a124cec7dcfaebc65b44ba8d31834fc0.ppt
- Количество слайдов: 87
 Chapter 5 Topology Control 1 2018/3/17
Chapter 5 Topology Control 1 2018/3/17
 Outline 5. 2. Power Control and Energy Conservation 5. 3. Tree Topology 5. 4. k-hop Connected Dominating Set 5. 5. Adaptive node activity 2 5. 1. Motivations and Goals 5. 6. Conclusions 2018/3/17
Outline 5. 2. Power Control and Energy Conservation 5. 3. Tree Topology 5. 4. k-hop Connected Dominating Set 5. 5. Adaptive node activity 2 5. 1. Motivations and Goals 5. 6. Conclusions 2018/3/17
 Outline 5. 2. Power Control and Energy Conservation 5. 3. Tree Topology 5. 4. k-hop Connected Dominating Set 5. 5. Adaptive node activity 3 5. 1. Motivations and Goals 5. 6. Conclusions 2018/3/17
Outline 5. 2. Power Control and Energy Conservation 5. 3. Tree Topology 5. 4. k-hop Connected Dominating Set 5. 5. Adaptive node activity 3 5. 1. Motivations and Goals 5. 6. Conclusions 2018/3/17
 Motivations A typical characteristic of wireless sensor networks 4 deploying many nodes in a small area ensure sufficient coverage of an area, or protect against node failures Networks can be too dense: too many nodes in close (radio) vicinity 2018/3/17
Motivations A typical characteristic of wireless sensor networks 4 deploying many nodes in a small area ensure sufficient coverage of an area, or protect against node failures Networks can be too dense: too many nodes in close (radio) vicinity 2018/3/17
 Motivations In a very dense networks, too many nodes 5 Too many collisions Too complex operation for a MAC protocol Too many paths to be chosen from for a routing protocol, … 2018/3/17
Motivations In a very dense networks, too many nodes 5 Too many collisions Too complex operation for a MAC protocol Too many paths to be chosen from for a routing protocol, … 2018/3/17
 Goals This chapter looks at methods to deal with such networks by 6 Reducing/controlling transmission power Deciding which links to use Turning some nodes off 2018/3/17
Goals This chapter looks at methods to deal with such networks by 6 Reducing/controlling transmission power Deciding which links to use Turning some nodes off 2018/3/17
 Topology Control Topology control: Make topology less complex 7 Topology: Which node is able/allowed to communicate with which other nodes Topology control needs to maintain invariants, e. g. , connectivity 2018/3/17
Topology Control Topology control: Make topology less complex 7 Topology: Which node is able/allowed to communicate with which other nodes Topology control needs to maintain invariants, e. g. , connectivity 2018/3/17
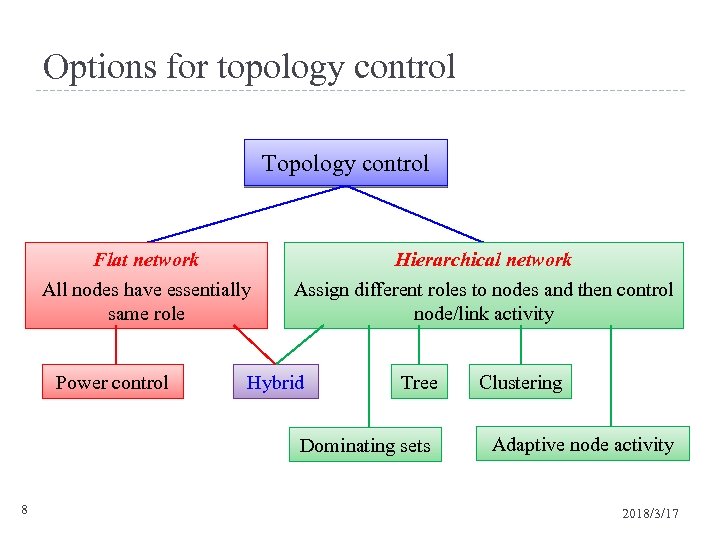 Options for topology control Topology control Flat network Hierarchical network All nodes have essentially same role Assign different roles to nodes and then control node/link activity Power control Hybrid Tree Dominating sets 8 Clustering Adaptive node activity 2018/3/17
Options for topology control Topology control Flat network Hierarchical network All nodes have essentially same role Assign different roles to nodes and then control node/link activity Power control Hybrid Tree Dominating sets 8 Clustering Adaptive node activity 2018/3/17
 Outline 5. 2. Power Control and Energy Conservation 5. 3. Tree Topology 5. 4. k-hop Connected Dominating Set 5. 5. Adaptive node activity 9 5. 1. Motivation and Goals 5. 6. Conclusions 2018/3/17
Outline 5. 2. Power Control and Energy Conservation 5. 3. Tree Topology 5. 4. k-hop Connected Dominating Set 5. 5. Adaptive node activity 9 5. 1. Motivation and Goals 5. 6. Conclusions 2018/3/17
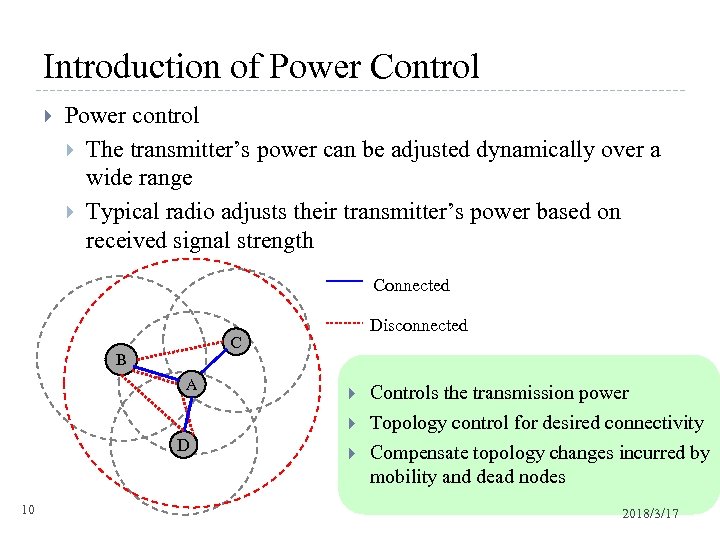 Introduction of Power Control Power control The transmitter’s power can be adjusted dynamically over a wide range Typical radio adjusts their transmitter’s power based on received signal strength Connected Disconnected C B A D 10 Controls the transmission power Topology control for desired connectivity Compensate topology changes incurred by mobility and dead nodes 2018/3/17
Introduction of Power Control Power control The transmitter’s power can be adjusted dynamically over a wide range Typical radio adjusts their transmitter’s power based on received signal strength Connected Disconnected C B A D 10 Controls the transmission power Topology control for desired connectivity Compensate topology changes incurred by mobility and dead nodes 2018/3/17
 Introduction of Power Control Interactions Power control Large Battery makes Longer Lifetime 11 Battery drain 2018/3/17
Introduction of Power Control Interactions Power control Large Battery makes Longer Lifetime 11 Battery drain 2018/3/17
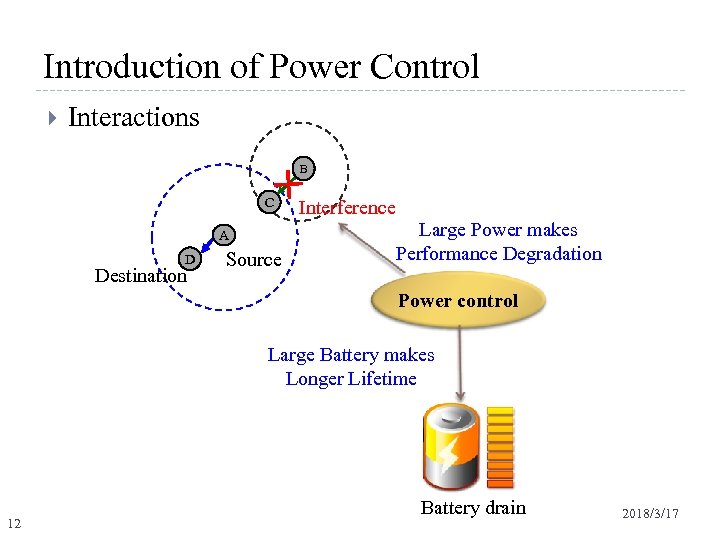 Introduction of Power Control Interactions B C A D Destination Source Interference Large Power makes Performance Degradation Power control Large Battery makes Longer Lifetime 12 Battery drain 2018/3/17
Introduction of Power Control Interactions B C A D Destination Source Interference Large Power makes Performance Degradation Power control Large Battery makes Longer Lifetime 12 Battery drain 2018/3/17
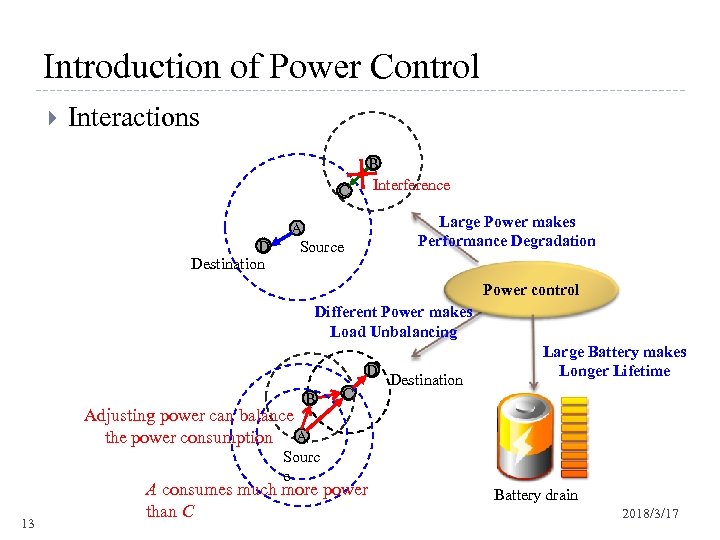 Introduction of Power Control Interactions B Interference C D Destination Large Power makes Performance Degradation A Source Power control Different Power makes Load Unbalancing D B C Destination Large Battery makes Longer Lifetime Adjusting power can balance the power consumption A Sourc e 13 A consumes much more power than C Battery drain 2018/3/17
Introduction of Power Control Interactions B Interference C D Destination Large Power makes Performance Degradation A Source Power control Different Power makes Load Unbalancing D B C Destination Large Battery makes Longer Lifetime Adjusting power can balance the power consumption A Sourc e 13 A consumes much more power than C Battery drain 2018/3/17
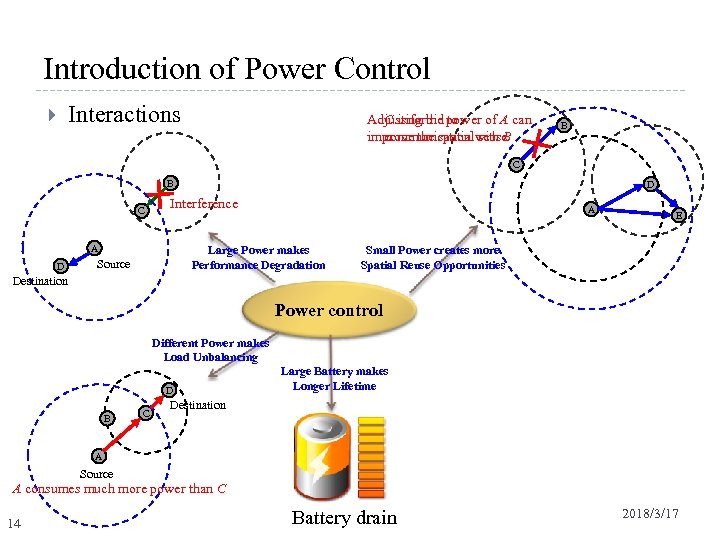 Introduction of Power Control Interactions Adjusting the power of A can C is forbid to improve the spatialwith B communication reuse B C Interference A D D A Large Power makes Performance Degradation Source E Small Power creates more Spatial Reuse Opportunities Destination Power control Different Power makes Load Unbalancing D B C Large Battery makes Longer Lifetime Destination A Source A consumes much more power than C 14 Battery drain 2018/3/17
Introduction of Power Control Interactions Adjusting the power of A can C is forbid to improve the spatialwith B communication reuse B C Interference A D D A Large Power makes Performance Degradation Source E Small Power creates more Spatial Reuse Opportunities Destination Power control Different Power makes Load Unbalancing D B C Large Battery makes Longer Lifetime Destination A Source A consumes much more power than C 14 Battery drain 2018/3/17
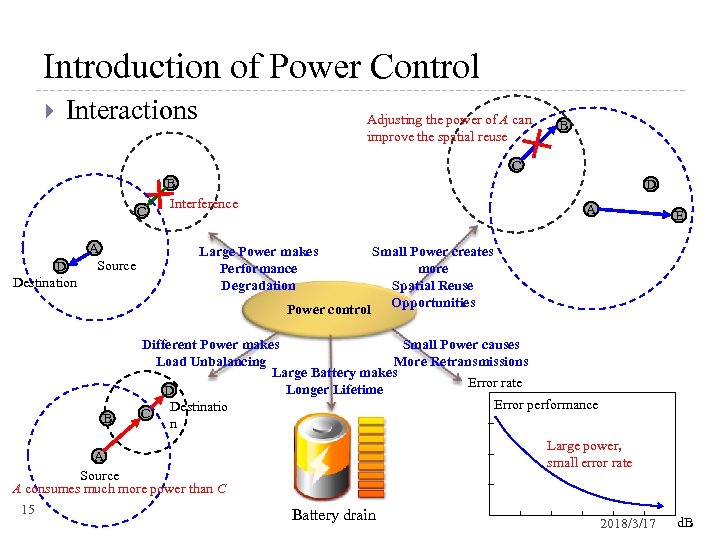 Introduction of Power Control Interactions Adjusting the power of A can improve the spatial reuse B C C D Destination A Source B Interference D A Large Power makes Performance Degradation Power control B E Small Power creates more Spatial Reuse Opportunities Small Power causes Different Power makes More Retransmissions Load Unbalancing Large Battery makes Error rate Longer Lifetime D Error performance Destinatio C n A Source A consumes much more power than C 15 Large power, small error rate Battery drain 2018/3/17 d. B
Introduction of Power Control Interactions Adjusting the power of A can improve the spatial reuse B C C D Destination A Source B Interference D A Large Power makes Performance Degradation Power control B E Small Power creates more Spatial Reuse Opportunities Small Power causes Different Power makes More Retransmissions Load Unbalancing Large Battery makes Error rate Longer Lifetime D Error performance Destinatio C n A Source A consumes much more power than C 15 Large power, small error rate Battery drain 2018/3/17 d. B
 Introduction of Power Control Targets and Issues 16 Improve network throughput Improve transmission range Improve fairness Improve connectivity Power control helps in scheduling Reduce the interference and energy consumption Partial combination of above targets etc. 2018/3/17
Introduction of Power Control Targets and Issues 16 Improve network throughput Improve transmission range Improve fairness Improve connectivity Power control helps in scheduling Reduce the interference and energy consumption Partial combination of above targets etc. 2018/3/17
 Power Control and Energy Conservation Topology Control of Multihop Wireless Networks using Transmit Power Adjustment R. Ramanathan and R. Rosales-Hain IEEE INFOCOM 2000 17 2018/3/17
Power Control and Energy Conservation Topology Control of Multihop Wireless Networks using Transmit Power Adjustment R. Ramanathan and R. Rosales-Hain IEEE INFOCOM 2000 17 2018/3/17
 Introduction Topology 18 The set of communication links between node pairs used by routing mechanism Uncontrollable factor: mobility, weather, interference, noise Controllable factor: transmission power, antenna direction 2018/3/17
Introduction Topology 18 The set of communication links between node pairs used by routing mechanism Uncontrollable factor: mobility, weather, interference, noise Controllable factor: transmission power, antenna direction 2018/3/17
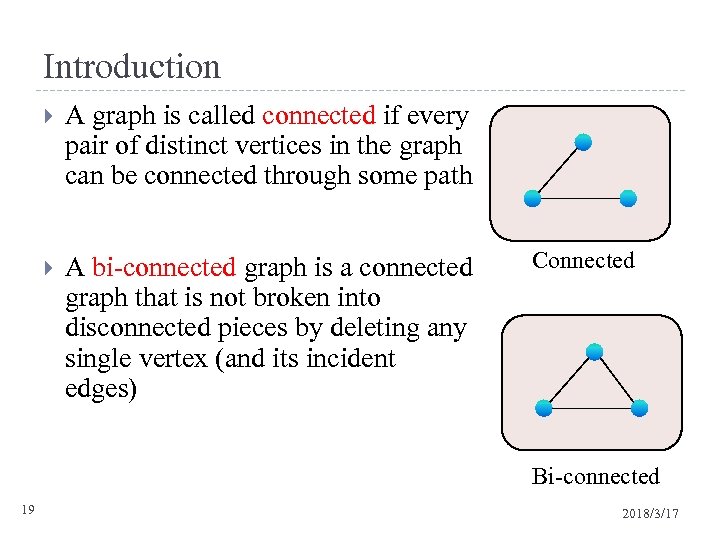 Introduction A graph is called connected if every pair of distinct vertices in the graph can be connected through some path A bi-connected graph is a connected graph that is not broken into disconnected pieces by deleting any single vertex (and its incident edges) Connected Bi-connected 19 2018/3/17
Introduction A graph is called connected if every pair of distinct vertices in the graph can be connected through some path A bi-connected graph is a connected graph that is not broken into disconnected pieces by deleting any single vertex (and its incident edges) Connected Bi-connected 19 2018/3/17
 Motivation Drawbacks of wrong topology Sparse network A danger of network partitioning High end to end delays Dense network 20 Reduce network capacity Increase interference Increase end-to-end packet delay Many nodes interfere with each other 2018/3/17
Motivation Drawbacks of wrong topology Sparse network A danger of network partitioning High end to end delays Dense network 20 Reduce network capacity Increase interference Increase end-to-end packet delay Many nodes interfere with each other 2018/3/17
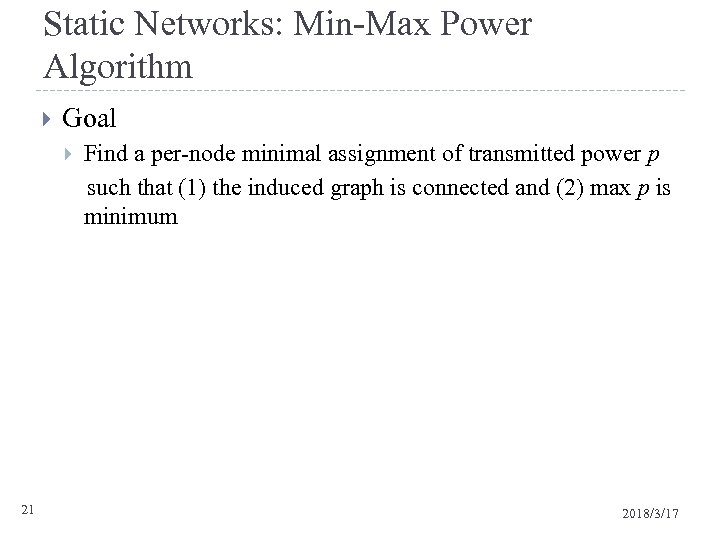 Static Networks: Min-Max Power Algorithm Goal 21 Find a per-node minimal assignment of transmitted power p such that (1) the induced graph is connected and (2) max p is minimum 2018/3/17
Static Networks: Min-Max Power Algorithm Goal 21 Find a per-node minimal assignment of transmitted power p such that (1) the induced graph is connected and (2) max p is minimum 2018/3/17
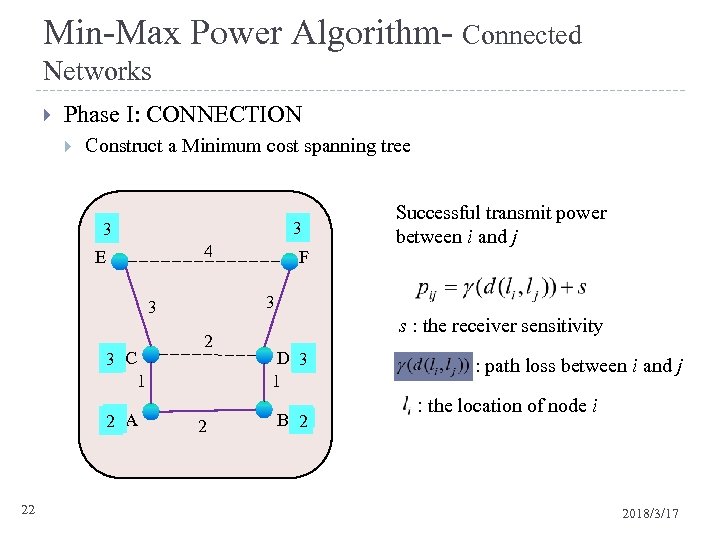 Min-Max Power Algorithm- Connected Networks Phase I: CONNECTION Construct a Minimum cost spanning tree 3 3 4 E 3 3 1 3 C 1 1 2 A 22 F Successful transmit power between i and j 2 2 s : the receiver sensitivity D 1 3 1 B 1 2 : path loss between i and j : the location of node i 2018/3/17
Min-Max Power Algorithm- Connected Networks Phase I: CONNECTION Construct a Minimum cost spanning tree 3 3 4 E 3 3 1 3 C 1 1 2 A 22 F Successful transmit power between i and j 2 2 s : the receiver sensitivity D 1 3 1 B 1 2 : path loss between i and j : the location of node i 2018/3/17
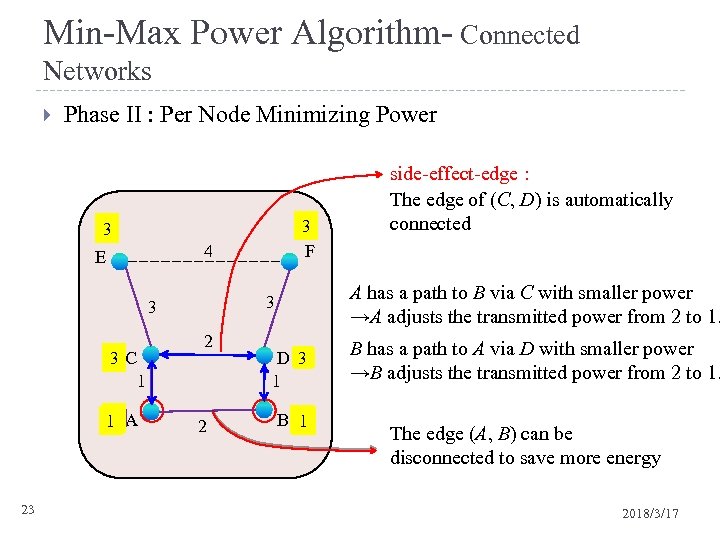 Min-Max Power Algorithm- Connected Networks Phase II : Per Node Minimizing Power 3 F 3 4 E 1 C 3 1 2 1 1 A 23 A has a path to B via C with smaller power →A adjusts the transmitted power from 2 to 1. 3 3 2 2 side-effect-edge : The edge of (C, D) is automatically connected D 3 1 1 B 1 2 1 B has a path to A via D with smaller power →B adjusts the transmitted power from 2 to 1. The edge (A, B) can be disconnected to save more energy 2018/3/17
Min-Max Power Algorithm- Connected Networks Phase II : Per Node Minimizing Power 3 F 3 4 E 1 C 3 1 2 1 1 A 23 A has a path to B via C with smaller power →A adjusts the transmitted power from 2 to 1. 3 3 2 2 side-effect-edge : The edge of (C, D) is automatically connected D 3 1 1 B 1 2 1 B has a path to A via D with smaller power →B adjusts the transmitted power from 2 to 1. The edge (A, B) can be disconnected to save more energy 2018/3/17
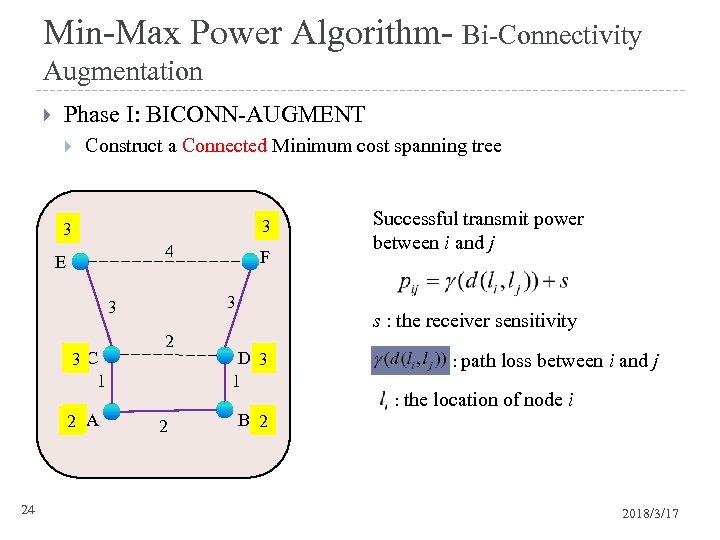 Min-Max Power Algorithm- Bi-Connectivity Augmentation Phase I: BICONN-AUGMENT Construct a Connected Minimum cost spanning tree 3 3 4 E 3 3 1 C 3 1 1 2 A 24 F 2 2 Successful transmit power between i and j s : the receiver sensitivity D 1 3 1 B 1 2 : path loss between i and j : the location of node i 2018/3/17
Min-Max Power Algorithm- Bi-Connectivity Augmentation Phase I: BICONN-AUGMENT Construct a Connected Minimum cost spanning tree 3 3 4 E 3 3 1 C 3 1 1 2 A 24 F 2 2 Successful transmit power between i and j s : the receiver sensitivity D 1 3 1 B 1 2 : path loss between i and j : the location of node i 2018/3/17
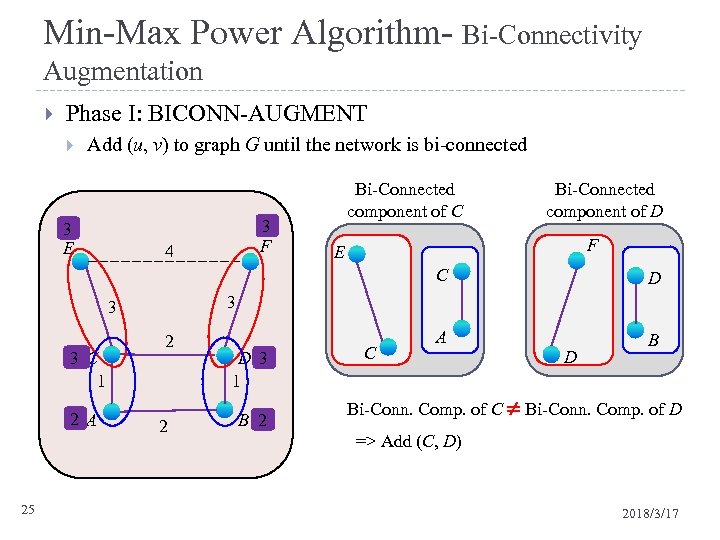 Min-Max Power Algorithm- Bi-Connectivity Augmentation Phase I: BICONN-AUGMENT Add (u, v) to graph G until the network is bi-connected 3 E 3 F 4 Bi-Connected component of C Bi-Connected component of D F E C 2 A 1 25 A B 3 3 1 C 3 1 D 2 2 D 3 1 1 2 B 1 C D Bi-Conn. Comp. of C Bi-Conn. Comp. of D => Add (C, D) 2018/3/17
Min-Max Power Algorithm- Bi-Connectivity Augmentation Phase I: BICONN-AUGMENT Add (u, v) to graph G until the network is bi-connected 3 E 3 F 4 Bi-Connected component of C Bi-Connected component of D F E C 2 A 1 25 A B 3 3 1 C 3 1 D 2 2 D 3 1 1 2 B 1 C D Bi-Conn. Comp. of C Bi-Conn. Comp. of D => Add (C, D) 2018/3/17
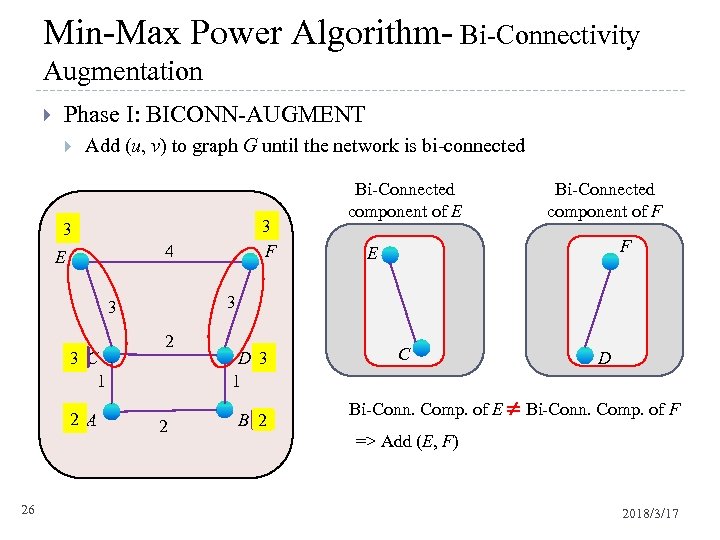 Min-Max Power Algorithm- Bi-Connectivity Augmentation Phase I: BICONN-AUGMENT Add (u, v) to graph G until the network is bi-connected 3 F 3 4 E 2 A 1 26 Bi-Connected component of F F E 3 3 1 C 3 1 Bi-Connected component of E 2 2 D 3 1 1 2 B 1 C D Bi-Conn. Comp. of E Bi-Conn. Comp. of F => Add (E, F) 2018/3/17
Min-Max Power Algorithm- Bi-Connectivity Augmentation Phase I: BICONN-AUGMENT Add (u, v) to graph G until the network is bi-connected 3 F 3 4 E 2 A 1 26 Bi-Connected component of F F E 3 3 1 C 3 1 Bi-Connected component of E 2 2 D 3 1 1 2 B 1 C D Bi-Conn. Comp. of E Bi-Conn. Comp. of F => Add (E, F) 2018/3/17
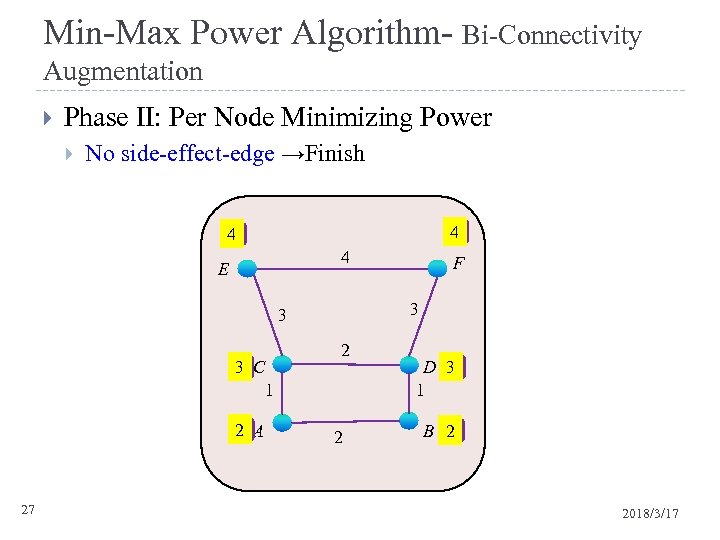 Min-Max Power Algorithm- Bi-Connectivity Augmentation Phase II: Per Node Minimizing Power No side-effect-edge →Finish 4 4 4 E 3 3 2 1 C 3 1 2 A 1 27 F 2 1 D 3 1 2 B 1 2018/3/17
Min-Max Power Algorithm- Bi-Connectivity Augmentation Phase II: Per Node Minimizing Power No side-effect-edge →Finish 4 4 4 E 3 3 2 1 C 3 1 2 A 1 27 F 2 1 D 3 1 2 B 1 2018/3/17
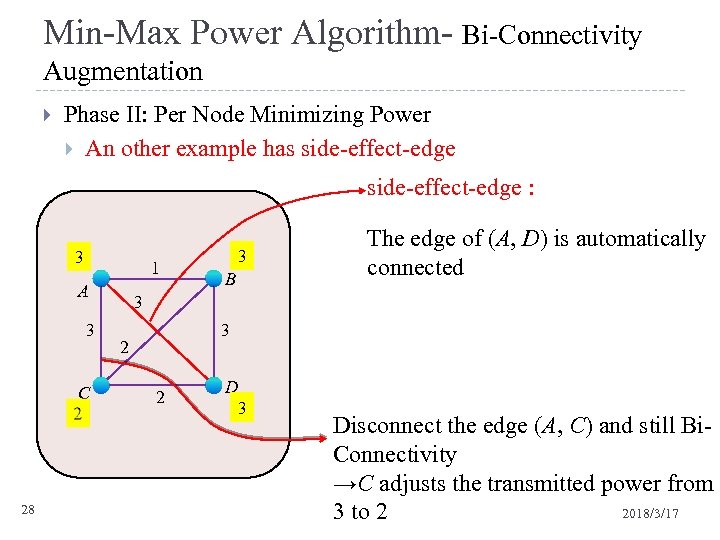 Min-Max Power Algorithm- Bi-Connectivity Augmentation Phase II: Per Node Minimizing Power An other example has side-effect-edge : 1 3 1 A 3 C 2 3 28 3 2 1 B The edge of (A, D) is automatically connected 3 3 2 2 D 3 Disconnect the edge (A, C) and still Bi. Connectivity →C adjusts the transmitted power from 2018/3/17 3 to 2
Min-Max Power Algorithm- Bi-Connectivity Augmentation Phase II: Per Node Minimizing Power An other example has side-effect-edge : 1 3 1 A 3 C 2 3 28 3 2 1 B The edge of (A, D) is automatically connected 3 3 2 2 D 3 Disconnect the edge (A, C) and still Bi. Connectivity →C adjusts the transmitted power from 2018/3/17 3 to 2
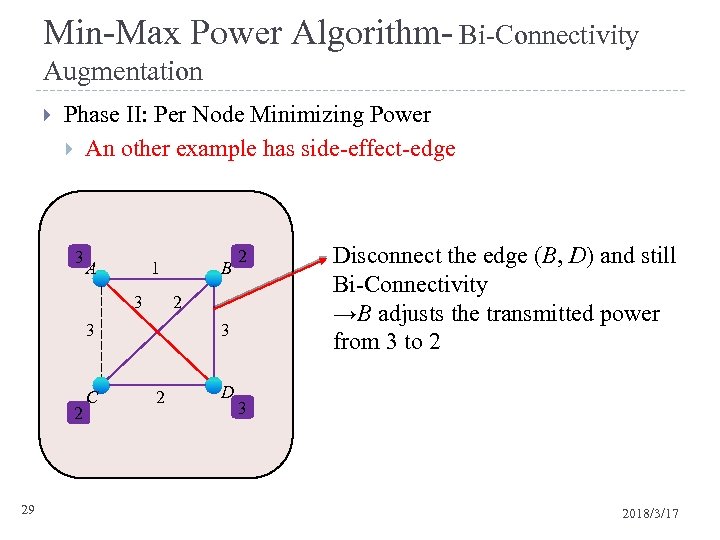 Min-Max Power Algorithm- Bi-Connectivity Augmentation Phase II: Per Node Minimizing Power An other example has side-effect-edge 3 1 A 1 3 2 29 3 2 1 2 3 C B 3 2 D Disconnect the edge (B, D) and still Bi-Connectivity →B adjusts the transmitted power from 3 to 2 3 2018/3/17
Min-Max Power Algorithm- Bi-Connectivity Augmentation Phase II: Per Node Minimizing Power An other example has side-effect-edge 3 1 A 1 3 2 29 3 2 1 2 3 C B 3 2 D Disconnect the edge (B, D) and still Bi-Connectivity →B adjusts the transmitted power from 3 to 2 3 2018/3/17
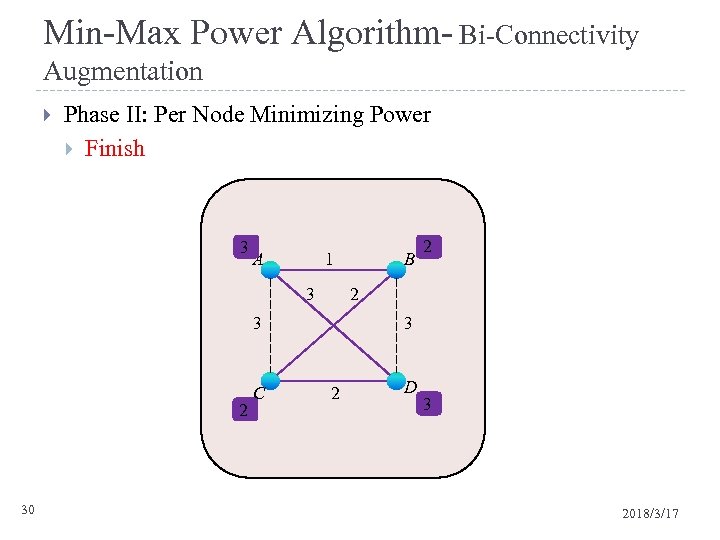 Min-Max Power Algorithm- Bi-Connectivity Augmentation Phase II: Per Node Minimizing Power Finish 1 3 A 1 2 3 3 2 30 C B 3 2 1 3 2 D 3 2018/3/17
Min-Max Power Algorithm- Bi-Connectivity Augmentation Phase II: Per Node Minimizing Power Finish 1 3 A 1 2 3 3 2 30 C B 3 2 1 3 2 D 3 2018/3/17
 Outline 5. 1. Motivation and Goals 5. 2. Power Control and Energy Conservation 5. 3. Tree Topology 5. 4. k-hop Connected Dominating Set 5. 5. Adaptive node activity 5. 6. Conclusions 31 2018/3/17
Outline 5. 1. Motivation and Goals 5. 2. Power Control and Energy Conservation 5. 3. Tree Topology 5. 4. k-hop Connected Dominating Set 5. 5. Adaptive node activity 5. 6. Conclusions 31 2018/3/17
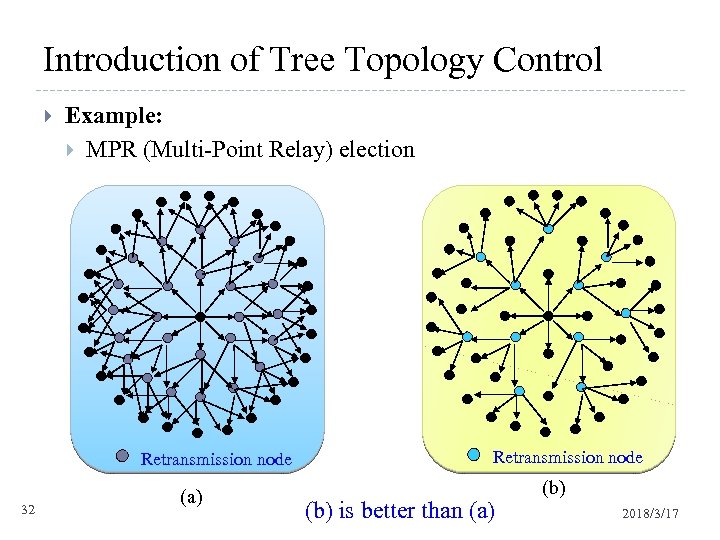 Introduction of Tree Topology Control Example: MPR (Multi-Point Relay) election Retransmission node 32 (a) Retransmission node (b) is better than (a) (b) 2018/3/17
Introduction of Tree Topology Control Example: MPR (Multi-Point Relay) election Retransmission node 32 (a) Retransmission node (b) is better than (a) (b) 2018/3/17
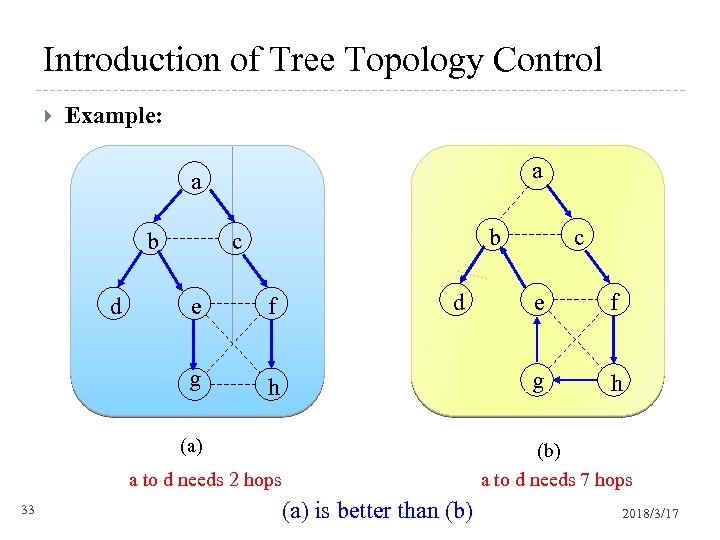 Introduction of Tree Topology Control Example: a a b d b c e f g d e f g h (a) h (b) a to d needs 7 hops a to d needs 2 hops 33 c (a) is better than (b) 2018/3/17
Introduction of Tree Topology Control Example: a a b d b c e f g d e f g h (a) h (b) a to d needs 7 hops a to d needs 2 hops 33 c (a) is better than (b) 2018/3/17
 Tree Topology Design and Analysis of an MST-Based Topology Control Algorithm N. Li, J. C. Hou, and L. Sha IEEE INFOCOM 2003 34 2018/3/17
Tree Topology Design and Analysis of an MST-Based Topology Control Algorithm N. Li, J. C. Hou, and L. Sha IEEE INFOCOM 2003 34 2018/3/17
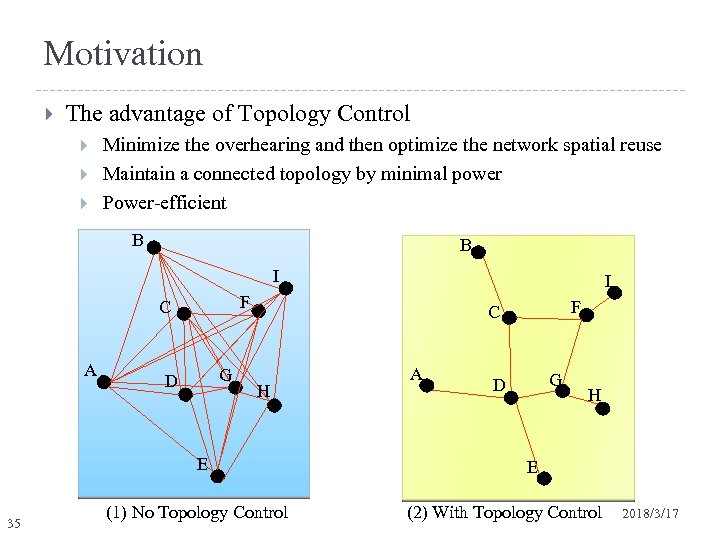 Motivation The advantage of Topology Control Minimize the overhearing and then optimize the network spatial reuse Maintain a connected topology by minimal power Power-efficient B B I F C A G D F C H E 35 I (1) No Topology Control A G D H E (2) With Topology Control 2018/3/17
Motivation The advantage of Topology Control Minimize the overhearing and then optimize the network spatial reuse Maintain a connected topology by minimal power Power-efficient B B I F C A G D F C H E 35 I (1) No Topology Control A G D H E (2) With Topology Control 2018/3/17
 Goal Determine the transmission power of each node 36 Maintain network connectivity Minimal power consumption 2018/3/17
Goal Determine the transmission power of each node 36 Maintain network connectivity Minimal power consumption 2018/3/17
 Local Minimum Spanning Tree Algorithm (LMST) 37 Step 1: Information Collection Step 2: Topology Construction Step 3: Determination of Transmission Power 2018/3/17
Local Minimum Spanning Tree Algorithm (LMST) 37 Step 1: Information Collection Step 2: Topology Construction Step 3: Determination of Transmission Power 2018/3/17
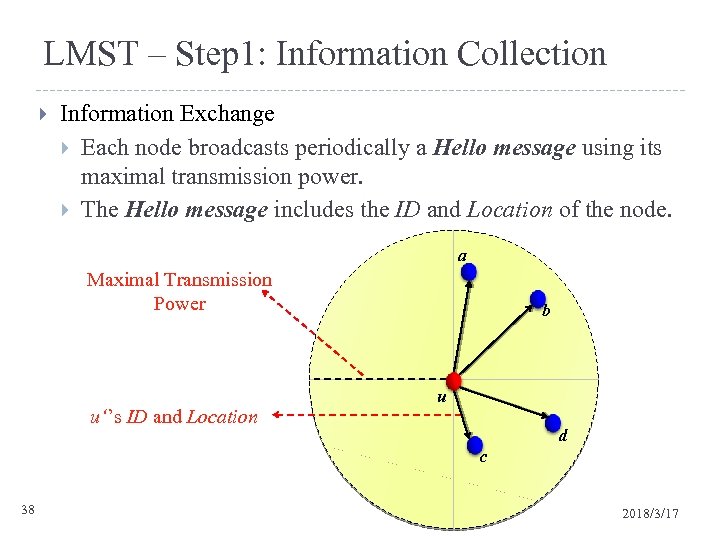 LMST – Step 1: Information Collection Information Exchange Each node broadcasts periodically a Hello message using its maximal transmission power. The Hello message includes the ID and Location of the node. a Maximal Transmission Power u‘’s ID and Location b u d c 38 2018/3/17
LMST – Step 1: Information Collection Information Exchange Each node broadcasts periodically a Hello message using its maximal transmission power. The Hello message includes the ID and Location of the node. a Maximal Transmission Power u‘’s ID and Location b u d c 38 2018/3/17
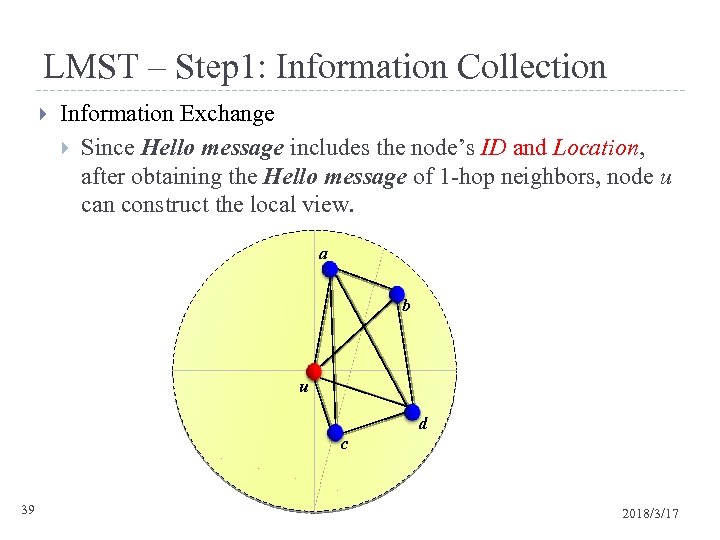 LMST – Step 1: Information Collection Information Exchange Since Hello message includes the node’s ID and Location, after obtaining the Hello message of 1 -hop neighbors, node u can construct the local view. a b u d c 39 2018/3/17
LMST – Step 1: Information Collection Information Exchange Since Hello message includes the node’s ID and Location, after obtaining the Hello message of 1 -hop neighbors, node u can construct the local view. a b u d c 39 2018/3/17
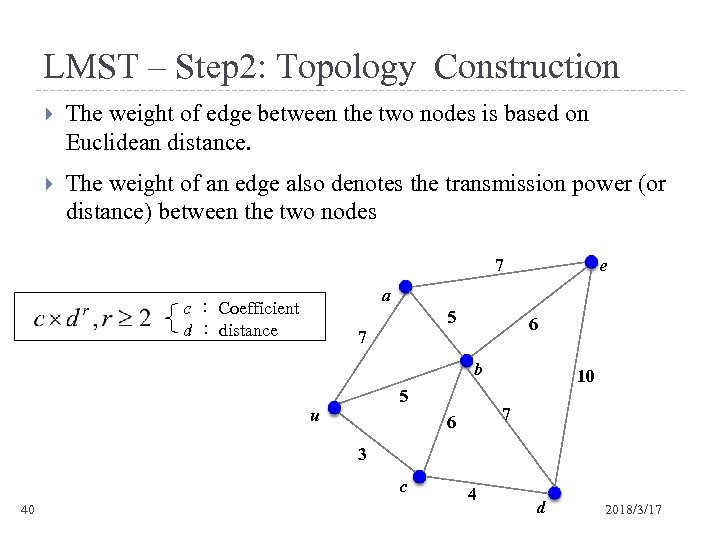 LMST – Step 2: Topology Construction The weight of edge between the two nodes is based on Euclidean distance. The weight of an edge also denotes the transmission power (or distance) between the two nodes 7 e a c : Coefficient d : distance 5 7 6 b 5 u 10 7 6 3 c 40 4 d 2018/3/17
LMST – Step 2: Topology Construction The weight of edge between the two nodes is based on Euclidean distance. The weight of an edge also denotes the transmission power (or distance) between the two nodes 7 e a c : Coefficient d : distance 5 7 6 b 5 u 10 7 6 3 c 40 4 d 2018/3/17
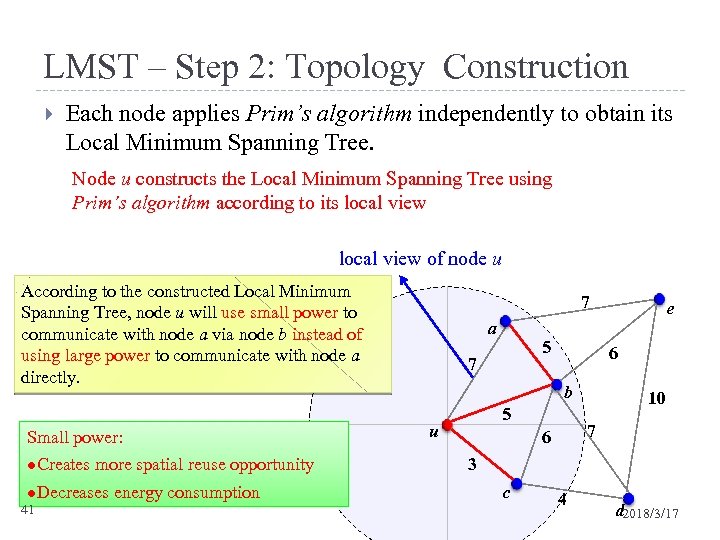 LMST – Step 2: Topology Construction Each node applies Prim’s algorithm independently to obtain its Local Minimum Spanning Tree. Node u constructs the Local Minimum Spanning Tree using Prim’s algorithm according to its local view of node u According to the constructed Local Minimum Spanning Tree, node u will use small power to communicate with node a via node b instead of using large power to communicate with node a directly. Small power: l. Creates more spatial reuse opportunity l. Decreases 41 energy consumption 7 a 5 7 6 b 5 u e 10 7 6 3 c 4 d 2018/3/17
LMST – Step 2: Topology Construction Each node applies Prim’s algorithm independently to obtain its Local Minimum Spanning Tree. Node u constructs the Local Minimum Spanning Tree using Prim’s algorithm according to its local view of node u According to the constructed Local Minimum Spanning Tree, node u will use small power to communicate with node a via node b instead of using large power to communicate with node a directly. Small power: l. Creates more spatial reuse opportunity l. Decreases 41 energy consumption 7 a 5 7 6 b 5 u e 10 7 6 3 c 4 d 2018/3/17
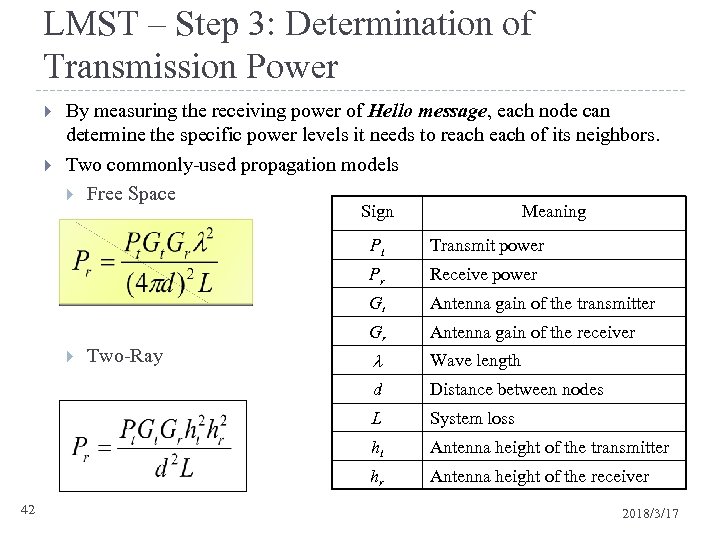 LMST – Step 3: Determination of Transmission Power By measuring the receiving power of Hello message, each node can determine the specific power levels it needs to reach of its neighbors. Two commonly-used propagation models Free Space Sign Meaning Pt Pr Antenna gain of the receiver Wave length d Distance between nodes L System loss ht Antenna height of the transmitter hr 42 Antenna gain of the transmitter Gr Two-Ray Receive power Gt Transmit power Antenna height of the receiver 2018/3/17
LMST – Step 3: Determination of Transmission Power By measuring the receiving power of Hello message, each node can determine the specific power levels it needs to reach of its neighbors. Two commonly-used propagation models Free Space Sign Meaning Pt Pr Antenna gain of the receiver Wave length d Distance between nodes L System loss ht Antenna height of the transmitter hr 42 Antenna gain of the transmitter Gr Two-Ray Receive power Gt Transmit power Antenna height of the receiver 2018/3/17
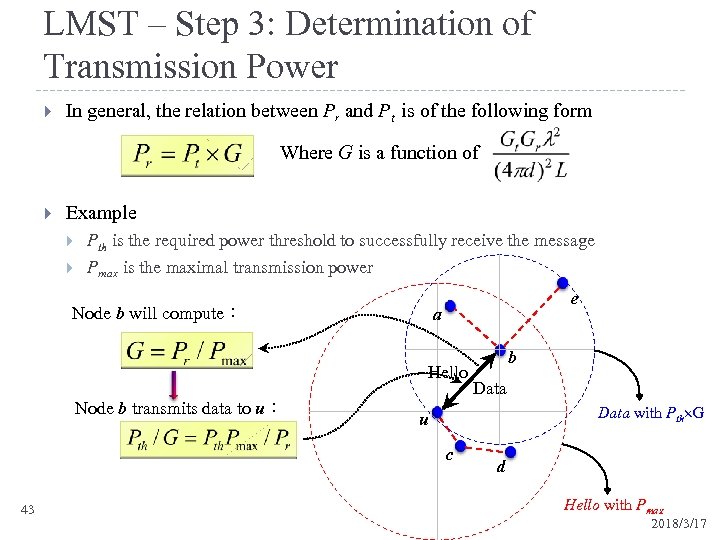 LMST – Step 3: Determination of Transmission Power In general, the relation between Pr and Pt is of the following form Where G is a function of Example Pth is the required power threshold to successfully receive the message Pmax is the maximal transmission power Node b will compute: e a Hello Node b transmits data to u: Data with Pth G u c 43 b d Hello with Pmax 2018/3/17
LMST – Step 3: Determination of Transmission Power In general, the relation between Pr and Pt is of the following form Where G is a function of Example Pth is the required power threshold to successfully receive the message Pmax is the maximal transmission power Node b will compute: e a Hello Node b transmits data to u: Data with Pth G u c 43 b d Hello with Pmax 2018/3/17
 Conclusions Advantages 44 Maintain network connectivity by low energy consumption Reduce the probability of interference Increase the spatial reuse Achieve high throughput 2018/3/17
Conclusions Advantages 44 Maintain network connectivity by low energy consumption Reduce the probability of interference Increase the spatial reuse Achieve high throughput 2018/3/17
 Tree Topology On the Construction of Energy-Efficient Broadcast and Multicast Trees in Wireless Networks J. Wieselthier, G. Nguyen, and A. Ephremides IEEE INFOCOM 2000 45 2018/3/17
Tree Topology On the Construction of Energy-Efficient Broadcast and Multicast Trees in Wireless Networks J. Wieselthier, G. Nguyen, and A. Ephremides IEEE INFOCOM 2000 45 2018/3/17
 Introduction The paper studies the problems of broadcasting and multicasting in wireless networks. To form a minimum-energy tree 46 Energy efficiency Maintain network connectivity 2018/3/17
Introduction The paper studies the problems of broadcasting and multicasting in wireless networks. To form a minimum-energy tree 46 Energy efficiency Maintain network connectivity 2018/3/17
 Network Assumptions The availability of a large number of bandwidth resources. 47 The power level of a transmission can be chosen within a given range of values. Sufficient transceiver resources are available at each of the nodes in the network. 2018/3/17
Network Assumptions The availability of a large number of bandwidth resources. 47 The power level of a transmission can be chosen within a given range of values. Sufficient transceiver resources are available at each of the nodes in the network. 2018/3/17
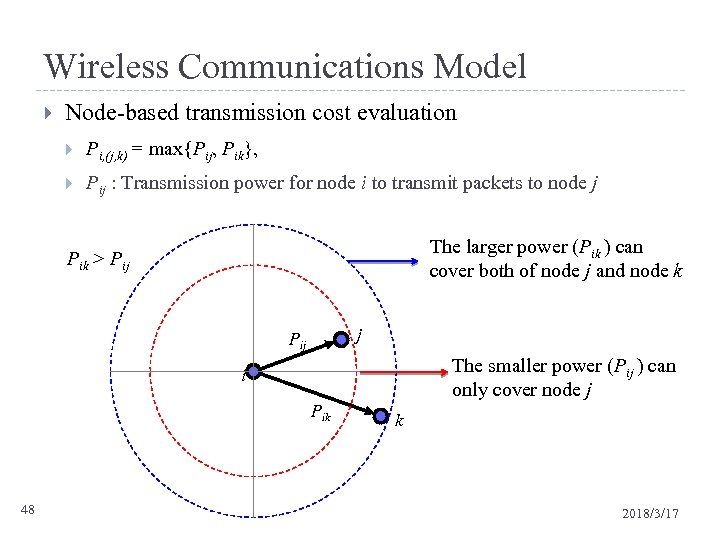 Wireless Communications Model Node-based transmission cost evaluation Pi, (j, k) = max{Pij, Pik}, Pij : Transmission power for node i to transmit packets to node j The larger power (Pik ) can cover both of node j and node k Pik > Pij j Pij The smaller power (Pij ) can only cover node j i Pik 48 k 2018/3/17
Wireless Communications Model Node-based transmission cost evaluation Pi, (j, k) = max{Pij, Pik}, Pij : Transmission power for node i to transmit packets to node j The larger power (Pik ) can cover both of node j and node k Pik > Pij j Pij The smaller power (Pij ) can only cover node j i Pik 48 k 2018/3/17
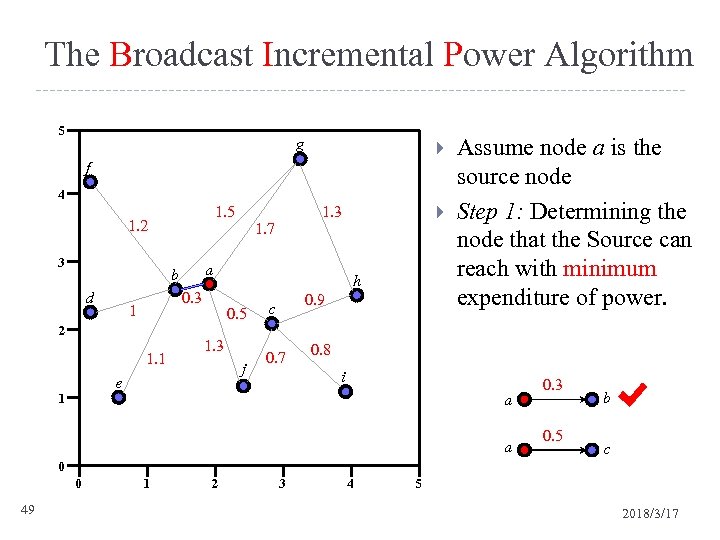 The Broadcast Incremental Power Algorithm 5 g f 4 3 d 0. 3 1 2 1. 1 h 0. 5 1. 3 j e 1 1. 7 a b 1. 3 1. 5 1. 2 0. 9 c 0. 7 Assume node a is the source node Step 1: Determining the node that the Source can reach with minimum expenditure of power. 0. 8 i a a 0. 3 0. 5 b c 0 0 49 1 2 3 4 5 2018/3/17
The Broadcast Incremental Power Algorithm 5 g f 4 3 d 0. 3 1 2 1. 1 h 0. 5 1. 3 j e 1 1. 7 a b 1. 3 1. 5 1. 2 0. 9 c 0. 7 Assume node a is the source node Step 1: Determining the node that the Source can reach with minimum expenditure of power. 0. 8 i a a 0. 3 0. 5 b c 0 0 49 1 2 3 4 5 2018/3/17
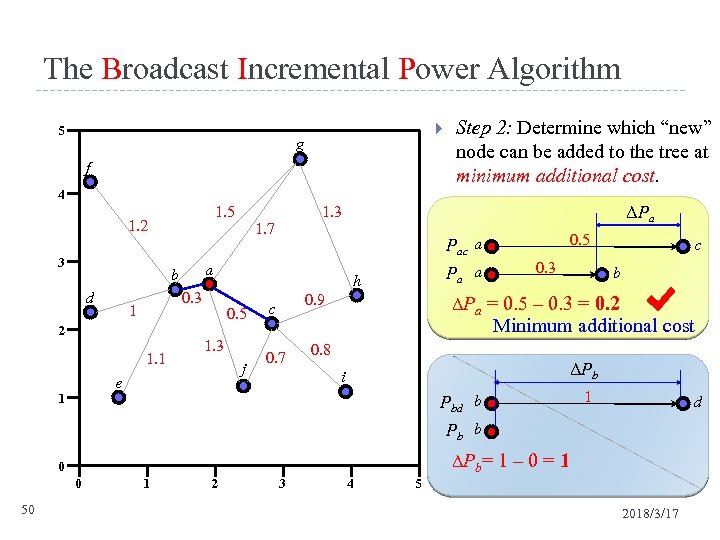 The Broadcast Incremental Power Algorithm 5 g f 4 3 d 0. 3 1 2 1. 1 1. 3 j 0. 5 Pac a Pa a h 0. 5 e 1 1. 7 a b ΔPa 1. 3 1. 5 1. 2 Step 2: Determine which “new” node can be added to the tree at minimum additional cost. 0. 9 c 0. 3 c b ΔPa = 0. 5 – 0. 3 = 0. 2 Minimum additional cost 0. 7 0. 8 ΔPb i Pbd b 1 d Pb b ΔP b = 1 – 0 = 1 0 0 50 1 2 3 4 5 2018/3/17
The Broadcast Incremental Power Algorithm 5 g f 4 3 d 0. 3 1 2 1. 1 1. 3 j 0. 5 Pac a Pa a h 0. 5 e 1 1. 7 a b ΔPa 1. 3 1. 5 1. 2 Step 2: Determine which “new” node can be added to the tree at minimum additional cost. 0. 9 c 0. 3 c b ΔPa = 0. 5 – 0. 3 = 0. 2 Minimum additional cost 0. 7 0. 8 ΔPb i Pbd b 1 d Pb b ΔP b = 1 – 0 = 1 0 0 50 1 2 3 4 5 2018/3/17
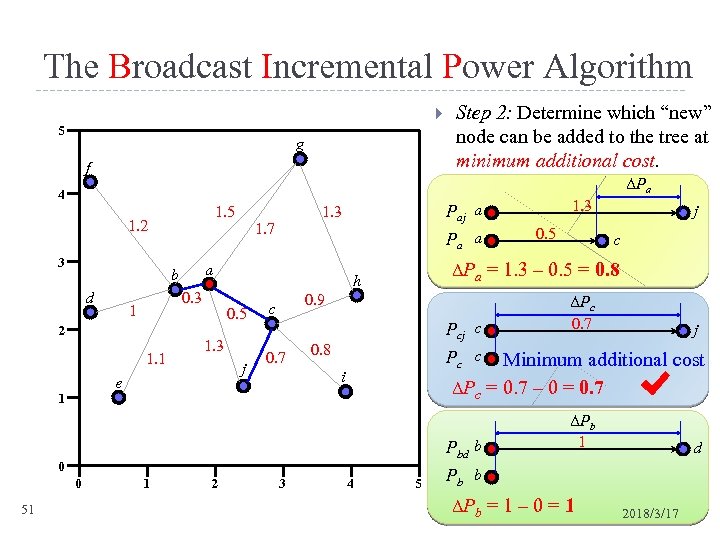 The Broadcast Incremental Power Algorithm 5 g f ΔPa 4 3 d 0. 3 1 2 1. 1 1. 7 Pa a a b 1. 3 j e 0. 9 c 0. 7 Pcj c 0. 8 51 2 i 3 ΔPc 0. 7 j Minimum additional cost ΔPc = 0. 7 – 0 = 0. 7 0 1 c Pc c Pbd b 0 0. 5 j ΔPa = 1. 3 – 0. 5 = 0. 8 h 0. 5 1. 3 Paj a 1. 3 1. 5 1. 2 1 Step 2: Determine which “new” node can be added to the tree at minimum additional cost. 4 5 ΔPb 1 d Pb b ΔP b = 1 – 0 = 1 2018/3/17
The Broadcast Incremental Power Algorithm 5 g f ΔPa 4 3 d 0. 3 1 2 1. 1 1. 7 Pa a a b 1. 3 j e 0. 9 c 0. 7 Pcj c 0. 8 51 2 i 3 ΔPc 0. 7 j Minimum additional cost ΔPc = 0. 7 – 0 = 0. 7 0 1 c Pc c Pbd b 0 0. 5 j ΔPa = 1. 3 – 0. 5 = 0. 8 h 0. 5 1. 3 Paj a 1. 3 1. 5 1. 2 1 Step 2: Determine which “new” node can be added to the tree at minimum additional cost. 4 5 ΔPb 1 d Pb b ΔP b = 1 – 0 = 1 2018/3/17
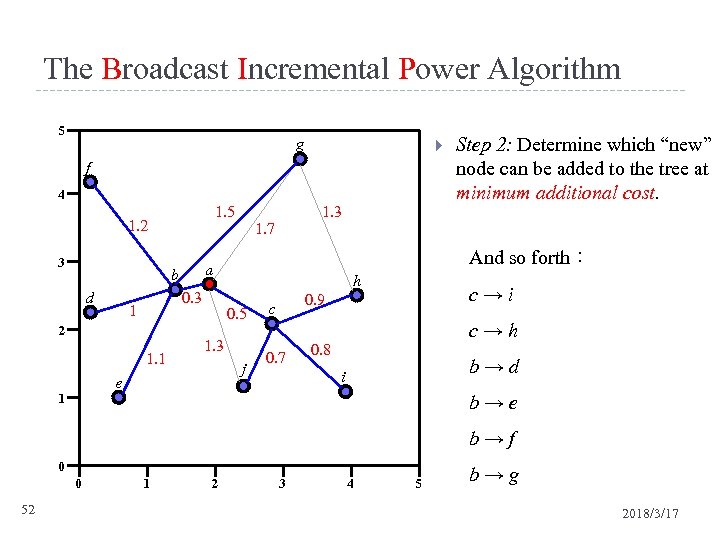 The Broadcast Incremental Power Algorithm 5 g f 4 3 0. 3 1 2 1. 1 And so forth: h 0. 5 1. 3 j e 1 1. 7 a b d 1. 3 1. 5 1. 2 Step 2: Determine which “new” node can be added to the tree at minimum additional cost. c→i 0. 9 c c→h 0. 7 0. 8 b→d i b→e b→f 0 0 52 1 2 3 4 5 b→g 2018/3/17
The Broadcast Incremental Power Algorithm 5 g f 4 3 0. 3 1 2 1. 1 And so forth: h 0. 5 1. 3 j e 1 1. 7 a b d 1. 3 1. 5 1. 2 Step 2: Determine which “new” node can be added to the tree at minimum additional cost. c→i 0. 9 c c→h 0. 7 0. 8 b→d i b→e b→f 0 0 52 1 2 3 4 5 b→g 2018/3/17
 The Broadcast Incremental Power Algorithm BIP is similar in principle to Prim’s algorithm. One fundamental difference: 53 The inputs to Prim’s algorithm are the link cost Pij. BIP must dynamically update the costs at each step. 2018/3/17
The Broadcast Incremental Power Algorithm BIP is similar in principle to Prim’s algorithm. One fundamental difference: 53 The inputs to Prim’s algorithm are the link cost Pij. BIP must dynamically update the costs at each step. 2018/3/17
 Conclusions Propose a centralized algorithm: The Broadcast Incremental Power(BIP) Algorithm Advantages 54 Improved performance can be obtained when exploiting the properties of the wireless medium Energy-efficient 2018/3/17
Conclusions Propose a centralized algorithm: The Broadcast Incremental Power(BIP) Algorithm Advantages 54 Improved performance can be obtained when exploiting the properties of the wireless medium Energy-efficient 2018/3/17
 Outline 5. 1. Motivation and Goals 5. 2. Power Control and Energy Conservation 5. 3. Tree Topology 5. 4. k-hop Connected Dominating Set 5. 5. Adaptive node activity 5. 6. Conclusions 55 2018/3/17
Outline 5. 1. Motivation and Goals 5. 2. Power Control and Energy Conservation 5. 3. Tree Topology 5. 4. k-hop Connected Dominating Set 5. 5. Adaptive node activity 5. 6. Conclusions 55 2018/3/17
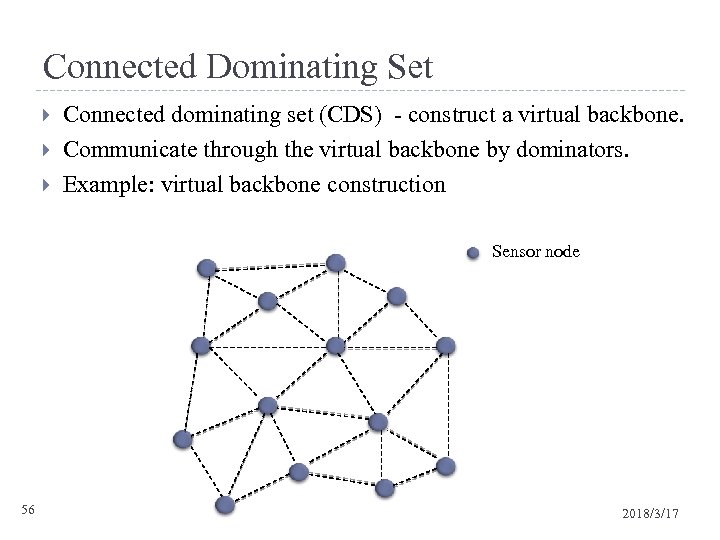 Connected Dominating Set Connected dominating set (CDS) - construct a virtual backbone. Communicate through the virtual backbone by dominators. Example: virtual backbone construction Sensor node 56 2018/3/17
Connected Dominating Set Connected dominating set (CDS) - construct a virtual backbone. Communicate through the virtual backbone by dominators. Example: virtual backbone construction Sensor node 56 2018/3/17
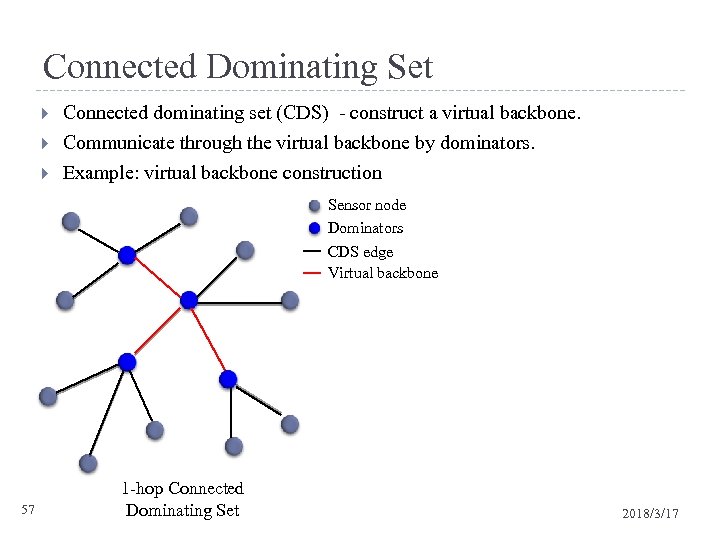 Connected Dominating Set Connected dominating set (CDS) - construct a virtual backbone. Communicate through the virtual backbone by dominators. Example: virtual backbone construction Sensor node Dominators CDS edge Virtual backbone 57 1 -hop Connected Dominating Set 2018/3/17
Connected Dominating Set Connected dominating set (CDS) - construct a virtual backbone. Communicate through the virtual backbone by dominators. Example: virtual backbone construction Sensor node Dominators CDS edge Virtual backbone 57 1 -hop Connected Dominating Set 2018/3/17
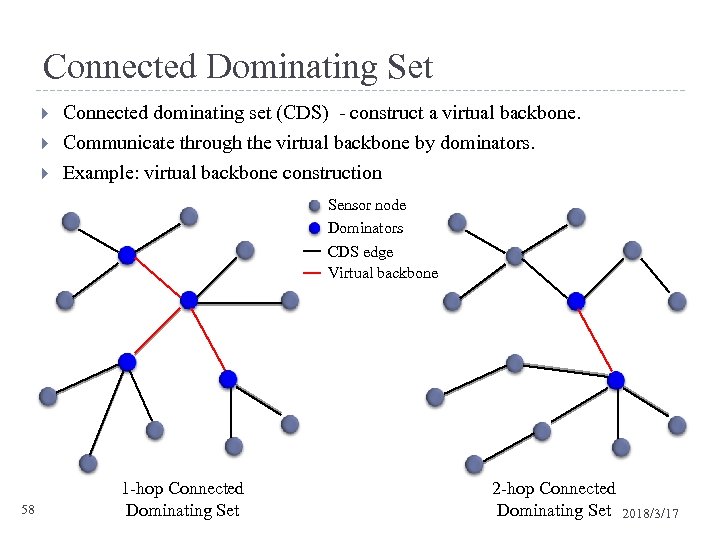 Connected Dominating Set Connected dominating set (CDS) - construct a virtual backbone. Communicate through the virtual backbone by dominators. Example: virtual backbone construction Sensor node Dominators CDS edge Virtual backbone 58 1 -hop Connected Dominating Set 2018/3/17
Connected Dominating Set Connected dominating set (CDS) - construct a virtual backbone. Communicate through the virtual backbone by dominators. Example: virtual backbone construction Sensor node Dominators CDS edge Virtual backbone 58 1 -hop Connected Dominating Set 2018/3/17
 A Hardness Result 59 The MDS (minimum dominating set) problem is NP-hard, it is even a hard problem to approximate in general. For the case of unit disk graphs, it is possible to find a Polynomial Time Approximation Scheme (PTAS). 2018/3/17
A Hardness Result 59 The MDS (minimum dominating set) problem is NP-hard, it is even a hard problem to approximate in general. For the case of unit disk graphs, it is possible to find a Polynomial Time Approximation Scheme (PTAS). 2018/3/17
 k-hop Connected Dominating Set On Calculating Power-Aware Connected Dominating Sets for Efficient Routing in Ad Hoc Wireless Networks Jie Wu, Fei Dai, Ming Gao, and Ivan Stojmenovic Journal of Communications and Networks 2002 60 2018/3/17
k-hop Connected Dominating Set On Calculating Power-Aware Connected Dominating Sets for Efficient Routing in Ad Hoc Wireless Networks Jie Wu, Fei Dai, Ming Gao, and Ivan Stojmenovic Journal of Communications and Networks 2002 60 2018/3/17
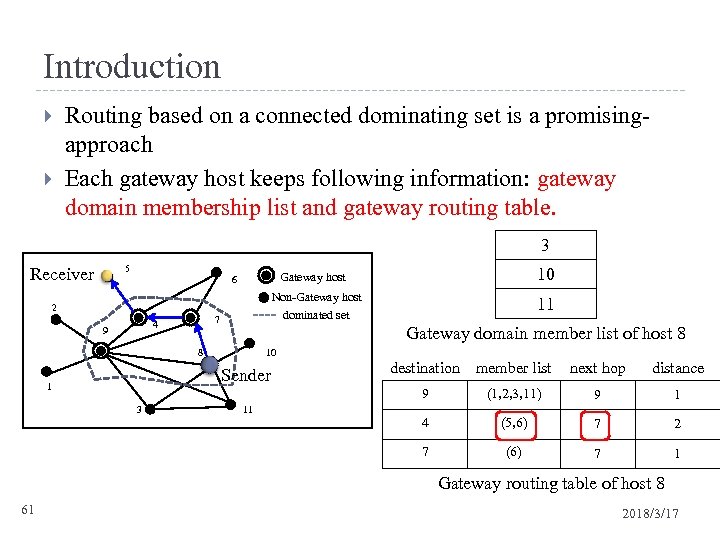 Introduction Routing based on a connected dominating set is a promisingapproach Each gateway host keeps following information: gateway domain membership list and gateway routing table. 3 5 Receiver Non-Gateway host dominated set 2 7 4 9 11 Gateway domain member list of host 8 8 10 Sender 1 10 Gateway host 6 destination member list next hop distance 9 11 9 1 4 (5, 6) 7 2 7 3 (1, 2, 3, 11) (6) 7 1 Gateway routing table of host 8 61 2018/3/17
Introduction Routing based on a connected dominating set is a promisingapproach Each gateway host keeps following information: gateway domain membership list and gateway routing table. 3 5 Receiver Non-Gateway host dominated set 2 7 4 9 11 Gateway domain member list of host 8 8 10 Sender 1 10 Gateway host 6 destination member list next hop distance 9 11 9 1 4 (5, 6) 7 2 7 3 (1, 2, 3, 11) (6) 7 1 Gateway routing table of host 8 61 2018/3/17
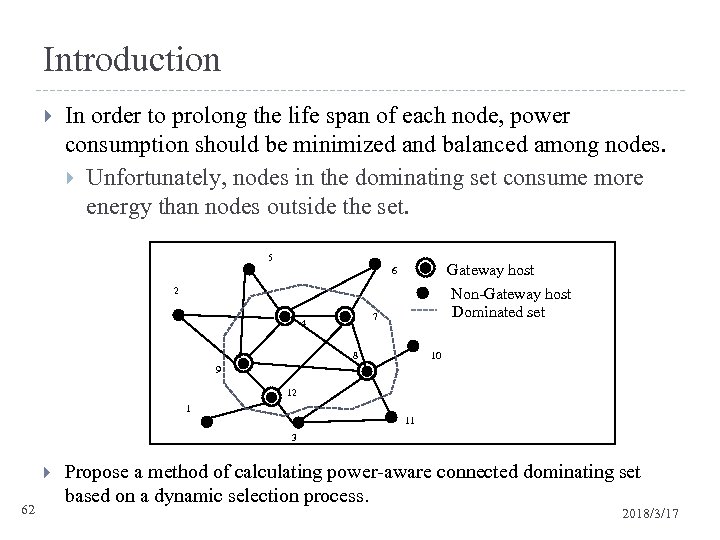 Introduction In order to prolong the life span of each node, power consumption should be minimized and balanced among nodes. Unfortunately, nodes in the dominating set consume more energy than nodes outside the set. 5 Gateway host Non-Gateway host Dominated set 6 2 7 4 8 10 9 12 1 11 3 62 Propose a method of calculating power-aware connected dominating set based on a dynamic selection process. 2018/3/17
Introduction In order to prolong the life span of each node, power consumption should be minimized and balanced among nodes. Unfortunately, nodes in the dominating set consume more energy than nodes outside the set. 5 Gateway host Non-Gateway host Dominated set 6 2 7 4 8 10 9 12 1 11 3 62 Propose a method of calculating power-aware connected dominating set based on a dynamic selection process. 2018/3/17
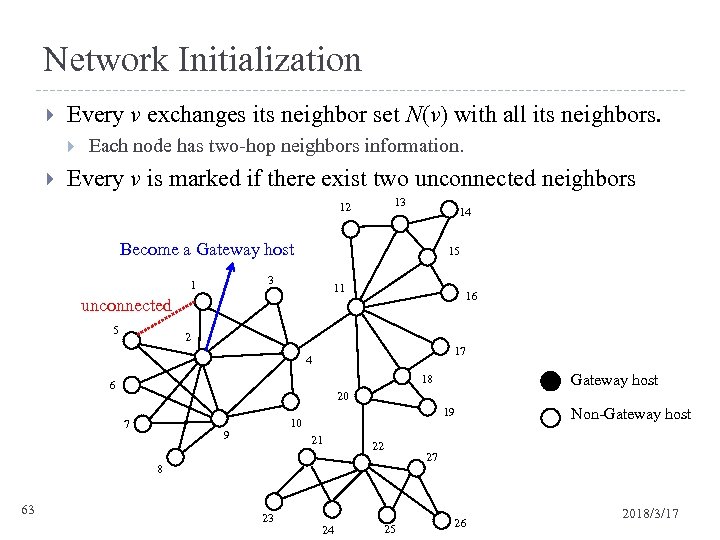 Network Initialization Every v exchanges its neighbor set N(v) with all its neighbors. Each node has two-hop neighbors information. Every v is marked if there exist two unconnected neighbors 13 12 14 Become a Gateway host 15 3 1 11 16 unconnected 5 2 17 4 20 7 19 10 9 21 22 23 24 Non-Gateway host 27 8 63 Gateway host 18 6 25 26 2018/3/17
Network Initialization Every v exchanges its neighbor set N(v) with all its neighbors. Each node has two-hop neighbors information. Every v is marked if there exist two unconnected neighbors 13 12 14 Become a Gateway host 15 3 1 11 16 unconnected 5 2 17 4 20 7 19 10 9 21 22 23 24 Non-Gateway host 27 8 63 Gateway host 18 6 25 26 2018/3/17
 Gateways Selection (Rules 1 and 2) 64 2018/3/17
Gateways Selection (Rules 1 and 2) 64 2018/3/17
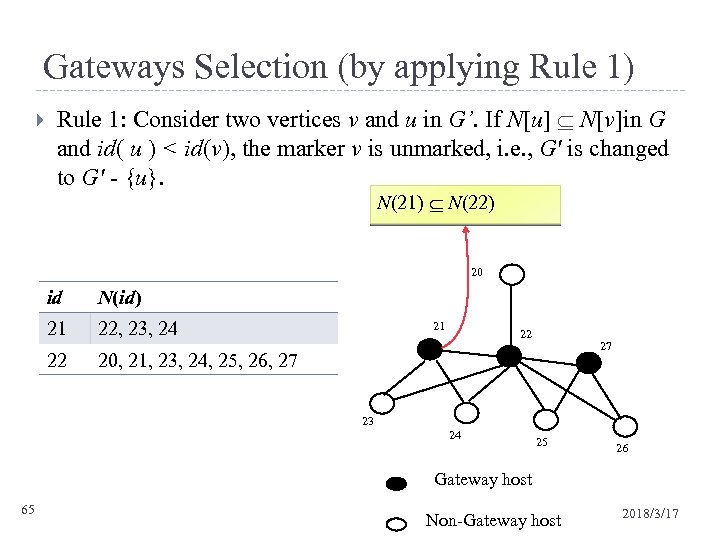 Gateways Selection (by applying Rule 1) Rule 1: Consider two vertices v and u in G’. If N[u] N[v]in G and id( u ) < id(v), the marker v is unmarked, i. e. , G' is changed to G' - {u}. N(21) N(22) 20 id N(id) 21 22, 23, 24 22 21 22 27 20, 21, 23, 24, 25, 26, 27 23 24 25 26 Gateway host 65 Non-Gateway host 2018/3/17
Gateways Selection (by applying Rule 1) Rule 1: Consider two vertices v and u in G’. If N[u] N[v]in G and id( u ) < id(v), the marker v is unmarked, i. e. , G' is changed to G' - {u}. N(21) N(22) 20 id N(id) 21 22, 23, 24 22 21 22 27 20, 21, 23, 24, 25, 26, 27 23 24 25 26 Gateway host 65 Non-Gateway host 2018/3/17
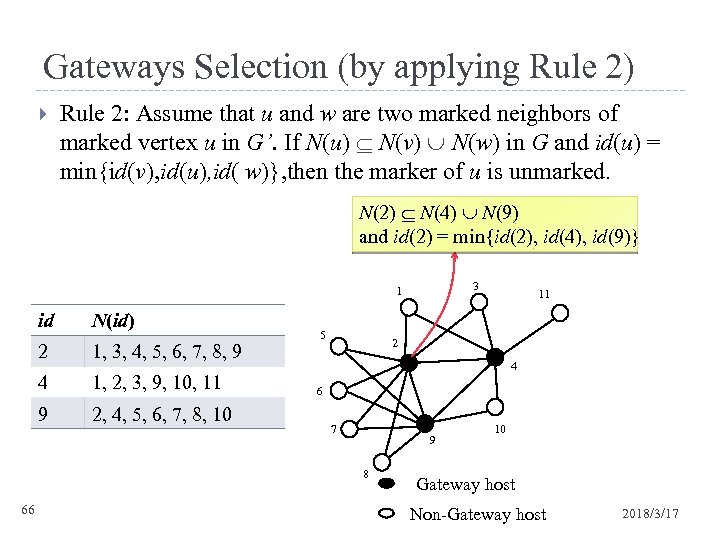 Gateways Selection (by applying Rule 2) Rule 2: Assume that u and w are two marked neighbors of marked vertex u in G’. If N(u) N(v) N(w) in G and id(u) = min{id(v), id(u), id( w)}, then the marker of u is unmarked. N(2) N(4) N(9) and id(2) = min{id(2), id(4), id(9)} 3 1 id N(id) 2 1, 3, 4, 5, 6, 7, 8, 9 4 1, 2, 3, 9, 10, 11 9 2, 4, 5, 6, 7, 8, 10 5 2 4 6 7 9 8 66 11 10 Gateway host Non-Gateway host 2018/3/17
Gateways Selection (by applying Rule 2) Rule 2: Assume that u and w are two marked neighbors of marked vertex u in G’. If N(u) N(v) N(w) in G and id(u) = min{id(v), id(u), id( w)}, then the marker of u is unmarked. N(2) N(4) N(9) and id(2) = min{id(2), id(4), id(9)} 3 1 id N(id) 2 1, 3, 4, 5, 6, 7, 8, 9 4 1, 2, 3, 9, 10, 11 9 2, 4, 5, 6, 7, 8, 10 5 2 4 6 7 9 8 66 11 10 Gateway host Non-Gateway host 2018/3/17
 Extended Rules Several extended approaches for selective removal 67 The node-degree-based approach aims at reducing the size of the connected dominating set The energy-level-based approach tries to prolong the average life span of each node. 2018/3/17
Extended Rules Several extended approaches for selective removal 67 The node-degree-based approach aims at reducing the size of the connected dominating set The energy-level-based approach tries to prolong the average life span of each node. 2018/3/17
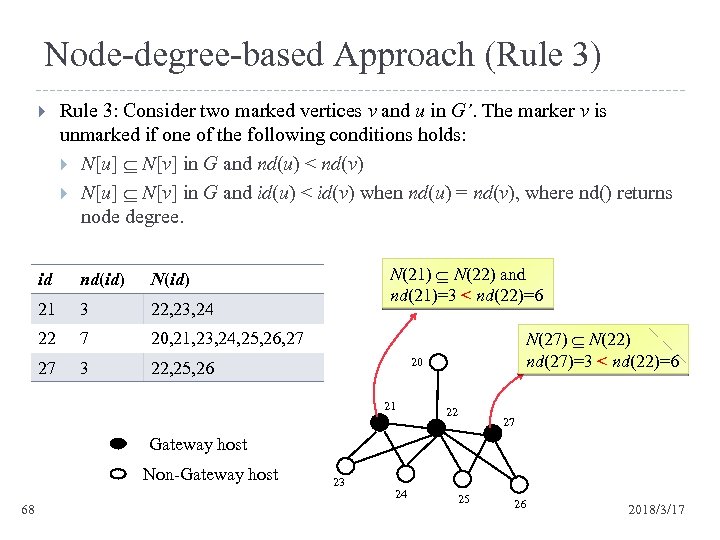 Node-degree-based Approach (Rule 3) Rule 3: Consider two marked vertices v and u in G’. The marker v is unmarked if one of the following conditions holds: N[u] N[v] in G and nd(u) < nd(v) N[u] N[v] in G and id(u) < id(v) when nd(u) = nd(v), where nd() returns node degree. id nd(id) 21 3 22, 23, 24 22 7 20, 21, 23, 24, 25, 26, 27 27 3 N(21) N(22) and nd(21)=3 < nd(22)=6 N(id) 22, 25, 26 N(27) N(22) nd(27)=3 < nd(22)=6 20 21 22 27 Gateway host Non-Gateway host 68 23 24 25 26 2018/3/17
Node-degree-based Approach (Rule 3) Rule 3: Consider two marked vertices v and u in G’. The marker v is unmarked if one of the following conditions holds: N[u] N[v] in G and nd(u) < nd(v) N[u] N[v] in G and id(u) < id(v) when nd(u) = nd(v), where nd() returns node degree. id nd(id) 21 3 22, 23, 24 22 7 20, 21, 23, 24, 25, 26, 27 27 3 N(21) N(22) and nd(21)=3 < nd(22)=6 N(id) 22, 25, 26 N(27) N(22) nd(27)=3 < nd(22)=6 20 21 22 27 Gateway host Non-Gateway host 68 23 24 25 26 2018/3/17
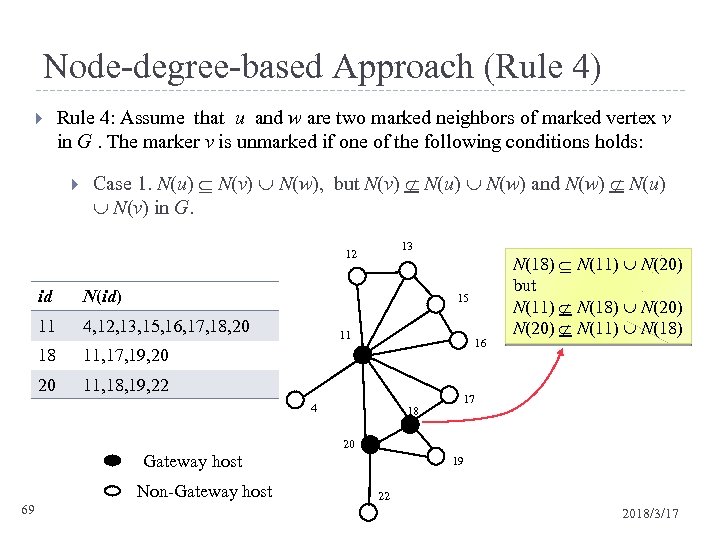 Node-degree-based Approach (Rule 4) Rule 4: Assume that u and w are two marked neighbors of marked vertex v in G. The marker v is unmarked if one of the following conditions holds: Case 1. N(u) N(v) N(w), but N(v) N(u) N(w) and N(w) N(u) N(v) in G. 13 12 id N(id) 11 4, 12, 13, 15, 16, 17, 18, 20 15 18 16 11, 17, 19, 20 20 11 11, 18, 19, 22 4 Gateway host Non-Gateway host 69 18 N(18) N(11) N(20) but N(11) N(18) N(20) N(11) N(18) 17 20 19 22 2018/3/17
Node-degree-based Approach (Rule 4) Rule 4: Assume that u and w are two marked neighbors of marked vertex v in G. The marker v is unmarked if one of the following conditions holds: Case 1. N(u) N(v) N(w), but N(v) N(u) N(w) and N(w) N(u) N(v) in G. 13 12 id N(id) 11 4, 12, 13, 15, 16, 17, 18, 20 15 18 16 11, 17, 19, 20 20 11 11, 18, 19, 22 4 Gateway host Non-Gateway host 69 18 N(18) N(11) N(20) but N(11) N(18) N(20) N(11) N(18) 17 20 19 22 2018/3/17
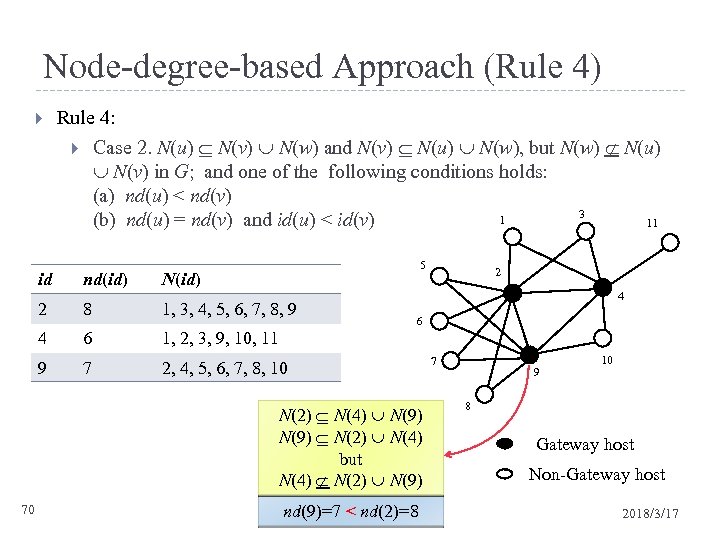 Node-degree-based Approach (Rule 4) Rule 4: Case 2. N(u) N(v) N(w) and N(v) N(u) N(w), but N(w) N(u) N(v) in G; and one of the following conditions holds: (a) nd(u) < nd(v) 3 1 (b) nd(u) = nd(v) and id(u) < id(v) 11 5 id nd(id) N(id) 2 8 1, 3, 4, 5, 6, 7, 8, 9 4 6 1, 2, 3, 9, 10, 11 9 7 2, 4, 5, 6, 7, 8, 10 4 6 N(2) N(4) N(9) N(2) N(4) but N(4) N(2) N(9) 70 2 nd(9)=7 < nd(2)=8 7 9 10 8 Gateway host Non-Gateway host 2018/3/17
Node-degree-based Approach (Rule 4) Rule 4: Case 2. N(u) N(v) N(w) and N(v) N(u) N(w), but N(w) N(u) N(v) in G; and one of the following conditions holds: (a) nd(u) < nd(v) 3 1 (b) nd(u) = nd(v) and id(u) < id(v) 11 5 id nd(id) N(id) 2 8 1, 3, 4, 5, 6, 7, 8, 9 4 6 1, 2, 3, 9, 10, 11 9 7 2, 4, 5, 6, 7, 8, 10 4 6 N(2) N(4) N(9) N(2) N(4) but N(4) N(2) N(9) 70 2 nd(9)=7 < nd(2)=8 7 9 10 8 Gateway host Non-Gateway host 2018/3/17
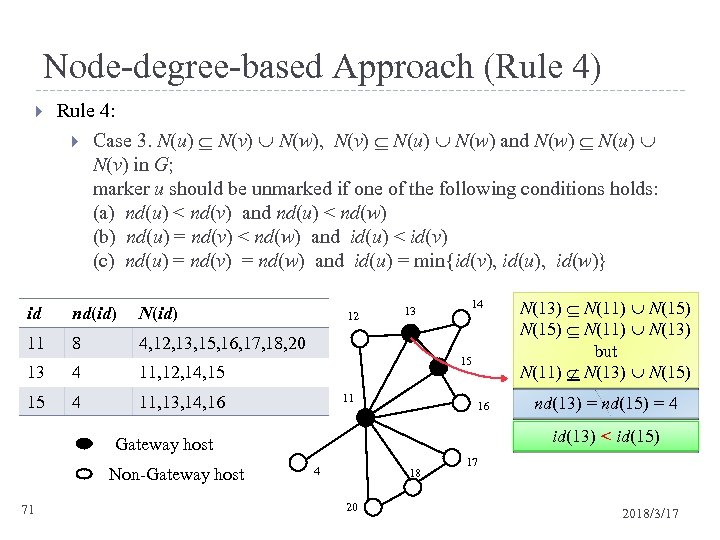 Node-degree-based Approach (Rule 4) Rule 4: Case 3. N(u) N(v) N(w), N(v) N(u) N(w) and N(w) N(u) N(v) in G; marker u should be unmarked if one of the following conditions holds: (a) nd(u) < nd(v) and nd(u) < nd(w) (b) nd(u) = nd(v) < nd(w) and id(u) < id(v) (c) nd(u) = nd(v) = nd(w) and id(u) = min{id(v), id(u), id(w)} id nd(id) N(id) 11 8 13 4 11, 12, 14, 15 15 4 11, 13, 14, 16 14 4, 12, 13, 15, 16, 17, 18, 20 12 13 15 11 16 71 nd(13) = nd(15) = 4 id(13) < id(15) Gateway host Non-Gateway host N(13) N(11) N(15) N(11) N(13) but N(11) N(13) N(15) 4 18 20 17 2018/3/17
Node-degree-based Approach (Rule 4) Rule 4: Case 3. N(u) N(v) N(w), N(v) N(u) N(w) and N(w) N(u) N(v) in G; marker u should be unmarked if one of the following conditions holds: (a) nd(u) < nd(v) and nd(u) < nd(w) (b) nd(u) = nd(v) < nd(w) and id(u) < id(v) (c) nd(u) = nd(v) = nd(w) and id(u) = min{id(v), id(u), id(w)} id nd(id) N(id) 11 8 13 4 11, 12, 14, 15 15 4 11, 13, 14, 16 14 4, 12, 13, 15, 16, 17, 18, 20 12 13 15 11 16 71 nd(13) = nd(15) = 4 id(13) < id(15) Gateway host Non-Gateway host N(13) N(11) N(15) N(11) N(13) but N(11) N(13) N(15) 4 18 20 17 2018/3/17
 Energy-level-based Approach (Rules 5、 6、 7、 8) Energy-level-based rules 72 Let EL denote energy level Rules 5, 6 Similar to rules 1 and 2, the only difference is to compare EL prior to node ID. Rules 7, 8 Similar to rules 3 and 4 The only difference: when nodes u and v have the same EL, they compare ND prior to node ID. 2018/3/17
Energy-level-based Approach (Rules 5、 6、 7、 8) Energy-level-based rules 72 Let EL denote energy level Rules 5, 6 Similar to rules 1 and 2, the only difference is to compare EL prior to node ID. Rules 7, 8 Similar to rules 3 and 4 The only difference: when nodes u and v have the same EL, they compare ND prior to node ID. 2018/3/17
 Conclusions Advantages 73 Overall energy consumption is balanced A relatively small connected dominating set is generated 2018/3/17
Conclusions Advantages 73 Overall energy consumption is balanced A relatively small connected dominating set is generated 2018/3/17
 Outline 5. 1. Motivation and Goals 5. 2. Power Control and Energy Conservation 5. 3. Tree Topology 5. 4. k-hop Connected Dominating Set 5. 5. Adaptive node activity 5. 6. Conclusions 74 2018/3/17
Outline 5. 1. Motivation and Goals 5. 2. Power Control and Energy Conservation 5. 3. Tree Topology 5. 4. k-hop Connected Dominating Set 5. 5. Adaptive node activity 5. 6. Conclusions 74 2018/3/17
 What’s Adaptive Node Activity? Influence the topology of a graph by Selecting certain nodes to be turned on or Selecting certain nodes to be turned off 75 An operation that of course also fits well into the context of clustering or backbone mechanisms. Nodes that are sources or sinks of data are always kept active 2018/3/17
What’s Adaptive Node Activity? Influence the topology of a graph by Selecting certain nodes to be turned on or Selecting certain nodes to be turned off 75 An operation that of course also fits well into the context of clustering or backbone mechanisms. Nodes that are sources or sinks of data are always kept active 2018/3/17
 Adaptive node activity Geography-Informed Energy Conservation for Ad Hoc Routing Y. Xu, J. Heidemann, and D. Estrin ACM/IEEE Mobi. Com 2001 76 2018/3/17
Adaptive node activity Geography-Informed Energy Conservation for Ad Hoc Routing Y. Xu, J. Heidemann, and D. Estrin ACM/IEEE Mobi. Com 2001 76 2018/3/17
 Introduction Motivation Goal 77 Nodes consume high energy during routing, especially during transmission Reduce the energy consumption in ad hoc wireless networks Increase the network lifetime Identifies equivalent nodes for routing Based on location information Turns off unnecessary nodes Load balancing energy usage Lifetime of all nodes remain as long as possible 2018/3/17
Introduction Motivation Goal 77 Nodes consume high energy during routing, especially during transmission Reduce the energy consumption in ad hoc wireless networks Increase the network lifetime Identifies equivalent nodes for routing Based on location information Turns off unnecessary nodes Load balancing energy usage Lifetime of all nodes remain as long as possible 2018/3/17
 Geographical Adaptive Fidelity(GAF) Routing 78 Distribute routing duties by electing new local leaders periodically. Leaders (active nodes) handle all routing traffic, allowing other nodes to sleep for extended periods of time and conserve energy. 2018/3/17
Geographical Adaptive Fidelity(GAF) Routing 78 Distribute routing duties by electing new local leaders periodically. Leaders (active nodes) handle all routing traffic, allowing other nodes to sleep for extended periods of time and conserve energy. 2018/3/17
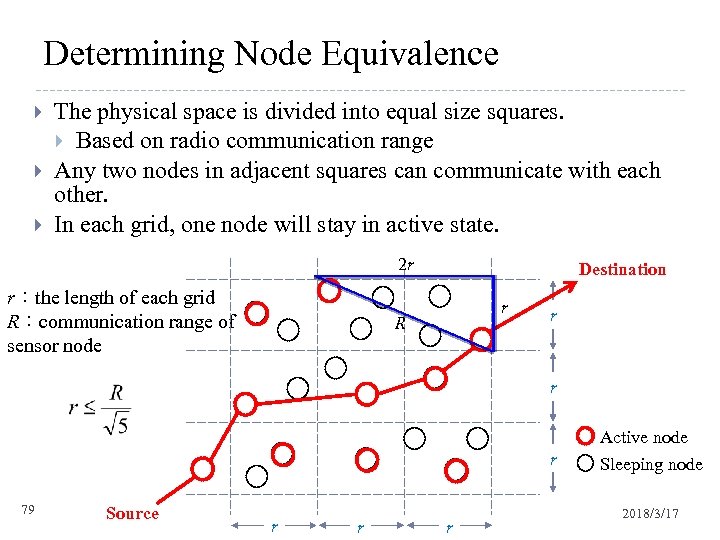 Determining Node Equivalence The physical space is divided into equal size squares. Based on radio communication range Any two nodes in adjacent squares can communicate with each other. In each grid, one node will stay in active state. 2 r r:the length of each grid R:communication range of sensor node Destination r R r r Active node r 79 Source r r r Sleeping node 2018/3/17
Determining Node Equivalence The physical space is divided into equal size squares. Based on radio communication range Any two nodes in adjacent squares can communicate with each other. In each grid, one node will stay in active state. 2 r r:the length of each grid R:communication range of sensor node Destination r R r r Active node r 79 Source r r r Sleeping node 2018/3/17
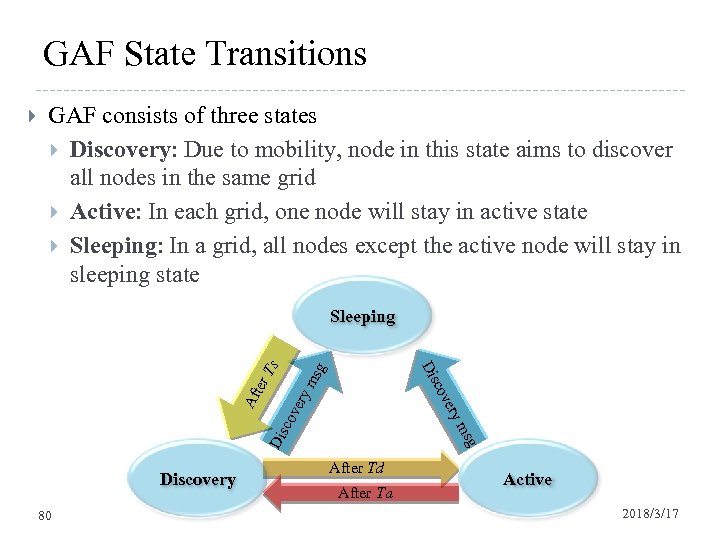 GAF State Transitions GAF consists of three states Discovery: Due to mobility, node in this state aims to discover all nodes in the same grid Active: In each grid, one node will stay in active state Sleeping: In a grid, all nodes except the active node will stay in sleeping state g ms Dis g ms cov ery ov ter c Dis Ts Sleeping Af Discovery 80 After Td After Ta Active 2018/3/17
GAF State Transitions GAF consists of three states Discovery: Due to mobility, node in this state aims to discover all nodes in the same grid Active: In each grid, one node will stay in active state Sleeping: In a grid, all nodes except the active node will stay in sleeping state g ms Dis g ms cov ery ov ter c Dis Ts Sleeping Af Discovery 80 After Td After Ta Active 2018/3/17
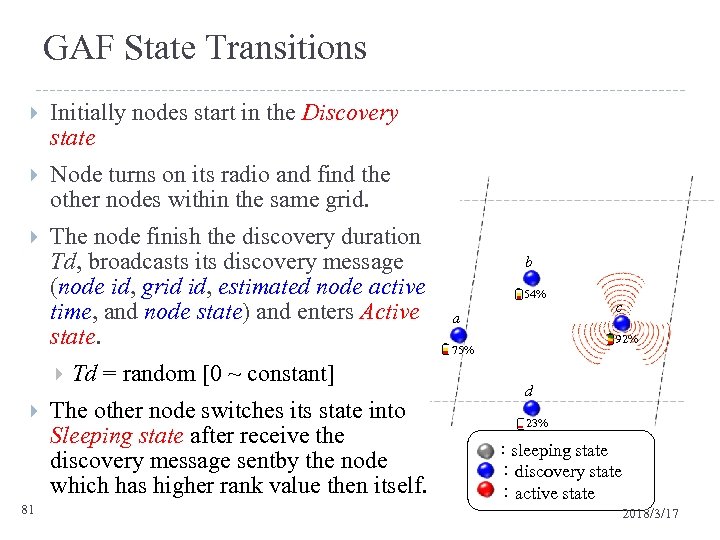 GAF State Transitions Initially nodes start in the Discovery state Node turns on its radio and find the other nodes within the same grid. The node finish the discovery duration Td, broadcasts its discovery message (node id, grid id, estimated node active time, and node state) and enters Active state. 81 Td = random [0 ~ constant] The other node switches its state into Sleeping state after receive the discovery message sentby the node which has higher rank value then itself. b 54% a c 92% 75% d 23% :sleeping state :discovery state :active state 2018/3/17
GAF State Transitions Initially nodes start in the Discovery state Node turns on its radio and find the other nodes within the same grid. The node finish the discovery duration Td, broadcasts its discovery message (node id, grid id, estimated node active time, and node state) and enters Active state. 81 Td = random [0 ~ constant] The other node switches its state into Sleeping state after receive the discovery message sentby the node which has higher rank value then itself. b 54% a c 92% 75% d 23% :sleeping state :discovery state :active state 2018/3/17
 Node Ranking Rule Given any two node i and j Ranki > Rankj , if and only if (enati > enatj) enat = estimated node active time duration , when enlt larger than a threshold , when enlt becomes less than a threshold (enlt = expected node lifetime) If node’s lifetime is less than a threshold, stay active state until energy exhaustion. If node’s lifetime is larger than a threshold, balancing the remain energy to avoid frequent switches between active/sleep states. 82 2018/3/17
Node Ranking Rule Given any two node i and j Ranki > Rankj , if and only if (enati > enatj) enat = estimated node active time duration , when enlt larger than a threshold , when enlt becomes less than a threshold (enlt = expected node lifetime) If node’s lifetime is less than a threshold, stay active state until energy exhaustion. If node’s lifetime is larger than a threshold, balancing the remain energy to avoid frequent switches between active/sleep states. 82 2018/3/17
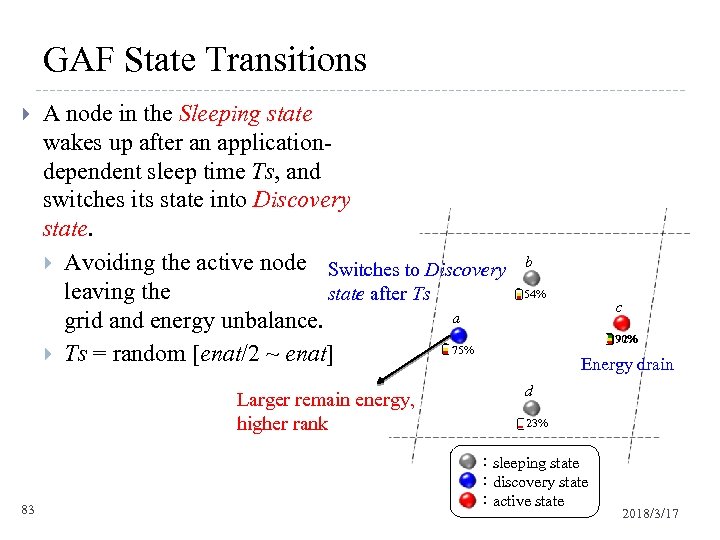 GAF State Transitions A node in the Sleeping state wakes up after an applicationdependent sleep time Ts, and switches its state into Discovery state. Avoiding the active node Switches to Discovery leaving the state after Ts a grid and energy unbalance. 75% Ts = random [enat/2 ~ enat] Larger remain energy, higher rank 83 b 54% c 70% 92% Energy drain d 23% :sleeping state :discovery state :active state 2018/3/17
GAF State Transitions A node in the Sleeping state wakes up after an applicationdependent sleep time Ts, and switches its state into Discovery state. Avoiding the active node Switches to Discovery leaving the state after Ts a grid and energy unbalance. 75% Ts = random [enat/2 ~ enat] Larger remain energy, higher rank 83 b 54% c 70% 92% Energy drain d 23% :sleeping state :discovery state :active state 2018/3/17
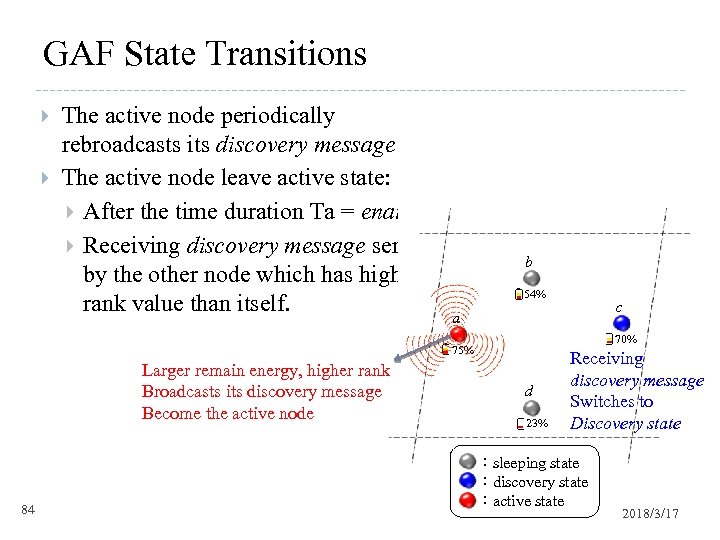 GAF State Transitions The active node periodically rebroadcasts its discovery message The active node leave active state: After the time duration Ta = enat. Receiving discovery message send by the other node which has higher rank value than itself. b 54% 70% 75% Larger remain energy, higher rank Broadcasts its discovery message Become the active node 84 c a d 23% Receiving discovery message Switches to Discovery state :sleeping state :discovery state :active state 2018/3/17
GAF State Transitions The active node periodically rebroadcasts its discovery message The active node leave active state: After the time duration Ta = enat. Receiving discovery message send by the other node which has higher rank value than itself. b 54% 70% 75% Larger remain energy, higher rank Broadcasts its discovery message Become the active node 84 c a d 23% Receiving discovery message Switches to Discovery state :sleeping state :discovery state :active state 2018/3/17
 Conclusions Distribute routing duties by electing new local leaders periodically 85 GAF increases the network lifetime without decreases the performance substantially All nodes remain up for as long as possible 2018/3/17
Conclusions Distribute routing duties by electing new local leaders periodically 85 GAF increases the network lifetime without decreases the performance substantially All nodes remain up for as long as possible 2018/3/17
 Conclusions Various approaches exist to adjust the topology of a network to a desired shape Most of them produce some non-negligible overhead 86 Some distributed coordination among neighbors require additional information. Constructed structures can turn out to be somewhat brittle and the overhead might be wasted. Benefits have to be carefully weighted against risks for the particular scenario at hand 2018/3/17
Conclusions Various approaches exist to adjust the topology of a network to a desired shape Most of them produce some non-negligible overhead 86 Some distributed coordination among neighbors require additional information. Constructed structures can turn out to be somewhat brittle and the overhead might be wasted. Benefits have to be carefully weighted against risks for the particular scenario at hand 2018/3/17
 References R. Ramanathan and R. Rosales-Hain. Topology Control of Multihop Wireless Networks using Transmit Power Adjustment. In Proceedings of IEEE Infocom, pages 404– 413, Tel-Aviv, Israel, March 2000 N. Li, J. C. Hou, and L. Sha. Design and Analysis of an MST-Based Topology Control Algorithm. In Proceedings of IEEE INFOCOM, San Francisco, CA, March 2003 J. Wieselthier, G. Nguyen, and A. Ephremides, On the Construction of Energy-Efficient Broadcast and Multicast Trees in Wireless Networks, in Proc. IEEE Infocom’ 2000, Tel Aviv, Israel, pp. 585– 594, 2000 Jie Wu, Fei Dai, Ming Gao, and Ivan Stojmenovic, On Calculating Power-Aware Connected Dominating Sets for Efficient Routing in Ad Hoc Wireless Networks, Journal of Communications and Networks, vol. 4, No. 1, march 2002 B. Chen, K. Jamieson, H. Balakrishnan, and R. Morris. Span: An Energy-Efficient Coordination Algorithm for Topology Maintenance in Ad Hoc Wireless Networks, 8(5): 481– 494, 2002 Y. Xu, J. Heidemann, and D. Estrin. Geography-Informed Energy Conservation for Ad Hoc Routing. In Proceedings of the 7 th Annual International Conference on Mobile Computing and Networking (Mobi. Com), pages 70– 84, Rome, Italy, July 2001. ACM. ) 87 2018/3/17
References R. Ramanathan and R. Rosales-Hain. Topology Control of Multihop Wireless Networks using Transmit Power Adjustment. In Proceedings of IEEE Infocom, pages 404– 413, Tel-Aviv, Israel, March 2000 N. Li, J. C. Hou, and L. Sha. Design and Analysis of an MST-Based Topology Control Algorithm. In Proceedings of IEEE INFOCOM, San Francisco, CA, March 2003 J. Wieselthier, G. Nguyen, and A. Ephremides, On the Construction of Energy-Efficient Broadcast and Multicast Trees in Wireless Networks, in Proc. IEEE Infocom’ 2000, Tel Aviv, Israel, pp. 585– 594, 2000 Jie Wu, Fei Dai, Ming Gao, and Ivan Stojmenovic, On Calculating Power-Aware Connected Dominating Sets for Efficient Routing in Ad Hoc Wireless Networks, Journal of Communications and Networks, vol. 4, No. 1, march 2002 B. Chen, K. Jamieson, H. Balakrishnan, and R. Morris. Span: An Energy-Efficient Coordination Algorithm for Topology Maintenance in Ad Hoc Wireless Networks, 8(5): 481– 494, 2002 Y. Xu, J. Heidemann, and D. Estrin. Geography-Informed Energy Conservation for Ad Hoc Routing. In Proceedings of the 7 th Annual International Conference on Mobile Computing and Networking (Mobi. Com), pages 70– 84, Rome, Italy, July 2001. ACM. ) 87 2018/3/17


