20a440301afa9a445ff53c01e1d98933.ppt
- Количество слайдов: 35

Cisco NAC Luc Billot Security Consulting Engineer lbillot@cisco. com October 2007 Network Academy Istambul Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 1

The Diversity of Education Networks Every bit of user data touches the network Every device students and admin has is attached to the network In this environment, EVERYTHING is a potential target AND a potential threat >> Threat vectors have changed: your “trusted users” can be the weakest link in your network’s security Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 2

The Evolution of Education Threats Mitigating threats via policy compliance Balancing access and security in a “connected” world Changing threats from infection to “targeted attacks” >> Education vectors have changed: you are accountable for your “policies” that are not enforced Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 3
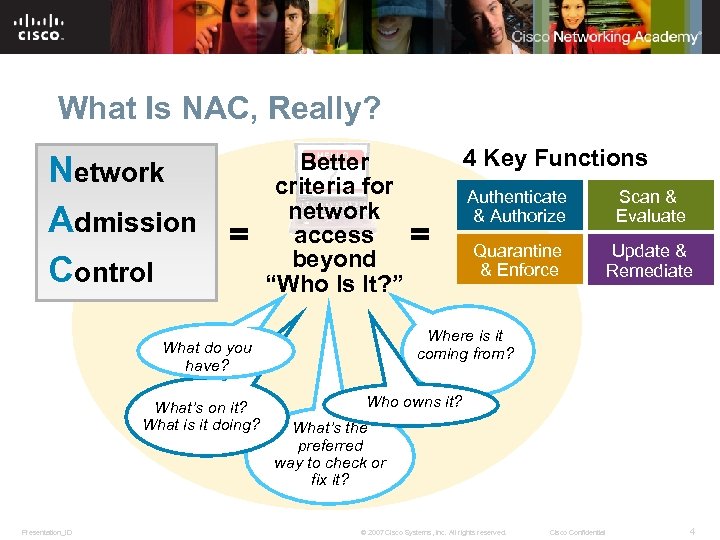
What Is NAC, Really? Network Admission = Control Better criteria for network access = beyond “Who Is It? ” Presentation_ID Authenticate & Authorize Scan & Evaluate Quarantine & Enforce Update & Remediate Where is it coming from? What do you have? What’s on it? What is it doing? 4 Key Functions Who owns it? What’s the preferred way to check or fix it? © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 4

NAC Means Better Criteria for Education What System Is It? Who Owns It? Where Is It Coming From? What’s On It? Is It Running? What’s The Preferred Way To Check/Fix It? Presentation_ID Windows, Mac or Linux Laptop or Desktop or PDA Printer or Other Corporate Asset University Faculty Student Guest Unknown VPN LAN WAN Anti-Virus, Anti-Spyware Personal Firewall Patching Tools Pre-Configured Checks Customized Checks Self-Remediation or Auto-Remediation Third-Party Software © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 5

NAC Must Address Top Pain Points Implement identity-based access control Applies identity and access policies based on roles to all users and devices Handle guest and unmanaged users Authenticates and controls guest and unmanaged assets Enforce endpoint policy requirements Assesses, quarantines, and remediates noncompliant endpoints Source: Current Analysis, July 2006 Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 6
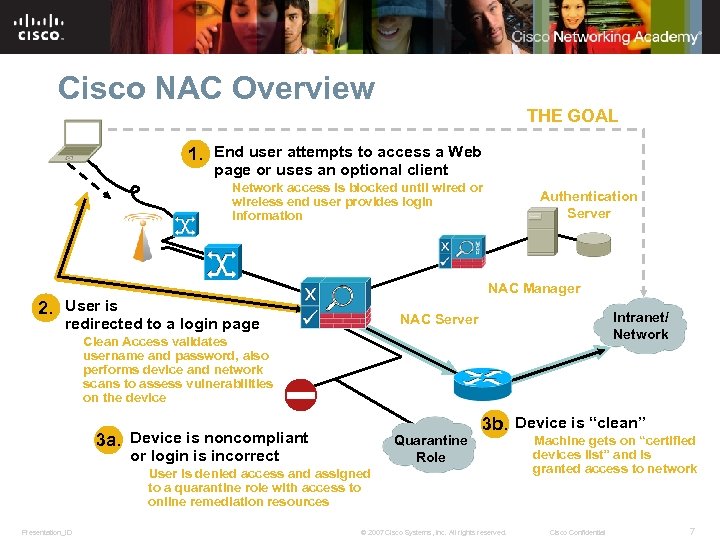
Cisco NAC Overview THE GOAL 1. End user attempts to access a Web page or uses an optional client Network access is blocked until wired or wireless end user provides login information Authentication Server NAC Manager 2. User is Intranet/ Network NAC Server redirected to a login page Clean Access validates username and password, also performs device and network scans to assess vulnerabilities on the device 3 a. Device is noncompliant Quarantine Role or login is incorrect 3 b. Device is “clean” User is denied access and assigned to a quarantine role with access to online remediation resources Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Machine gets on “certified devices list” and is granted access to network Cisco Confidential 7
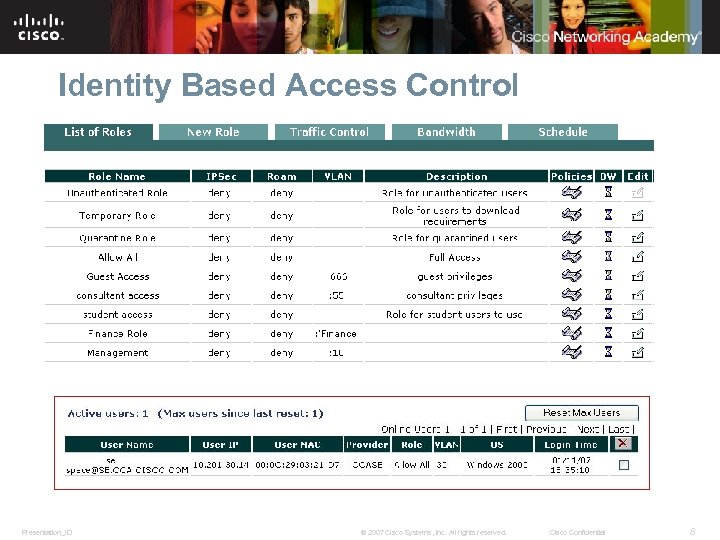
Identity Based Access Control Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 8
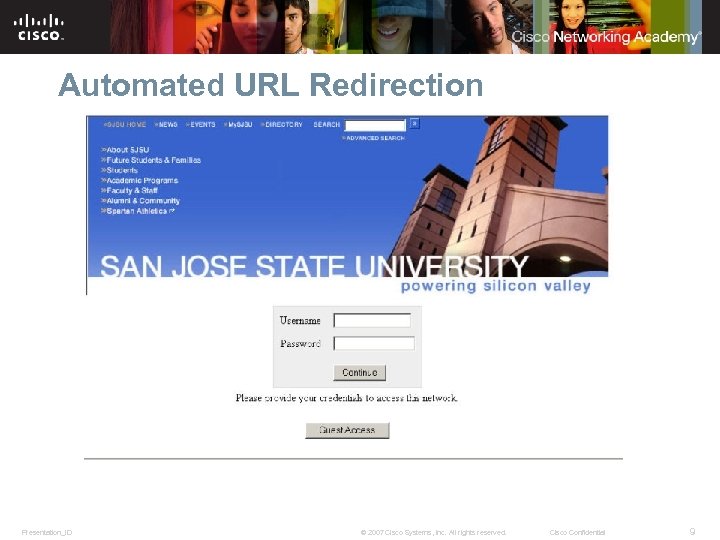
Automated URL Redirection Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 9
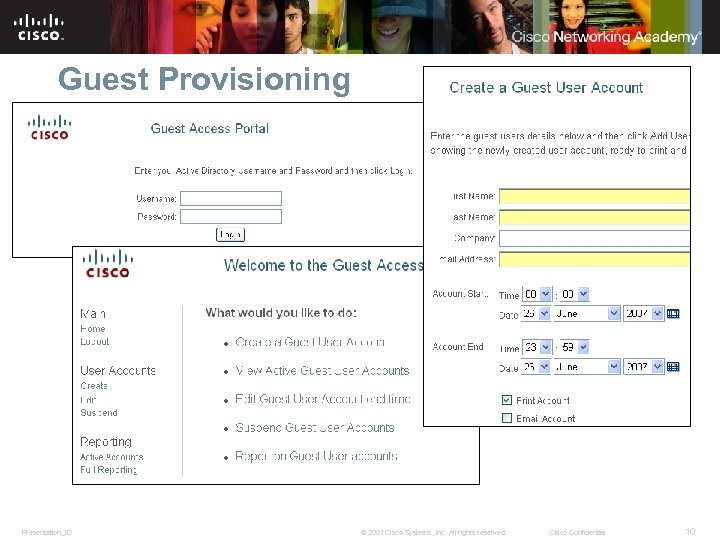
Guest Provisioning Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 10
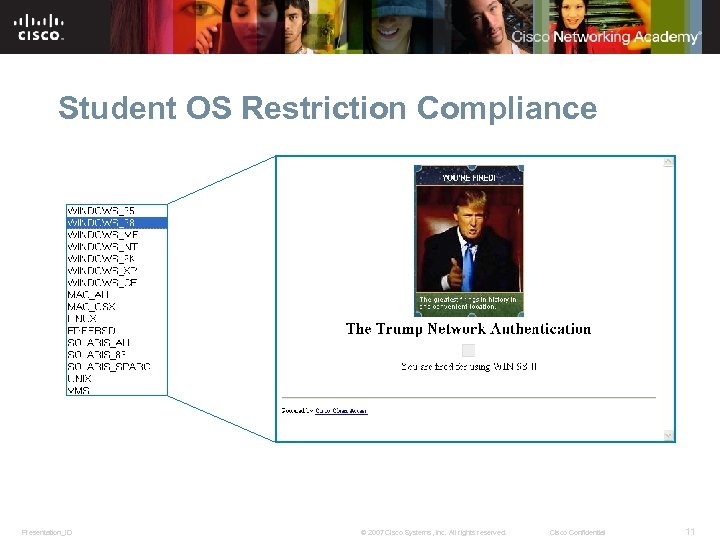
Student OS Restriction Compliance Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 11
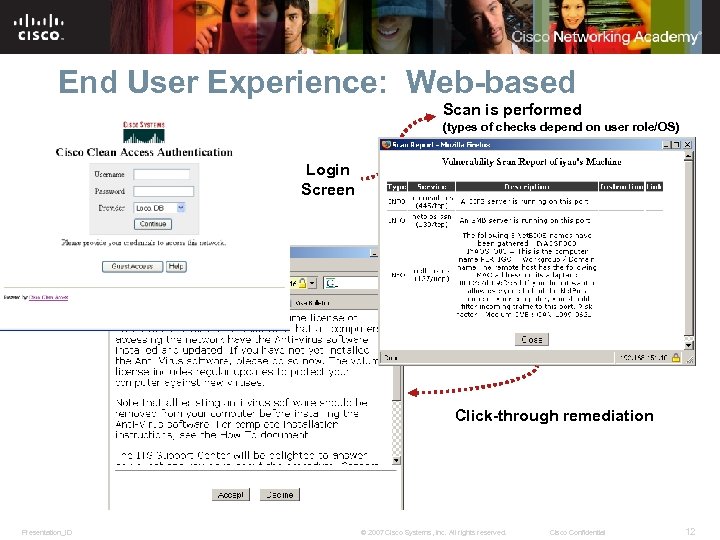
End User Experience: Web-based Scan is performed (types of checks depend on user role/OS) Login Screen Click-through remediation Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 12

Downloading the Agent (Optional) § Guest user will be offered the choice to download agent for posture § Guest user can still proceed by clicking Restricted Network Access if they choose not to download the agent Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 13
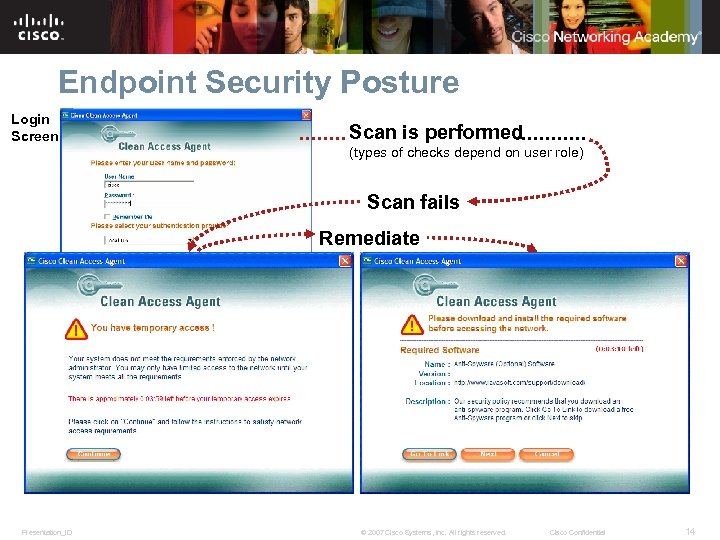
Endpoint Security Posture Login Screen Scan is performed (types of checks depend on user role) Scan fails Remediate 4. Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 14
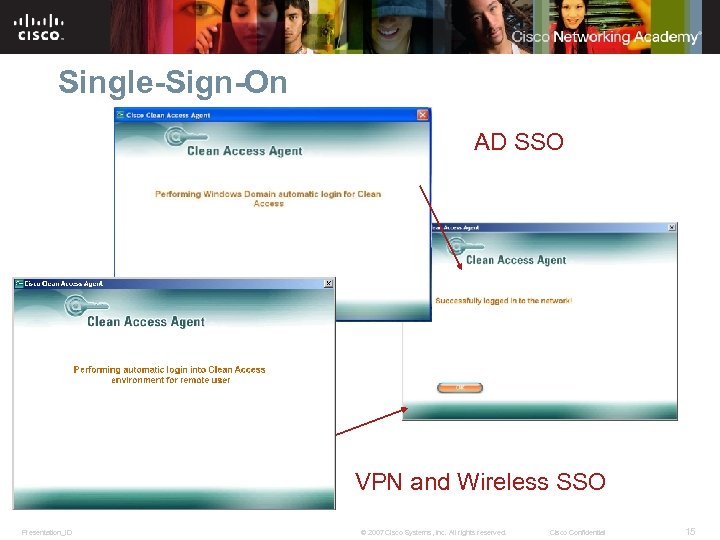
Single-Sign-On AD SSO VPN and Wireless SSO Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 15
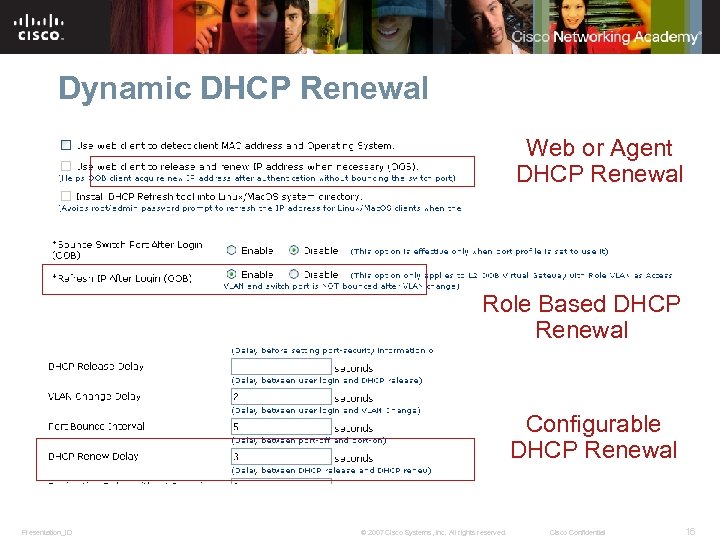
Dynamic DHCP Renewal Web or Agent DHCP Renewal Role Based DHCP Renewal Configurable DHCP Renewal Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 16
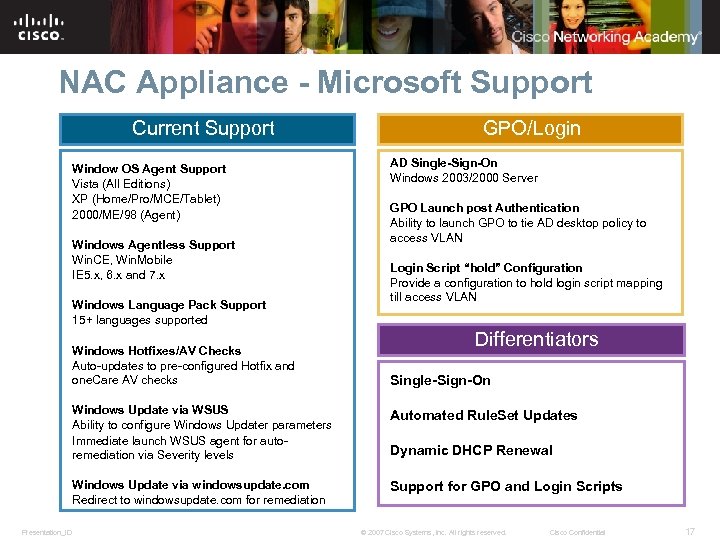
NAC Appliance - Microsoft Support Current Support Window OS Agent Support Vista (All Editions) XP (Home/Pro/MCE/Tablet) 2000/ME/98 (Agent) Windows Agentless Support Win. CE, Win. Mobile IE 5. x, 6. x and 7. x Windows Language Pack Support 15+ languages supported Windows Hotfixes/AV Checks Auto-updates to pre-configured Hotfix and one. Care AV checks GPO/Login AD Single-Sign-On Windows 2003/2000 Server GPO Launch post Authentication Ability to launch GPO to tie AD desktop policy to access VLAN Login Script “hold” Configuration Provide a configuration to hold login script mapping till access VLAN Differentiators Single-Sign-On Windows Update via WSUS Ability to configure Windows Updater parameters Immediate launch WSUS agent for autoremediation via Severity levels Windows Update via windowsupdate. com Redirect to windowsupdate. com for remediation Presentation_ID Automated Rule. Set Updates Support for GPO and Login Scripts Dynamic DHCP Renewal © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 17

NAC Manager: Simplified NAC Management Automated Cisco updates simplifies management for over 350+ partner applications Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 18

NAC Server: Integrated NAC Services Integrating posture and profiling services to ensure that incoming devices are compliant. Guest Portal Services Posture Services § Guest & Registration Portal § Managed Device Posture § OS Detection & Restriction § Unmanaged Device Scanning § Role based AUP § Remediation Authentication Services Profiling Services § Web, MAC, IP Authentication § Behavioral Monitoring § Radius Accounting Proxy Presentation_ID § Device Profiling § Authentication & SSO NEW! § Device Reporting © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 19
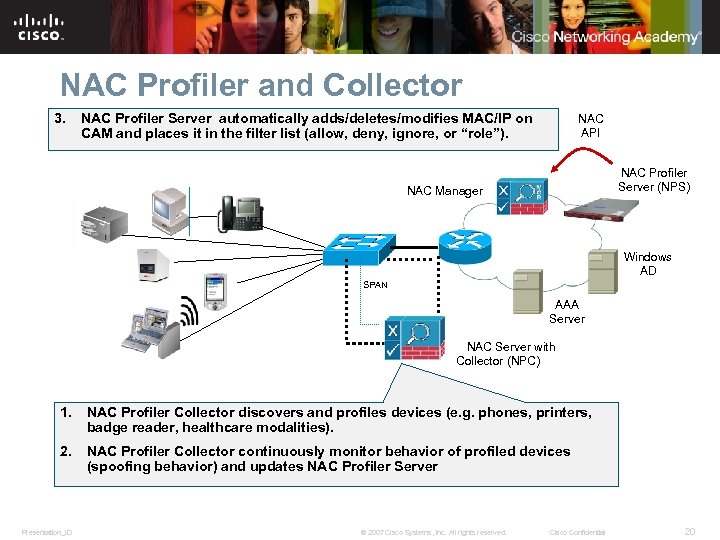
NAC Profiler and Collector 3. NAC Profiler Server automatically adds/deletes/modifies MAC/IP on CAM and places it in the filter list (allow, deny, ignore, or “role”). NAC API NAC Profiler Server (NPS) NAC Manager Windows AD SPAN AAA Server NAC Server with Collector (NPC) 1. NAC Profiler Collector discovers and profiles devices (e. g. phones, printers, badge reader, healthcare modalities). 2. NAC Profiler Collector continuously monitor behavior of profiled devices (spoofing behavior) and updates NAC Profiler Server Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 20
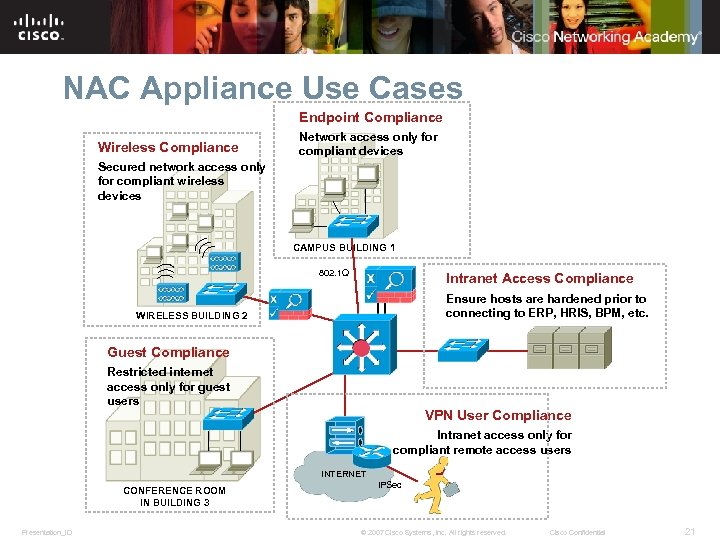
NAC Appliance Use Cases Endpoint Compliance Wireless Compliance Network access only for compliant devices Secured network access only for compliant wireless devices CAMPUS BUILDING 1 802. 1 Q Intranet Access Compliance Ensure hosts are hardened prior to connecting to ERP, HRIS, BPM, etc. WIRELESS BUILDING 2 Guest Compliance Restricted internet access only for guest users VPN User Compliance Intranet access only for compliant remote access users INTERNET CONFERENCE ROOM IN BUILDING 3 Presentation_ID IPSec © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 21
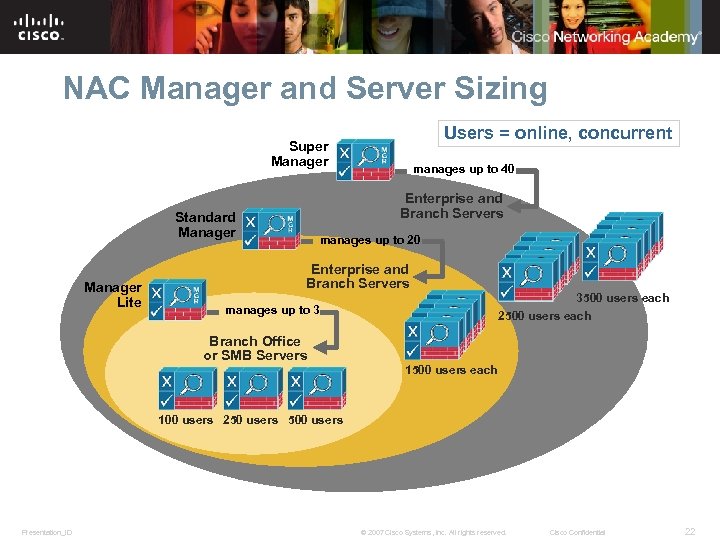
NAC Manager and Server Sizing Users = online, concurrent Super Manager Enterprise and Branch Servers Standard Manager Lite manages up to 40 manages up to 20 Enterprise and Branch Servers manages up to 3 3500 users each 2500 users each Branch Office or SMB Servers 1500 users each 100 users 250 users 500 users Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 22
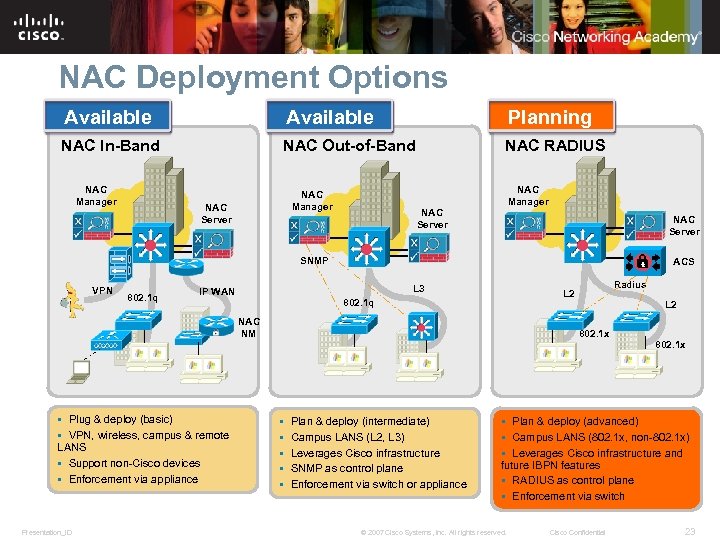
NAC Deployment Options Available Planning NAC In-Band NAC Out-of-Band NAC RADIUS NAC Manager NAC Server SNMP VPN 802. 1 q ACS L 3 IP WAN 802. 1 q NAC NM § Plug & deploy (basic) § VPN, wireless, campus & remote LANS § Support non-Cisco devices § Enforcement via appliance Presentation_ID Radius L 2 802. 1 x § § § Plan & deploy (intermediate) Campus LANS (L 2, L 3) Leverages Cisco infrastructure SNMP as control plane Enforcement via switch or appliance 802. 1 x § Plan & deploy (advanced) § Campus LANS (802. 1 x, non-802. 1 x) § Leverages Cisco infrastructure and future IBPN features § RADIUS as control plane § Enforcement via switch © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 23
NAC Server Foundation: Virtual Gateway and Real IP Gateway § NAC Servers at the most basic level can pass traffic in one of two ways: Bridged Mode = Virtual Gateway Routed Mode = Real IP Gateway / NAT Gateway § Any NAC Server can be configured for either method, but a NAC Server can only be one at a time § Gateway mode selection affects the logical traffic path § Does not affect whether a NAC Server is in Layer 2 mode, Layer 3 mode, In Band or Out of Band Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 24
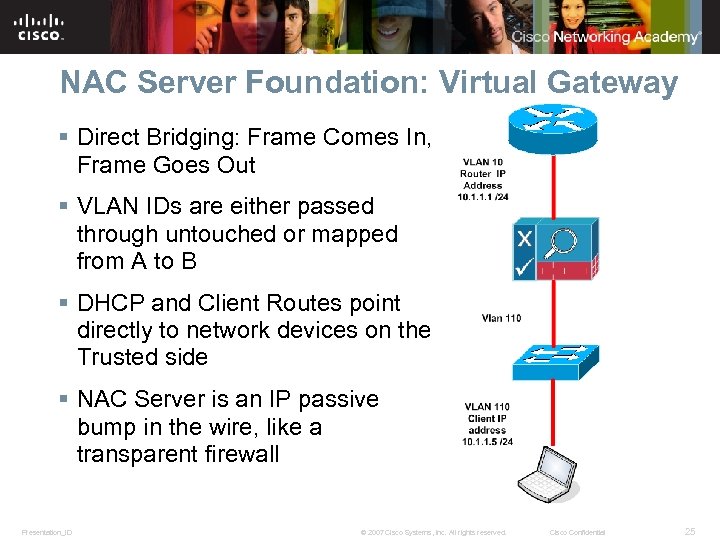
NAC Server Foundation: Virtual Gateway § Direct Bridging: Frame Comes In, Frame Goes Out § VLAN IDs are either passed through untouched or mapped from A to B § DHCP and Client Routes point directly to network devices on the Trusted side § NAC Server is an IP passive bump in the wire, like a transparent firewall Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 25
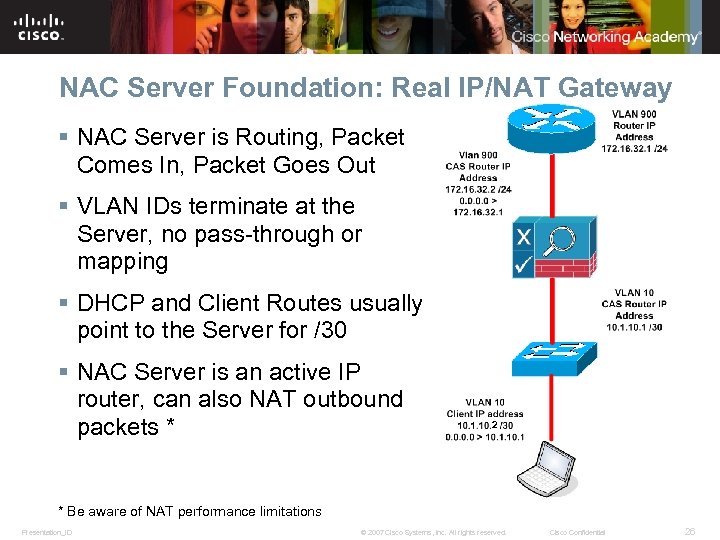
NAC Server Foundation: Real IP/NAT Gateway § NAC Server is Routing, Packet Comes In, Packet Goes Out § VLAN IDs terminate at the Server, no pass-through or mapping § DHCP and Client Routes usually point to the Server for /30 § NAC Server is an active IP router, can also NAT outbound packets * 2 * Be aware of NAT performance limitations Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 26
NAC Server Foundation: Edge and Central Deployment § NAC Servers have two physical deployment models Edge Deployment Central Deployment § Any NAC Server can be configured for either method § Deployment mode selection affects the physical traffic path § Does not affect whether a NAC Server is in Layer 2 mode, Layer 3 mode, In Band or Out of Band Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 27
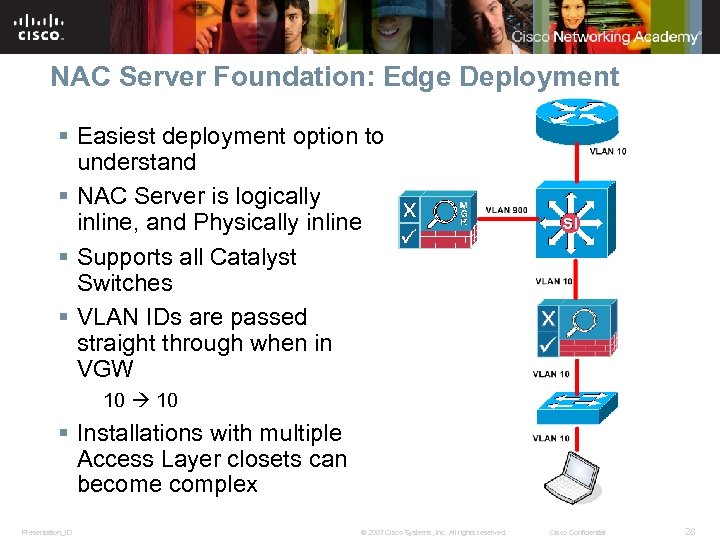
NAC Server Foundation: Edge Deployment § Easiest deployment option to understand § NAC Server is logically inline, and Physically inline § Supports all Catalyst Switches § VLAN IDs are passed straight through when in VGW 10 § Installations with multiple Access Layer closets can become complex Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 28
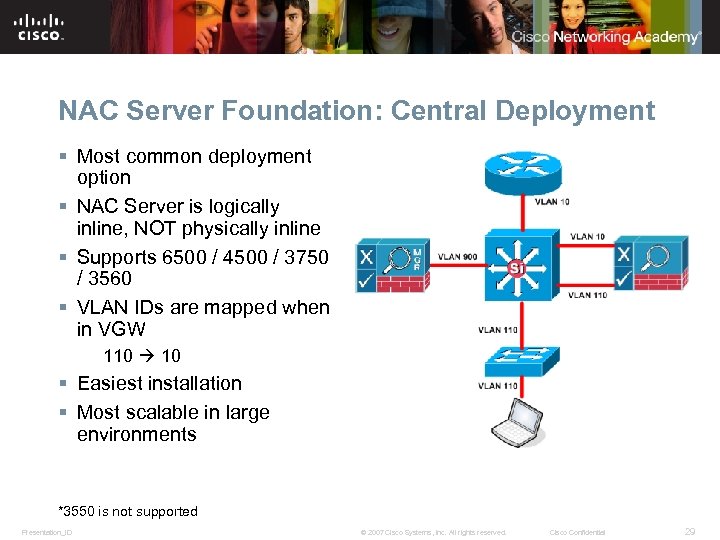
NAC Server Foundation: Central Deployment § Most common deployment option § NAC Server is logically inline, NOT physically inline § Supports 6500 / 4500 / 3750 / 3560 § VLAN IDs are mapped when in VGW 110 10 § Easiest installation § Most scalable in large environments *3550 is not supported Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 29
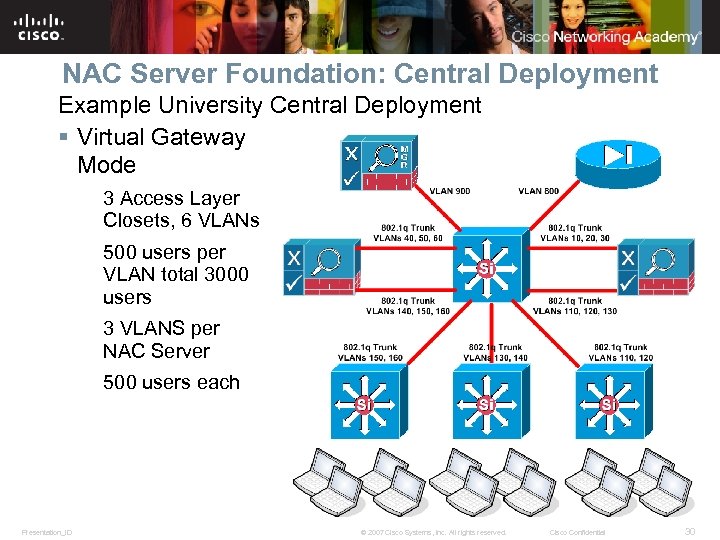
NAC Server Foundation: Central Deployment Example University Central Deployment § Virtual Gateway Mode 3 Access Layer Closets, 6 VLANs 500 users per VLAN total 3000 users 3 VLANS per NAC Server 500 users each Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 30
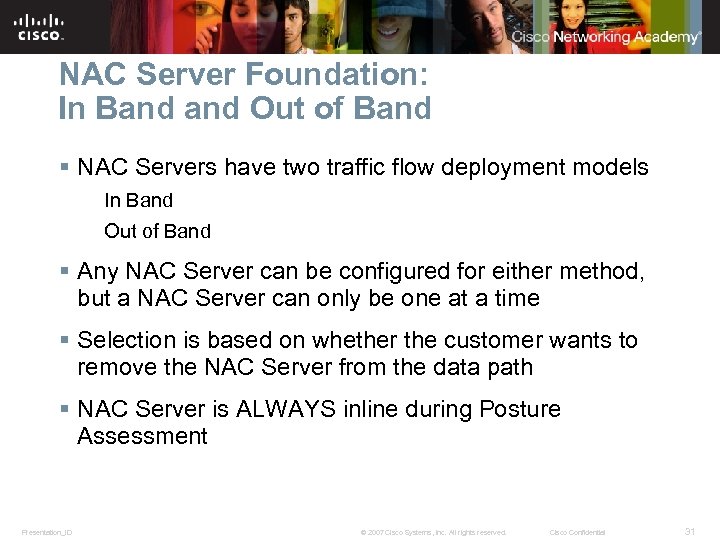
NAC Server Foundation: In Band Out of Band § NAC Servers have two traffic flow deployment models In Band Out of Band § Any NAC Server can be configured for either method, but a NAC Server can only be one at a time § Selection is based on whether the customer wants to remove the NAC Server from the data path § NAC Server is ALWAYS inline during Posture Assessment Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 31
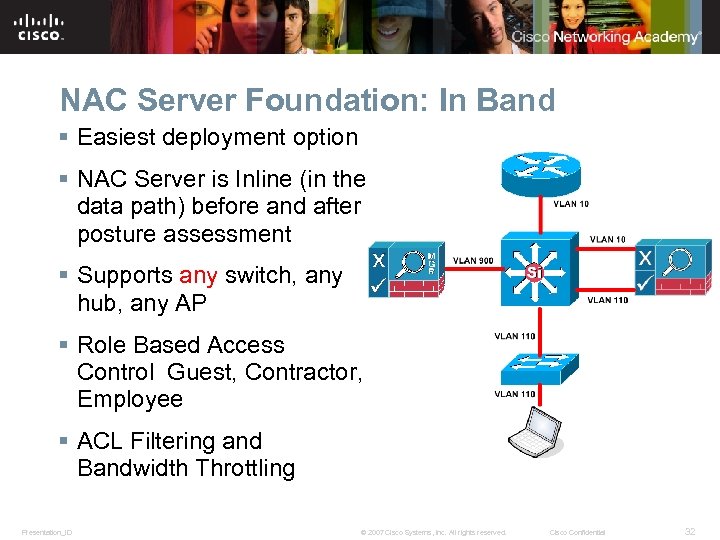
NAC Server Foundation: In Band § Easiest deployment option § NAC Server is Inline (in the data path) before and after posture assessment § Supports any switch, any hub, any AP § Role Based Access Control Guest, Contractor, Employee § ACL Filtering and Bandwidth Throttling Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 32
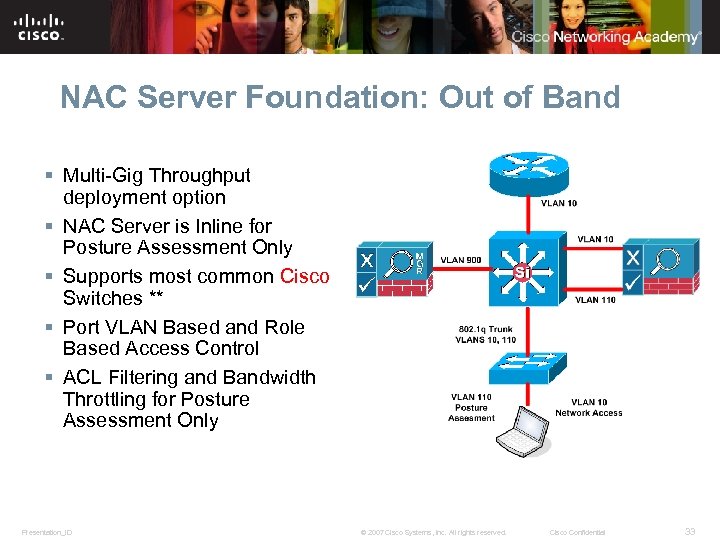
NAC Server Foundation: Out of Band § Multi-Gig Throughput deployment option § NAC Server is Inline for Posture Assessment Only § Supports most common Cisco Switches ** § Port VLAN Based and Role Based Access Control § ACL Filtering and Bandwidth Throttling for Posture Assessment Only Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 33

Q& A Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 34

Presentation_ID © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 35
20a440301afa9a445ff53c01e1d98933.ppt