank Surge attack Bias attack Geometric attack
How can an attacker remain undetected? • • Attacker – – Wants to be undetected for n time steps Wants to maximize the pressure in the tank Surge attack Bias attack Geometric attack
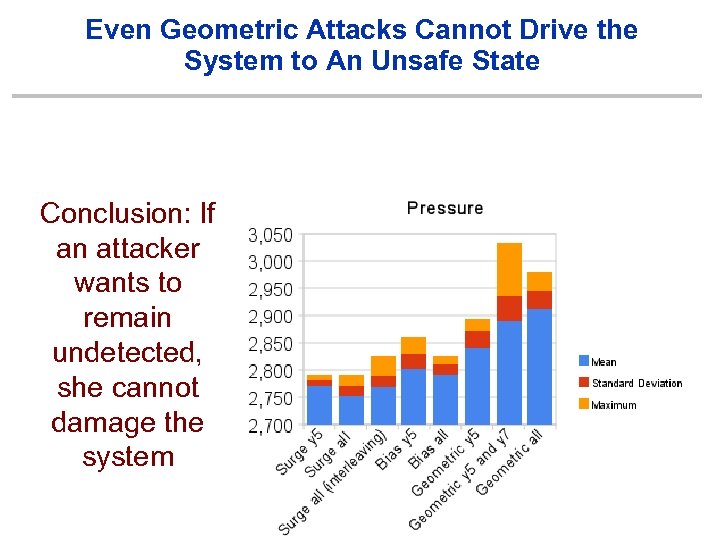 Even Geometric Attacks Cannot Drive the System to An Unsafe State Conclusion: If an attacker wants to remain undetected, she cannot damage the system
Even Geometric Attacks Cannot Drive the System to An Unsafe State Conclusion: If an attacker wants to remain undetected, she cannot damage the system
 Do. S Attack Signatures for Secure Control Problem
Do. S Attack Signatures for Secure Control Problem
 Key Ideas from Robust Control
Key Ideas from Robust Control
 High Confidence CPS Systems: Research Taxonomy • Robust Inferencing for Control • Closing the Loop with fault tolerant networked control systems • Effects of Mobility on Loop Closure • Graceful Degradation Under Attack: Trustworthy systems • Key Applications – Process Control and SCADA systems – Action Webs for Energy Efficient Buildings
High Confidence CPS Systems: Research Taxonomy • Robust Inferencing for Control • Closing the Loop with fault tolerant networked control systems • Effects of Mobility on Loop Closure • Graceful Degradation Under Attack: Trustworthy systems • Key Applications – Process Control and SCADA systems – Action Webs for Energy Efficient Buildings


