98120828a6be3047d637b441b3961468.ppt
- Количество слайдов: 96
 Chapter 9 Security
Chapter 9 Security
 Topics n Introduction n n Security channel n n n Authentication, integrity, confidentiality Access control n n Threats, mechanisms, cryptography Firewall, secure mobile code Security management Examples n Kerberos, E-commerce
Topics n Introduction n n Security channel n n n Authentication, integrity, confidentiality Access control n n Threats, mechanisms, cryptography Firewall, secure mobile code Security management Examples n Kerberos, E-commerce
 What Do We Need to Protect? n Data n n Resources n n Information we keep on computers (product design, financial records, personnel data) Unauthorized use of computer time & space Reputation n Misrepresentation, forgery, negative publicity
What Do We Need to Protect? n Data n n Resources n n Information we keep on computers (product design, financial records, personnel data) Unauthorized use of computer time & space Reputation n Misrepresentation, forgery, negative publicity
 Fundamental Security Objectives n n Confidentiality - Protection from unauthorized persons Integrity - consistency of data; no unauthorized creation, alteration or destruction Availability - ensuring access to legitimate users Access control - ensuring appropriate use by authorized users
Fundamental Security Objectives n n Confidentiality - Protection from unauthorized persons Integrity - consistency of data; no unauthorized creation, alteration or destruction Availability - ensuring access to legitimate users Access control - ensuring appropriate use by authorized users
 Security Threats n Interception n Interruption n Unauthorized changing of data Fabrication n n Unavailable of service or data Denial of service attack Modification n n Unauthorized access to a service or data Eavesdropping Adding data or activity normally not exist. Security policy
Security Threats n Interception n Interruption n Unauthorized changing of data Fabrication n n Unavailable of service or data Denial of service attack Modification n n Unauthorized access to a service or data Eavesdropping Adding data or activity normally not exist. Security policy
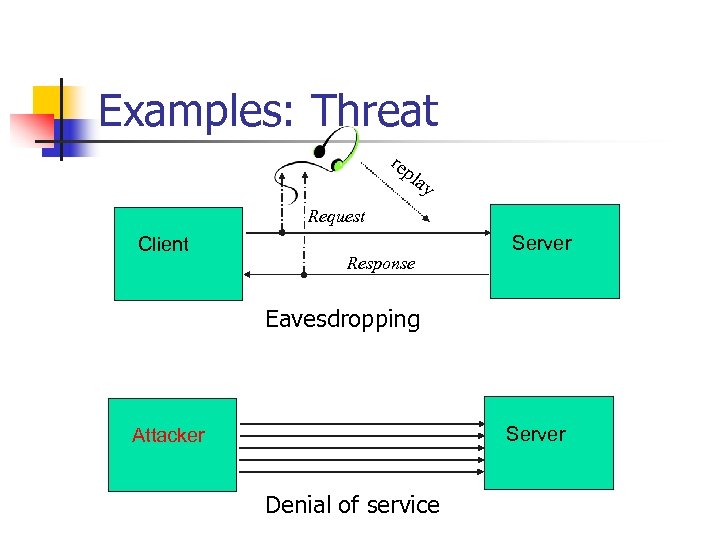 Examples: Threat rep lay Request Client Response Server Eavesdropping Server Attacker Denial of service
Examples: Threat rep lay Request Client Response Server Eavesdropping Server Attacker Denial of service
 Example: Security Policy n Chinese Wall Model: widely used in financial world n n Group datasets into “conflict of interest classes” Subjects are allowed to access to at most one dataset belonging to each such conflict of interest class n Subject s can access company c’s data only if n n a) s has already accessed c’s data or b) s has not yet accessed any of c’s competitors’ data s can write to c’s data only if s can not read any other company’s sensitive data Mandatory security policy for UK Stock Exchange.
Example: Security Policy n Chinese Wall Model: widely used in financial world n n Group datasets into “conflict of interest classes” Subjects are allowed to access to at most one dataset belonging to each such conflict of interest class n Subject s can access company c’s data only if n n a) s has already accessed c’s data or b) s has not yet accessed any of c’s competitors’ data s can write to c’s data only if s can not read any other company’s sensitive data Mandatory security policy for UK Stock Exchange.
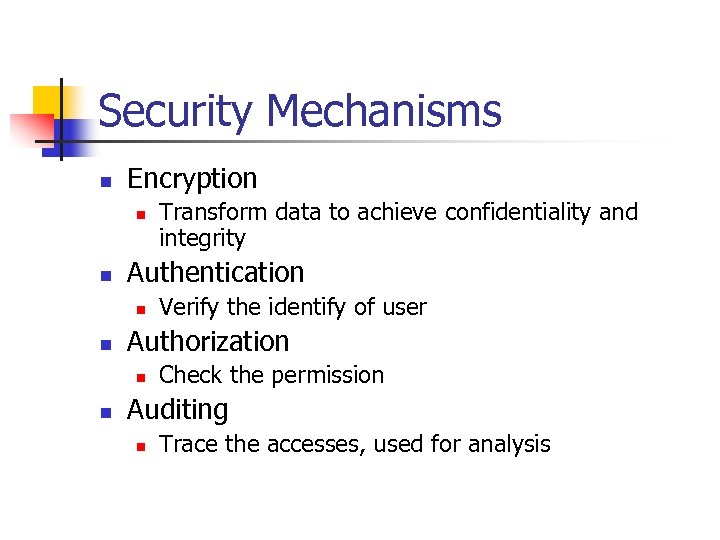 Security Mechanisms n Encryption n n Authentication n n Verify the identify of user Authorization n n Transform data to achieve confidentiality and integrity Check the permission Auditing n Trace the accesses, used for analysis
Security Mechanisms n Encryption n n Authentication n n Verify the identify of user Authorization n n Transform data to achieve confidentiality and integrity Check the permission Auditing n Trace the accesses, used for analysis
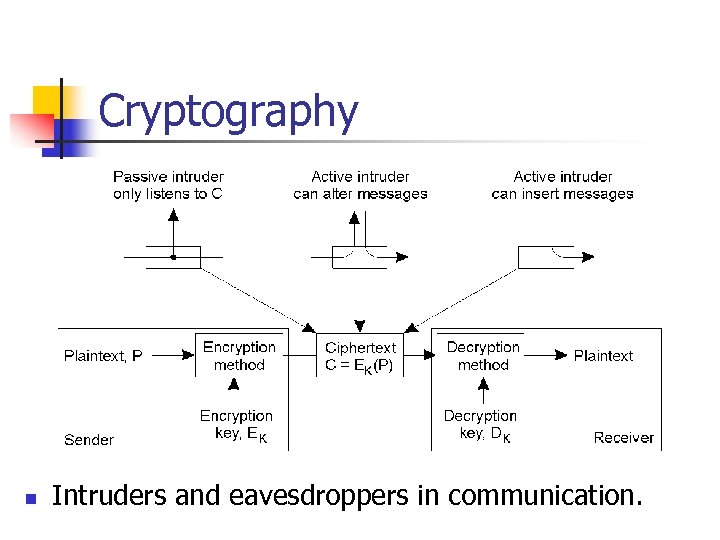 Cryptography n Intruders and eavesdroppers in communication.
Cryptography n Intruders and eavesdroppers in communication.
 Classifications n Symmetric cryptography: shared Key n n n Asymmetric cryptography: a pair of keys n n n P=DK(EK(P)) DES P=DKD(EKE(P)) RAS Hash function: one way function, not reversible n n h=H(m) MD 5
Classifications n Symmetric cryptography: shared Key n n n Asymmetric cryptography: a pair of keys n n n P=DK(EK(P)) DES P=DKD(EKE(P)) RAS Hash function: one way function, not reversible n n h=H(m) MD 5
 Notations Notation Description KA, B Secret key shared by A and B Public key of A Private key of A
Notations Notation Description KA, B Secret key shared by A and B Public key of A Private key of A
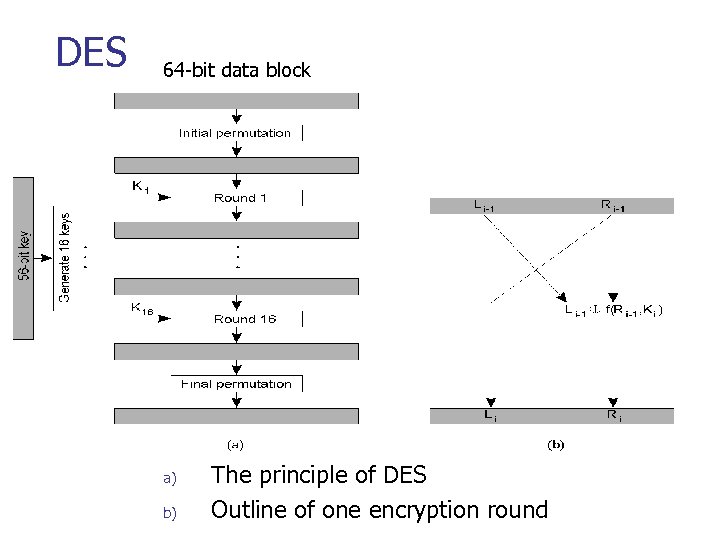 DES 64 -bit data block a) b) The principle of DES Outline of one encryption round
DES 64 -bit data block a) b) The principle of DES Outline of one encryption round
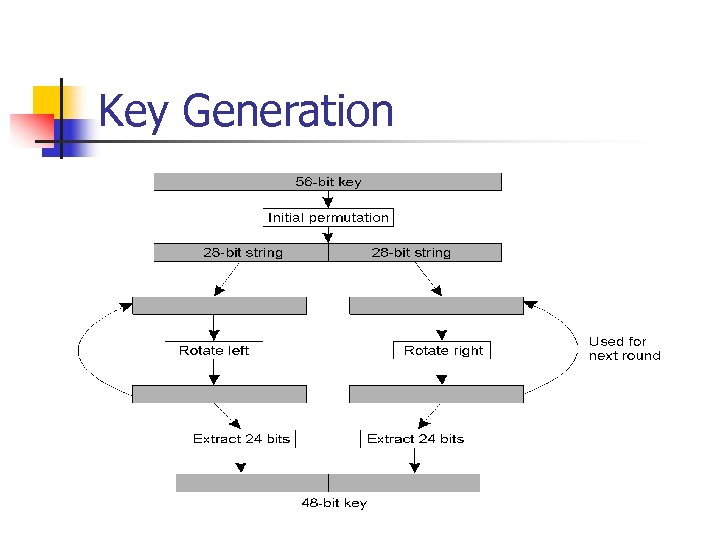 Key Generation
Key Generation
 Attacking DES n Cryptanalysis n n n Relies on nature of the encryption algorithm and additional knowledge of the general types of plain texts (frequencies of letters etc. ) Some samples of plain- and cipher texts Brute-force n Test every possible key on some cipher text until readable result be done in advance if key is not changed
Attacking DES n Cryptanalysis n n n Relies on nature of the encryption algorithm and additional knowledge of the general types of plain texts (frequencies of letters etc. ) Some samples of plain- and cipher texts Brute-force n Test every possible key on some cipher text until readable result be done in advance if key is not changed
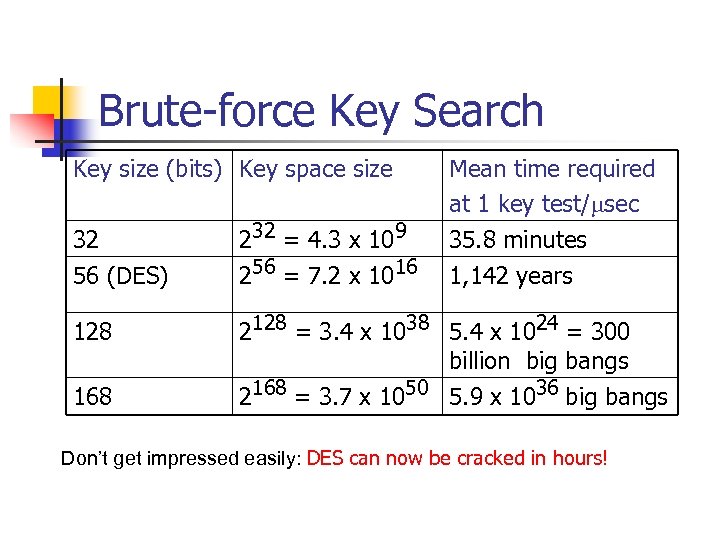 Brute-force Key Search Key size (bits) Key space size Mean time required at 1 key test/msec 32 232 = 4. 3 x 109 35. 8 minutes 56 (DES) 256 = 7. 2 x 1016 1, 142 years 128 2128 = 3. 4 x 1038 5. 4 x 1024 = 300 billion big bangs 2168 = 3. 7 x 1050 5. 9 x 1036 big bangs 168 Don’t get impressed easily: DES can now be cracked in hours!
Brute-force Key Search Key size (bits) Key space size Mean time required at 1 key test/msec 32 232 = 4. 3 x 109 35. 8 minutes 56 (DES) 256 = 7. 2 x 1016 1, 142 years 128 2128 = 3. 4 x 1038 5. 4 x 1024 = 300 billion big bangs 2168 = 3. 7 x 1050 5. 9 x 1036 big bangs 168 Don’t get impressed easily: DES can now be cracked in hours!
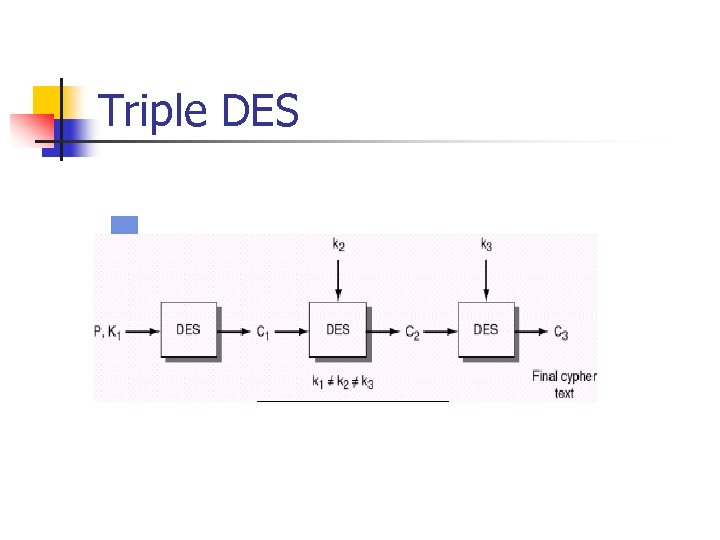 Triple DES
Triple DES
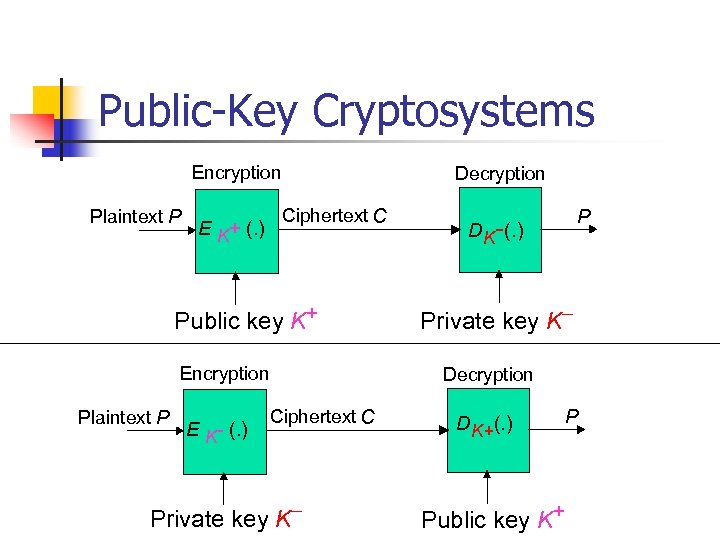 Public-Key Cryptosystems Encryption Plaintext P E K+ (. ) Decryption Ciphertext C Public key K+ Encryption Plaintext P E K- (. ) P DK-(. ) Private key KDecryption Ciphertext C Private key K- DK+(. ) P Public key K+
Public-Key Cryptosystems Encryption Plaintext P E K+ (. ) Decryption Ciphertext C Public key K+ Encryption Plaintext P E K- (. ) P DK-(. ) Private key KDecryption Ciphertext C Private key K- DK+(. ) P Public key K+
 Idea n Questions: n n 314159265358979 * 314159265358979=? 3912571506419387090594828508241 = ? *? Idea: Use easy algorithm for encryption. Use difficult algorithm for decryption A user picks a public key/private key pair n n publish the public key private key not published
Idea n Questions: n n 314159265358979 * 314159265358979=? 3912571506419387090594828508241 = ? *? Idea: Use easy algorithm for encryption. Use difficult algorithm for decryption A user picks a public key/private key pair n n publish the public key private key not published
 RSA: Rivest, Shamir and Adleman Foundation: no known method that can efficiently find the prime factors of large numbers. n n In RSA, private and public keys are constructed from very large prime numbers (consisting of hundreds of decimal digits) Four steps to construct the keys: n n n Choose two very large prime numbers, p and q Compute n = p x q and z = (p – 1) x (q – 1) Choose a number d that is relatively prime to z Compute the number e such that e x d = 1 mod z
RSA: Rivest, Shamir and Adleman Foundation: no known method that can efficiently find the prime factors of large numbers. n n In RSA, private and public keys are constructed from very large prime numbers (consisting of hundreds of decimal digits) Four steps to construct the keys: n n n Choose two very large prime numbers, p and q Compute n = p x q and z = (p – 1) x (q – 1) Choose a number d that is relatively prime to z Compute the number e such that e x d = 1 mod z
 How It Works? n How it works? n n n Encryption: C = Pe mod n Decryption: P = Cd mod n K+ = (e, n), K- = (d, n) The intruder needs to factor n into p and q to crack the code. Higher cost of computation. Problems: n n n 1) Is the number of primes infinite? Yes! 2) Are they scarce? Yes! 4% of the first 25 billion numbers. And the percentage drops as the numbers get bigger. Implication: it is tricky to propose a new prime number. E. g. , is 687, 532, 127 a prime?
How It Works? n How it works? n n n Encryption: C = Pe mod n Decryption: P = Cd mod n K+ = (e, n), K- = (d, n) The intruder needs to factor n into p and q to crack the code. Higher cost of computation. Problems: n n n 1) Is the number of primes infinite? Yes! 2) Are they scarce? Yes! 4% of the first 25 billion numbers. And the percentage drops as the numbers get bigger. Implication: it is tricky to propose a new prime number. E. g. , is 687, 532, 127 a prime?
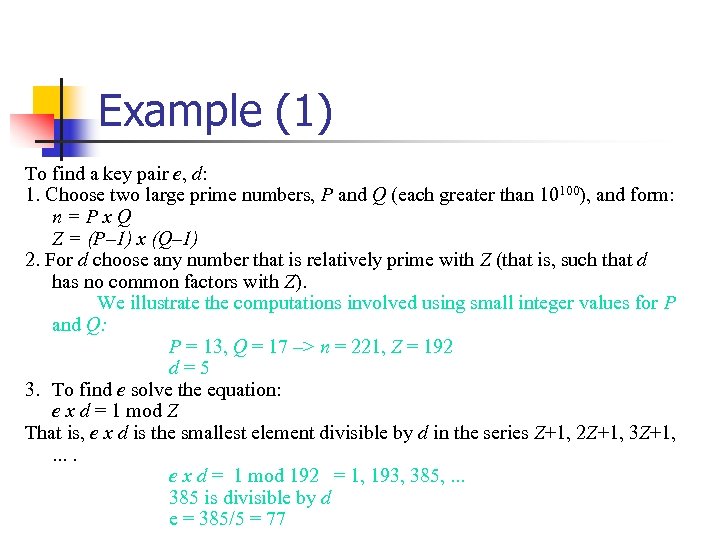 Example (1) To find a key pair e, d: 1. Choose two large prime numbers, P and Q (each greater than 10100), and form: n=Px. Q Z = (P– 1) x (Q– 1) 2. For d choose any number that is relatively prime with Z (that is, such that d has no common factors with Z). We illustrate the computations involved using small integer values for P and Q: P = 13, Q = 17 –> n = 221, Z = 192 d=5 3. To find e solve the equation: e x d = 1 mod Z That is, e x d is the smallest element divisible by d in the series Z+1, 2 Z+1, 3 Z+1, . . e x d = 1 mod 192 = 1, 193, 385, . . . 385 is divisible by d e = 385/5 = 77
Example (1) To find a key pair e, d: 1. Choose two large prime numbers, P and Q (each greater than 10100), and form: n=Px. Q Z = (P– 1) x (Q– 1) 2. For d choose any number that is relatively prime with Z (that is, such that d has no common factors with Z). We illustrate the computations involved using small integer values for P and Q: P = 13, Q = 17 –> n = 221, Z = 192 d=5 3. To find e solve the equation: e x d = 1 mod Z That is, e x d is the smallest element divisible by d in the series Z+1, 2 Z+1, 3 Z+1, . . e x d = 1 mod 192 = 1, 193, 385, . . . 385 is divisible by d e = 385/5 = 77
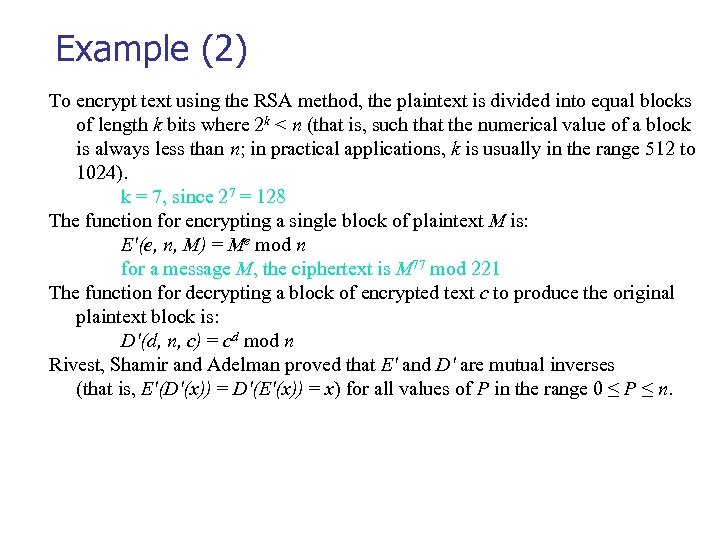 Example (2) To encrypt text using the RSA method, the plaintext is divided into equal blocks of length k bits where 2 k < n (that is, such that the numerical value of a block is always less than n; in practical applications, k is usually in the range 512 to 1024). k = 7, since 27 = 128 The function for encrypting a single block of plaintext M is: E'(e, n, M) = Me mod n for a message M, the ciphertext is M 77 mod 221 The function for decrypting a block of encrypted text c to produce the original plaintext block is: D'(d, n, c) = cd mod n Rivest, Shamir and Adelman proved that E' and D' are mutual inverses (that is, E'(D'(x)) = D'(E'(x)) = x) for all values of P in the range 0 ≤ P ≤ n.
Example (2) To encrypt text using the RSA method, the plaintext is divided into equal blocks of length k bits where 2 k < n (that is, such that the numerical value of a block is always less than n; in practical applications, k is usually in the range 512 to 1024). k = 7, since 27 = 128 The function for encrypting a single block of plaintext M is: E'(e, n, M) = Me mod n for a message M, the ciphertext is M 77 mod 221 The function for decrypting a block of encrypted text c to produce the original plaintext block is: D'(d, n, c) = cd mod n Rivest, Shamir and Adelman proved that E' and D' are mutual inverses (that is, E'(D'(x)) = D'(E'(x)) = x) for all values of P in the range 0 ≤ P ≤ n.
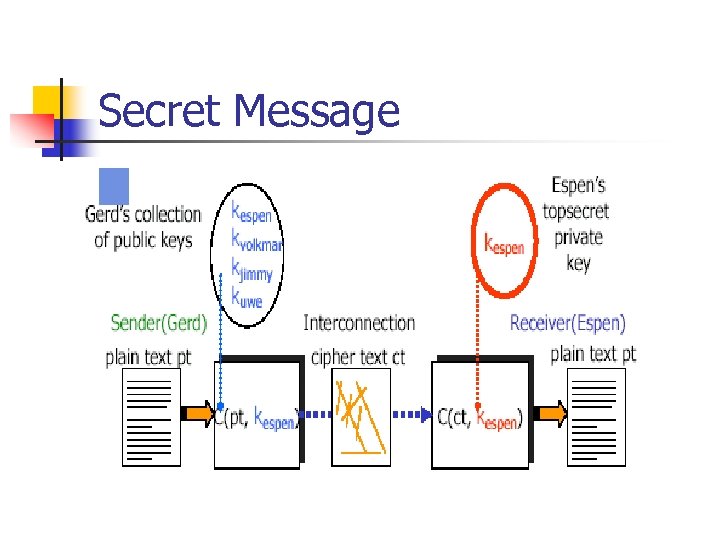 Secret Message
Secret Message
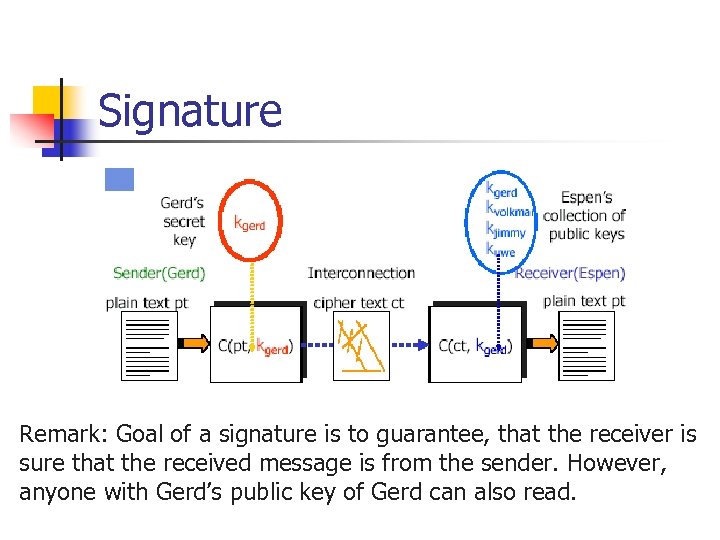 Signature Remark: Goal of a signature is to guarantee, that the receiver is sure that the received message is from the sender. However, anyone with Gerd’s public key of Gerd can also read.
Signature Remark: Goal of a signature is to guarantee, that the receiver is sure that the received message is from the sender. However, anyone with Gerd’s public key of Gerd can also read.
 Message Digest n Cryptographic checksum n n One-way function n n Just as a regular checksum protects the receiver from accidental changes to the message , a cryptographic checksum protects the receiver from malicious changes. Given a cryptographic checksum for a msg, it is virtually impossible to figure out what msg produced that checksum; it is not computationally feasible to find two msg that hash to the same cryptographic checksum. Relevance n If you are given a checksum for a message & you are able to compute exactly the same checksum for that message, then it is highly likely this message produced the checksum you were given.
Message Digest n Cryptographic checksum n n One-way function n n Just as a regular checksum protects the receiver from accidental changes to the message , a cryptographic checksum protects the receiver from malicious changes. Given a cryptographic checksum for a msg, it is virtually impossible to figure out what msg produced that checksum; it is not computationally feasible to find two msg that hash to the same cryptographic checksum. Relevance n If you are given a checksum for a message & you are able to compute exactly the same checksum for that message, then it is highly likely this message produced the checksum you were given.
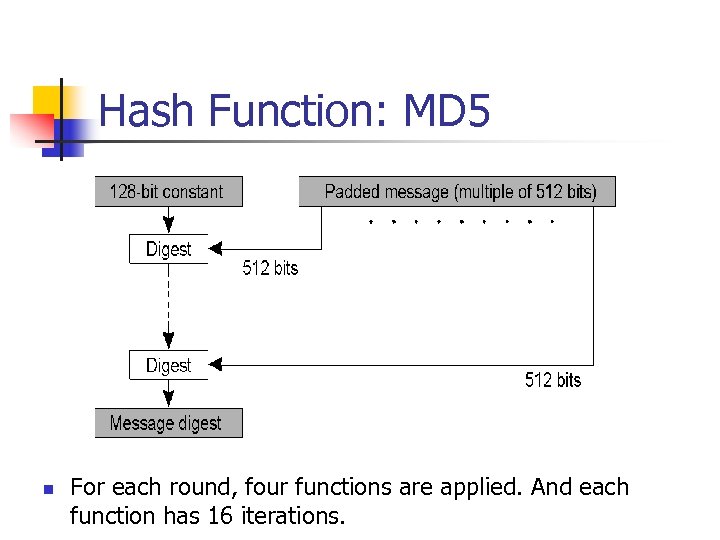 Hash Function: MD 5 n For each round, four functions are applied. And each function has 16 iterations.
Hash Function: MD 5 n For each round, four functions are applied. And each function has 16 iterations.
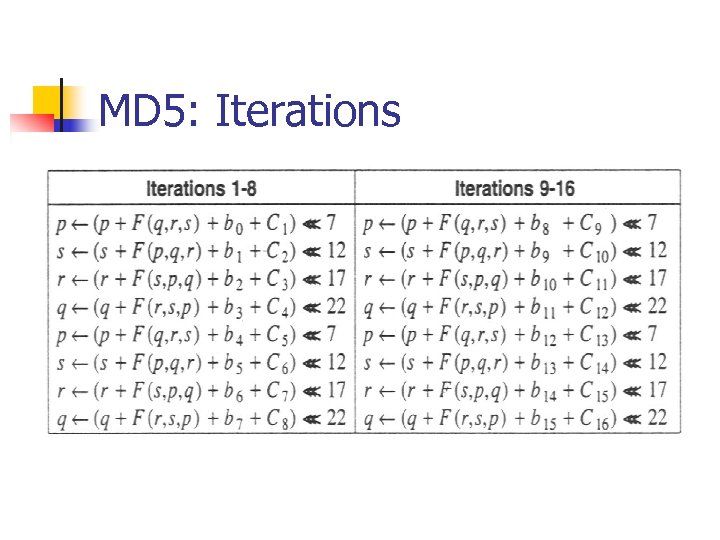 MD 5: Iterations
MD 5: Iterations
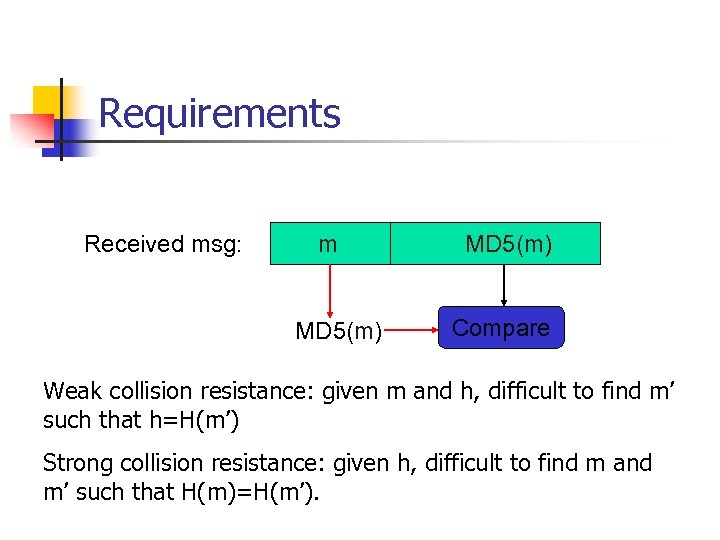 Requirements Received msg: m MD 5(m) Compare Weak collision resistance: given m and h, difficult to find m’ such that h=H(m’) Strong collision resistance: given h, difficult to find m and m’ such that H(m)=H(m’).
Requirements Received msg: m MD 5(m) Compare Weak collision resistance: given m and h, difficult to find m’ such that h=H(m’) Strong collision resistance: given h, difficult to find m and m’ such that H(m)=H(m’).
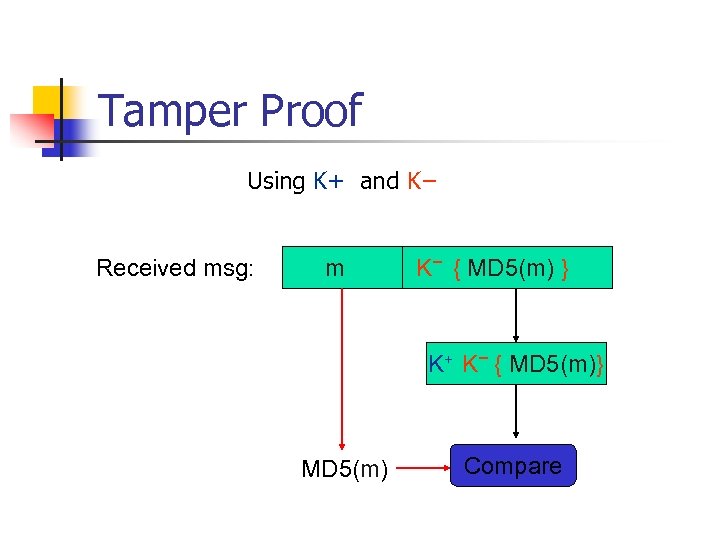 Tamper Proof Using K+ and K− Received msg: m K− { MD 5(m) } K+ K− { MD 5(m)} MD 5(m) Compare
Tamper Proof Using K+ and K− Received msg: m K− { MD 5(m) } K+ K− { MD 5(m)} MD 5(m) Compare
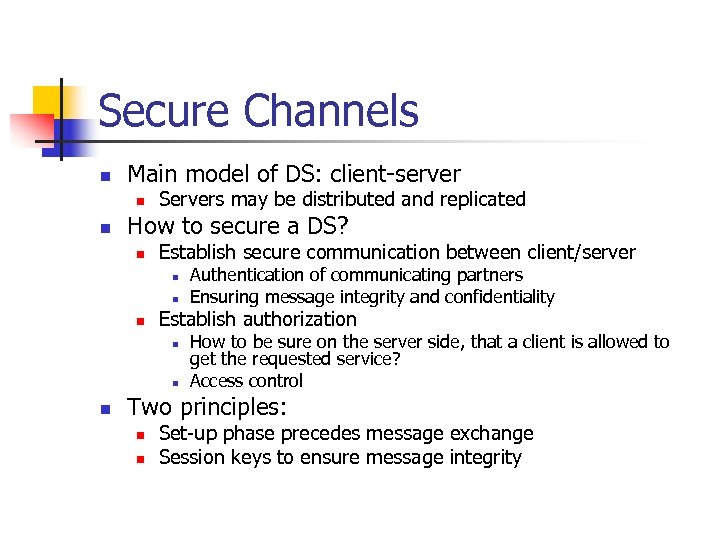 Secure Channels n Main model of DS: client-server n n Servers may be distributed and replicated How to secure a DS? n Establish secure communication between client/server n n n Establish authorization n Authentication of communicating partners Ensuring message integrity and confidentiality How to be sure on the server side, that a client is allowed to get the requested service? Access control Two principles: n n Set-up phase precedes message exchange Session keys to ensure message integrity
Secure Channels n Main model of DS: client-server n n Servers may be distributed and replicated How to secure a DS? n Establish secure communication between client/server n n n Establish authorization n Authentication of communicating partners Ensuring message integrity and confidentiality How to be sure on the server side, that a client is allowed to get the requested service? Access control Two principles: n n Set-up phase precedes message exchange Session keys to ensure message integrity
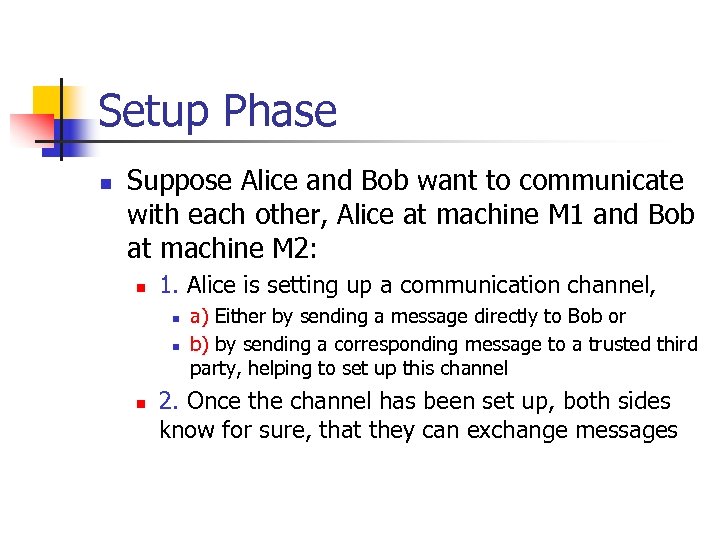 Setup Phase n Suppose Alice and Bob want to communicate with each other, Alice at machine M 1 and Bob at machine M 2: n 1. Alice is setting up a communication channel, n n n a) Either by sending a message directly to Bob or b) by sending a corresponding message to a trusted third party, helping to set up this channel 2. Once the channel has been set up, both sides know for sure, that they can exchange messages
Setup Phase n Suppose Alice and Bob want to communicate with each other, Alice at machine M 1 and Bob at machine M 2: n 1. Alice is setting up a communication channel, n n n a) Either by sending a message directly to Bob or b) by sending a corresponding message to a trusted third party, helping to set up this channel 2. Once the channel has been set up, both sides know for sure, that they can exchange messages
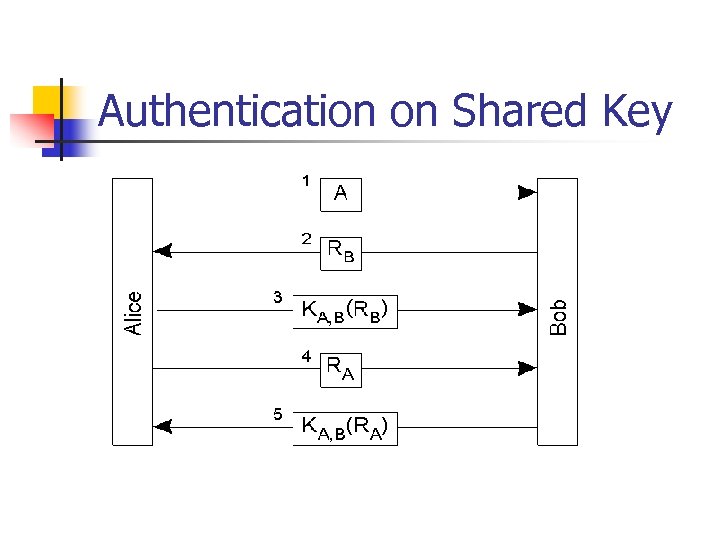 Authentication on Shared Key
Authentication on Shared Key
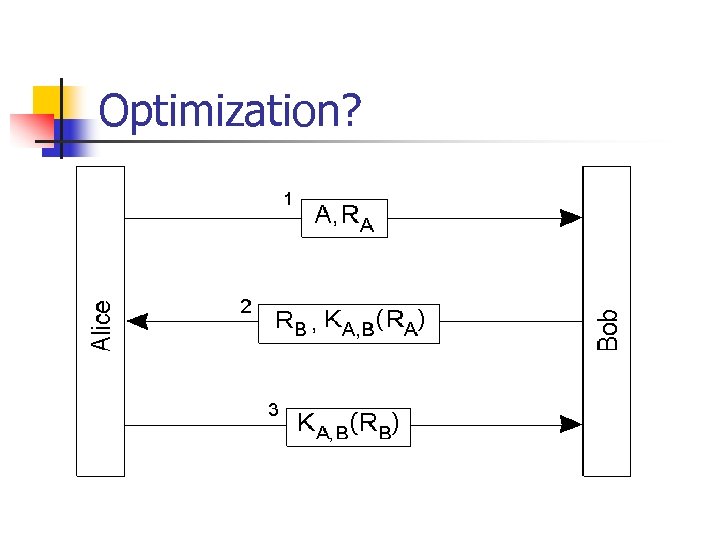 Optimization?
Optimization?
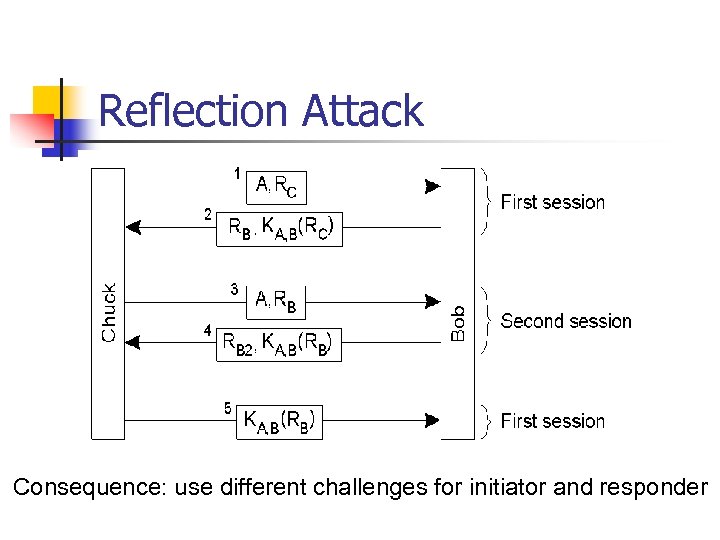 Reflection Attack Consequence: use different challenges for initiator and responder
Reflection Attack Consequence: use different challenges for initiator and responder
 Scalability of Session Keys n Suppose we have N hosts each sharing a secret key with each of the other N-1 hosts n n n DS has (N-1)*N/2 secret session keys and each host has manage (N-1) session keys For large N #session keys will be a problem Instead you can install a trusted key distribution center KDC on one of the nodes of the DS
Scalability of Session Keys n Suppose we have N hosts each sharing a secret key with each of the other N-1 hosts n n n DS has (N-1)*N/2 secret session keys and each host has manage (N-1) session keys For large N #session keys will be a problem Instead you can install a trusted key distribution center KDC on one of the nodes of the DS
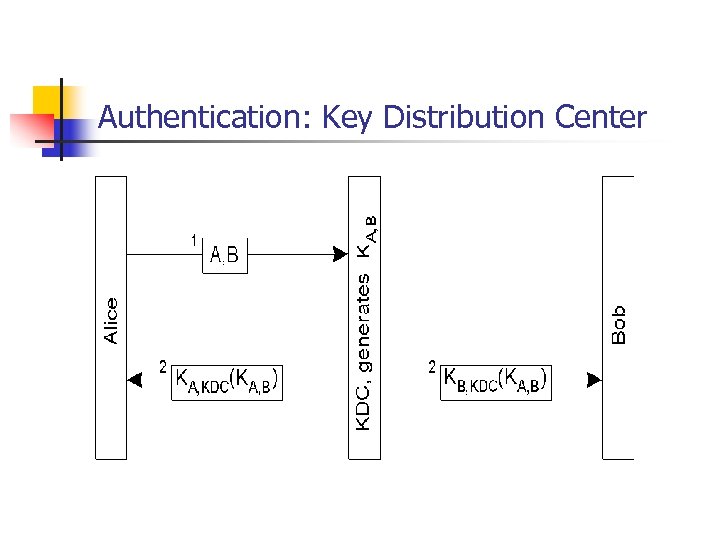 Authentication: Key Distribution Center
Authentication: Key Distribution Center
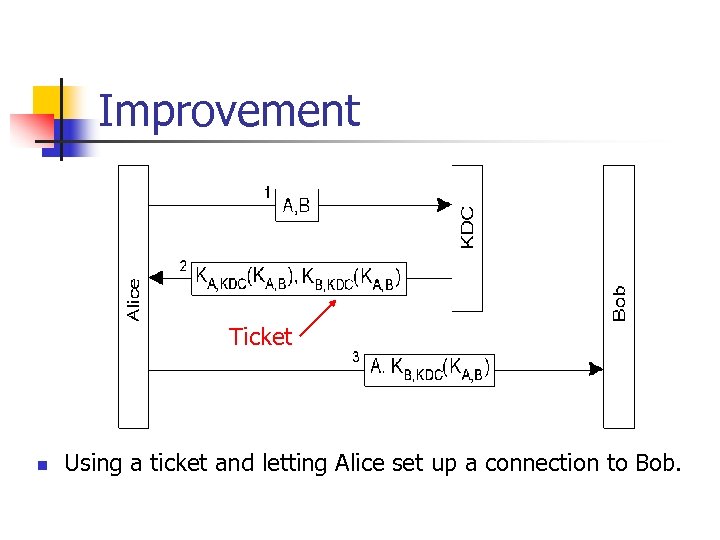 Improvement Ticket n Using a ticket and letting Alice set up a connection to Bob.
Improvement Ticket n Using a ticket and letting Alice set up a connection to Bob.
 Needham-Schroeder Authentication Protocol n In early distributed systems (1974 -84) it was difficult to protect the servers n n E. g. against masquerading attacks on a file server because there was no mechanism for authenticating the origins of requests public-key cryptography was not yet available or practical n n n computers too slow for trap-door calculations RSA algorithm not available until 1978 Needham and Schroeder therefore developed an authentication and key-distribution protocol for use in a local network n n An early example of the care required to design a safe security protocol Introduced several design ideas including the use of nonces.
Needham-Schroeder Authentication Protocol n In early distributed systems (1974 -84) it was difficult to protect the servers n n E. g. against masquerading attacks on a file server because there was no mechanism for authenticating the origins of requests public-key cryptography was not yet available or practical n n n computers too slow for trap-door calculations RSA algorithm not available until 1978 Needham and Schroeder therefore developed an authentication and key-distribution protocol for use in a local network n n An early example of the care required to design a safe security protocol Introduced several design ideas including the use of nonces.
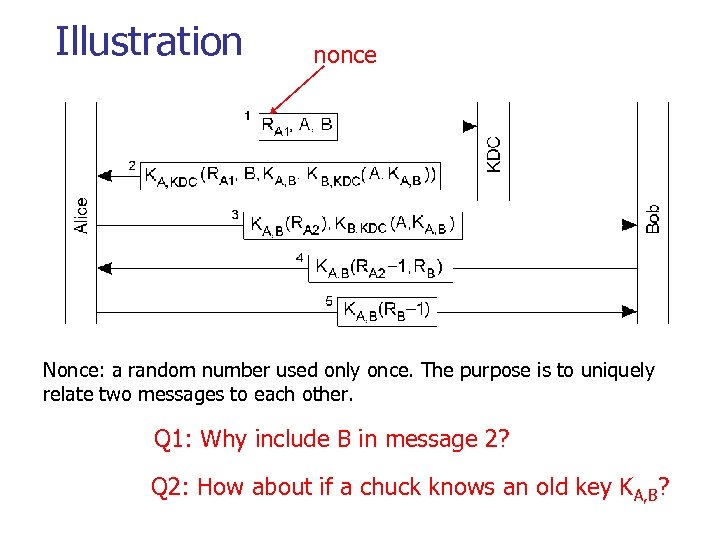 Illustration nonce Nonce: a random number used only once. The purpose is to uniquely relate two messages to each other. Q 1: Why include B in message 2? Q 2: How about if a chuck knows an old key KA, B?
Illustration nonce Nonce: a random number used only once. The purpose is to uniquely relate two messages to each other. Q 1: Why include B in message 2? Q 2: How about if a chuck knows an old key KA, B?
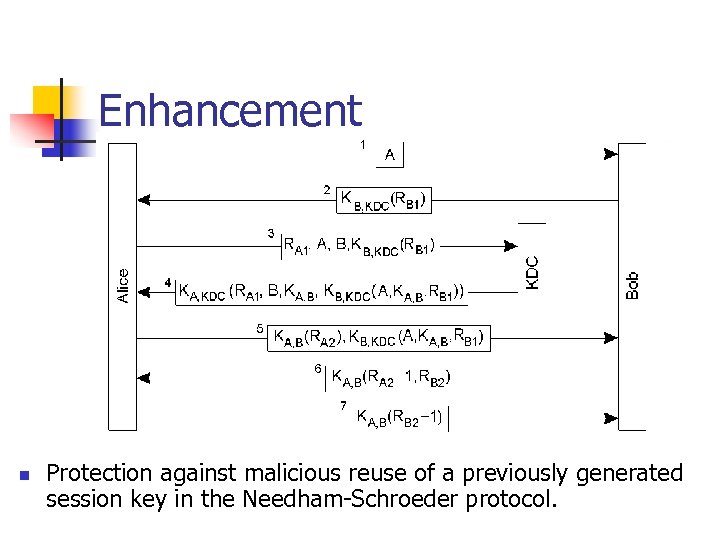 Enhancement n Protection against malicious reuse of a previously generated session key in the Needham-Schroeder protocol.
Enhancement n Protection against malicious reuse of a previously generated session key in the Needham-Schroeder protocol.
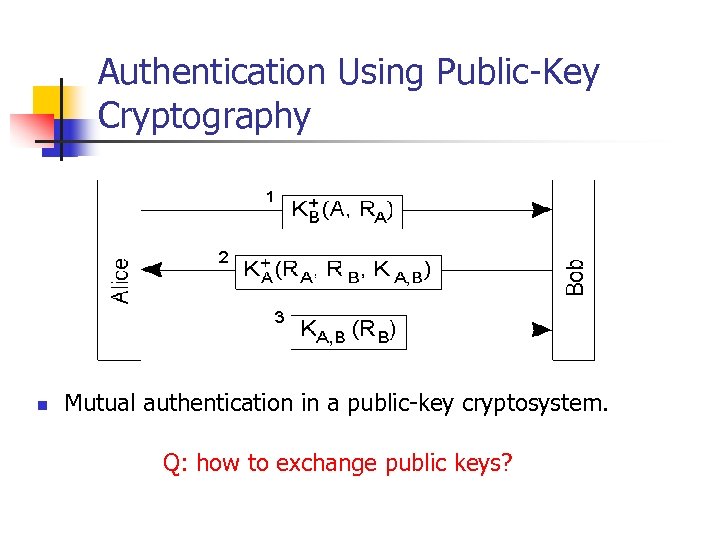 Authentication Using Public-Key Cryptography n Mutual authentication in a public-key cryptosystem. Q: how to exchange public keys?
Authentication Using Public-Key Cryptography n Mutual authentication in a public-key cryptosystem. Q: how to exchange public keys?
 Message Integrity & Confidentiality
Message Integrity & Confidentiality
 Digital Signature n Goals: n n To authenticate stored document files as well as messages To protect against forgery To prevent the signer from repudiating a signed document (denying their responsibility) Encryption of a document in a secret key constitutes a signature - impossible for others to perform without knowledge of the key strong authentication of document strong protection against forgery weak against repudiation (signer could claim key was compromised)
Digital Signature n Goals: n n To authenticate stored document files as well as messages To protect against forgery To prevent the signer from repudiating a signed document (denying their responsibility) Encryption of a document in a secret key constitutes a signature - impossible for others to perform without knowledge of the key strong authentication of document strong protection against forgery weak against repudiation (signer could claim key was compromised)
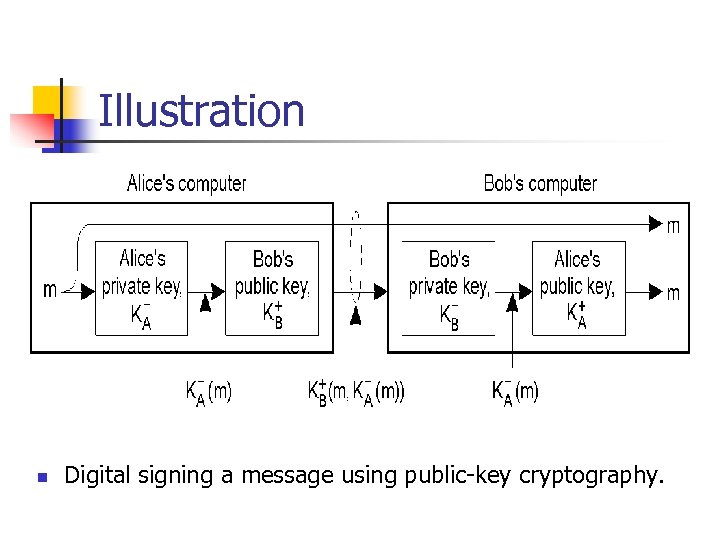 Illustration n Digital signing a message using public-key cryptography.
Illustration n Digital signing a message using public-key cryptography.
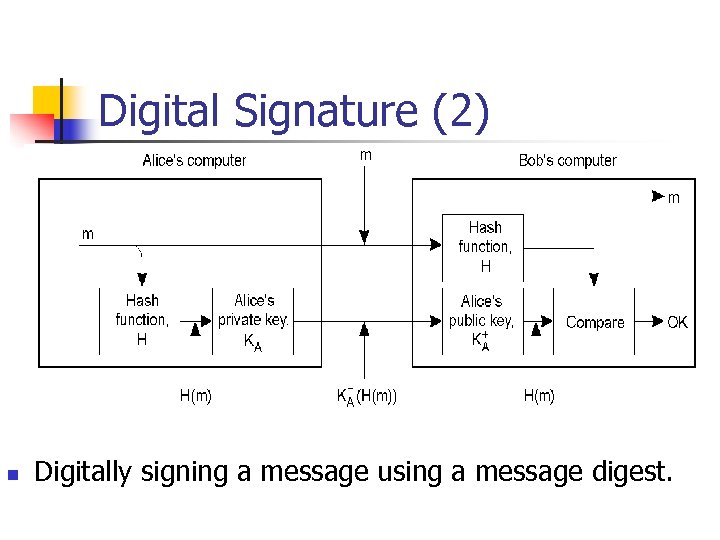 Digital Signature (2) n Digitally signing a message using a message digest.
Digital Signature (2) n Digitally signing a message using a message digest.
 Certificate Authority (CA) n Verify the owner of a public key n n CA are organized in a hierarchy. n n n Maintain the (owner, public_key) by a certificate authority For each merchant, it issues a certificate. The names of CA are widely known, e. g. Verisign. Chain of trust n Certified by a higher-level CA: the central authority: IPRA
Certificate Authority (CA) n Verify the owner of a public key n n CA are organized in a hierarchy. n n n Maintain the (owner, public_key) by a certificate authority For each merchant, it issues a certificate. The names of CA are widely known, e. g. Verisign. Chain of trust n Certified by a higher-level CA: the central authority: IPRA
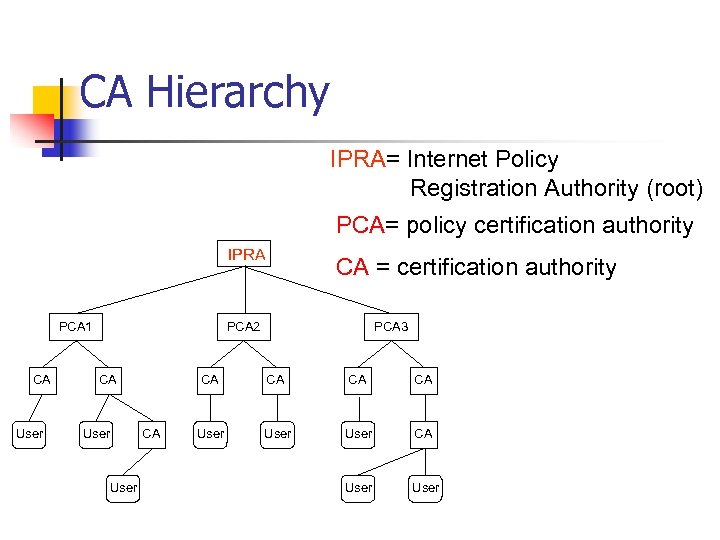 CA Hierarchy IPRA= Internet Policy Registration Authority (root) PCA= policy certification authority IPRA PCA 1 CA User CA = certification authority PCA 2 CA User PCA 3 CA CA CA User CA User
CA Hierarchy IPRA= Internet Policy Registration Authority (root) PCA= policy certification authority IPRA PCA 1 CA User CA = certification authority PCA 2 CA User PCA 3 CA CA CA User CA User
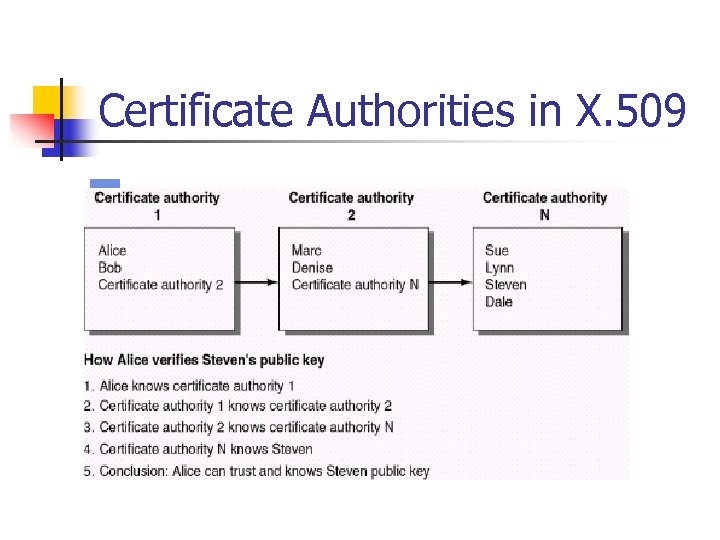 Certificate Authorities in X. 509
Certificate Authorities in X. 509
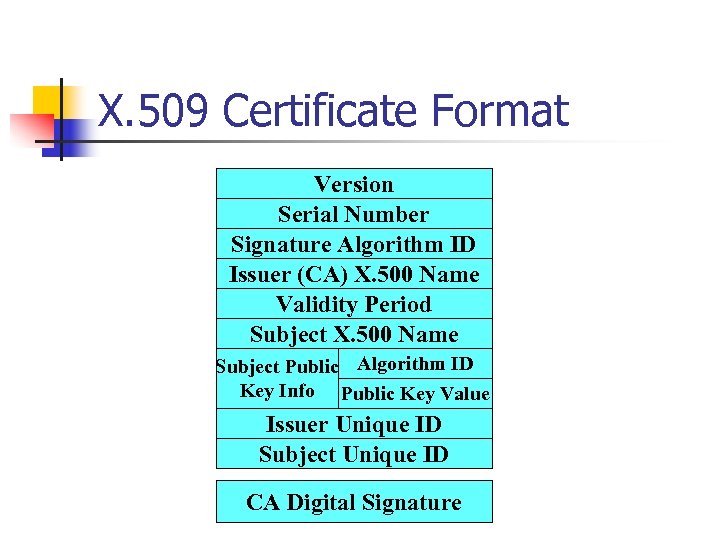 X. 509 Certificate Format Version Serial Number Signature Algorithm ID Issuer (CA) X. 500 Name Validity Period Subject X. 500 Name Subject Public Algorithm ID Key Info Public Key Value Issuer Unique ID Subject Unique ID CA Digital Signature
X. 509 Certificate Format Version Serial Number Signature Algorithm ID Issuer (CA) X. 500 Name Validity Period Subject X. 500 Name Subject Public Algorithm ID Key Info Public Key Value Issuer Unique ID Subject Unique ID CA Digital Signature
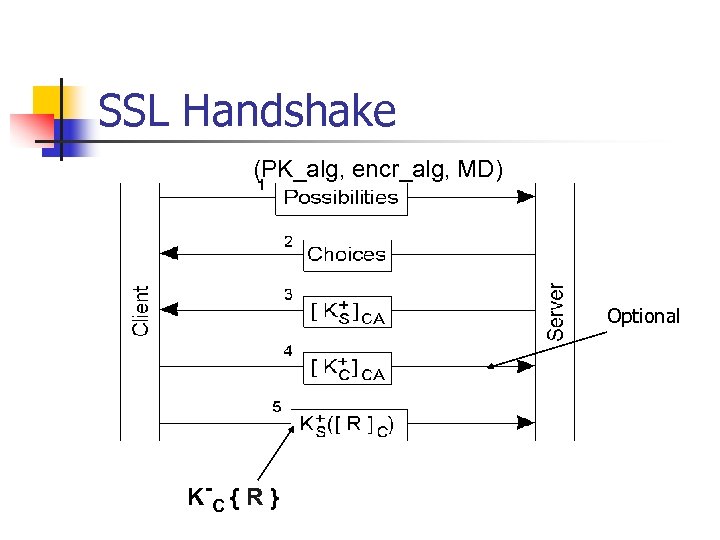 SSL Handshake (PK_alg, encr_alg, MD) Optional K -C { R }
SSL Handshake (PK_alg, encr_alg, MD) Optional K -C { R }
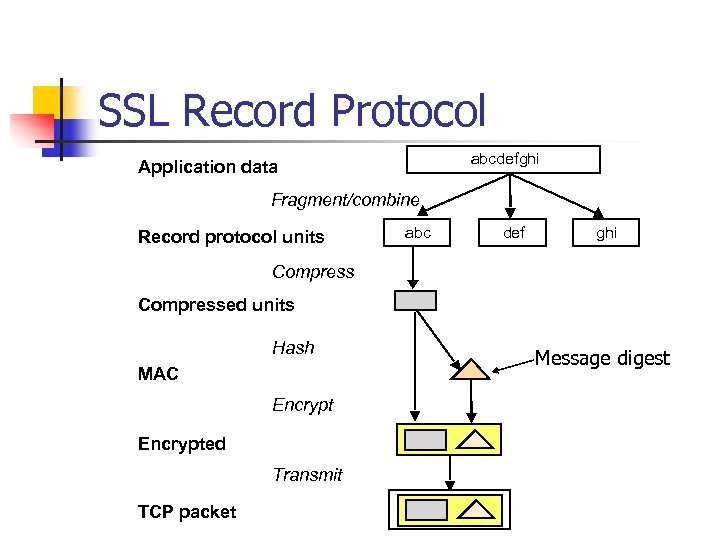 SSL Record Protocol abcdefghi Application data Fragment/combine Record protocol units abc def ghi Compressed units Hash MAC Encrypted Transmit TCP packet Message digest
SSL Record Protocol abcdefghi Application data Fragment/combine Record protocol units abc def ghi Compressed units Hash MAC Encrypted Transmit TCP packet Message digest
 Confidential Group Communication n n Goal: secure channels between each pair of nodes Share one key? Share a key between each pair of nodes? Each node has its own private key but all the nodes share a public key.
Confidential Group Communication n n Goal: secure channels between each pair of nodes Share one key? Share a key between each pair of nodes? Each node has its own private key but all the nodes share a public key.
 Access Control
Access Control
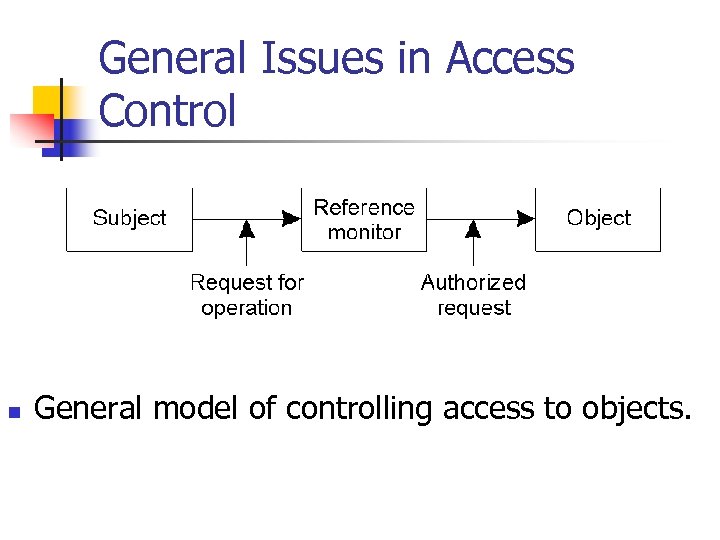 General Issues in Access Control n General model of controlling access to objects.
General Issues in Access Control n General model of controlling access to objects.
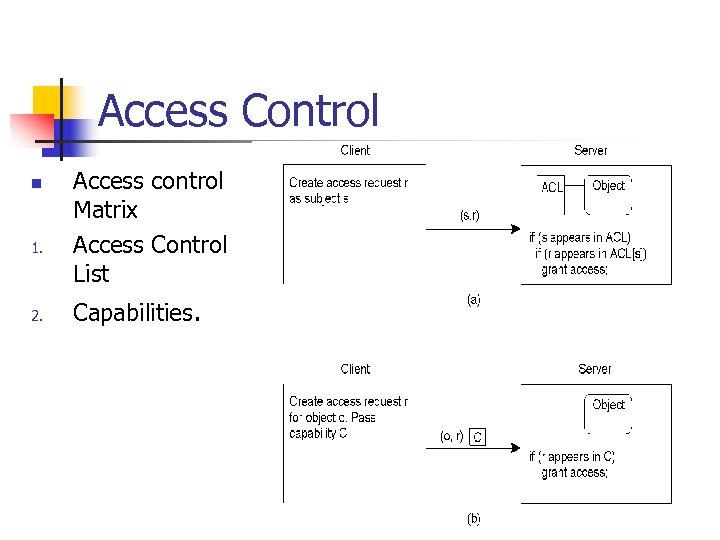 Access Control n 1. 2. Access control Matrix Access Control List Capabilities.
Access Control n 1. 2. Access control Matrix Access Control List Capabilities.
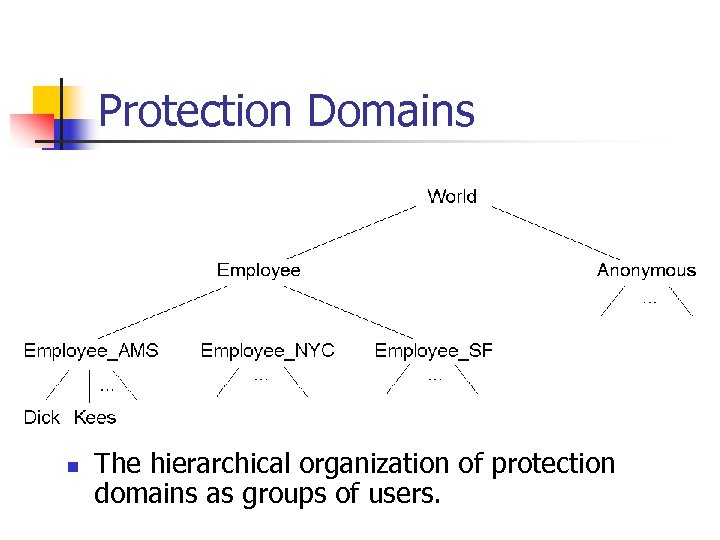 Protection Domains n The hierarchical organization of protection domains as groups of users.
Protection Domains n The hierarchical organization of protection domains as groups of users.
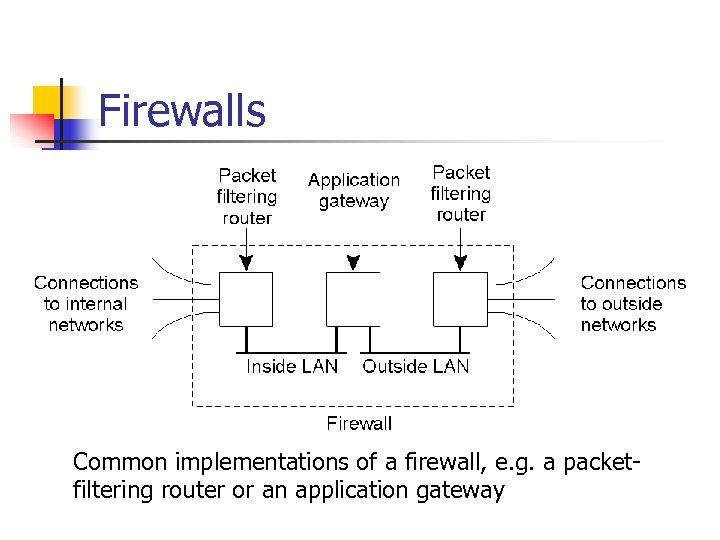 Firewalls Common implementations of a firewall, e. g. a packetfiltering router or an application gateway
Firewalls Common implementations of a firewall, e. g. a packetfiltering router or an application gateway
 Firewall Solutions n Definition - hardware &/or software components that restrict access between a restricted network & the Internet or between networks Logically - a separator, restricter, analyzer n Rarely a single object n n Restricts people to entering at a controlled point Prevents attackers from getting close to other defenses (host controls) Restricts people to leaving at a controlled point
Firewall Solutions n Definition - hardware &/or software components that restrict access between a restricted network & the Internet or between networks Logically - a separator, restricter, analyzer n Rarely a single object n n Restricts people to entering at a controlled point Prevents attackers from getting close to other defenses (host controls) Restricts people to leaving at a controlled point
 Firewall Capabilities n n Focus security decisions - single point to leverage control Enforce security policy -minimize exceptions Log Internet activity - analysis Limit exposure - separate sensitive areas of one network from another or outside world
Firewall Capabilities n n Focus security decisions - single point to leverage control Enforce security policy -minimize exceptions Log Internet activity - analysis Limit exposure - separate sensitive areas of one network from another or outside world
 Firewall Limitations n Can’t protect against malicious insiders n connections that don’t go through it n new threats n viruses n n scans for source & destination addresses & port numbers, not details of data
Firewall Limitations n Can’t protect against malicious insiders n connections that don’t go through it n new threats n viruses n n scans for source & destination addresses & port numbers, not details of data
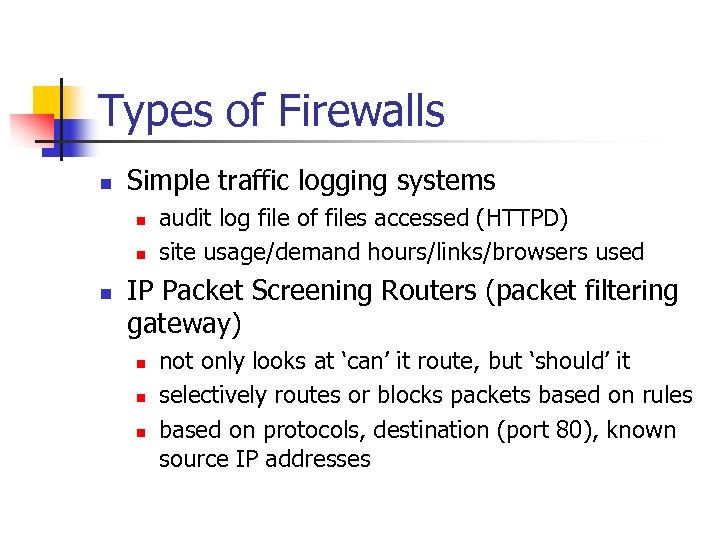 Types of Firewalls n Simple traffic logging systems n n n audit log file of files accessed (HTTPD) site usage/demand hours/links/browsers used IP Packet Screening Routers (packet filtering gateway) n not only looks at ‘can’ it route, but ‘should’ it selectively routes or blocks packets based on rules based on protocols, destination (port 80), known source IP addresses
Types of Firewalls n Simple traffic logging systems n n n audit log file of files accessed (HTTPD) site usage/demand hours/links/browsers used IP Packet Screening Routers (packet filtering gateway) n not only looks at ‘can’ it route, but ‘should’ it selectively routes or blocks packets based on rules based on protocols, destination (port 80), known source IP addresses
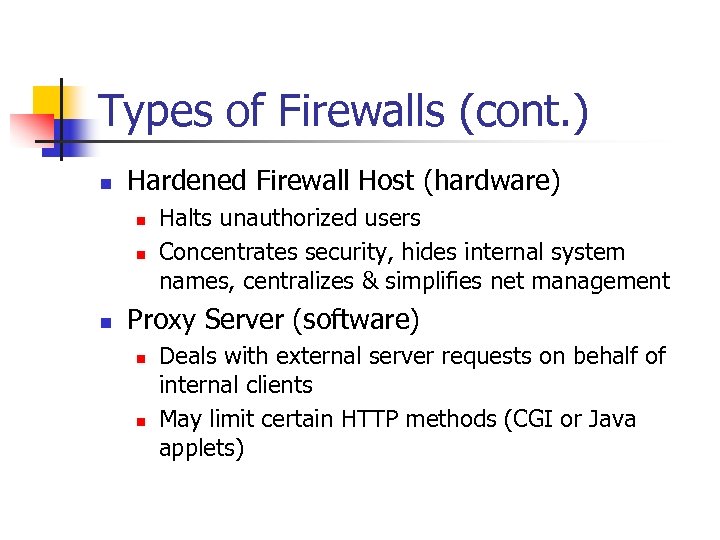 Types of Firewalls (cont. ) n Hardened Firewall Host (hardware) n n n Halts unauthorized users Concentrates security, hides internal system names, centralizes & simplifies net management Proxy Server (software) n n Deals with external server requests on behalf of internal clients May limit certain HTTP methods (CGI or Java applets)
Types of Firewalls (cont. ) n Hardened Firewall Host (hardware) n n n Halts unauthorized users Concentrates security, hides internal system names, centralizes & simplifies net management Proxy Server (software) n n Deals with external server requests on behalf of internal clients May limit certain HTTP methods (CGI or Java applets)
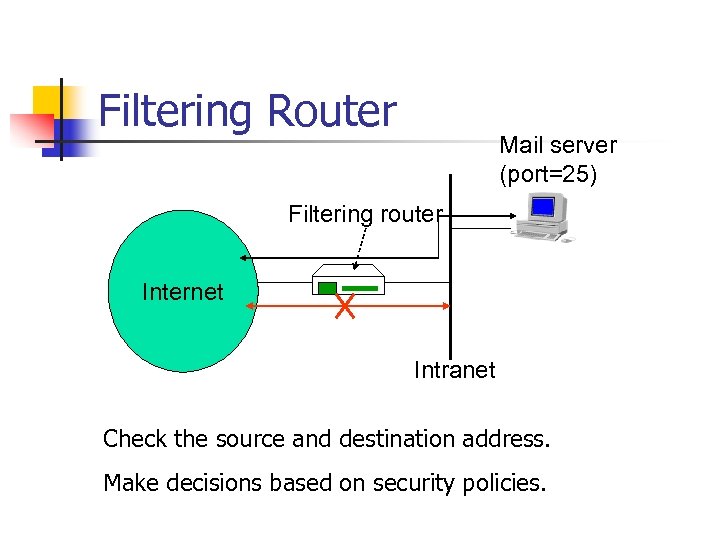 Filtering Router Mail server (port=25) Filtering router Internet Intranet Check the source and destination address. Make decisions based on security policies.
Filtering Router Mail server (port=25) Filtering router Internet Intranet Check the source and destination address. Make decisions based on security policies.
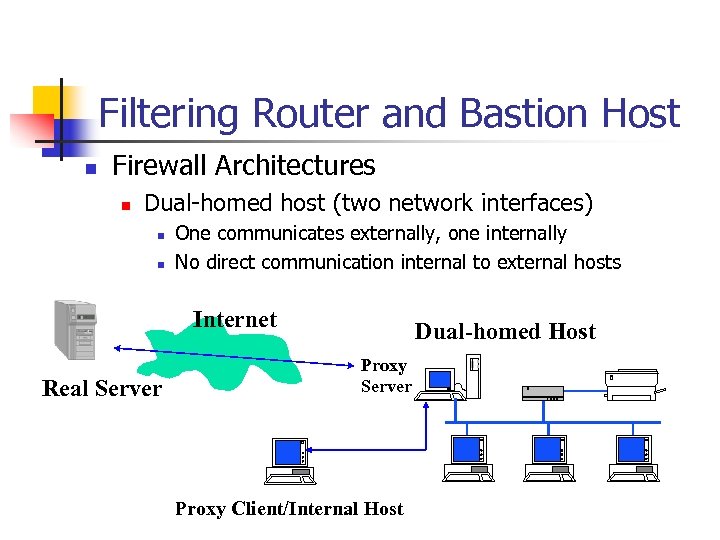 Filtering Router and Bastion Host n Firewall Architectures n Dual-homed host (two network interfaces) n n One communicates externally, one internally No direct communication internal to external hosts Internet Real Server Dual-homed Host Proxy Server Proxy Client/Internal Host
Filtering Router and Bastion Host n Firewall Architectures n Dual-homed host (two network interfaces) n n One communicates externally, one internally No direct communication internal to external hosts Internet Real Server Dual-homed Host Proxy Server Proxy Client/Internal Host
 Advantages n n All accesses can be logged Reduce the number of Internet connections by making it a caching proxy Does not reveal the names and addresses of actual clients inside But: slow down page downloading by an order of magnitude.
Advantages n n All accesses can be logged Reduce the number of Internet connections by making it a caching proxy Does not reveal the names and addresses of actual clients inside But: slow down page downloading by an order of magnitude.
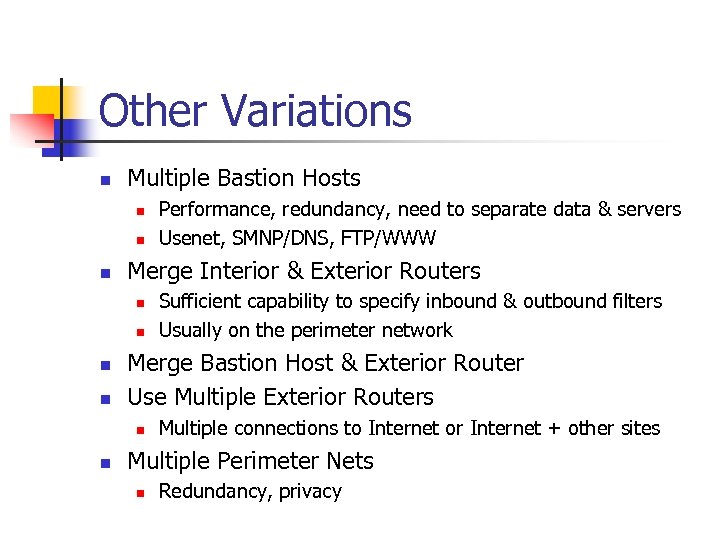 Other Variations n Multiple Bastion Hosts n n n Merge Interior & Exterior Routers n n Sufficient capability to specify inbound & outbound filters Usually on the perimeter network Merge Bastion Host & Exterior Router Use Multiple Exterior Routers n n Performance, redundancy, need to separate data & servers Usenet, SMNP/DNS, FTP/WWW Multiple connections to Internet or Internet + other sites Multiple Perimeter Nets n Redundancy, privacy
Other Variations n Multiple Bastion Hosts n n n Merge Interior & Exterior Routers n n Sufficient capability to specify inbound & outbound filters Usually on the perimeter network Merge Bastion Host & Exterior Router Use Multiple Exterior Routers n n Performance, redundancy, need to separate data & servers Usenet, SMNP/DNS, FTP/WWW Multiple connections to Internet or Internet + other sites Multiple Perimeter Nets n Redundancy, privacy
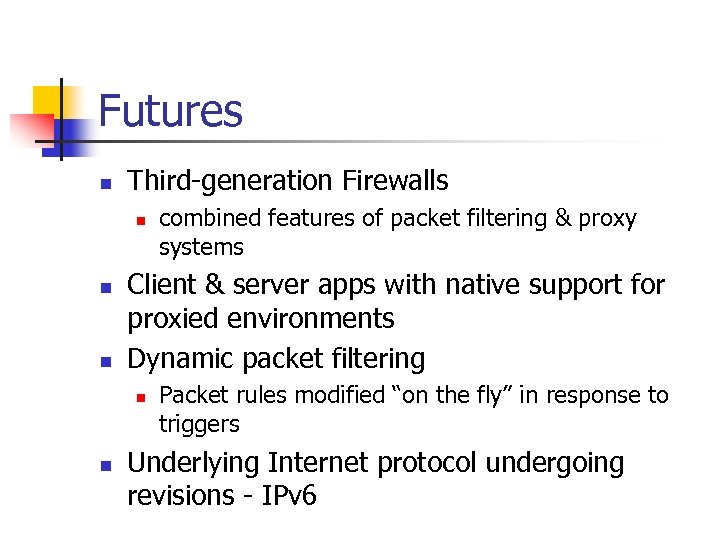 Futures n Third-generation Firewalls n n n Client & server apps with native support for proxied environments Dynamic packet filtering n n combined features of packet filtering & proxy systems Packet rules modified “on the fly” in response to triggers Underlying Internet protocol undergoing revisions - IPv 6
Futures n Third-generation Firewalls n n n Client & server apps with native support for proxied environments Dynamic packet filtering n n combined features of packet filtering & proxy systems Packet rules modified “on the fly” in response to triggers Underlying Internet protocol undergoing revisions - IPv 6
 Not Recommended n Merging Bastion Host & Interior Router n n Breach of host leaves access to internal net Using Multiple Interior Routers n n Routing software could decide fastest way to another internal system is via the perimeter net Difficult to keep multiple interior routers configured correctly Most important & complex set of packet filters May need to use multiples to resolve performance bottlenecks or separate internal networks
Not Recommended n Merging Bastion Host & Interior Router n n Breach of host leaves access to internal net Using Multiple Interior Routers n n Routing software could decide fastest way to another internal system is via the perimeter net Difficult to keep multiple interior routers configured correctly Most important & complex set of packet filters May need to use multiples to resolve performance bottlenecks or separate internal networks
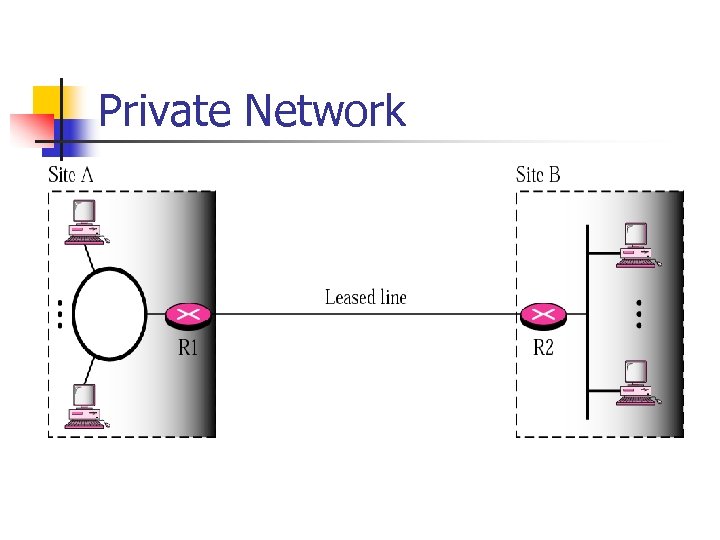 Private Network
Private Network
 Virtual Private Network Intranet A Internet Intranet B Tunneling Router RA Router RB RB 200 Station 100 Data encrypted Station 200
Virtual Private Network Intranet A Internet Intranet B Tunneling Router RA Router RB RB 200 Station 100 Data encrypted Station 200
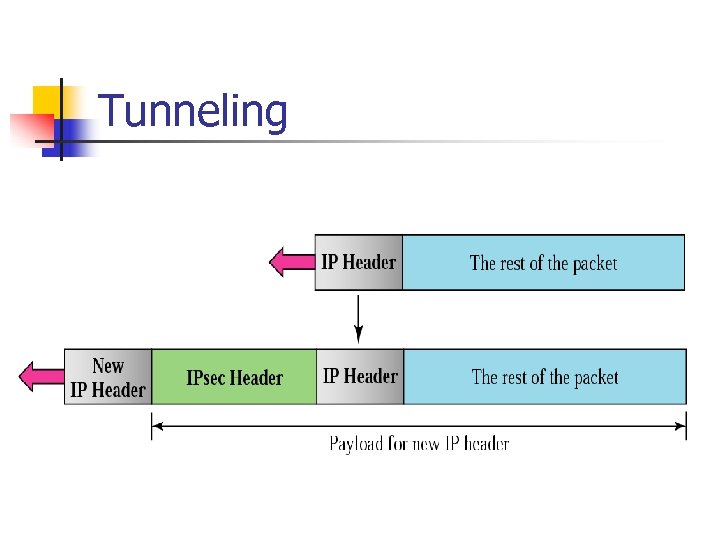 Tunneling
Tunneling
 Virus
Virus
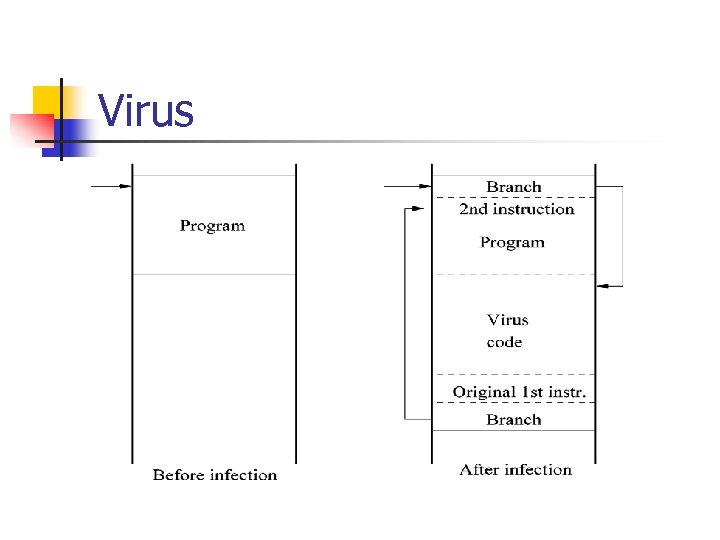 Virus
Virus
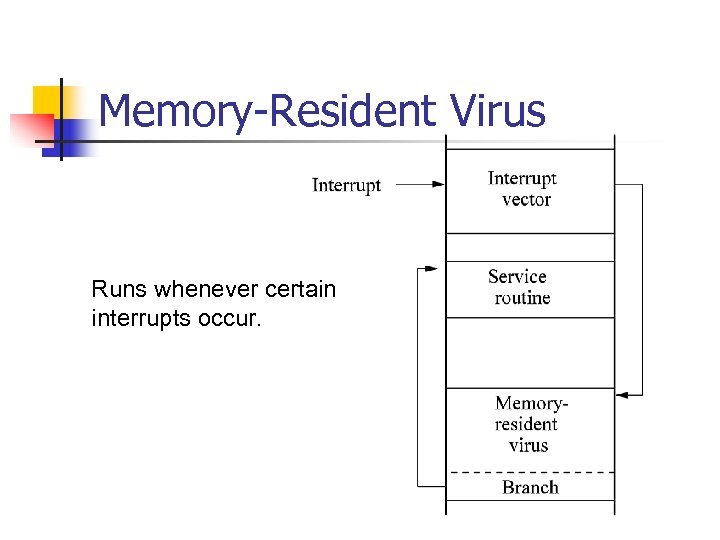 Memory-Resident Virus Runs whenever certain interrupts occur.
Memory-Resident Virus Runs whenever certain interrupts occur.
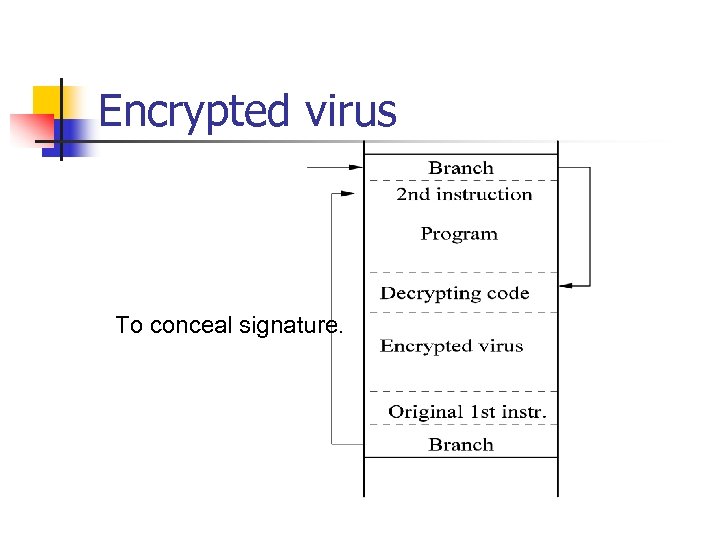 Encrypted virus To conceal signature.
Encrypted virus To conceal signature.
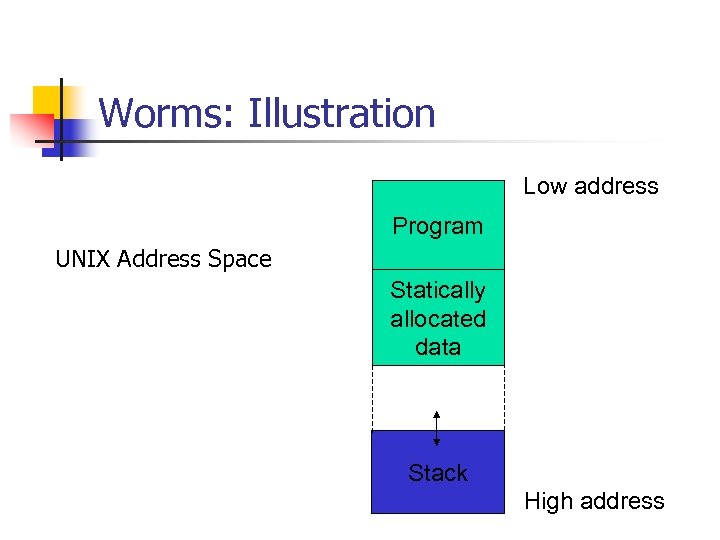 Worms: Illustration Low address Program UNIX Address Space Statically allocated data Stack High address
Worms: Illustration Low address Program UNIX Address Space Statically allocated data Stack High address
![Procedure Call E. g. , finger aabbcc [PC] aa bb cc ret para 2 Procedure Call E. g. , finger aabbcc [PC] aa bb cc ret para 2](https://present5.com/presentation/98120828a6be3047d637b441b3961468/image-77.jpg) Procedure Call E. g. , finger aabbcc [PC] aa bb cc ret para 2 para 1 Stack Buffer area allocated by called fingerd (512 bytes) Return address High address
Procedure Call E. g. , finger aabbcc [PC] aa bb cc ret para 2 para 1 Stack Buffer area allocated by called fingerd (512 bytes) Return address High address
![Buffer Overflow E. g. , finger aabb…zz 0100 [PC] aa bb cc … … Buffer Overflow E. g. , finger aabb…zz 0100 [PC] aa bb cc … …](https://present5.com/presentation/98120828a6be3047d637b441b3961468/image-78.jpg) Buffer Overflow E. g. , finger aabb…zz 0100 [PC] aa bb cc … … 0100 para 2 para 1 Stack Malicious program (binary) Return address
Buffer Overflow E. g. , finger aabb…zz 0100 [PC] aa bb cc … … 0100 para 2 para 1 Stack Malicious program (binary) Return address
 Security Management
Security Management
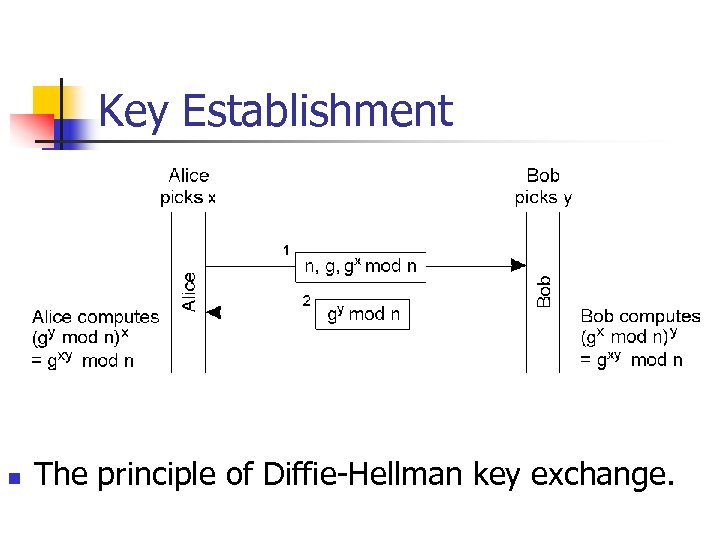 Key Establishment n The principle of Diffie-Hellman key exchange.
Key Establishment n The principle of Diffie-Hellman key exchange.
 Key Distribution (1) n Secret-key distribution
Key Distribution (1) n Secret-key distribution
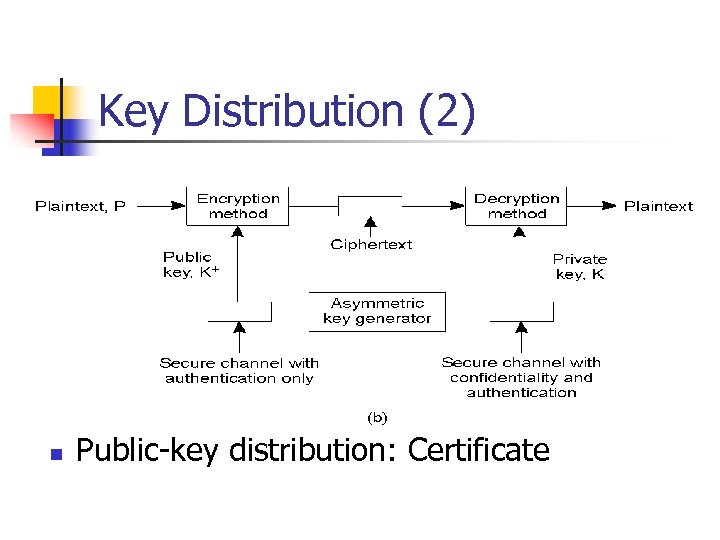 Key Distribution (2) n Public-key distribution: Certificate
Key Distribution (2) n Public-key distribution: Certificate
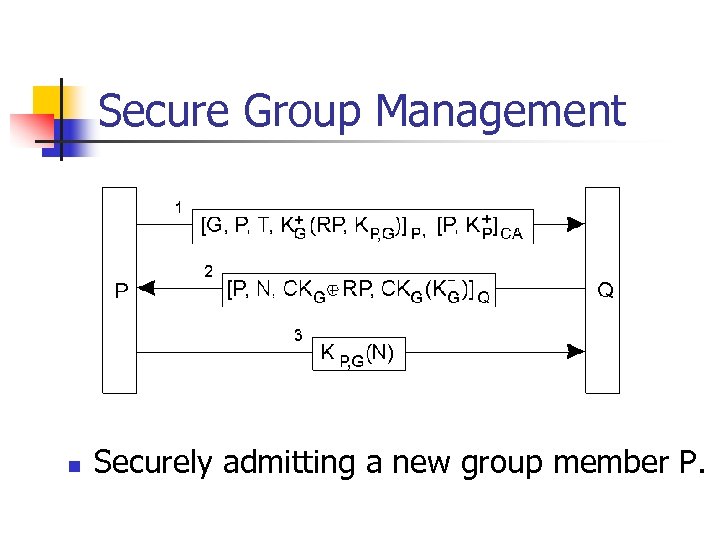 Secure Group Management n Securely admitting a new group member P.
Secure Group Management n Securely admitting a new group member P.
 Authorization Management
Authorization Management
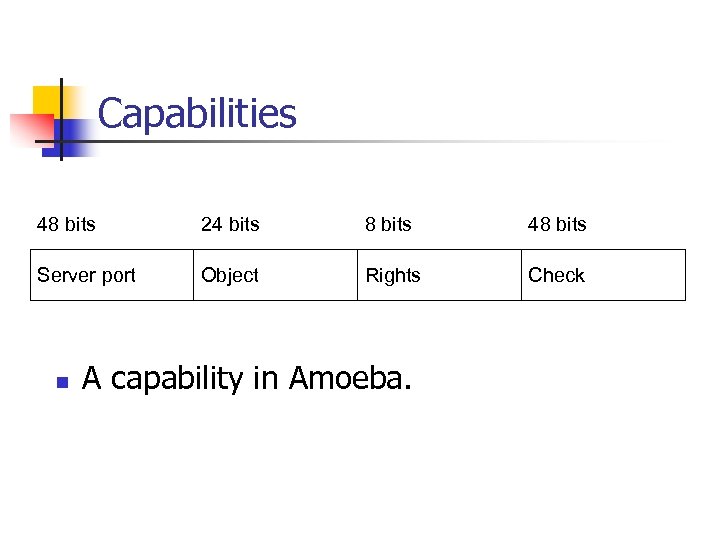 Capabilities 48 bits 24 bits 8 bits 48 bits Server port Object Rights Check n A capability in Amoeba.
Capabilities 48 bits 24 bits 8 bits 48 bits Server port Object Rights Check n A capability in Amoeba.
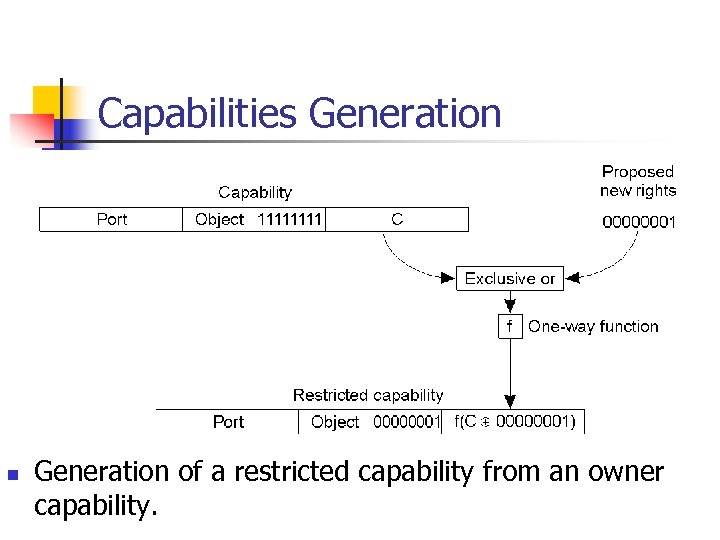 Capabilities Generation n Generation of a restricted capability from an owner capability.
Capabilities Generation n Generation of a restricted capability from an owner capability.
 Delegation n n Transfer the access rights on files, resources, etc. Suppose Alice wants to delegate rights to Bob n n If Alice knows everyone, broadcast the certificate Otherwise, construct a certificate saying “The bearer of this certificate has rights R. ” n n Problems? Using proxy, a token that allows its owner to operate with the rights granted in the token.
Delegation n n Transfer the access rights on files, resources, etc. Suppose Alice wants to delegate rights to Bob n n If Alice knows everyone, broadcast the certificate Otherwise, construct a certificate saying “The bearer of this certificate has rights R. ” n n Problems? Using proxy, a token that allows its owner to operate with the rights granted in the token.
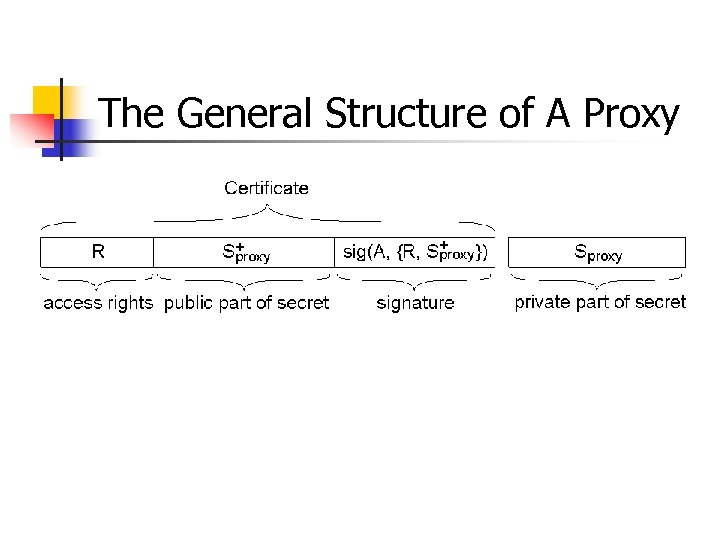 The General Structure of A Proxy
The General Structure of A Proxy
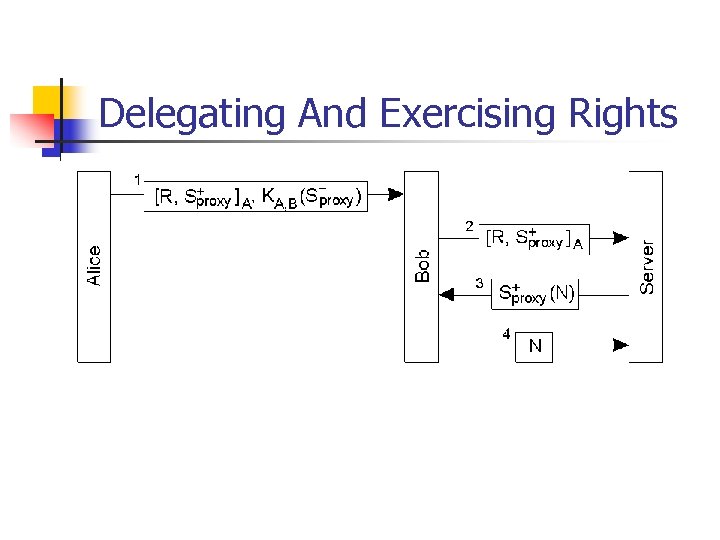 Delegating And Exercising Rights
Delegating And Exercising Rights
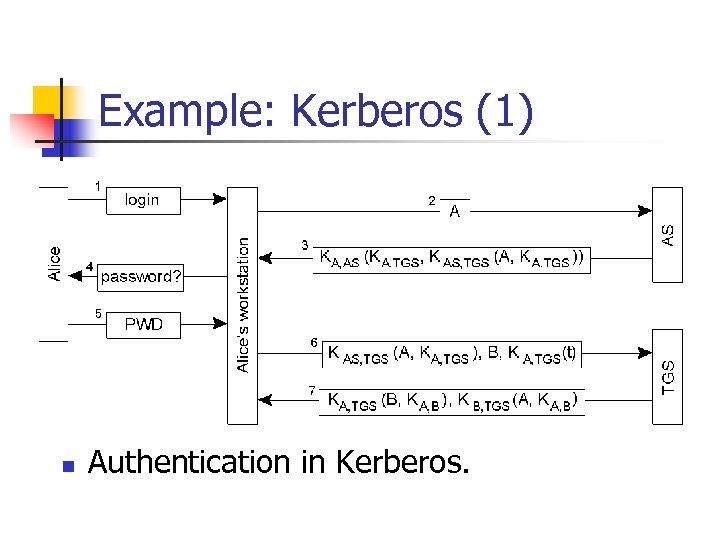 Example: Kerberos (1) n Authentication in Kerberos.
Example: Kerberos (1) n Authentication in Kerberos.
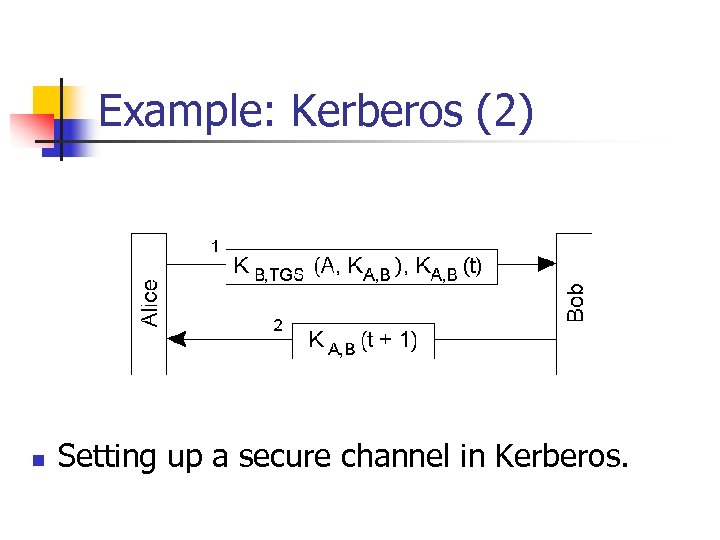 Example: Kerberos (2) n Setting up a secure channel in Kerberos.
Example: Kerberos (2) n Setting up a secure channel in Kerberos.
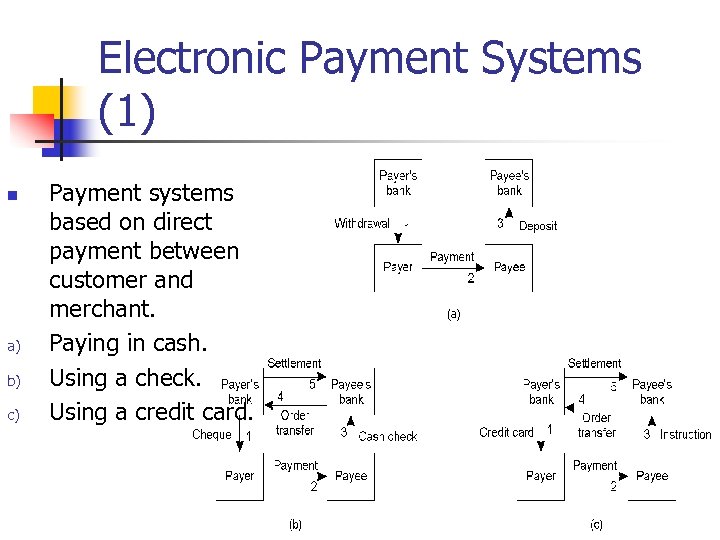 Electronic Payment Systems (1) n a) b) c) Payment systems based on direct payment between customer and merchant. Paying in cash. Using a check. Using a credit card.
Electronic Payment Systems (1) n a) b) c) Payment systems based on direct payment between customer and merchant. Paying in cash. Using a check. Using a credit card.
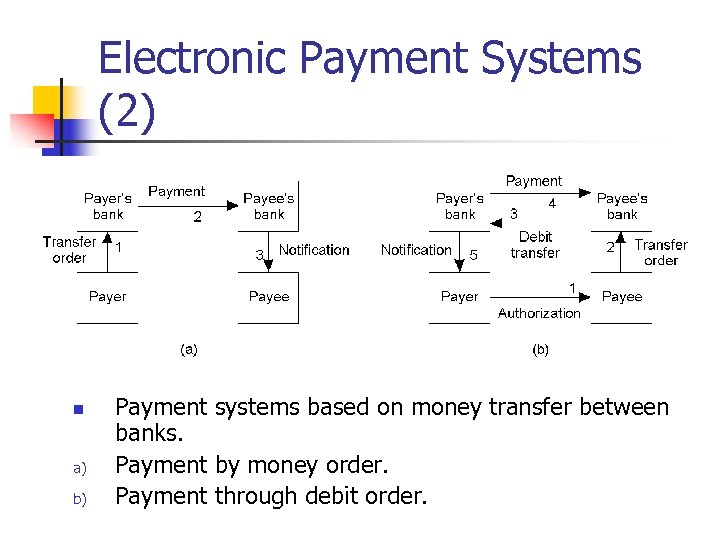 Electronic Payment Systems (2) n a) b) Payment systems based on money transfer between banks. Payment by money order. Payment through debit order.
Electronic Payment Systems (2) n a) b) Payment systems based on money transfer between banks. Payment by money order. Payment through debit order.
 Privacy Issue n n n Using cash Using credit card Online
Privacy Issue n n n Using cash Using credit card Online
 Digital Money n Suppose Alice wants to pay $12 to Bob n n Contact her bank and request withdrawal $12 Bank hands out digital money (each note is signed) n n n Each note carries a unique serial number Hand over the notes to Bob contact the bank if the money has been used. Problem: privacy issue. Solution: blind signature
Digital Money n Suppose Alice wants to pay $12 to Bob n n Contact her bank and request withdrawal $12 Bank hands out digital money (each note is signed) n n n Each note carries a unique serial number Hand over the notes to Bob contact the bank if the money has been used. Problem: privacy issue. Solution: blind signature
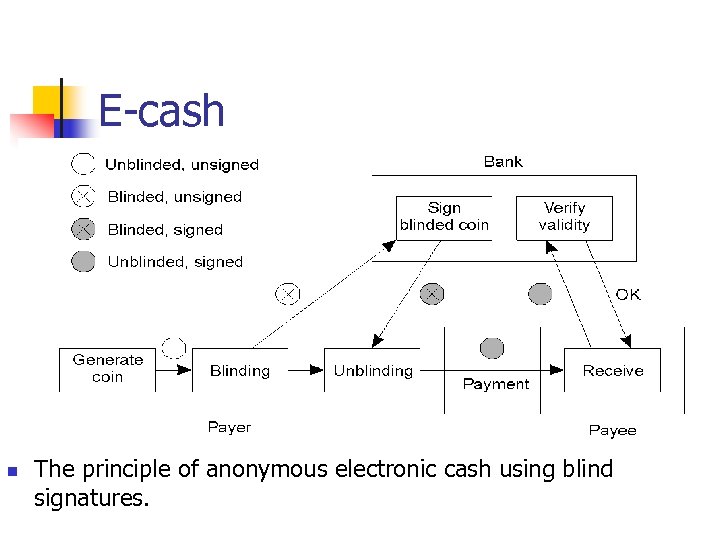 E-cash n The principle of anonymous electronic cash using blind signatures.
E-cash n The principle of anonymous electronic cash using blind signatures.


