d4d954cf22c90a643963057fbff32901.ppt
- Количество слайдов: 62
 Citrix and ADFS Leverage Active Directory Federation Services in a Presentation Server Environment Jay Tomlin Sr. Technology Specialist Mgr NA Field Readiness 08 December 2006
Citrix and ADFS Leverage Active Directory Federation Services in a Presentation Server Environment Jay Tomlin Sr. Technology Specialist Mgr NA Field Readiness 08 December 2006
 Copyright & Disclaimer Copyright © 2006, Citrix Unpublished work of Citrix. All Rights Reserved. This work is an unpublished work and contains confidential, proprietary, and trade secret information of Citrix. Access to this work is restricted to Citrix employees who have a need to know to perform tasks within the scope of their assignments, or to authorized organizations under a Non-Disclosure Agreement. Any use or exploitation of this work without authorization could subject the perpetrator to criminal and civil liability. General Disclaimer This document is not to be construed as a promise by any participating company to develop, deliver, or market a product. Citrix makes no representations or warranties with respect to the contents of this document, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Citrix, reserves the right to revise this document and to make changes to its content, at any time, without obligation to notify any person or entity of such revisions or changes. 2 © 2005 Citrix Systems, Inc. —All rights reserved.
Copyright & Disclaimer Copyright © 2006, Citrix Unpublished work of Citrix. All Rights Reserved. This work is an unpublished work and contains confidential, proprietary, and trade secret information of Citrix. Access to this work is restricted to Citrix employees who have a need to know to perform tasks within the scope of their assignments, or to authorized organizations under a Non-Disclosure Agreement. Any use or exploitation of this work without authorization could subject the perpetrator to criminal and civil liability. General Disclaimer This document is not to be construed as a promise by any participating company to develop, deliver, or market a product. Citrix makes no representations or warranties with respect to the contents of this document, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Citrix, reserves the right to revise this document and to make changes to its content, at any time, without obligation to notify any person or entity of such revisions or changes. 2 © 2005 Citrix Systems, Inc. —All rights reserved.
 Agenda 1. Introduction to Active Directory Federation Services 2. Web Interface ADFS Integration 3. Configuration Walk-through 4. Alternative Deployment Scenarios 5. Q&A 3 © 2005 Citrix Systems, Inc. —All rights reserved.
Agenda 1. Introduction to Active Directory Federation Services 2. Web Interface ADFS Integration 3. Configuration Walk-through 4. Alternative Deployment Scenarios 5. Q&A 3 © 2005 Citrix Systems, Inc. —All rights reserved.
 Part 1: Introduction to ADFS
Part 1: Introduction to ADFS
 What is Federation? A set of standards-based technology & IT processes to facilitate distributed identification, authentication & authorization across boundaries (security, departmental, organizational or platform). • Users: Fewer passwords, more productivity • IT: Centralized, automated, delegated user management • Dev: Leveraged, outsourced service infrastructure 5 © 2005 Citrix Systems, Inc. —All rights reserved.
What is Federation? A set of standards-based technology & IT processes to facilitate distributed identification, authentication & authorization across boundaries (security, departmental, organizational or platform). • Users: Fewer passwords, more productivity • IT: Centralized, automated, delegated user management • Dev: Leveraged, outsourced service infrastructure 5 © 2005 Citrix Systems, Inc. —All rights reserved.
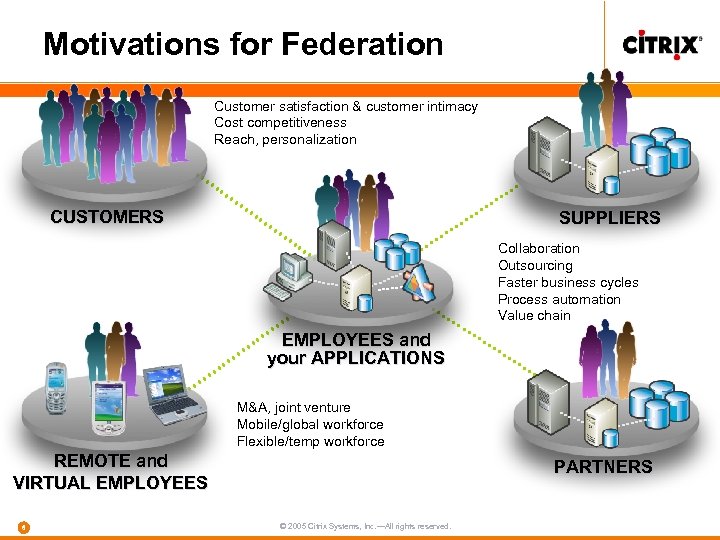 Motivations for Federation Customer satisfaction & customer intimacy Cost competitiveness Reach, personalization CUSTOMERS SUPPLIERS Collaboration Outsourcing Faster business cycles Process automation Value chain EMPLOYEES and your APPLICATIONS M&A, joint venture Mobile/global workforce Flexible/temp workforce REMOTE and VIRTUAL EMPLOYEES 6 PARTNERS © 2005 Citrix Systems, Inc. —All rights reserved.
Motivations for Federation Customer satisfaction & customer intimacy Cost competitiveness Reach, personalization CUSTOMERS SUPPLIERS Collaboration Outsourcing Faster business cycles Process automation Value chain EMPLOYEES and your APPLICATIONS M&A, joint venture Mobile/global workforce Flexible/temp workforce REMOTE and VIRTUAL EMPLOYEES 6 PARTNERS © 2005 Citrix Systems, Inc. —All rights reserved.
 Federation Benefits • Better Access Experience – Single sign-on across networks & organizational boundaries • Increased Security & Simpler Administration – Heightened identity assurance – No passwords involved – Account de-activation is handled by the account partner – Account partner can easily be disabled at the organizational level – Strong authentication such as user certificates or OTP tokens can be layered on top of federation claim 7 © 2005 Citrix Systems, Inc. —All rights reserved.
Federation Benefits • Better Access Experience – Single sign-on across networks & organizational boundaries • Increased Security & Simpler Administration – Heightened identity assurance – No passwords involved – Account de-activation is handled by the account partner – Account partner can easily be disabled at the organizational level – Strong authentication such as user certificates or OTP tokens can be layered on top of federation claim 7 © 2005 Citrix Systems, Inc. —All rights reserved.
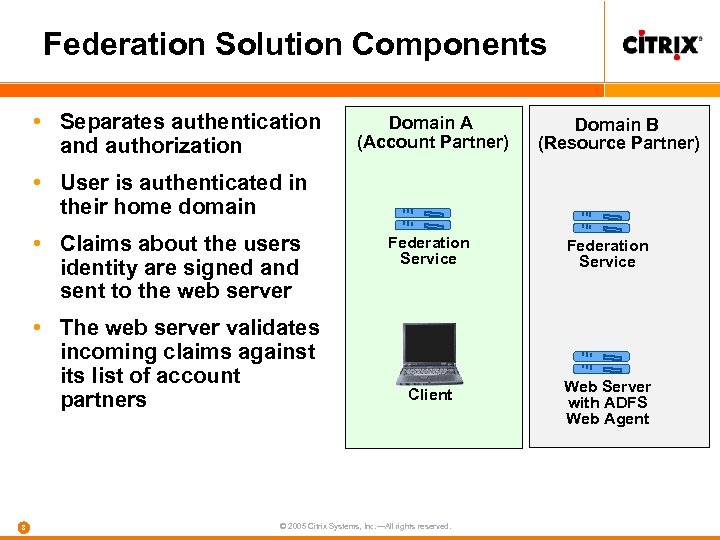 Federation Solution Components • Separates authentication and authorization Domain A (Account Partner) Domain B (Resource Partner) • User is authenticated in their home domain • Claims about the users identity are signed and sent to the web server • The web server validates incoming claims against its list of account partners 8 Federation Service Client Web Server with ADFS Web Agent © 2005 Citrix Systems, Inc. —All rights reserved.
Federation Solution Components • Separates authentication and authorization Domain A (Account Partner) Domain B (Resource Partner) • User is authenticated in their home domain • Claims about the users identity are signed and sent to the web server • The web server validates incoming claims against its list of account partners 8 Federation Service Client Web Server with ADFS Web Agent © 2005 Citrix Systems, Inc. —All rights reserved.
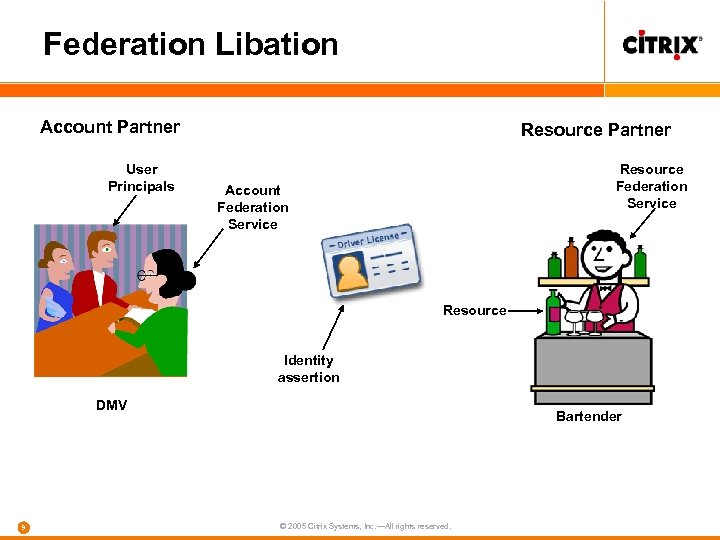 Federation Libation Account Partner User Principals Resource Partner Resource Federation Service Account Federation Service Resource Identity assertion DMV 9 Bartender © 2005 Citrix Systems, Inc. —All rights reserved.
Federation Libation Account Partner User Principals Resource Partner Resource Federation Service Account Federation Service Resource Identity assertion DMV 9 Bartender © 2005 Citrix Systems, Inc. —All rights reserved.
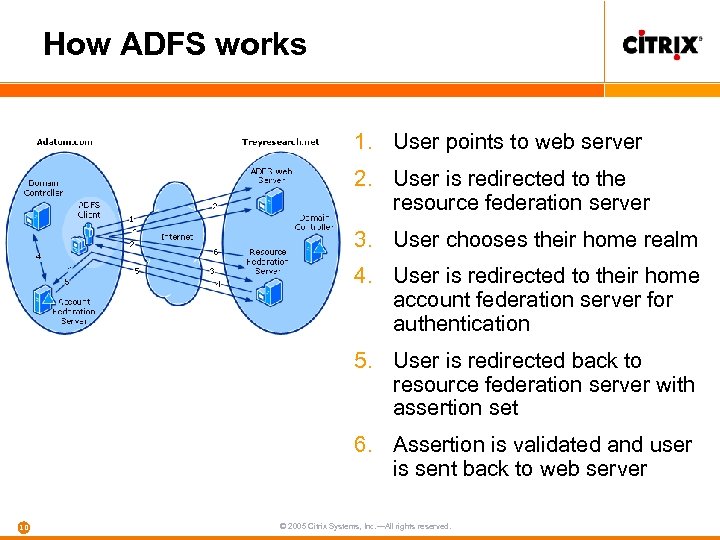 How ADFS works 1. User points to web server 2. User is redirected to the resource federation server 3. User chooses their home realm 4. User is redirected to their home account federation server for authentication 5. User is redirected back to resource federation server with assertion set 6. Assertion is validated and user is sent back to web server 10 © 2005 Citrix Systems, Inc. —All rights reserved.
How ADFS works 1. User points to web server 2. User is redirected to the resource federation server 3. User chooses their home realm 4. User is redirected to their home account federation server for authentication 5. User is redirected back to resource federation server with assertion set 6. Assertion is validated and user is sent back to web server 10 © 2005 Citrix Systems, Inc. —All rights reserved.
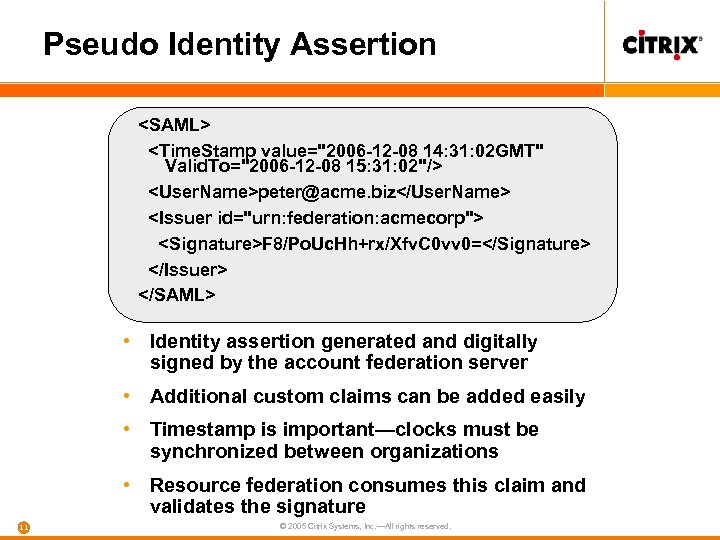 Pseudo Identity Assertion
Pseudo Identity Assertion
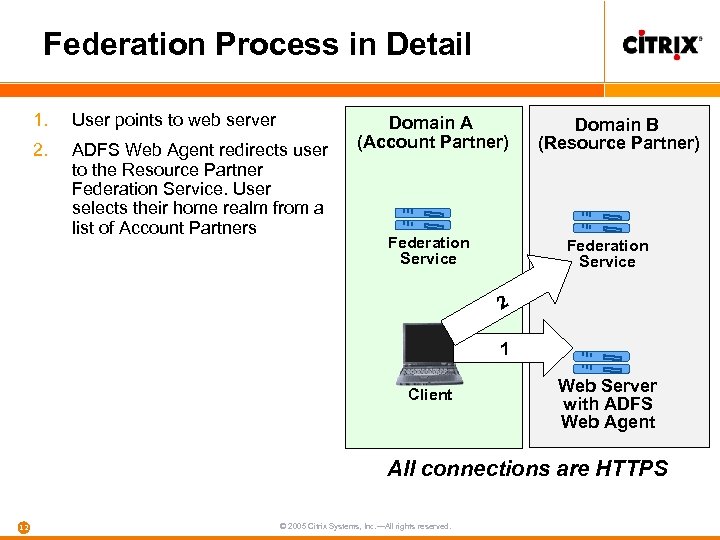 Federation Process in Detail 1. User points to web server 2. ADFS Web Agent redirects user to the Resource Partner Federation Service. User selects their home realm from a list of Account Partners Domain A (Account Partner) Federation Service Domain B (Resource Partner) Federation Service 2 1 Client Web Server with ADFS Web Agent All connections are HTTPS 12 © 2005 Citrix Systems, Inc. —All rights reserved.
Federation Process in Detail 1. User points to web server 2. ADFS Web Agent redirects user to the Resource Partner Federation Service. User selects their home realm from a list of Account Partners Domain A (Account Partner) Federation Service Domain B (Resource Partner) Federation Service 2 1 Client Web Server with ADFS Web Agent All connections are HTTPS 12 © 2005 Citrix Systems, Inc. —All rights reserved.
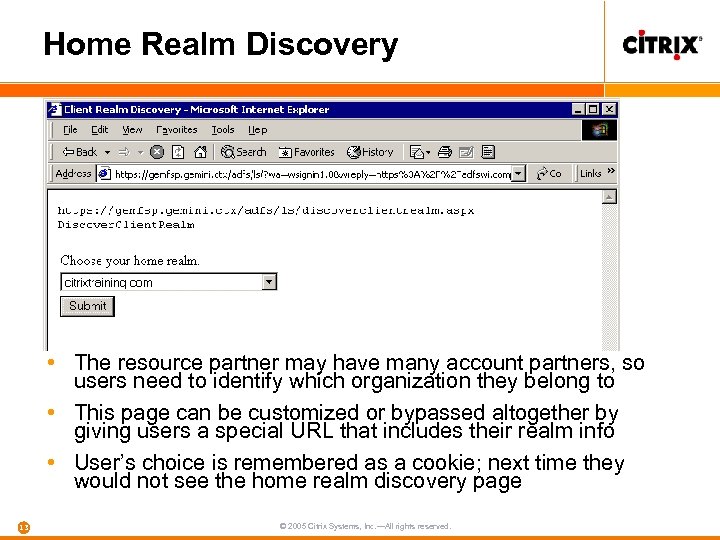 Home Realm Discovery • The resource partner may have many account partners, so users need to identify which organization they belong to • This page can be customized or bypassed altogether by giving users a special URL that includes their realm info • User’s choice is remembered as a cookie; next time they would not see the home realm discovery page 13 © 2005 Citrix Systems, Inc. —All rights reserved.
Home Realm Discovery • The resource partner may have many account partners, so users need to identify which organization they belong to • This page can be customized or bypassed altogether by giving users a special URL that includes their realm info • User’s choice is remembered as a cookie; next time they would not see the home realm discovery page 13 © 2005 Citrix Systems, Inc. —All rights reserved.
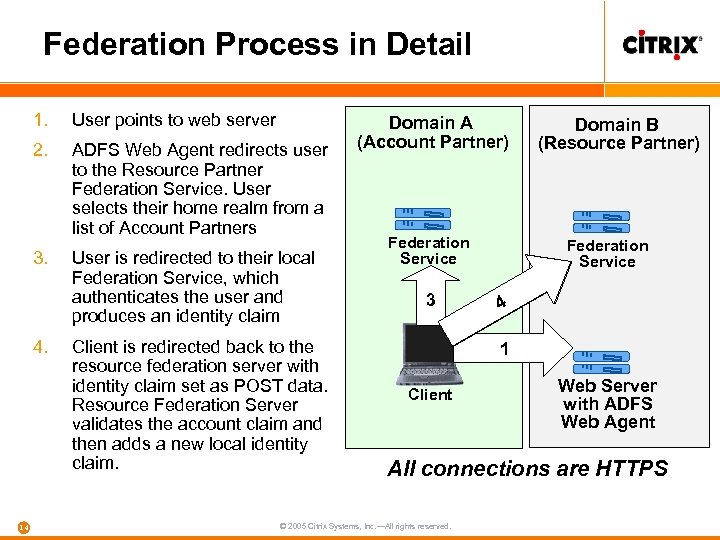 Federation Process in Detail 1. User points to web server 2. ADFS Web Agent redirects user to the Resource Partner Federation Service. User selects their home realm from a list of Account Partners 3. 4. 14 User is redirected to their local Federation Service, which authenticates the user and produces an identity claim Client is redirected back to the resource federation server with identity claim set as POST data. Resource Federation Server validates the account claim and then adds a new local identity claim. Domain A (Account Partner) Federation Service 3 Domain B (Resource Partner) Federation Service 2 4 1 Client Web Server with ADFS Web Agent All connections are HTTPS © 2005 Citrix Systems, Inc. —All rights reserved.
Federation Process in Detail 1. User points to web server 2. ADFS Web Agent redirects user to the Resource Partner Federation Service. User selects their home realm from a list of Account Partners 3. 4. 14 User is redirected to their local Federation Service, which authenticates the user and produces an identity claim Client is redirected back to the resource federation server with identity claim set as POST data. Resource Federation Server validates the account claim and then adds a new local identity claim. Domain A (Account Partner) Federation Service 3 Domain B (Resource Partner) Federation Service 2 4 1 Client Web Server with ADFS Web Agent All connections are HTTPS © 2005 Citrix Systems, Inc. —All rights reserved.
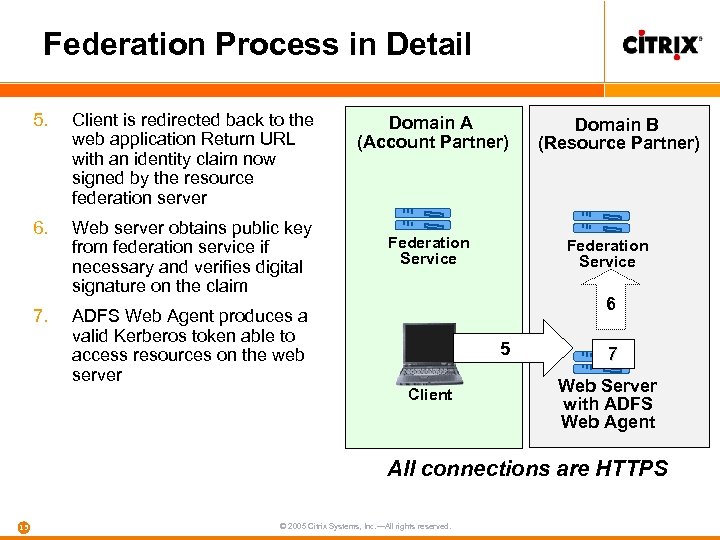 Federation Process in Detail 5. Client is redirected back to the web application Return URL with an identity claim now signed by the resource federation server 6. Web server obtains public key from federation service if necessary and verifies digital signature on the claim 7. ADFS Web Agent produces a valid Kerberos token able to access resources on the web server Domain A (Account Partner) Federation Service Domain B (Resource Partner) Federation Service 6 5 Client 7 Web Server with ADFS Web Agent All connections are HTTPS 15 © 2005 Citrix Systems, Inc. —All rights reserved.
Federation Process in Detail 5. Client is redirected back to the web application Return URL with an identity claim now signed by the resource federation server 6. Web server obtains public key from federation service if necessary and verifies digital signature on the claim 7. ADFS Web Agent produces a valid Kerberos token able to access resources on the web server Domain A (Account Partner) Federation Service Domain B (Resource Partner) Federation Service 6 5 Client 7 Web Server with ADFS Web Agent All connections are HTTPS 15 © 2005 Citrix Systems, Inc. —All rights reserved.
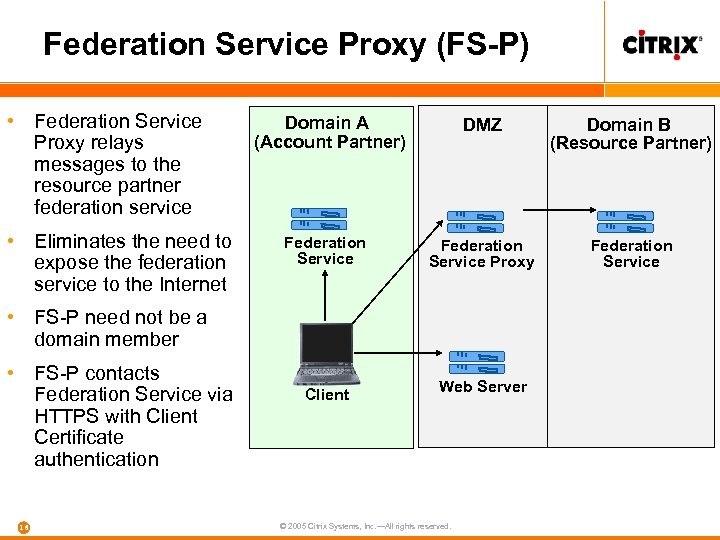 Federation Service Proxy (FS-P) • Federation Service Proxy relays messages to the resource partner federation service • Eliminates the need to expose the federation service to the Internet Domain A (Account Partner) DMZ Domain B (Resource Partner) Federation Service Proxy Federation Service • FS-P need not be a domain member • FS-P contacts Federation Service via HTTPS with Client Certificate authentication 16 Client Web Server © 2005 Citrix Systems, Inc. —All rights reserved.
Federation Service Proxy (FS-P) • Federation Service Proxy relays messages to the resource partner federation service • Eliminates the need to expose the federation service to the Internet Domain A (Account Partner) DMZ Domain B (Resource Partner) Federation Service Proxy Federation Service • FS-P need not be a domain member • FS-P contacts Federation Service via HTTPS with Client Certificate authentication 16 Client Web Server © 2005 Citrix Systems, Inc. —All rights reserved.
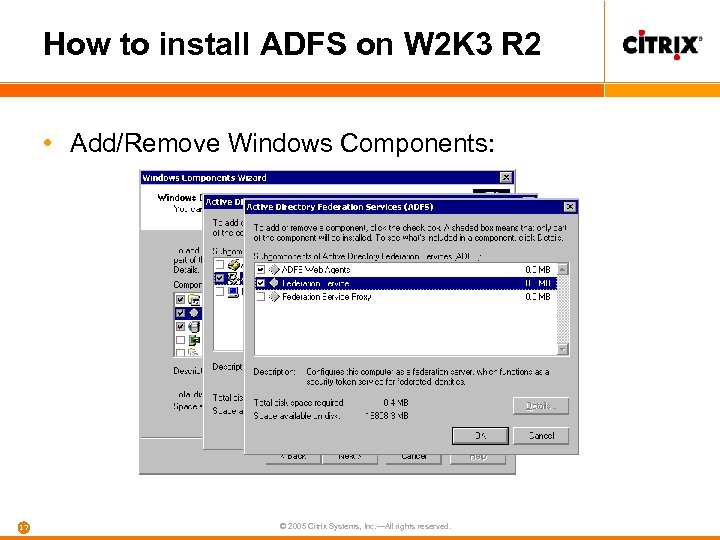 How to install ADFS on W 2 K 3 R 2 • Add/Remove Windows Components: 17 © 2005 Citrix Systems, Inc. —All rights reserved.
How to install ADFS on W 2 K 3 R 2 • Add/Remove Windows Components: 17 © 2005 Citrix Systems, Inc. —All rights reserved.
 Synchronicity • Federation servers at the account partner and resource partner must have their clocks set within 5 minutes of each other • For best results, use an Internet time server such as time. nist. gov • Different time zones don’t matter 18 © 2005 Citrix Systems, Inc. —All rights reserved.
Synchronicity • Federation servers at the account partner and resource partner must have their clocks set within 5 minutes of each other • For best results, use an Internet time server such as time. nist. gov • Different time zones don’t matter 18 © 2005 Citrix Systems, Inc. —All rights reserved.
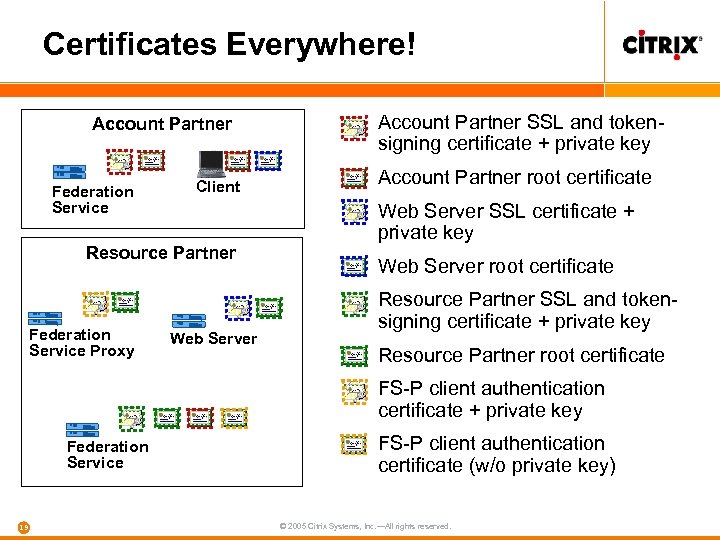 Certificates Everywhere! Account Partner Federation Service Client Resource Partner Federation Service Proxy Web Server Account Partner SSL and tokensigning certificate + private key Account Partner root certificate Web Server SSL certificate + private key Web Server root certificate Resource Partner SSL and tokensigning certificate + private key Resource Partner root certificate FS-P client authentication certificate + private key Federation Service 19 FS-P client authentication certificate (w/o private key) © 2005 Citrix Systems, Inc. —All rights reserved.
Certificates Everywhere! Account Partner Federation Service Client Resource Partner Federation Service Proxy Web Server Account Partner SSL and tokensigning certificate + private key Account Partner root certificate Web Server SSL certificate + private key Web Server root certificate Resource Partner SSL and tokensigning certificate + private key Resource Partner root certificate FS-P client authentication certificate + private key Federation Service 19 FS-P client authentication certificate (w/o private key) © 2005 Citrix Systems, Inc. —All rights reserved.
 Part 2: Web Interface and ADFS
Part 2: Web Interface and ADFS
 Citrix Announces Federation Interoperability Citrix extends federation benefits – To rich applications (e. g. SAP R/3 client, mainframe emulator) – To file shares – To web apps inside the firewall Citrix increases federation security – Provides greater control over data usage – Allows for increased identity assurance – Facilitates access logging and auditing across organizations 21 © 2005 Citrix Systems, Inc. —All rights reserved.
Citrix Announces Federation Interoperability Citrix extends federation benefits – To rich applications (e. g. SAP R/3 client, mainframe emulator) – To file shares – To web apps inside the firewall Citrix increases federation security – Provides greater control over data usage – Allows for increased identity assurance – Facilitates access logging and auditing across organizations 21 © 2005 Citrix Systems, Inc. —All rights reserved.
 Only Citrix can Federate to Windows Applications • Identity federation was designed for web applications only • The ADFS support in Web Interface bridges the gap between web applications and Windows or hostbased applications Citrix uniquely enables federated SSO to Web, Windows and host-based applications 22 © 2005 Citrix Systems, Inc. —All rights reserved.
Only Citrix can Federate to Windows Applications • Identity federation was designed for web applications only • The ADFS support in Web Interface bridges the gap between web applications and Windows or hostbased applications Citrix uniquely enables federated SSO to Web, Windows and host-based applications 22 © 2005 Citrix Systems, Inc. —All rights reserved.
 The User’s Experience • Click on a link to the ADFS WI site • Icons appear without prompting the user • Applications launch without prompting the user 23 © 2005 Citrix Systems, Inc. —All rights reserved.
The User’s Experience • Click on a link to the ADFS WI site • Icons appear without prompting the user • Applications launch without prompting the user 23 © 2005 Citrix Systems, Inc. —All rights reserved.
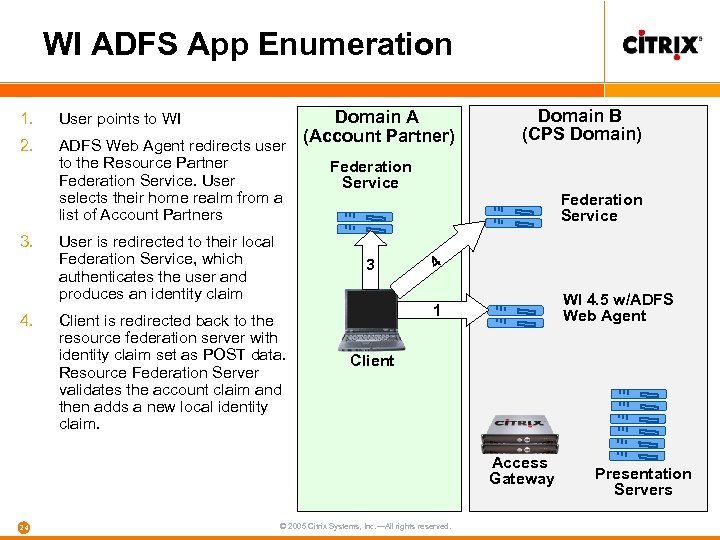 WI ADFS App Enumeration 1. User points to WI 2. ADFS Web Agent redirects user to the Resource Partner Federation Service. User selects their home realm from a list of Account Partners 3. 4. User is redirected to their local Federation Service, which authenticates the user and produces an identity claim Domain A (Account Partner) Federation Service 3 Client is redirected back to the resource federation server with identity claim set as POST data. Resource Federation Server validates the account claim and then adds a new local identity claim. Domain B (CPS Domain) Federation Service 4 2 WI 4. 5 w/ADFS Web Agent 1 Client Access Gateway 24 © 2005 Citrix Systems, Inc. —All rights reserved. Presentation Servers
WI ADFS App Enumeration 1. User points to WI 2. ADFS Web Agent redirects user to the Resource Partner Federation Service. User selects their home realm from a list of Account Partners 3. 4. User is redirected to their local Federation Service, which authenticates the user and produces an identity claim Domain A (Account Partner) Federation Service 3 Client is redirected back to the resource federation server with identity claim set as POST data. Resource Federation Server validates the account claim and then adds a new local identity claim. Domain B (CPS Domain) Federation Service 4 2 WI 4. 5 w/ADFS Web Agent 1 Client Access Gateway 24 © 2005 Citrix Systems, Inc. —All rights reserved. Presentation Servers
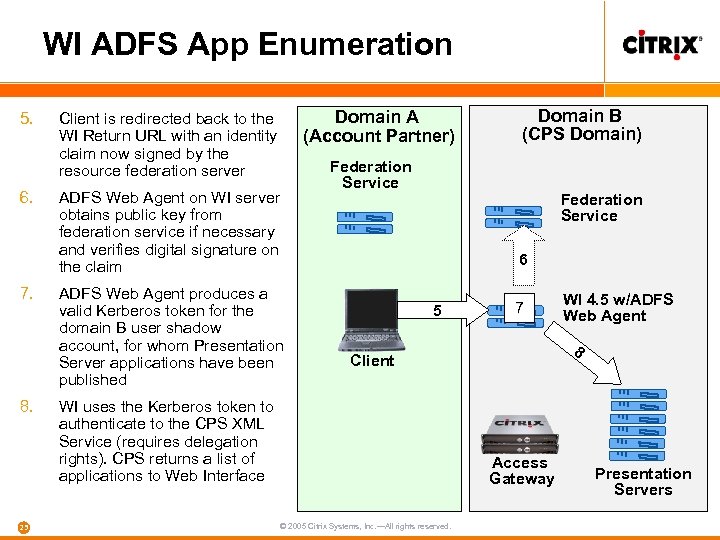 WI ADFS App Enumeration 5. 6. 7. 8. 25 Domain A (Account Partner) Client is redirected back to the WI Return URL with an identity claim now signed by the resource federation server Domain B (CPS Domain) Federation Service ADFS Web Agent on WI server obtains public key from federation service if necessary and verifies digital signature on the claim Federation Service 6 ADFS Web Agent produces a valid Kerberos token for the domain B user shadow account, for whom Presentation Server applications have been published 5 7 8 Client WI uses the Kerberos token to authenticate to the CPS XML Service (requires delegation rights). CPS returns a list of applications to Web Interface Access Gateway © 2005 Citrix Systems, Inc. —All rights reserved. WI 4. 5 w/ADFS Web Agent Presentation Servers
WI ADFS App Enumeration 5. 6. 7. 8. 25 Domain A (Account Partner) Client is redirected back to the WI Return URL with an identity claim now signed by the resource federation server Domain B (CPS Domain) Federation Service ADFS Web Agent on WI server obtains public key from federation service if necessary and verifies digital signature on the claim Federation Service 6 ADFS Web Agent produces a valid Kerberos token for the domain B user shadow account, for whom Presentation Server applications have been published 5 7 8 Client WI uses the Kerberos token to authenticate to the CPS XML Service (requires delegation rights). CPS returns a list of applications to Web Interface Access Gateway © 2005 Citrix Systems, Inc. —All rights reserved. WI 4. 5 w/ADFS Web Agent Presentation Servers
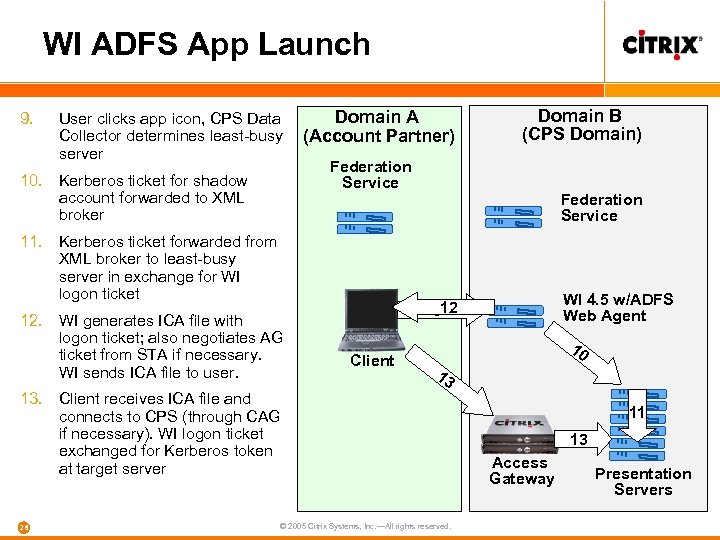 WI ADFS App Launch 9. User clicks app icon, CPS Data Collector determines least-busy server 10. Kerberos ticket for shadow account forwarded to XML broker Domain A (Account Partner) Federation Service 11. Kerberos ticket forwarded from XML broker to least-busy server in exchange for WI logon ticket 12. WI generates ICA file with logon ticket; also negotiates AG ticket from STA if necessary. WI sends ICA file to user. Federation Service WI 4. 5 w/ADFS Web Agent 912 Client 10 13 13. Client receives ICA file and connects to CPS (through CAG if necessary). WI logon ticket exchanged for Kerberos token at target server 26 Domain B (CPS Domain) © 2005 Citrix Systems, Inc. —All rights reserved. 11 13 Access Gateway Presentation Servers
WI ADFS App Launch 9. User clicks app icon, CPS Data Collector determines least-busy server 10. Kerberos ticket for shadow account forwarded to XML broker Domain A (Account Partner) Federation Service 11. Kerberos ticket forwarded from XML broker to least-busy server in exchange for WI logon ticket 12. WI generates ICA file with logon ticket; also negotiates AG ticket from STA if necessary. WI sends ICA file to user. Federation Service WI 4. 5 w/ADFS Web Agent 912 Client 10 13 13. Client receives ICA file and connects to CPS (through CAG if necessary). WI logon ticket exchanged for Kerberos token at target server 26 Domain B (CPS Domain) © 2005 Citrix Systems, Inc. —All rights reserved. 11 13 Access Gateway Presentation Servers
 Requirements • WI and Federation servers must be W 2 K 3 R 2 • CPS 4. 5 or 4. 0 with hotfix rollup #2 or later – Enable “Trust requests sent to the XML Service” • Domain functional level must be native Win 2 K 3 – Domain Controllers need not be upgraded to R 2 • Alternate UPN suffix must be added to the resource domain, and shadow accounts must be created using the partner’s UPN suffix – Usernames and passwords are not known by the user 27 © 2005 Citrix Systems, Inc. —All rights reserved.
Requirements • WI and Federation servers must be W 2 K 3 R 2 • CPS 4. 5 or 4. 0 with hotfix rollup #2 or later – Enable “Trust requests sent to the XML Service” • Domain functional level must be native Win 2 K 3 – Domain Controllers need not be upgraded to R 2 • Alternate UPN suffix must be added to the resource domain, and shadow accounts must be created using the partner’s UPN suffix – Usernames and passwords are not known by the user 27 © 2005 Citrix Systems, Inc. —All rights reserved.
 Constraints • Web Interface server must be a domain member • XML service must be delivered via IIS port sharing • Revocation information for all certificates must be accessible by all parties – Best practice: Use a commercial CA 28 © 2005 Citrix Systems, Inc. —All rights reserved.
Constraints • Web Interface server must be a domain member • XML service must be delivered via IIS port sharing • Revocation information for all certificates must be accessible by all parties – Best practice: Use a commercial CA 28 © 2005 Citrix Systems, Inc. —All rights reserved.
 Part 3: Configuration Walkthrough
Part 3: Configuration Walkthrough
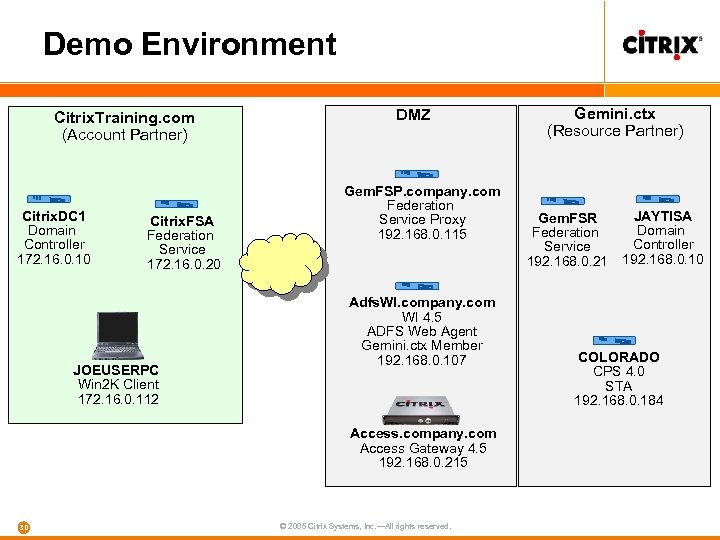 Demo Environment Citrix. Training. com (Account Partner) Citrix. DC 1 Domain Controller 172. 16. 0. 10 Citrix. FSA Federation Service 172. 16. 0. 20 JOEUSERPC Win 2 K Client 172. 16. 0. 112 DMZ Gem. FSP. company. com Federation Service Proxy 192. 168. 0. 115 Adfs. WI. company. com WI 4. 5 ADFS Web Agent Gemini. ctx Member 192. 168. 0. 107 Access. company. com Access Gateway 4. 5 192. 168. 0. 215 30 © 2005 Citrix Systems, Inc. —All rights reserved. Gemini. ctx (Resource Partner) JAYTISA Gem. FSR Domain Federation Controller Service 192. 168. 0. 10 192. 168. 0. 21 COLORADO CPS 4. 0 STA 192. 168. 0. 184
Demo Environment Citrix. Training. com (Account Partner) Citrix. DC 1 Domain Controller 172. 16. 0. 10 Citrix. FSA Federation Service 172. 16. 0. 20 JOEUSERPC Win 2 K Client 172. 16. 0. 112 DMZ Gem. FSP. company. com Federation Service Proxy 192. 168. 0. 115 Adfs. WI. company. com WI 4. 5 ADFS Web Agent Gemini. ctx Member 192. 168. 0. 107 Access. company. com Access Gateway 4. 5 192. 168. 0. 215 30 © 2005 Citrix Systems, Inc. —All rights reserved. Gemini. ctx (Resource Partner) JAYTISA Gem. FSR Domain Federation Controller Service 192. 168. 0. 10 192. 168. 0. 21 COLORADO CPS 4. 0 STA 192. 168. 0. 184
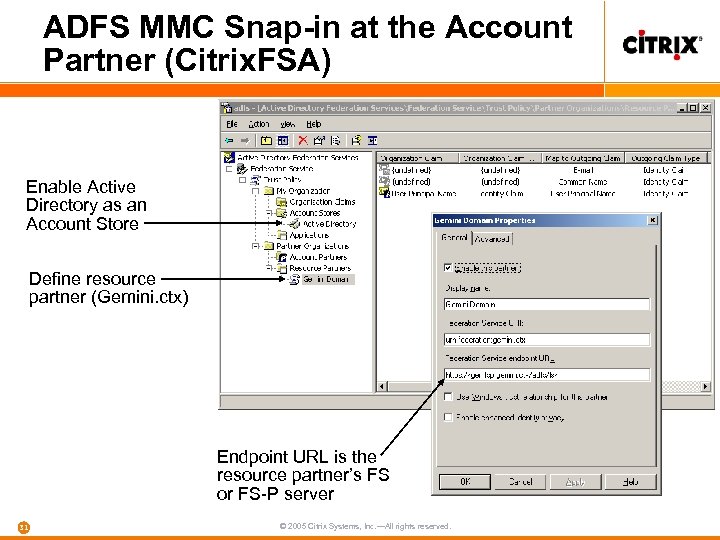 ADFS MMC Snap-in at the Account Partner (Citrix. FSA) Enable Active Directory as an Account Store Define resource partner (Gemini. ctx) Endpoint URL is the resource partner’s FS or FS-P server 31 © 2005 Citrix Systems, Inc. —All rights reserved.
ADFS MMC Snap-in at the Account Partner (Citrix. FSA) Enable Active Directory as an Account Store Define resource partner (Gemini. ctx) Endpoint URL is the resource partner’s FS or FS-P server 31 © 2005 Citrix Systems, Inc. —All rights reserved.
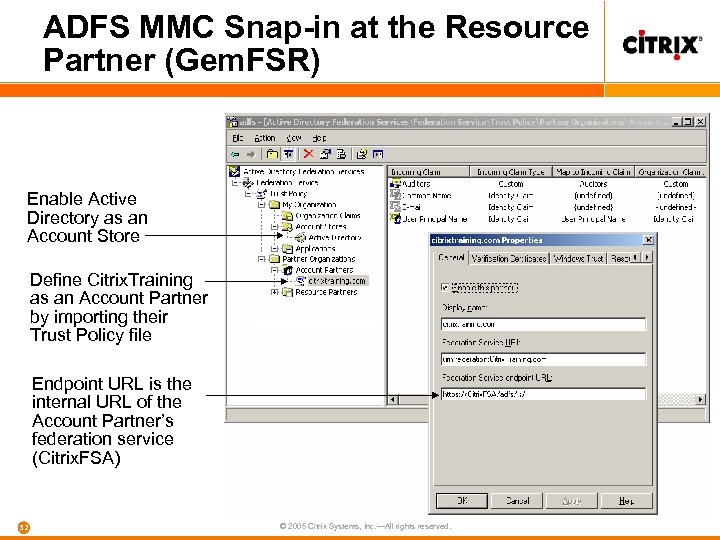 ADFS MMC Snap-in at the Resource Partner (Gem. FSR) Enable Active Directory as an Account Store Define Citrix. Training as an Account Partner by importing their Trust Policy file Endpoint URL is the internal URL of the Account Partner’s federation service (Citrix. FSA) 32 © 2005 Citrix Systems, Inc. —All rights reserved.
ADFS MMC Snap-in at the Resource Partner (Gem. FSR) Enable Active Directory as an Account Store Define Citrix. Training as an Account Partner by importing their Trust Policy file Endpoint URL is the internal URL of the Account Partner’s federation service (Citrix. FSA) 32 © 2005 Citrix Systems, Inc. —All rights reserved.
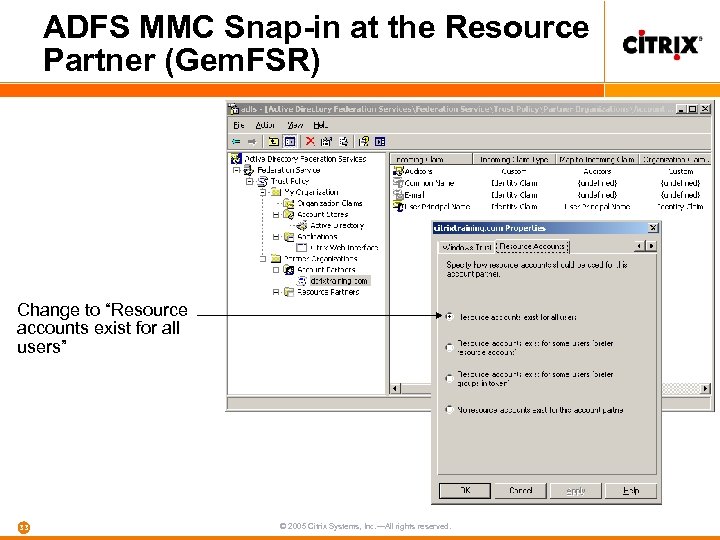 ADFS MMC Snap-in at the Resource Partner (Gem. FSR) Change to “Resource accounts exist for all users” 33 © 2005 Citrix Systems, Inc. —All rights reserved.
ADFS MMC Snap-in at the Resource Partner (Gem. FSR) Change to “Resource accounts exist for all users” 33 © 2005 Citrix Systems, Inc. —All rights reserved.
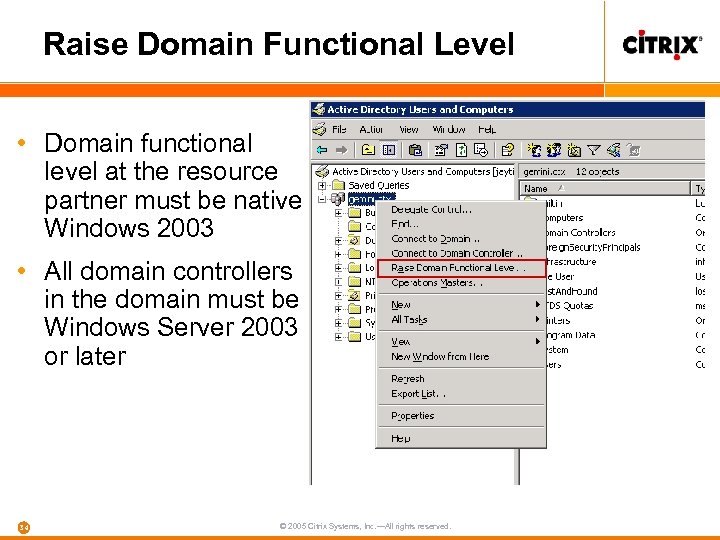 Raise Domain Functional Level • Domain functional level at the resource partner must be native Windows 2003 • All domain controllers in the domain must be Windows Server 2003 or later 34 © 2005 Citrix Systems, Inc. —All rights reserved.
Raise Domain Functional Level • Domain functional level at the resource partner must be native Windows 2003 • All domain controllers in the domain must be Windows Server 2003 or later 34 © 2005 Citrix Systems, Inc. —All rights reserved.
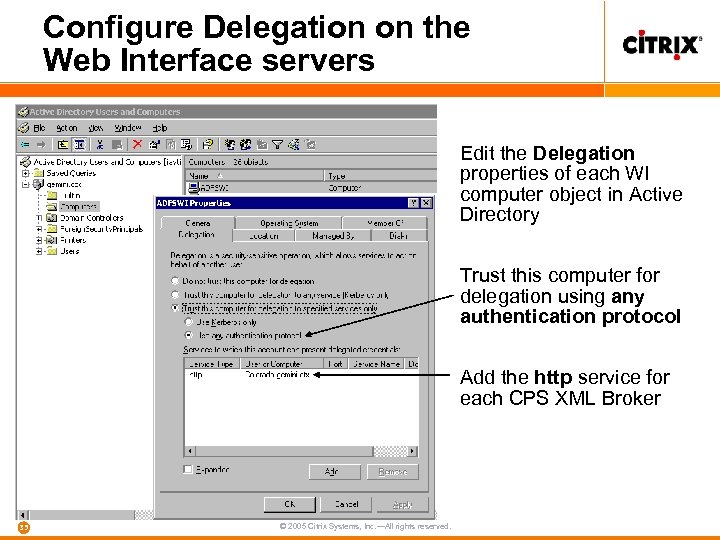 Configure Delegation on the Web Interface servers Edit the Delegation properties of each WI computer object in Active Directory Trust this computer for delegation using any authentication protocol Add the http service for each CPS XML Broker 35 © 2005 Citrix Systems, Inc. —All rights reserved.
Configure Delegation on the Web Interface servers Edit the Delegation properties of each WI computer object in Active Directory Trust this computer for delegation using any authentication protocol Add the http service for each CPS XML Broker 35 © 2005 Citrix Systems, Inc. —All rights reserved.
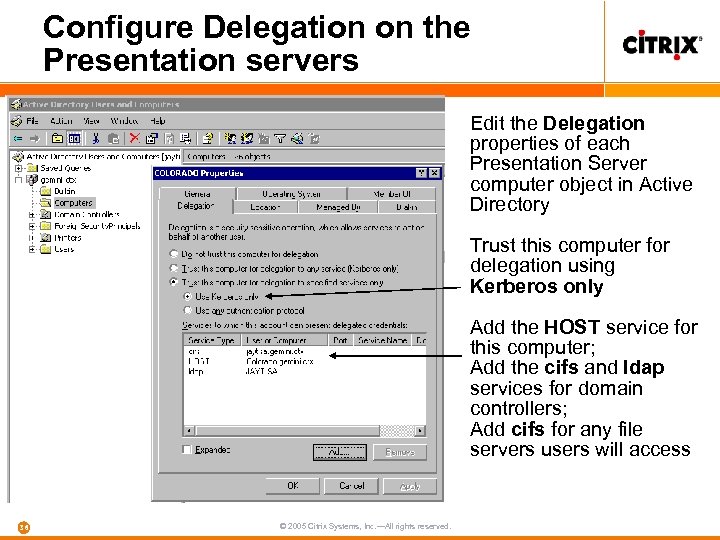 Configure Delegation on the Presentation servers Edit the Delegation properties of each Presentation Server computer object in Active Directory Trust this computer for delegation using Kerberos only Add the HOST service for this computer; Add the cifs and ldap services for domain controllers; Add cifs for any file servers users will access 36 © 2005 Citrix Systems, Inc. —All rights reserved.
Configure Delegation on the Presentation servers Edit the Delegation properties of each Presentation Server computer object in Active Directory Trust this computer for delegation using Kerberos only Add the HOST service for this computer; Add the cifs and ldap services for domain controllers; Add cifs for any file servers users will access 36 © 2005 Citrix Systems, Inc. —All rights reserved.
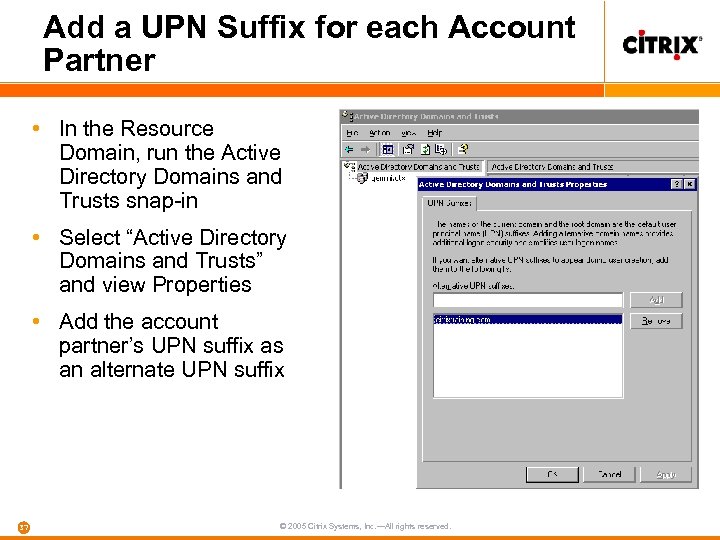 Add a UPN Suffix for each Account Partner • In the Resource Domain, run the Active Directory Domains and Trusts snap-in • Select “Active Directory Domains and Trusts” and view Properties • Add the account partner’s UPN suffix as an alternate UPN suffix 37 © 2005 Citrix Systems, Inc. —All rights reserved.
Add a UPN Suffix for each Account Partner • In the Resource Domain, run the Active Directory Domains and Trusts snap-in • Select “Active Directory Domains and Trusts” and view Properties • Add the account partner’s UPN suffix as an alternate UPN suffix 37 © 2005 Citrix Systems, Inc. —All rights reserved.
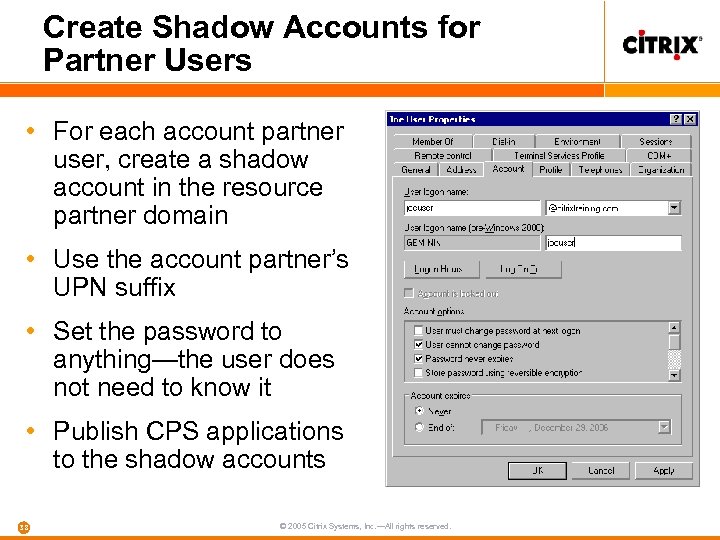 Create Shadow Accounts for Partner Users • For each account partner user, create a shadow account in the resource partner domain • Use the account partner’s UPN suffix • Set the password to anything—the user does not need to know it • Publish CPS applications to the shadow accounts 38 © 2005 Citrix Systems, Inc. —All rights reserved.
Create Shadow Accounts for Partner Users • For each account partner user, create a shadow account in the resource partner domain • Use the account partner’s UPN suffix • Set the password to anything—the user does not need to know it • Publish CPS applications to the shadow accounts 38 © 2005 Citrix Systems, Inc. —All rights reserved.
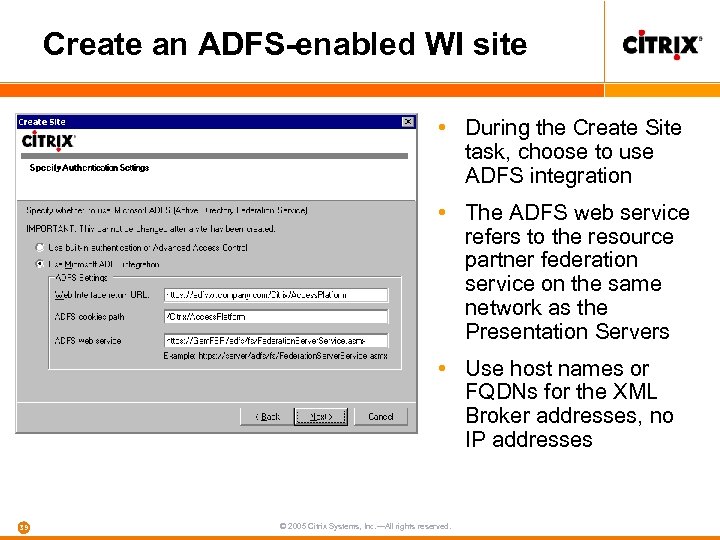 Create an ADFS-enabled WI site • During the Create Site task, choose to use ADFS integration • The ADFS web service refers to the resource partner federation service on the same network as the Presentation Servers • Use host names or FQDNs for the XML Broker addresses, no IP addresses 39 © 2005 Citrix Systems, Inc. —All rights reserved.
Create an ADFS-enabled WI site • During the Create Site task, choose to use ADFS integration • The ADFS web service refers to the resource partner federation service on the same network as the Presentation Servers • Use host names or FQDNs for the XML Broker addresses, no IP addresses 39 © 2005 Citrix Systems, Inc. —All rights reserved.
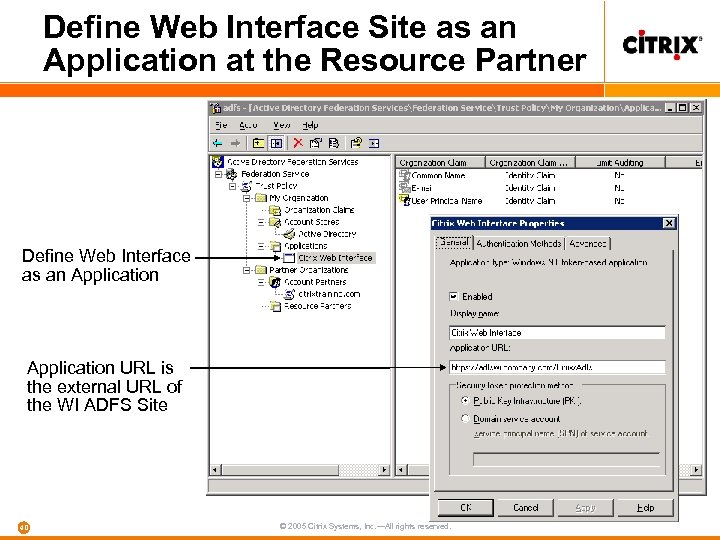 Define Web Interface Site as an Application at the Resource Partner Define Web Interface as an Application URL is the external URL of the WI ADFS Site 40 © 2005 Citrix Systems, Inc. —All rights reserved.
Define Web Interface Site as an Application at the Resource Partner Define Web Interface as an Application URL is the external URL of the WI ADFS Site 40 © 2005 Citrix Systems, Inc. —All rights reserved.
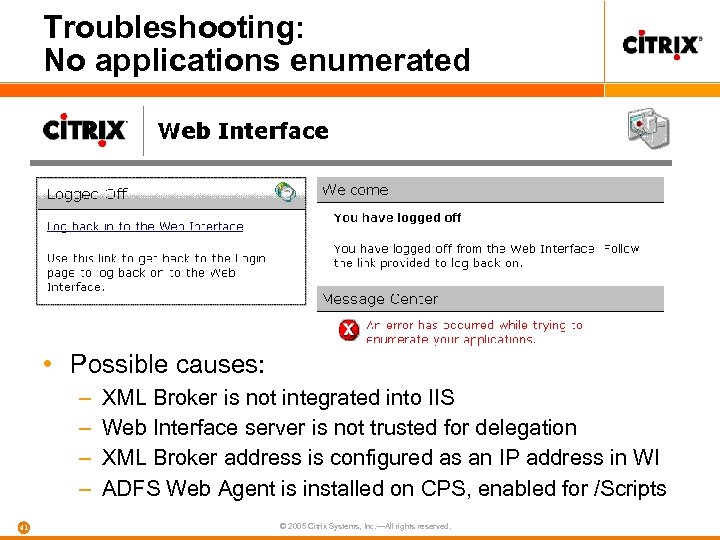 Troubleshooting: No applications enumerated • Possible causes: – – 41 XML Broker is not integrated into IIS Web Interface server is not trusted for delegation XML Broker address is configured as an IP address in WI ADFS Web Agent is installed on CPS, enabled for /Scripts © 2005 Citrix Systems, Inc. —All rights reserved.
Troubleshooting: No applications enumerated • Possible causes: – – 41 XML Broker is not integrated into IIS Web Interface server is not trusted for delegation XML Broker address is configured as an IP address in WI ADFS Web Agent is installed on CPS, enabled for /Scripts © 2005 Citrix Systems, Inc. —All rights reserved.
 Part 4: Deployment Scenarios
Part 4: Deployment Scenarios
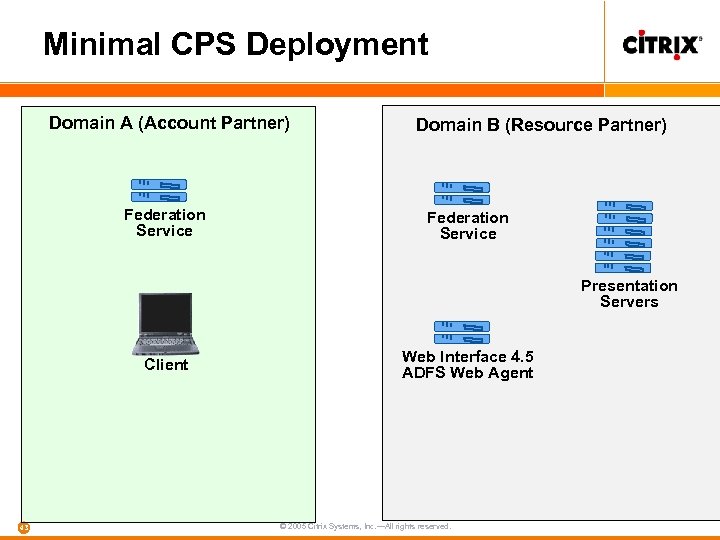 Minimal CPS Deployment Domain A (Account Partner) Federation Service Domain B (Resource Partner) Federation Service Presentation Servers Client 43 Web Interface 4. 5 ADFS Web Agent © 2005 Citrix Systems, Inc. —All rights reserved.
Minimal CPS Deployment Domain A (Account Partner) Federation Service Domain B (Resource Partner) Federation Service Presentation Servers Client 43 Web Interface 4. 5 ADFS Web Agent © 2005 Citrix Systems, Inc. —All rights reserved.
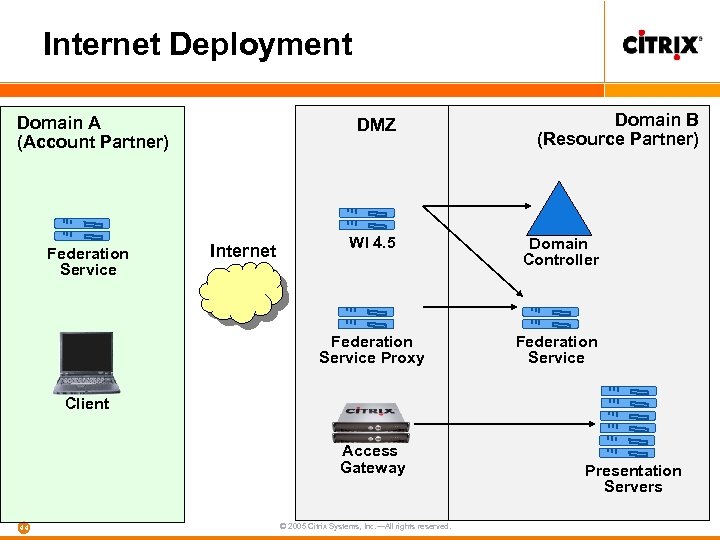 Internet Deployment Domain A (Account Partner) DMZ Domain B (Resource Partner) Internet WI 4. 5 Domain Controller Federation Service Proxy Federation Service Client Access Gateway 44 © 2005 Citrix Systems, Inc. —All rights reserved. Presentation Servers
Internet Deployment Domain A (Account Partner) DMZ Domain B (Resource Partner) Internet WI 4. 5 Domain Controller Federation Service Proxy Federation Service Client Access Gateway 44 © 2005 Citrix Systems, Inc. —All rights reserved. Presentation Servers
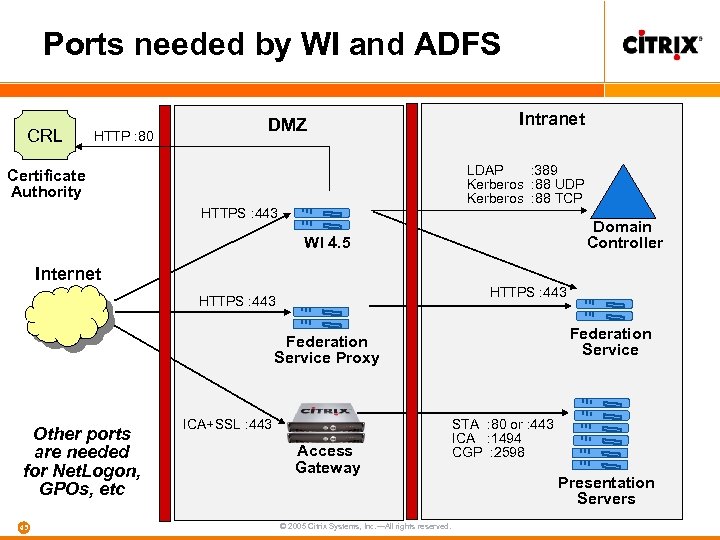 Ports needed by WI and ADFS CRL HTTP : 80 DMZ Intranet LDAP : 389 Kerberos : 88 UDP Kerberos : 88 TCP Certificate Authority HTTPS : 443 Domain Controller WI 4. 5 Internet HTTPS : 443 Federation Service Proxy Other ports are needed for Net. Logon, GPOs, etc 45 ICA+SSL : 443 Access Gateway © 2005 Citrix Systems, Inc. —All rights reserved. STA : 80 or : 443 ICA : 1494 CGP : 2598 Presentation Servers
Ports needed by WI and ADFS CRL HTTP : 80 DMZ Intranet LDAP : 389 Kerberos : 88 UDP Kerberos : 88 TCP Certificate Authority HTTPS : 443 Domain Controller WI 4. 5 Internet HTTPS : 443 Federation Service Proxy Other ports are needed for Net. Logon, GPOs, etc 45 ICA+SSL : 443 Access Gateway © 2005 Citrix Systems, Inc. —All rights reserved. STA : 80 or : 443 ICA : 1494 CGP : 2598 Presentation Servers
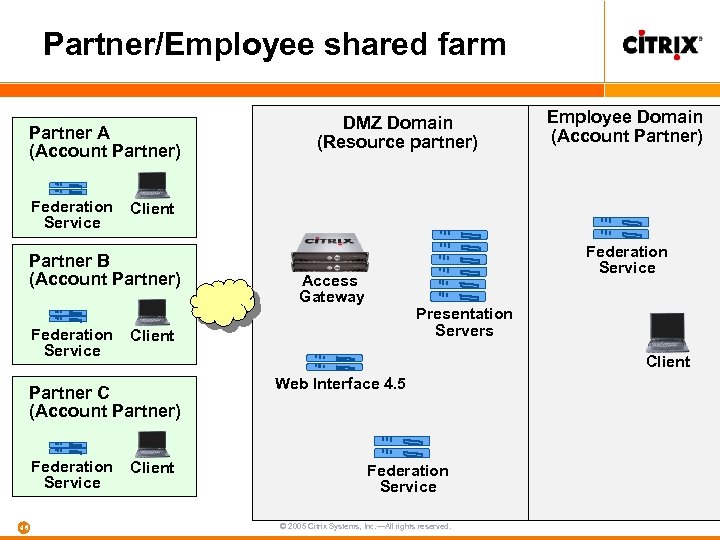 Partner/Employee shared farm Partner A (Account Partner) Federation Service 46 Federation Service Access Gateway Presentation Servers Client Partner C (Account Partner) Federation Service Employee Domain (Account Partner) Client Partner B (Account Partner) Federation Service DMZ Domain (Resource partner) Client Web Interface 4. 5 Federation Service © 2005 Citrix Systems, Inc. —All rights reserved.
Partner/Employee shared farm Partner A (Account Partner) Federation Service 46 Federation Service Access Gateway Presentation Servers Client Partner C (Account Partner) Federation Service Employee Domain (Account Partner) Client Partner B (Account Partner) Federation Service DMZ Domain (Resource partner) Client Web Interface 4. 5 Federation Service © 2005 Citrix Systems, Inc. —All rights reserved.
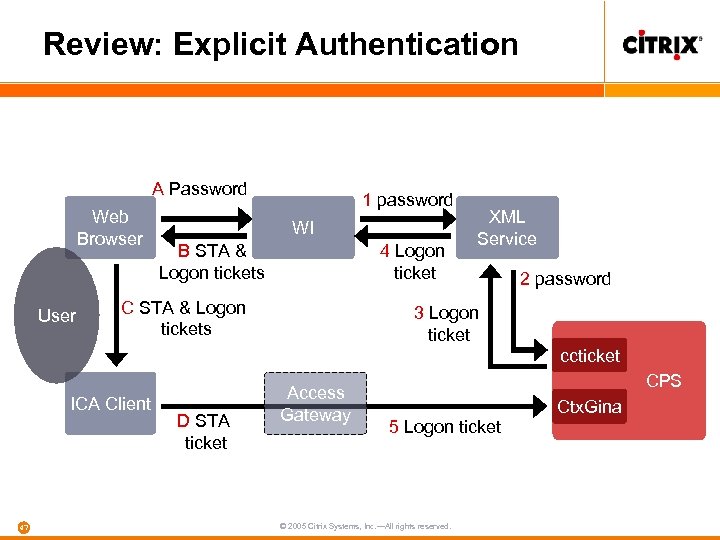 Review: Explicit Authentication A Password Web Browser User 1 password WI B STA & Logon tickets 4 Logon ticket C STA & Logon tickets XML Service 2 password 3 Logon ticket ccticket ICA Client 47 D STA ticket Access Gateway CPS 5 Logon ticket © 2005 Citrix Systems, Inc. —All rights reserved. Ctx. Gina
Review: Explicit Authentication A Password Web Browser User 1 password WI B STA & Logon tickets 4 Logon ticket C STA & Logon tickets XML Service 2 password 3 Logon ticket ccticket ICA Client 47 D STA ticket Access Gateway CPS 5 Logon ticket © 2005 Citrix Systems, Inc. —All rights reserved. Ctx. Gina
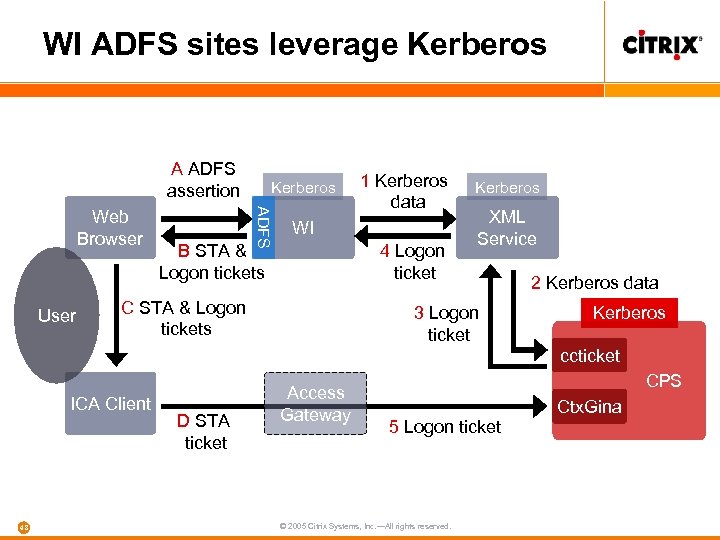 WI ADFS sites leverage Kerberos A ADFS assertion User ADFS Web Browser Kerberos 1 Kerberos data WI B STA & Logon tickets 4 Logon ticket C STA & Logon tickets Kerberos XML Service 3 Logon ticket 2 Kerberos data Kerberos ccticket ICA Client 48 D STA ticket Access Gateway CPS 5 Logon ticket © 2005 Citrix Systems, Inc. —All rights reserved. Ctx. Gina
WI ADFS sites leverage Kerberos A ADFS assertion User ADFS Web Browser Kerberos 1 Kerberos data WI B STA & Logon tickets 4 Logon ticket C STA & Logon tickets Kerberos XML Service 3 Logon ticket 2 Kerberos data Kerberos ccticket ICA Client 48 D STA ticket Access Gateway CPS 5 Logon ticket © 2005 Citrix Systems, Inc. —All rights reserved. Ctx. Gina
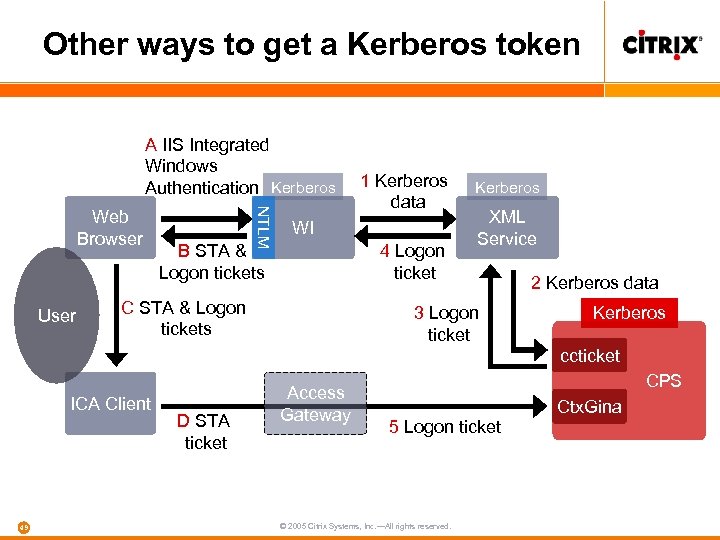 Other ways to get a Kerberos token A IIS Integrated Windows Authentication Kerberos User NTLM Web Browser 1 Kerberos data WI B STA & Logon tickets 4 Logon ticket C STA & Logon tickets Kerberos XML Service 3 Logon ticket 2 Kerberos data Kerberos ccticket ICA Client 49 D STA ticket Access Gateway CPS 5 Logon ticket © 2005 Citrix Systems, Inc. —All rights reserved. Ctx. Gina
Other ways to get a Kerberos token A IIS Integrated Windows Authentication Kerberos User NTLM Web Browser 1 Kerberos data WI B STA & Logon tickets 4 Logon ticket C STA & Logon tickets Kerberos XML Service 3 Logon ticket 2 Kerberos data Kerberos ccticket ICA Client 49 D STA ticket Access Gateway CPS 5 Logon ticket © 2005 Citrix Systems, Inc. —All rights reserved. Ctx. Gina
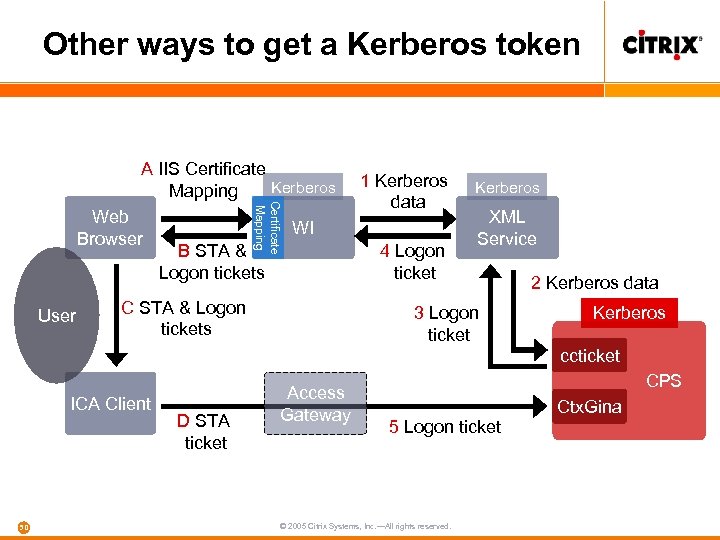 Other ways to get a Kerberos token Web Browser User Certificate Mapping A IIS Certificate Kerberos Mapping 1 Kerberos data WI B STA & Logon tickets C STA & Logon tickets 4 Logon ticket Kerberos XML Service 3 Logon ticket 2 Kerberos data Kerberos ccticket ICA Client 50 D STA ticket Access Gateway CPS 5 Logon ticket © 2005 Citrix Systems, Inc. —All rights reserved. Ctx. Gina
Other ways to get a Kerberos token Web Browser User Certificate Mapping A IIS Certificate Kerberos Mapping 1 Kerberos data WI B STA & Logon tickets C STA & Logon tickets 4 Logon ticket Kerberos XML Service 3 Logon ticket 2 Kerberos data Kerberos ccticket ICA Client 50 D STA ticket Access Gateway CPS 5 Logon ticket © 2005 Citrix Systems, Inc. —All rights reserved. Ctx. Gina
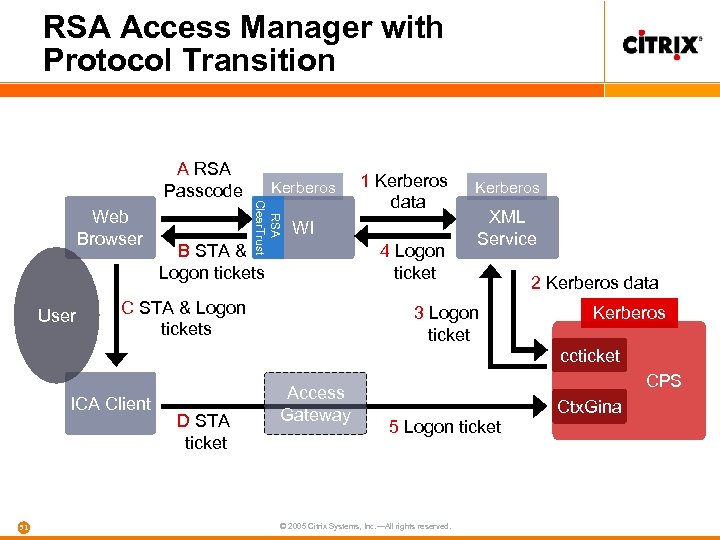 RSA Access Manager with Protocol Transition Web Browser User Kerberos RSA Clear. Trust A RSA Passcode 1 Kerberos data WI B STA & Logon tickets C STA & Logon tickets 4 Logon ticket Kerberos XML Service 3 Logon ticket 2 Kerberos data Kerberos ccticket ICA Client 51 D STA ticket Access Gateway CPS 5 Logon ticket © 2005 Citrix Systems, Inc. —All rights reserved. Ctx. Gina
RSA Access Manager with Protocol Transition Web Browser User Kerberos RSA Clear. Trust A RSA Passcode 1 Kerberos data WI B STA & Logon tickets C STA & Logon tickets 4 Logon ticket Kerberos XML Service 3 Logon ticket 2 Kerberos data Kerberos ccticket ICA Client 51 D STA ticket Access Gateway CPS 5 Logon ticket © 2005 Citrix Systems, Inc. —All rights reserved. Ctx. Gina
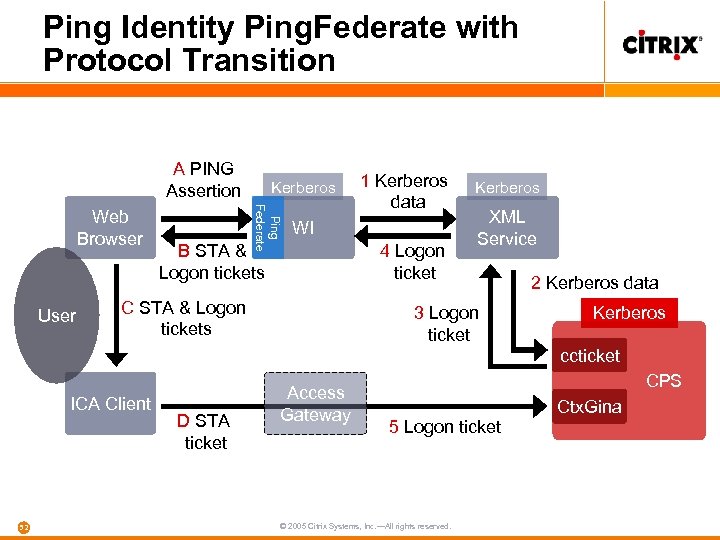 Ping Identity Ping. Federate with Protocol Transition A PING Assertion User Ping Federate Web Browser Kerberos 1 Kerberos data WI B STA & Logon tickets C STA & Logon tickets 4 Logon ticket Kerberos XML Service 3 Logon ticket 2 Kerberos data Kerberos ccticket ICA Client 52 D STA ticket Access Gateway CPS 5 Logon ticket © 2005 Citrix Systems, Inc. —All rights reserved. Ctx. Gina
Ping Identity Ping. Federate with Protocol Transition A PING Assertion User Ping Federate Web Browser Kerberos 1 Kerberos data WI B STA & Logon tickets C STA & Logon tickets 4 Logon ticket Kerberos XML Service 3 Logon ticket 2 Kerberos data Kerberos ccticket ICA Client 52 D STA ticket Access Gateway CPS 5 Logon ticket © 2005 Citrix Systems, Inc. —All rights reserved. Ctx. Gina
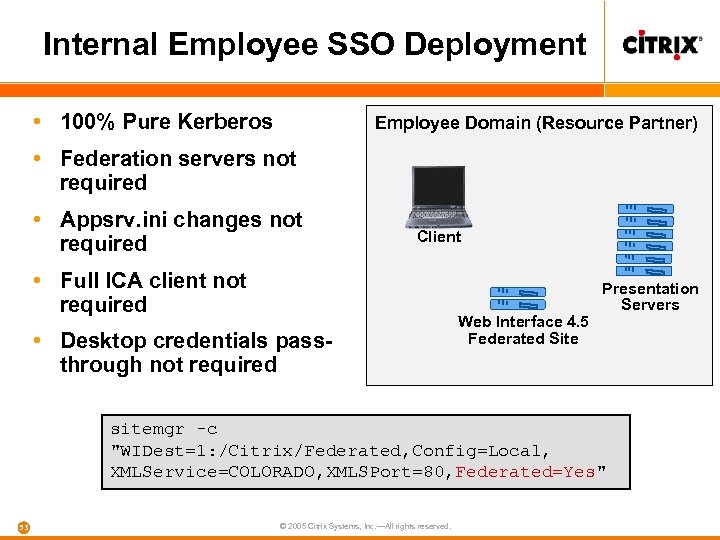 Internal Employee SSO Deployment • 100% Pure Kerberos Employee Domain (Resource Partner) • Federation servers not required • Appsrv. ini changes not required Client • Full ICA client not required • Desktop credentials passthrough not required Web Interface 4. 5 Federated Site Presentation Servers sitemgr -c "WIDest=1: /Citrix/Federated, Config=Local, XMLService=COLORADO, XMLSPort=80, Federated=Yes" 53 © 2005 Citrix Systems, Inc. —All rights reserved.
Internal Employee SSO Deployment • 100% Pure Kerberos Employee Domain (Resource Partner) • Federation servers not required • Appsrv. ini changes not required Client • Full ICA client not required • Desktop credentials passthrough not required Web Interface 4. 5 Federated Site Presentation Servers sitemgr -c "WIDest=1: /Citrix/Federated, Config=Local, XMLService=COLORADO, XMLSPort=80, Federated=Yes" 53 © 2005 Citrix Systems, Inc. —All rights reserved.
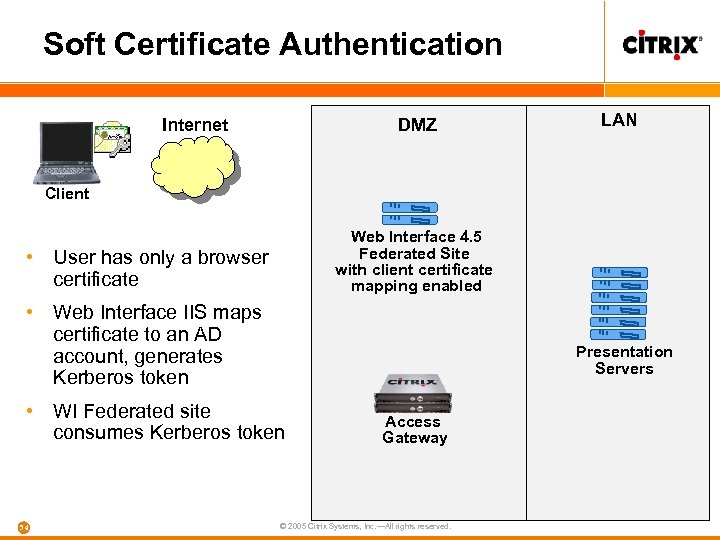 Soft Certificate Authentication DMZ Internet LAN Client Web Interface 4. 5 Federated Site with client certificate mapping enabled • User has only a browser certificate • Web Interface IIS maps certificate to an AD account, generates Kerberos token Presentation Servers • WI Federated site consumes Kerberos token 54 Access Gateway © 2005 Citrix Systems, Inc. —All rights reserved.
Soft Certificate Authentication DMZ Internet LAN Client Web Interface 4. 5 Federated Site with client certificate mapping enabled • User has only a browser certificate • Web Interface IIS maps certificate to an AD account, generates Kerberos token Presentation Servers • WI Federated site consumes Kerberos token 54 Access Gateway © 2005 Citrix Systems, Inc. —All rights reserved.
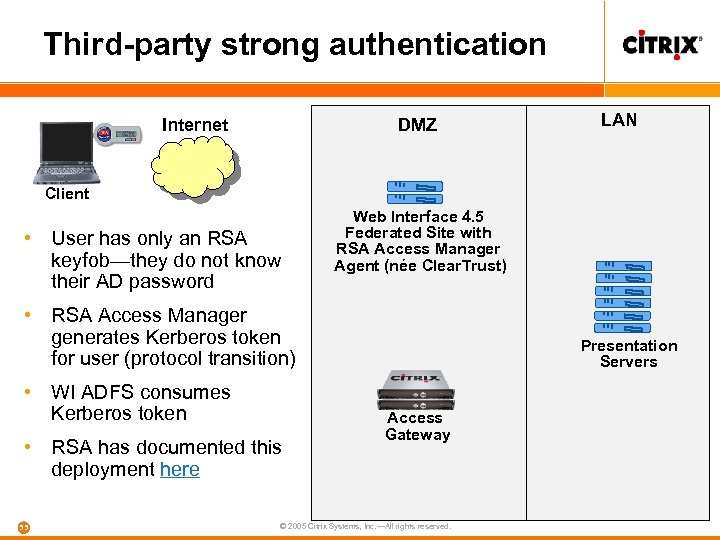 Third-party strong authentication DMZ Internet LAN Client • User has only an RSA keyfob—they do not know their AD password Web Interface 4. 5 Federated Site with RSA Access Manager Agent (née Clear. Trust) • RSA Access Manager generates Kerberos token for user (protocol transition) • WI ADFS consumes Kerberos token • RSA has documented this deployment here 55 Presentation Servers Access Gateway © 2005 Citrix Systems, Inc. —All rights reserved.
Third-party strong authentication DMZ Internet LAN Client • User has only an RSA keyfob—they do not know their AD password Web Interface 4. 5 Federated Site with RSA Access Manager Agent (née Clear. Trust) • RSA Access Manager generates Kerberos token for user (protocol transition) • WI ADFS consumes Kerberos token • RSA has documented this deployment here 55 Presentation Servers Access Gateway © 2005 Citrix Systems, Inc. —All rights reserved.
 Other product integrations • Secure Gateway or Access Gateway can be used to proxy ICA traffic – But don’t proxy HTTPS into the LAN • Password Manager 4. 5 CPS agent functions properly with Kerberos logons (blank password; uses Data Protection API instead) • Net. Scaler can load-balance multiple WI servers, Federation servers, or Federation Proxy servers 56 © 2005 Citrix Systems, Inc. —All rights reserved.
Other product integrations • Secure Gateway or Access Gateway can be used to proxy ICA traffic – But don’t proxy HTTPS into the LAN • Password Manager 4. 5 CPS agent functions properly with Kerberos logons (blank password; uses Data Protection API instead) • Net. Scaler can load-balance multiple WI servers, Federation servers, or Federation Proxy servers 56 © 2005 Citrix Systems, Inc. —All rights reserved.
 High Availability • Use Netscaler to load-balance multiple WI servers, Federation Service Proxies, and Federation Services • Web Interface is stateful, so persistence is required • Federation Service and Federation Service Proxy servers are stateless • Endpoint URLs and application URLs can be FQDNs that map to a virtual IP 57 © 2005 Citrix Systems, Inc. —All rights reserved.
High Availability • Use Netscaler to load-balance multiple WI servers, Federation Service Proxies, and Federation Services • Web Interface is stateful, so persistence is required • Federation Service and Federation Service Proxy servers are stateless • Endpoint URLs and application URLs can be FQDNs that map to a virtual IP 57 © 2005 Citrix Systems, Inc. —All rights reserved.
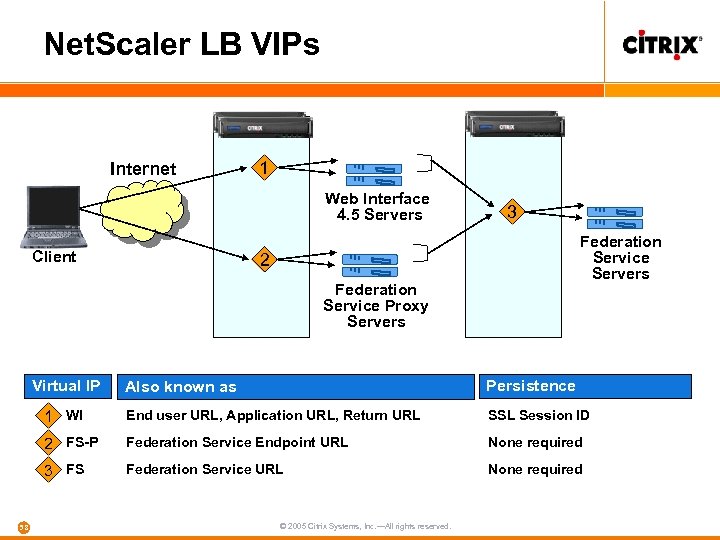 Net. Scaler LB VIPs Internet 1 Web Interface 4. 5 Servers Client 3 Federation Service Servers 2 Federation Service Proxy Servers Virtual IP Persistence 1 WI End user URL, Application URL, Return URL SSL Session ID 2 FS-P Federation Service Endpoint URL None required 3 FS 58 Also known as Federation Service URL None required © 2005 Citrix Systems, Inc. —All rights reserved.
Net. Scaler LB VIPs Internet 1 Web Interface 4. 5 Servers Client 3 Federation Service Servers 2 Federation Service Proxy Servers Virtual IP Persistence 1 WI End user URL, Application URL, Return URL SSL Session ID 2 FS-P Federation Service Endpoint URL None required 3 FS 58 Also known as Federation Service URL None required © 2005 Citrix Systems, Inc. —All rights reserved.
 Current Issues and pain points • Web Interface must be a member of the resource domain • No ADFS-enabled reverse proxy in Access Gateway, so Web Interface must reside in the DMZ • Applications which should be filtered out due to Access Control filters are not filtered out. – CPS 4. 0 XML Service issue; will be fixed in CPS 4. 5 – Users are correctly refused access if they try to connect, but the icon should not appear in the application list • Delegation must be configured for every Web Interface and Presentation Server, a chore for large farms 59 © 2005 Citrix Systems, Inc. —All rights reserved.
Current Issues and pain points • Web Interface must be a member of the resource domain • No ADFS-enabled reverse proxy in Access Gateway, so Web Interface must reside in the DMZ • Applications which should be filtered out due to Access Control filters are not filtered out. – CPS 4. 0 XML Service issue; will be fixed in CPS 4. 5 – Users are correctly refused access if they try to connect, but the icon should not appear in the application list • Delegation must be configured for every Web Interface and Presentation Server, a chore for large farms 59 © 2005 Citrix Systems, Inc. —All rights reserved.
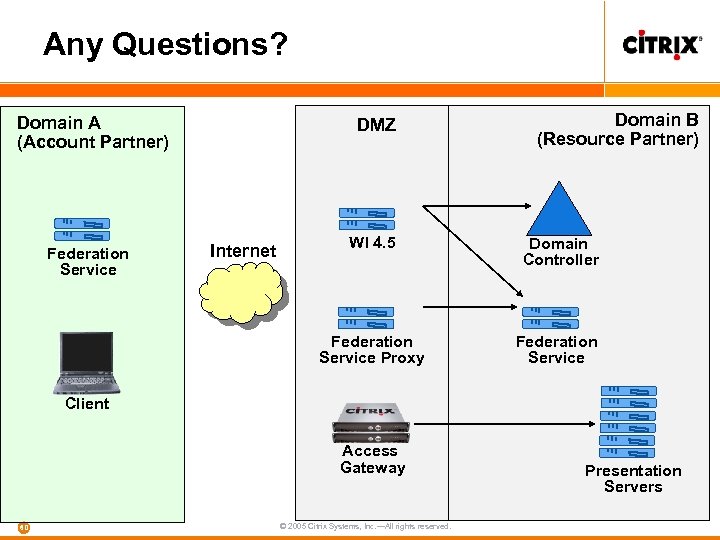 Any Questions? Domain A (Account Partner) DMZ Domain B (Resource Partner) Internet WI 4. 5 Domain Controller Federation Service Proxy Federation Service Client Access Gateway 60 © 2005 Citrix Systems, Inc. —All rights reserved. Presentation Servers
Any Questions? Domain A (Account Partner) DMZ Domain B (Resource Partner) Internet WI 4. 5 Domain Controller Federation Service Proxy Federation Service Client Access Gateway 60 © 2005 Citrix Systems, Inc. —All rights reserved. Presentation Servers
 Good Reading/Viewing • ADFS Tech. Center • Troubleshooting Kerberos Delegation • Don Schmidt ADFS seminar • Web Interface with ADFS Support Admin Guide • Web Interface with ADFS Support FAQ • RSA Secured Implementation Guide For Portal Servers and Web-Based Applications http: //technet 2. microsoft. com/windowsserver/en/technologies/featured/adfs/default. mspx http: //www. microsoft. com/technet/prodtechnol/windowsserver 2003/technologies/security/tkerbdel. mspx http: //www. microsoft. com/emea/itsshowtime/sessionl. aspx? videoid=78 http: //support. citrix. com/article/CTX 109702 http: //support. citrix. com/article/CTX 110118 http: //rsasecurity. agora. com/rsasecured/guides/cleartrust/Citrix_Web_Interface_4_CT 553. pdf • ADFS Forum on support. citrix. com • How to Install Web Interface 4. 0 for ADFS on Servers without ADFS (Advanced Kerberos support only) http: //support. citrix. com/forums/forum. jspa? forum. ID=112 http: //support. citrix. com/article/CTX 110392 61 © 2005 Citrix Systems, Inc. —All rights reserved.
Good Reading/Viewing • ADFS Tech. Center • Troubleshooting Kerberos Delegation • Don Schmidt ADFS seminar • Web Interface with ADFS Support Admin Guide • Web Interface with ADFS Support FAQ • RSA Secured Implementation Guide For Portal Servers and Web-Based Applications http: //technet 2. microsoft. com/windowsserver/en/technologies/featured/adfs/default. mspx http: //www. microsoft. com/technet/prodtechnol/windowsserver 2003/technologies/security/tkerbdel. mspx http: //www. microsoft. com/emea/itsshowtime/sessionl. aspx? videoid=78 http: //support. citrix. com/article/CTX 109702 http: //support. citrix. com/article/CTX 110118 http: //rsasecurity. agora. com/rsasecured/guides/cleartrust/Citrix_Web_Interface_4_CT 553. pdf • ADFS Forum on support. citrix. com • How to Install Web Interface 4. 0 for ADFS on Servers without ADFS (Advanced Kerberos support only) http: //support. citrix. com/forums/forum. jspa? forum. ID=112 http: //support. citrix. com/article/CTX 110392 61 © 2005 Citrix Systems, Inc. —All rights reserved.
 62
62


