c974fb238272d65be668d76a203670a7.ppt
- Количество слайдов: 99
 Chapter Two Test Review
Chapter Two Test Review
 Question 1 Of the following choices, what type of control is least privilege? A. Corrective B. Detective C. Preventative D. Technical
Question 1 Of the following choices, what type of control is least privilege? A. Corrective B. Detective C. Preventative D. Technical
 Question 2 Of the following choices, what type of control is a vulnerability assessment? A. Management B. Operational C. Technical D. Corrective
Question 2 Of the following choices, what type of control is a vulnerability assessment? A. Management B. Operational C. Technical D. Corrective
 Question 3 Which of the following is a preventative control that can prevent outages due to ad-hoc (as-needed) configuration error? A. Least privilege B. Change management plan C. A periodic review of user rights D. Security audit
Question 3 Which of the following is a preventative control that can prevent outages due to ad-hoc (as-needed) configuration error? A. Least privilege B. Change management plan C. A periodic review of user rights D. Security audit
 Question 4 Which of the following is a preventative control? A. Least privilege B. Security guard C. Security audit D. Periodic review of user rights
Question 4 Which of the following is a preventative control? A. Least privilege B. Security guard C. Security audit D. Periodic review of user rights
 Question 5 Your organization regularly performs routine security audits to assess the security posture. What type of control is this? A. Detective B. Corrective C. Technical D. Preventative
Question 5 Your organization regularly performs routine security audits to assess the security posture. What type of control is this? A. Detective B. Corrective C. Technical D. Preventative
 Question 6 Of the following choices, what is a detective security control? A. Change management B. CCTV - Closed-Circuit TV C. HVAC - Heating/Ventilation/Air Conditioning D. User training
Question 6 Of the following choices, what is a detective security control? A. Change management B. CCTV - Closed-Circuit TV C. HVAC - Heating/Ventilation/Air Conditioning D. User training
 Question 7 An administrator is assigning access to users in different departments based on their job functions. What access control model is the administrator using? A. RBAC B. MAC C. DAC D. CAC
Question 7 An administrator is assigning access to users in different departments based on their job functions. What access control model is the administrator using? A. RBAC B. MAC C. DAC D. CAC
 Question 8 You manage user accounts for sales department. You have created a sales user account template to comply with the principle of least privilege. What access control model are you following? A. DAC B. RBAC C. CAC D. MAC
Question 8 You manage user accounts for sales department. You have created a sales user account template to comply with the principle of least privilege. What access control model are you following? A. DAC B. RBAC C. CAC D. MAC
 Question 9 Windows systems protect files and folders with New Technology File System (NTFS). What access control model does NTFS use? A. MAC B. RBAC C. DAC D. Implicit allow
Question 9 Windows systems protect files and folders with New Technology File System (NTFS). What access control model does NTFS use? A. MAC B. RBAC C. DAC D. Implicit allow
 Question 10 What is the purpose of a cypher lock system? A. Control door access with a proximity card B. Control door access with a keypad C. Control access to a laptop with biometrics D. Control access to laptop with a smart card
Question 10 What is the purpose of a cypher lock system? A. Control door access with a proximity card B. Control door access with a keypad C. Control access to a laptop with biometrics D. Control access to laptop with a smart card
 Question 11 What can you use to electronically unlock a door for specific users? A. Token B. Physical key C. Proximity cards D. Certificate
Question 11 What can you use to electronically unlock a door for specific users? A. Token B. Physical key C. Proximity cards D. Certificate
 Question 12 An administrator notices that former temporary employees’ accounts are still active on a domain. Which of the following can be implemented to increase security and prevent this from happening? A. Implement a password expiration policy. B. Implement an account expiration date for permanent employees. C. Implement time of day restrictions for all temporary employees. D. Run a last logon script to look for inactive accounts.
Question 12 An administrator notices that former temporary employees’ accounts are still active on a domain. Which of the following can be implemented to increase security and prevent this from happening? A. Implement a password expiration policy. B. Implement an account expiration date for permanent employees. C. Implement time of day restrictions for all temporary employees. D. Run a last logon script to look for inactive accounts.
 Question 13 A company hosts a datacenter with highly sensitive data. Of the following choices, what can provide the best type of physical security to prevent unauthorized entry? A. ID badges B. Mantrap C. CCTV D. Proximity card
Question 13 A company hosts a datacenter with highly sensitive data. Of the following choices, what can provide the best type of physical security to prevent unauthorized entry? A. ID badges B. Mantrap C. CCTV D. Proximity card
 Question 14 Two employees have entered a secure datacenter. However, only one employee provided credentials. How did the other employee gain entry? A. Mantrap B. Tailgating C. HVAC D. Vishing
Question 14 Two employees have entered a secure datacenter. However, only one employee provided credentials. How did the other employee gain entry? A. Mantrap B. Tailgating C. HVAC D. Vishing
 Question 15 Your organization has several portable USB drives that users are able to use to transfer large video files instead of copying them over the network. What should be used to prevent theft of these drives A. Locked cabinet B. Video surveillance C. TPM - Trusted Platform Module D. HSM - Hardware Security Module
Question 15 Your organization has several portable USB drives that users are able to use to transfer large video files instead of copying them over the network. What should be used to prevent theft of these drives A. Locked cabinet B. Video surveillance C. TPM - Trusted Platform Module D. HSM - Hardware Security Module
 Question 16 Your organization requires users to create passwords of at least ten characters for their user accounts. Which of the following is being enforced? A. Password complexity B. Password length C. Password masking D. Password history
Question 16 Your organization requires users to create passwords of at least ten characters for their user accounts. Which of the following is being enforced? A. Password complexity B. Password length C. Password masking D. Password history
 Question 17 Your password policy includes password history. What else should be configured to ensure that users aren't able to easily reuse the same password? A. Password masking B. Maximum age C. Minimum age D. Password complexity
Question 17 Your password policy includes password history. What else should be configured to ensure that users aren't able to easily reuse the same password? A. Password masking B. Maximum age C. Minimum age D. Password complexity
 Question 18 Your organization has a password policy that requires employees to change their passwords at least every forty-five days and prevents users from reusing any of their last five passwords. However, when forced to change their passwords, users are changing their passwords five more times to keep their original password. What can resolve this security vulnerability? A. Modify the password policy to require users to change their password after a day has passed. B. Modify the password policy to prevent users from changing the password until a day has passed. C. Modify the password policy to remember the last twelve passwords. D. Modify the password policy to remember the last twenty-four passwords.
Question 18 Your organization has a password policy that requires employees to change their passwords at least every forty-five days and prevents users from reusing any of their last five passwords. However, when forced to change their passwords, users are changing their passwords five more times to keep their original password. What can resolve this security vulnerability? A. Modify the password policy to require users to change their password after a day has passed. B. Modify the password policy to prevent users from changing the password until a day has passed. C. Modify the password policy to remember the last twelve passwords. D. Modify the password policy to remember the last twenty-four passwords.
 Question 19 A user has forgotten his password and calls the help desk for assistance. The help-desk professional will reset the password and tell the user the new password. What should the help desk professional configure to ensure the user immediately resets the password? A. Password complexity B. Password masking C. Password expiration D. Password history
Question 19 A user has forgotten his password and calls the help desk for assistance. The help-desk professional will reset the password and tell the user the new password. What should the help desk professional configure to ensure the user immediately resets the password? A. Password complexity B. Password masking C. Password expiration D. Password history
 Question 20 Users in your network are required to change their passwords every sixty days. What is this an example of? A. Password strength requirement B. Password length requirement C. Password history requirement D. Password expiration requirement
Question 20 Users in your network are required to change their passwords every sixty days. What is this an example of? A. Password strength requirement B. Password length requirement C. Password history requirement D. Password expiration requirement
 Question 21 Your company has hired a temporary contractor that needs a computer account for sixty days. You want to ensure the account is automatically disabled after sixty days. What feature would you use? A. Account expiration B. Account lockout C. Deletion through automated scripting D. Manual deletion
Question 21 Your company has hired a temporary contractor that needs a computer account for sixty days. You want to ensure the account is automatically disabled after sixty days. What feature would you use? A. Account expiration B. Account lockout C. Deletion through automated scripting D. Manual deletion
 Question 22 After an employee is terminated, what should be done to revoke the employee's access? A. Expire the password B. Lock out the account C. Disable the account D. Delete the account
Question 22 After an employee is terminated, what should be done to revoke the employee's access? A. Expire the password B. Lock out the account C. Disable the account D. Delete the account
 Question 23 Management wants to prevent users in the Marketing Department from logging onto network systems between 6: 00 p. m. and 5: 00 a. m. How can this be accomplished? A. Account expiration B. Use time-of-day restrictions C. Password expiration D. Implement a detective control
Question 23 Management wants to prevent users in the Marketing Department from logging onto network systems between 6: 00 p. m. and 5: 00 a. m. How can this be accomplished? A. Account expiration B. Use time-of-day restrictions C. Password expiration D. Implement a detective control
 Question 24 You have recently added a server to your network that will host data used and updated by employees. You want to monitor security events on the system. Of the following, what is the most important security event to monitor? A. Account login attempts B. UDP connections C. Data modifications D. TCP connections
Question 24 You have recently added a server to your network that will host data used and updated by employees. You want to monitor security events on the system. Of the following, what is the most important security event to monitor? A. Account login attempts B. UDP connections C. Data modifications D. TCP connections
 Question 25 A password history value of three means which of the following? A. A password cannot be reused once changed for three years. B. Three different passwords are used before one can be reused. C. After three hours a password must be re-entered to continue. D. The server stores passwords in the database for three days.
Question 25 A password history value of three means which of the following? A. A password cannot be reused once changed for three years. B. Three different passwords are used before one can be reused. C. After three hours a password must be re-entered to continue. D. The server stores passwords in the database for three days.
 Question 26 Which of the following is the BEST approach to perform risk mitigation of user access control rights? A. Implement periodic vulnerability scanning. B. Disable user accounts that have not been used within the last two weeks. C. Perform routine user permission reviews. D. Conduct surveys and rank the results.
Question 26 Which of the following is the BEST approach to perform risk mitigation of user access control rights? A. Implement periodic vulnerability scanning. B. Disable user accounts that have not been used within the last two weeks. C. Perform routine user permission reviews. D. Conduct surveys and rank the results.
 Question 27 If Pete, a security administrator, wants to ensure that certain users can only gain access to the system during their respective shifts, which of the following best practices would he implement? A. Separation of duties B. Time of day restrictions C. Implicit deny rule D. Least privilege
Question 27 If Pete, a security administrator, wants to ensure that certain users can only gain access to the system during their respective shifts, which of the following best practices would he implement? A. Separation of duties B. Time of day restrictions C. Implicit deny rule D. Least privilege
 Question 28 A small business owner has asked the security consultant to suggest an inexpensive means to deter physical intrusions at their place of business. Which of the following would BEST meet their request? A. Fake cameras B. Proximity readers C. Infrared cameras D. Security guards
Question 28 A small business owner has asked the security consultant to suggest an inexpensive means to deter physical intrusions at their place of business. Which of the following would BEST meet their request? A. Fake cameras B. Proximity readers C. Infrared cameras D. Security guards
 Question 29 Employee badges are encoded with a private encryption key and specific personal information. The encoding is then used to provide access to the network. Which of the following describes this access control type? A. Smartcard B. Token C. Discretionary access control D. Mandatory access control
Question 29 Employee badges are encoded with a private encryption key and specific personal information. The encoding is then used to provide access to the network. Which of the following describes this access control type? A. Smartcard B. Token C. Discretionary access control D. Mandatory access control
 Question 30 A security administrator wants to check user password complexity. Which of the following is the BEST tool to use? A. Password history B. Password logging C. Password cracker D. Password hashing
Question 30 A security administrator wants to check user password complexity. Which of the following is the BEST tool to use? A. Password history B. Password logging C. Password cracker D. Password hashing
 Question 31 An employee is granted access to only areas of a network folder needed to perform their job. Which of the following describes this form of access control? A. Separation of duties B. Time of day restrictions C. Implicit deny D. Least privilege
Question 31 An employee is granted access to only areas of a network folder needed to perform their job. Which of the following describes this form of access control? A. Separation of duties B. Time of day restrictions C. Implicit deny D. Least privilege
 Question 32 To help prevent unauthorized access to PCs, a security administrator implements screen savers that lock the PC after five minutes of inactivity. Which of the following controls is being described in this situation? A. Management B. Administrative C. Technical D. Operational
Question 32 To help prevent unauthorized access to PCs, a security administrator implements screen savers that lock the PC after five minutes of inactivity. Which of the following controls is being described in this situation? A. Management B. Administrative C. Technical D. Operational
 Question 33 To reduce an organization’s risk exposure by verifying compliance with company policy, which of the following should be performed periodically? A. Qualitative analysis B. Quantitative analysis C. Routine audits D. Incident management
Question 33 To reduce an organization’s risk exposure by verifying compliance with company policy, which of the following should be performed periodically? A. Qualitative analysis B. Quantitative analysis C. Routine audits D. Incident management
 Question 34 Which of the following access controls enforces permissions based on data labeling at specific levels? A. Mandatory access control B. Separation of duties access control C. Discretionary access control D. Role based access control
Question 34 Which of the following access controls enforces permissions based on data labeling at specific levels? A. Mandatory access control B. Separation of duties access control C. Discretionary access control D. Role based access control
 Question 35 Use of group accounts should be minimized to ensure which of the following? A. Password security B. Regular auditing C. Baseline management D. Individual accountability
Question 35 Use of group accounts should be minimized to ensure which of the following? A. Password security B. Regular auditing C. Baseline management D. Individual accountability
 Question 36 Sara, a company’s security officer, often receives reports of unauthorized personnel having access codes to the cipher locks of secure areas in the building. Sara should immediately implement which of the following? A. Acceptable Use Policy B. Physical security controls C. Technical controls D. Security awareness training
Question 36 Sara, a company’s security officer, often receives reports of unauthorized personnel having access codes to the cipher locks of secure areas in the building. Sara should immediately implement which of the following? A. Acceptable Use Policy B. Physical security controls C. Technical controls D. Security awareness training
 Question 37 Users require access to a certain server depending on their job function. Which of the following would be the MOST appropriate strategy for securing the server? A. Common access card B. Role based access control C. Discretionary access control D. Mandatory access control
Question 37 Users require access to a certain server depending on their job function. Which of the following would be the MOST appropriate strategy for securing the server? A. Common access card B. Role based access control C. Discretionary access control D. Mandatory access control
 Question 38 During an anonymous penetration test, Jane, a system administrator, was able to identify a shared print spool directory, and was able to download a document from the spool. Which statement BEST describes her privileges? A. All users have write access to the directory. B. Jane has read access to the file. C. All users have read access to the file. D. Jane has read access to the directory
Question 38 During an anonymous penetration test, Jane, a system administrator, was able to identify a shared print spool directory, and was able to download a document from the spool. Which statement BEST describes her privileges? A. All users have write access to the directory. B. Jane has read access to the file. C. All users have read access to the file. D. Jane has read access to the directory
 Question 39 Pete, an IT Administrator, needs to secure his server room. Which of the following mitigation methods would provide the MOST physical protection? A. Sign in and sign out logs B. Mantrap C. Video surveillance D. HVAC
Question 39 Pete, an IT Administrator, needs to secure his server room. Which of the following mitigation methods would provide the MOST physical protection? A. Sign in and sign out logs B. Mantrap C. Video surveillance D. HVAC
 Question 40 Which of the following should be connected to the fire alarm system in order to help prevent the spread of a fire in a server room without data loss to assist in an FM-200 deployment? A. Water base sprinkler system B. Electrical C. HVAC D. Video surveillance
Question 40 Which of the following should be connected to the fire alarm system in order to help prevent the spread of a fire in a server room without data loss to assist in an FM-200 deployment? A. Water base sprinkler system B. Electrical C. HVAC D. Video surveillance
 Question 41 Pete has obtained a highly sensitive document and has placed it on a network drive which has been formatted with NTFS and is shared via CIFS. Which of the following access controls apply to the sensitive file on the server? A. Discretionary B. Rule based C. Role based D. Mandatory
Question 41 Pete has obtained a highly sensitive document and has placed it on a network drive which has been formatted with NTFS and is shared via CIFS. Which of the following access controls apply to the sensitive file on the server? A. Discretionary B. Rule based C. Role based D. Mandatory
 Question 42 A database server containing personal information and a file server containing non-critical information must be secured. Which of the following would be a BEST practice to secure the servers? (Select TWO). A. Place the file server behind a door requiring biometric authorization. B. Place both servers under the system administrator’s desk. C. Place the database server behind a door with a cipher lock. D. Place the file server in an unlocked rack cabinet. E. Place the database server behind a door requiring biometric authorization.
Question 42 A database server containing personal information and a file server containing non-critical information must be secured. Which of the following would be a BEST practice to secure the servers? (Select TWO). A. Place the file server behind a door requiring biometric authorization. B. Place both servers under the system administrator’s desk. C. Place the database server behind a door with a cipher lock. D. Place the file server in an unlocked rack cabinet. E. Place the database server behind a door requiring biometric authorization.
 Question 43 A security technician is working with the network firewall team to implement access controls at the company’s demarc (telephony network) as part of the initiation of configuration management processes. One of the network technicians asks the security technician to explain the access control type found in a firewall. With which of the following should the security technician respond? A. Rule based access control B. Role based access control C. Discretionary access control D. Mandatory access contro
Question 43 A security technician is working with the network firewall team to implement access controls at the company’s demarc (telephony network) as part of the initiation of configuration management processes. One of the network technicians asks the security technician to explain the access control type found in a firewall. With which of the following should the security technician respond? A. Rule based access control B. Role based access control C. Discretionary access control D. Mandatory access contro
 Question 44 Which of the following can be used to discover if a security attack is occurring on a web server? A. Creating a new baseline B. Disable unused accounts C. Implementing full disk encryption D. Monitoring access logs
Question 44 Which of the following can be used to discover if a security attack is occurring on a web server? A. Creating a new baseline B. Disable unused accounts C. Implementing full disk encryption D. Monitoring access logs
 Question 45 After a production outage, which of the following documents contains detailed information on the order in which the system should be restored to service? A. Succession planning B. Disaster recovery plan C. Information security plan D. Business impact analysis
Question 45 After a production outage, which of the following documents contains detailed information on the order in which the system should be restored to service? A. Succession planning B. Disaster recovery plan C. Information security plan D. Business impact analysis
 2015 -2016 Test SYO-401 Study Guide First 45 questions are from SYO-301 Study Guide
2015 -2016 Test SYO-401 Study Guide First 45 questions are from SYO-301 Study Guide
 Question 1 - 401 Which of the following accurately identifies the primary security control classifications? A. Role-based, mandatory, and discretionary B. Technical, management, and operational C. Physical, logical, and technical D. Preventive, detective, and technical
Question 1 - 401 Which of the following accurately identifies the primary security control classifications? A. Role-based, mandatory, and discretionary B. Technical, management, and operational C. Physical, logical, and technical D. Preventive, detective, and technical
 Question 2 - 401 You need to reduce the attack surface of a web server. Which of the following is a preventive control that will assist with this goal? A. Disabling unnecessary services B. Identifying the initial baseline configuration C. Using hardware locks D. Monitoring logs for trends
Question 2 - 401 You need to reduce the attack surface of a web server. Which of the following is a preventive control that will assist with this goal? A. Disabling unnecessary services B. Identifying the initial baseline configuration C. Using hardware locks D. Monitoring logs for trends
 Question 3 - 401 A security expert is identifying and implementing several different physical deterrent controls to protect an organization’s server room. Which of the following choices would BEST meet this objective? A. Using hardware locks B. Utilizing data encryption C. Performing a vulnerability assessment D. Training users
Question 3 - 401 A security expert is identifying and implementing several different physical deterrent controls to protect an organization’s server room. Which of the following choices would BEST meet this objective? A. Using hardware locks B. Utilizing data encryption C. Performing a vulnerability assessment D. Training users
 Question 4 - 401 You need to secure access to a data center. Which of the following choices provides the BEST physical security to meet this need? (Select THREE. ) A. Biometrics B. Cable locks C. CCTV D. Mantrap
Question 4 - 401 You need to secure access to a data center. Which of the following choices provides the BEST physical security to meet this need? (Select THREE. ) A. Biometrics B. Cable locks C. CCTV D. Mantrap
 Question 5 - 401 A security professional needs to identify a physical security control that will identify and authenticate individuals before allowing them to pass, and restrict passage to only a single person at a time. What should the professional recommend? A. Tailgating B. Smart cards C. Biometrics D. Mantrap
Question 5 - 401 A security professional needs to identify a physical security control that will identify and authenticate individuals before allowing them to pass, and restrict passage to only a single person at a time. What should the professional recommend? A. Tailgating B. Smart cards C. Biometrics D. Mantrap
 Question 6 - 401 Your company wants to control access to a restricted area of the building by adding an additional physical security control that includes facial recognition Which of the following provides the BEST solution? A. Bollards B. Guards C. Palm scanners D. Video surveillance
Question 6 - 401 Your company wants to control access to a restricted area of the building by adding an additional physical security control that includes facial recognition Which of the following provides the BEST solution? A. Bollards B. Guards C. Palm scanners D. Video surveillance
 Question 7 - 401 Employees access a secure area by entering a cipher code, but this code does not identify individuals. After a recent security incident, management has decided to implement a key card system that will identify individuals who enter and exit this security area. However, the installation might take six months or longer. Which of the following choices can the organization install immediately to identify individuals who enter or exit the secure area? A. Mantrap B. Access list (ACL) C. CCTV D. Bollards
Question 7 - 401 Employees access a secure area by entering a cipher code, but this code does not identify individuals. After a recent security incident, management has decided to implement a key card system that will identify individuals who enter and exit this security area. However, the installation might take six months or longer. Which of the following choices can the organization install immediately to identify individuals who enter or exit the secure area? A. Mantrap B. Access list (ACL) C. CCTV D. Bollards
 Question 8 - 401 Thieves recently rammed a truck through the entrance of your company’s main building. During the chaos, their partners proceeded to steal a significant amount of IT equipment. Which of the following choices can you use to prevent this from happening again? A. Bollards B. Guards C. CCTV D. Mantrap
Question 8 - 401 Thieves recently rammed a truck through the entrance of your company’s main building. During the chaos, their partners proceeded to steal a significant amount of IT equipment. Which of the following choices can you use to prevent this from happening again? A. Bollards B. Guards C. CCTV D. Mantrap
 Question 9 - 401 You maintain a training lab with eighteen computers. You have enough rights and permissions on these machines so that you can configure them as needed for classes. However, you do not have the rights to add them to your organization’s domain which of the following choices BEST describes this example? A. Least privilege B. Need to know C. User-based privileges D. Separation of duties
Question 9 - 401 You maintain a training lab with eighteen computers. You have enough rights and permissions on these machines so that you can configure them as needed for classes. However, you do not have the rights to add them to your organization’s domain which of the following choices BEST describes this example? A. Least privilege B. Need to know C. User-based privileges D. Separation of duties
 Question 10 - 401 Developers in your organization have created AN APPLICATION DESIGNED FOR THE SALES TEAM. Salespeople can log on to the application using a simple password of 1234. However, this password does not meet the organization’s password policy. What is the BEST response by the security administrator after learning about this? A. Nothing Strong passwords aren’t required in applications. B. Modify the security policy to accept this password. C. Document this as an exception in the application’s documentation. D. Direct the application team manager to ensure the application adheres to the organization’s password policy. duties
Question 10 - 401 Developers in your organization have created AN APPLICATION DESIGNED FOR THE SALES TEAM. Salespeople can log on to the application using a simple password of 1234. However, this password does not meet the organization’s password policy. What is the BEST response by the security administrator after learning about this? A. Nothing Strong passwords aren’t required in applications. B. Modify the security policy to accept this password. C. Document this as an exception in the application’s documentation. D. Direct the application team manager to ensure the application adheres to the organization’s password policy. duties
 Question 11 - 401 You are redesigning your password policy to increase the security of the passwords. Which of the following choices provides the BEST security? (Select three. ) A. Maximum password age B. Password complexity C. Password history D. Password length E. Minimum password age
Question 11 - 401 You are redesigning your password policy to increase the security of the passwords. Which of the following choices provides the BEST security? (Select three. ) A. Maximum password age B. Password complexity C. Password history D. Password length E. Minimum password age
 Question 12 - 401 A company’s account management policy dictates that administrators should disable user accounts instead of deleting them when an employee leaves the company. What security benefit does this provide? A. Ensures that user keys are retained B. Ensures that user files are retained C. Makes it easier to enable the account if the employee returns D. Ensures that users cannot log on remotely
Question 12 - 401 A company’s account management policy dictates that administrators should disable user accounts instead of deleting them when an employee leaves the company. What security benefit does this provide? A. Ensures that user keys are retained B. Ensures that user files are retained C. Makes it easier to enable the account if the employee returns D. Ensures that users cannot log on remotely
 Question 13 - 401 You need to create an account for a contractor who will be working at your company for 90 days. Which of the following is the BEST security step to take when creating this account? A. Configure history on the account B. Configure a password expiration date on the account C. Configure an expiration date on the account D. Configure complexity
Question 13 - 401 You need to create an account for a contractor who will be working at your company for 90 days. Which of the following is the BEST security step to take when creating this account? A. Configure history on the account B. Configure a password expiration date on the account C. Configure an expiration date on the account D. Configure complexity
 Question 14 - 401 You’re asked to identify who is accessing a spreadsheet containing employee salary data. Detailed logging is configured correctly on this file. However, you are unable to identify a specific person who is accessing the file. What is the MOST likely reason? A. Shared accounts are not prohibited B. Guest accounts are disabled C. Permissions for the file were assigned to a group D. Account lockout has been enabled
Question 14 - 401 You’re asked to identify who is accessing a spreadsheet containing employee salary data. Detailed logging is configured correctly on this file. However, you are unable to identify a specific person who is accessing the file. What is the MOST likely reason? A. Shared accounts are not prohibited B. Guest accounts are disabled C. Permissions for the file were assigned to a group D. Account lockout has been enabled
 Question 15 - 401 Members of a project team came in on the weekend to complete some work on a key project. However, they found that they were unable to access any of the project data. Which of the following choices is the MOST likely reason why they can’t access this data? A. Discretionary access control B. Time-of-day access control C. Rule-based access control D. Role-based access control
Question 15 - 401 Members of a project team came in on the weekend to complete some work on a key project. However, they found that they were unable to access any of the project data. Which of the following choices is the MOST likely reason why they can’t access this data? A. Discretionary access control B. Time-of-day access control C. Rule-based access control D. Role-based access control
 Question 16 - 401 An administrator needs to grant users access to different servers based on their job functions. Which access control model is the BEST choice to use? A. Discretionary access control B. Mandatory access control C. Role-based access control D. Rule-based access control
Question 16 - 401 An administrator needs to grant users access to different servers based on their job functions. Which access control model is the BEST choice to use? A. Discretionary access control B. Mandatory access control C. Role-based access control D. Rule-based access control
 Question 17 - 401 Interns from a local college frequently work at your company. Some interns work with the database developers, some interns work with the web application developers, and some interns work with both developers. Interns working with the database developers require different privileges. What is the simplest method to meet these requirements ? A. Use generic accounts B. Create user-based privileges C. Use group-based privileges D. Grant the interns access to the Guest account
Question 17 - 401 Interns from a local college frequently work at your company. Some interns work with the database developers, some interns work with the web application developers, and some interns work with both developers. Interns working with the database developers require different privileges. What is the simplest method to meet these requirements ? A. Use generic accounts B. Create user-based privileges C. Use group-based privileges D. Grant the interns access to the Guest account
 Question 18 - 401 Your organization wants to reduce the administrative workload related to account management. Which of the following is the BEST choice? A. Implement group-based privileges B. Implement user-based privileges C. Implement the Guest account and Guests group D. Implement periodic reviews of user access
Question 18 - 401 Your organization wants to reduce the administrative workload related to account management. Which of the following is the BEST choice? A. Implement group-based privileges B. Implement user-based privileges C. Implement the Guest account and Guests group D. Implement periodic reviews of user access
 Question 19 - 401 Bart has read access to an accounting database and Lisa has both reach and write access to this database. A database application automatically triggers a change in permissions so that Bart has both read and write access when Lisa is absent. What type of access control system is in place? A. DAC B. MAC C. Role-BAC D. Rule-BAC
Question 19 - 401 Bart has read access to an accounting database and Lisa has both reach and write access to this database. A database application automatically triggers a change in permissions so that Bart has both read and write access when Lisa is absent. What type of access control system is in place? A. DAC B. MAC C. Role-BAC D. Rule-BAC
 Question 20 - 401 Your organization hosts several classified systems in the data center. Management wants to increase security with these systems by implanting two-factor authentication. Management also wants to restrict access to these systems to employees who have a need to know. Which of the following choices should management implement for authorization? A. USB token and PIN B. Username and password C. Mandatory access control D. Rule-based access control
Question 20 - 401 Your organization hosts several classified systems in the data center. Management wants to increase security with these systems by implanting two-factor authentication. Management also wants to restrict access to these systems to employees who have a need to know. Which of the following choices should management implement for authorization? A. USB token and PIN B. Username and password C. Mandatory access control D. Rule-based access control
 Question 21 - 401 A security professional has reported an increase in the number of tailgating violations into a secure data center. What can prevent this? A. CCTV B. Mantrap C. Proximity card D. Cipher lock
Question 21 - 401 A security professional has reported an increase in the number of tailgating violations into a secure data center. What can prevent this? A. CCTV B. Mantrap C. Proximity card D. Cipher lock
 Question 22 - 401 Bart is in a break area outside the office. He told Lisa that he forgot his badge inside and asked Lisa to let him follow her when she goes back inside. What does this act decribe? ? A. spear phishing B. whaling C. mantrap D. tailgating
Question 22 - 401 Bart is in a break area outside the office. He told Lisa that he forgot his badge inside and asked Lisa to let him follow her when she goes back inside. What does this act decribe? ? A. spear phishing B. whaling C. mantrap D. tailgating
 Question 23 - 401 A user call into the help desk and asked the help-desk professional to reset his password. Which of the following choices is the BEST choice for what the help-desk professional should do before resetting the password? A. Verify the user’s original password B. Disable the user’s account C. Verify the user’s identity D. Enable the user’s account
Question 23 - 401 A user call into the help desk and asked the help-desk professional to reset his password. Which of the following choices is the BEST choice for what the help-desk professional should do before resetting the password? A. Verify the user’s original password B. Disable the user’s account C. Verify the user’s identity D. Enable the user’s account
 Question 24 - 401 The Retirement Castle uses groups for ease of administration and management. They recently hired Jasper as their new accountant. Jasper needs access to all the files and folders used by the Accounting department. What should the administrator do to give Jasper appropriate access? A. Create an account for Jasper and add the account to the Accounting group B. Give Jasper the password for the Guest account C. Create an account for Japer and use rule-based access control for accounting D. Create and account for Jasper and add the account to the Administrators group
Question 24 - 401 The Retirement Castle uses groups for ease of administration and management. They recently hired Jasper as their new accountant. Jasper needs access to all the files and folders used by the Accounting department. What should the administrator do to give Jasper appropriate access? A. Create an account for Jasper and add the account to the Accounting group B. Give Jasper the password for the Guest account C. Create an account for Japer and use rule-based access control for accounting D. Create and account for Jasper and add the account to the Administrators group
 Question 25 - 401 You are logging on to your bank’s web site using your email address and a password. What is the purpose of the email address in this example? A. Identification B. Authentication C. Authorization D. Availability
Question 25 - 401 You are logging on to your bank’s web site using your email address and a password. What is the purpose of the email address in this example? A. Identification B. Authentication C. Authorization D. Availability
 Question 26 - 401 Developers are planning to develop an application using role -based access control. Which of the following would they MOST likely include in their planning? A. A listing of labels reflecting classification levels B. A requirements list identifying need to know C. A listing of owners D. A matrix of functions matched with their required privileges
Question 26 - 401 Developers are planning to develop an application using role -based access control. Which of the following would they MOST likely include in their planning? A. A listing of labels reflecting classification levels B. A requirements list identifying need to know C. A listing of owners D. A matrix of functions matched with their required privileges
 Question 27 - 401 Your organization has a password policy with a password history value of twelve. What does this indicate? A. Your password must be at least 12 characters long B. Twelve different passwords must be used before reusing the same password C. Passwords must be changed every twelve days D. Passwords cannot be changed until twelve days have passed
Question 27 - 401 Your organization has a password policy with a password history value of twelve. What does this indicate? A. Your password must be at least 12 characters long B. Twelve different passwords must be used before reusing the same password C. Passwords must be changed every twelve days D. Passwords cannot be changed until twelve days have passed
 Question 28 - 401 Your organization wants to ensure that security controls continue to function, helping to maintain an appropriate security posture. Which of the following is the BEST choice to meet this goal? A. Auditing logs B. Routine audits C. Continuous security monitoring D. Vulnerability scans
Question 28 - 401 Your organization wants to ensure that security controls continue to function, helping to maintain an appropriate security posture. Which of the following is the BEST choice to meet this goal? A. Auditing logs B. Routine audits C. Continuous security monitoring D. Vulnerability scans
 Question 29 - 401 Homer called into the help desk and says he forgot his password. Which of the following choices is the BEST choice for what the help-desk professional should do? A. Verify the user’s account exists B. Look up the user’s password and tell the user what it is C. Disable the user’s account D. Reset the password and configure the password to expire after the first use
Question 29 - 401 Homer called into the help desk and says he forgot his password. Which of the following choices is the BEST choice for what the help-desk professional should do? A. Verify the user’s account exists B. Look up the user’s password and tell the user what it is C. Disable the user’s account D. Reset the password and configure the password to expire after the first use
 Question 30 - 401 An outside security auditor recently completed an in-depth security audit on your network. One of the issues he reported was related to passwords. Specifically, he found the following passwords used on the network: Pa$$, 1@W 2, G 7 b. T 3. What should be changed to avoid the problem shown with these passwords? A. Password complexity B. Password length C. Password history D. Password reuse
Question 30 - 401 An outside security auditor recently completed an in-depth security audit on your network. One of the issues he reported was related to passwords. Specifically, he found the following passwords used on the network: Pa$$, 1@W 2, G 7 b. T 3. What should be changed to avoid the problem shown with these passwords? A. Password complexity B. Password length C. Password history D. Password reuse
 Question 31 - 401 Your organization routinely hires contractors to assist with different projects. Administrators are rarely notified when a project ends and contractors leave. Which of the following is the BEST choice to ensure that contractors cannot log on with their account after they leave? A. Enable account expiration B. Enable an account enablement policy C. Enable an account recovery policy D. Enable generic accounts
Question 31 - 401 Your organization routinely hires contractors to assist with different projects. Administrators are rarely notified when a project ends and contractors leave. Which of the following is the BEST choice to ensure that contractors cannot log on with their account after they leave? A. Enable account expiration B. Enable an account enablement policy C. Enable an account recovery policy D. Enable generic accounts
 Question 32 - 401 Your organization includes the following statement in the security policy. “Security controls need to protect against both online and offline password brute force attacks. ” Which of the following controls is the LEAST helpful to meet these goals? A. Account expiration B. Account lockout C. Password complexity D. Password length
Question 32 - 401 Your organization includes the following statement in the security policy. “Security controls need to protect against both online and offline password brute force attacks. ” Which of the following controls is the LEAST helpful to meet these goals? A. Account expiration B. Account lockout C. Password complexity D. Password length
 Question 33 - 401 An e-commerce website does not currently have an access recovery process for customers who have forgotten their passwords. Which of the following choices are the BEST items to include if website designers add this process? (Select two. ) A. Create a web-based form that verifies customer identities using another method B. Set a temporary password that expires upon first use C. Implement biometric authentication D. Email the password to the user
Question 33 - 401 An e-commerce website does not currently have an access recovery process for customers who have forgotten their passwords. Which of the following choices are the BEST items to include if website designers add this process? (Select two. ) A. Create a web-based form that verifies customer identities using another method B. Set a temporary password that expires upon first use C. Implement biometric authentication D. Email the password to the user
 Question 34 - 401 You have discovered that some users have been using the same passwords for months, even though the password policy requires users to change their password every thirty days. You want to ensure that users cannot reuse the same password. Which settings should you configure? (Select two. ) A. Maximum password age B. Password length C. Password history D. Password complexity E. Minimum password age
Question 34 - 401 You have discovered that some users have been using the same passwords for months, even though the password policy requires users to change their password every thirty days. You want to ensure that users cannot reuse the same password. Which settings should you configure? (Select two. ) A. Maximum password age B. Password length C. Password history D. Password complexity E. Minimum password age
 Question 35 - 401 You configure access control for users in your organization. Some departments have a high employee turnover, so you want to simplify account administration. Which of the following is the BEST choice? A. User-assigned privileges B. Group-based privileges C. Domain-assigned privileges D. Network-assigned privileges
Question 35 - 401 You configure access control for users in your organization. Some departments have a high employee turnover, so you want to simplify account administration. Which of the following is the BEST choice? A. User-assigned privileges B. Group-based privileges C. Domain-assigned privileges D. Network-assigned privileges
 Question 36 - 401 A secure computing environment labels data with various security classifications. Authenticated users must have clearance to read this classified data. What type of access control model is this? A. MAC B. DAC C. Role-BAC D. Rule-BAC
Question 36 - 401 A secure computing environment labels data with various security classifications. Authenticated users must have clearance to read this classified data. What type of access control model is this? A. MAC B. DAC C. Role-BAC D. Rule-BAC
 Question 37 - 401 To ease giving access to network resources for employees, you decide there must be an easier way than granting users individual access to files, printers, computers, and applications. What security model should you consider using? A. Mandatory access control B. Discretionary access control C. Role-based access control D. Time-of-day access control
Question 37 - 401 To ease giving access to network resources for employees, you decide there must be an easier way than granting users individual access to files, printers, computers, and applications. What security model should you consider using? A. Mandatory access control B. Discretionary access control C. Role-based access control D. Time-of-day access control
 Question 38 - 401 Linda creates a folder called Budget Projections in her home account and shares it with colleagues in her department. Which of he following best describes this type of access control system? A. MAC B. DAC C. Role-based access control D. Time-of-day access control
Question 38 - 401 Linda creates a folder called Budget Projections in her home account and shares it with colleagues in her department. Which of he following best describes this type of access control system? A. MAC B. DAC C. Role-based access control D. Time-of-day access control
 Question 39 - 401 You require that users not be logged on to the network after 6 p. m. while you analyze network traffic during nonbusiness hours. What should you do? A. Unplug their stations from the network B. Tell users to press CTRL-ALT-DEL to lock their stations C. Configure time-of-day restrictions to ensure nobody can be logged in after 6 p. m. D. Disable user accounts at 6 p. m.
Question 39 - 401 You require that users not be logged on to the network after 6 p. m. while you analyze network traffic during nonbusiness hours. What should you do? A. Unplug their stations from the network B. Tell users to press CTRL-ALT-DEL to lock their stations C. Configure time-of-day restrictions to ensure nobody can be logged in after 6 p. m. D. Disable user accounts at 6 p. m.
 Question 40 - 401 One of your users, Matthias, is taking a three-month sabbatical because of a medical condition, after which he will return to work. What should you do with Matthias’ user account? A. Delete the account and re-create it when he returns B. Disable the account and enable it when he returns C. Export his account properties to a text file for later import and then delete it D. Ensure you have a backup of his account details and delete his account
Question 40 - 401 One of your users, Matthias, is taking a three-month sabbatical because of a medical condition, after which he will return to work. What should you do with Matthias’ user account? A. Delete the account and re-create it when he returns B. Disable the account and enable it when he returns C. Export his account properties to a text file for later import and then delete it D. Ensure you have a backup of his account details and delete his account
 Question 41 - 401 During an IT security meeting, the topic of account lockout surfaces. When you suggest all user accounts be locked for 30 minutes after three incorrect logon attempts, your colleague Phil states this is a serious problems when applied to administrative accounts. What types of issues might Phil be referring to? A. Dictionary attacks could break into administrative accounts B. Administrative accounts are much sought after by attackers C. Administrative accounts are placed into administrative groups D. Do. S (Denial of Service) attacks could render administrative accounts unusable
Question 41 - 401 During an IT security meeting, the topic of account lockout surfaces. When you suggest all user accounts be locked for 30 minutes after three incorrect logon attempts, your colleague Phil states this is a serious problems when applied to administrative accounts. What types of issues might Phil be referring to? A. Dictionary attacks could break into administrative accounts B. Administrative accounts are much sought after by attackers C. Administrative accounts are placed into administrative groups D. Do. S (Denial of Service) attacks could render administrative accounts unusable
 Question 42 - 401 Your VPN (Virtual Private Network) appliance is configured to disallow user authentication unless the user or group is listed as allowed. Regarding blocked users, what best describes this configuration? A. Implicit allow B. Implicit deny C. Explicit allow D. Explicit deny
Question 42 - 401 Your VPN (Virtual Private Network) appliance is configured to disallow user authentication unless the user or group is listed as allowed. Regarding blocked users, what best describes this configuration? A. Implicit allow B. Implicit deny C. Explicit allow D. Explicit deny
 Question 43 - 401 Which term is best defined as an object’s list of users, groups, processes, and their permissions? A. ACE (Access Control Explicit) B. ACL (Access Control List) C. Active directory D. Access log
Question 43 - 401 Which term is best defined as an object’s list of users, groups, processes, and their permissions? A. ACE (Access Control Explicit) B. ACL (Access Control List) C. Active directory D. Access log
 Question 44 - 401 What security model uses data classifications and security clearances? A. R-BAC B. DAC C. PKI (Public Key Infrastructure) D. MAC
Question 44 - 401 What security model uses data classifications and security clearances? A. R-BAC B. DAC C. PKI (Public Key Infrastructure) D. MAC
 Question 45 - 401 A windows server has an inbound firewall rule allowing inbound RDP (Remote Desktop Protocol) as shown in Figure 11 -1. Which term best describes this particular firewall rule? A. Explicit allow B. Explicit deny C. Implicit allow D. Implicit deny
Question 45 - 401 A windows server has an inbound firewall rule allowing inbound RDP (Remote Desktop Protocol) as shown in Figure 11 -1. Which term best describes this particular firewall rule? A. Explicit allow B. Explicit deny C. Implicit allow D. Implicit deny
 Question 46 - 401 Users complain that they must remember passwords for a multitude of user accounts to access software required for their jobs. How can this be solved? ? A. SSO B. ACL C. PKI D. MAC
Question 46 - 401 Users complain that they must remember passwords for a multitude of user accounts to access software required for their jobs. How can this be solved? ? A. SSO B. ACL C. PKI D. MAC
 Question 47 - 401 The permissions for a Windows folder are shown in Figure 11 -2. Permission inheritance has been disabled. User Rlachance attempts to access the folder Jones_Vs_Cowell. What is the result? A. Rlachance is denied access because of explicit denial. B. Rlachance is allowed access because of being in the Everyone group. C. Rlachance is denied access because of implicit denial. D. Rlachance is allowed access because of implicit allowal.
Question 47 - 401 The permissions for a Windows folder are shown in Figure 11 -2. Permission inheritance has been disabled. User Rlachance attempts to access the folder Jones_Vs_Cowell. What is the result? A. Rlachance is denied access because of explicit denial. B. Rlachance is allowed access because of being in the Everyone group. C. Rlachance is denied access because of implicit denial. D. Rlachance is allowed access because of implicit allowal.
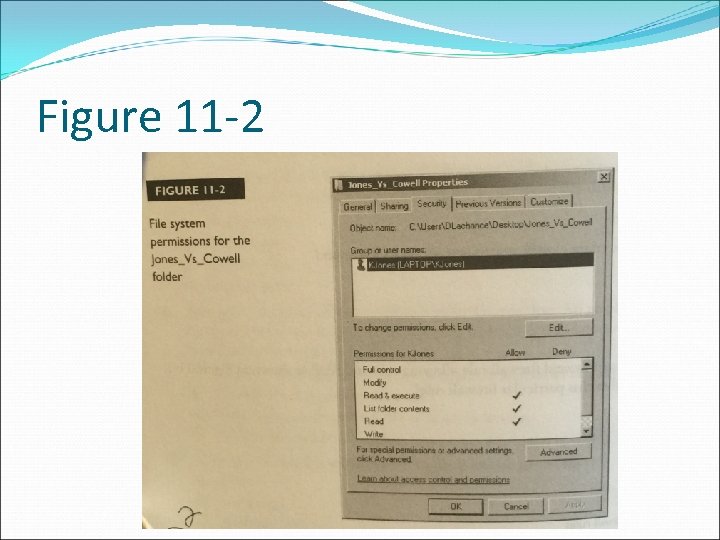 Figure 11 -2
Figure 11 -2
 Question 48 - 401 A Microsoft SQL database administrator creates a service account for the SQL server agent with the settings shown in Figure 11 -3. What security problem exists with this configuration? A. The username does not follow a naming convention B. The password is not long enough C. The password never expires option is enabled D. The account is disabled option is not disabled
Question 48 - 401 A Microsoft SQL database administrator creates a service account for the SQL server agent with the settings shown in Figure 11 -3. What security problem exists with this configuration? A. The username does not follow a naming convention B. The password is not long enough C. The password never expires option is enabled D. The account is disabled option is not disabled
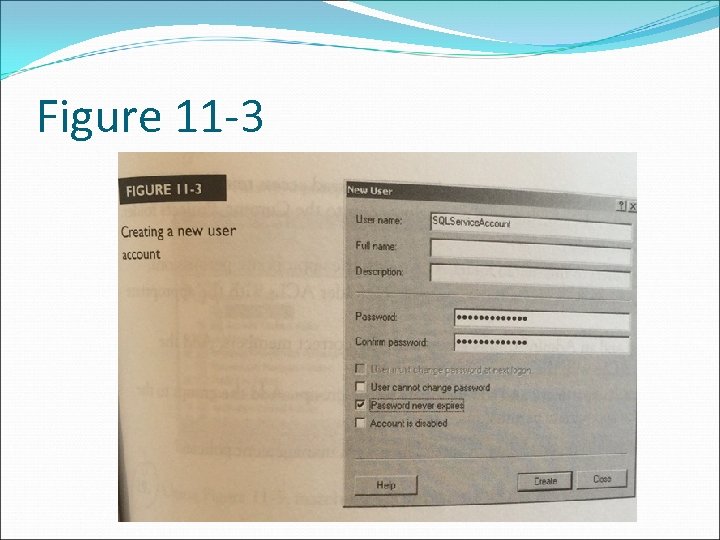 Figure 11 -3
Figure 11 -3
 Question 49 - 401 What is the difference between security clearances and classification labels? (Choose two. ) A. There is no difference B. Classification labels identify data sensitivity C. Security clearances identify data sensitivity D. Security clearances are compared with classification labels
Question 49 - 401 What is the difference between security clearances and classification labels? (Choose two. ) A. There is no difference B. Classification labels identify data sensitivity C. Security clearances identify data sensitivity D. Security clearances are compared with classification labels
 Question 50 - 401 Complex passwords are considered which type of security control? A. Management B. Technical C. Physical D. Operational
Question 50 - 401 Complex passwords are considered which type of security control? A. Management B. Technical C. Physical D. Operational


