f011f52e57bf5acb526d9d40b222a6cc.ppt
- Количество слайдов: 33
 Chapter 31 Network Security 31. 1 Copyright © The Mc. Graw-Hill Companies, Inc. Permission required for reproduction or display.
Chapter 31 Network Security 31. 1 Copyright © The Mc. Graw-Hill Companies, Inc. Permission required for reproduction or display.
 31 -1 SECURITY SERVICES Network security can provide five services. Four of these services are related to the message exchanged using the network. The fifth service provides entity authentication or identification. Topics discussed in this section: Message Confidentiality Message Integrity Message Authentication Message Nonrepudiation Entity Authentication 31. 2
31 -1 SECURITY SERVICES Network security can provide five services. Four of these services are related to the message exchanged using the network. The fifth service provides entity authentication or identification. Topics discussed in this section: Message Confidentiality Message Integrity Message Authentication Message Nonrepudiation Entity Authentication 31. 2
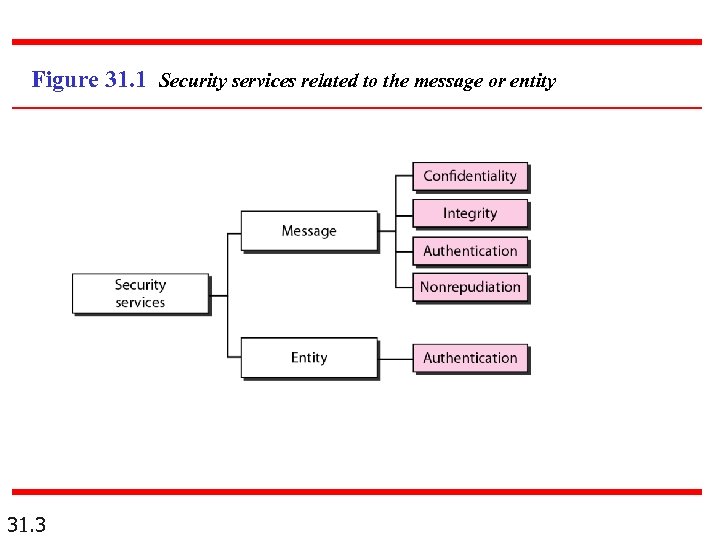 Figure 31. 1 Security services related to the message or entity 31. 3
Figure 31. 1 Security services related to the message or entity 31. 3
 31 -3 MESSAGE INTEGRITY Encryption and decryption provide secrecy, or confidentiality, but not integrity. However, on occasion we may not even need secrecy, but instead must have integrity. Topics discussed in this section: Document and Fingerprint Message and Message Digest Creating and Checking the Digest Hash Function Criteria Hash Algorithms: SHA-1 31. 4
31 -3 MESSAGE INTEGRITY Encryption and decryption provide secrecy, or confidentiality, but not integrity. However, on occasion we may not even need secrecy, but instead must have integrity. Topics discussed in this section: Document and Fingerprint Message and Message Digest Creating and Checking the Digest Hash Function Criteria Hash Algorithms: SHA-1 31. 4
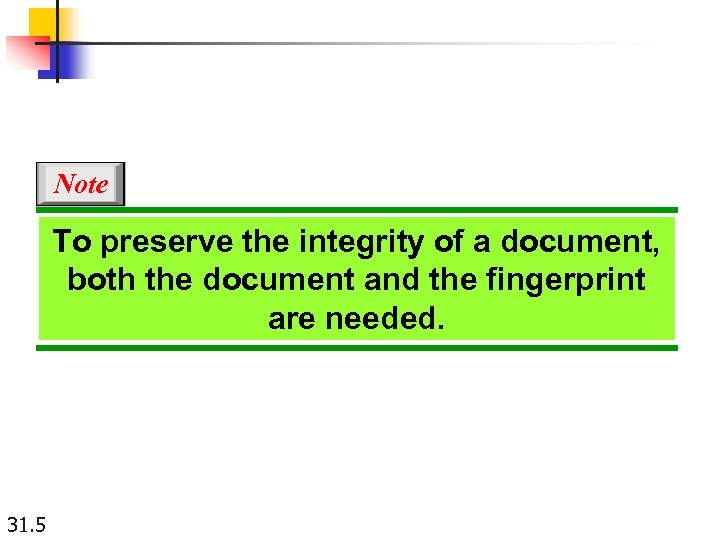 Note To preserve the integrity of a document, both the document and the fingerprint are needed. 31. 5
Note To preserve the integrity of a document, both the document and the fingerprint are needed. 31. 5
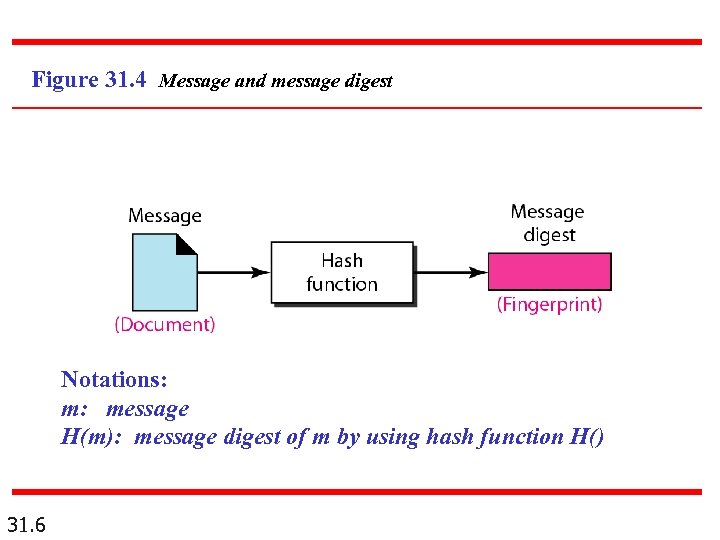 Figure 31. 4 Message and message digest Notations: m: message H(m): message digest of m by using hash function H() 31. 6
Figure 31. 4 Message and message digest Notations: m: message H(m): message digest of m by using hash function H() 31. 6
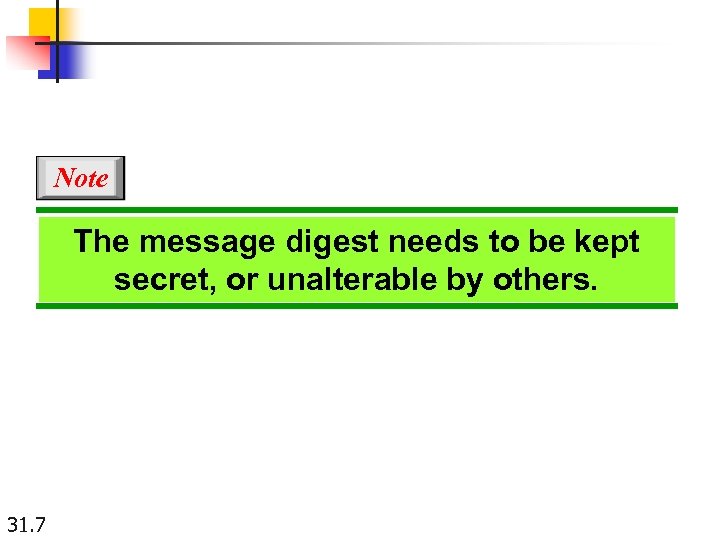 Note The message digest needs to be kept secret, or unalterable by others. 31. 7
Note The message digest needs to be kept secret, or unalterable by others. 31. 7
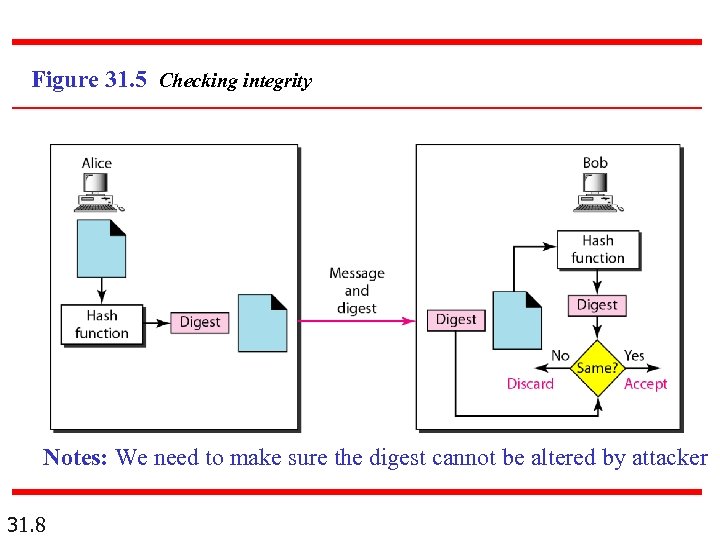 Figure 31. 5 Checking integrity Notes: We need to make sure the digest cannot be altered by attacker 31. 8
Figure 31. 5 Checking integrity Notes: We need to make sure the digest cannot be altered by attacker 31. 8
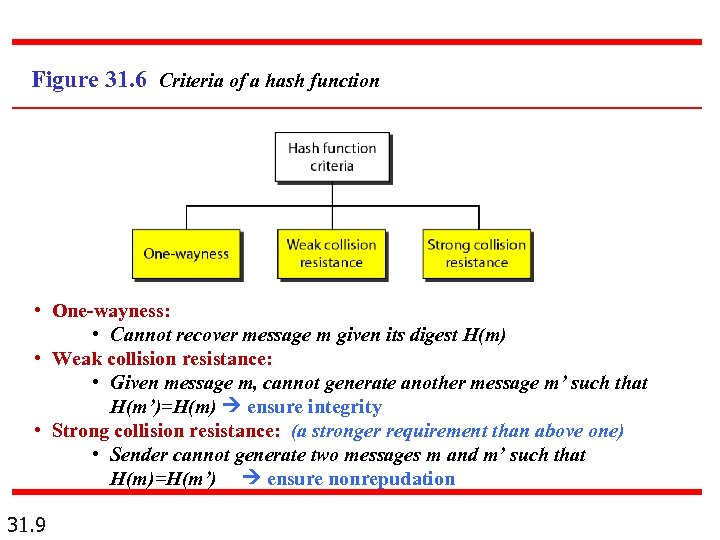 Figure 31. 6 Criteria of a hash function • One-wayness: • Cannot recover message m given its digest H(m) • Weak collision resistance: • Given message m, cannot generate another message m’ such that H(m’)=H(m) ensure integrity • Strong collision resistance: (a stronger requirement than above one) • Sender cannot generate two messages m and m’ such that H(m)=H(m’) ensure nonrepudation 31. 9
Figure 31. 6 Criteria of a hash function • One-wayness: • Cannot recover message m given its digest H(m) • Weak collision resistance: • Given message m, cannot generate another message m’ such that H(m’)=H(m) ensure integrity • Strong collision resistance: (a stronger requirement than above one) • Sender cannot generate two messages m and m’ such that H(m)=H(m’) ensure nonrepudation 31. 9
 Example 31. 1 Can we use a conventional lossless compression method as a hashing function? Solution We cannot. A lossless compression method creates a compressed message that is reversible. You can uncompress the compressed message to get the original one. 31. 10
Example 31. 1 Can we use a conventional lossless compression method as a hashing function? Solution We cannot. A lossless compression method creates a compressed message that is reversible. You can uncompress the compressed message to get the original one. 31. 10
 Example 31. 2 Can we use a checksum method as a hashing function? Solution We cannot. A checksum function is not reversible; it meets the first criterion. However, it does not meet the other criteria. That is to say, an attacker can easily modify a message without being detected. 31. 11
Example 31. 2 Can we use a checksum method as a hashing function? Solution We cannot. A checksum function is not reversible; it meets the first criterion. However, it does not meet the other criteria. That is to say, an attacker can easily modify a message without being detected. 31. 11
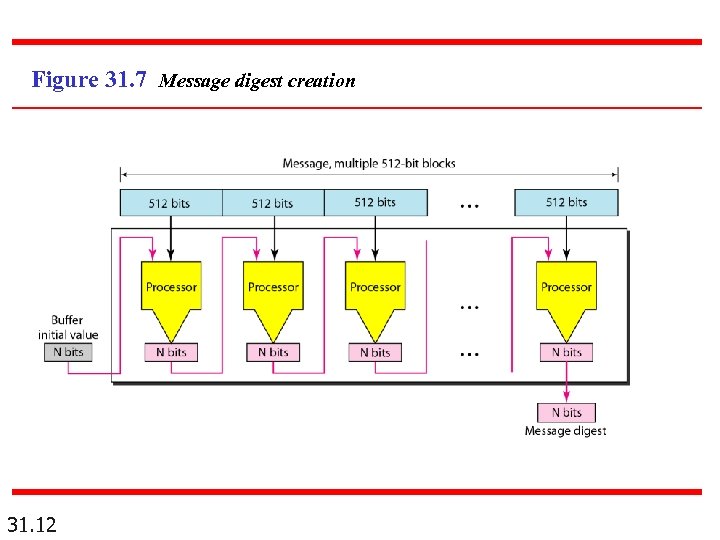 Figure 31. 7 Message digest creation 31. 12
Figure 31. 7 Message digest creation 31. 12
 Note SHA-1 hash algorithms create an N-bit message digest out of a message of 512 -bit blocks. SHA-1 has a message digest of 160 bits. Another popular hash algorithm is MD 5 (message digest algorithm 5). It is an older generation than SHA-1. 31. 13
Note SHA-1 hash algorithms create an N-bit message digest out of a message of 512 -bit blocks. SHA-1 has a message digest of 160 bits. Another popular hash algorithm is MD 5 (message digest algorithm 5). It is an older generation than SHA-1. 31. 13
 31 -4 MESSAGE AUTHENTICATION A hash function per se cannot provide authentication. The digest created by a hash function can detect any modification in the message, but not authentication. Topics discussed in this section: MAC (message authentication code): can be used to ensure both integrity and authentication 31. 14
31 -4 MESSAGE AUTHENTICATION A hash function per se cannot provide authentication. The digest created by a hash function can detect any modification in the message, but not authentication. Topics discussed in this section: MAC (message authentication code): can be used to ensure both integrity and authentication 31. 14
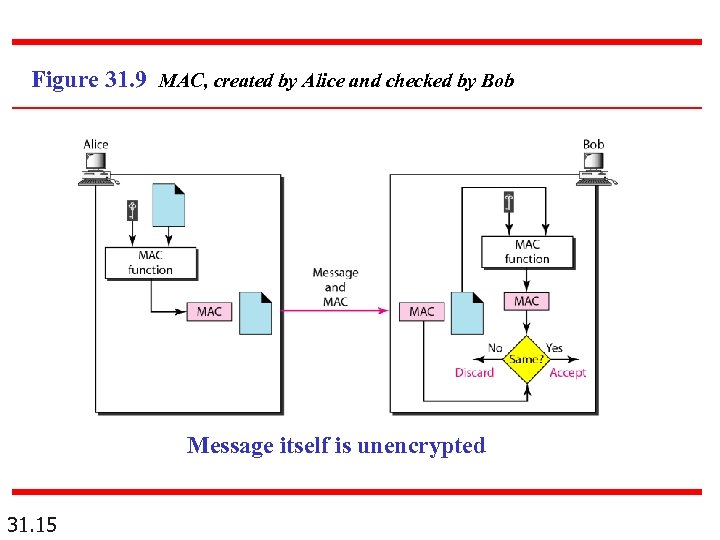 Figure 31. 9 MAC, created by Alice and checked by Bob Message itself is unencrypted 31. 15
Figure 31. 9 MAC, created by Alice and checked by Bob Message itself is unencrypted 31. 15
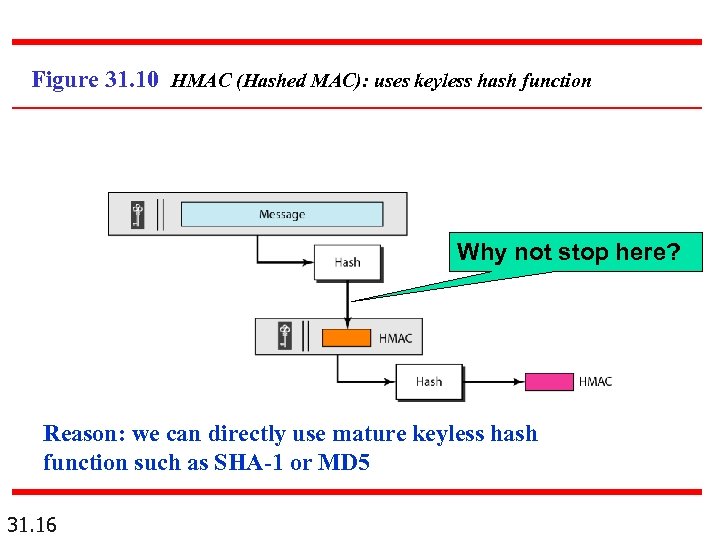 Figure 31. 10 HMAC (Hashed MAC): uses keyless hash function Why not stop here? Reason: we can directly use mature keyless hash function such as SHA-1 or MD 5 31. 16
Figure 31. 10 HMAC (Hashed MAC): uses keyless hash function Why not stop here? Reason: we can directly use mature keyless hash function such as SHA-1 or MD 5 31. 16
 31 -5 DIGITAL SIGNATURE When Alice sends a message to Bob, Bob needs to check the authenticity of the sender; he needs to be sure that the message comes from Alice and not Eve. Bob can ask Alice to sign the message electronically. In other words, an electronic signature can prove the authenticity of Alice as the sender of the message. We refer to this type of signature as a digital signature. Topics discussed in this section: Comparison Need for Keys Process 31. 17
31 -5 DIGITAL SIGNATURE When Alice sends a message to Bob, Bob needs to check the authenticity of the sender; he needs to be sure that the message comes from Alice and not Eve. Bob can ask Alice to sign the message electronically. In other words, an electronic signature can prove the authenticity of Alice as the sender of the message. We refer to this type of signature as a digital signature. Topics discussed in this section: Comparison Need for Keys Process 31. 17
 Note A digital signature needs a public-key system. Notations: m: message H(m): message digest of m by using hash function H() KA- : Private key of user A KA+ : Public key of user A KAB: Symmetric key between A and B K(m): ciphertext of message m by using encryption key K 31. 18
Note A digital signature needs a public-key system. Notations: m: message H(m): message digest of m by using hash function H() KA- : Private key of user A KA+ : Public key of user A KAB: Symmetric key between A and B K(m): ciphertext of message m by using encryption key K 31. 18
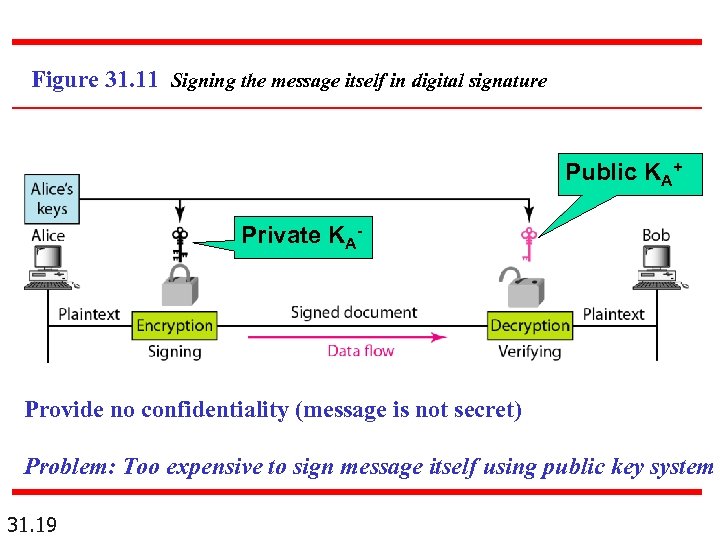 Figure 31. 11 Signing the message itself in digital signature Public KA+ Private KA- Provide no confidentiality (message is not secret) Problem: Too expensive to sign message itself using public key system 31. 19
Figure 31. 11 Signing the message itself in digital signature Public KA+ Private KA- Provide no confidentiality (message is not secret) Problem: Too expensive to sign message itself using public key system 31. 19
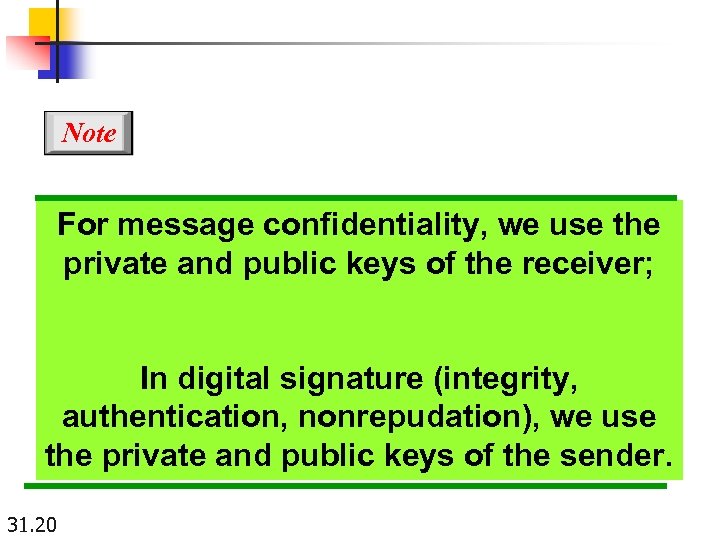 Note For message confidentiality, we use the private and public keys of the receiver; In digital signature (integrity, authentication, nonrepudation), we use the private and public keys of the sender. 31. 20
Note For message confidentiality, we use the private and public keys of the receiver; In digital signature (integrity, authentication, nonrepudation), we use the private and public keys of the sender. 31. 20
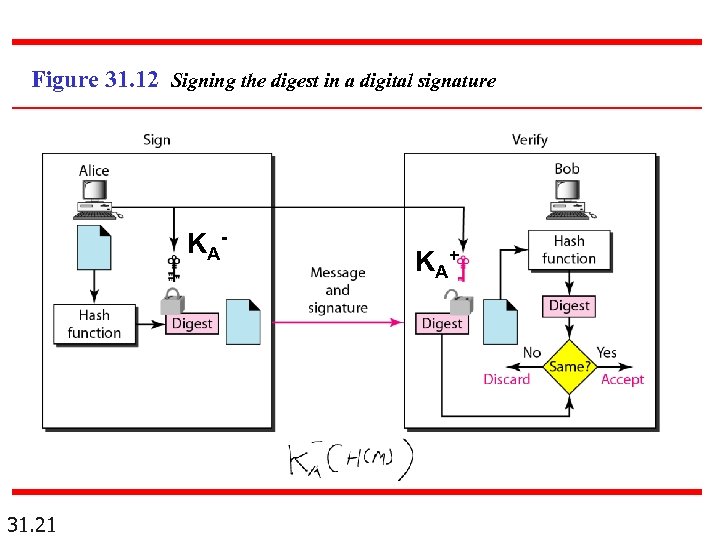 Figure 31. 12 Signing the digest in a digital signature K A- 31. 21 K A+
Figure 31. 12 Signing the digest in a digital signature K A- 31. 21 K A+
 Digital signature provides three out of the five services we mentioned for security systems üIntegrity üAuthentication üNonrepudiation 31. 22
Digital signature provides three out of the five services we mentioned for security systems üIntegrity üAuthentication üNonrepudiation 31. 22
 31 -7 KEY MANAGEMENT We never discussed how secret keys in symmetric-key cryptography and how public keys in asymmetric-key cryptography are distributed and maintained. In this section, we touch on these two issues. We first discuss the distribution of symmetric keys; we then discuss the distribution of asymmetric keys. Topics discussed in this section: Symmetric-Key Distribution Public-Key Distribution 31. 23
31 -7 KEY MANAGEMENT We never discussed how secret keys in symmetric-key cryptography and how public keys in asymmetric-key cryptography are distributed and maintained. In this section, we touch on these two issues. We first discuss the distribution of symmetric keys; we then discuss the distribution of asymmetric keys. Topics discussed in this section: Symmetric-Key Distribution Public-Key Distribution 31. 23
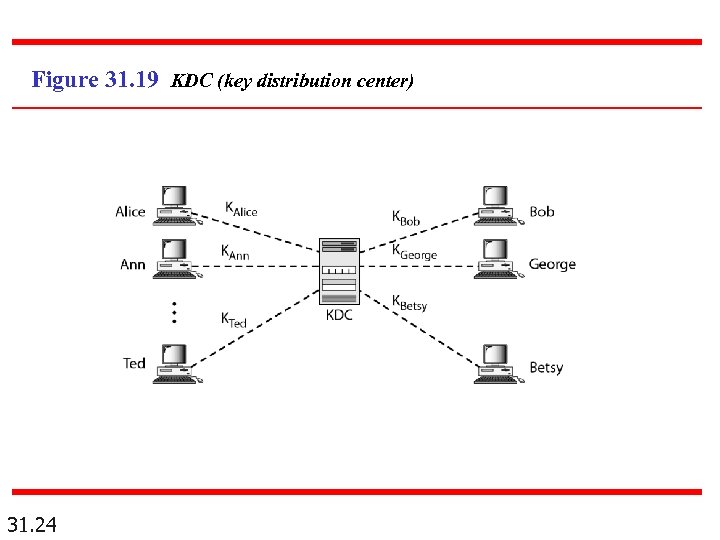 Figure 31. 19 KDC (key distribution center) 31. 24
Figure 31. 19 KDC (key distribution center) 31. 24
 Note A session symmetric key between two parties is used only once. 31. 25
Note A session symmetric key between two parties is used only once. 31. 25
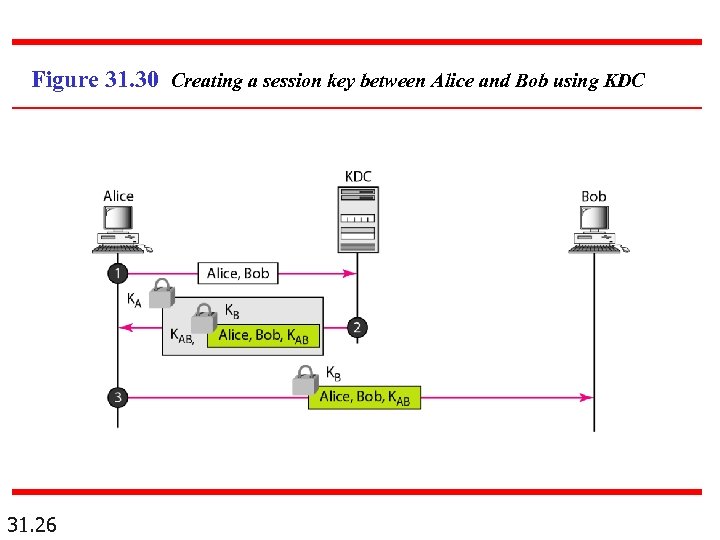 Figure 31. 30 Creating a session key between Alice and Bob using KDC 31. 26
Figure 31. 30 Creating a session key between Alice and Bob using KDC 31. 26
 Note In public-key cryptography, everyone has access to everyone’s public key; public keys are available to the public. 31. 27
Note In public-key cryptography, everyone has access to everyone’s public key; public keys are available to the public. 31. 27
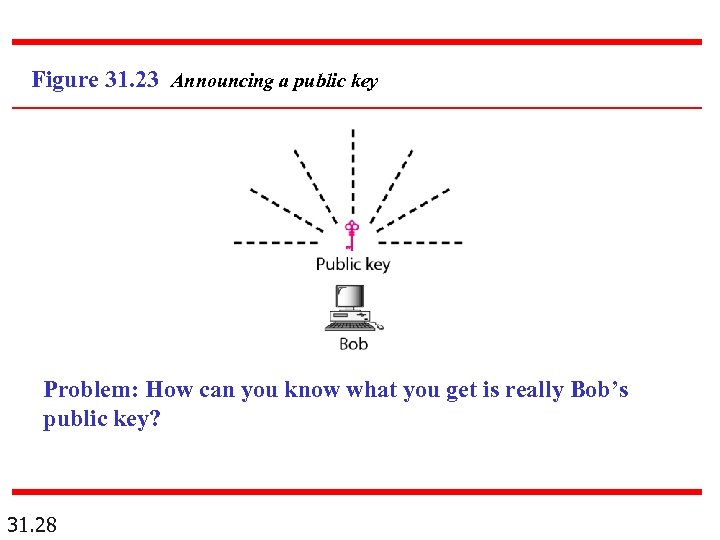 Figure 31. 23 Announcing a public key Problem: How can you know what you get is really Bob’s public key? 31. 28
Figure 31. 23 Announcing a public key Problem: How can you know what you get is really Bob’s public key? 31. 28
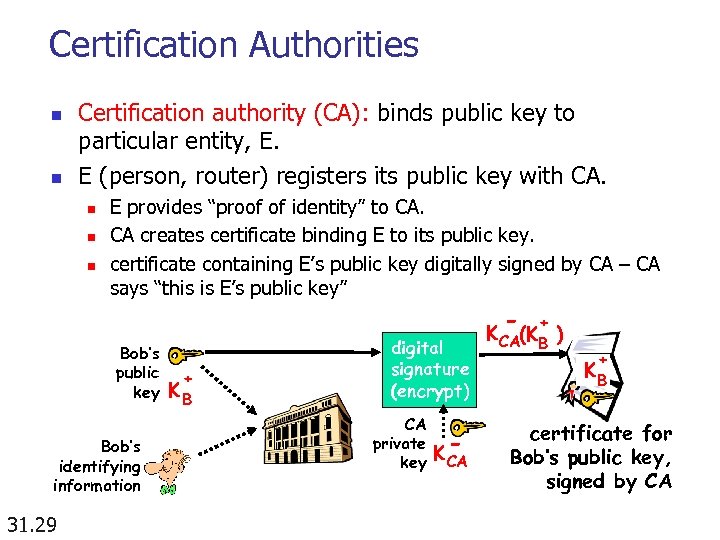 Certification Authorities n n Certification authority (CA): binds public key to particular entity, E. E (person, router) registers its public key with CA. n n n E provides “proof of identity” to CA. CA creates certificate binding E to its public key. certificate containing E’s public key digitally signed by CA – CA says “this is E’s public key” Bob’s public key Bob’s identifying information 31. 29 + KB digital signature (encrypt) CA private key K- CA - + K CA(KB ) + KB certificate for Bob’s public key, signed by CA
Certification Authorities n n Certification authority (CA): binds public key to particular entity, E. E (person, router) registers its public key with CA. n n n E provides “proof of identity” to CA. CA creates certificate binding E to its public key. certificate containing E’s public key digitally signed by CA – CA says “this is E’s public key” Bob’s public key Bob’s identifying information 31. 29 + KB digital signature (encrypt) CA private key K- CA - + K CA(KB ) + KB certificate for Bob’s public key, signed by CA
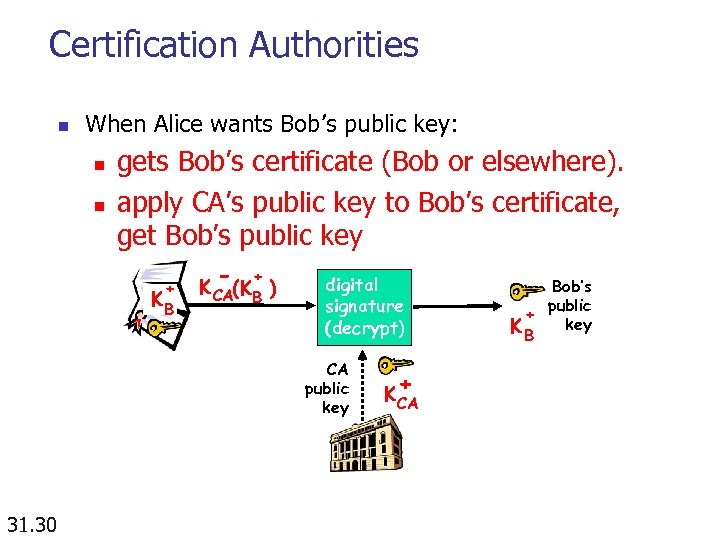 Certification Authorities n When Alice wants Bob’s public key: n n gets Bob’s certificate (Bob or elsewhere). apply CA’s public key to Bob’s certificate, get Bob’s public key + KB - + K CA(KB ) digital signature (decrypt) CA public key 31. 30 + K CA Bob’s public + key KB
Certification Authorities n When Alice wants Bob’s public key: n n gets Bob’s certificate (Bob or elsewhere). apply CA’s public key to Bob’s certificate, get Bob’s public key + KB - + K CA(KB ) digital signature (decrypt) CA public key 31. 30 + K CA Bob’s public + key KB
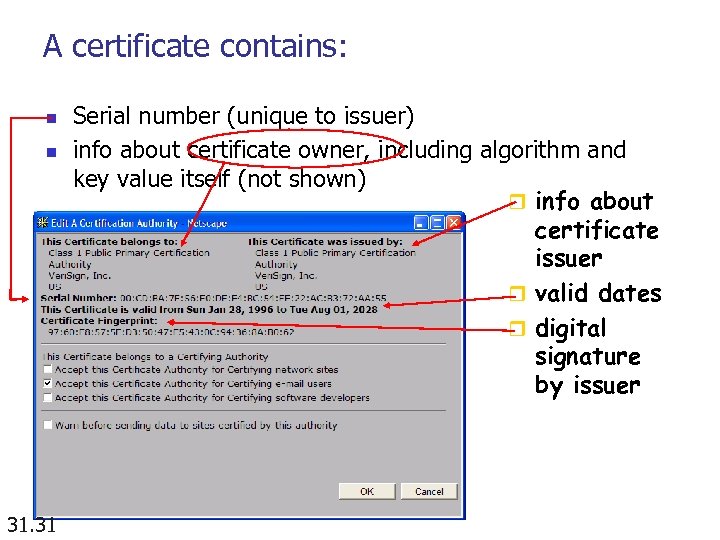 A certificate contains: n n 31. 31 Serial number (unique to issuer) info about certificate owner, including algorithm and key value itself (not shown) r info about certificate issuer r valid dates r digital signature by issuer
A certificate contains: n n 31. 31 Serial number (unique to issuer) info about certificate owner, including algorithm and key value itself (not shown) r info about certificate issuer r valid dates r digital signature by issuer
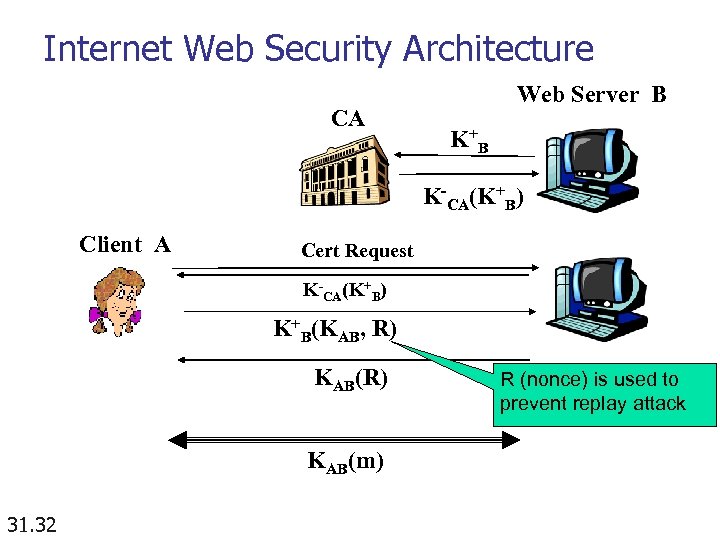 Internet Web Security Architecture CA Web Server B K +B K-CA(K+B) Client A Cert Request K-CA(K+B) K+B(KAB, R) KAB(m) 31. 32 R (nonce) is used to prevent replay attack
Internet Web Security Architecture CA Web Server B K +B K-CA(K+B) Client A Cert Request K-CA(K+B) K+B(KAB, R) KAB(m) 31. 32 R (nonce) is used to prevent replay attack
 Internet Web Security Conditions n Clients’ web browsers have built-in CAs are trustable Web servers have certificates in CAs. n Q: What if a server has no certificate? n n n 31. 33 Example: SSH servers
Internet Web Security Conditions n Clients’ web browsers have built-in CAs are trustable Web servers have certificates in CAs. n Q: What if a server has no certificate? n n n 31. 33 Example: SSH servers


