5c29f59186e1d01d5c1f4a98a41b0e97.ppt
- Количество слайдов: 47
 CIS 81 Fundamentals of Networking Chapter 3: Network Protocols and Communications Rick Graziani Cabrillo College graziani@cabrillo. edu Spring 2018
CIS 81 Fundamentals of Networking Chapter 3: Network Protocols and Communications Rick Graziani Cabrillo College graziani@cabrillo. edu Spring 2018
 Chapter 2 - Objectives § Explain how rules are used to facilitate communication. § Explain the role of protocols and standards organizations in facilitating interoperability in network communications. § Explain how devices on a LAN access resources in a small to medium-sized business network. 2
Chapter 2 - Objectives § Explain how rules are used to facilitate communication. § Explain the role of protocols and standards organizations in facilitating interoperability in network communications. § Explain how devices on a LAN access resources in a small to medium-sized business network. 2
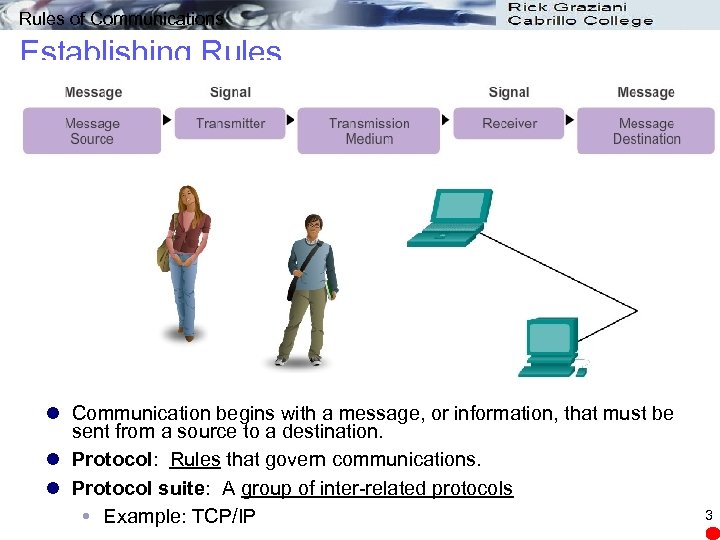 Rules of Communications Establishing Rules l Communication begins with a message, or information, that must be sent from a source to a destination. l Protocol: Rules that govern communications. l Protocol suite: A group of inter-related protocols Example: TCP/IP 3
Rules of Communications Establishing Rules l Communication begins with a message, or information, that must be sent from a source to a destination. l Protocol: Rules that govern communications. l Protocol suite: A group of inter-related protocols Example: TCP/IP 3
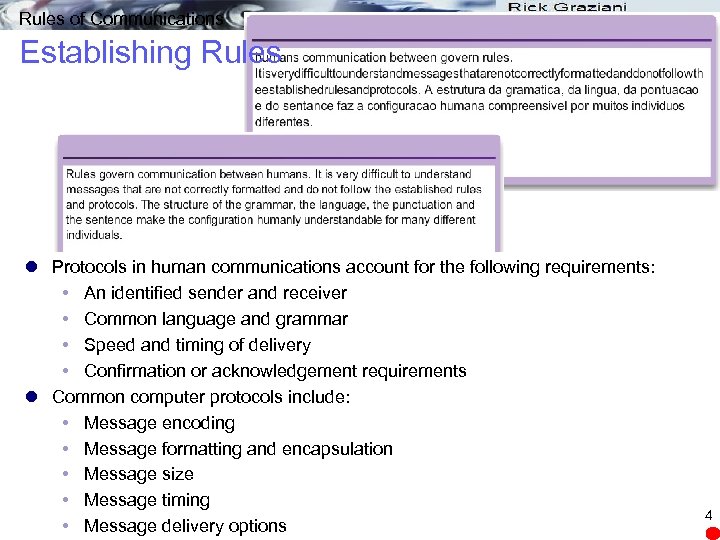 Rules of Communications Establishing Rules l Protocols in human communications account for the following requirements: An identified sender and receiver Common language and grammar Speed and timing of delivery Confirmation or acknowledgement requirements l Common computer protocols include: Message encoding Message formatting and encapsulation Message size Message timing Message delivery options 4
Rules of Communications Establishing Rules l Protocols in human communications account for the following requirements: An identified sender and receiver Common language and grammar Speed and timing of delivery Confirmation or acknowledgement requirements l Common computer protocols include: Message encoding Message formatting and encapsulation Message size Message timing Message delivery options 4
 Rules of Communications Message Encoding 5
Rules of Communications Message Encoding 5
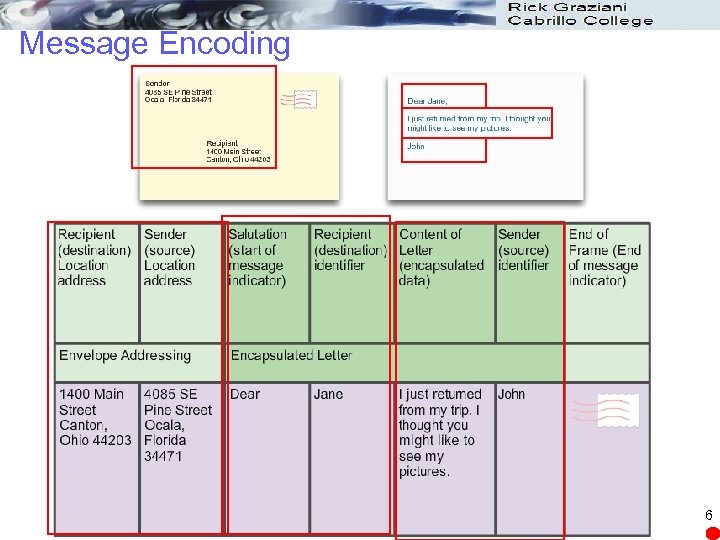 Message Encoding 6
Message Encoding 6
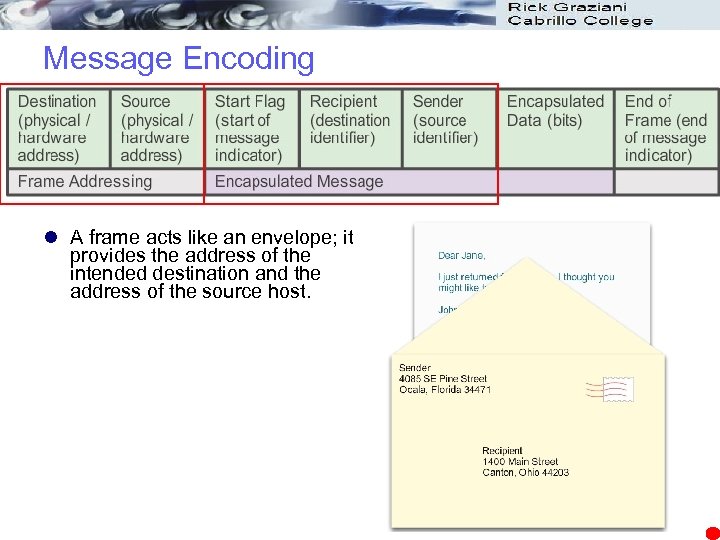 Message Encoding l A frame acts like an envelope; it provides the address of the intended destination and the address of the source host. 7
Message Encoding l A frame acts like an envelope; it provides the address of the intended destination and the address of the source host. 7
 Rules of Communication l Message Timing People use timing to determine when to speak, how fast/slow to talk, and how long to wait for a response. l Access Method Determines when someone is able to send a message. If two people talk at the same time, a collision occurs. Hosts on a network need an access method to know when to begin sending messages. l Flow Control How much information can be sent. Hosts use flow control to negotiate how much data can be sent/received. l Response Timeout Hosts on the network also have rules that specify how long to wait for responses and what action to take if a response timeout occurs.
Rules of Communication l Message Timing People use timing to determine when to speak, how fast/slow to talk, and how long to wait for a response. l Access Method Determines when someone is able to send a message. If two people talk at the same time, a collision occurs. Hosts on a network need an access method to know when to begin sending messages. l Flow Control How much information can be sent. Hosts use flow control to negotiate how much data can be sent/received. l Response Timeout Hosts on the network also have rules that specify how long to wait for responses and what action to take if a response timeout occurs.
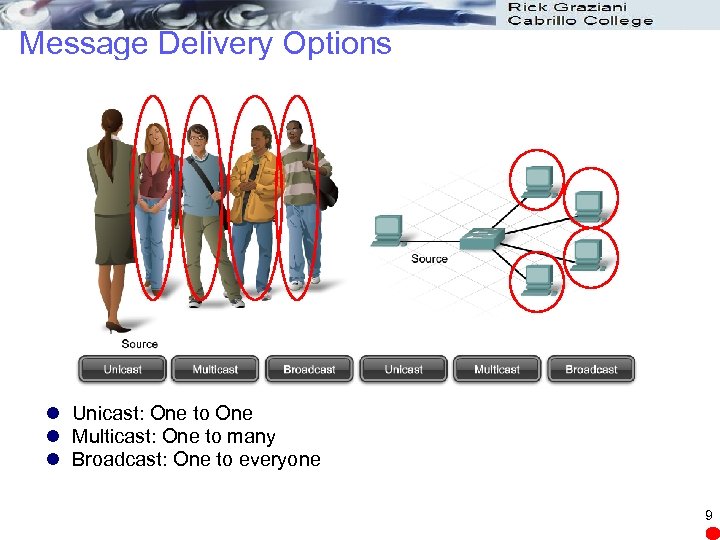 Message Delivery Options l Unicast: One to One l Multicast: One to many l Broadcast: One to everyone 9
Message Delivery Options l Unicast: One to One l Multicast: One to many l Broadcast: One to everyone 9
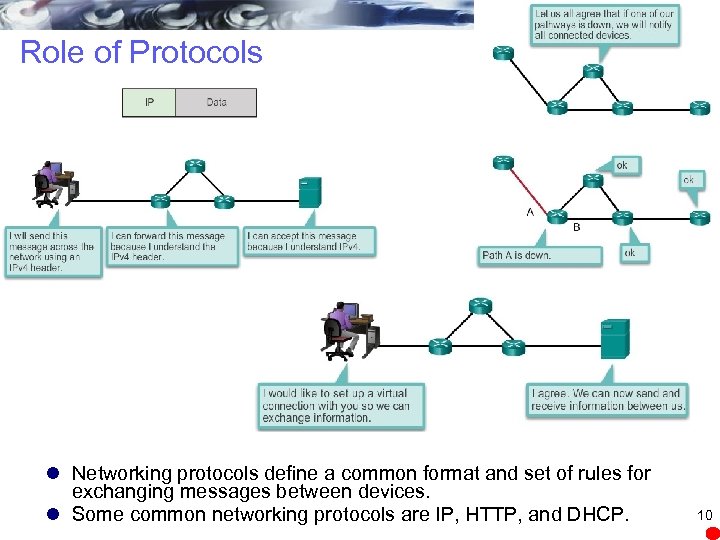 Role of Protocols l Networking protocols define a common format and set of rules for exchanging messages between devices. l Some common networking protocols are IP, HTTP, and DHCP. 10
Role of Protocols l Networking protocols define a common format and set of rules for exchanging messages between devices. l Some common networking protocols are IP, HTTP, and DHCP. 10
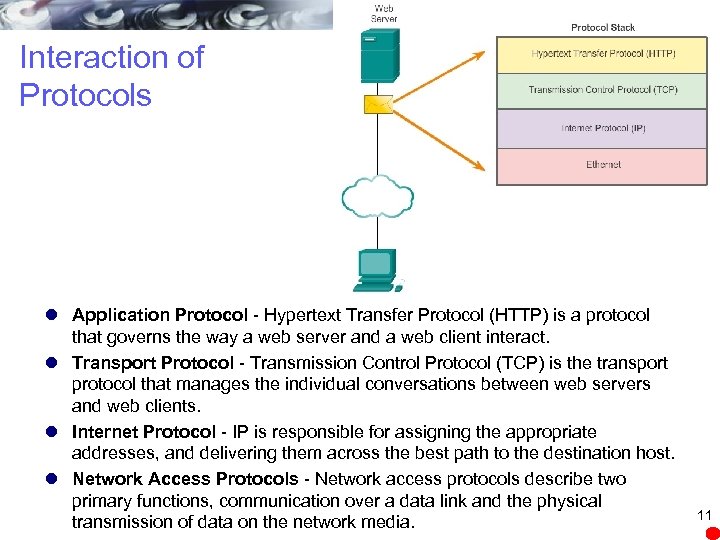 Interaction of Protocols l Application Protocol - Hypertext Transfer Protocol (HTTP) is a protocol that governs the way a web server and a web client interact. l Transport Protocol - Transmission Control Protocol (TCP) is the transport protocol that manages the individual conversations between web servers and web clients. l Internet Protocol - IP is responsible for assigning the appropriate addresses, and delivering them across the best path to the destination host. l Network Access Protocols - Network access protocols describe two primary functions, communication over a data link and the physical transmission of data on the network media. 11
Interaction of Protocols l Application Protocol - Hypertext Transfer Protocol (HTTP) is a protocol that governs the way a web server and a web client interact. l Transport Protocol - Transmission Control Protocol (TCP) is the transport protocol that manages the individual conversations between web servers and web clients. l Internet Protocol - IP is responsible for assigning the appropriate addresses, and delivering them across the best path to the destination host. l Network Access Protocols - Network access protocols describe two primary functions, communication over a data link and the physical transmission of data on the network media. 11
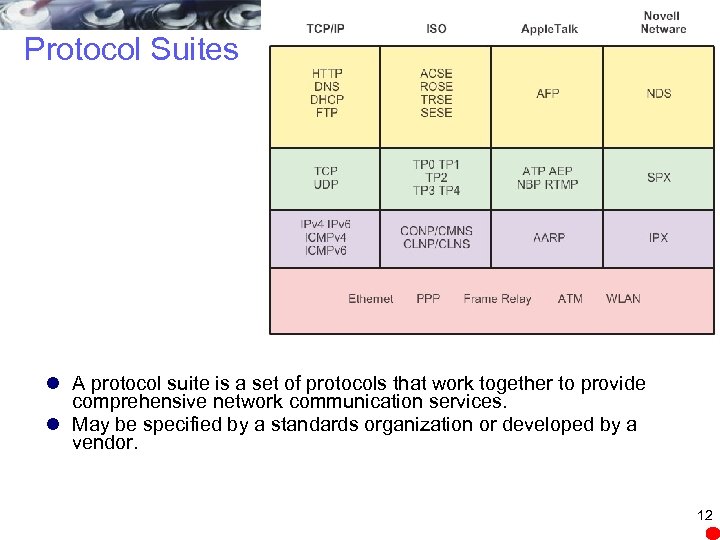 Protocol Suites l A protocol suite is a set of protocols that work together to provide comprehensive network communication services. l May be specified by a standards organization or developed by a vendor. 12
Protocol Suites l A protocol suite is a set of protocols that work together to provide comprehensive network communication services. l May be specified by a standards organization or developed by a vendor. 12
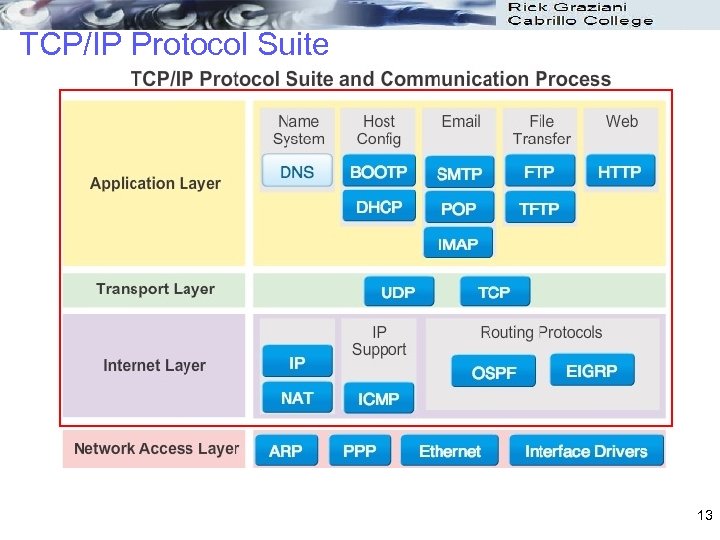 TCP/IP Protocol Suite 13
TCP/IP Protocol Suite 13
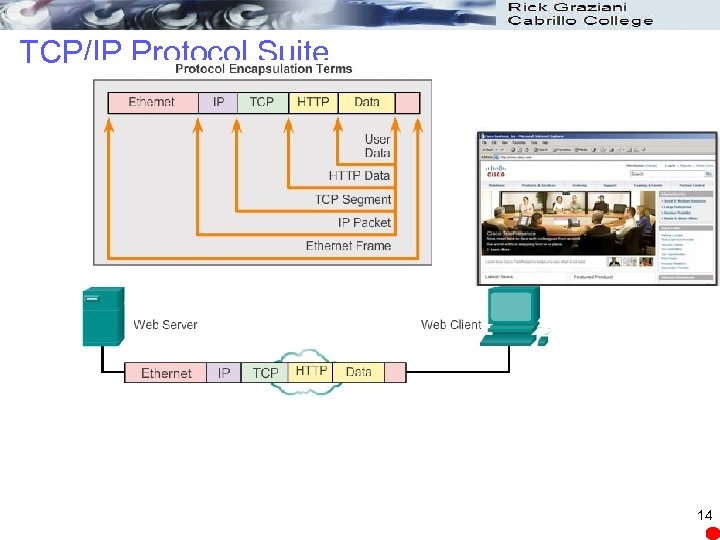 TCP/IP Protocol Suite 14
TCP/IP Protocol Suite 14
 Standards Organizations l Open standards encourage competition and innovation. l Guarantee that no single company’s product can monopolize the market, or have an unfair advantage over its competition. l Standards organizations include: The Internet Society (ISOC) The Internet Architecture Board (IAB) The Internet Engineering Task Force (IETF) The Institute of Electrical and Electronics Engineers (IEEE) The International Organization for Standardization (ISO) 15
Standards Organizations l Open standards encourage competition and innovation. l Guarantee that no single company’s product can monopolize the market, or have an unfair advantage over its competition. l Standards organizations include: The Internet Society (ISOC) The Internet Architecture Board (IAB) The Internet Engineering Task Force (IETF) The Institute of Electrical and Electronics Engineers (IEEE) The International Organization for Standardization (ISO) 15
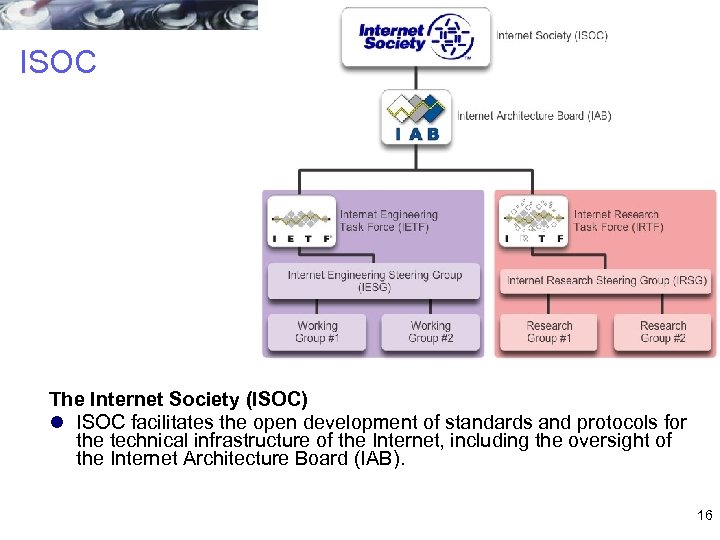 ISOC The Internet Society (ISOC) l ISOC facilitates the open development of standards and protocols for the technical infrastructure of the Internet, including the oversight of the Internet Architecture Board (IAB). 16
ISOC The Internet Society (ISOC) l ISOC facilitates the open development of standards and protocols for the technical infrastructure of the Internet, including the oversight of the Internet Architecture Board (IAB). 16
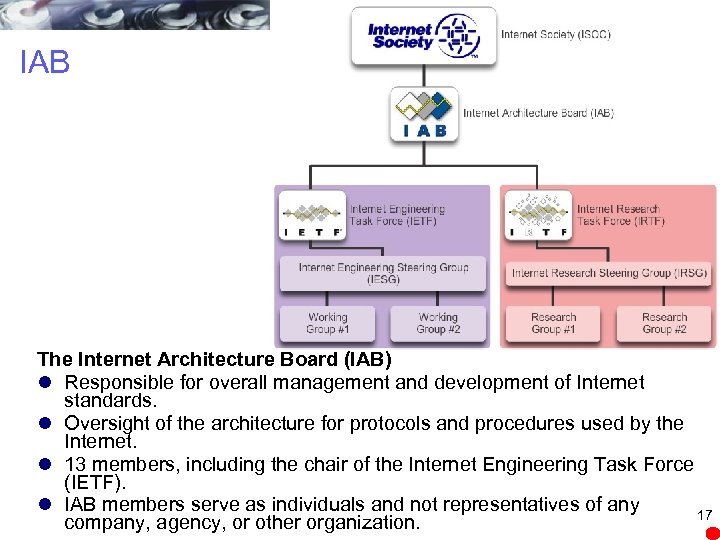 IAB The Internet Architecture Board (IAB) l Responsible for overall management and development of Internet standards. l Oversight of the architecture for protocols and procedures used by the Internet. l 13 members, including the chair of the Internet Engineering Task Force (IETF). l IAB members serve as individuals and not representatives of any 17 company, agency, or other organization.
IAB The Internet Architecture Board (IAB) l Responsible for overall management and development of Internet standards. l Oversight of the architecture for protocols and procedures used by the Internet. l 13 members, including the chair of the Internet Engineering Task Force (IETF). l IAB members serve as individuals and not representatives of any 17 company, agency, or other organization.
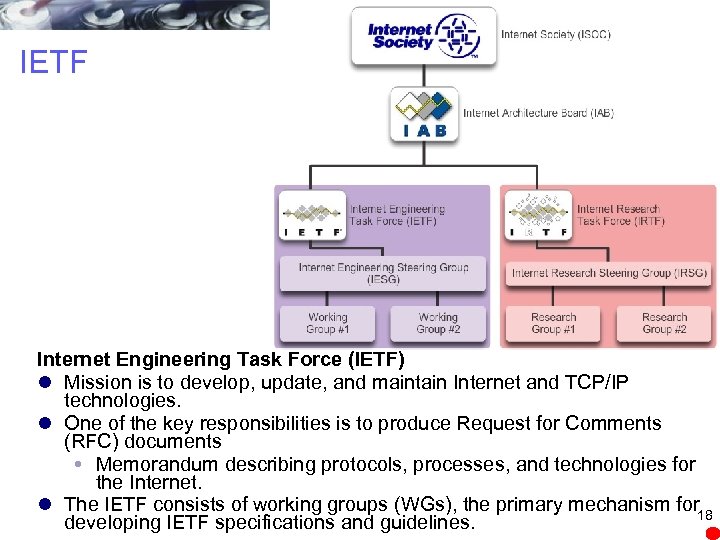 IETF Internet Engineering Task Force (IETF) l Mission is to develop, update, and maintain Internet and TCP/IP technologies. l One of the key responsibilities is to produce Request for Comments (RFC) documents Memorandum describing protocols, processes, and technologies for the Internet. l The IETF consists of working groups (WGs), the primary mechanism for 18 developing IETF specifications and guidelines.
IETF Internet Engineering Task Force (IETF) l Mission is to develop, update, and maintain Internet and TCP/IP technologies. l One of the key responsibilities is to produce Request for Comments (RFC) documents Memorandum describing protocols, processes, and technologies for the Internet. l The IETF consists of working groups (WGs), the primary mechanism for 18 developing IETF specifications and guidelines.
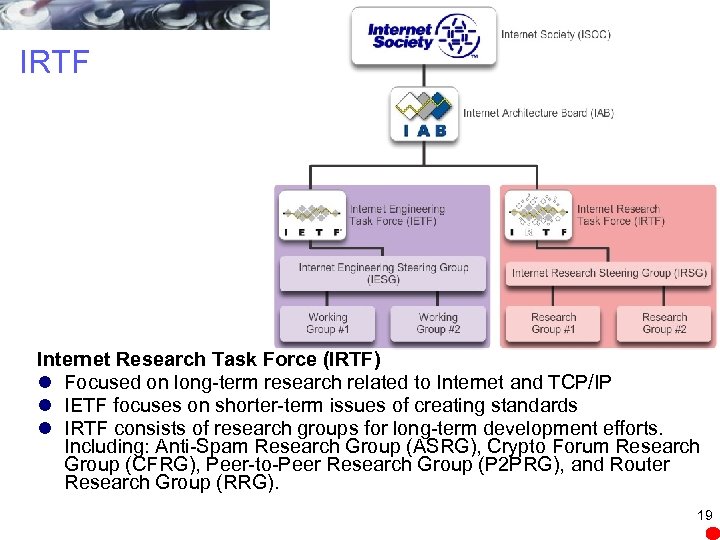 IRTF Internet Research Task Force (IRTF) l Focused on long-term research related to Internet and TCP/IP l IETF focuses on shorter-term issues of creating standards l IRTF consists of research groups for long-term development efforts. Including: Anti-Spam Research Group (ASRG), Crypto Forum Research Group (CFRG), Peer-to-Peer Research Group (P 2 PRG), and Router Research Group (RRG). 19
IRTF Internet Research Task Force (IRTF) l Focused on long-term research related to Internet and TCP/IP l IETF focuses on shorter-term issues of creating standards l IRTF consists of research groups for long-term development efforts. Including: Anti-Spam Research Group (ASRG), Crypto Forum Research Group (CFRG), Peer-to-Peer Research Group (P 2 PRG), and Router Research Group (RRG). 19
 IEEE Institute of Electrical and Electronics Engineers l A professional organization for those in the electrical engineering and electronics fields who are dedicated to advancing technological innovation and creating standards. l IEEE 802. 3 and IEEE 802. 11 standards are significant IEEE standards in computer networking. 20
IEEE Institute of Electrical and Electronics Engineers l A professional organization for those in the electrical engineering and electronics fields who are dedicated to advancing technological innovation and creating standards. l IEEE 802. 3 and IEEE 802. 11 standards are significant IEEE standards in computer networking. 20
 Cisco IOS Purpose of ISO, the International Organization for Standardization l World’s largest developer of international standards for a wide variety of products and services. l ISO is not an acronym but based on the Greek word ISOS, meaning equal. l ISO is best known for its Open Systems Interconnection (OSI) reference model. l ISO published the OSI reference model in 1984 to develop a layered framework for networking protocols. 21
Cisco IOS Purpose of ISO, the International Organization for Standardization l World’s largest developer of international standards for a wide variety of products and services. l ISO is not an acronym but based on the Greek word ISOS, meaning equal. l ISO is best known for its Open Systems Interconnection (OSI) reference model. l ISO published the OSI reference model in 1984 to develop a layered framework for networking protocols. 21
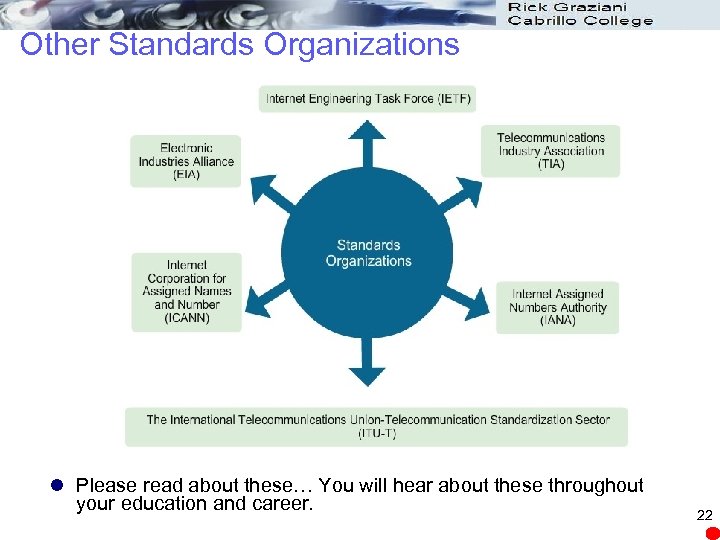 Other Standards Organizations l Please read about these… You will hear about these throughout your education and career. 22
Other Standards Organizations l Please read about these… You will hear about these throughout your education and career. 22
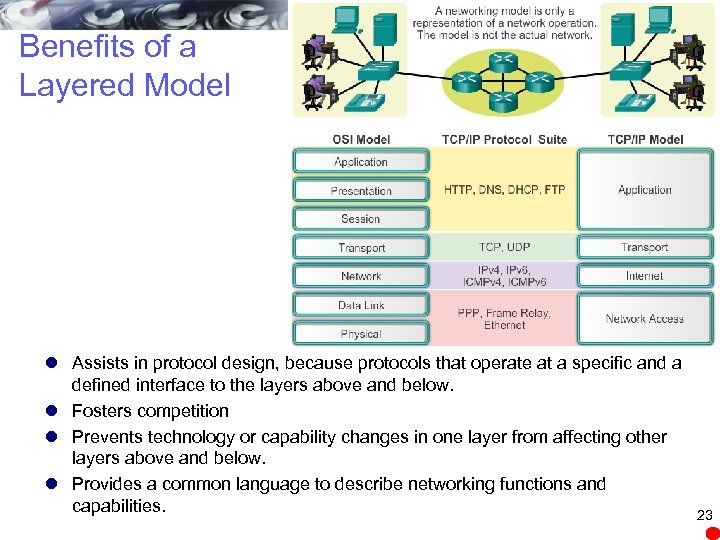 Benefits of a Layered Model l Assists in protocol design, because protocols that operate at a specific and a defined interface to the layers above and below. l Fosters competition l Prevents technology or capability changes in one layer from affecting other layers above and below. l Provides a common language to describe networking functions and capabilities. 23
Benefits of a Layered Model l Assists in protocol design, because protocols that operate at a specific and a defined interface to the layers above and below. l Fosters competition l Prevents technology or capability changes in one layer from affecting other layers above and below. l Provides a common language to describe networking functions and capabilities. 23
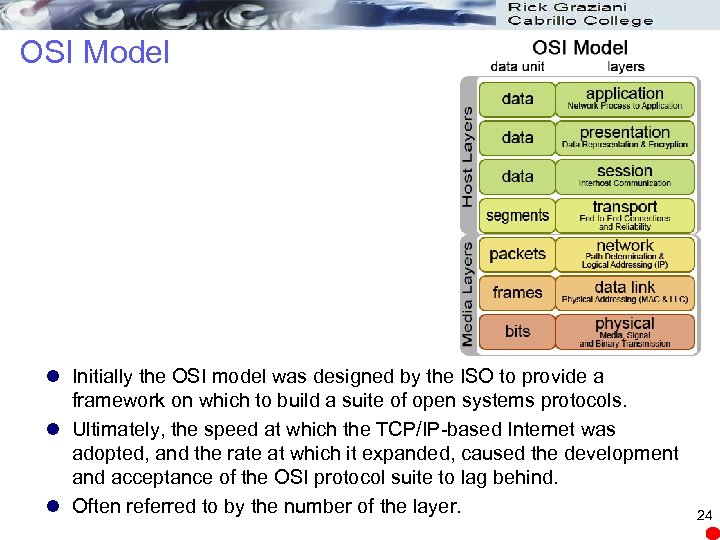 OSI Model l Initially the OSI model was designed by the ISO to provide a framework on which to build a suite of open systems protocols. l Ultimately, the speed at which the TCP/IP-based Internet was adopted, and the rate at which it expanded, caused the development and acceptance of the OSI protocol suite to lag behind. l Often referred to by the number of the layer. 24
OSI Model l Initially the OSI model was designed by the ISO to provide a framework on which to build a suite of open systems protocols. l Ultimately, the speed at which the TCP/IP-based Internet was adopted, and the rate at which it expanded, caused the development and acceptance of the OSI protocol suite to lag behind. l Often referred to by the number of the layer. 24
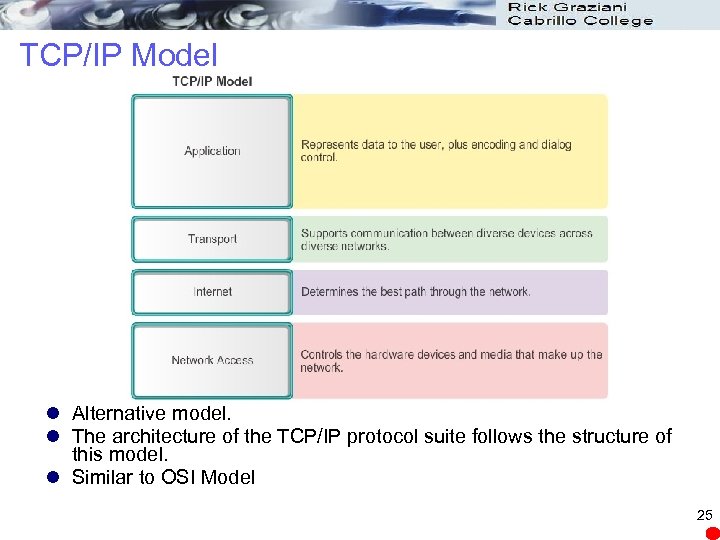 TCP/IP Model l Alternative model. l The architecture of the TCP/IP protocol suite follows the structure of this model. l Similar to OSI Model 25
TCP/IP Model l Alternative model. l The architecture of the TCP/IP protocol suite follows the structure of this model. l Similar to OSI Model 25
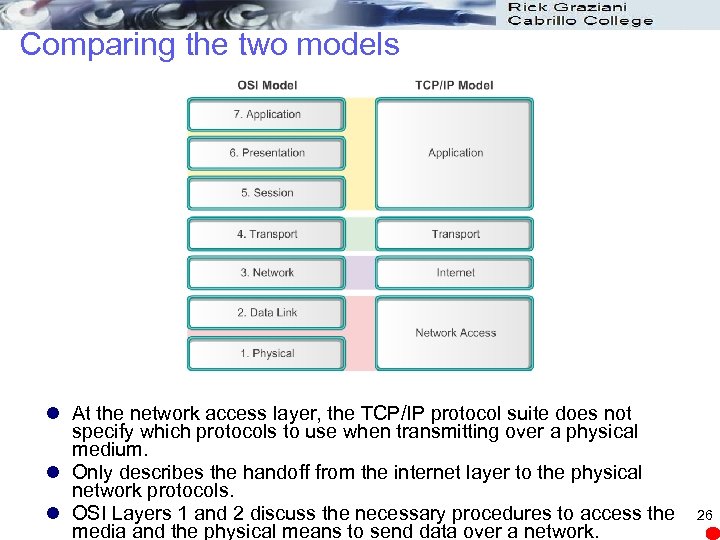 Comparing the two models l At the network access layer, the TCP/IP protocol suite does not specify which protocols to use when transmitting over a physical medium. l Only describes the handoff from the internet layer to the physical network protocols. l OSI Layers 1 and 2 discuss the necessary procedures to access the media and the physical means to send data over a network. 26
Comparing the two models l At the network access layer, the TCP/IP protocol suite does not specify which protocols to use when transmitting over a physical medium. l Only describes the handoff from the internet layer to the physical network protocols. l OSI Layers 1 and 2 discuss the necessary procedures to access the media and the physical means to send data over a network. 26
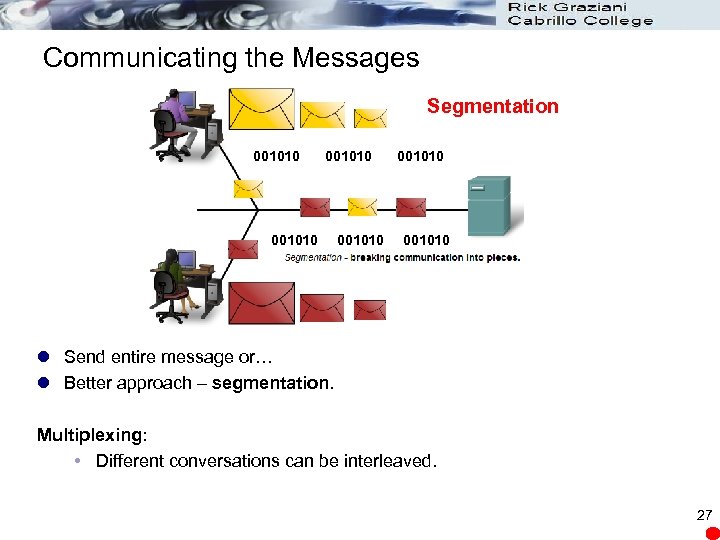 Communicating the Messages Segmentation 001010 001010 l Send entire message or… l Better approach – segmentation. Multiplexing: Different conversations can be interleaved. 27
Communicating the Messages Segmentation 001010 001010 l Send entire message or… l Better approach – segmentation. Multiplexing: Different conversations can be interleaved. 27
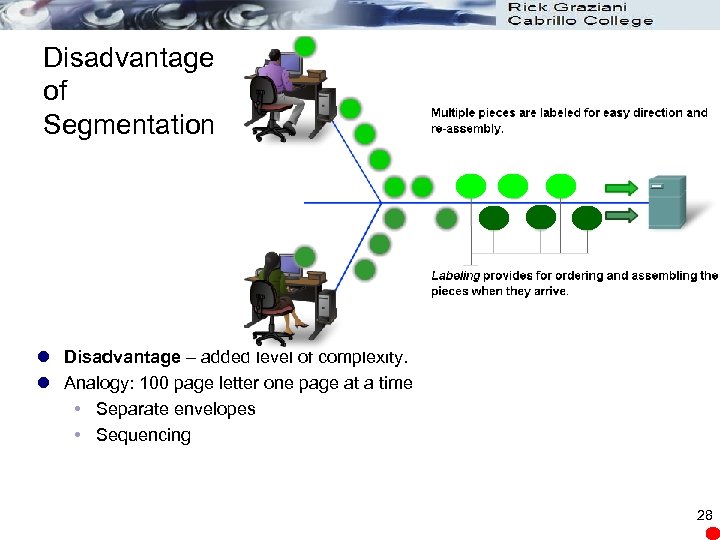 Disadvantage of Segmentation l Disadvantage – added level of complexity. l Analogy: 100 page letter one page at a time Separate envelopes Sequencing 28
Disadvantage of Segmentation l Disadvantage – added level of complexity. l Analogy: 100 page letter one page at a time Separate envelopes Sequencing 28
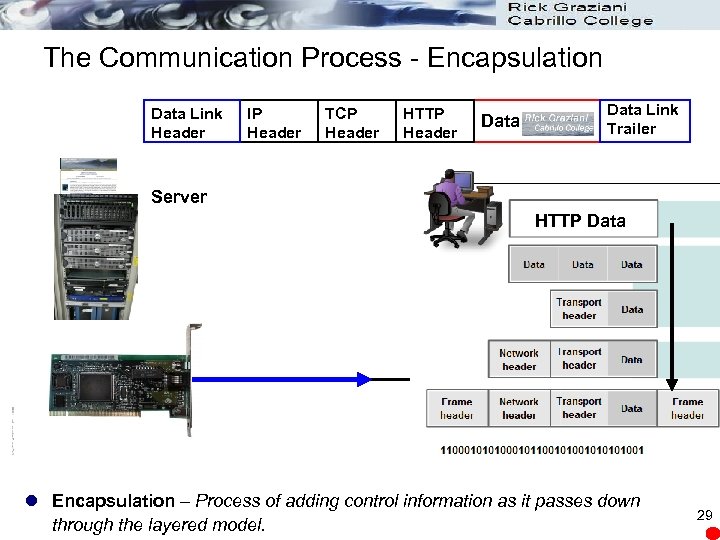 The Communication Process - Encapsulation Data Link Header IP Header TCP Header HTTP Header Data Link Trailer Server HTTP Data l Encapsulation – Process of adding control information as it passes down through the layered model. 29
The Communication Process - Encapsulation Data Link Header IP Header TCP Header HTTP Header Data Link Trailer Server HTTP Data l Encapsulation – Process of adding control information as it passes down through the layered model. 29
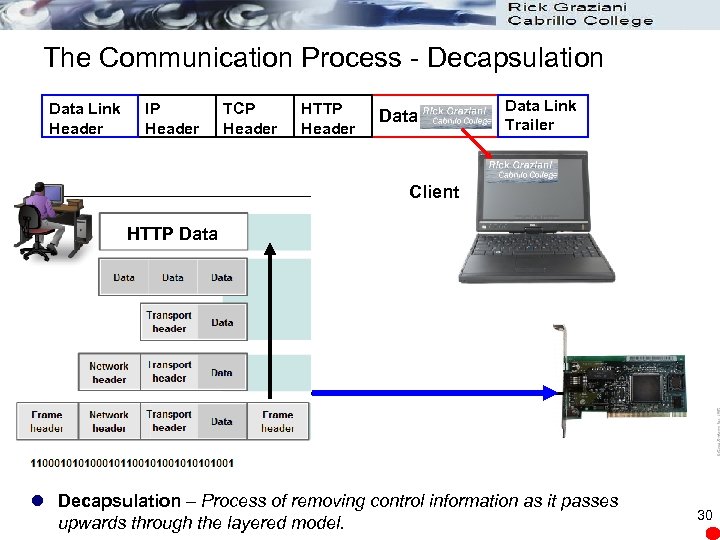 The Communication Process - Decapsulation Data Link Header IP Header TCP Header HTTP Header Data Link Trailer Client HTTP Data l Decapsulation – Process of removing control information as it passes upwards through the layered model. 30
The Communication Process - Decapsulation Data Link Header IP Header TCP Header HTTP Header Data Link Trailer Client HTTP Data l Decapsulation – Process of removing control information as it passes upwards through the layered model. 30
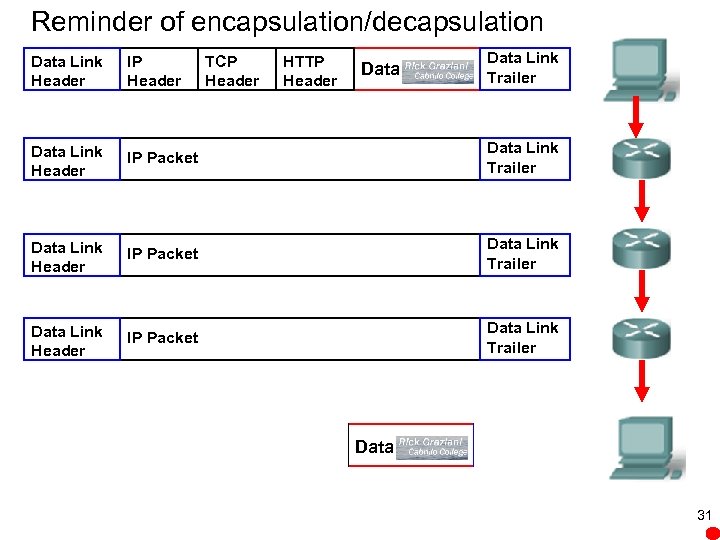 Reminder of encapsulation/decapsulation IP Header Data Link Header IP Packet Data Link Trailer Data Link Header IP Header TCP Header HTTP Header Data Link Trailer Data Link Header HTTP Header Data Link Trailer 31
Reminder of encapsulation/decapsulation IP Header Data Link Header IP Packet Data Link Trailer Data Link Header IP Header TCP Header HTTP Header Data Link Trailer Data Link Header HTTP Header Data Link Trailer 31
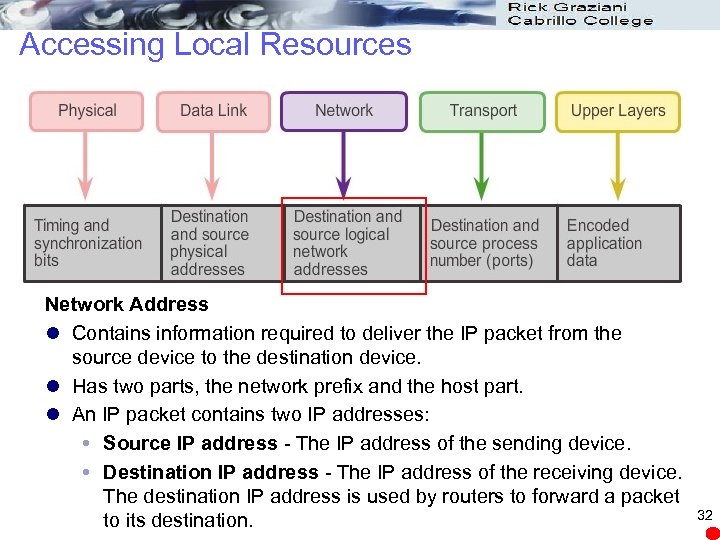 Accessing Local Resources Network Address l Contains information required to deliver the IP packet from the source device to the destination device. l Has two parts, the network prefix and the host part. l An IP packet contains two IP addresses: Source IP address - The IP address of the sending device. Destination IP address - The IP address of the receiving device. The destination IP address is used by routers to forward a packet to its destination. 32
Accessing Local Resources Network Address l Contains information required to deliver the IP packet from the source device to the destination device. l Has two parts, the network prefix and the host part. l An IP packet contains two IP addresses: Source IP address - The IP address of the sending device. Destination IP address - The IP address of the receiving device. The destination IP address is used by routers to forward a packet to its destination. 32
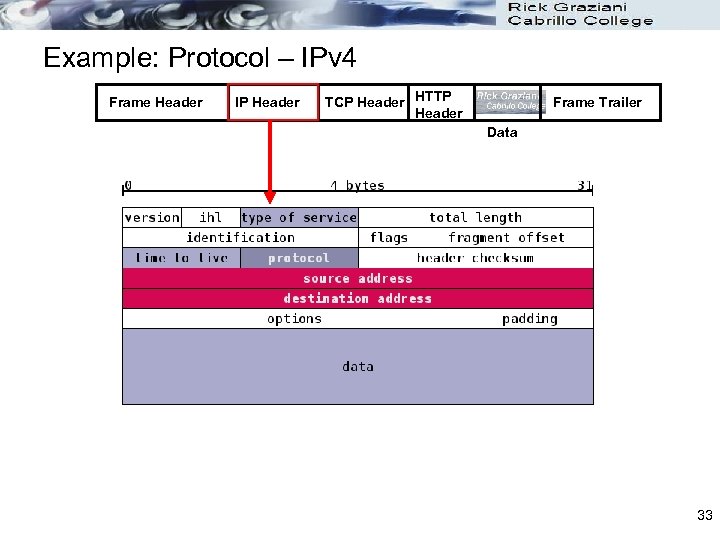 Example: Protocol – IPv 4 Frame Header IP Header TCP Header HTTP Header Frame Trailer Data 33
Example: Protocol – IPv 4 Frame Header IP Header TCP Header HTTP Header Frame Trailer Data 33
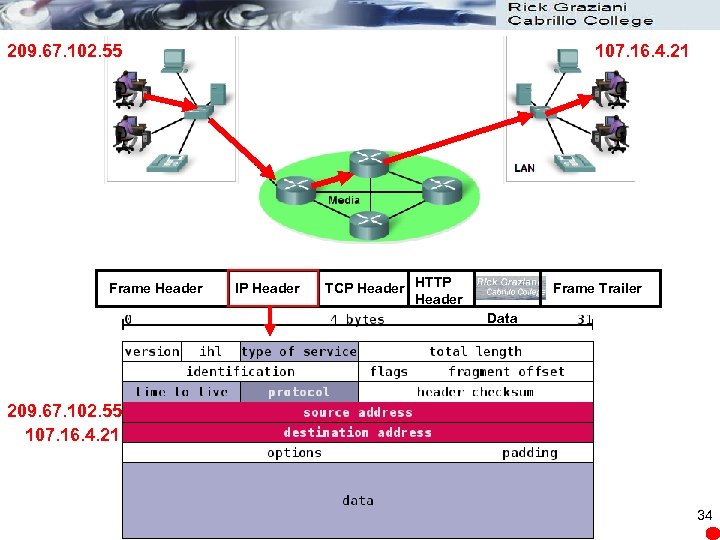 209. 67. 102. 55 Frame Header 107. 16. 4. 21 IP Header TCP Header HTTP Header Frame Trailer Data 209. 67. 102. 55 107. 16. 4. 21 34
209. 67. 102. 55 Frame Header 107. 16. 4. 21 IP Header TCP Header HTTP Header Frame Trailer Data 209. 67. 102. 55 107. 16. 4. 21 34
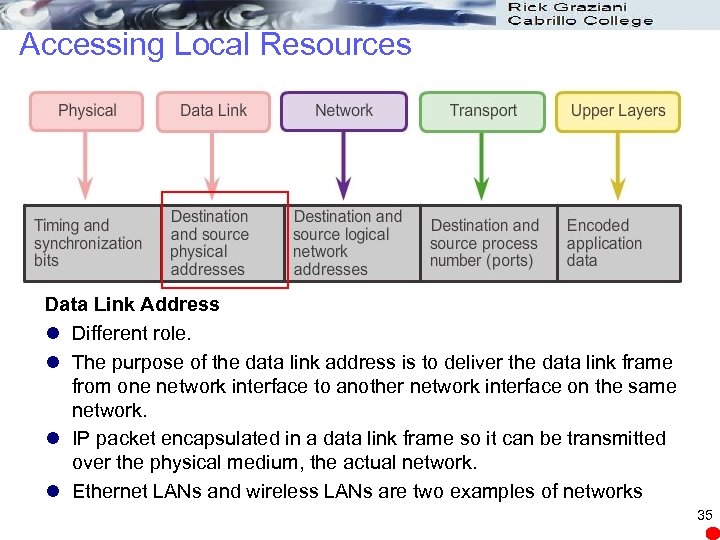 Accessing Local Resources Data Link Address l Different role. l The purpose of the data link address is to deliver the data link frame from one network interface to another network interface on the same network. l IP packet encapsulated in a data link frame so it can be transmitted over the physical medium, the actual network. l Ethernet LANs and wireless LANs are two examples of networks 35
Accessing Local Resources Data Link Address l Different role. l The purpose of the data link address is to deliver the data link frame from one network interface to another network interface on the same network. l IP packet encapsulated in a data link frame so it can be transmitted over the physical medium, the actual network. l Ethernet LANs and wireless LANs are two examples of networks 35
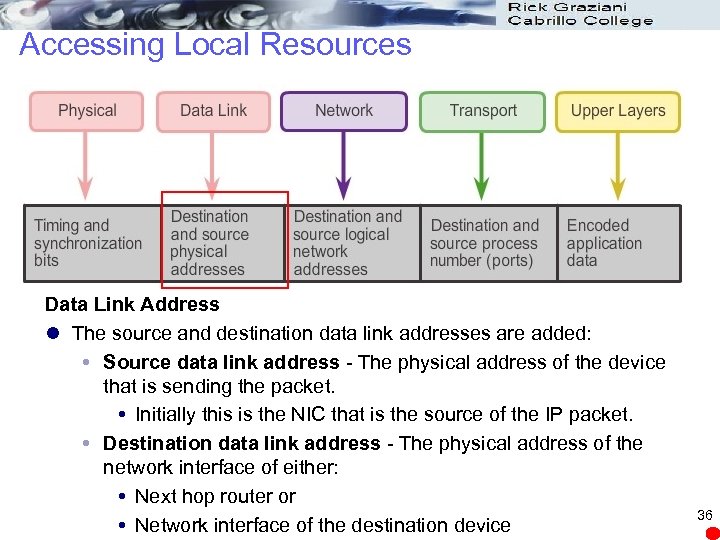 Accessing Local Resources Data Link Address l The source and destination data link addresses are added: Source data link address - The physical address of the device that is sending the packet. Initially this is the NIC that is the source of the IP packet. Destination data link address - The physical address of the network interface of either: Next hop router or Network interface of the destination device 36
Accessing Local Resources Data Link Address l The source and destination data link addresses are added: Source data link address - The physical address of the device that is sending the packet. Initially this is the NIC that is the source of the IP packet. Destination data link address - The physical address of the network interface of either: Next hop router or Network interface of the destination device 36
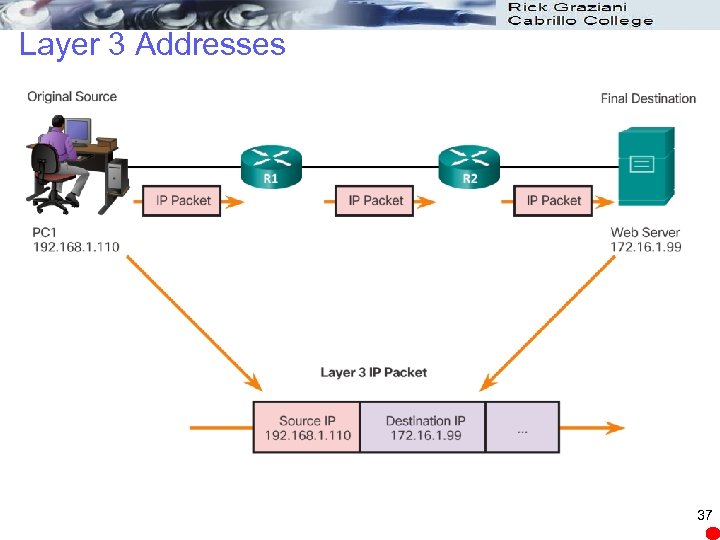 Layer 3 Addresses 37
Layer 3 Addresses 37
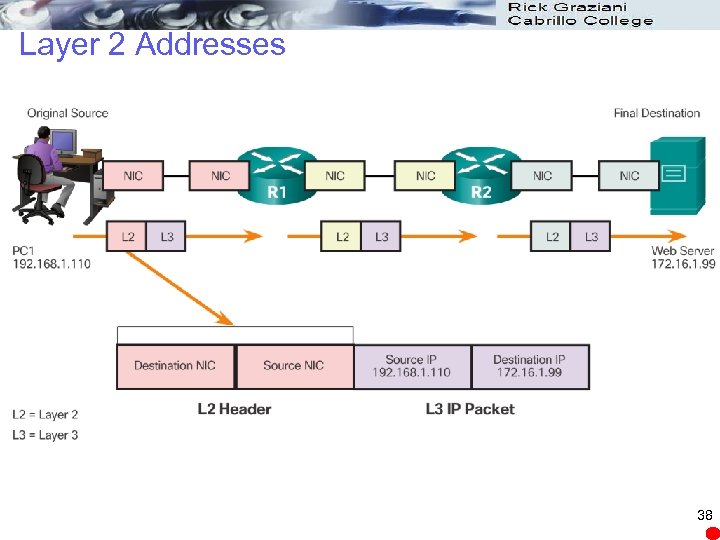 Layer 2 Addresses 38
Layer 2 Addresses 38
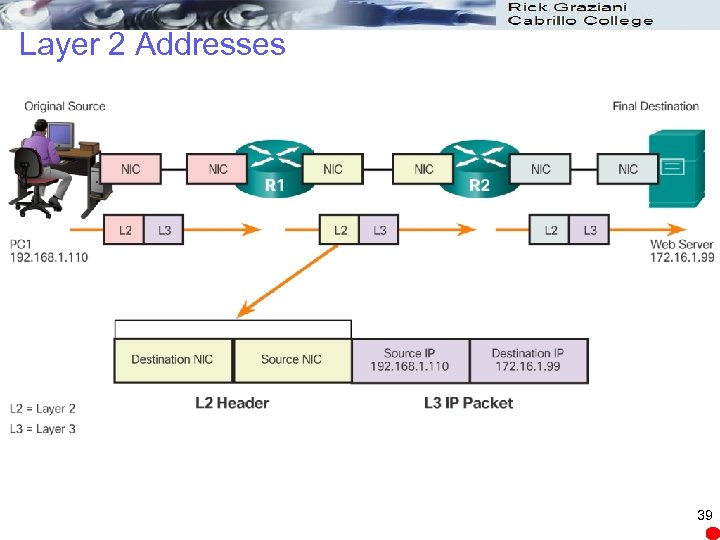 Layer 2 Addresses 39
Layer 2 Addresses 39
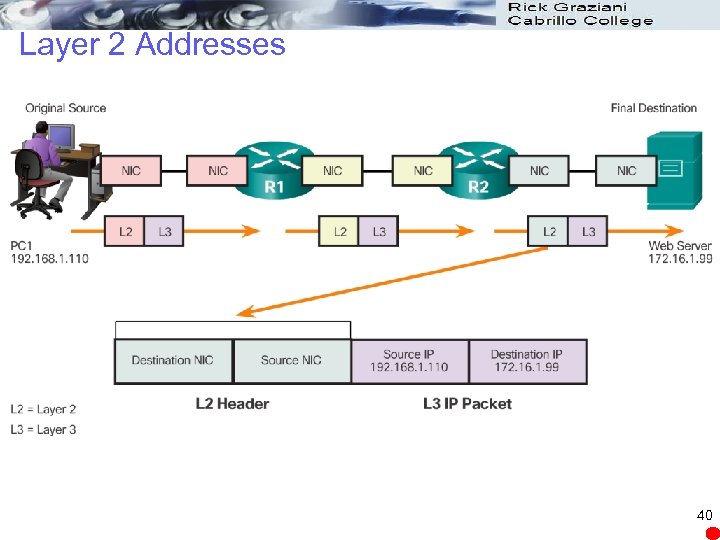 Layer 2 Addresses 40
Layer 2 Addresses 40
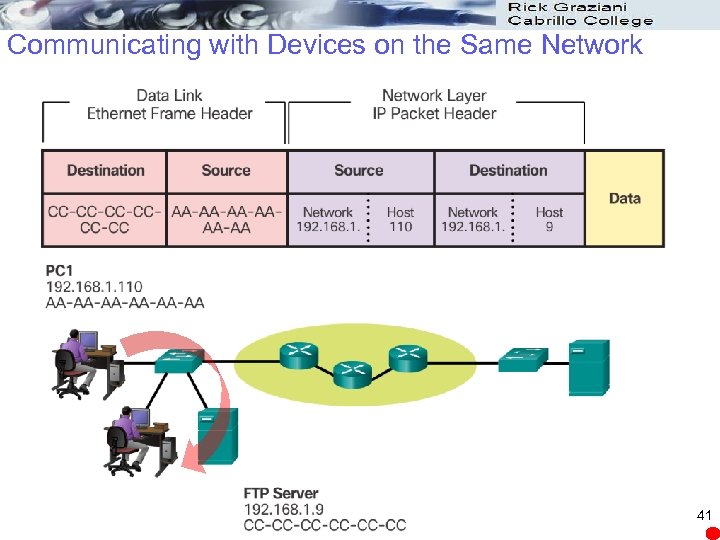 Communicating with Devices on the Same Network 41
Communicating with Devices on the Same Network 41
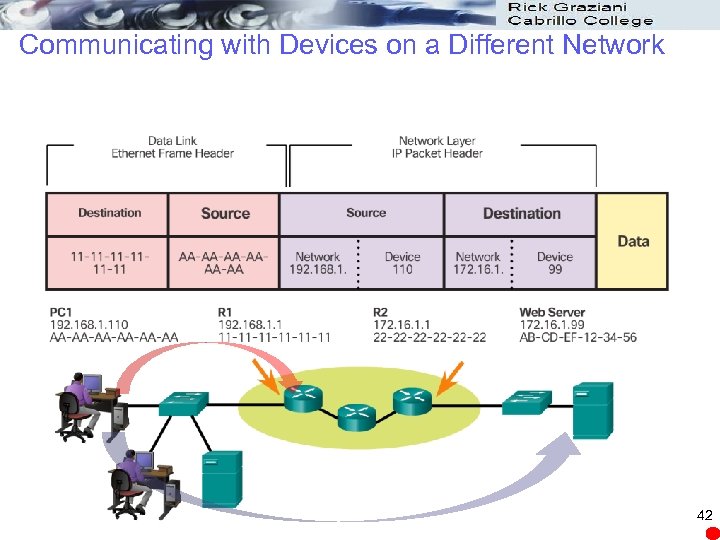 Communicating with Devices on a Different Network 42
Communicating with Devices on a Different Network 42
 Your Turn 47
Your Turn 47
 Your Turn 48
Your Turn 48
 Your Turn 49
Your Turn 49
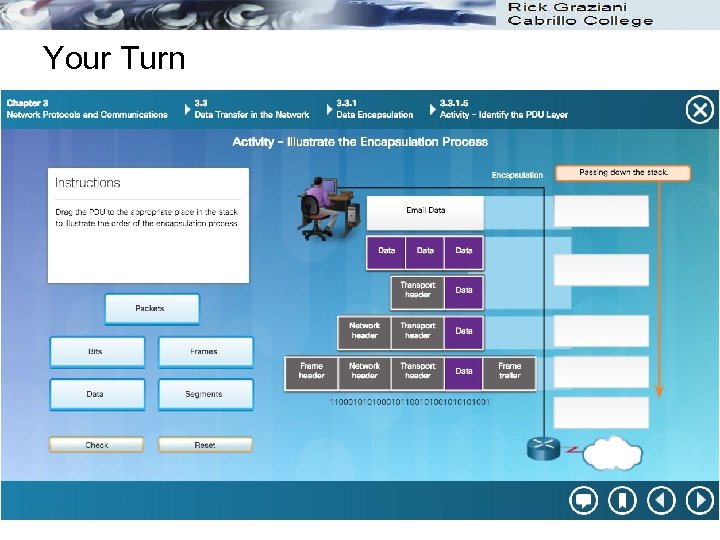 Your Turn 50
Your Turn 50
 CIS 81 Fundamentals of Networking Chapter 3: Network Protocols and Communications Rick Graziani Cabrillo College graziani@cabrillo. edu
CIS 81 Fundamentals of Networking Chapter 3: Network Protocols and Communications Rick Graziani Cabrillo College graziani@cabrillo. edu


