449a5893a9e052f6971e7086978396e1.ppt
- Количество слайдов: 20
 Chapters 1 - 8 Introduction to the Internet, the Web and e-Business
Chapters 1 - 8 Introduction to the Internet, the Web and e-Business
 What is a Computer? Computer – Device capable of performing computations and making logical decisions – Computers process data under the control of sets of instructions called programs which control the hardware Computer Components 1. Hardware 2. Software
What is a Computer? Computer – Device capable of performing computations and making logical decisions – Computers process data under the control of sets of instructions called programs which control the hardware Computer Components 1. Hardware 2. Software
 Types of Programming Languages Three types of programming languages 1. Machine languages Strings of numbers giving machine specific instructions Example: +1300042774 +1400593419 +1200274027 2. Assembly languages English-like abbreviations representing elementary computer operations (translated via assemblers) Example: LOAD ADD STORE BASEPAY OVERPAY GROSSPAY 3. High-level languages Codes similar to everyday English Use mathematical notations (translated via compilers) Example: gross. Pay = base. Pay + over. Time. Pay
Types of Programming Languages Three types of programming languages 1. Machine languages Strings of numbers giving machine specific instructions Example: +1300042774 +1400593419 +1200274027 2. Assembly languages English-like abbreviations representing elementary computer operations (translated via assemblers) Example: LOAD ADD STORE BASEPAY OVERPAY GROSSPAY 3. High-level languages Codes similar to everyday English Use mathematical notations (translated via compilers) Example: gross. Pay = base. Pay + over. Time. Pay
 The Future of Computing Future of Computers – Use increasing dramatically – Costs decreasing – Explosion of Internet and World Wide Web Multimedia content Increasing bandwidth Magazines and books already going online Easy international communication – Could replace TV, radio and phone – Helping the disabled
The Future of Computing Future of Computers – Use increasing dramatically – Costs decreasing – Explosion of Internet and World Wide Web Multimedia content Increasing bandwidth Magazines and books already going online Easy international communication – Could replace TV, radio and phone – Helping the disabled
 History of the World Wide Web WWW – Allows computer users to locate and view multimediabased documents – Introduced in 1990 by Tim Berners-Lee
History of the World Wide Web WWW – Allows computer users to locate and view multimediabased documents – Introduced in 1990 by Tim Berners-Lee
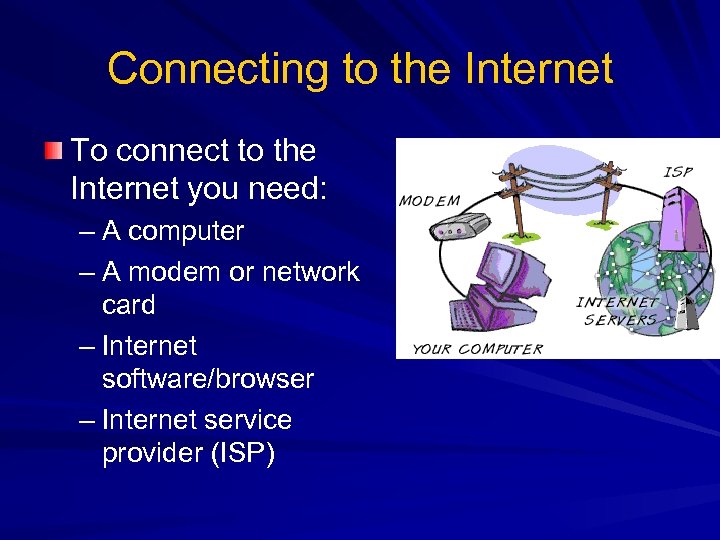 Connecting to the Internet To connect to the Internet you need: – A computer – A modem or network card – Internet software/browser – Internet service provider (ISP)
Connecting to the Internet To connect to the Internet you need: – A computer – A modem or network card – Internet software/browser – Internet service provider (ISP)
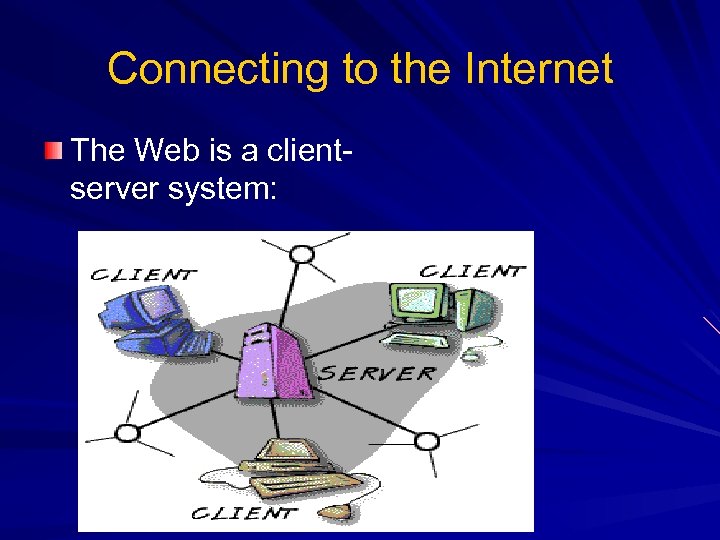 Connecting to the Internet The Web is a clientserver system:
Connecting to the Internet The Web is a clientserver system:
 Connecting to the Internet The WWW Consortium purpose is to promote the growth of the Web – developing technical specifications and reference software that will be freely available to everyone.
Connecting to the Internet The WWW Consortium purpose is to promote the growth of the Web – developing technical specifications and reference software that will be freely available to everyone.
 Connecting to the Internet In what ways can you take advantage of the characteristics that distinguish the web from print media? – – – Graphics Links Interactive sites Asynchronous communication Ability to be accessed from just about anywhere in the world
Connecting to the Internet In what ways can you take advantage of the characteristics that distinguish the web from print media? – – – Graphics Links Interactive sites Asynchronous communication Ability to be accessed from just about anywhere in the world
 Domain name Registration – Domain-it. com, register. com and Network Solutions Available domain names decreasing – ICANN (Internet Corporation for Assigned Names and Numbers) considering new suffixes Domain type – – – – – . com (commercial). edu (educational). gov (government). mil (military). net (network). org (non-profit organization). pdf (portable data format). uk (Great Britain). il (Israel)
Domain name Registration – Domain-it. com, register. com and Network Solutions Available domain names decreasing – ICANN (Internet Corporation for Assigned Names and Numbers) considering new suffixes Domain type – – – – – . com (commercial). edu (educational). gov (government). mil (military). net (network). org (non-profit organization). pdf (portable data format). uk (Great Britain). il (Israel)
 e-business VS e-Commerce e-Business: is defined as a company that has an online presence. – – – Provides products and services 24 hours a day Provides unlimited inventory Allows consumer to comparison shop Essential to business success Replacing “brick and mortar” stores Personalize user’s experience e-Commerce: is an e-Business that have the ability to sell, trade, barter and transact over the Web. – E-commerce allows companies to conduct business 24 by-7, all day everyday, worldwide A companies policy, operations, technology and ideology define its business model
e-business VS e-Commerce e-Business: is defined as a company that has an online presence. – – – Provides products and services 24 hours a day Provides unlimited inventory Allows consumer to comparison shop Essential to business success Replacing “brick and mortar” stores Personalize user’s experience e-Commerce: is an e-Business that have the ability to sell, trade, barter and transact over the Web. – E-commerce allows companies to conduct business 24 by-7, all day everyday, worldwide A companies policy, operations, technology and ideology define its business model
 Consequences of Internet and Web Privacy invasion – One of the risks of Internet – Personal information on the Web – Tracking of Web movement – Credit card security Piracy of intellectual property – Copyright infringement – MP 3
Consequences of Internet and Web Privacy invasion – One of the risks of Internet – Personal information on the Web – Tracking of Web movement – Credit card security Piracy of intellectual property – Copyright infringement – MP 3
 e-Business Model Storefront Model: Amazon. com, e-toys. com Auction Model: e. Bay Portal Model: ask. com, Yahoo. com, google. com Dynamic Pricing Models: priceline. com, AOL. com B 2 B Exchange: biz 2 biz. com B 2 B Service Providers: Freemarkets. com Online Trading and Lending Models: E*TRADE, Schwab. com, fidelity. com Online Loan: E-loan. com, mortgagebot. com Recruiting on the Web: monster. com, sixfigurejobs. com Online News Services: WSJ. com, ESPN. com, CNN. com Online Travel Services: expedia. com, Travelosity. com, Cheaptickets. com Online Entertainment: i. Cast. com, Farmclub. com Online Automobile sites: Autobytel. com, Autoparts. com Energy Online: retailenergy. com Selling Brainpower: questionexchange. com Online Art Dealers: Art. com, art. net E-Learning: webct. com, Blackboard. com, getmymba. com; click 2 learn Click-and-Mortar Businesses (hybrid): circuitcity. com, 1800 flower. com
e-Business Model Storefront Model: Amazon. com, e-toys. com Auction Model: e. Bay Portal Model: ask. com, Yahoo. com, google. com Dynamic Pricing Models: priceline. com, AOL. com B 2 B Exchange: biz 2 biz. com B 2 B Service Providers: Freemarkets. com Online Trading and Lending Models: E*TRADE, Schwab. com, fidelity. com Online Loan: E-loan. com, mortgagebot. com Recruiting on the Web: monster. com, sixfigurejobs. com Online News Services: WSJ. com, ESPN. com, CNN. com Online Travel Services: expedia. com, Travelosity. com, Cheaptickets. com Online Entertainment: i. Cast. com, Farmclub. com Online Automobile sites: Autobytel. com, Autoparts. com Energy Online: retailenergy. com Selling Brainpower: questionexchange. com Online Art Dealers: Art. com, art. net E-Learning: webct. com, Blackboard. com, getmymba. com; click 2 learn Click-and-Mortar Businesses (hybrid): circuitcity. com, 1800 flower. com
 Internet Marketing 1. Choosing a Domain Name: register at networksolutions. com, register. com, domainit. com 2. Internet Marketing Research: mediametrix. com 3. Web Design: Appealing, user friendly, simple to navigate, Privacy policy 4. E-mail Marketing: fast, Cheap, far reaching, includes spam 5. Promotions: Offer discounts when purchases are made online 6. E-Business Advertising: Online advertising: place links on other Web sites, register with search engines and directories 7. Webcasting and Interactive Advertising: Involves using streaming media to broadcast an event over the Web 8. E-Business Public Relations: Keeps customers and company current on latest information about products, services 9. Customer Relationship Management (CRM): Data mining, keep track of visitors, customers registration, personalization 10. B 2 B marketing on the Web: selling products to another business 11. Search Engines: registering with search engines companies increase traffic to their sites Alta. Vista, Yahoo!, Lycos, Excite, Google and Ask Jeeves 12. Partnerships: Forming a strategic union with another company 13. Marketing to the world: Sensitivity to linguistic, legal and cultural differences
Internet Marketing 1. Choosing a Domain Name: register at networksolutions. com, register. com, domainit. com 2. Internet Marketing Research: mediametrix. com 3. Web Design: Appealing, user friendly, simple to navigate, Privacy policy 4. E-mail Marketing: fast, Cheap, far reaching, includes spam 5. Promotions: Offer discounts when purchases are made online 6. E-Business Advertising: Online advertising: place links on other Web sites, register with search engines and directories 7. Webcasting and Interactive Advertising: Involves using streaming media to broadcast an event over the Web 8. E-Business Public Relations: Keeps customers and company current on latest information about products, services 9. Customer Relationship Management (CRM): Data mining, keep track of visitors, customers registration, personalization 10. B 2 B marketing on the Web: selling products to another business 11. Search Engines: registering with search engines companies increase traffic to their sites Alta. Vista, Yahoo!, Lycos, Excite, Google and Ask Jeeves 12. Partnerships: Forming a strategic union with another company 13. Marketing to the world: Sensitivity to linguistic, legal and cultural differences
 Online Monetary Transaction Credit card Transactions: To accept online credit-card payments, a merchant must have an Internet merchant account with a bank or third-party services E-wallets: Keep track of your billing and shipping information so that it can be entered with one click at participating merchants’ sites. store e-checks, ecash, credit-card information Alternate Consumer Payment Options: if credit card not accepted use Check, Debit card, money order, or cash on delivery (COD) Digital Currency: Digital cash where consumers deposit money to used in their digital transactions Peer-to-peer Payments: allow online monetary transfer between consumers. Transfer of digital cash via e-mail. Pay. Pal Smart Cards: Card with computer chip embedded on its face, holds more information than ordinary credit card with magnetic strip (health, frequent-flyer program…) Micropayments: Payments that generally do not exceed $10, some companies form strategic partnerships with utility companies to decrease transaction fees on credit and debit cards B 2 B Transaction: Payments are often larger than B 2 C transactions and involve complex business accounting systems E-billing: transfer from consumer checking account. Online Banking: offer online banking and services such as e-wallets.
Online Monetary Transaction Credit card Transactions: To accept online credit-card payments, a merchant must have an Internet merchant account with a bank or third-party services E-wallets: Keep track of your billing and shipping information so that it can be entered with one click at participating merchants’ sites. store e-checks, ecash, credit-card information Alternate Consumer Payment Options: if credit card not accepted use Check, Debit card, money order, or cash on delivery (COD) Digital Currency: Digital cash where consumers deposit money to used in their digital transactions Peer-to-peer Payments: allow online monetary transfer between consumers. Transfer of digital cash via e-mail. Pay. Pal Smart Cards: Card with computer chip embedded on its face, holds more information than ordinary credit card with magnetic strip (health, frequent-flyer program…) Micropayments: Payments that generally do not exceed $10, some companies form strategic partnerships with utility companies to decrease transaction fees on credit and debit cards B 2 B Transaction: Payments are often larger than B 2 C transactions and involve complex business accounting systems E-billing: transfer from consumer checking account. Online Banking: offer online banking and services such as e-wallets.
 Legal Issues Privacy on the Internet – Difficulty of applying traditional law to the Internet – The Internet industry essentially governs itself. – Many Internet companies collect users’ personal information Tracking Devices: Identifies what activities and products are most popular among consumers. ID card, Click-through advertisements, Web Bugs. Cookies: A text file stored by a Web site on an individual’s personal computer that allows a site to track the actions of its visitors – Record passwords for returning visitors – Keeps track of shopping-cart materials and register preferences – Helps businesses by allowing them to address their target market with greater accuracy Employer and Employees: employees surveillance to prevent Harassment suits, Low productivity Protecting Yourself as a User: Anonymity and pseudonymity Protecting your Business: Core Fair Information Practices – Consumers should be made aware that personal information will be collected – The consumer should have a say in how this information will be used – The consumer should have the ability to check the information collected to ensure that it is complete and accurate – The information collected should be secured – The Web site should be responsible for seeing that these practices are followed
Legal Issues Privacy on the Internet – Difficulty of applying traditional law to the Internet – The Internet industry essentially governs itself. – Many Internet companies collect users’ personal information Tracking Devices: Identifies what activities and products are most popular among consumers. ID card, Click-through advertisements, Web Bugs. Cookies: A text file stored by a Web site on an individual’s personal computer that allows a site to track the actions of its visitors – Record passwords for returning visitors – Keeps track of shopping-cart materials and register preferences – Helps businesses by allowing them to address their target market with greater accuracy Employer and Employees: employees surveillance to prevent Harassment suits, Low productivity Protecting Yourself as a User: Anonymity and pseudonymity Protecting your Business: Core Fair Information Practices – Consumers should be made aware that personal information will be collected – The consumer should have a say in how this information will be used – The consumer should have the ability to check the information collected to ensure that it is complete and accurate – The information collected should be secured – The Web site should be responsible for seeing that these practices are followed
 Ethicalreputation, honor or good name through Issues Defamation: The act of injuring another’s false written or oral communication Sexually Explicit Speech: Challenge of community standards in cyberspace Children and the Internet: – Communications Decency Act of 1996 (CDA) and Children’s Online Protection Act of 1998 (COPA): Designed to restrict pornography on the Internet – Children’s Online Privacy Protection Act of 2000 (COPPA): Prohibits Web sites from collecting personal information from children under the age of 13 Intellectual Property: Patents and Copyright – Copyright: The protection given to the author of an original piece. Guaranteed for the life of the author plus 70 years – Patent: Grants the creator sole rights to the new discovery, for 20 years Trademark and Domain Name Registration: – Parasite: Selects a domain name based on common typos made when entering a popular domain name – Cybersquatter: Buys an assortment of domain names that are obvious representations of a brick-and-mortar company Unsolicited Commercial E-mail (Spam): Organizations distributing spam – Maintain anonymity and receivers cannot request to be taken off the organization’s mailing list – Present themselves as a legitimate company and damage the legitimate companies reputation Online Auctions: Sellers bid for their own items in order to increase the bid price Online Contracts: Electronic Signatures in Global and National Commerce Act of 2000 (E-Sign bill)
Ethicalreputation, honor or good name through Issues Defamation: The act of injuring another’s false written or oral communication Sexually Explicit Speech: Challenge of community standards in cyberspace Children and the Internet: – Communications Decency Act of 1996 (CDA) and Children’s Online Protection Act of 1998 (COPA): Designed to restrict pornography on the Internet – Children’s Online Privacy Protection Act of 2000 (COPPA): Prohibits Web sites from collecting personal information from children under the age of 13 Intellectual Property: Patents and Copyright – Copyright: The protection given to the author of an original piece. Guaranteed for the life of the author plus 70 years – Patent: Grants the creator sole rights to the new discovery, for 20 years Trademark and Domain Name Registration: – Parasite: Selects a domain name based on common typos made when entering a popular domain name – Cybersquatter: Buys an assortment of domain names that are obvious representations of a brick-and-mortar company Unsolicited Commercial E-mail (Spam): Organizations distributing spam – Maintain anonymity and receivers cannot request to be taken off the organization’s mailing list – Present themselves as a legitimate company and damage the legitimate companies reputation Online Auctions: Sellers bid for their own items in order to increase the bid price Online Contracts: Electronic Signatures in Global and National Commerce Act of 2000 (E-Sign bill)
 Social Issues, Internet Taxation Social Issues: Online Communities – Online Communities: Online users can move about the Web, not limited by gender, race, creed, age and sexual orientation – Online Activism: Social and political action on the Web – Disabilities and the Web: Enables disabled individuals to work in many new fields. Voice activation, visual enhancers and auditory aids Global Issues: The Internet poses challenges to a world comprised of different cultures, attitudes, languages, codes of conduct and government authorities Internet Taxation: Taxation methods – If both a vendor and a consumer are located in the same state – If the vendor and the consumer are not located in the same state, then the sale is subject to a use tax – If the vendor has a physical presence, or nexus, then it is required to collect the tax; otherwise the vendor must assess the tax and pay it directly to the state
Social Issues, Internet Taxation Social Issues: Online Communities – Online Communities: Online users can move about the Web, not limited by gender, race, creed, age and sexual orientation – Online Activism: Social and political action on the Web – Disabilities and the Web: Enables disabled individuals to work in many new fields. Voice activation, visual enhancers and auditory aids Global Issues: The Internet poses challenges to a world comprised of different cultures, attitudes, languages, codes of conduct and government authorities Internet Taxation: Taxation methods – If both a vendor and a consumer are located in the same state – If the vendor and the consumer are not located in the same state, then the sale is subject to a use tax – If the vendor has a physical presence, or nexus, then it is required to collect the tax; otherwise the vendor must assess the tax and pay it directly to the state
 Computer and Network Security Ancient Ciphers to Modern Cryptosystems: – Cryptography: Used to secure information, by encrypting it Secret-key Cryptography: Same key to encrypt and decrypt message – Sender sends message and key to receiver Public Key Cryptography: – Asymmetric – two inversely related keys (Private key & Public key) – If public key encrypts only private can decrypt and vice versa Key Agreement Protocols: Process by which parties can exchange keys Key Management: Key-generation must be truly random Digital Signatures: Authenticates sender’s identity Public Key Infrastructure, Certificates and Certification Authorities: – Verisign (www. verisign. com) Leading certificate authority Cryptoanalysis: Trying to decrypt ciphertext without the decryption key Security Attacks: Hackers, Viruses, Worm Network Security: – Firewalls: Safety barrier for data flowing in and out – Kerberos: Uses symmetric secret-key cryptography to authenticate users in a network – Biometrics: uses unique personal information to identify (fingerprints, eyeball iris scans or face scans) Steganography: Practice of hiding information within other information
Computer and Network Security Ancient Ciphers to Modern Cryptosystems: – Cryptography: Used to secure information, by encrypting it Secret-key Cryptography: Same key to encrypt and decrypt message – Sender sends message and key to receiver Public Key Cryptography: – Asymmetric – two inversely related keys (Private key & Public key) – If public key encrypts only private can decrypt and vice versa Key Agreement Protocols: Process by which parties can exchange keys Key Management: Key-generation must be truly random Digital Signatures: Authenticates sender’s identity Public Key Infrastructure, Certificates and Certification Authorities: – Verisign (www. verisign. com) Leading certificate authority Cryptoanalysis: Trying to decrypt ciphertext without the decryption key Security Attacks: Hackers, Viruses, Worm Network Security: – Firewalls: Safety barrier for data flowing in and out – Kerberos: Uses symmetric secret-key cryptography to authenticate users in a network – Biometrics: uses unique personal information to identify (fingerprints, eyeball iris scans or face scans) Steganography: Practice of hiding information within other information
 Hardware, Software, & Communication. Technological advances – Computer and communications costs decreasing – Computer power and speed increasing – Speed of data transfers virtually unlimited Hardware – Host computers: Servers… – Communications media used to connect computers: cables… – Storage Area Networks (SANs): Provide backup and recovery services Specialized software for Internet businesses – Application service providers (ASPs) – Operating systems: Unix, Linux, Macintosh and Windows – Databases: Integrated collection of data Connecting to the Internet: Internet Service Provider (ISP) – Digital Subscriber Lines (DSL): Connect to Internet through phone lines – Broadband: Translates digital signals for transmission over television cables – Integrated Services Digital Network (ISDN): Terminal adaptor – Wireless: Manage information away from computer – Web. TV: Low cost Internet connection through TV
Hardware, Software, & Communication. Technological advances – Computer and communications costs decreasing – Computer power and speed increasing – Speed of data transfers virtually unlimited Hardware – Host computers: Servers… – Communications media used to connect computers: cables… – Storage Area Networks (SANs): Provide backup and recovery services Specialized software for Internet businesses – Application service providers (ASPs) – Operating systems: Unix, Linux, Macintosh and Windows – Databases: Integrated collection of data Connecting to the Internet: Internet Service Provider (ISP) – Digital Subscriber Lines (DSL): Connect to Internet through phone lines – Broadband: Translates digital signals for transmission over television cables – Integrated Services Digital Network (ISDN): Terminal adaptor – Wireless: Manage information away from computer – Web. TV: Low cost Internet connection through TV


