77dc54309e39a8aa87c6fc5321ad6e6d.ppt
- Количество слайдов: 33
 Check Point Endpoint Security Secure. Fast. Simple Date Name © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 1
Check Point Endpoint Security Secure. Fast. Simple Date Name © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 1
 Agenda § Endpoint Security Challenges Today § The Check Point Solution – – Comprehensive endpoint security Secure, fast and simple to use Market leading data security Optimized Total Security § Summary © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 2
Agenda § Endpoint Security Challenges Today § The Check Point Solution – – Comprehensive endpoint security Secure, fast and simple to use Market leading data security Optimized Total Security § Summary © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 2
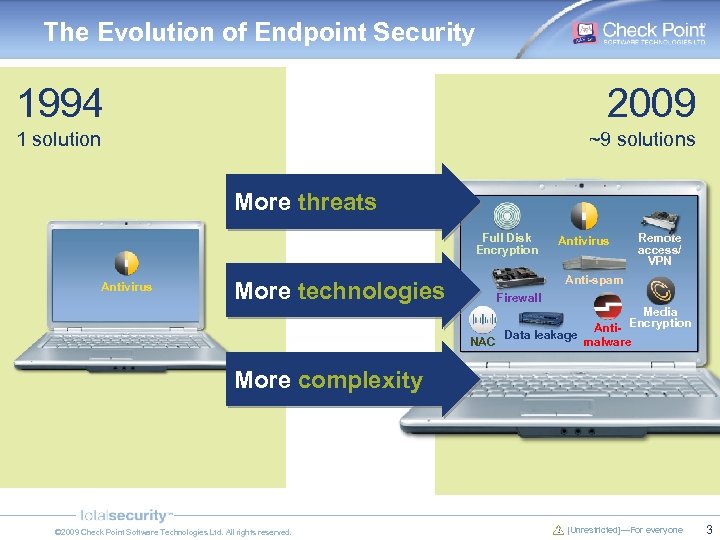 The Evolution of Endpoint Security 1994 2009 1 solution ~9 solutions More threats Full Disk Encryption Antivirus More technologies Antivirus Remote access/ VPN Anti-spam Firewall Media Encryption Anti. Data leakage NAC malware More complexity © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 3
The Evolution of Endpoint Security 1994 2009 1 solution ~9 solutions More threats Full Disk Encryption Antivirus More technologies Antivirus Remote access/ VPN Anti-spam Firewall Media Encryption Anti. Data leakage NAC malware More complexity © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 3
 Too Much End User Complexity Security updates and patching Repeated security logons Multiple passwords Multiple security applications Reconnecting to VPN Trying to reconfigure VPN © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 4
Too Much End User Complexity Security updates and patching Repeated security logons Multiple passwords Multiple security applications Reconnecting to VPN Trying to reconfigure VPN © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 4
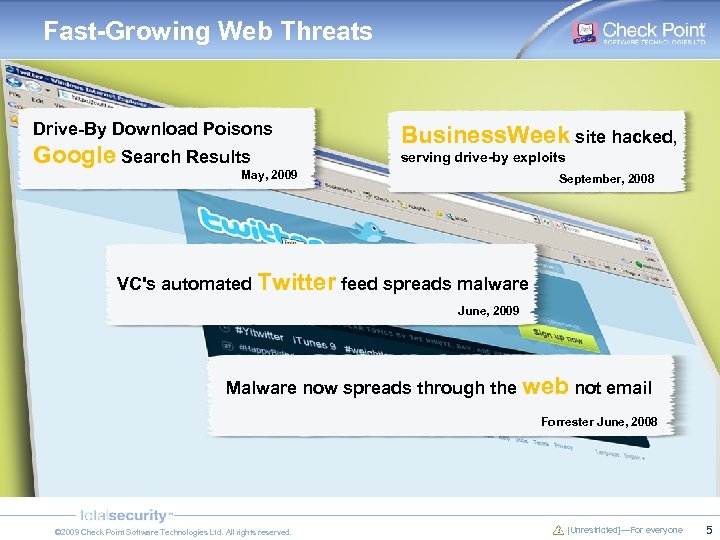 Fast-Growing Web Threats Drive-By Download Poisons Google Search Results Business. Week site hacked, serving drive-by exploits May, 2009 September, 2008 VC's automated Twitter feed spreads malware June, 2009 Malware now spreads through the web not email Forrester June, 2008 © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 5
Fast-Growing Web Threats Drive-By Download Poisons Google Search Results Business. Week site hacked, serving drive-by exploits May, 2009 September, 2008 VC's automated Twitter feed spreads malware June, 2009 Malware now spreads through the web not email Forrester June, 2008 © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 5
 The Headache of Data Security 53% of professionals have confidential data on their laptop 65% don’t protect them 12, 000 61% stolen laptops in U. S. airports/week of data breaches due to lack of policy enforcement Dell & Ponemon Institute, Airport Insecurity: the case of lost laptops, June 30, 2008 © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 6
The Headache of Data Security 53% of professionals have confidential data on their laptop 65% don’t protect them 12, 000 61% stolen laptops in U. S. airports/week of data breaches due to lack of policy enforcement Dell & Ponemon Institute, Airport Insecurity: the case of lost laptops, June 30, 2008 © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 6
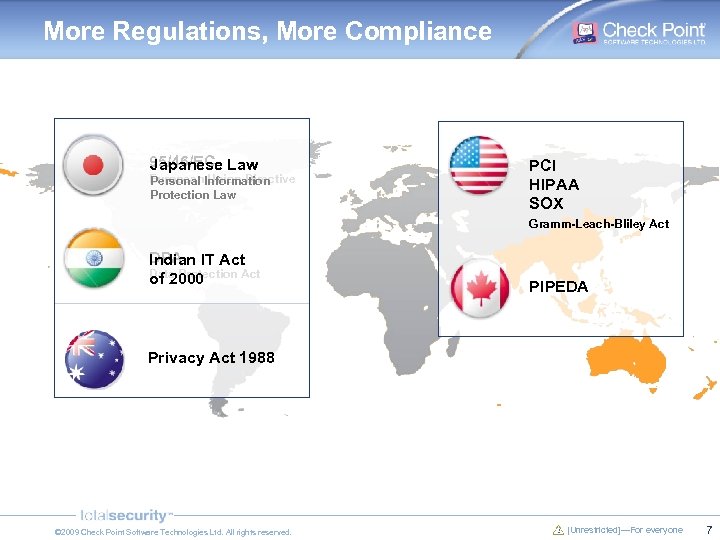 More Regulations, More Compliance 95/46/EC Law Japanese European. Information Personal Union Directive Protection Law PCI HIPAA SOX Gramm-Leach-Bliley Act DPA IT Act Indian Data Protection Act of 2000 PIPEDA Privacy Act 1988 © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 7
More Regulations, More Compliance 95/46/EC Law Japanese European. Information Personal Union Directive Protection Law PCI HIPAA SOX Gramm-Leach-Bliley Act DPA IT Act Indian Data Protection Act of 2000 PIPEDA Privacy Act 1988 © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 7
 Endpoint Security Needs Highest level of endpoint protection Simplified user experience Corporate data loss prevention Reduced complexity © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 8
Endpoint Security Needs Highest level of endpoint protection Simplified user experience Corporate data loss prevention Reduced complexity © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 8
 Agenda § Endpoint Security Challenges Today § The Check Point Solution – – Comprehensive endpoint security Secure, fast and simple to use Market leading data security Optimized Total Security § Summary © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 9
Agenda § Endpoint Security Challenges Today § The Check Point Solution – – Comprehensive endpoint security Secure, fast and simple to use Market leading data security Optimized Total Security § Summary © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 9
 Check Point Endpoint Security 2008 2009 The First and Only Single Agent for Endpoint Security Introducing Endpoint Security R 73 © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 10
Check Point Endpoint Security 2008 2009 The First and Only Single Agent for Endpoint Security Introducing Endpoint Security R 73 © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 10
 Check Point Endpoint Security Comprehensive Endpoint Protection Transparent and Simple to Use Market-Leading Data Security Optimized Total Security © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 11
Check Point Endpoint Security Comprehensive Endpoint Protection Transparent and Simple to Use Market-Leading Data Security Optimized Total Security © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 11
![Comprehensive Endpoint Protection © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For Comprehensive Endpoint Protection © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For](https://present5.com/presentation/77dc54309e39a8aa87c6fc5321ad6e6d/image-12.jpg) Comprehensive Endpoint Protection © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 12
Comprehensive Endpoint Protection © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 12
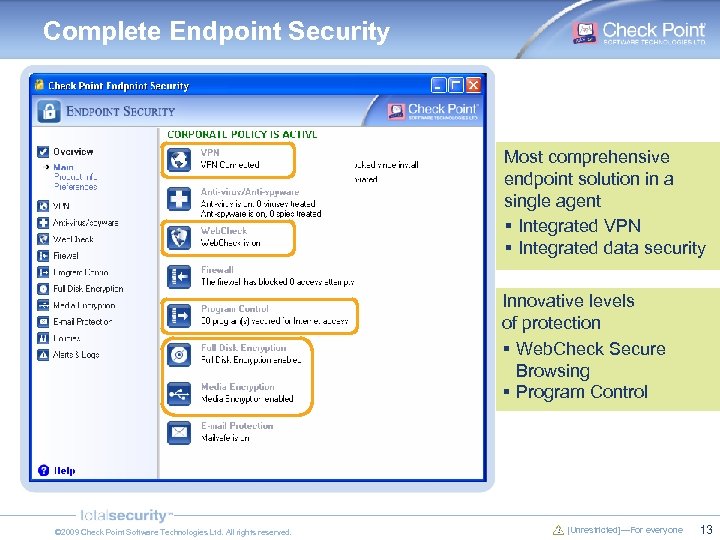 Complete Endpoint Security Most comprehensive endpoint solution in a single agent § Integrated VPN § Integrated data security Innovative levels of protection § Web. Check Secure Browsing § Program Control © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 13
Complete Endpoint Security Most comprehensive endpoint solution in a single agent § Integrated VPN § Integrated data security Innovative levels of protection § Web. Check Secure Browsing § Program Control © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 13
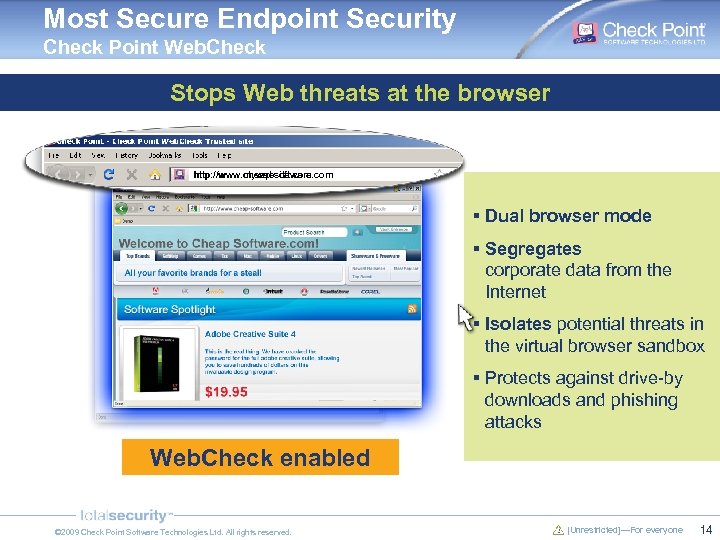 Most Secure Endpoint Security Check Point Web. Check Stops Web threats at the browser http: //www. mywebsite. com http: //www. cheap-software. com § Dual browser mode § Segregates corporate data from the Internet § Isolates potential threats in the virtual browser sandbox § Protects against drive-by downloads and phishing attacks Web. Check site Untrustedenabled Trusted site © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 14
Most Secure Endpoint Security Check Point Web. Check Stops Web threats at the browser http: //www. mywebsite. com http: //www. cheap-software. com § Dual browser mode § Segregates corporate data from the Internet § Isolates potential threats in the virtual browser sandbox § Protects against drive-by downloads and phishing attacks Web. Check site Untrustedenabled Trusted site © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 14
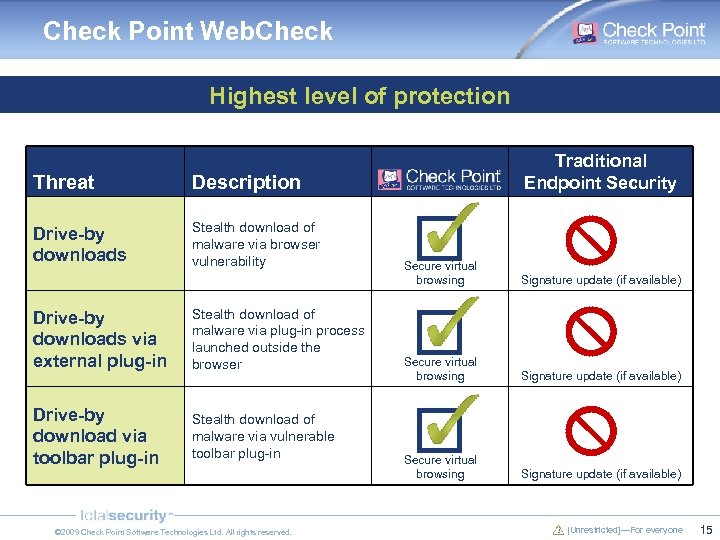 Check Point Web. Check Highest level of protection Threat Description Drive-by downloads Stealth download of malware via browser vulnerability Traditional Endpoint Security Drive-by downloads via external plug-in Stealth download of malware via plug-in process launched outside the browser Drive-by download via toolbar plug-in Stealth download of malware via vulnerable toolbar plug-in © 2009 Check Point Software Technologies Ltd. All rights reserved. Secure virtual browsing Signature update (if available) [Unrestricted]—For everyone 15
Check Point Web. Check Highest level of protection Threat Description Drive-by downloads Stealth download of malware via browser vulnerability Traditional Endpoint Security Drive-by downloads via external plug-in Stealth download of malware via plug-in process launched outside the browser Drive-by download via toolbar plug-in Stealth download of malware via vulnerable toolbar plug-in © 2009 Check Point Software Technologies Ltd. All rights reserved. Secure virtual browsing Signature update (if available) [Unrestricted]—For everyone 15
 Check Point Program Control Protect from malware by controlling endpoint applications Authorized Applications § Lock down endpoint to reduce support costs and complexity § Easy to maintain with Program Advisor service automating application policy decisions © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 16
Check Point Program Control Protect from malware by controlling endpoint applications Authorized Applications § Lock down endpoint to reduce support costs and complexity § Easy to maintain with Program Advisor service automating application policy decisions © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 16
 Transparent and Simple to Use © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 17
Transparent and Simple to Use © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 17
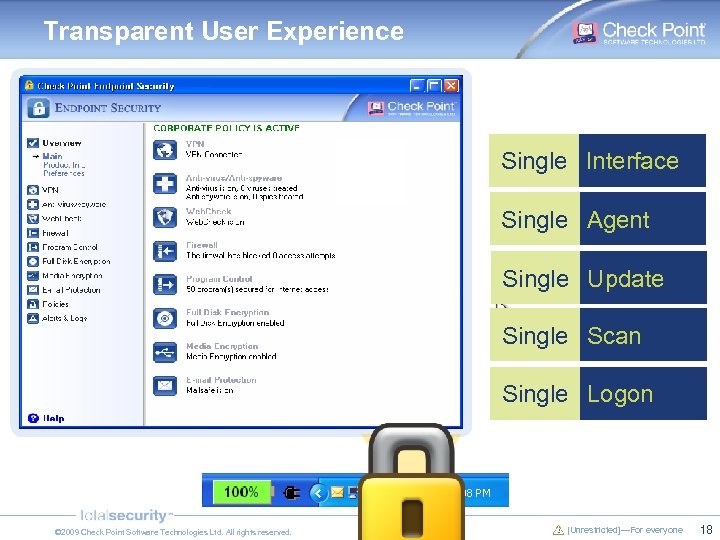 Transparent User Experience Single Interface Single Agent Single Update Single Scan Single Logon © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 18
Transparent User Experience Single Interface Single Agent Single Update Single Scan Single Logon © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 18
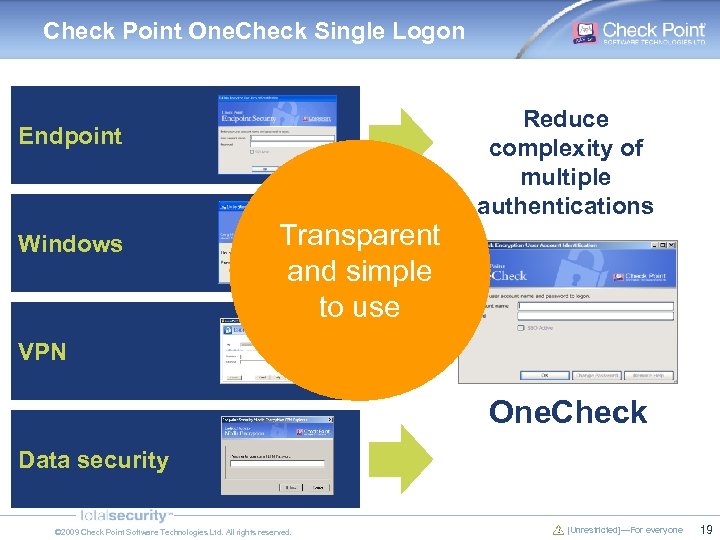 Check Point One. Check Single Logon Endpoint Windows Transparent and simple to use Reduce complexity of multiple authentications VPN One. Check Data security © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 19
Check Point One. Check Single Logon Endpoint Windows Transparent and simple to use Reduce complexity of multiple authentications VPN One. Check Data security © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 19
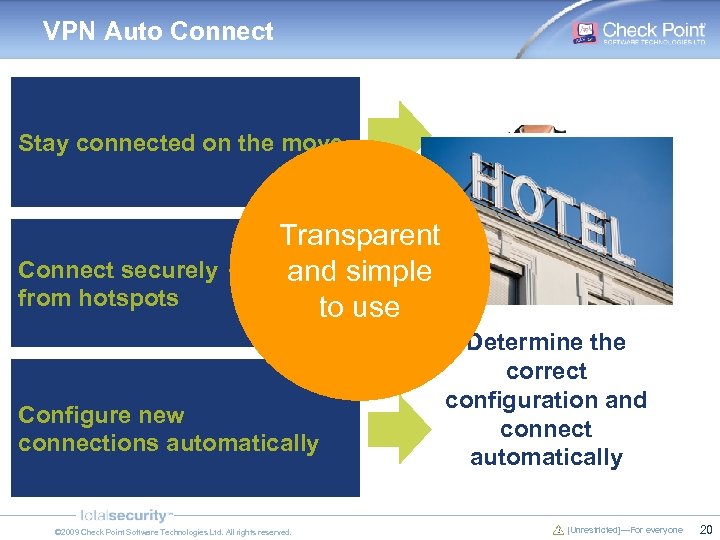 VPN Auto Connect Stay connected on the move Connect securely from hotspots Transparent and simple to use Configure new connections automatically © 2009 Check Point Software Technologies Ltd. All rights reserved. Automaticallythe Determine open reconnect when hotspot registration correct moving between page immediately configuration and networks (LAN, Wi. Fi, upon connection connect GPRS) automatically [Unrestricted]—For everyone 20
VPN Auto Connect Stay connected on the move Connect securely from hotspots Transparent and simple to use Configure new connections automatically © 2009 Check Point Software Technologies Ltd. All rights reserved. Automaticallythe Determine open reconnect when hotspot registration correct moving between page immediately configuration and networks (LAN, Wi. Fi, upon connection connect GPRS) automatically [Unrestricted]—For everyone 20
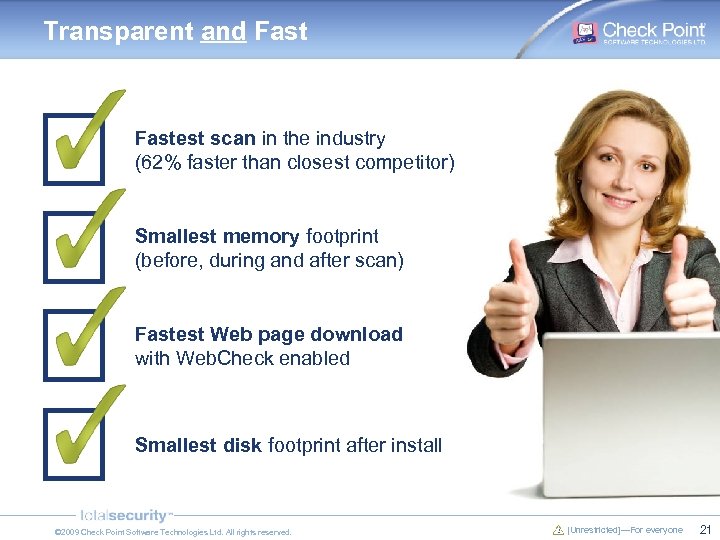 Transparent and Fastest scan in the industry (62% faster than closest competitor) Smallest memory footprint (before, during and after scan) Fastest Web page download with Web. Check enabled Smallest disk footprint after install © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 21
Transparent and Fastest scan in the industry (62% faster than closest competitor) Smallest memory footprint (before, during and after scan) Fastest Web page download with Web. Check enabled Smallest disk footprint after install © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 21
 Market Leading Data Security © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 22
Market Leading Data Security © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 22
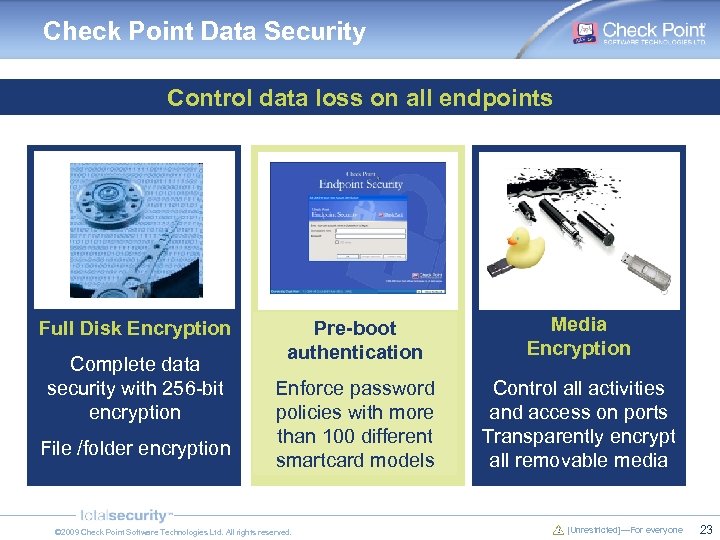 Check Point Data Security Control data loss on all endpoints Full Disk Encryption Complete data security with 256 -bit encryption File /folder encryption Pre-boot authentication Media Encryption Enforce password policies with more than 100 different smartcard models Control all activities and access on ports Transparently encrypt all removable media © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 23
Check Point Data Security Control data loss on all endpoints Full Disk Encryption Complete data security with 256 -bit encryption File /folder encryption Pre-boot authentication Media Encryption Enforce password policies with more than 100 different smartcard models Control all activities and access on ports Transparently encrypt all removable media © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 23
 Data Security Market Leader Secure data on all platforms Best Mobile Device Solution Windows 7 Highest level of certification Product Excellence Encryption Mac Solution Leader in Magic Quadrant 9 Years in a Row Recognized across the industry © 2009 Check Point Software Technologies Ltd. All rights reserved. Linux Smartphones Gold Medal 2009 Reader’s Choice Awards [Unrestricted]—For everyone 24
Data Security Market Leader Secure data on all platforms Best Mobile Device Solution Windows 7 Highest level of certification Product Excellence Encryption Mac Solution Leader in Magic Quadrant 9 Years in a Row Recognized across the industry © 2009 Check Point Software Technologies Ltd. All rights reserved. Linux Smartphones Gold Medal 2009 Reader’s Choice Awards [Unrestricted]—For everyone 24
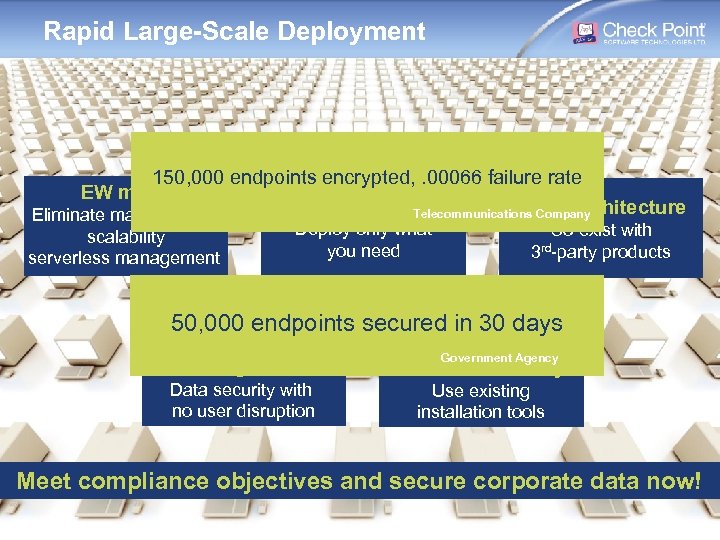 Rapid Large-Scale Deployment 150, 000 endpoints encrypted, . 00066 failure rate EW mode Flexible agent Open architecture Telecommunications Company Eliminate management scalability serverless management Deploy only what you need Co-exist with 3 rd-party products 50, 000 endpoints secured in 30 days Windows-integrated logon Endpoint Government Agency distribution utility Data security with no user disruption Use existing installation tools Meet compliance objectives and secure corporate data now! © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 25
Rapid Large-Scale Deployment 150, 000 endpoints encrypted, . 00066 failure rate EW mode Flexible agent Open architecture Telecommunications Company Eliminate management scalability serverless management Deploy only what you need Co-exist with 3 rd-party products 50, 000 endpoints secured in 30 days Windows-integrated logon Endpoint Government Agency distribution utility Data security with no user disruption Use existing installation tools Meet compliance objectives and secure corporate data now! © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 25
![Optimized Total Security © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For Optimized Total Security © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For](https://present5.com/presentation/77dc54309e39a8aa87c6fc5321ad6e6d/image-26.jpg) Optimized Total Security © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 26
Optimized Total Security © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 26
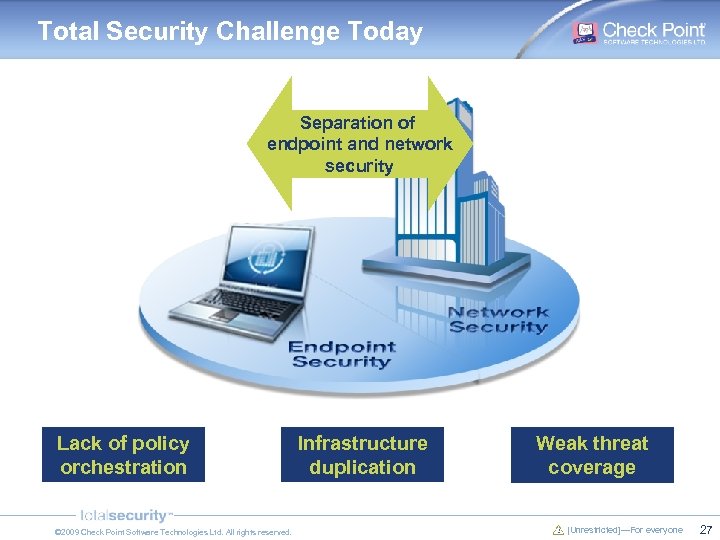 Total Security Challenge Today Separation of endpoint and network security Lack of policy orchestration © 2009 Check Point Software Technologies Ltd. All rights reserved. Infrastructure duplication Weak threat coverage [Unrestricted]—For everyone 27
Total Security Challenge Today Separation of endpoint and network security Lack of policy orchestration © 2009 Check Point Software Technologies Ltd. All rights reserved. Infrastructure duplication Weak threat coverage [Unrestricted]—For everyone 27
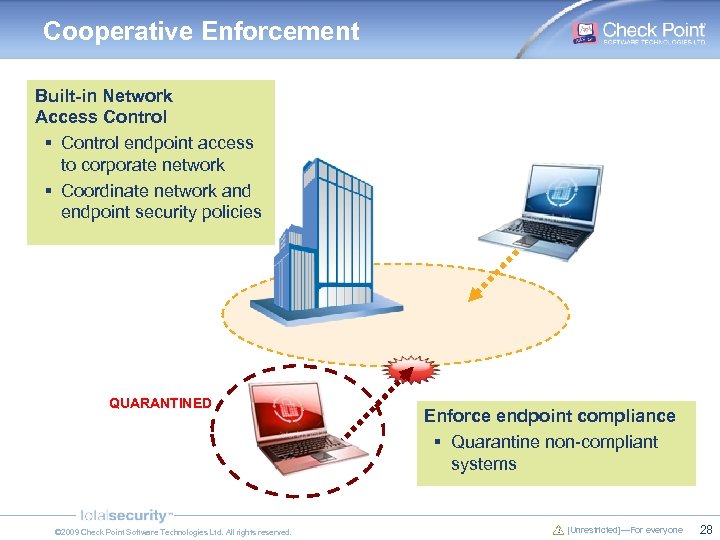 Cooperative Enforcement Built-in Network Access Control § Control endpoint access to corporate network § Coordinate network and endpoint security policies QUARANTINED © 2009 Check Point Software Technologies Ltd. All rights reserved. Enforce endpoint compliance § Quarantine non-compliant systems [Unrestricted]—For everyone 28
Cooperative Enforcement Built-in Network Access Control § Control endpoint access to corporate network § Coordinate network and endpoint security policies QUARANTINED © 2009 Check Point Software Technologies Ltd. All rights reserved. Enforce endpoint compliance § Quarantine non-compliant systems [Unrestricted]—For everyone 28
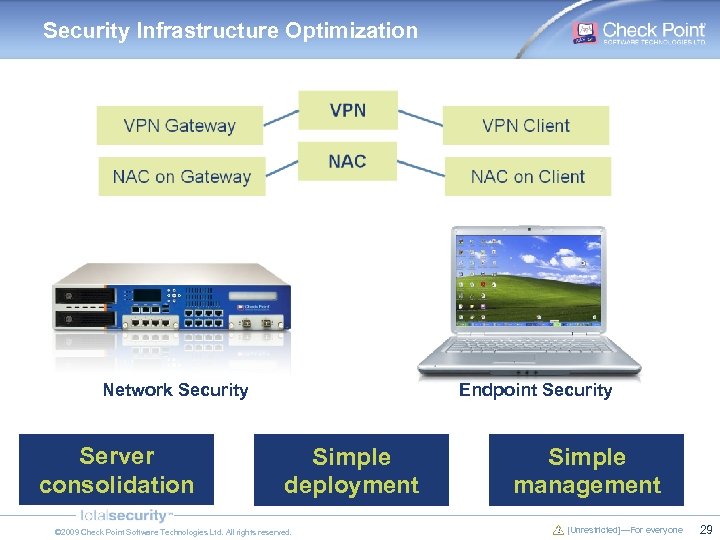 Security Infrastructure Optimization Network Security Server consolidation Endpoint Security Simple deployment © 2009 Check Point Software Technologies Ltd. All rights reserved. Simple management [Unrestricted]—For everyone 29
Security Infrastructure Optimization Network Security Server consolidation Endpoint Security Simple deployment © 2009 Check Point Software Technologies Ltd. All rights reserved. Simple management [Unrestricted]—For everyone 29
 Unified Threat Research Check Point Protection Update Worldwide coordinated network Unified notifications and endpoint threat research for new threats Update Protection against Microsoft Office Web Components Multiple Active. X Controls Remote Code Execution Vulnerability (MS 09 -043) Overview Details Protection Subscribe Check Point Reference: CPAI-2009 -1029 Date Published: 15 -Jul-09 Severity: Critical Source: MSFT Security Bulletin Industry Reference CVE-2009 -0562 CVE-2009 -1136 Protection Provided by: Endpoint Security R 72 Security Gateway R 70 VPN-1 NGX R 65 IPS-1 Common threat definitions across endpoint and network © 2009 Check Point Software Technologies Ltd. All rights reserved. Multi-layered protection across endpoint and network security [Unrestricted]—For everyone 30
Unified Threat Research Check Point Protection Update Worldwide coordinated network Unified notifications and endpoint threat research for new threats Update Protection against Microsoft Office Web Components Multiple Active. X Controls Remote Code Execution Vulnerability (MS 09 -043) Overview Details Protection Subscribe Check Point Reference: CPAI-2009 -1029 Date Published: 15 -Jul-09 Severity: Critical Source: MSFT Security Bulletin Industry Reference CVE-2009 -0562 CVE-2009 -1136 Protection Provided by: Endpoint Security R 72 Security Gateway R 70 VPN-1 NGX R 65 IPS-1 Common threat definitions across endpoint and network © 2009 Check Point Software Technologies Ltd. All rights reserved. Multi-layered protection across endpoint and network security [Unrestricted]—For everyone 30
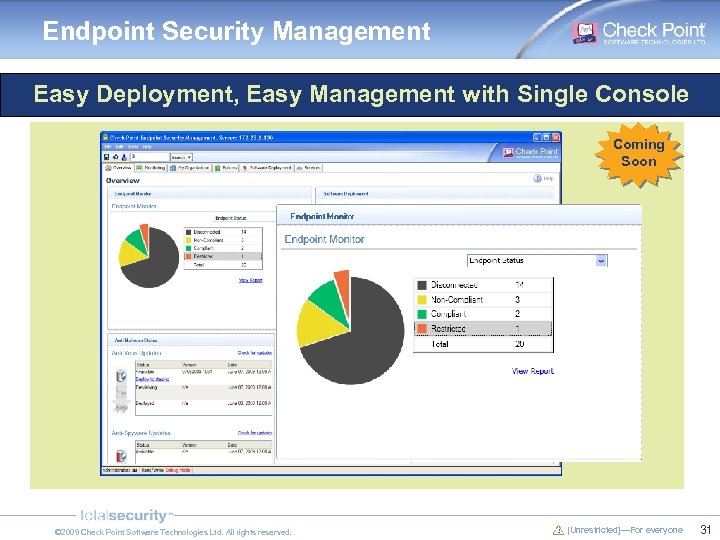 Endpoint Security Management Easy Deployment, Easy Management with Single Console Coming Soon © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 31
Endpoint Security Management Easy Deployment, Easy Management with Single Console Coming Soon © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 31
 Your Opportunity with Check Point Best endpoint security User transparency and ease of use Corporate data loss prevention Reduced complexity © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 32
Your Opportunity with Check Point Best endpoint security User transparency and ease of use Corporate data loss prevention Reduced complexity © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 32
 Summary Comprehensive Endpoint Protection Transparent and Simple to Use Market-Leading Data Security Optimized Total Security © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 33
Summary Comprehensive Endpoint Protection Transparent and Simple to Use Market-Leading Data Security Optimized Total Security © 2009 Check Point Software Technologies Ltd. All rights reserved. [Unrestricted]—For everyone 33


