07cc7cc00caf20b7f997cb9b74996585.ppt
- Количество слайдов: 41
 Chapter Six Windows XP Security and Access Controls
Chapter Six Windows XP Security and Access Controls
 Objectives Describe the Windows XP security model, and the key role of logon authentication n Customize the logon process n Discuss domain security concepts n Understand the Local Computer Policy n
Objectives Describe the Windows XP security model, and the key role of logon authentication n Customize the logon process n Discuss domain security concepts n Understand the Local Computer Policy n
 Objectives Enable and use auditing n Encrypt NTFS files, folders, or drives using the Encrypted File System (EFS) n Understand implement Internet security n
Objectives Enable and use auditing n Encrypt NTFS files, folders, or drives using the Encrypted File System (EFS) n Understand implement Internet security n
 The Windows XP Security Model n n Windows XP Professional can establish local security when used as a standalone system, or participate in domain security Domain security n n Control of user accounts, group memberships, and resource access for all members of a network Password n Unique string of characters that must be provided before logon or an access is authorized
The Windows XP Security Model n n Windows XP Professional can establish local security when used as a standalone system, or participate in domain security Domain security n n Control of user accounts, group memberships, and resource access for all members of a network Password n Unique string of characters that must be provided before logon or an access is authorized
 The Windows XP Security Model n A user who successfully logs on receives and access token n Process n n Primary unit of execution in the Windows XP operating system environment Access control list (ACL) n List of security identifiers that are contained by a resource object
The Windows XP Security Model n A user who successfully logs on receives and access token n Process n n Primary unit of execution in the Windows XP operating system environment Access control list (ACL) n List of security identifiers that are contained by a resource object
 Logon Authentication n The logon process has two components: n Identification n Requires that a use supply a valid account name (and in a domain environment, the name of the domain to which that user account belongs) n Authentication n Means that a user must use some method to verify his or her identity
Logon Authentication n The logon process has two components: n Identification n Requires that a use supply a valid account name (and in a domain environment, the name of the domain to which that user account belongs) n Authentication n Means that a user must use some method to verify his or her identity
 Logon Authentication n n An access token includes all security information pertaining to that user, including the user’s security ID (SID) and SIDs for each of the groups to which the user belongs An access token includes the following components: n n n Unique SID for the account List of groups to which the user belongs List of rights and privileges associated with the specific user’s account
Logon Authentication n n An access token includes all security information pertaining to that user, including the user’s security ID (SID) and SIDs for each of the groups to which the user belongs An access token includes the following components: n n n Unique SID for the account List of groups to which the user belongs List of rights and privileges associated with the specific user’s account
 Logon Authentication n Access to the system is allowed only after the user receives the access token Each access token is created for one-time use during the logon process Once constructed, the access token is attached to the user’s shell process
Logon Authentication n Access to the system is allowed only after the user receives the access token Each access token is created for one-time use during the logon process Once constructed, the access token is attached to the user’s shell process
 Objects In Windows XP, access to individual resources is controlled at the object level n Object n Everything within the Windows XP operating environment is an object n Objects include files, folders, shares, printers, processes, etc. n
Objects In Windows XP, access to individual resources is controlled at the object level n Object n Everything within the Windows XP operating environment is an object n Objects include files, folders, shares, printers, processes, etc. n
 Access Control n The Windows XP logon procedure provides security through the use of the following: Mandatory logon n Restricted user mode n Physical logon n User profiles n
Access Control n The Windows XP logon procedure provides security through the use of the following: Mandatory logon n Restricted user mode n Physical logon n User profiles n
 Customizing the Logon Process n The Win. Logon process can be customized to display some or all of the following characteristics: n n n Retain or disable the last logon name entered Add a logon security warning Change the default shell Enable/Disable the Win. Logon Shutdown button Enable automated logon
Customizing the Logon Process n The Win. Logon process can be customized to display some or all of the following characteristics: n n n Retain or disable the last logon name entered Add a logon security warning Change the default shell Enable/Disable the Win. Logon Shutdown button Enable automated logon
 Customizing the Logon Process Figure 6 -1: The Win. Logon key viewed through Regedit
Customizing the Logon Process Figure 6 -1: The Win. Logon key viewed through Regedit
 Disabling the Default Username n n n By default, the logon window displays the name of the last user to log on It is possible to change the default by altering the value of its associated Registry key or Local Security Policy value Disabling the default username option presents a blank username field at the logon prompt
Disabling the Default Username n n n By default, the logon window displays the name of the last user to log on It is possible to change the default by altering the value of its associated Registry key or Local Security Policy value Disabling the default username option presents a blank username field at the logon prompt
 Adding a Security Warning Message n n Depending on your organization’s security policy, you might be legally obligated to add a warning message that appears before the logon prompt is displayed Two Registry or Local Security Policy values are involved in this effort: n n Legal. Notice. Caption Legal. Notice. Text
Adding a Security Warning Message n n Depending on your organization’s security policy, you might be legally obligated to add a warning message that appears before the logon prompt is displayed Two Registry or Local Security Policy values are involved in this effort: n n Legal. Notice. Caption Legal. Notice. Text
 Changing the Shell The default shell is Windows Explorer n You can change the shell to a custom or thirdparty application depending on the needs or security policy of your organization n
Changing the Shell The default shell is Windows Explorer n You can change the shell to a custom or thirdparty application depending on the needs or security policy of your organization n
 Disabling the Shutdown Button n n By default, the Windows XP logon window includes a Shutdown button However, in an environment in which users have access to the keyboard and mouse on a Windows XP machine, this option has the potential for unwanted system shutdowns n Fortunately, this option can be disabled
Disabling the Shutdown Button n n By default, the Windows XP logon window includes a Shutdown button However, in an environment in which users have access to the keyboard and mouse on a Windows XP machine, this option has the potential for unwanted system shutdowns n Fortunately, this option can be disabled
 Automating Logons n To set up an automated logon, the following Registry value entries must be defined and set within the HKEY_LOCAL_MACHINESOFTWAREMicrosoft Windows NTCurrent. VersionWinlogon key: n n Default. Domain. Name Default. User. Name Default. Password Auto. Admin. Logon
Automating Logons n To set up an automated logon, the following Registry value entries must be defined and set within the HKEY_LOCAL_MACHINESOFTWAREMicrosoft Windows NTCurrent. VersionWinlogon key: n n Default. Domain. Name Default. User. Name Default. Password Auto. Admin. Logon
 Automatic Account Lockout n n n Disables a user account if a predetermined number of failed logon attempts occur within a specified time limit This feature is intended to prevent intrusion by unauthorized users attempting to gain access by guessing a password or launching a dictionary attack The default setting in Windows XP is to allow an unlimited number of failed access attempts to a user account without locking out that account
Automatic Account Lockout n n n Disables a user account if a predetermined number of failed logon attempts occur within a specified time limit This feature is intended to prevent intrusion by unauthorized users attempting to gain access by guessing a password or launching a dictionary attack The default setting in Windows XP is to allow an unlimited number of failed access attempts to a user account without locking out that account
 Domain Security Concepts and Systems n n A domain is a collection of computers with centrally managed security and activities Domain security n n Control of user accounts, group memberships, and resource access for all members of a network Domain controller n Windows 2000. NET Server system with the Active Directory support services installed and configured
Domain Security Concepts and Systems n n A domain is a collection of computers with centrally managed security and activities Domain security n n Control of user accounts, group memberships, and resource access for all members of a network Domain controller n Windows 2000. NET Server system with the Active Directory support services installed and configured
 Kerberos and Authentication Services n Kerberos version 5 n n An authentication encryption protocol employed by Windows XP to protect logon credentials Network authentication n Act of connecting to or accessing resources from some other member of the domain network
Kerberos and Authentication Services n Kerberos version 5 n n An authentication encryption protocol employed by Windows XP to protect logon credentials Network authentication n Act of connecting to or accessing resources from some other member of the domain network
 Kerberos and Authentication Services n The communications that occur during network authentication are protected by one of several methods, including: Kerberos v 5 n Secure Socket Layer/Transport Layer Security (SSL/TLS) n NTLM (NT LAN Manager) authentication for compatibility with Windows NT 4. 0 n
Kerberos and Authentication Services n The communications that occur during network authentication are protected by one of several methods, including: Kerberos v 5 n Secure Socket Layer/Transport Layer Security (SSL/TLS) n NTLM (NT LAN Manager) authentication for compatibility with Windows NT 4. 0 n
 Kerberos and Authentication Services n Kerberos version 5 authentication n n Windows XP uses Kerberos version 5 as the primary protocol for authentication security Secure Socket Layer/Transport Layer Authentication scheme often used by Web-based applications and is supported on Windows XP through IIS n SSL functions by issuing an identity certificate to both the client and server n
Kerberos and Authentication Services n Kerberos version 5 authentication n n Windows XP uses Kerberos version 5 as the primary protocol for authentication security Secure Socket Layer/Transport Layer Authentication scheme often used by Web-based applications and is supported on Windows XP through IIS n SSL functions by issuing an identity certificate to both the client and server n
 Kerberos and Authentication Services n NTLM (NT LAN Manager) authentication Mechanism used by Windows NT 4. 0 n Windows XP supports this authentication method solely for backward compatibility with Windows NT Servers and Windows NT Workstation clients n NTLM is significantly less secure than Kerberos version 5 n
Kerberos and Authentication Services n NTLM (NT LAN Manager) authentication Mechanism used by Windows NT 4. 0 n Windows XP supports this authentication method solely for backward compatibility with Windows NT Servers and Windows NT Workstation clients n NTLM is significantly less secure than Kerberos version 5 n
 Local Computer Policy n n Combination of controls that in Windows NT existed only in the Registry, through system policies, or as Control Panel applet controls Sometimes the local computer policy is called a software policy or an environmental policy or even a Windows XP policy n No matter what name is actually used, the local computer policy is simply the local system’s group policy
Local Computer Policy n n Combination of controls that in Windows NT existed only in the Registry, through system policies, or as Control Panel applet controls Sometimes the local computer policy is called a software policy or an environmental policy or even a Windows XP policy n No matter what name is actually used, the local computer policy is simply the local system’s group policy
 Local Computer Policy Figure 6 -2: MMC with Group Policy snap-in displaying Local Computer Policy with Security Settings selected on a Windows XP Professional System
Local Computer Policy Figure 6 -2: MMC with Group Policy snap-in displaying Local Computer Policy with Security Settings selected on a Windows XP Professional System
 Computer Configuration n There are three purposes for using the public key policies: n n n To offer additional controls over the EFS To enable the issuing of certificates To allow you to establish trust in a certificate authority
Computer Configuration n There are three purposes for using the public key policies: n n n To offer additional controls over the EFS To enable the issuing of certificates To allow you to establish trust in a certificate authority
 Computer Configuration n IP Security (IPSec) n n n Security measure added to TCP/IP to protect communications between two systems using that protocol Negotiates a secure encrypted communications link between a client and server through public and private encryption key management Can be used over a RAS or WAN link (through L 2 TP) or within a LAN
Computer Configuration n IP Security (IPSec) n n n Security measure added to TCP/IP to protect communications between two systems using that protocol Negotiates a secure encrypted communications link between a client and server through public and private encryption key management Can be used over a RAS or WAN link (through L 2 TP) or within a LAN
 Computer Configuration n The controls available through the Administrative Templates folder include: Controlling security and software updates for Internet Explorer n Controlling access and use of the Task Scheduler and Windows Installer n Controlling logon security features and operations n Controlling disk quotas n
Computer Configuration n The controls available through the Administrative Templates folder include: Controlling security and software updates for Internet Explorer n Controlling access and use of the Task Scheduler and Windows Installer n Controlling logon security features and operations n Controlling disk quotas n
 Computer Configuration n The controls available through the Administrative Templates folder include (cont. ): n n Managing how group policies are processed Managing system file protection Managing offline access of network resources Controlling printer use and function
Computer Configuration n The controls available through the Administrative Templates folder include (cont. ): n n Managing how group policies are processed Managing system file protection Managing offline access of network resources Controlling printer use and function
 User Configuration n The items contained in the User Configuration’s Administrative Templates section include: n n Internet Explorer configuration, interface, features, and function controls Windows Explorer management (interface, available commands, features) MMC Management Task Scheduler and Windows Installer controls
User Configuration n The items contained in the User Configuration’s Administrative Templates section include: n n Internet Explorer configuration, interface, features, and function controls Windows Explorer management (interface, available commands, features) MMC Management Task Scheduler and Windows Installer controls
 User Configuration n The items contained in the User Configuration’s Administrative Templates section include (cont. ): Start menu and Taskbar features management n Desktop environment management n Control Panel applet management n Offline network access control n
User Configuration n The items contained in the User Configuration’s Administrative Templates section include (cont. ): Start menu and Taskbar features management n Desktop environment management n Control Panel applet management n Offline network access control n
 User Configuration n The items contained in the User Configuration’s Administrative Templates section include (cont. ): Network connection management n Logon and logoff script management n Group Policy application n
User Configuration n The items contained in the User Configuration’s Administrative Templates section include (cont. ): Network connection management n Logon and logoff script management n Group Policy application n
 User Configuration Figure 6 -3: The Explain tab of a Local Computer Policy control dialog box
User Configuration Figure 6 -3: The Explain tab of a Local Computer Policy control dialog box
 User Configuration n The Policy tab on the Properties dialog box for each control offers three settings: Not configured n Enabled n Disabled n
User Configuration n The Policy tab on the Properties dialog box for each control offers three settings: Not configured n Enabled n Disabled n
 Auditing n n Security process that records the occurrence of specific operating system events in a Security log Event Viewer n Utility that maintains application, security, and system event logs on your computer
Auditing n n Security process that records the occurrence of specific operating system events in a Security log Event Viewer n Utility that maintains application, security, and system event logs on your computer
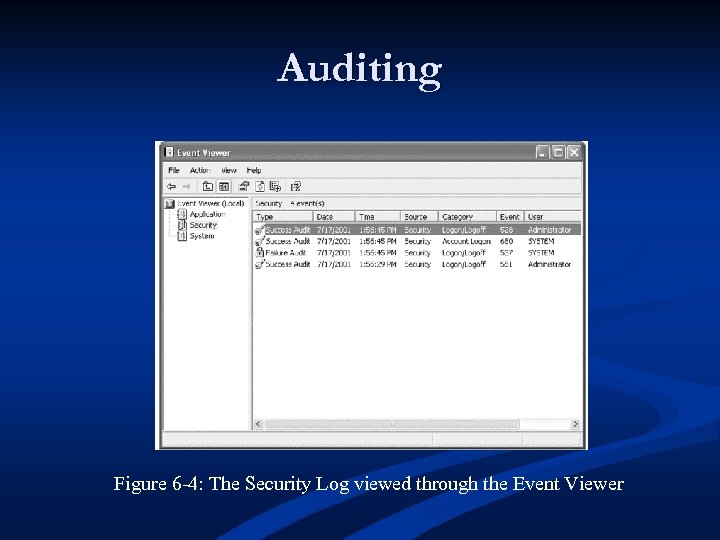 Auditing Figure 6 -4: The Security Log viewed through the Event Viewer
Auditing Figure 6 -4: The Security Log viewed through the Event Viewer
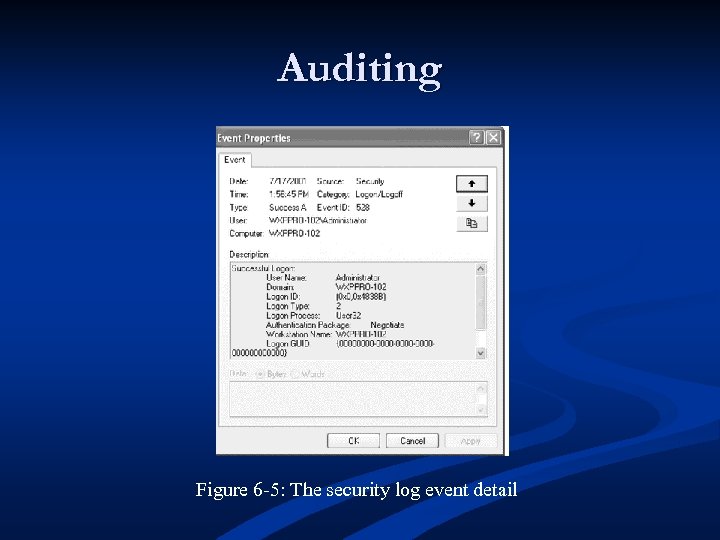 Auditing Figure 6 -5: The security log event detail
Auditing Figure 6 -5: The security log event detail
 Encrypted File System (EFS) Allows you to encrypt data stored on NTFS drive n When EFS is enabled on a file, folder, or drive, only the enabling user can gain access to the encrypted object n EFS uses a public and private key encryption method n
Encrypted File System (EFS) Allows you to encrypt data stored on NTFS drive n When EFS is enabled on a file, folder, or drive, only the enabling user can gain access to the encrypted object n EFS uses a public and private key encryption method n
 Internet Security n n n Connecting to the Internet requires that you accept some risk Most of the security features used to protect data within a LAN or even on a standalone system can also be leveraged to protect against Internet attacks As well, Microsoft has added the Internet Connection Firewall (ICF) to Windows XP
Internet Security n n n Connecting to the Internet requires that you accept some risk Most of the security features used to protect data within a LAN or even on a standalone system can also be leveraged to protect against Internet attacks As well, Microsoft has added the Internet Connection Firewall (ICF) to Windows XP
 Chapter Summary n n n Windows XP has object-level access controls that provide the foundation on which all resource access rest The Windows XP logon process strictly controls how users identify themselves and log onto a Windows XP machine Likewise, Win. Logon’s protected memory structures keep this all-important gatekeeper function from being replaced by would-be system crackers
Chapter Summary n n n Windows XP has object-level access controls that provide the foundation on which all resource access rest The Windows XP logon process strictly controls how users identify themselves and log onto a Windows XP machine Likewise, Win. Logon’s protected memory structures keep this all-important gatekeeper function from being replaced by would-be system crackers
 Chapter Summary n n n Win. Logon also supports a number of logon controls Key Local Computer Policy settings can be used to block unauthorized break-in attempts The local computer policy controls many aspects of the security system as well as enabling or restricting specific functions and features of the operating system
Chapter Summary n n n Win. Logon also supports a number of logon controls Key Local Computer Policy settings can be used to block unauthorized break-in attempts The local computer policy controls many aspects of the security system as well as enabling or restricting specific functions and features of the operating system


