75c2aa0d2940b35fa4dad8a4770ce5bd.ppt
- Количество слайдов: 19

CIS 3360: Chapter 8: Cryptography Application of Public Cryptography Cliff Zou Spring 2012 Network Security 7 -1

Acknowledgement r Some slides are modified from the slides provided by textbook: v Computer Networking: A Top Down Approach Featuring the Internet, J. Kurose & K. Ross, Addison Wesley, 4 rd ed. , 2007 Network Security 7 -2

Digital Signatures Cryptographic technique analogous to handwritten signatures. r sender (Bob) digitally signs document, establishing he is document owner/creator. r verifiable, nonforgeable: recipient (Alice) can prove to someone that Bob, and no one else (including Alice), must have signed document Network Security 7 -3
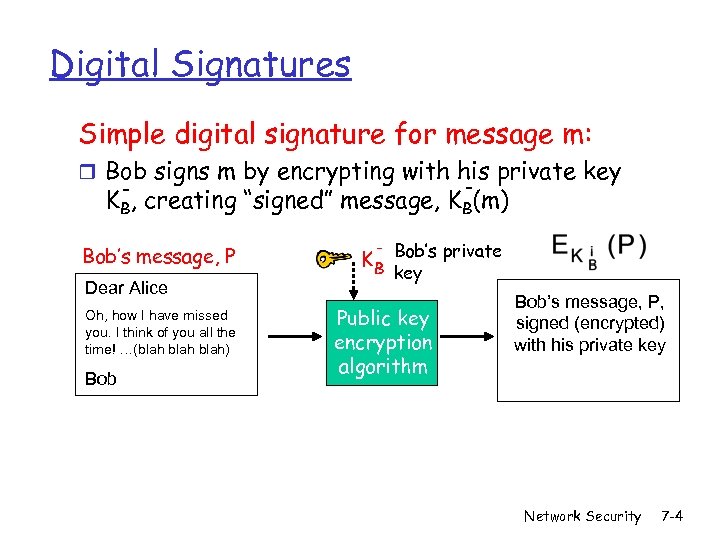
Digital Signatures Simple digital signature for message m: r Bob signs m by encrypting with his private key - KB, creating “signed” message, KB(m) Bob’s message, P Dear Alice Oh, how I have missed you. I think of you all the time! …(blah) Bob K B Bob’s private key Public key encryption algorithm Bob’s message, P, signed (encrypted) with his private key Network Security 7 -4
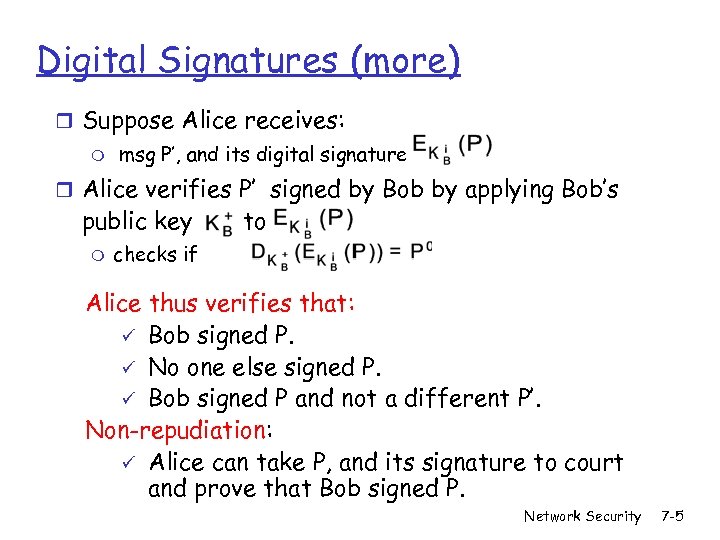
Digital Signatures (more) r Suppose Alice receives: m msg P’, and its digital signature r Alice verifies P’ signed by Bob by applying Bob’s public key m to checks if Alice thus verifies that: ü Bob signed P. ü No one else signed P. ü Bob signed P and not a different P’. Non-repudiation: ü Alice can take P, and its signature to court and prove that Bob signed P. Network Security 7 -5
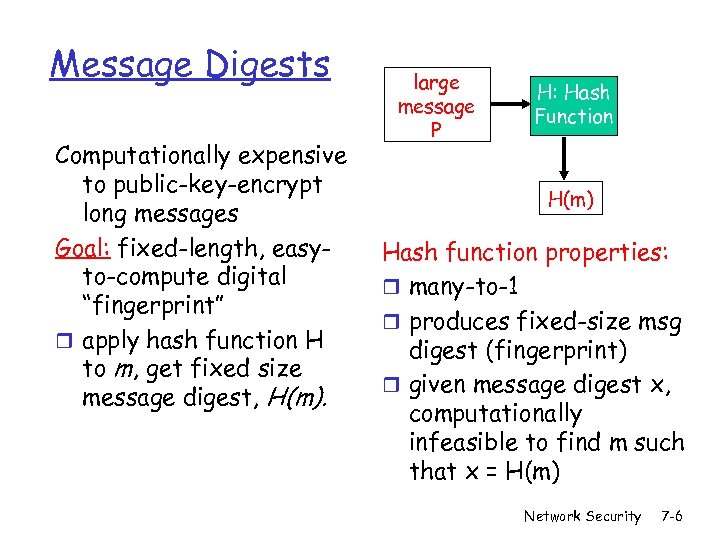
Message Digests Computationally expensive to public-key-encrypt long messages Goal: fixed-length, easyto-compute digital “fingerprint” r apply hash function H to m, get fixed size message digest, H(m). large message P H: Hash Function H(m) Hash function properties: r many-to-1 r produces fixed-size msg digest (fingerprint) r given message digest x, computationally infeasible to find m such that x = H(m) Network Security 7 -6
Hash Function Algorithms r MD 5 hash function widely used (RFC 1321) m computes 128 -bit message digest in 4 -step process. m arbitrary 128 -bit string x, appears difficult to construct msg m whose MD 5 hash is equal to x. r SHA-1 is also used. m US standard [NIST, FIPS PUB 180 -1] m 160 -bit message digest Network Security 7 -7
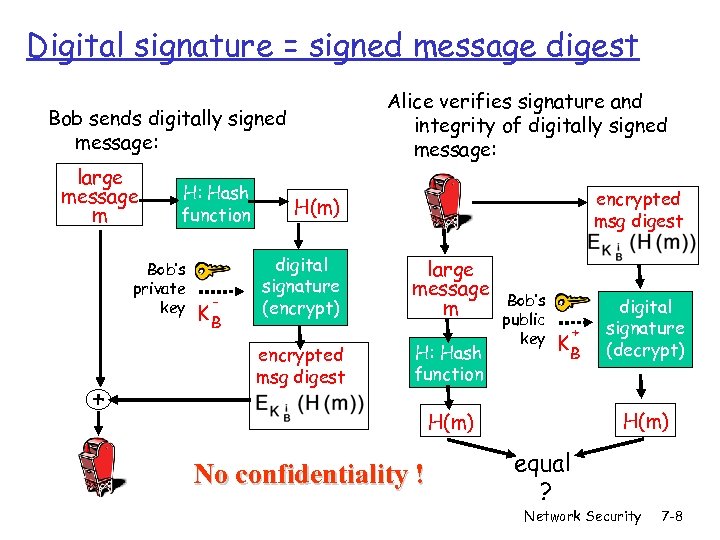
Digital signature = signed message digest Alice verifies signature and integrity of digitally signed message: Bob sends digitally signed message: large message m H: Hash function Bob’s private key + - KB encrypted msg digest H(m) digital signature (encrypt) encrypted msg digest large message m H: Hash function Bob’s public key H(m) No confidentiality ! + KB digital signature (decrypt) equal ? Network Security 7 -8
Trusted Intermediaries Public key problem: r When Alice obtains Bob’s public key (from web site, e-mail, diskette), how does she know it is Bob’s public key, not Trudy’s? Solution: r trusted certification authority (CA) Network Security 7 -9
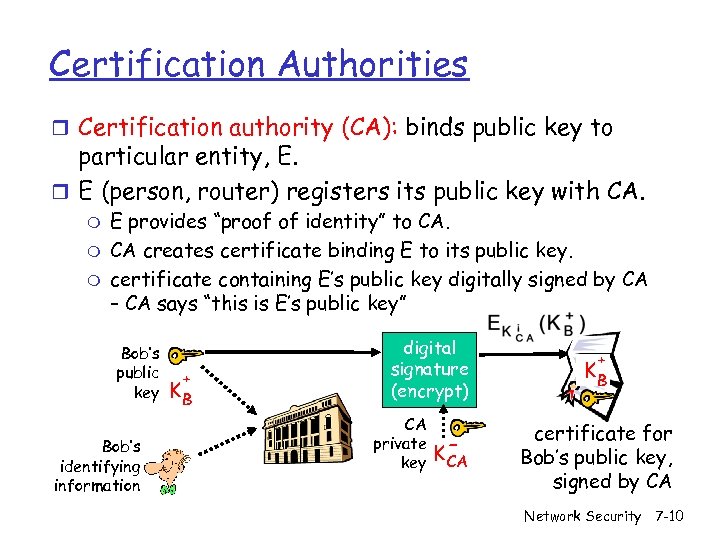
Certification Authorities r Certification authority (CA): binds public key to particular entity, E. r E (person, router) registers its public key with CA. m m m E provides “proof of identity” to CA. CA creates certificate binding E to its public key. certificate containing E’s public key digitally signed by CA – CA says “this is E’s public key” Bob’s public key Bob’s identifying information + KB digital signature (encrypt) CA private key K- CA + KB certificate for Bob’s public key, signed by CA Network Security 7 -10
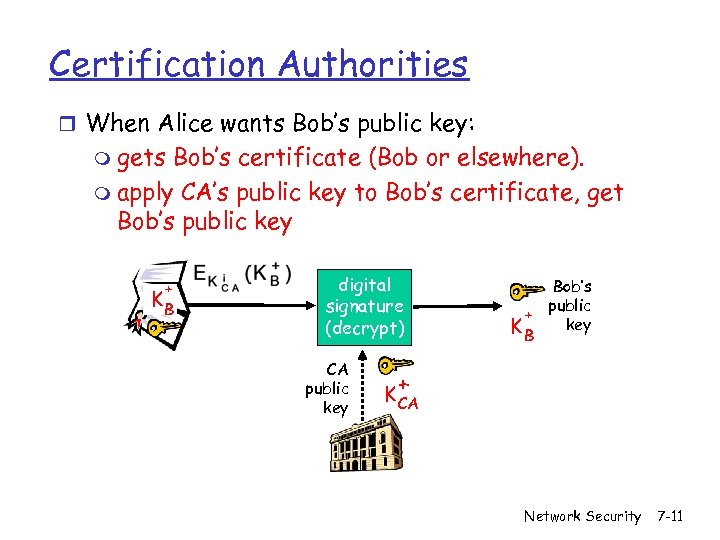
Certification Authorities r When Alice wants Bob’s public key: m gets Bob’s certificate (Bob or elsewhere). m apply CA’s public key to Bob’s certificate, get Bob’s public key + KB digital signature (decrypt) CA public key Bob’s public + key KB + K CA Network Security 7 -11
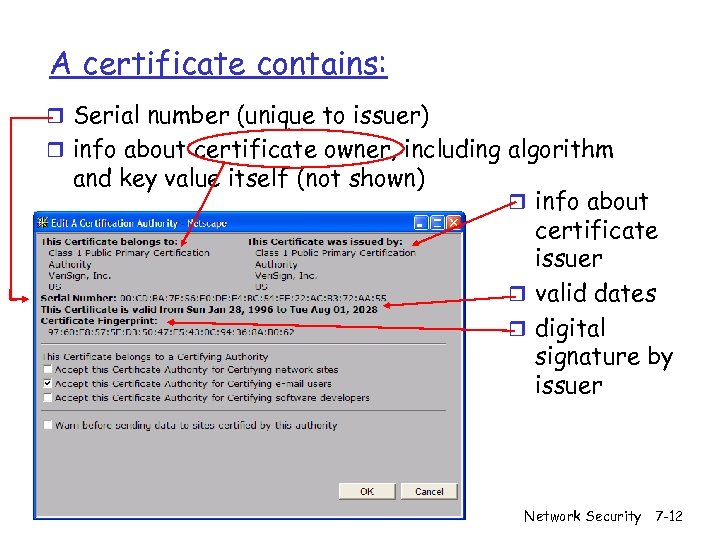
A certificate contains: r Serial number (unique to issuer) r info about certificate owner, including algorithm and key value itself (not shown) r info about certificate issuer r valid dates r digital signature by issuer Network Security 7 -12
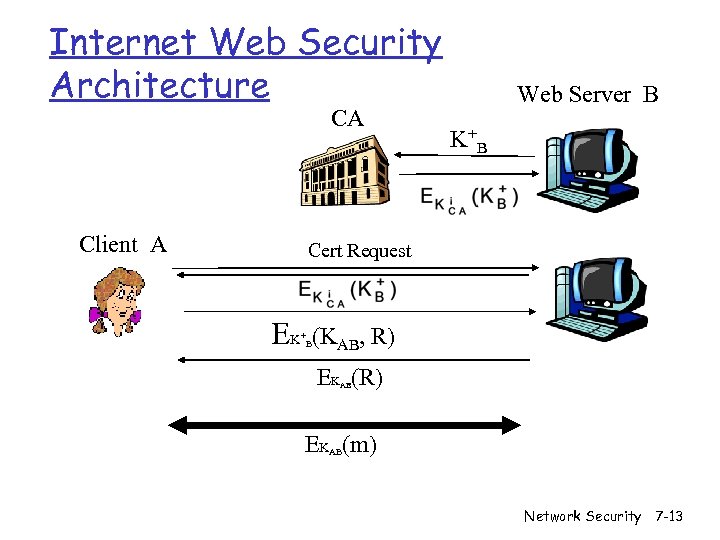
Internet Web Security Architecture CA Client A Web Server B K+ B Cert Request EK + (KAB, R) B EK (R) AB EK (m) AB Network Security 7 -13

Internet Web Security Conditions r Clients’ web browsers have built-in CAs. r CAs are trustable r Web servers have certificates in CAs. r Q: What if a server has no certificate? m Example: SSH servers Network Security 7 -14
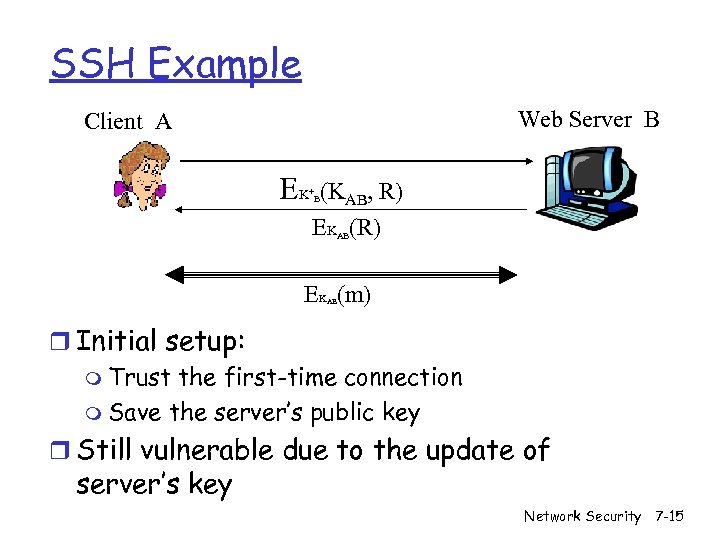
SSH Example Web Server B Client A EK + (KAB, R) B EK (R) AB EK (m) AB r Initial setup: m Trust the first-time connection m Save the server’s public key r Still vulnerable due to the update of server’s key Network Security 7 -15
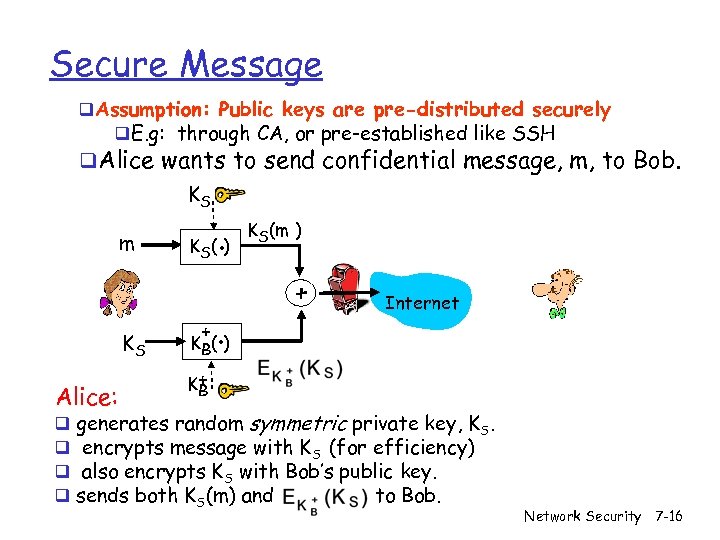
Secure Message q. Assumption: Public keys are pre-distributed securely q. E. g: through CA, or pre-established like SSH q. Alice wants to send confidential message, m, to Bob. KS m KS Alice: q q . K S( ) + . KS(m ) + Internet K B( ) K+ B generates random symmetric private key, KS. encrypts message with KS (for efficiency) also encrypts KS with Bob’s public key. sends both KS(m) and to Bob. Network Security 7 -16
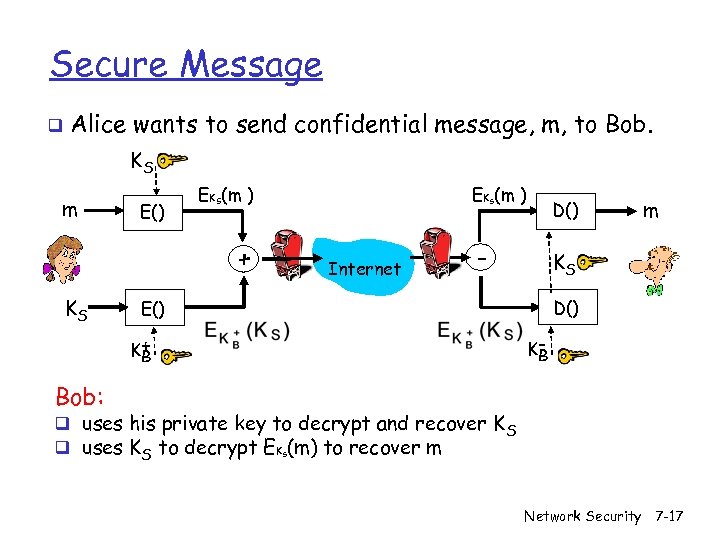
Secure Message q Alice wants to send confidential message, m, to Bob. KS m E() + KS EKS(m ) Internet - m KS D() E() K+ B D() KB Bob: q uses his private key to decrypt and recover K S q uses KS to decrypt EKS(m) to recover m Network Security 7 -17
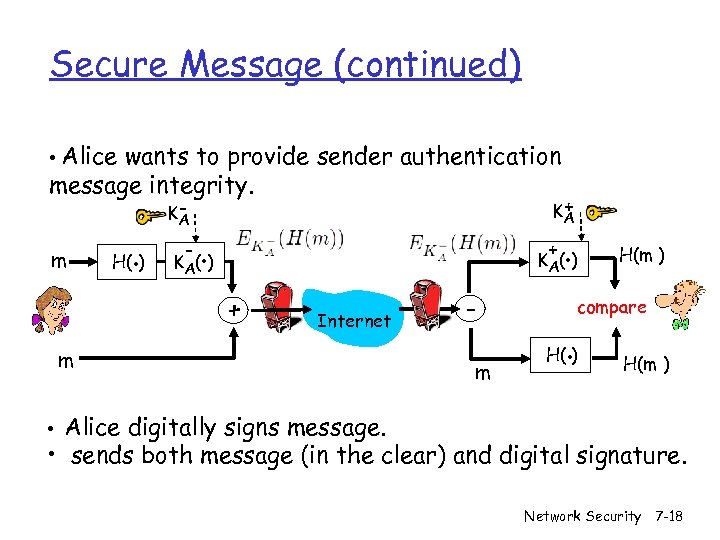
Secure Message (continued) • Alice wants to provide sender authentication message integrity. m H(. ) KA - + KA . + . K A( ) + Internet m m H(m ) compare . H( ) H(m ) • Alice digitally signs message. • sends both message (in the clear) and digital signature. Network Security 7 -18
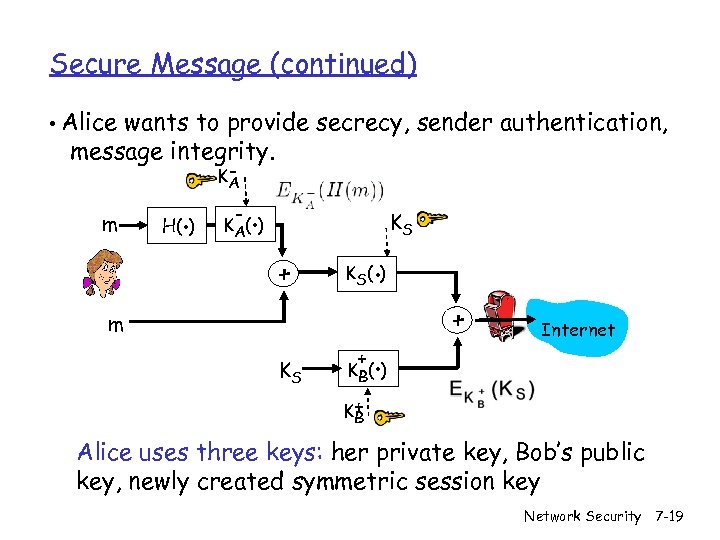
Secure Message (continued) • Alice wants to provide secrecy, sender authentication, message integrity. m . H( ) KA - . KS K A( ) + . K S( ) m KS + . + Internet K B( ) K+ B Alice uses three keys: her private key, Bob’s public key, newly created symmetric session key Network Security 7 -19
75c2aa0d2940b35fa4dad8a4770ce5bd.ppt