948b0d2e7d323a3e2d317a0f223a0b64.ppt
- Количество слайдов: 87
 Chapter 2 Network Models 2. 1 Copyright © The Mc. Graw-Hill Companies, Inc. Permission required for reproduction or display.
Chapter 2 Network Models 2. 1 Copyright © The Mc. Graw-Hill Companies, Inc. Permission required for reproduction or display.
 2 -1 LAYERED TASKS We use the concept of layers in our daily life. As an example, let us consider two friends who communicate through postal mail. The process of sending a letter to a friend would be complex if there were no services available from the post office. Topics discussed in this section: Sender, Receiver, and Carrier Hierarchy 2. 2
2 -1 LAYERED TASKS We use the concept of layers in our daily life. As an example, let us consider two friends who communicate through postal mail. The process of sending a letter to a friend would be complex if there were no services available from the post office. Topics discussed in this section: Sender, Receiver, and Carrier Hierarchy 2. 2
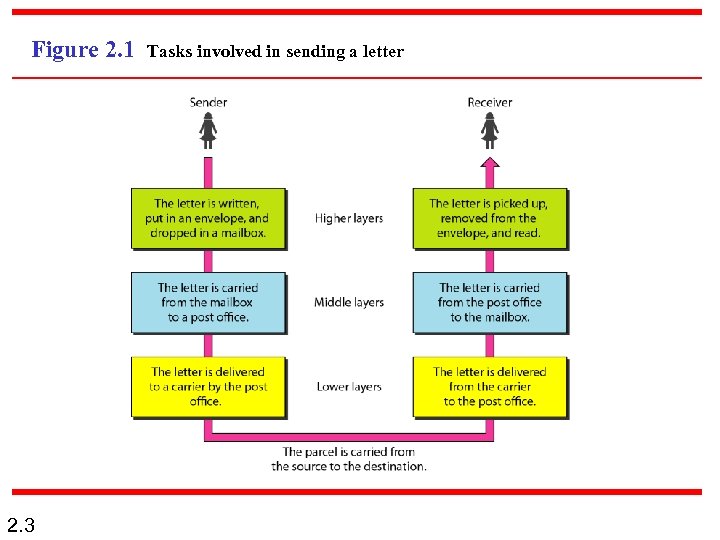 Figure 2. 1 2. 3 Tasks involved in sending a letter
Figure 2. 1 2. 3 Tasks involved in sending a letter
 2 -2 THE OSI MODEL Established in 1947, the International Standards Organization (ISO) is a multinational body dedicated to worldwide agreement on international standards. An ISO standard that covers all aspects of network communications is the Open Systems Interconnection (OSI) model. It was first introduced in the late 1970 s. Topics discussed in this section: Layered Architecture Peer-to-Peer Processes Encapsulation 2. 4
2 -2 THE OSI MODEL Established in 1947, the International Standards Organization (ISO) is a multinational body dedicated to worldwide agreement on international standards. An ISO standard that covers all aspects of network communications is the Open Systems Interconnection (OSI) model. It was first introduced in the late 1970 s. Topics discussed in this section: Layered Architecture Peer-to-Peer Processes Encapsulation 2. 4
 Note ISO is the organization. OSI is the model. 2. 5
Note ISO is the organization. OSI is the model. 2. 5
 Introduction to the OSI layer n n n Open Systems/ Interconnection (OSI) Each layer support the layers above it and offers services to the layers below Each layer performs unique and specific task A layer only has knowledge of its neighbour layers only A layer service is independent of the implementation
Introduction to the OSI layer n n n Open Systems/ Interconnection (OSI) Each layer support the layers above it and offers services to the layers below Each layer performs unique and specific task A layer only has knowledge of its neighbour layers only A layer service is independent of the implementation
 How OSI was created and how n n n An attempt for a framework for developing networking technologies OSI became a tool for explaining the Networking in general Before OSI was created people created their Software/Hardware as they wanted it to be. There was not any compatibility. Now OSI is used as a rule set for all vendors to create their Software/Hardware by using the standards.
How OSI was created and how n n n An attempt for a framework for developing networking technologies OSI became a tool for explaining the Networking in general Before OSI was created people created their Software/Hardware as they wanted it to be. There was not any compatibility. Now OSI is used as a rule set for all vendors to create their Software/Hardware by using the standards.
 Remember n n 2. 8 The OSI model is not a protocol; it is model for understanding and designing a network architecture that is flexible, robust and interoperable An open system is a model that allows any two different systems to communicate regardless of their underlying architecture (hardware or software).
Remember n n 2. 8 The OSI model is not a protocol; it is model for understanding and designing a network architecture that is flexible, robust and interoperable An open system is a model that allows any two different systems to communicate regardless of their underlying architecture (hardware or software).
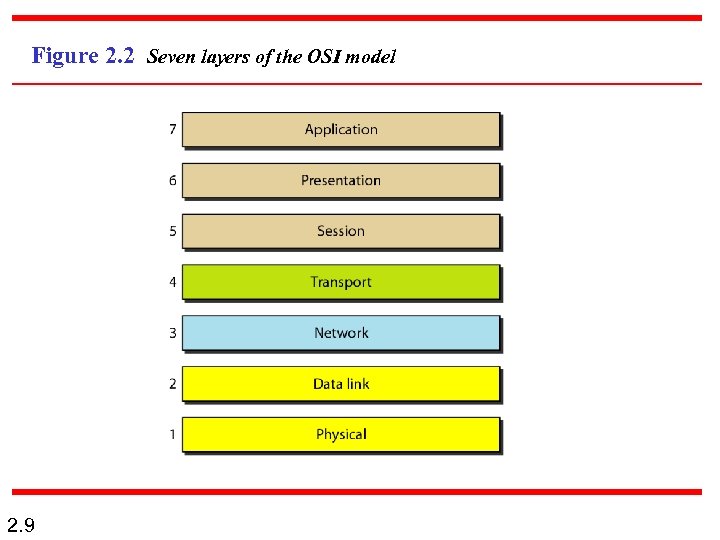 Figure 2. 2 Seven layers of the OSI model 2. 9
Figure 2. 2 Seven layers of the OSI model 2. 9
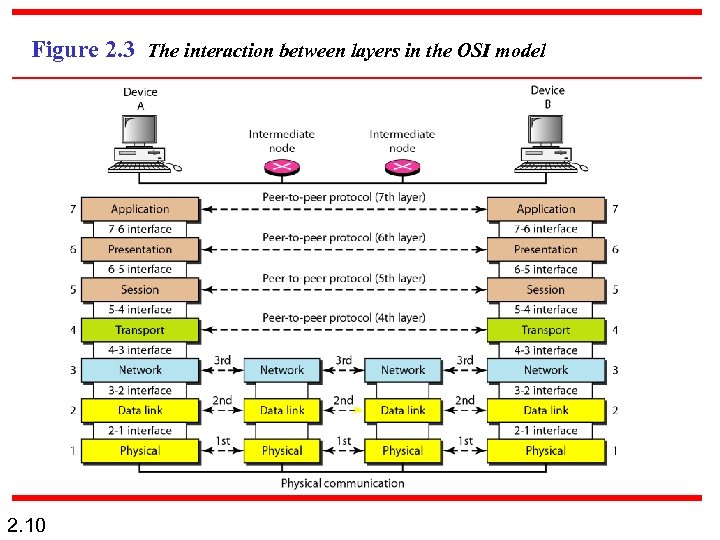 Figure 2. 3 The interaction between layers in the OSI model 2. 10
Figure 2. 3 The interaction between layers in the OSI model 2. 10
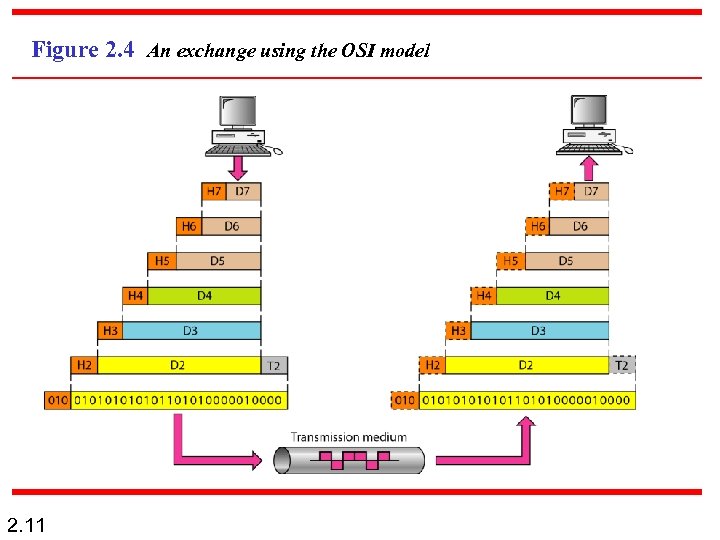 Figure 2. 4 An exchange using the OSI model 2. 11
Figure 2. 4 An exchange using the OSI model 2. 11
 2 -3 LAYERS IN THE OSI MODEL In this section we briefly describe the functions of each layer in the OSI model. Topics discussed in this section: Physical Layer Data Link Layer Network Layer Transport Layer Session Layer Presentation Layer Application Layer 2. 12
2 -3 LAYERS IN THE OSI MODEL In this section we briefly describe the functions of each layer in the OSI model. Topics discussed in this section: Physical Layer Data Link Layer Network Layer Transport Layer Session Layer Presentation Layer Application Layer 2. 12
 Physical Layer n n 2. 13 The physical layer coordinates the functions required to transmit a bit stream over a physical medium. It also defines the procedures and functions that physical devices and interfaces have to perform for transmission occur.
Physical Layer n n 2. 13 The physical layer coordinates the functions required to transmit a bit stream over a physical medium. It also defines the procedures and functions that physical devices and interfaces have to perform for transmission occur.
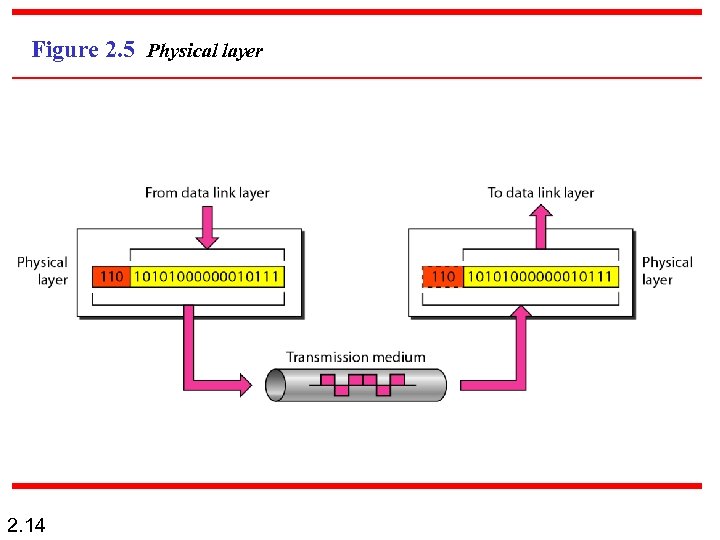 Figure 2. 5 Physical layer 2. 14
Figure 2. 5 Physical layer 2. 14
 Note The physical layer is responsible for movements of individual bits from one hop (node) to the next. 2. 15
Note The physical layer is responsible for movements of individual bits from one hop (node) to the next. 2. 15
 OSI REFERENCE The physical layer is concerned with the following: n Physical characteristics of interfaces and media: The physical layer defines the characteristics of the interface between devices and the transmission media, including its type. n Representation of the bits: the physical layer data consist of a stream of bits without any interpretation. To be transmitted, bits must be encoded into signals – electrical or optical-. The physical layer defines the type of encoding. n Data rate: The physical layer defines the transmission rate, the number of bits sent each second. • Data Transmission and Reception (half duplex, full duplex ) • Topology and Physical Network Design (mesh, ring, bus) • 2. 16 PDU: bit
OSI REFERENCE The physical layer is concerned with the following: n Physical characteristics of interfaces and media: The physical layer defines the characteristics of the interface between devices and the transmission media, including its type. n Representation of the bits: the physical layer data consist of a stream of bits without any interpretation. To be transmitted, bits must be encoded into signals – electrical or optical-. The physical layer defines the type of encoding. n Data rate: The physical layer defines the transmission rate, the number of bits sent each second. • Data Transmission and Reception (half duplex, full duplex ) • Topology and Physical Network Design (mesh, ring, bus) • 2. 16 PDU: bit
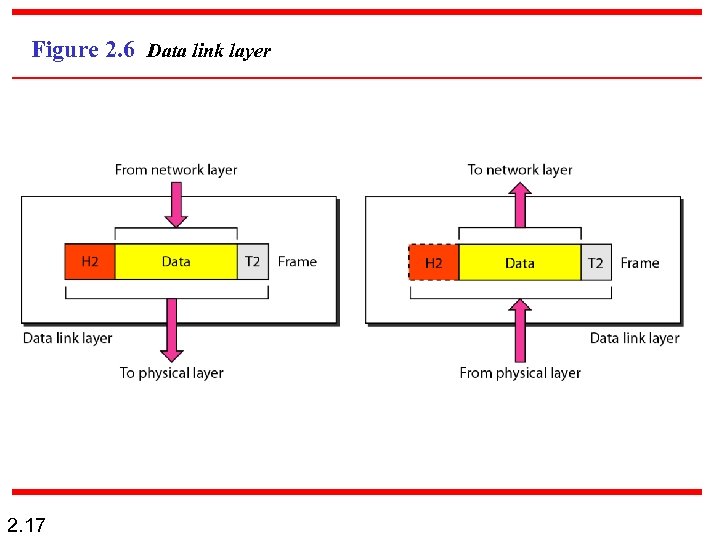 Figure 2. 6 Data link layer 2. 17
Figure 2. 6 Data link layer 2. 17
 Note The data link layer is responsible for moving frames from one hop (node) to the next. 2. 18
Note The data link layer is responsible for moving frames from one hop (node) to the next. 2. 18
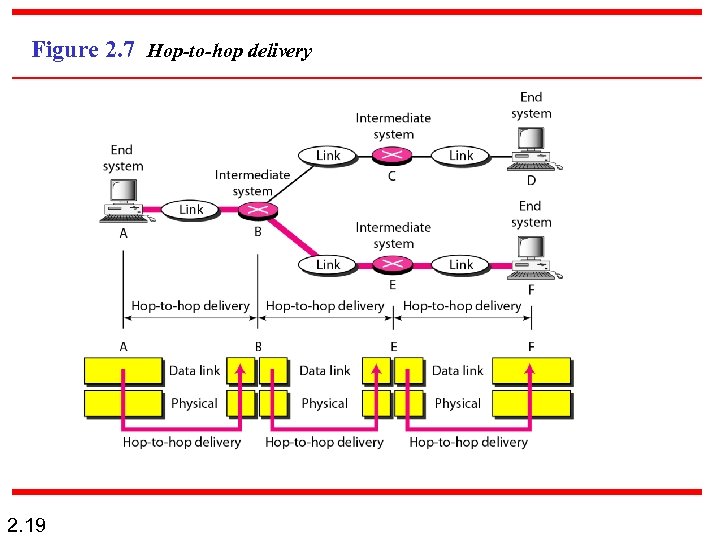 Figure 2. 7 Hop-to-hop delivery 2. 19
Figure 2. 7 Hop-to-hop delivery 2. 19
 DATA LINK LAYER n 2. 20 The data link layer transforms the physical layer, a raw transmission facility, to a reliable link and is responsible for node-to-node delivery. It makes the physical layer appear error free to the upper layer (network layer).
DATA LINK LAYER n 2. 20 The data link layer transforms the physical layer, a raw transmission facility, to a reliable link and is responsible for node-to-node delivery. It makes the physical layer appear error free to the upper layer (network layer).
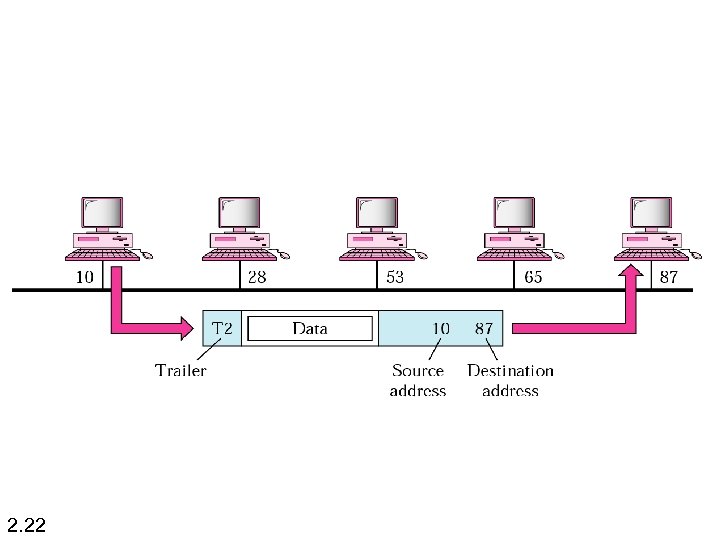
 Functions of the data link layer: n Framing. The data link layer divides the stream of bits received from the network layer into data units called frames. n n 2. 21 Physical addressing. If frames are to be distributed to different systems on the network, the data link layer adds a header to the frame to define the physical address of the sender (source address) and/or receiver (destination address) of the frame. If the frame is intended for a system outside the sender’s network, the receiver address is the address of the device that connects one network to the next.
Functions of the data link layer: n Framing. The data link layer divides the stream of bits received from the network layer into data units called frames. n n 2. 21 Physical addressing. If frames are to be distributed to different systems on the network, the data link layer adds a header to the frame to define the physical address of the sender (source address) and/or receiver (destination address) of the frame. If the frame is intended for a system outside the sender’s network, the receiver address is the address of the device that connects one network to the next.
 2. 22
2. 22
 n n n 2. 23 Flow Control. If the rate at which the data are absorbed by the receiver is less than the rate produced in the sender, the data link layer imposes a flow control mechanism to prevent overwhelming the receiver. Error control. The data link layer adds reliability to the physical layer by adding mechanisms to detect and retransmit damaged or lost frames. Error control is normally achieved through a trailer to the end of the frame. Access Control. When two or more devices are connected to the same link, data link layer protocols are necessary to determine which device has control over the link at any time.
n n n 2. 23 Flow Control. If the rate at which the data are absorbed by the receiver is less than the rate produced in the sender, the data link layer imposes a flow control mechanism to prevent overwhelming the receiver. Error control. The data link layer adds reliability to the physical layer by adding mechanisms to detect and retransmit damaged or lost frames. Error control is normally achieved through a trailer to the end of the frame. Access Control. When two or more devices are connected to the same link, data link layer protocols are necessary to determine which device has control over the link at any time.
 OSI REFERENCE 2. Data Link Layer 2. 1. Logical Link Control (LLC ) n Establishment and control of logical links between local devices on a network. 2. 2. Media Access Control (MAC) n The procedures used by devices to control access to the network medium. n • • • 2. 24 Frame sequencing Frame acknowledgment Addressing Frame error checking PDU: frame
OSI REFERENCE 2. Data Link Layer 2. 1. Logical Link Control (LLC ) n Establishment and control of logical links between local devices on a network. 2. 2. Media Access Control (MAC) n The procedures used by devices to control access to the network medium. n • • • 2. 24 Frame sequencing Frame acknowledgment Addressing Frame error checking PDU: frame
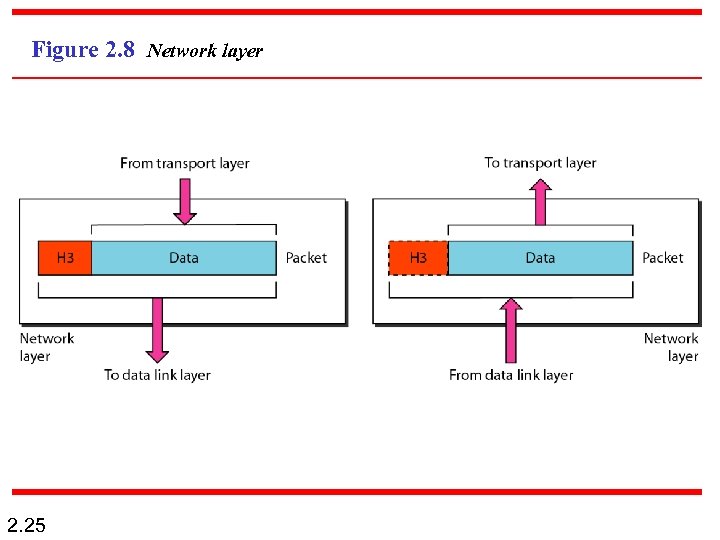 Figure 2. 8 Network layer 2. 25
Figure 2. 8 Network layer 2. 25
 Note The network layer is responsible for the delivery of individual packets from the source host to the destination host. 2. 26
Note The network layer is responsible for the delivery of individual packets from the source host to the destination host. 2. 26
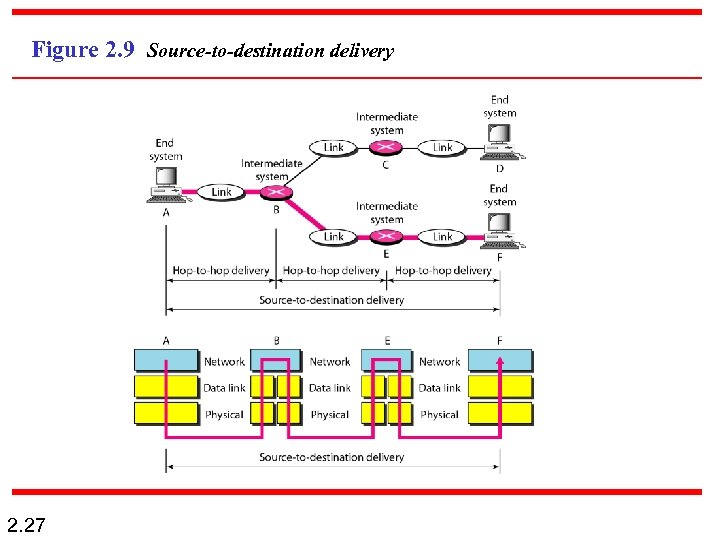 Figure 2. 9 Source-to-destination delivery 2. 27
Figure 2. 9 Source-to-destination delivery 2. 27
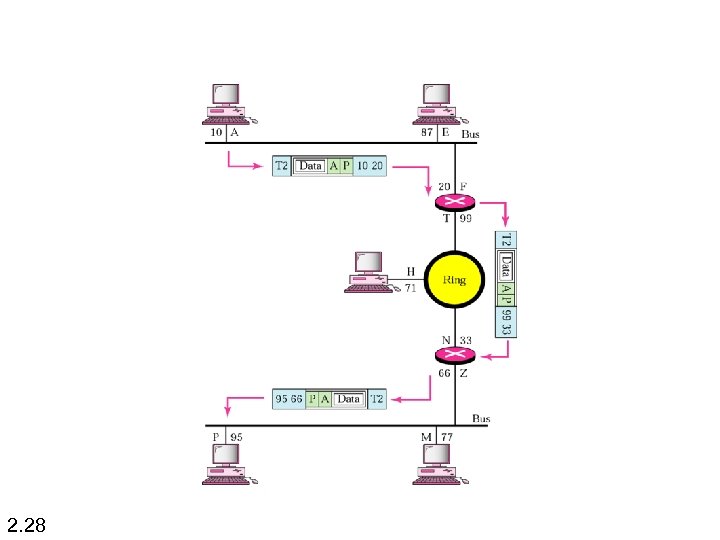 2. 28
2. 28
 n n 2. 29 The network layer is responsible for routing datagrams from one host to another. Logical addressing. The physical addressing implemented by the data link layer handles the addressing problem locally. The network layer adds a header to the packet coming from the upper layer, among other things, includes the logical address of the sender and receiver. Routing. When independent networks or links are connected together to create an internetwork (a network of networks) or a large network, the connecting devices (called routers or gateways) route or switch the packets to their final destination.
n n 2. 29 The network layer is responsible for routing datagrams from one host to another. Logical addressing. The physical addressing implemented by the data link layer handles the addressing problem locally. The network layer adds a header to the packet coming from the upper layer, among other things, includes the logical address of the sender and receiver. Routing. When independent networks or links are connected together to create an internetwork (a network of networks) or a large network, the connecting devices (called routers or gateways) route or switch the packets to their final destination.
 Summary n n n • • 2. 30 Addressing (IPV 4) Encapsulation (Inserts a header with source and destination IPs) Routing (Move a packet over the Internet) Decapsulation (Open the packet and check the destination host) IP is connectionless Functions: Logical addressing. Routing
Summary n n n • • 2. 30 Addressing (IPV 4) Encapsulation (Inserts a header with source and destination IPs) Routing (Move a packet over the Internet) Decapsulation (Open the packet and check the destination host) IP is connectionless Functions: Logical addressing. Routing
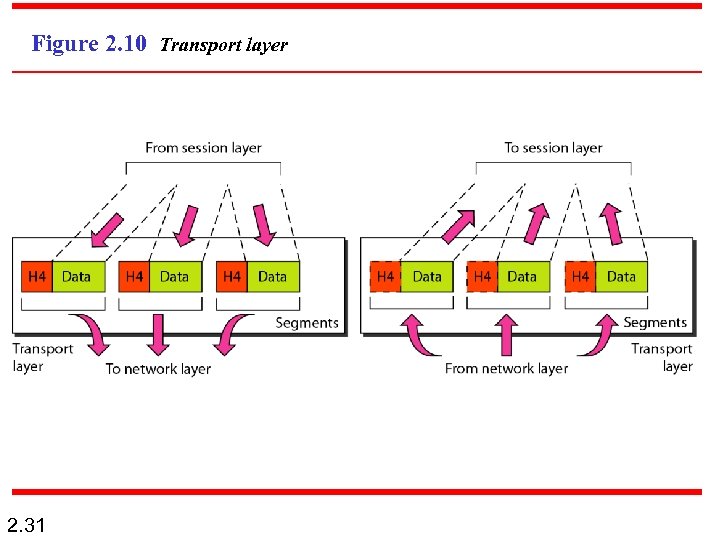 Figure 2. 10 Transport layer 2. 31
Figure 2. 10 Transport layer 2. 31
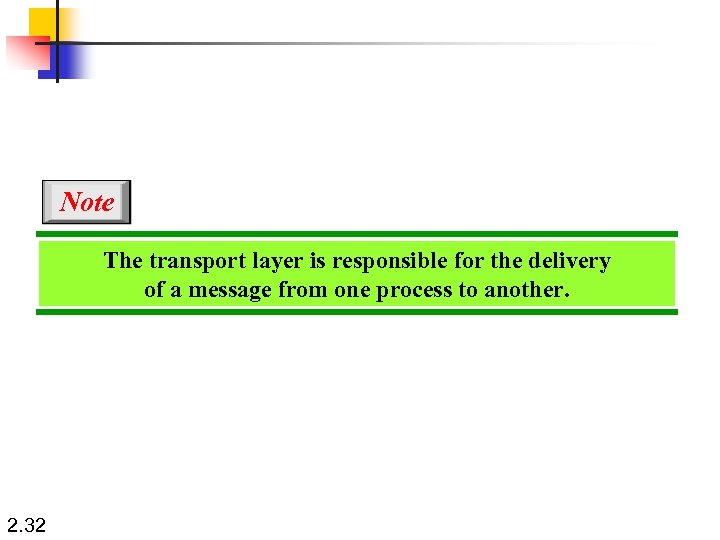 Note The transport layer is responsible for the delivery of a message from one process to another. 2. 32
Note The transport layer is responsible for the delivery of a message from one process to another. 2. 32
 n n The transport layer is responsible for process-to-process delivery of the entire message. The transport layer ensures that the whole message arrives intact and in order, overseeing both error control and flow control at the process-to-process level. 2. 33
n n The transport layer is responsible for process-to-process delivery of the entire message. The transport layer ensures that the whole message arrives intact and in order, overseeing both error control and flow control at the process-to-process level. 2. 33
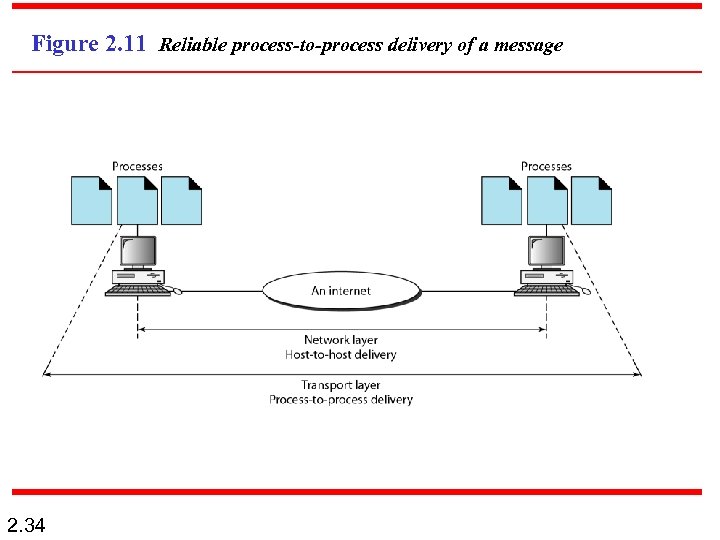 Figure 2. 11 Reliable process-to-process delivery of a message 2. 34
Figure 2. 11 Reliable process-to-process delivery of a message 2. 34
 Functions n n n 2. 35 Port addressing: computer often run several processes (running programs) at the same time. Process-to-process delivery means delivery from a specific process on one computer to a specific process on the other. The transport layer header include a type of address called port address. The network layer gets each packet to the correct computer; the transport layer gets the entire message to the correct process on that computer.
Functions n n n 2. 35 Port addressing: computer often run several processes (running programs) at the same time. Process-to-process delivery means delivery from a specific process on one computer to a specific process on the other. The transport layer header include a type of address called port address. The network layer gets each packet to the correct computer; the transport layer gets the entire message to the correct process on that computer.
 n n 2. 36 Segmentation and reassembly: a message is divided into transmittable segments, each having a sequence number. These numbers enable the transport layer to reassemble the message correctly upon arrival at the destination. Connection control: The transport layer can be either connectionless or connectionoriented. TCP – Web Browser UDP – Video Streaming Applications
n n 2. 36 Segmentation and reassembly: a message is divided into transmittable segments, each having a sequence number. These numbers enable the transport layer to reassemble the message correctly upon arrival at the destination. Connection control: The transport layer can be either connectionless or connectionoriented. TCP – Web Browser UDP – Video Streaming Applications
 n n 2. 37 Flow control: the transport layer performs a flow control end to end. The data link layer performs flow control across a single link. Error control: the transport layer performs error control end to end. The data link layer performs control across a single link.
n n 2. 37 Flow control: the transport layer performs a flow control end to end. The data link layer performs flow control across a single link. Error control: the transport layer performs error control end to end. The data link layer performs control across a single link.
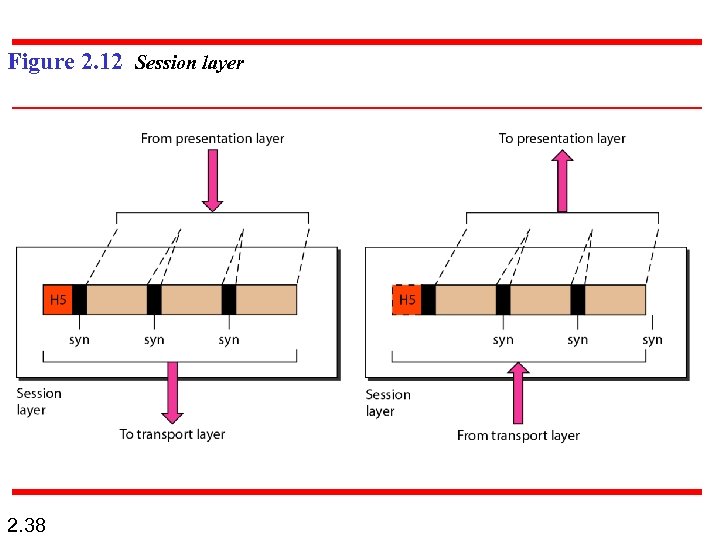 Figure 2. 12 Session layer 2. 38
Figure 2. 12 Session layer 2. 38
 Note The session layer is responsible for dialog control and synchronization. 2. 39
Note The session layer is responsible for dialog control and synchronization. 2. 39
 The session layer is the network dialog controller. It was designed to establish, maintain, and synchronize the interaction between communicating devices EXAMPLE n Sessions are used to keep track of individual connections to remote servers. Your web browser is an excellent example of the use of sessions. n Your web browser (an application layer object) opens a web page. That page contains text, graphics, Macromedia Flash objects and perhaps a Java applet. The graphics, the Flash object and the Java applet are all stored as separate files on the web server. To access them, a separate download must be started. Your web browser opens a separate session to the web server to download each of the individual files. The session layer keeps track of which packets and data belong to which file and keeps track of where they go (in this case, to your web browser). n 2. 40
The session layer is the network dialog controller. It was designed to establish, maintain, and synchronize the interaction between communicating devices EXAMPLE n Sessions are used to keep track of individual connections to remote servers. Your web browser is an excellent example of the use of sessions. n Your web browser (an application layer object) opens a web page. That page contains text, graphics, Macromedia Flash objects and perhaps a Java applet. The graphics, the Flash object and the Java applet are all stored as separate files on the web server. To access them, a separate download must be started. Your web browser opens a separate session to the web server to download each of the individual files. The session layer keeps track of which packets and data belong to which file and keeps track of where they go (in this case, to your web browser). n 2. 40
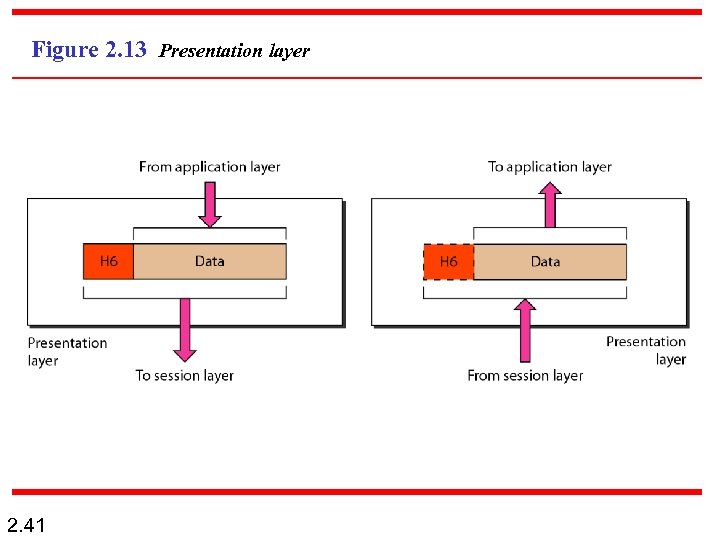 Figure 2. 13 Presentation layer 2. 41
Figure 2. 13 Presentation layer 2. 41
 Note The presentation layer is responsible for translation, compression, and encryption. 2. 42
Note The presentation layer is responsible for translation, compression, and encryption. 2. 42
 n 2. 43 The presentation layer is responsible for the delivery and formatting of information to the application layer for further processing or display. [4] It relieves the application layer of concern regarding syntactical differences in data representation within the end-user systems. An example of a presentation service would be the conversion of an EBCDIC-coded text computer file to an ASCIIcoded file.
n 2. 43 The presentation layer is responsible for the delivery and formatting of information to the application layer for further processing or display. [4] It relieves the application layer of concern regarding syntactical differences in data representation within the end-user systems. An example of a presentation service would be the conversion of an EBCDIC-coded text computer file to an ASCIIcoded file.
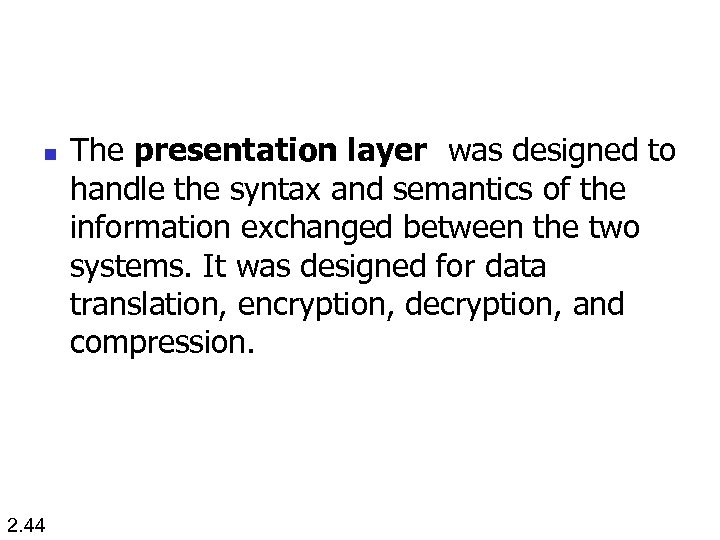 n 2. 44 The presentation layer was designed to handle the syntax and semantics of the information exchanged between the two systems. It was designed for data translation, encryption, decryption, and compression.
n 2. 44 The presentation layer was designed to handle the syntax and semantics of the information exchanged between the two systems. It was designed for data translation, encryption, decryption, and compression.
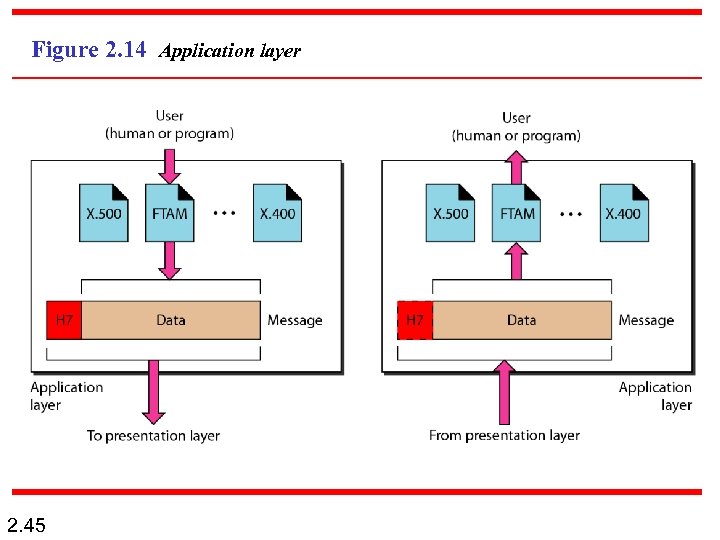 Figure 2. 14 Application layer 2. 45
Figure 2. 14 Application layer 2. 45
 Note The application layer is responsible for providing services to the user. 2. 46
Note The application layer is responsible for providing services to the user. 2. 46
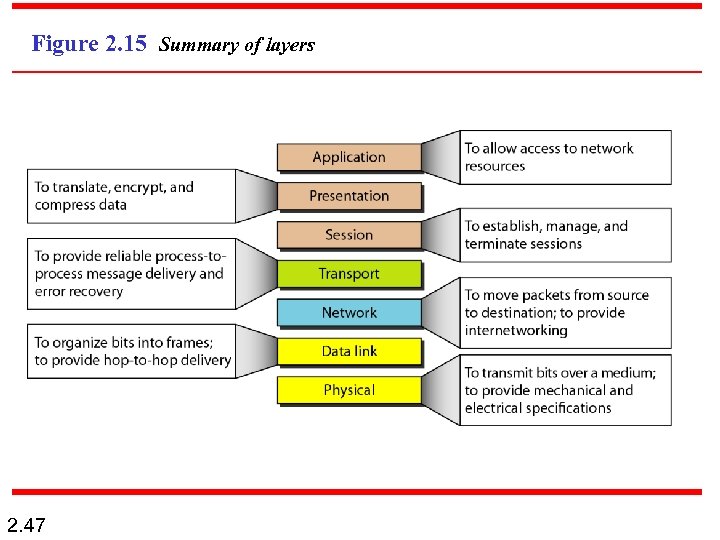 Figure 2. 15 Summary of layers 2. 47
Figure 2. 15 Summary of layers 2. 47
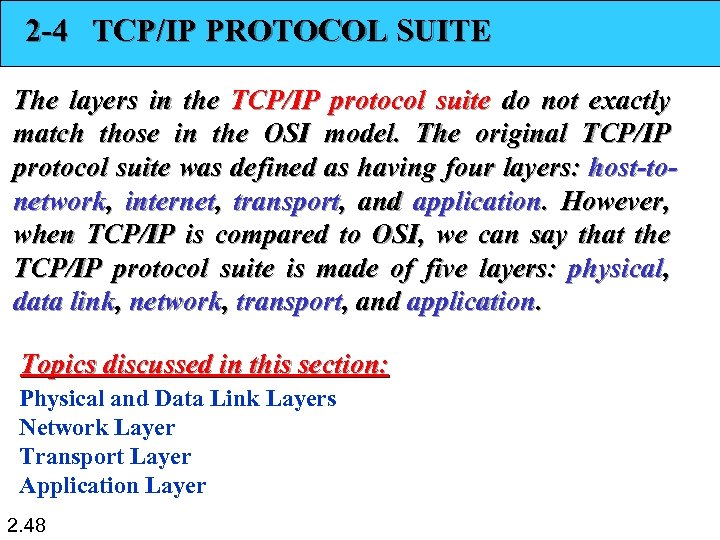 2 -4 TCP/IP PROTOCOL SUITE The layers in the TCP/IP protocol suite do not exactly match those in the OSI model. The original TCP/IP protocol suite was defined as having four layers: host-tonetwork, internet, transport, and application. However, when TCP/IP is compared to OSI, we can say that the TCP/IP protocol suite is made of five layers: physical, data link, network, transport, and application. Topics discussed in this section: Physical and Data Link Layers Network Layer Transport Layer Application Layer 2. 48
2 -4 TCP/IP PROTOCOL SUITE The layers in the TCP/IP protocol suite do not exactly match those in the OSI model. The original TCP/IP protocol suite was defined as having four layers: host-tonetwork, internet, transport, and application. However, when TCP/IP is compared to OSI, we can say that the TCP/IP protocol suite is made of five layers: physical, data link, network, transport, and application. Topics discussed in this section: Physical and Data Link Layers Network Layer Transport Layer Application Layer 2. 48
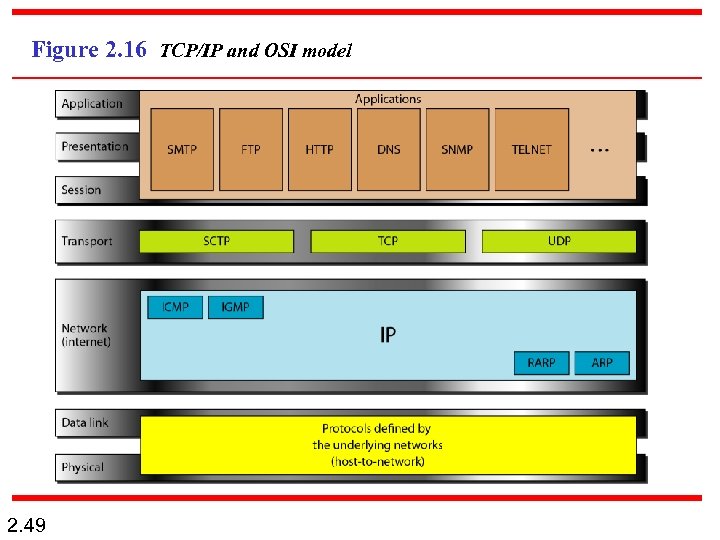 Figure 2. 16 TCP/IP and OSI model 2. 49
Figure 2. 16 TCP/IP and OSI model 2. 49
 2 -5 ADDRESSING Four levels of addresses are used in an internet employing the TCP/IP protocols: physical, logical, port, and specific. Topics discussed in this section: Physical Addresses Logical Addresses Port Addresses Specific Addresses 2. 50
2 -5 ADDRESSING Four levels of addresses are used in an internet employing the TCP/IP protocols: physical, logical, port, and specific. Topics discussed in this section: Physical Addresses Logical Addresses Port Addresses Specific Addresses 2. 50
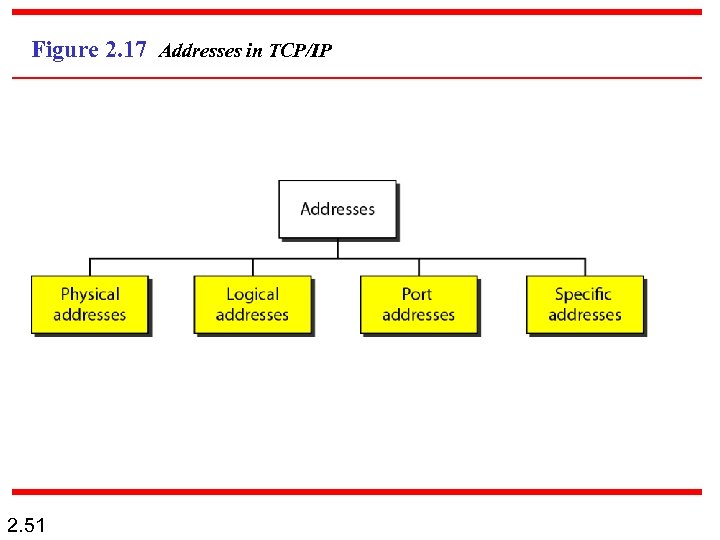 Figure 2. 17 Addresses in TCP/IP 2. 51
Figure 2. 17 Addresses in TCP/IP 2. 51
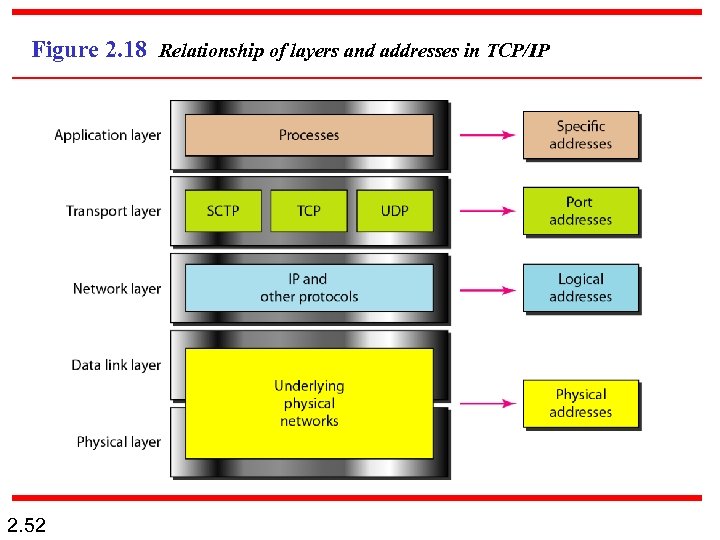 Figure 2. 18 Relationship of layers and addresses in TCP/IP 2. 52
Figure 2. 18 Relationship of layers and addresses in TCP/IP 2. 52
 Example 2. 1 In Figure 2. 19 a node with physical address 10 sends a frame to a node with physical address 87. The two nodes are connected by a link (bus topology LAN). As the figure shows, the computer with physical address 10 is the sender, and the computer with physical address 87 is the receiver. 2. 53
Example 2. 1 In Figure 2. 19 a node with physical address 10 sends a frame to a node with physical address 87. The two nodes are connected by a link (bus topology LAN). As the figure shows, the computer with physical address 10 is the sender, and the computer with physical address 87 is the receiver. 2. 53
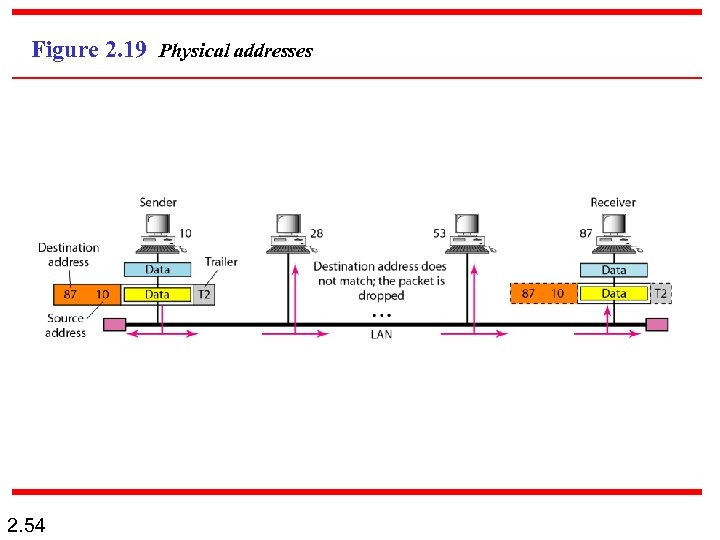 Figure 2. 19 Physical addresses 2. 54
Figure 2. 19 Physical addresses 2. 54
 Example 2. 2 Most local-area networks use a 48 -bit (6 -byte) physical address written as 12 hexadecimal digits; every byte (2 hexadecimal digits) is separated by a colon, as shown below: 07: 01: 02: 01: 2 C: 4 B A 6 -byte (12 hexadecimal digits) physical address. 2. 55
Example 2. 2 Most local-area networks use a 48 -bit (6 -byte) physical address written as 12 hexadecimal digits; every byte (2 hexadecimal digits) is separated by a colon, as shown below: 07: 01: 02: 01: 2 C: 4 B A 6 -byte (12 hexadecimal digits) physical address. 2. 55
 Example 2. 3 Figure 2. 20 shows a part of an internet with two routers connecting three LANs. Each device (computer or router) has a pair of addresses (logical and physical) for each connection. In this case, each computer is connected to only one link and therefore has only one pair of addresses. Each router, however, is connected to three networks (only two are shown in the figure). So each router has three pairs of addresses, one for each connection. 2. 56
Example 2. 3 Figure 2. 20 shows a part of an internet with two routers connecting three LANs. Each device (computer or router) has a pair of addresses (logical and physical) for each connection. In this case, each computer is connected to only one link and therefore has only one pair of addresses. Each router, however, is connected to three networks (only two are shown in the figure). So each router has three pairs of addresses, one for each connection. 2. 56
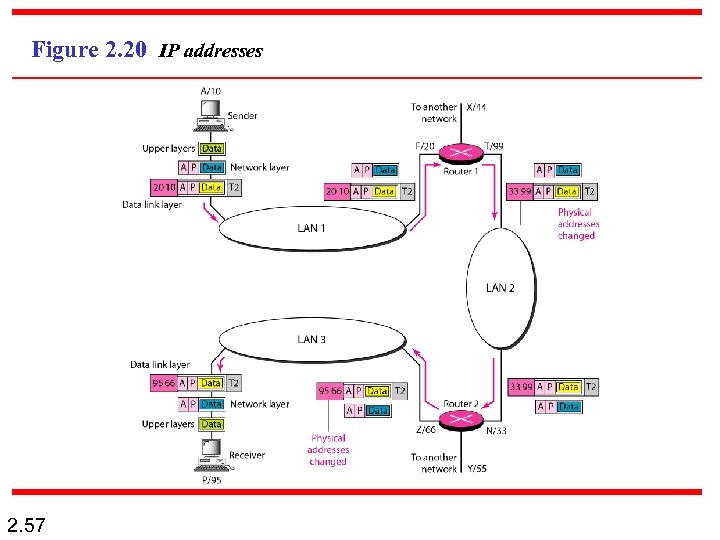 Figure 2. 20 IP addresses 2. 57
Figure 2. 20 IP addresses 2. 57
 Example 2. 4 Figure 2. 21 shows two computers communicating via the Internet. The sending computer is running three processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to hop, logical and port addresses remain the same from the source to destination. 2. 58
Example 2. 4 Figure 2. 21 shows two computers communicating via the Internet. The sending computer is running three processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to hop, logical and port addresses remain the same from the source to destination. 2. 58
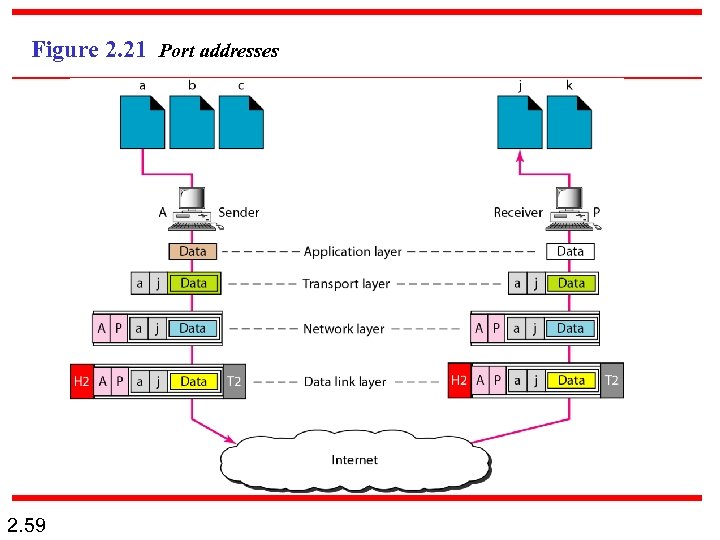 Figure 2. 21 Port addresses 2. 59
Figure 2. 21 Port addresses 2. 59
 Note The physical addresses will change from hop to hop, but the logical addresses usually remain the same. 2. 60
Note The physical addresses will change from hop to hop, but the logical addresses usually remain the same. 2. 60
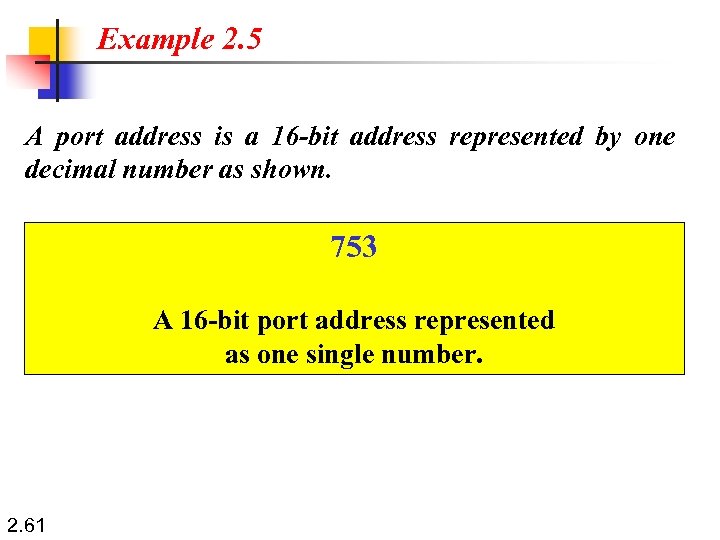 Example 2. 5 A port address is a 16 -bit address represented by one decimal number as shown. 753 A 16 -bit port address represented as one single number. 2. 61
Example 2. 5 A port address is a 16 -bit address represented by one decimal number as shown. 753 A 16 -bit port address represented as one single number. 2. 61
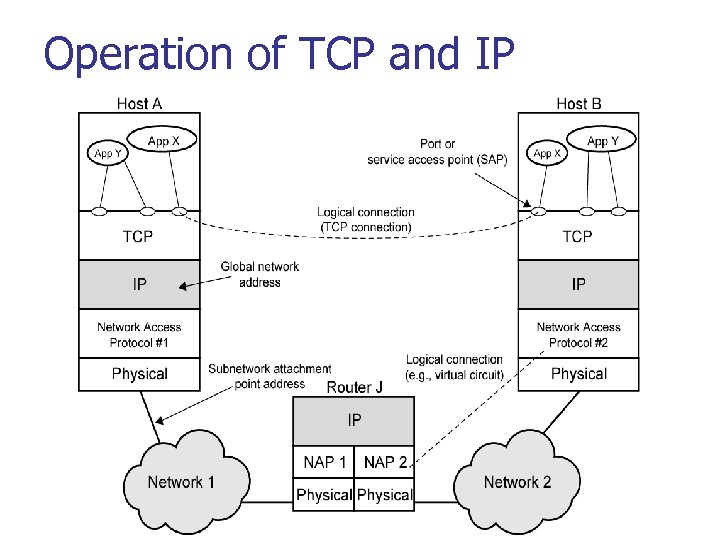 Operation of TCP and IP
Operation of TCP and IP
 Addressing Requirements n n two levels of addressing required each host on a subnet needs a unique global network address n n its IP address each application on a (multi-tasking) host needs a unique address within the host n known as a port
Addressing Requirements n n two levels of addressing required each host on a subnet needs a unique global network address n n its IP address each application on a (multi-tasking) host needs a unique address within the host n known as a port
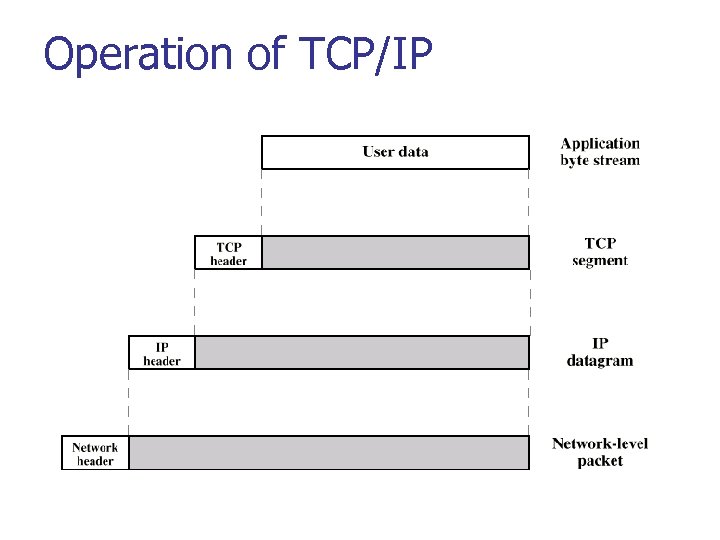 Operation of TCP/IP
Operation of TCP/IP
 Transmission Control Protocol (TCP) n n usual transport layer is (TCP) provides a reliable connection for transfer of data between applications a TCP segment is the basic protocol unit TCP tracks segments between entities for duration of each connection
Transmission Control Protocol (TCP) n n usual transport layer is (TCP) provides a reliable connection for transfer of data between applications a TCP segment is the basic protocol unit TCP tracks segments between entities for duration of each connection
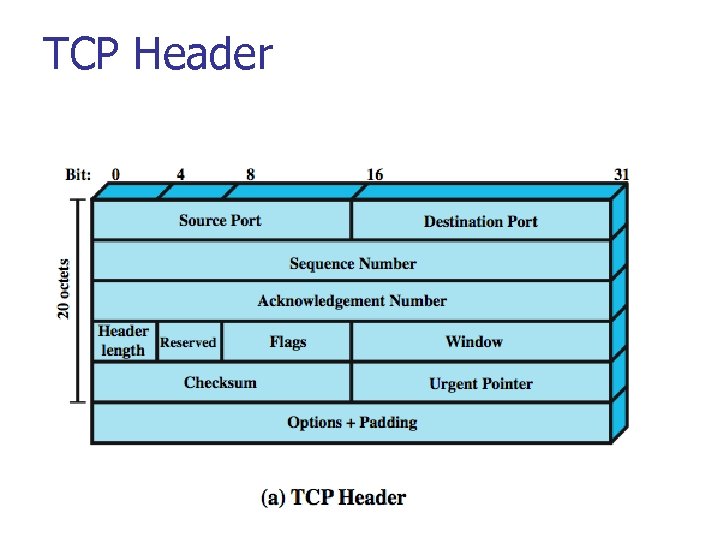 TCP Header
TCP Header
 User Datagram Protocol (UDP) n n n an alternative to TCP no guaranteed delivery no preservation of sequence no protection against duplication minimum overhead Just adds port addressing to IP
User Datagram Protocol (UDP) n n n an alternative to TCP no guaranteed delivery no preservation of sequence no protection against duplication minimum overhead Just adds port addressing to IP
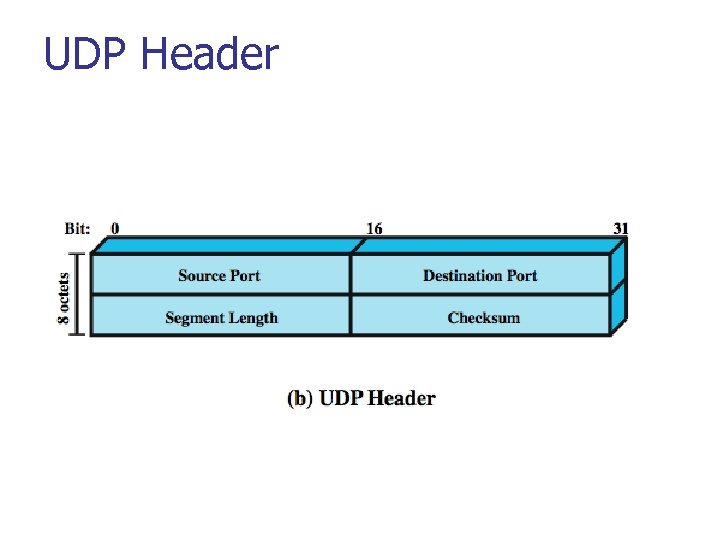 UDP Header
UDP Header
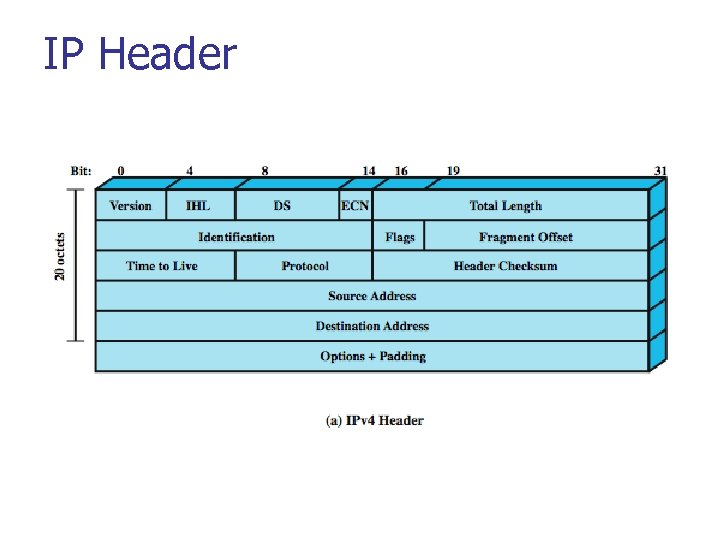 IP Header
IP Header
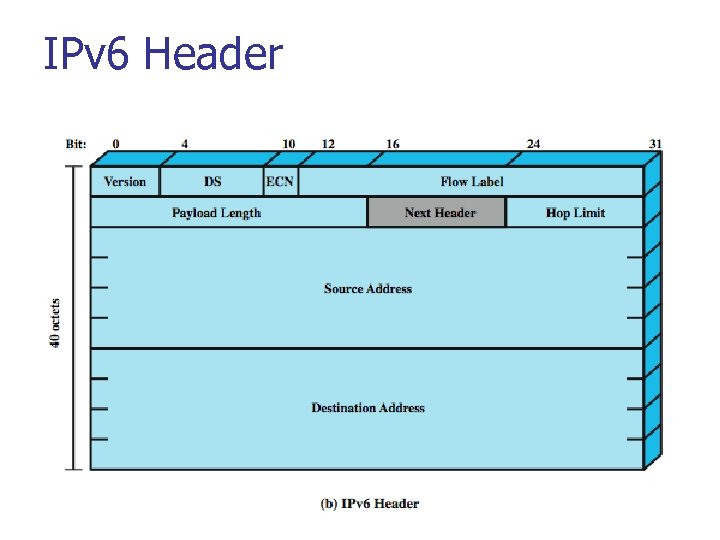 IPv 6 Header
IPv 6 Header
 TCP/IP Applications n have a number of standard TCP/IP applications such as n n n Simple Mail Transfer Protocol (SMTP) File Transfer Protocol (FTP) – control and data connections Telnet
TCP/IP Applications n have a number of standard TCP/IP applications such as n n n Simple Mail Transfer Protocol (SMTP) File Transfer Protocol (FTP) – control and data connections Telnet
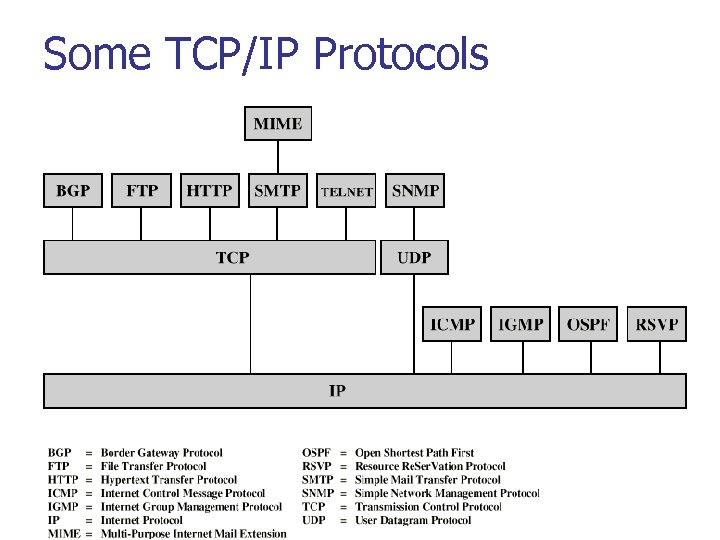 Some TCP/IP Protocols
Some TCP/IP Protocols
 OSI n n n Open Systems Interconnection developed by the International Organization for Standardization (ISO) has seven layers – too many is a theoretical system delivered too late! TCP/IP is the de facto standard
OSI n n n Open Systems Interconnection developed by the International Organization for Standardization (ISO) has seven layers – too many is a theoretical system delivered too late! TCP/IP is the de facto standard
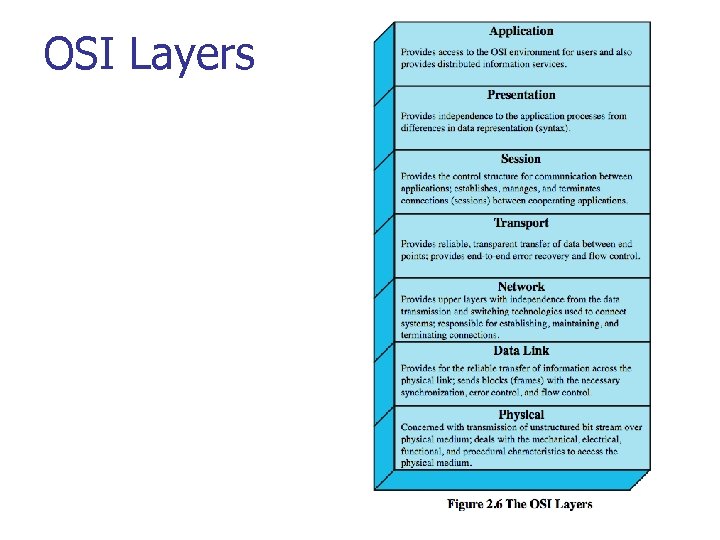 OSI Layers
OSI Layers
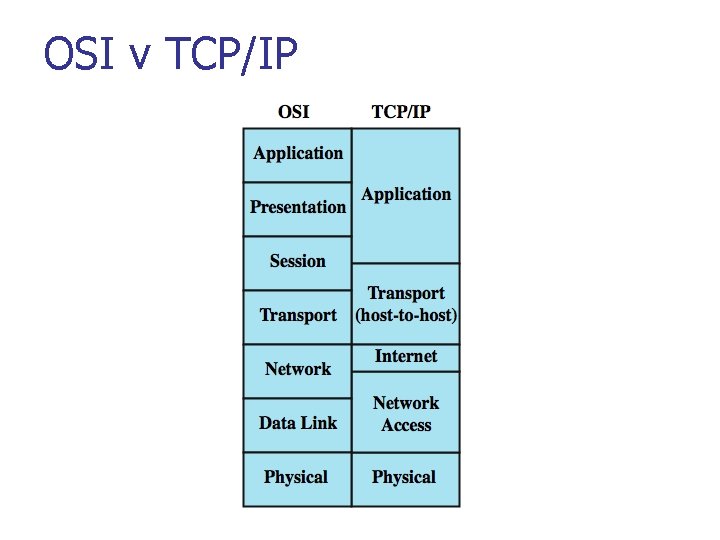 OSI v TCP/IP
OSI v TCP/IP
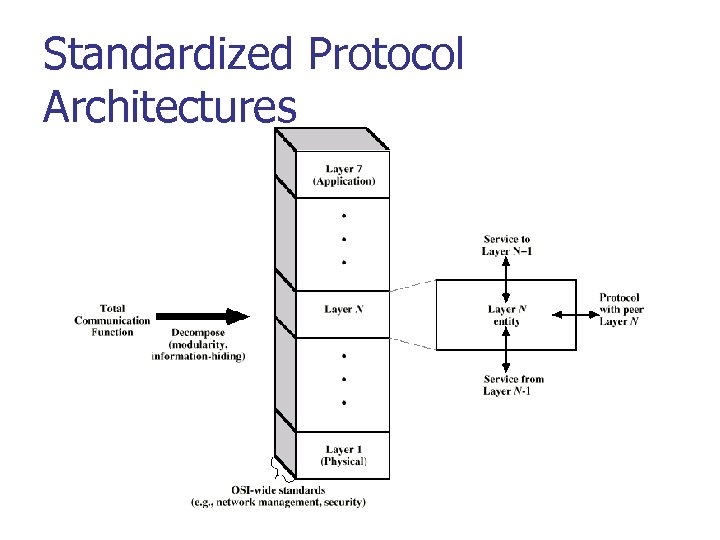 Standardized Protocol Architectures
Standardized Protocol Architectures
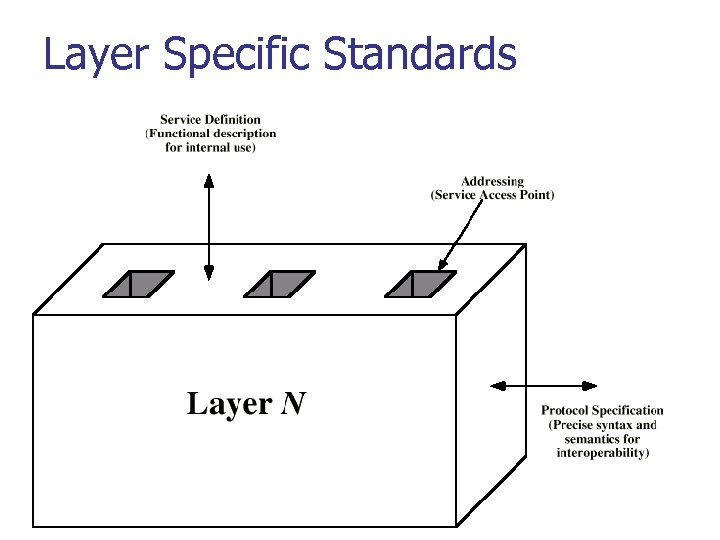 Layer Specific Standards
Layer Specific Standards
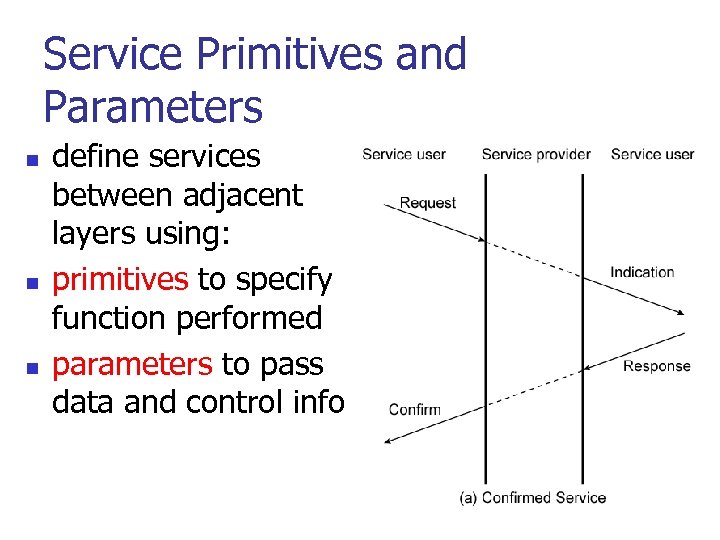 Service Primitives and Parameters n n n define services between adjacent layers using: primitives to specify function performed parameters to pass data and control info
Service Primitives and Parameters n n n define services between adjacent layers using: primitives to specify function performed parameters to pass data and control info
 Primitive Types REQUEST A primitive issued by a service user to invoke some service and to pass the parameters needed to specify fully the requested service INDICATION A primitive issued by a service provider either to: indicate that a procedure has been invoked by the peer service user on the connection and to provide the associated parameters, or notify the service user of a provider-initiated action RESPONSE A primitive issued by a service user to acknowledge or complete some procedure previously invoked by an indication to that user CONFIRM A primitive issued by a service provider to acknowledge or complete some procedure previously invoked by a request by the service user
Primitive Types REQUEST A primitive issued by a service user to invoke some service and to pass the parameters needed to specify fully the requested service INDICATION A primitive issued by a service provider either to: indicate that a procedure has been invoked by the peer service user on the connection and to provide the associated parameters, or notify the service user of a provider-initiated action RESPONSE A primitive issued by a service user to acknowledge or complete some procedure previously invoked by an indication to that user CONFIRM A primitive issued by a service provider to acknowledge or complete some procedure previously invoked by a request by the service user
 Traditional vs Multimedia Applications n traditionally Internet dominated by info retrieval applications n n n typically using text and image transfer E. g. email, file transfer, web see increasing growth in multimedia applications n n involving massive amounts of data such as streaming audio and video
Traditional vs Multimedia Applications n traditionally Internet dominated by info retrieval applications n n n typically using text and image transfer E. g. email, file transfer, web see increasing growth in multimedia applications n n involving massive amounts of data such as streaming audio and video
 Elastic and Inelastic Traffic n elastic traffic n n can adjust to delay & throughput changes over a wide range E. g. traditional “data” style TCP/IP traffic some applications more sensitive though inelastic traffic n n n does not adapt to such changes E. g. “real-time” voice & video traffic need minimum requirements on net arch
Elastic and Inelastic Traffic n elastic traffic n n can adjust to delay & throughput changes over a wide range E. g. traditional “data” style TCP/IP traffic some applications more sensitive though inelastic traffic n n n does not adapt to such changes E. g. “real-time” voice & video traffic need minimum requirements on net arch
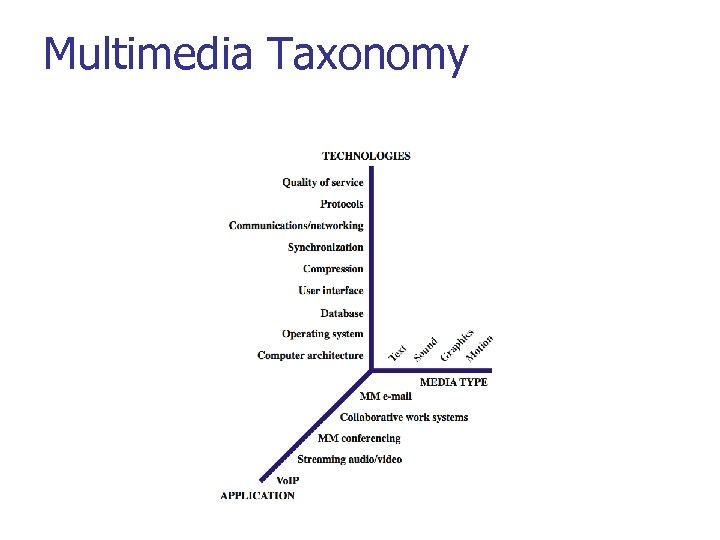 Multimedia Taxonomy
Multimedia Taxonomy
 Summary n n introduced need for protocol architecture TCP/IP protocol architecture OSI Model & protocol architecture standardization traditional vs multimedia application needs
Summary n n introduced need for protocol architecture TCP/IP protocol architecture OSI Model & protocol architecture standardization traditional vs multimedia application needs
 MCQ Ø Ø Ø The process to process delivery of the entire message is the responsibility of the Network/Transport/Application/Physical layer. As the data packet moves from the lower to the upper layers, headers are added/subtracted/rearranged/modified. Following is an application layer service. Remote log-in/file transfer/mail service/all of the above
MCQ Ø Ø Ø The process to process delivery of the entire message is the responsibility of the Network/Transport/Application/Physical layer. As the data packet moves from the lower to the upper layers, headers are added/subtracted/rearranged/modified. Following is an application layer service. Remote log-in/file transfer/mail service/all of the above
 MCQ Ø Ø Ø Match the following with one of the five internet layers. Communicates directly with user application program Error correction and retransmission Mechanical, electrical, and functional interface Reassembly of data packets
MCQ Ø Ø Ø Match the following with one of the five internet layers. Communicates directly with user application program Error correction and retransmission Mechanical, electrical, and functional interface Reassembly of data packets
 Problems n n n Q 1. In a protocol suite, layer N is above layer (N -1). In the case of segmentation, is it necessary that each (N-1) level segment contain a copy of the level N-header? Why? Blocking means combining several level N PDUs into one (N-1) level PDU. In the case of blocking, is it necessary that each level- N PDU retain its own header? Why?
Problems n n n Q 1. In a protocol suite, layer N is above layer (N -1). In the case of segmentation, is it necessary that each (N-1) level segment contain a copy of the level N-header? Why? Blocking means combining several level N PDUs into one (N-1) level PDU. In the case of blocking, is it necessary that each level- N PDU retain its own header? Why?
 Problems n Q 2. A TCP segment of 1500 bit data and 160 bit header is sent to the IP layer adds 160 bit header. It is then transmitted through a network which uses 24 -bit packet header. The destination network can accept packet size of 800 bits. How many bits (including header) are delivered to the destination network layer?
Problems n Q 2. A TCP segment of 1500 bit data and 160 bit header is sent to the IP layer adds 160 bit header. It is then transmitted through a network which uses 24 -bit packet header. The destination network can accept packet size of 800 bits. How many bits (including header) are delivered to the destination network layer?


