3a23789bb3453e56c2165775709caa77.ppt
- Количество слайдов: 15
 Cisco Security Conversion Tool (SCT) Check Point™ to Cisco Conversion Tool Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 1
Cisco Security Conversion Tool (SCT) Check Point™ to Cisco Conversion Tool Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 1
 Cisco Security Conversion Tool (SCT) Overview • Tool to convert a Check Point configuration to a Cisco ASA/PIX/FWSM configuration. • Creates a Cisco device configuration that can be managed with CLI, PDM, ASDM or Cisco Security Manager. • Provides an option to optimize the ACL rule table when used in Cisco Security Manager or ASDM 5. 2 or higher. • Make the tool available at no cost to customers, Cisco SE’s, Advanced Services, and Cisco Security Partners. Note: The output from this tool should be manually reviewed to verify the accuracy and completeness of the conversion. Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 2
Cisco Security Conversion Tool (SCT) Overview • Tool to convert a Check Point configuration to a Cisco ASA/PIX/FWSM configuration. • Creates a Cisco device configuration that can be managed with CLI, PDM, ASDM or Cisco Security Manager. • Provides an option to optimize the ACL rule table when used in Cisco Security Manager or ASDM 5. 2 or higher. • Make the tool available at no cost to customers, Cisco SE’s, Advanced Services, and Cisco Security Partners. Note: The output from this tool should be manually reviewed to verify the accuracy and completeness of the conversion. Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 2
 SCT Benefits • Reduced time to convert from Check Point to Cisco firewalls. • Increased accuracy in the conversion from Check Point to Cisco firewalls. • Allows you to use Cisco TAC for questions/support on their new Cisco firewalls. • Optimized option to convert from Check Point to the new Cisco Security Manager. • Increased traceability since inline comments are created to indicate which Check Point commands correlate to which Cisco commands. • Automated report that summarizes the conversion process. Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 3
SCT Benefits • Reduced time to convert from Check Point to Cisco firewalls. • Increased accuracy in the conversion from Check Point to Cisco firewalls. • Allows you to use Cisco TAC for questions/support on their new Cisco firewalls. • Optimized option to convert from Check Point to the new Cisco Security Manager. • Increased traceability since inline comments are created to indicate which Check Point commands correlate to which Cisco commands. • Automated report that summarizes the conversion process. Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 3
 Note • Several assumptions are made during the conversion process since Check Point and Cisco firewalls are managed differently. A user, Cisco Advanced Services or a partner should manually review and verify the output from Cisco SCT. Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 4
Note • Several assumptions are made during the conversion process since Check Point and Cisco firewalls are managed differently. A user, Cisco Advanced Services or a partner should manually review and verify the output from Cisco SCT. Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 4
 System Requirements • Runs on Windows XP and 2000 platforms. • Converts from Check Point 4. x, NG and NGX Firewalls. • Converts to an ASA/PIX 7. x and FWSM 2. x or 3. x Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 5
System Requirements • Runs on Windows XP and 2000 platforms. • Converts from Check Point 4. x, NG and NGX Firewalls. • Converts to an ASA/PIX 7. x and FWSM 2. x or 3. x Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 5
 What is Required for the Conversion? • objects. C (Check Point 4. x) or objects_5_0. C (Check Point NG) – contains the objects definition •
What is Required for the Conversion? • objects. C (Check Point 4. x) or objects_5_0. C (Check Point NG) – contains the objects definition •
 What Will Be Converted? • Access rules (security policies) • Network objects and network object groups • Service objects and service object groups • NAT rules • Static routes • Interface-related configuration Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 7
What Will Be Converted? • Access rules (security policies) • Network objects and network object groups • Service objects and service object groups • NAT rules • Static routes • Interface-related configuration Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 7
 Cisco SCT Output • Corresponding ASA, PIX, or FWSM CLI configuration. • Summary of what was converted. • Conversion report indicating any errors or warnings during the conversion. • Detailed HTML report with hyperlinks from the CLI conversion to the original Check Point policy. Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 8
Cisco SCT Output • Corresponding ASA, PIX, or FWSM CLI configuration. • Summary of what was converted. • Conversion report indicating any errors or warnings during the conversion. • Detailed HTML report with hyperlinks from the CLI conversion to the original Check Point policy. Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 8
 Getting Started with Cisco SCT • Download SCT • Install SCT • Launch SCT • Run demo or select files Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 9
Getting Started with Cisco SCT • Download SCT • Install SCT • Launch SCT • Run demo or select files Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 9
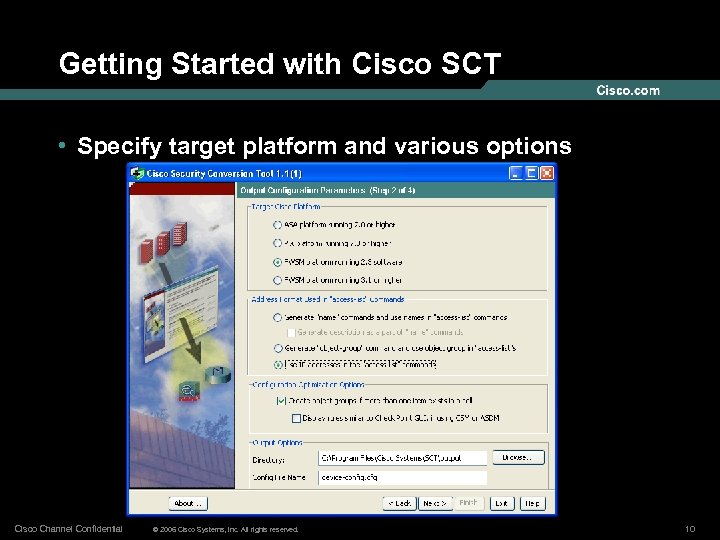 Getting Started with Cisco SCT • Specify target platform and various options Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 10
Getting Started with Cisco SCT • Specify target platform and various options Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 10
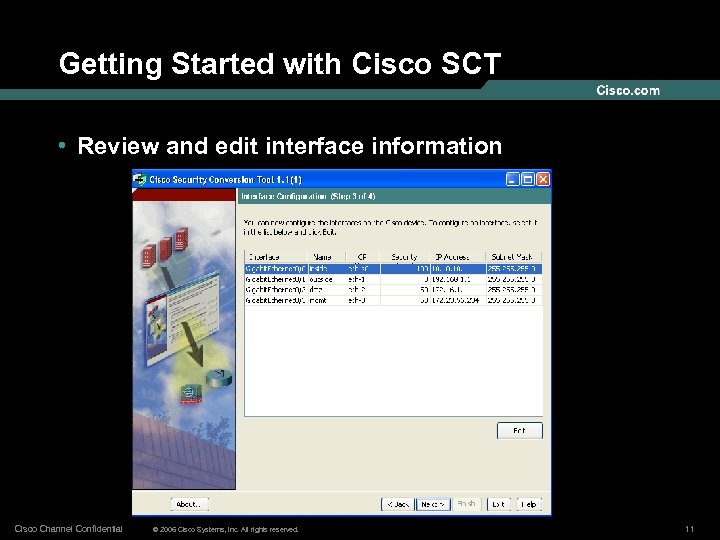 Getting Started with Cisco SCT • Review and edit interface information Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 11
Getting Started with Cisco SCT • Review and edit interface information Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 11
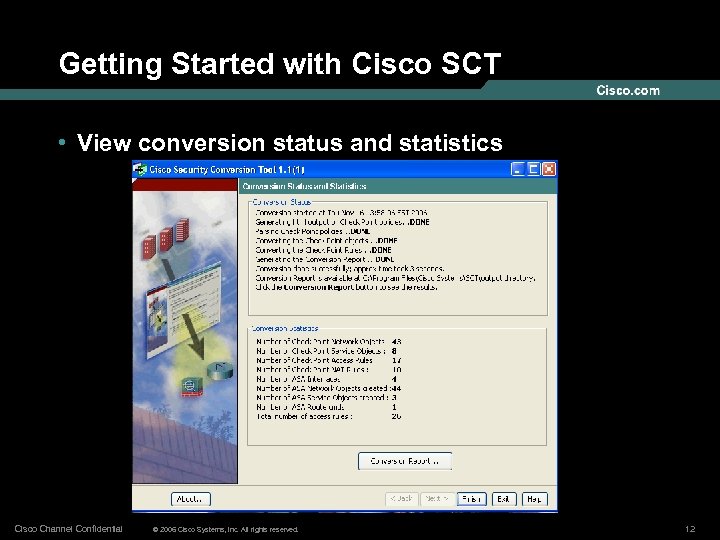 Getting Started with Cisco SCT • View conversion status and statistics Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 12
Getting Started with Cisco SCT • View conversion status and statistics Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 12
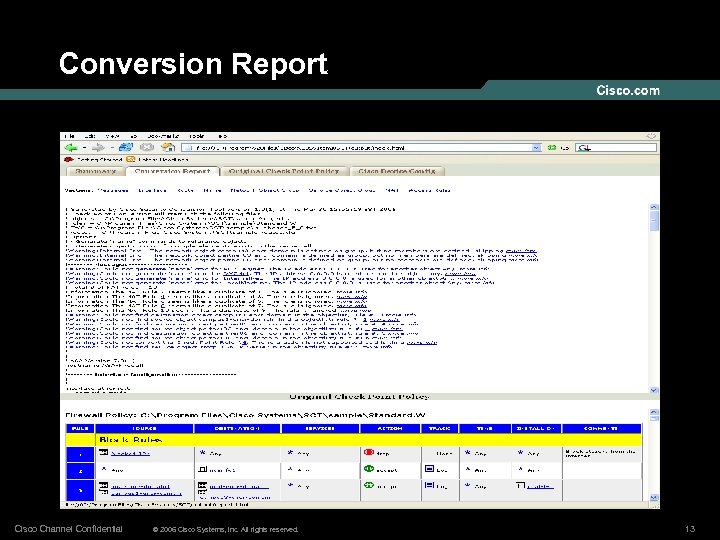 Conversion Report Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 13
Conversion Report Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 13
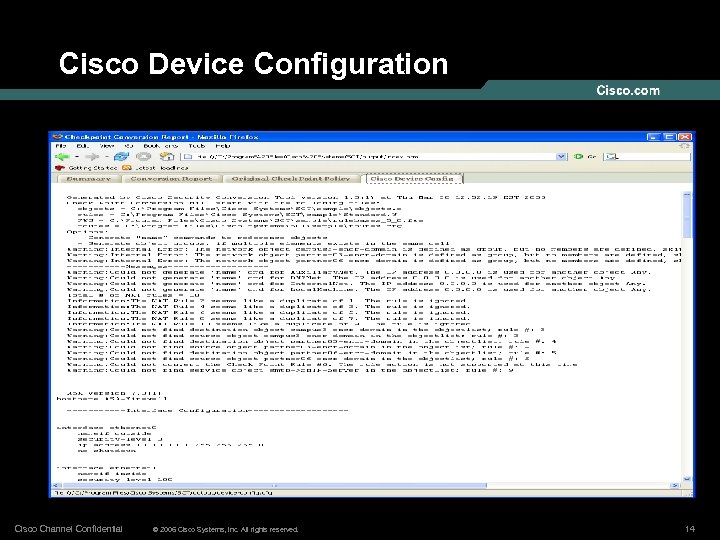 Cisco Device Configuration Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 14
Cisco Device Configuration Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 14
 Additional Cisco SCT Resources • Download Site (requires a CCO user ID): http: //www. cisco. com/cgi-bin/tablebuild. pl/sct • Technical Support: sct-support@cisco. com • Report your success and give us feedback! sct-wins@cisco. com Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 15
Additional Cisco SCT Resources • Download Site (requires a CCO user ID): http: //www. cisco. com/cgi-bin/tablebuild. pl/sct • Technical Support: sct-support@cisco. com • Report your success and give us feedback! sct-wins@cisco. com Cisco Channel Confidential © 2006 Cisco Systems, Inc. All rights reserved. 15


