998bd93d9145042832e1c1dcfd384706.ppt
- Количество слайдов: 13

CIPC Confidentiality: Public Release NERC CIPC March 16, 2006 Roadmap to Secure Control Systems in the Energy Sector U. S. Department of Energy Office of Electricity Delivery and Energy Reliability Hank Kenchington 202 -586 -1878 henry. kenchington@hq. doe. gov
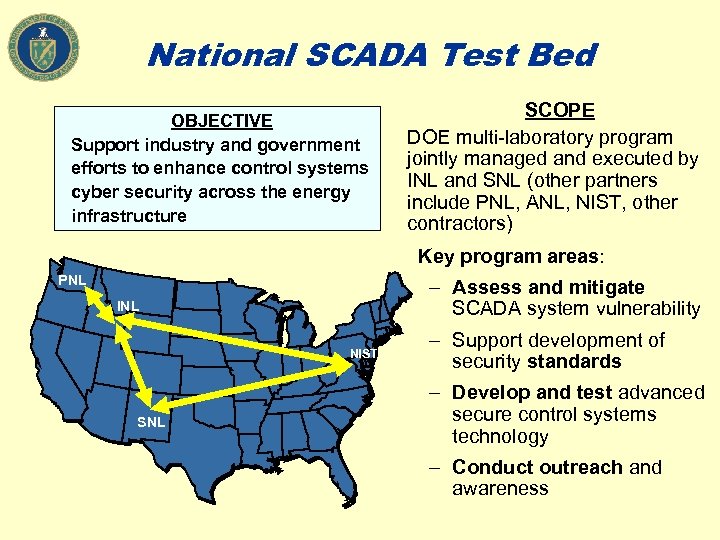
National SCADA Test Bed OBJECTIVE Support industry and government efforts to enhance control systems cyber security across the energy infrastructure SCOPE DOE multi-laboratory program jointly managed and executed by INL and SNL (other partners include PNL, ANL, NIST, other contractors) Key program areas: PNL – Assess and mitigate SCADA system vulnerability INL NIST SNL – Support development of security standards – Develop and test advanced secure control systems technology – Conduct outreach and awareness

National SCADA Test Bed Key Activities: 1. SCADA System Assessments - ABB, AREVA, GE, Siemens 2. Provided cyber security training to over 400 end-users 3. Evaluated use of COTS IT antivirus and firewall tools in control systems 4. Working closely with electricity sector, developed mitigation strategies for “top 10” vulnerabilities 5. Conducting performance testing and cryptographic analysis of AGA 12 6. Evaluated and cataloged existing SCADA Standards Results: 1. New “hardened” SCADA systems now being deployed 2. Software patches developed by vendors and supplied to end-users to better secure existing systems
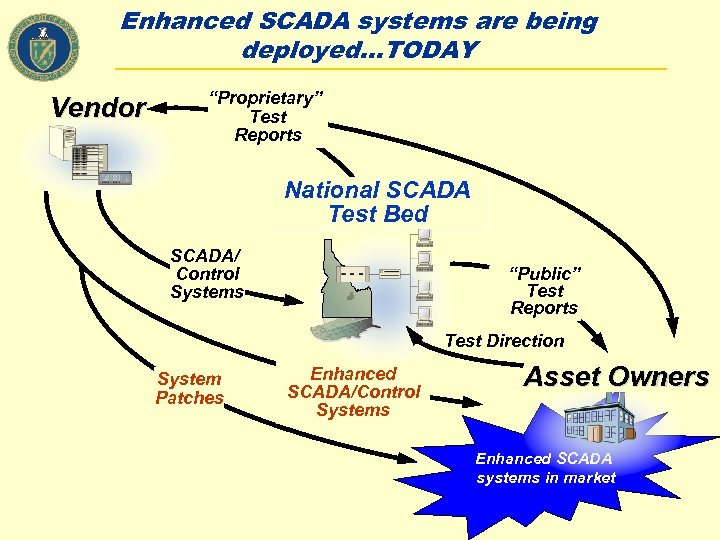
Enhanced SCADA systems are being deployed…TODAY Vendor “Proprietary” Test Reports National SCADA Test Bed SCADA/ Control Systems “Public” Test Reports Test Direction System Patches Enhanced SCADA/Control Systems Asset Owners Enhanced SCADA systems in market
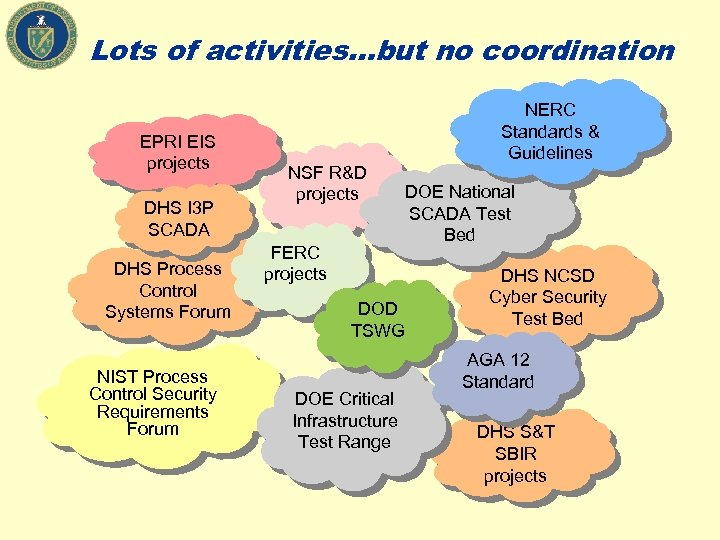
Lots of activities…but no coordination EPRI EIS projects DHS I 3 P SCADA DHS Process Control Systems Forum NIST Process Control Security Requirements Forum NSF R&D projects FERC projects NERC Standards & Guidelines DOE National SCADA Test Bed DOD TSWG DOE Critical Infrastructure Test Range DHS NCSD Cyber Security Test Bed AGA 12 Standard DHS S&T SBIR projects
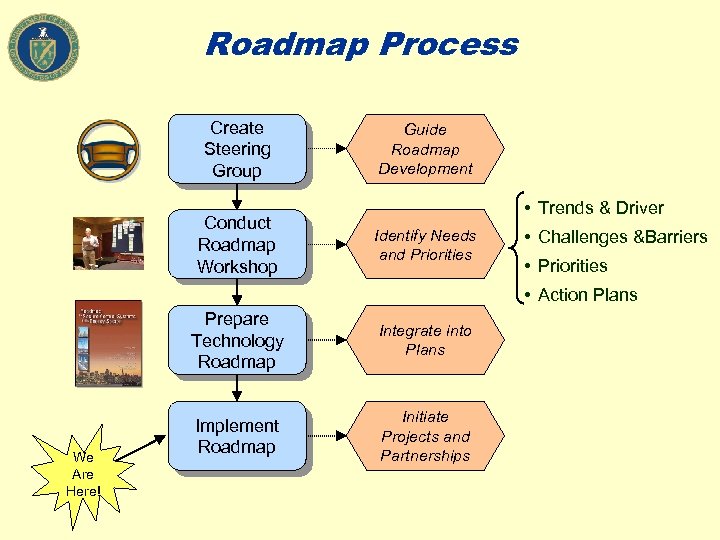
Roadmap Process Create Steering Group Conduct Roadmap Workshop Guide Roadmap Development • Trends & Driver Identify Needs and Priorities • Challenges &Barriers • Priorities • Action Plans Prepare Technology Roadmap We Are Here! Integrate into Plans Implement Roadmap Initiate Projects and Partnerships

Roadmap Steering Committee Asset Owners and Operators Government • Tom Flowers - Center. Point Energy (electricity) • Linda Nappier – Ameren (electricity) • Al Rivero – formerly w/Chevron (oil and gas) • David Poczynek – Williams Co. (oil and gas) • Tom Frobase – TEPPCO (oil and gas) • Michael Assante – formerly w/AEP and IEIA Forum • Doug Maughan – U. S. DHS • Hank Kenchington – U. S. DOE • David Darling – Natural Resources Canada Industry Organizations • • • Bill Rush – GTI Lisa Soda – API Kimberly Denbow – AGA Gary Gardner – AGA Tom Kropp - EPRI Researchers (National Laboratories) • Tommy Cabe – Sandia National Laboratories • Jeff Dagle – Pacific Northwest National Laboratory • Bob Hill – Idaho National Laboratory
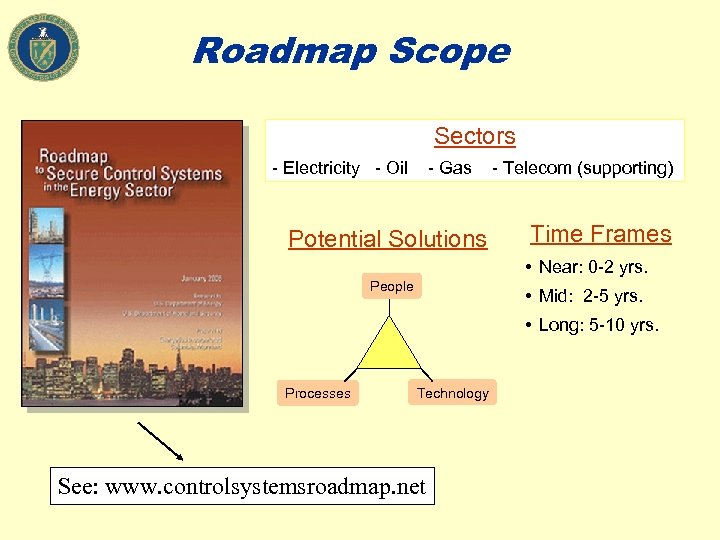
Roadmap Scope Sectors - Electricity - Oil - Gas Potential Solutions - Telecom (supporting) Time Frames • Near: 0 -2 yrs. People • Mid: 2 -5 yrs. • Long: 5 -10 yrs. Processes Technology See: www. controlsystemsroadmap. net

Workshop Participants Target Participants Operations, 5 Commercial Suppliers Industry Organizations 7 Government 15 & Labs 8 Asset Owners and Operators Business and Security, 10 30 Control Systems, 15 • Led by energy sector owners and operators • Includes representatives from electricity, oil, gas, telecom industries • Engages a cross-section of stakeholders and experts
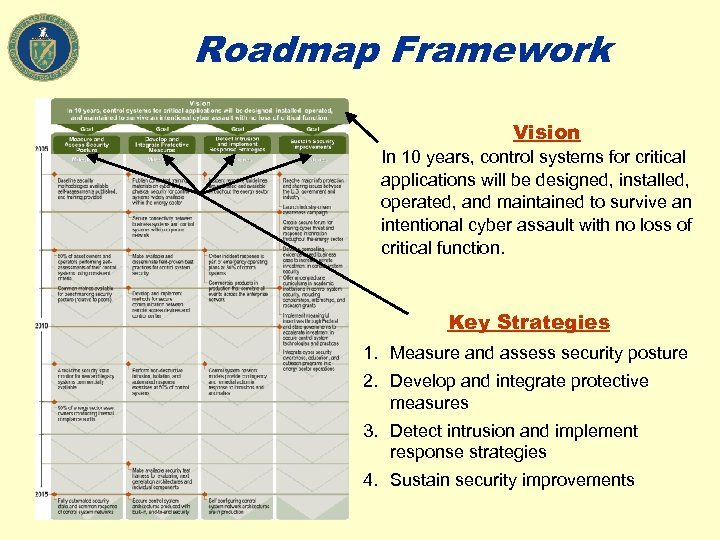
Roadmap Framework Vision In 10 years, control systems for critical applications will be designed, installed, operated, and maintained to survive an intentional cyber assault with no loss of critical function. Key Strategies 1. Measure and assess security posture 2. Develop and integrate protective measures 3. Detect intrusion and implement response strategies 4. Sustain security improvements
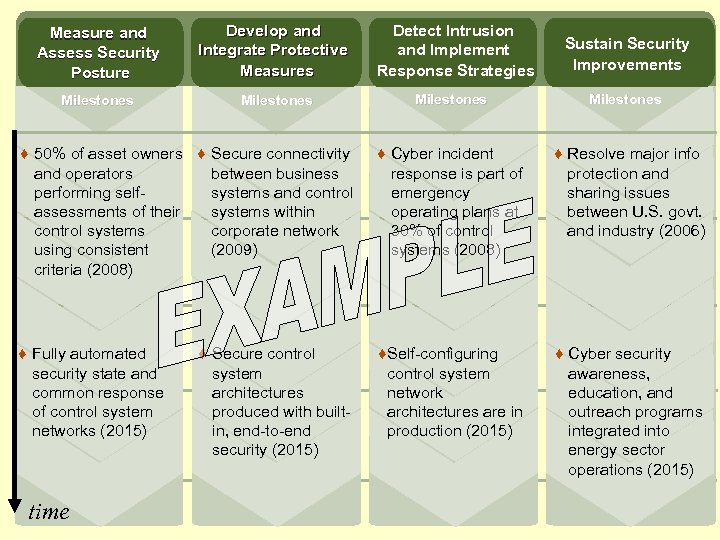
Measure and Assess Security Posture Develop and Integrate Protective Measures Milestones Detect Intrusion and Implement Response Strategies Sustain Security Improvements Milestones ♦ 50% of asset owners ♦ Secure connectivity and operators between business performing selfsystems and control assessments of their systems within control systems corporate network using consistent (2009) criteria (2008) ♦ Cyber incident response is part of emergency operating plans at 30% of control systems (2008) ♦ Resolve major info protection and sharing issues between U. S. govt. and industry (2006) ♦ Fully automated security state and common response of control system networks (2015) ♦Self-configuring control system network architectures are in production (2015) ♦ Cyber security awareness, education, and outreach programs integrated into energy sector operations (2015) time ♦ Secure control system architectures produced with builtin, end-to-end security (2015)
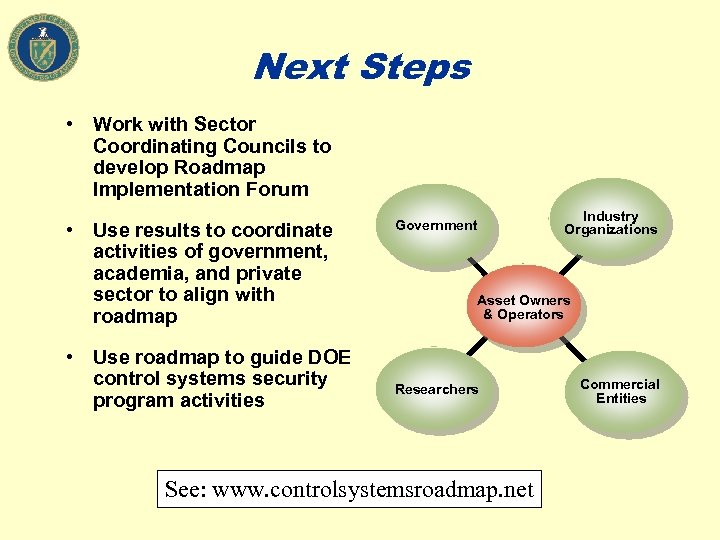
Next Steps • Work with Sector Coordinating Councils to develop Roadmap Implementation Forum • Use results to coordinate activities of government, academia, and private sector to align with roadmap • Use roadmap to guide DOE control systems security program activities Government Industry Organizations Asset Owners & Operators Researchers See: www. controlsystemsroadmap. net Commercial Entities

END US Department of Energy Office of Electricity Delivery and Energy Reliability Hank Kenchington henry. kenchington@hq. doe. gov 202 -586 -1878
998bd93d9145042832e1c1dcfd384706.ppt