 Chapter 5: Security Architecture
Chapter 5: Security Architecture
 Architecture (281)
Architecture (281)
 CPU (281)
CPU (281)
 CPU (285)
CPU (285)
 Multiprocessing (286)
Multiprocessing (286)
 Process management (287)
Process management (287)
 Multi-programming (288)
Multi-programming (288)
 Multi-programming (290)
Multi-programming (290)
 Multi-programming (291)
Multi-programming (291)
 A thread (292)
A thread (292)
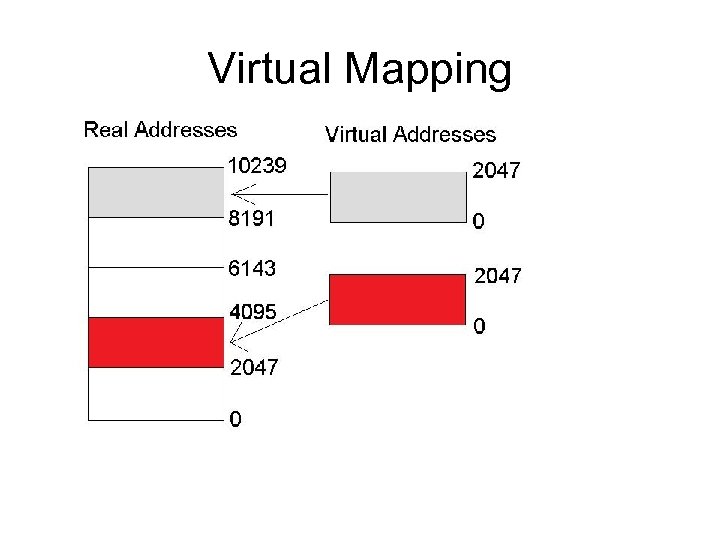 Virtual Mapping
Virtual Mapping
 Memory Management (296)
Memory Management (296)
 Memory Management (297)
Memory Management (297)
 Memory Management
Memory Management
 Memory Types (298)
Memory Types (298)
 Memory Types (298)
Memory Types (298)
 Other Memory Terms (305)
Other Memory Terms (305)
 Virtual Machines
Virtual Machines
 I/O device management
I/O device management
 Done with Computing and OS Terms
Done with Computing and OS Terms
 System Architecture (321)
System Architecture (321)
 Security Terms
Security Terms
 Security Perimeter (326)
Security Perimeter (326)
 Reference Monitor (327)
Reference Monitor (327)
 Security Kernel (327)
Security Kernel (327)
 System Security Models
System Security Models
 System Security Model (330)
System Security Model (330)
 System Security Model
System Security Model
 Systems Security Models
Systems Security Models
 State Machine model
State Machine model
 Bell-La. Padula Model (333)
Bell-La. Padula Model (333)
 B-LP (333)
B-LP (333)
 B-LP (334)
B-LP (334)
 Biba Model
Biba Model
 Biba (336)
Biba (336)
 Clark Wilson (338)
Clark Wilson (338)
 Clark Wilson (339)
Clark Wilson (339)
 Clark Wilson (341)
Clark Wilson (341)
 Clark Wilson (341)
Clark Wilson (341)
 Covert Channels
Covert Channels
 Covert Channels (343)
Covert Channels (343)
 Non Interference Model (345)
Non Interference Model (345)
 Non-Interference
Non-Interference
 Lattice Model
Lattice Model
 Brewer Nash / Chinese Wall
Brewer Nash / Chinese Wall
 Graham-Denning Model (349)
Graham-Denning Model (349)
 GD model (349)
GD model (349)
 End of Specific Security Models
End of Specific Security Models
 Security Modes
Security Modes
 Security Modes of Operation
Security Modes of Operation
 Dedicated Security Mode (352)
Dedicated Security Mode (352)
 Multilevel Security Mode
Multilevel Security Mode
 Guards (353)
Guards (353)
 Let’s recap the Security Modes
Let’s recap the Security Modes
 Trust and Assurance
Trust and Assurance
 Trust and Assurance (355)
Trust and Assurance (355)
 Trust and Assurance (356)
Trust and Assurance (356)
 Trust and Assurance
Trust and Assurance
 Orange Book / TCSEC (357)
Orange Book / TCSEC (357)
 TCSEC (357)
TCSEC (357)
 TSEC (357)
TSEC (357)
 TCSEC rating (D) (359)
TCSEC rating (D) (359)
 TCSEC C (359)
TCSEC C (359)
 TCSEC wrap up
TCSEC wrap up
 TCSEC wrap up
TCSEC wrap up
 Rainbow series (361)
Rainbow series (361)
 ITSEC (364)
ITSEC (364)
 ITSEC (365)
ITSEC (365)
 ITSEC (365)
ITSEC (365)
 Common Criteria (366)
Common Criteria (366)
 CC (367)
CC (367)
 CC (367)
CC (367)
 Enough of Trust and Assurance already!
Enough of Trust and Assurance already!
 C vs. A (369)
C vs. A (369)
 Accreditation
Accreditation
 Accreditation
Accreditation
 Attacks
Attacks