6efd42947f322ad509ae580f7d7b81f8.ppt
- Количество слайдов: 36

Clearswift Overview

Rise of new collaboration tools grow businesses There is no doubt that the emergence of Web 2. 0 technologies… is changing the way that all organizations do business…. At T-Mobile we make use of Facebook, for example, to aid our graduate recruitment process. As an organization, we need to ensure that as such technologies develop we fully understand the potential and the impact on our business Head of HR Operations, T-Mobile “ “
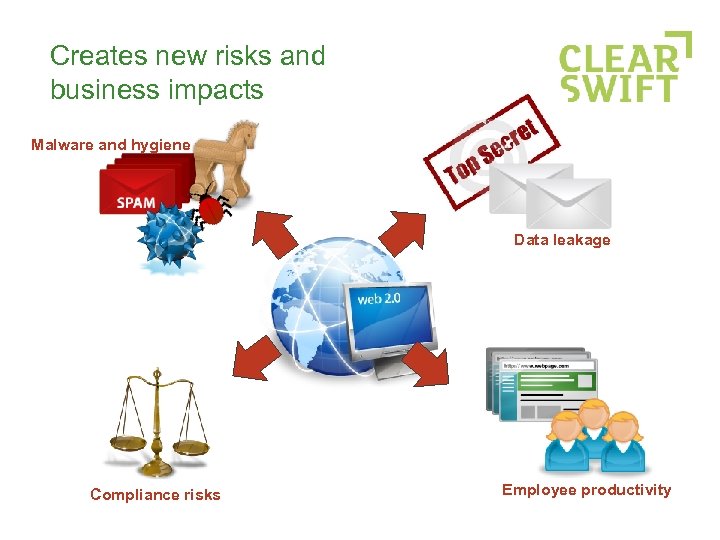
Creates new risks and business impacts Malware and hygiene Data leakage Compliance risks Employee productivity

What if you could embrace collaboration and… ü ü Stay in control of intellectual property and customer sensitive data? Stop dangerous security threats and malware? Monitor and log communications for compliance and productivity? Reduce the cost of securing collaboration?

With Clearswift you can collaborate more • • • Fewer products to manage Less time in training Less time on the phone with support configure flexible and policies that With Clearswift’s. I MIMEsweeper we canproduct that can do thetailor-made such little fit our company. don't know any other same with effort. " “ “ Less costs – hardware, licensing, resources and support Less risks

About Clearswift ü ü ü We’re different because we start by understanding content 20+ years helping companies collaborate confidently Trusted by over 17, 000 organizations Used by 40% of the Global Fortune 500 97% of customers would recommend us to a peer

Clearswift Email & Web Appliance
Designed for the job • Secure and resilient platform – optimized OS tuned for high throughput performance – hardened Linux kernel – Builtin Kaspersky AV • Easy installation and deployment – 7 -step ‘Getting Started’ deployment & installation guide – pre-loaded and configured ‘default’ policy • Easy to use & manage – 100% web user interface – simple to use policy model – Automation to reduce admin effort
Deployment platforms 1) HW Appliance 2) SW Appliance 3) Virtual Appliance y Hyper. V • Customers can re-use existing hardware to save buying a new devices • Customer can virtualize all or part of their solution • Customers can mix and match deployments to suit them
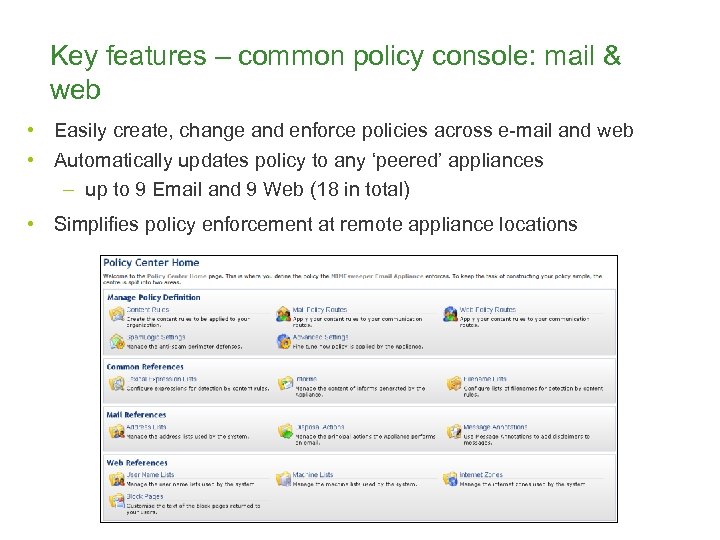
Key features – common policy console: mail & web • Easily create, change and enforce policies across e-mail and web • Automatically updates policy to any ‘peered’ appliances – up to 9 Email and 9 Web (18 in total) • Simplifies policy enforcement at remote appliance locations
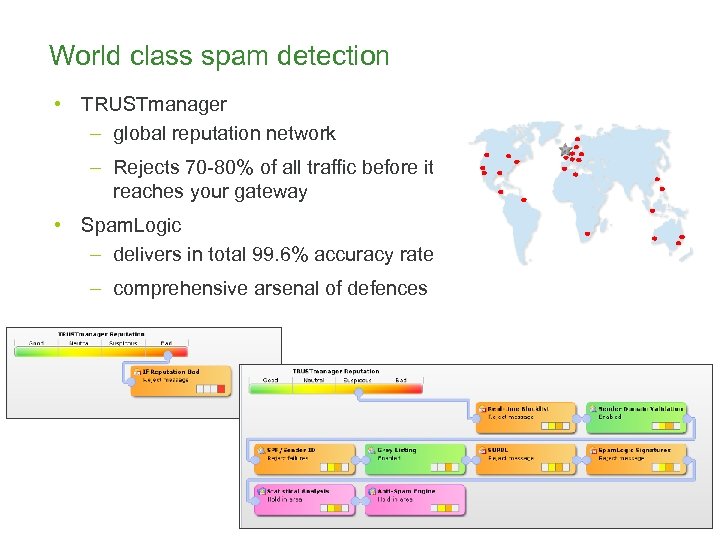
World class spam detection • TRUSTmanager – global reputation network – Rejects 70 -80% of all traffic before it reaches your gateway • Spam. Logic – delivers in total 99. 6% accuracy rate – comprehensive arsenal of defences
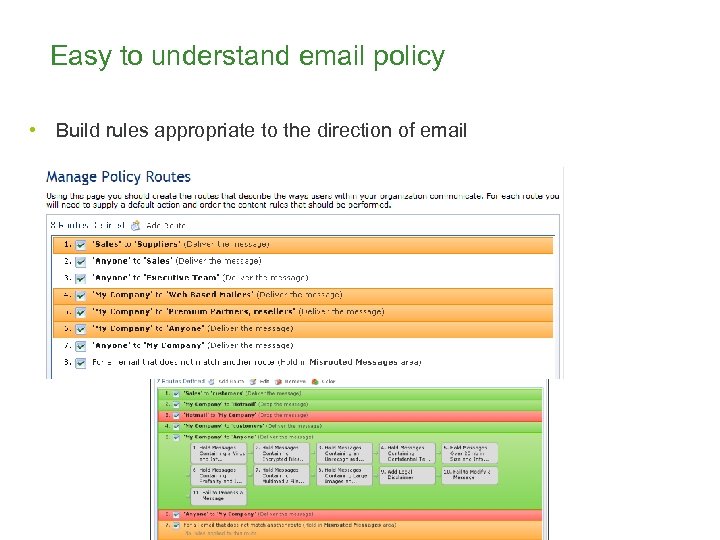
Easy to understand email policy • Build rules appropriate to the direction of email

Superior web security without compromise MIMEsweeper content engine – True binary signature file identification – Recursive decomposition – Lexical analysis/templates – Granular policy based on user – Comprehensive data leakage controls URL filtering from the leading vendor – 40 categories more than 18 million web sites – Important component for policy and reporting Anti-virus from Kaspersky – Viruses, worms, Trojans and malicious code Anti-spyware from Sunbelt Software – Signature based detection and prevention – Spyware “call home” prevention – Tracking Cookie detection/removal
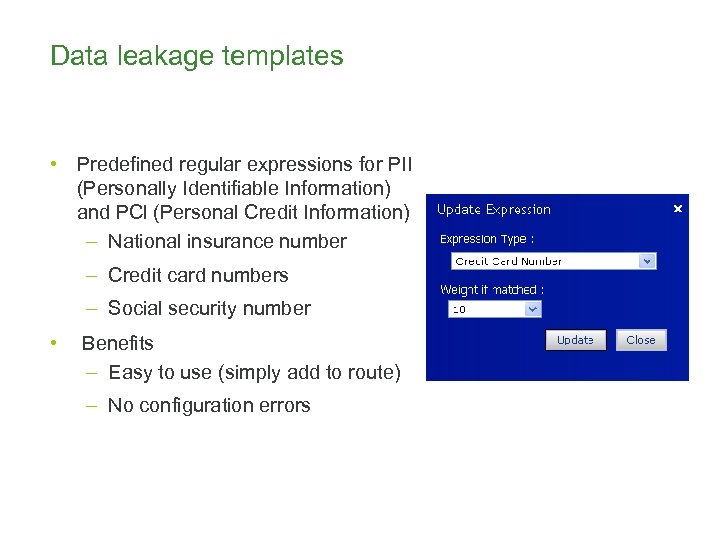
Data leakage templates • Predefined regular expressions for PII (Personally Identifiable Information) and PCl (Personal Credit Information) – National insurance number – Credit card numbers – Social security number • Benefits – Easy to use (simply add to route) – No configuration errors

Time based policy In the example for the ‘Everyone to Shopping’ route shown previously – The green area defines when access to this route is allowed – The White area defines when it is blocked – The orange area defines a period with 60 minutes browse time quota – On Saturday the Blue are defines a period with 30 minutes time quota
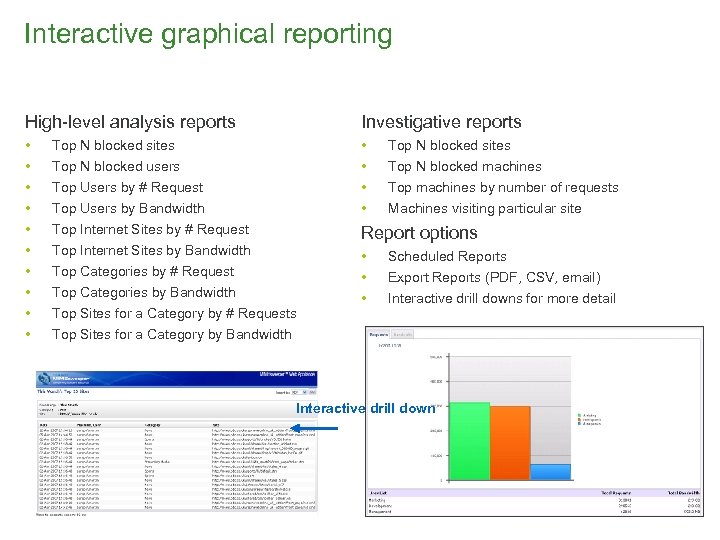
Interactive graphical reporting High-level analysis reports Investigative reports • • • • Top N blocked sites Top N blocked users Top Users by # Request Top Users by Bandwidth Top Internet Sites by # Request Top Internet Sites by Bandwidth Top Categories by # Request Top Categories by Bandwidth Top Sites for a Category by # Requests Top Sites for a Category by Bandwidth Top N blocked sites Top N blocked machines Top machines by number of requests Machines visiting particular site Report options • • • Scheduled Reports Export Reports (PDF, CSV, email) Interactive drill downs for more detail Interactive drill down
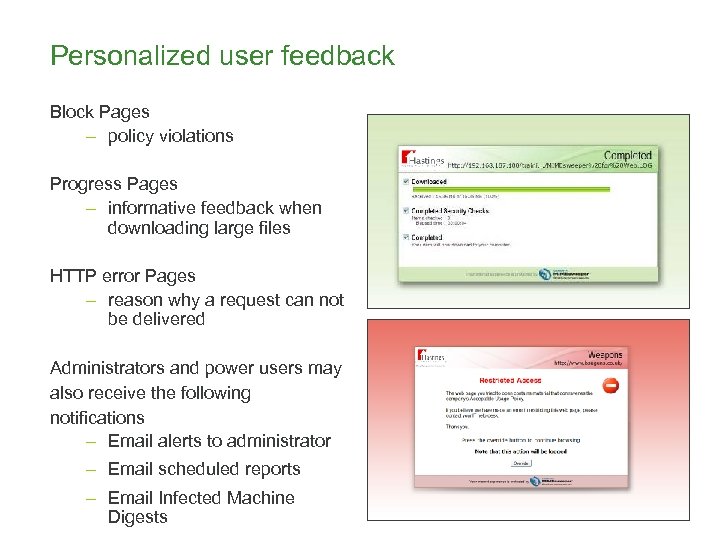
Personalized user feedback Block Pages – policy violations Progress Pages – informative feedback when downloading large files HTTP error Pages – reason why a request can not be delivered Administrators and power users may also receive the following notifications – Email alerts to administrator – Email scheduled reports – Email Infected Machine Digests
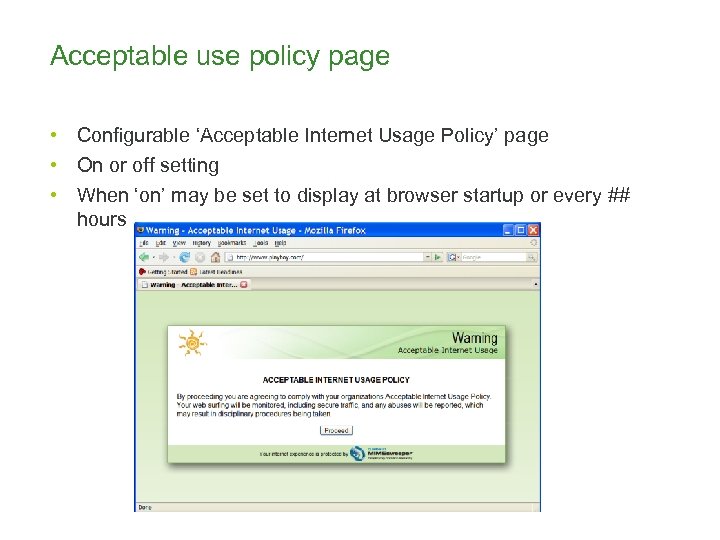
Acceptable use policy page • Configurable ‘Acceptable Internet Usage Policy’ page • On or off setting • When ‘on’ may be set to display at browser startup or every ## hours
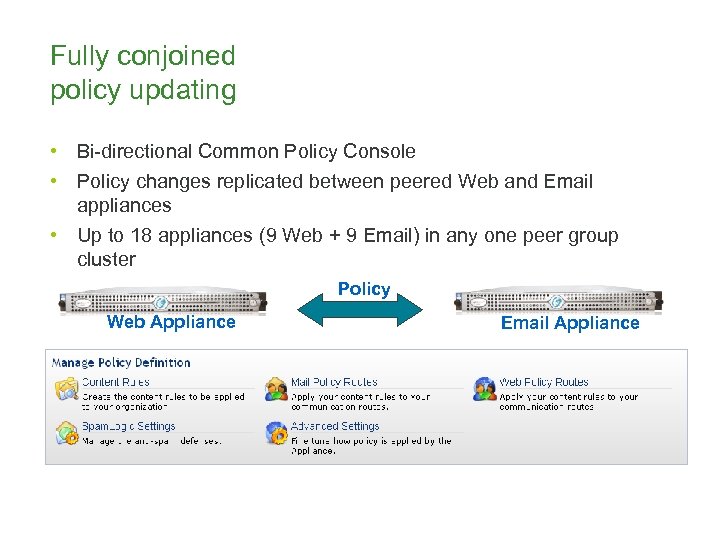
Fully conjoined policy updating • Bi-directional Common Policy Console • Policy changes replicated between peered Web and Email appliances • Up to 18 appliances (9 Web + 9 Email) in any one peer group cluster Policy Web Appliance Email Appliance
HTTPS content scanning and analysis • • Cost option Full content scanning of HTTPS/SSL encrypted data Detects any malware or data leakage in encrypted traffic Flexible deployment i. e. , create specific routes NOT to be scanned, e. g. , “Financial” • Also provides policy based certificate checking for added protection

CONTENTSafe Appliance

Data leakage - the stealth threat to business The penalties can be significant In 2006 the United States Veteran’s Administration lost the names and social security numbers of 27 million living exsoldiers stored on an employee’s laptop computer stolen from a home office. This resulted in huge penalty costs and reputation damage for the VA and the US federal government Source: www. usa. gov/veteransinfo/#FAQs Cost isn’t be measured in dollars alone In December 2006 retailer TJX announced that information from 45 million credit and debit cards from transactions in 2003 was stolen by hackers from its computer systems. The company couldn’t determine the extent of the breach or what customer information may have been compromised, nor could it quantify the financial impact of the breach. One credit union sent The TJX Companies an invoice for $590, 000 to cover the monetary costs and reputational damage that the financial institution says it incurred as a result of the data breach. Sources: www. computerworld. com/action/article. do? com mand=view. Article. Basic&article. Id=295516&sour ce=rss_topic 82
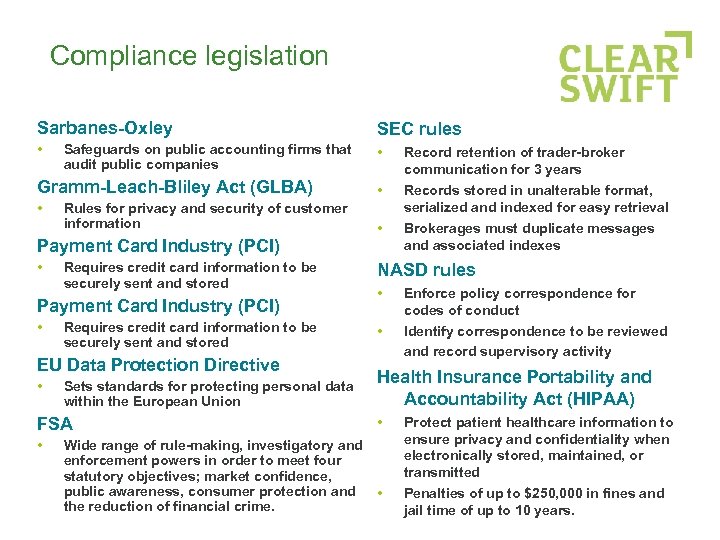
Compliance legislation Sarbanes-Oxley SEC rules • • Safeguards on public accounting firms that audit public companies Gramm-Leach-Bliley Act (GLBA) • Rules for privacy and security of customer information Payment Card Industry (PCI) • Requires credit card information to be securely sent and stored EU Data Protection Directive • Sets standards for protecting personal data within the European Union FSA • • • Record retention of trader-broker communication for 3 years Records stored in unalterable format, serialized and indexed for easy retrieval Brokerages must duplicate messages and associated indexes NASD rules • • Enforce policy correspondence for codes of conduct Identify correspondence to be reviewed and record supervisory activity Health Insurance Portability and Accountability Act (HIPAA) • Wide range of rule-making, investigatory and enforcement powers in order to meet four statutory objectives; market confidence, public awareness, consumer protection and • the reduction of financial crime. Protect patient healthcare information to ensure privacy and confidentiality when electronically stored, maintained, or transmitted Penalties of up to $250, 000 in fines and jail time of up to 10 years.

81% of companies surveyed admit to data breaches occurring over previous 12 months 39% involve confidential business information 27% involve personal information about customers 14% involve intellectual property (including software source code) 10% involve personal information about employees Source: Ponemon Institute Source: www. breachblog. com What is the scale of the problem? University Health Care (2) University of Akron (2) University of Arizona (1) University of California (3) University of Cincinnati (1) University of Colorado (1) Providence Alaska Medical Center State of Tennessee (1) Memorial Hospital (1) IKON Office Solutions (1) Downingtown Area School District Capital Health (2) 1 st Source Bank (1) University of Florida (3) (1) State of Utah (2) Memorial University (1) Illinois Eye Center (1) Caremark (1) A. J. Falciani Realty (1) University of Georgia (1) Prudential plc (1) State of Virginia (1) Merrill Lynch (1) Illinois Tools Works (1) Dudley Group of Hospitals (2) Carmel Unified School District (1) ABC Phones (1) University of Glamorgan (1) Purdue Pharma (1) State of West Virginia (1) Microsoft (1) Indiana State University (1) Duke School of Law (1) Carnegie Mellon University (1) ABN Amro Mortgage (1) University of Illinois (1) Purdue University (1) State of Wisconsin (2) Middle Tennessee State University Indiana University-Purdue University Duke University (2) Cascade Healthcare Community (1) Academy Hearing Centres (1) University of Iowa (2) Queen Mary's Sidcup Hospital (1) State Street Corporation (1) Fort Wayne (1) E. On (1) Castlecroft Medical Practice (1) ACAP Security (1) University of Kansas (1) Queens University of Charlotte (1) State University College at Milwaukee County (2) Indianapolis Power and Light (1) East Tennessee State University (1) Catalina Conservancy Divers (1) Administaff (1) University of Maryland (1) Quest Diagnostics (1) Brockport (1) MLSGear. com (1) Insecure Discard (37) Eastern Connecticut State Catholic Healthcare West (1) Administrative Systems Inc (1) University of Massachusetts (1) R. E. Moulton (1) State University of New York (1) Modesto City Schools (1) Inter. Active Financial Marketing University (1) CBIZ Benefits and Insurance (1) Adobe Systems (1) University of Miami (1) Recovery (1) Staten Island University Hospital (1) Monroe Community College (1) Group (1) Eastern Sales and Marketing (NE) Centocor (1) Advance Auto Parts (1) University of Michigan (1) Rent-a-Center (1) Stedman's (1) Monroe County (1) Interbank FX (1) Central Bank of the UAE (1) Advanced Medical Partners (1) University of Minnesota Physicians Rentway (1) Stock and Options Solutions (1) Montana State University (2) Internal Revenue Service (1) Eastern School District (1) Central Collection Bureau (1) Affiliated Computer Services (1) Republic of Korea (1) Stockport Primary Care Trust (1) Montgomery Ward (1) International Brokerage Dallas (1) Ebay (1) Central Connecticut State University Affordable Realty (1) University of Nevada (1) Robotic Industries Association (1) Stokes County Schools (1) Monthly (1) International Market Place (1) Edgewood Independent School (1) Agilent Technologies (1) University of New Hampshire (1) Roman Catholic Diocese of Stolen Computer (32) Moore Stephens Consulting (1) Intrusion (20) District (1) Central Piedmont Community Alaska Air Group (1) University of North Carolina at Providence (1) Stolen Device (18) Moraine Park Technical College (1) Invision HR Staffing Group (1) Edmonton Catholic School District College (1) Alliance Boots (1) Charlotte (1) Roses Only (1) Stolen Documents (3) MTV Networks (1) Iowa State University (1) Charter Communications (1) Allied Irish Bank (1) University of South Carolina (2) Royal Bank of Scotland (1) Stolen Laptop (105) National Guard Bureau (1) Iron Mountain (2) EDS Corporation (1) Chilean Government (1) Altman Weil (1) University of Texas System (2) Royal Bolton Hospital (1) Stolen Tape (6) National Heart Lung and Blood Isle of Wight NHS PCT (1) Electronic Data Systems (2) Chipotle Mexican Grill (1) American Airlines (1) University of Toledo (2) Royal Perth Hospital (1) Stryker Corporation (1) Institute (1) IVAX (1) Elliot Health System (1) Chrysler Corporation (1) American Express (1) University of Utah (2) Russells Hall Hospital (1) Sun. Gard Higher Education (1) National Institutes of Health (1) J. Lohr Vineyards (1) Emotive (1) Chrysler Financial (1) Americhoice (1) University of Virginia (1) S and K Famous Brands (1) Super 8 Worldwide (1) Nationwide Building Society (1) J. C. Penney (1) Employee Fraud (21) Citibank Student Loan Corporation Anheuser-Busch Companies (1) University of Wisconsin (1) S and K Menswear (1) Sweetbay Supermarket (1) Nat. West (1) Jobs. ie (1) Employee Mistake (56) (1) Antioch University (1) Unknown (3) Saks Incorporated (1) Swimwear Boutique (1) Naval Surface Warfare Center Johns Hopkins Hospital (1) Employee Theft (2) Citizens Advice (1) Aon Consulting (1) update (1) Salem Associates (1) Sydney West Area Health Service Dahlgren (1) Johnson and Johnson (2) Fallon Community Health Plan (1) Citizens for Responsible Applera Corporation (1) USinternetworking Inc. (3) Sales. Force. com (2) (1) Nestle Waters North America (1) Joliet Township High Schools (1) Family Video (1) Government Network (1) Arapahoe Community College (1) UT-Battelle LLC (1) Salt Lake Community College (1) Systematic Automation Inc (6) Nevada Department of Public Safety Kansas State University (1) Ferris State University (1) City of Columbus (1) Archive America (1) UTUIA (1) Sandown Health Centre (1) T. Rowe Price (1) Keller Independent School District Fidelity Investments (1) City of Gary (1) ARCO (1) VA Medical Center (2) Scarborough & Tweed (1) Target Corporation (1) Nevada State Democratic Party (1) Fidelity National Information City of Minneola (FL) (1) Arizona Board of Regents (1) Verified Identity Pass (1) Schering Plough (1) TD Ameritrade (1) New England School of Law (1) Kellogg Community Federal Credit Services (1) City of San Francisco (1) Arizona State University (1) Verisign (1) Sears. Home. Center. com (1) TD Bank Financial Group (1) New Mexico State University (1) Union (1) First Calgary Savings (1) City of Yuma (1) Art. com (1) Verizon Wireless (1) Sears. Room. For. Kids. com (1) TD Canada Trust (1) New South Wales Government (1) Kims. Crafts (1) First Magnus Financial (1) City University of New York (1) Associated Newspapers (1) Vertical Web Media (1)
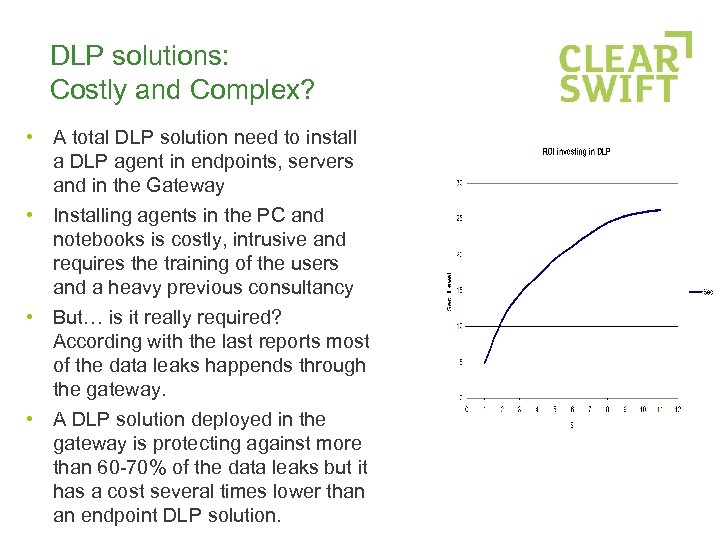
DLP solutions: Costly and Complex? • A total DLP solution need to install a DLP agent in endpoints, servers and in the Gateway • Installing agents in the PC and notebooks is costly, intrusive and requires the training of the users and a heavy previous consultancy • But… is it really required? According with the last reports most of the data leaks happends through the gateway. • A DLP solution deployed in the gateway is protecting against more than 60 -70% of the data leaks but it has a cost several times lower than an endpoint DLP solution.
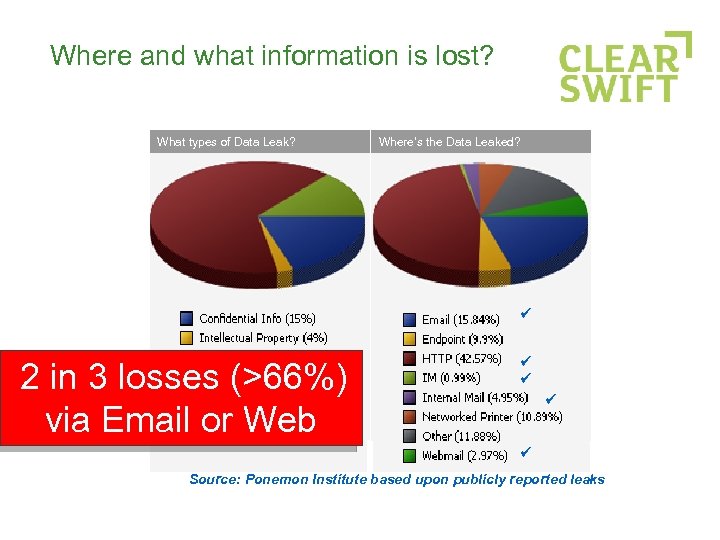
Where and what information is lost? What types of Data Leak? 2 in 3 losses (>66%) via Email or Web Where’s the Data Leaked? Source: Ponemon Institute based upon publicly reported leaks
Introduction - Clearswift Data Loss Prevention (DLP) today ……………………………………………………. . . …. ………………………………………………………. . Clearswift already offers - Multiple protocols || Common policy and management || Bi-directional protection || DLP & Boundary hygiene ……………………………………………………. . . …. ………………………………………………………. . MIMEsweeper DLP includes: • • Enhanced deep content inspection True file/data type recognition Lexical analysis Managed & User defined lists for HIPAA, SOX, SEC, Stock Trading Profanity, harassment, paedophilia control Image control • • • Templates to detect PII and PCI data Lexical expressions and scripts IPR protection Whole document checksum controls (SMTP) Sender, recipient, direction, size, file-type And more…. • • ……………………………………………………. . . …. ………………………………………………………. .

What is Clearswift CONTENTsafe™? • • • An extension to MIMEsweeper’s data loss prevention capabilities Designed to allow ‘line of business’ staff to easily identify and protect their highly confidential information Providing a central repository for protected document checksums With the checksums used to deliver policy driven security control over documented information and all of its constituent parts Integrates with any MIMEsweeper e-mail or web* gateway security solution * MIMEsweeper Web & Email appliances by mid-2009
What additional data loss capabilities does CONTENTsafe™ provide? • Universal identification of sensitive content • Protocol agnostic content detection • Mapping of individual user network locations for sensitive information • Creation of checksums with a guaranteed 150 character match rate • Automatic scanning of file & document locations for new documents & changes to existing documents • Document protection expiry rules & dates • Granular roles based user access & user delegation • Multi-language and multi-byte character support • White-listing to minimize false positives
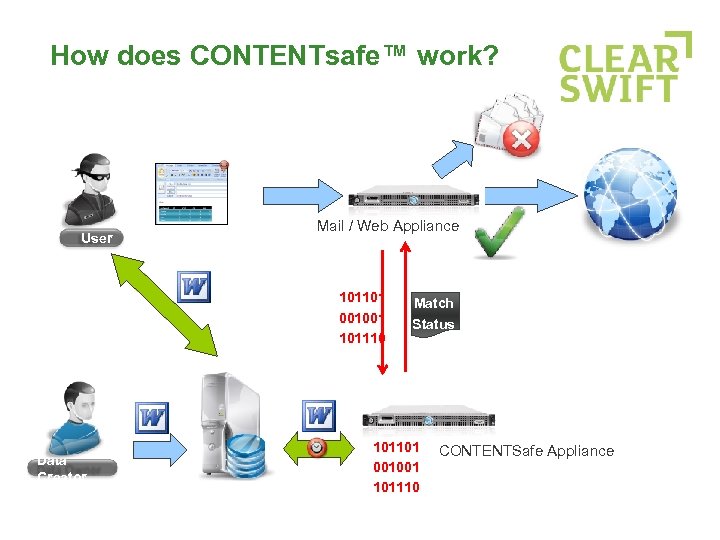
How does CONTENTsafe™ work? User Mail / Web Appliance 101101 001001 101110 Data Creator Match Status 101101 001001 101110 CONTENTSafe Appliance

What file types are protected by CONTENTsafe™? • Uses MIMEsweeper deep content inspection so can extract documents from zip, tar, TNEF etc. • Able to checksum/fingerprint content from: – CDA, HTML, Ichitaro, MS Excel, Outlook file attachment, MS Power. Point, MS Project, MS Word, Open document text, Open document spreadsheet, Open document presentation, Open document formula, Open document drawing, Open document master, PDF, PEM message if not encrypted, PGP message if not encrypted, RTF encoded HTML, text, XML, Script

What is the performance of CONTENTsafe? • A single CONTENTsafe appliance is designed to protect up to 500, 000 documents • A single CONTENTsafe appliance is able to process 1 million e-mail queries per day with negligible impact on e-mail throughput • The average time to check a message from SMTP is less than 50 ms + any network latency * These results were obtained via simulation as part of the ongoing develop
How is CONTENTsafe™ available? Hardened 64 bit Linux appliance 500, 000 document capacity Individual user areas Document registration via: • Network locations, • Uploaded documents • Pasting text fragments • Whole document detection • Document extract white-listing Violation alerting Global & User Management/Auditing/Reporting Business roles administration

Clearswift Overview Questions?
6efd42947f322ad509ae580f7d7b81f8.ppt