75aa81e8470c502b08d778c0699e4d1f.ppt
- Количество слайдов: 38

Class 36: Public-Key Cryptography If you want a guarantee, buy a toaster. Clint Eastwood (The Rookie, 1990) CS 200: Computer Science David Evans University of Virginia 16 April 2004 CS 200 Spring 2004 http: //www. cs. virginia. edu/evans Computer Science

Last Time • How to store securely – Store the hash of the password • One-way, collision resistant hashing function (e. g. , md 5) – Check the hash of the entered password matches the stored hash • The password is transmitted over the Internet 16 April 2004 CS 200 Spring 2004 2
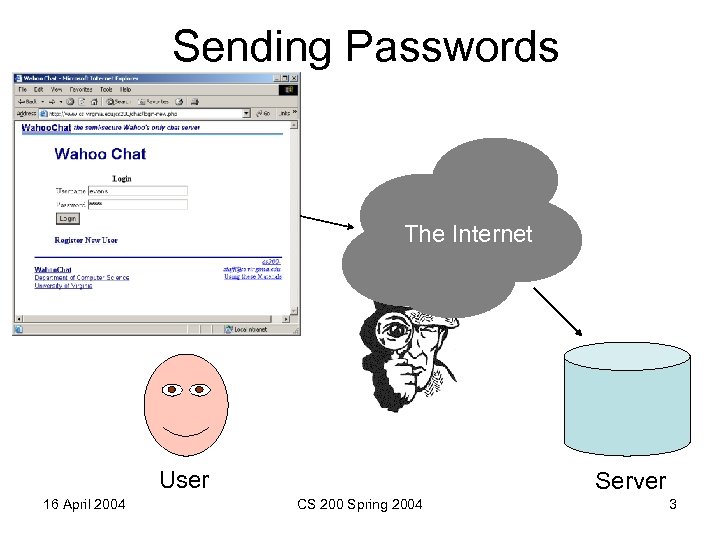
Sending Passwords Encrypt The Internet User 16 April 2004 Server CS 200 Spring 2004 3
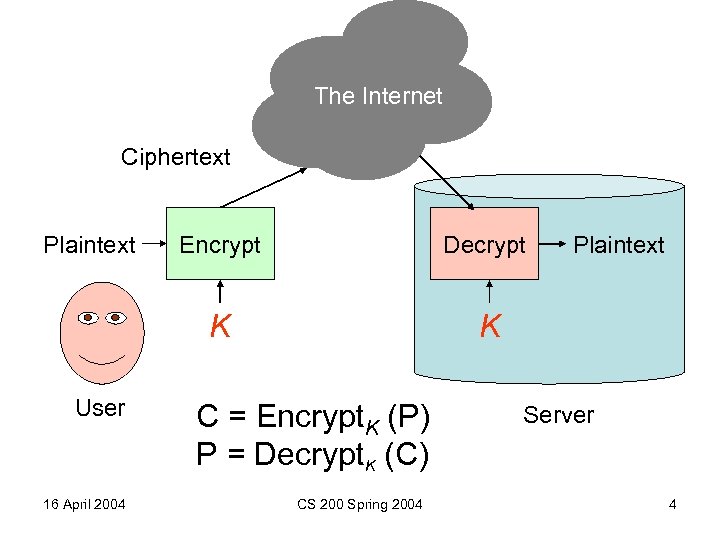
The Internet Ciphertext Plaintext 16 April 2004 Decrypt K User Encrypt K C = Encrypt. K (P) P = Decrypt. K (C) CS 200 Spring 2004 Plaintext Server 4
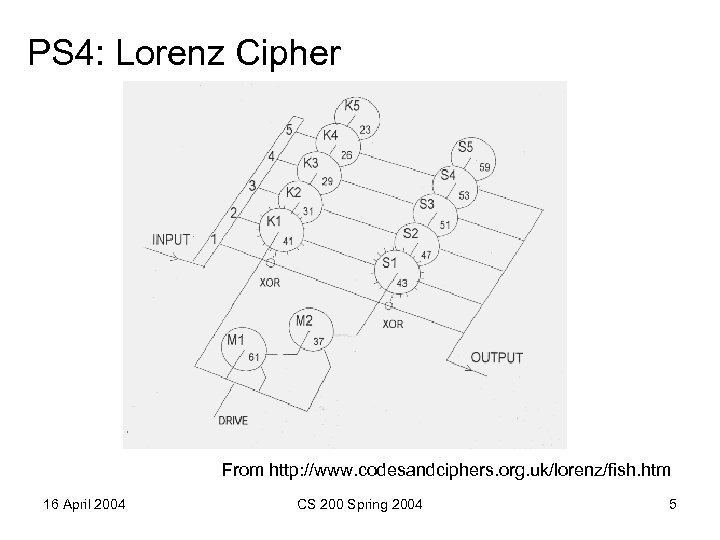
PS 4: Lorenz Cipher From http: //www. codesandciphers. org. uk/lorenz/fish. htm 16 April 2004 CS 200 Spring 2004 5
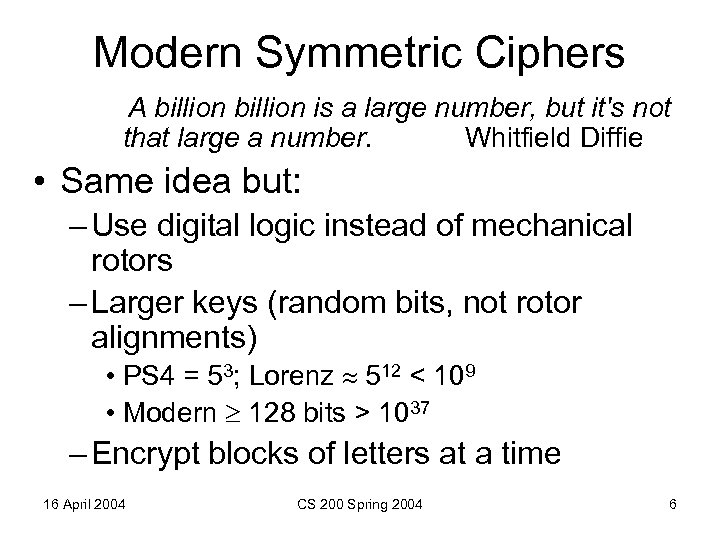
Modern Symmetric Ciphers A billion is a large number, but it's not that large a number. Whitfield Diffie • Same idea but: – Use digital logic instead of mechanical rotors – Larger keys (random bits, not rotor alignments) • PS 4 = 53; Lorenz 512 < 109 • Modern 128 bits > 1037 – Encrypt blocks of letters at a time 16 April 2004 CS 200 Spring 2004 6
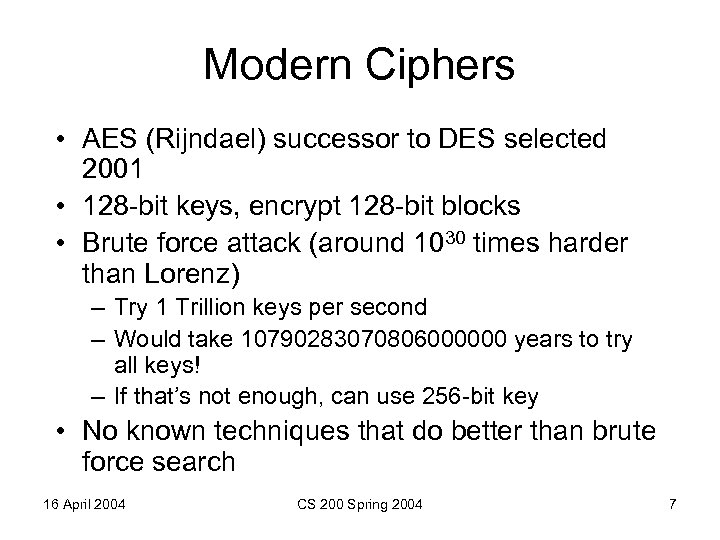
Modern Ciphers • AES (Rijndael) successor to DES selected 2001 • 128 -bit keys, encrypt 128 -bit blocks • Brute force attack (around 1030 times harder than Lorenz) – Try 1 Trillion keys per second – Would take 10790283070806000000 years to try all keys! – If that’s not enough, can use 256 -bit key • No known techniques that do better than brute force search 16 April 2004 CS 200 Spring 2004 7
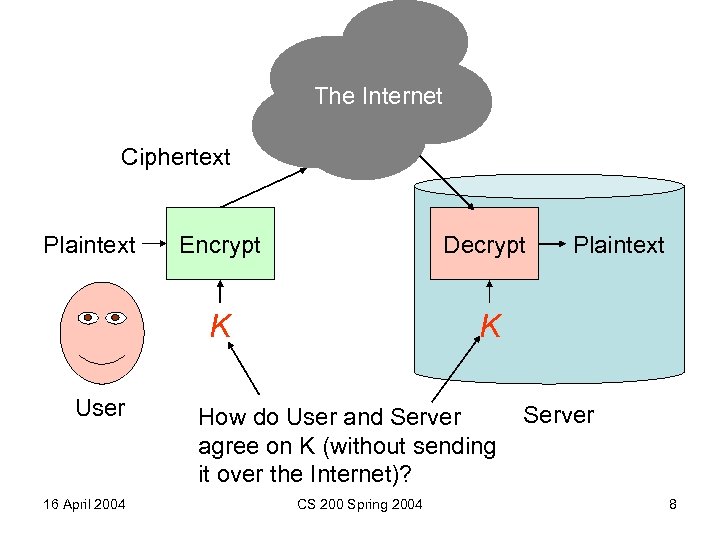
The Internet Ciphertext Plaintext 16 April 2004 Decrypt K User Encrypt K How do User and Server agree on K (without sending it over the Internet)? CS 200 Spring 2004 Plaintext Server 8
Key Agreement Demo (Animated version at end of slides. ) 16 April 2004 CS 200 Spring 2004 9

Asymmetric Cryptosystems • Need a hard problem (like symmetric cryptosystems) • With a trap door: if you know a secret, the hard problem becomes easy 16 April 2004 CS 200 Spring 2004 10

One-Way Functions • Easy to compute, hard to invert • Trap-door one way function: – D (E (M)) = M – E and D are easy to compute. – Revealing E doesn’t reveal an easy way to compute D. – Hence, anyone who knows E can encrypt, but only someone who knows D can decrypt 16 April 2004 CS 200 Spring 2004 11
![RSA [Rivest, Shamir, Adelman 78] One-way function: multiplication is easy, factoring is hard Trap-door: RSA [Rivest, Shamir, Adelman 78] One-way function: multiplication is easy, factoring is hard Trap-door:](https://present5.com/presentation/75aa81e8470c502b08d778c0699e4d1f/image-12.jpg)
RSA [Rivest, Shamir, Adelman 78] One-way function: multiplication is easy, factoring is hard Trap-door: number theory (Euler and Fermat) 16 April 2004 CS 200 Spring 2004 12

Security of RSA • n is public, but not p and q where n = pq • How much work is factoring n? Number Field Sieve (fastest known factoring algorithm) is: 1. 9223((ln (n))1/3 (ln (n)))2/3) O(e n ~200 digits – would take quintillions of years 16 April 2004 The movie Sneakers is about what happens if someone discovers a O(nk) factoring algorithm. CS 200 Spring 2004 13
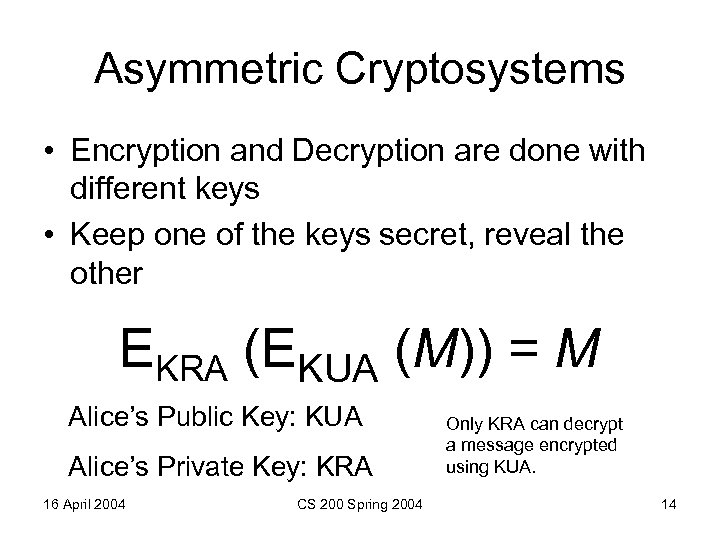
Asymmetric Cryptosystems • Encryption and Decryption are done with different keys • Keep one of the keys secret, reveal the other EKRA (EKUA (M)) = M Alice’s Public Key: KUA Alice’s Private Key: KRA 16 April 2004 CS 200 Spring 2004 Only KRA can decrypt a message encrypted using KUA. 14
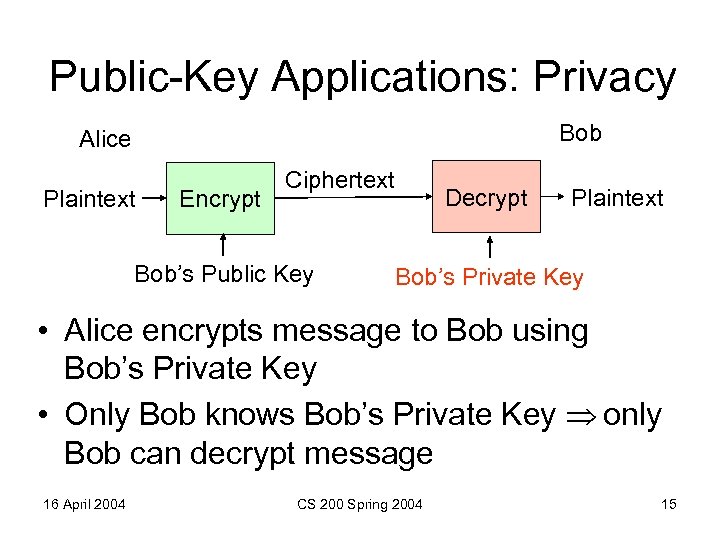
Public-Key Applications: Privacy Bob Alice Plaintext Encrypt Ciphertext Bob’s Public Key Decrypt Plaintext Bob’s Private Key • Alice encrypts message to Bob using Bob’s Private Key • Only Bob knows Bob’s Private Key only Bob can decrypt message 16 April 2004 CS 200 Spring 2004 15
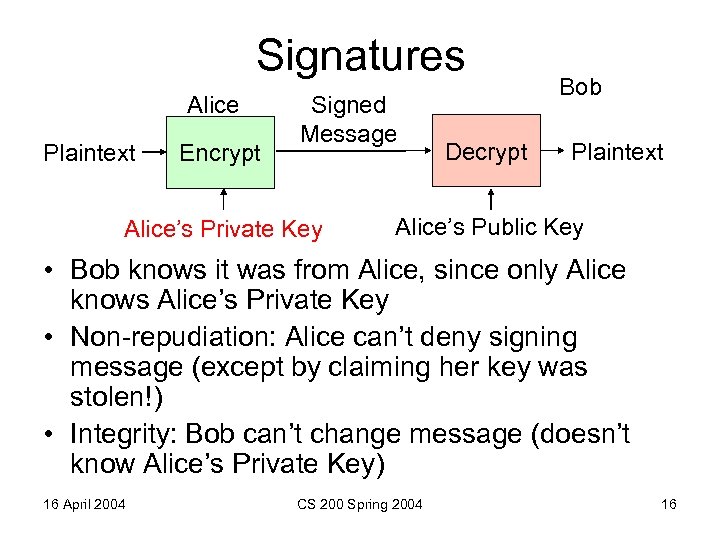
Signatures Alice Plaintext Encrypt Signed Message Alice’s Private Key Decrypt Bob Plaintext Alice’s Public Key • Bob knows it was from Alice, since only Alice knows Alice’s Private Key • Non-repudiation: Alice can’t deny signing message (except by claiming her key was stolen!) • Integrity: Bob can’t change message (doesn’t know Alice’s Private Key) 16 April 2004 CS 200 Spring 2004 16
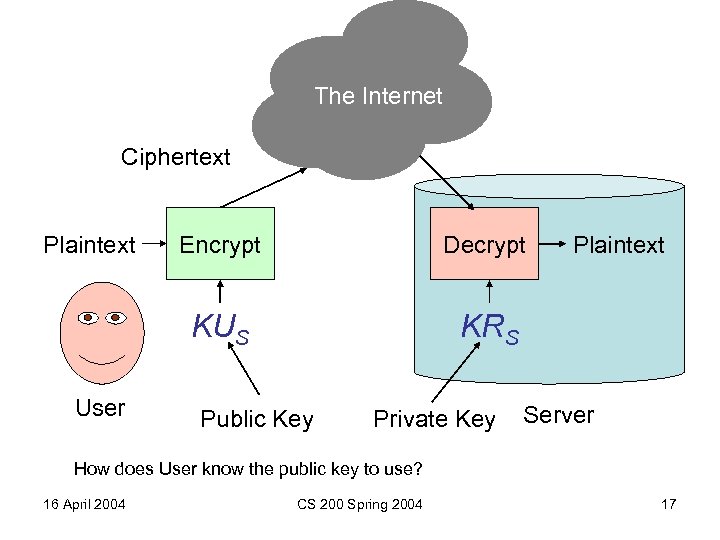
The Internet Ciphertext Plaintext Decrypt KUS User Encrypt KRS Public Key Private Key Plaintext Server How does User know the public key to use? 16 April 2004 CS 200 Spring 2004 17

Key Management 16 April 2004 CS 200 Spring 2004 18

Approach 1: Meet Secretly • User and Server Operator meet secretly and swap public keys – If you can do that, might as well agree on a secret (symmetric key) instead – Doesn’t work for Internet transactions 16 April 2004 CS 200 Spring 2004 19

Approach 2: Public Announcement • Publish public keys in a public forum – Append to email messages – Post on web site – New York Time classifieds • Easy for rogue to pretend to be someone else – Forge email, alter web site, lie to New York Times 16 April 2004 CS 200 Spring 2004 20

Approach 3: Public Directory • Trusted authority maintains directory mapping names to public keys • Entities register public keys with authority in some secure way • Authority publishes directory – Print using watermarked paper, special fonts, etc. – Allow secure electronic access • Depends on secure distribution of directory’s key 16 April 2004 CS 200 Spring 2004 21
![Approach 4: Certificates Veri. Sign KUS $$$$ CS = EKRVeri. Sign[“Server”, KUS] Request User Approach 4: Certificates Veri. Sign KUS $$$$ CS = EKRVeri. Sign[“Server”, KUS] Request User](https://present5.com/presentation/75aa81e8470c502b08d778c0699e4d1f/image-22.jpg)
Approach 4: Certificates Veri. Sign KUS $$$$ CS = EKRVeri. Sign[“Server”, KUS] Request User CS EKUVeri. Sign (CS) = [“Server”, KUS] 16 April 2004 CS 200 Spring 2004 Server Knows KRS 22
![SSL (Secure Sockets Layer) Browser Server Hello KRCA[Server Identity, KUS] Check Certificate using KUCA SSL (Secure Sockets Layer) Browser Server Hello KRCA[Server Identity, KUS] Check Certificate using KUCA](https://present5.com/presentation/75aa81e8470c502b08d778c0699e4d1f/image-23.jpg)
SSL (Secure Sockets Layer) Browser Server Hello KRCA[Server Identity, KUS] Check Certificate using KUCA Pick random K Note: This is slightly simplified from the actual SSL protocol. This version is vulnerable to a person-inthe-middle attack! 16 April 2004 KUS[K] Find K using KRS Secure channel using K CS 200 Spring 2004 23
Data encrypted using secret key exchanged using some public key associated with some certificate. 16 April 2004 CS 200 Spring 2004 24
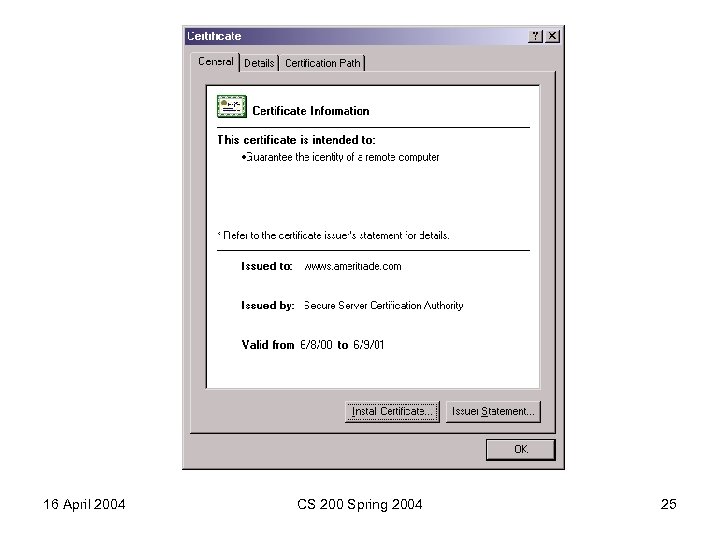
16 April 2004 CS 200 Spring 2004 25
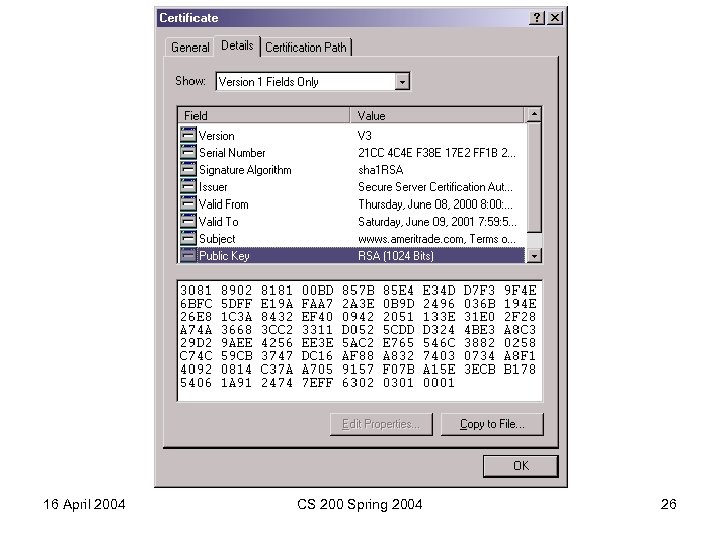
16 April 2004 CS 200 Spring 2004 26
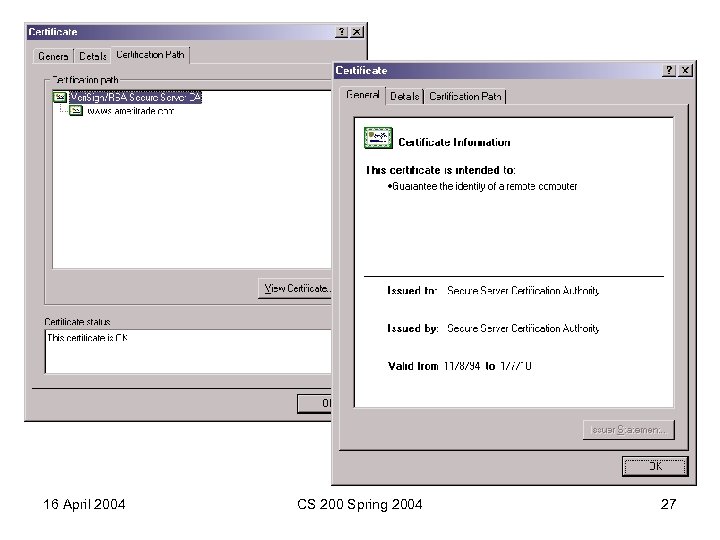
16 April 2004 CS 200 Spring 2004 27
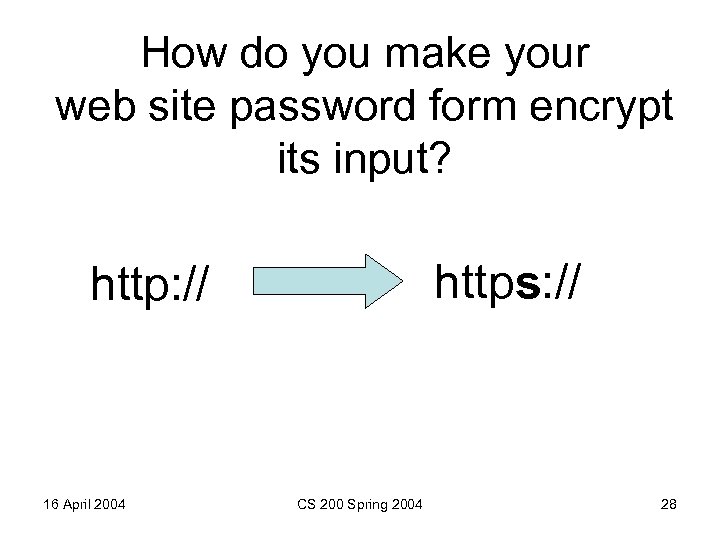
How do you make your web site password form encrypt its input? https: // http: // 16 April 2004 CS 200 Spring 2004 28
Charge • Exam 2 due Monday • Next week: – Why Sneakers is also about solving the Cracker Barrel puzzle in O(nk) – (Not necessary to see Sneakers for next week’s classes) 16 April 2004 CS 200 Spring 2004 29

Animated version of Asymmetric Cryptography Demo 16 April 2004 CS 200 Spring 2004 30
Padlocked Boxes Hi! Alice 16 April 2004 CS 200 Spring 2004 31
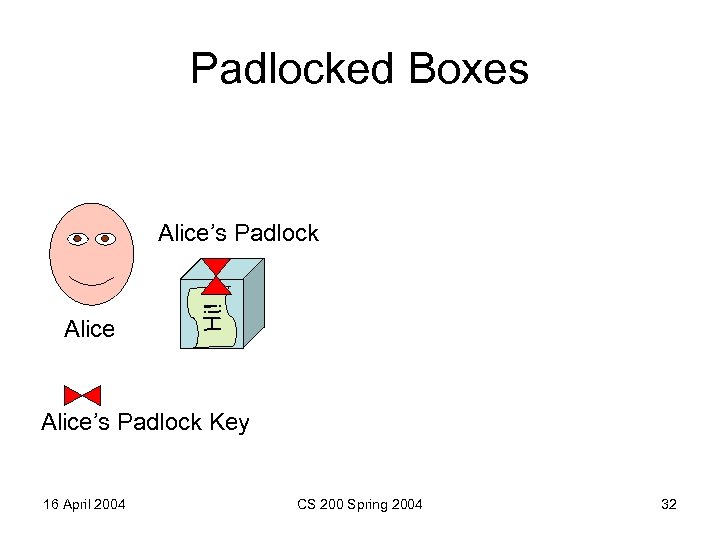
Padlocked Boxes Alice Hi! Alice’s Padlock Key 16 April 2004 CS 200 Spring 2004 32
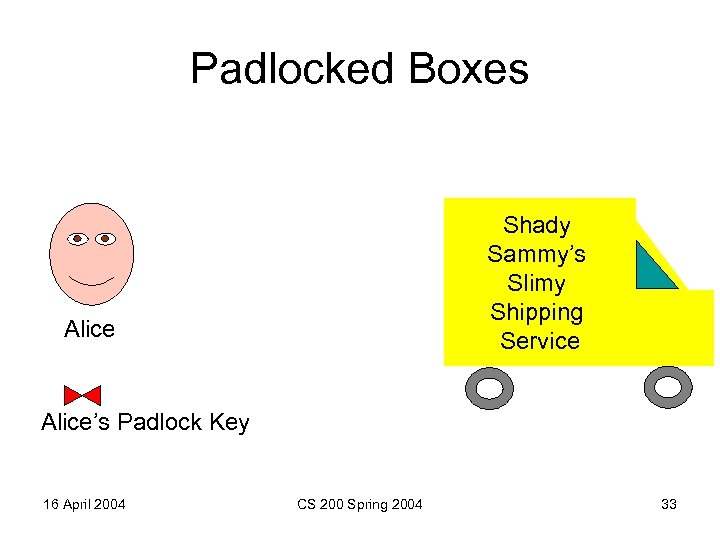
Padlocked Boxes Shady Sammy’s Slimy Shipping Service Alice’s Padlock Key 16 April 2004 CS 200 Spring 2004 33
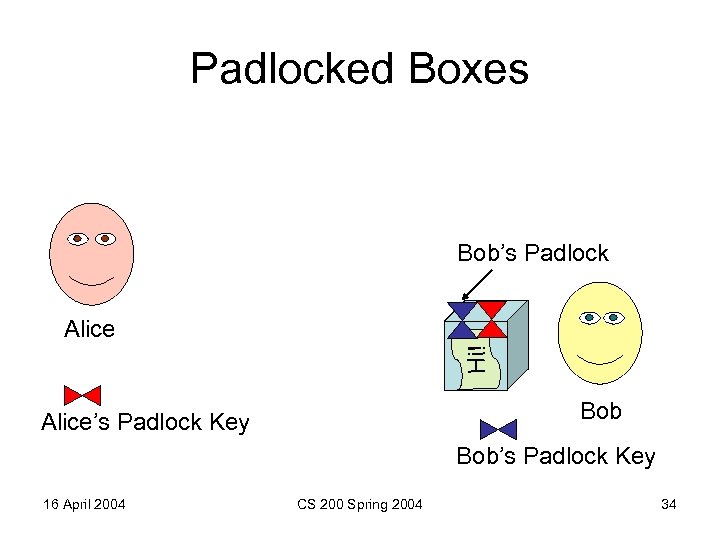
Padlocked Boxes Bob’s Padlock Hi! Alice Bob Alice’s Padlock Key Bob’s Padlock Key 16 April 2004 CS 200 Spring 2004 34
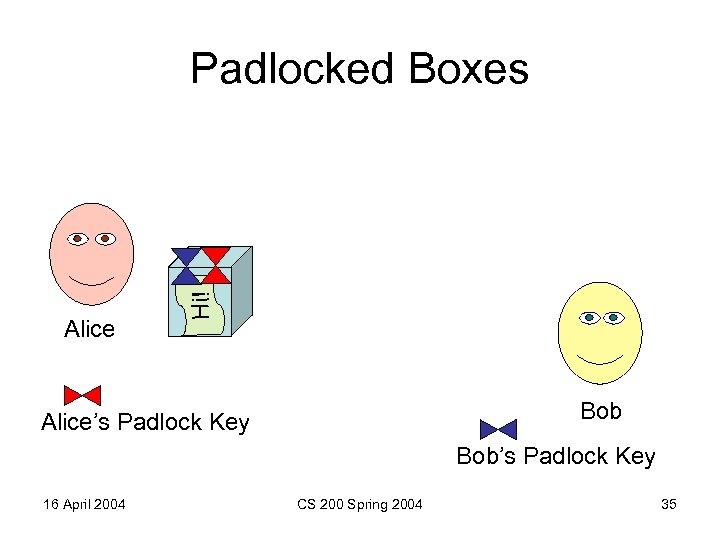
Alice Hi! Padlocked Boxes Bob Alice’s Padlock Key Bob’s Padlock Key 16 April 2004 CS 200 Spring 2004 35
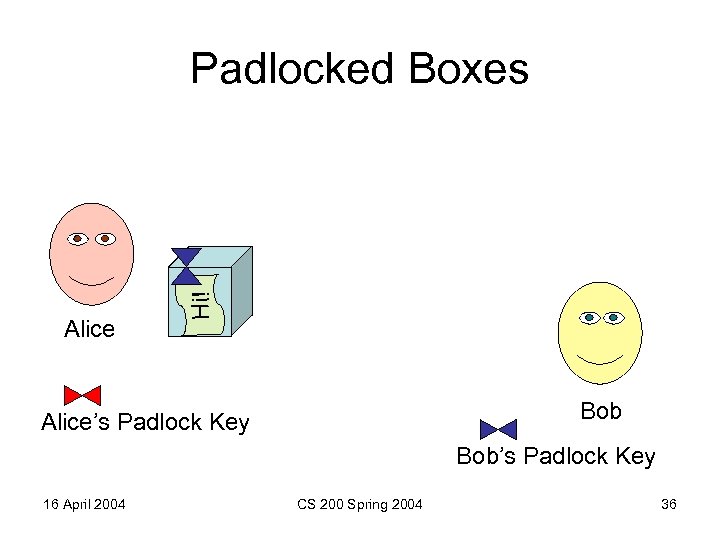
Alice Hi! Padlocked Boxes Bob Alice’s Padlock Key Bob’s Padlock Key 16 April 2004 CS 200 Spring 2004 36
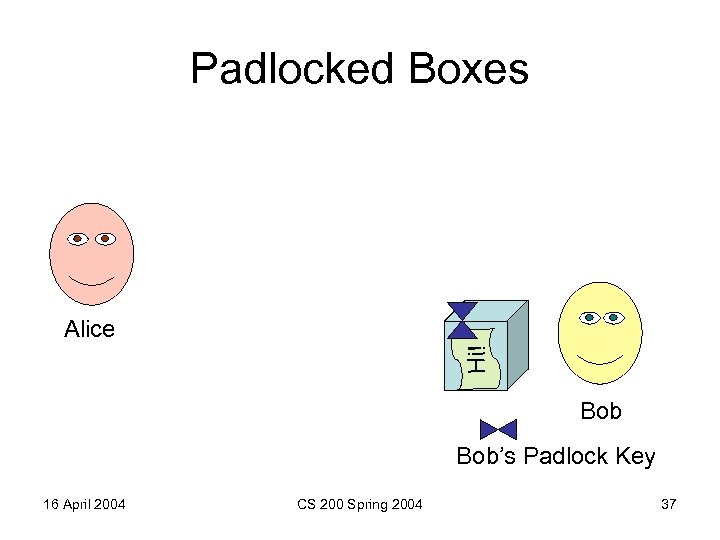
Padlocked Boxes Hi! Alice Bob’s Padlock Key 16 April 2004 CS 200 Spring 2004 37
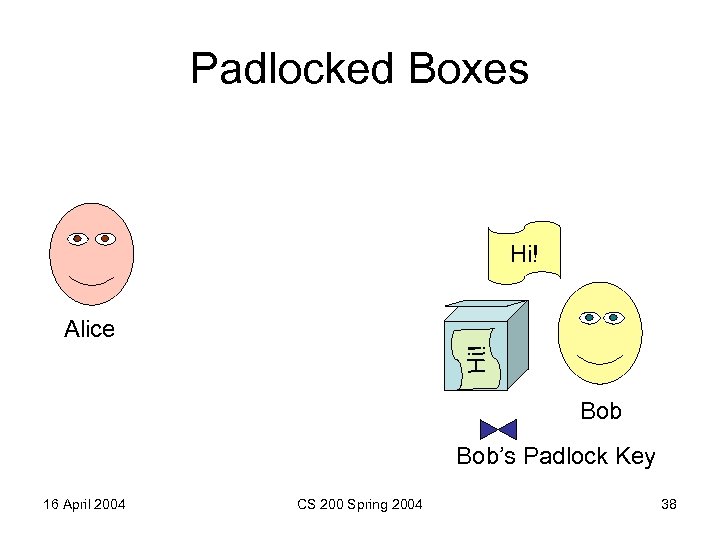
Padlocked Boxes Hi! Alice Bob’s Padlock Key 16 April 2004 CS 200 Spring 2004 38
75aa81e8470c502b08d778c0699e4d1f.ppt