3402656ad3353f0ff8bfa58cb08eea42.ppt
- Количество слайдов: 67
 Chapter 2 Network Models 1 Copyright © The Mc. Graw-Hill Companies, Inc. Permission required for reproduction or display.
Chapter 2 Network Models 1 Copyright © The Mc. Graw-Hill Companies, Inc. Permission required for reproduction or display.
 Network Models n Network Architecture: n n 2 A) Hardware: at the core of any network; e. g. ) Tx/Rx devices, modems, codecs, physical links, switches B) Software: to derive the core H/W to communicate end users. The S/W is so complex as its task. Hence it is divided into
Network Models n Network Architecture: n n 2 A) Hardware: at the core of any network; e. g. ) Tx/Rx devices, modems, codecs, physical links, switches B) Software: to derive the core H/W to communicate end users. The S/W is so complex as its task. Hence it is divided into
 n n n 3 subtasks each of which is confined to a set of related processes to perform a specific function. --Each subtask S/W is called a “ Layer” --Layers are stacked over each other forming the net model stack, e. g. , ISO, TCP/IP
n n n 3 subtasks each of which is confined to a set of related processes to perform a specific function. --Each subtask S/W is called a “ Layer” --Layers are stacked over each other forming the net model stack, e. g. , ISO, TCP/IP
 2 -1 LAYERED TASKS We use the concept of layers in our daily life. As an example, let us consider two friends who communicate through postal mail. The process of sending a letter to a friend would be complex if there were no services available from the post office. Topics discussed in this section: Sender, Receiver, and Carrier Hierarchy 4
2 -1 LAYERED TASKS We use the concept of layers in our daily life. As an example, let us consider two friends who communicate through postal mail. The process of sending a letter to a friend would be complex if there were no services available from the post office. Topics discussed in this section: Sender, Receiver, and Carrier Hierarchy 4
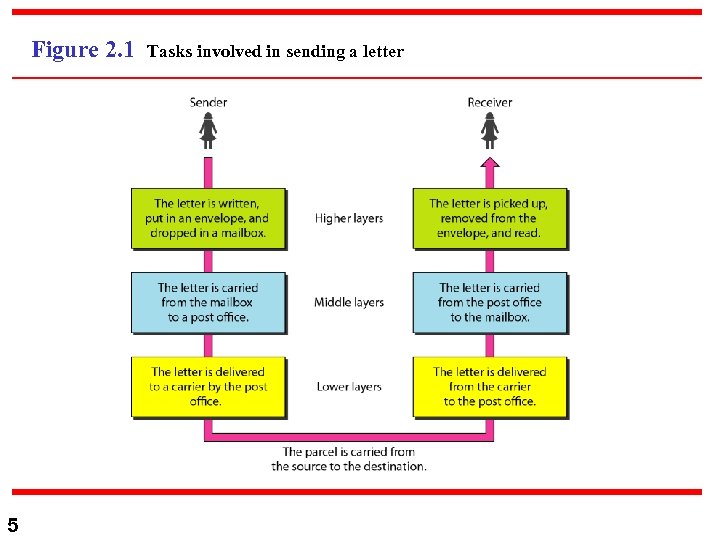 Figure 2. 1 5 Tasks involved in sending a letter
Figure 2. 1 5 Tasks involved in sending a letter
 2 -2 THE OSI MODEL Established in 1947, the International Standards Organization (ISO) is a multinational body dedicated to worldwide agreement on international standards. An ISO standard that covers all aspects of network communications is the Open Systems Interconnection (OSI) model. It was first introduced in the late 1970 s. Topics discussed in this section: Layered Architecture Peer-to-Peer Processes Encapsulation 6
2 -2 THE OSI MODEL Established in 1947, the International Standards Organization (ISO) is a multinational body dedicated to worldwide agreement on international standards. An ISO standard that covers all aspects of network communications is the Open Systems Interconnection (OSI) model. It was first introduced in the late 1970 s. Topics discussed in this section: Layered Architecture Peer-to-Peer Processes Encapsulation 6
 Layered Architecture n n 7 OSI model is composed of seven ordered layers. Figure 2. 3 shows the layers involved when message is sent from device A to device B Each layer defines a family of function distinct from those of the other layers. The OSI model allows complete interoperability.
Layered Architecture n n 7 OSI model is composed of seven ordered layers. Figure 2. 3 shows the layers involved when message is sent from device A to device B Each layer defines a family of function distinct from those of the other layers. The OSI model allows complete interoperability.
 Note ISO is the organization. OSI is the model. 8
Note ISO is the organization. OSI is the model. 8
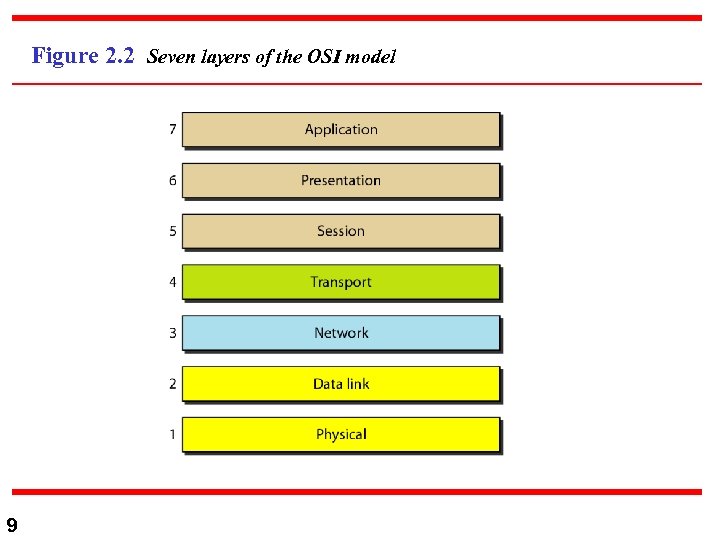 Figure 2. 2 Seven layers of the OSI model 9
Figure 2. 2 Seven layers of the OSI model 9
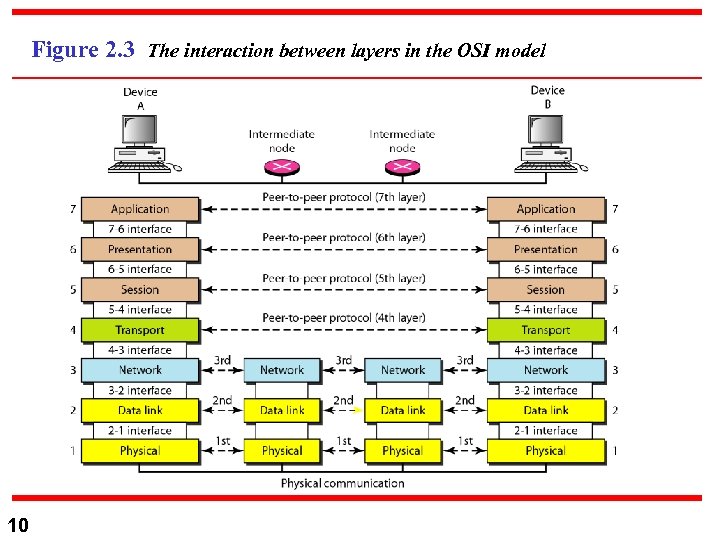 Figure 2. 3 The interaction between layers in the OSI model 10
Figure 2. 3 The interaction between layers in the OSI model 10
 Network Models (cont. . ) n 11 Each Layer has a “Peer-to-Peer” protocol that seems to represent (and carry out) the rest of the network task, yet it does only a specific part and delegate the rest to the layer beneath it (via its interface). It also has an “ interface” that defines the services that is provided to the layer above it.
Network Models (cont. . ) n 11 Each Layer has a “Peer-to-Peer” protocol that seems to represent (and carry out) the rest of the network task, yet it does only a specific part and delegate the rest to the layer beneath it (via its interface). It also has an “ interface” that defines the services that is provided to the layer above it.
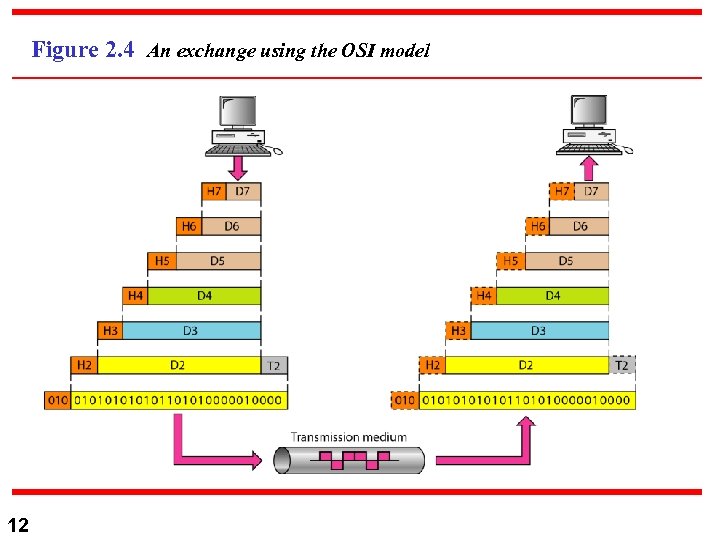 Figure 2. 4 An exchange using the OSI model 12
Figure 2. 4 An exchange using the OSI model 12
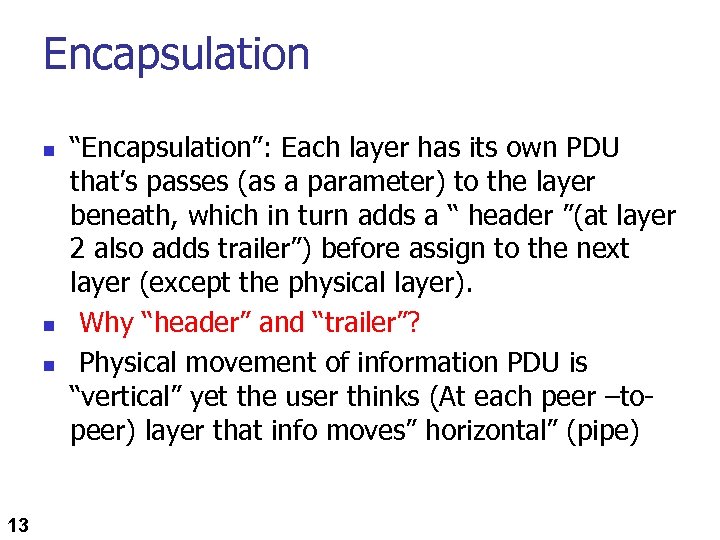 Encapsulation n 13 “Encapsulation”: Each layer has its own PDU that’s passes (as a parameter) to the layer beneath, which in turn adds a “ header ”(at layer 2 also adds trailer”) before assign to the next layer (except the physical layer). Why “header” and “trailer”? Physical movement of information PDU is “vertical” yet the user thinks (At each peer –topeer) layer that info moves” horizontal” (pipe)
Encapsulation n 13 “Encapsulation”: Each layer has its own PDU that’s passes (as a parameter) to the layer beneath, which in turn adds a “ header ”(at layer 2 also adds trailer”) before assign to the next layer (except the physical layer). Why “header” and “trailer”? Physical movement of information PDU is “vertical” yet the user thinks (At each peer –topeer) layer that info moves” horizontal” (pipe)
 2 -3 LAYERS IN THE OSI MODEL In this section we briefly describe the functions of each layer in the OSI model. Topics discussed in this section: Physical Layer Data Link Layer Network Layer Transport Layer Session Layer Presentation Layer Application Layer 14
2 -3 LAYERS IN THE OSI MODEL In this section we briefly describe the functions of each layer in the OSI model. Topics discussed in this section: Physical Layer Data Link Layer Network Layer Transport Layer Session Layer Presentation Layer Application Layer 14
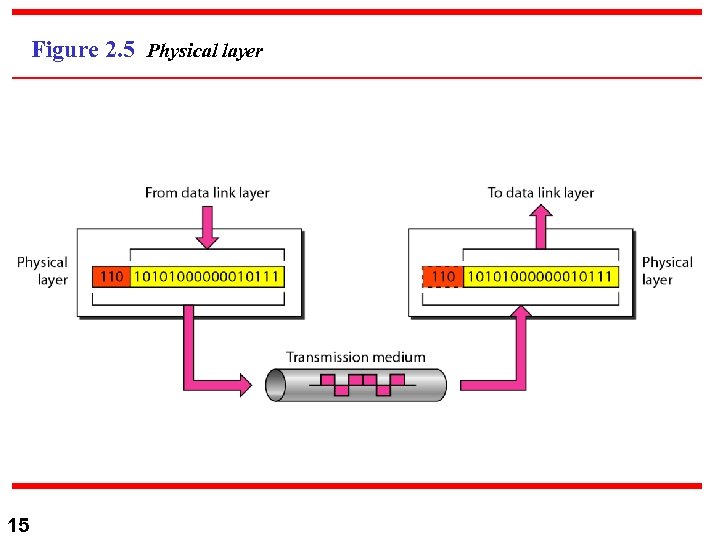 Figure 2. 5 Physical layer 15
Figure 2. 5 Physical layer 15
 1) Physical Layer n n n n n 16 1) Physical Layer: PDU N/A, bit stream. Moves bit sequence over a physical link. Defines the following: a) Physical characteristics of EIA interfaces and medium. b) Bit representation: encoding/decoding, electrical/optical. c) Data rate: (b/s) bit TX duration. d) Bits synch: sender and receiver clock synch and same data rate. e) Line configuration: Point-to-point, Multipoint f) Physical Topology: Mesh, ring, bus, and hybrid. g) Transfer mode: Simplex, Fid, and Hid
1) Physical Layer n n n n n 16 1) Physical Layer: PDU N/A, bit stream. Moves bit sequence over a physical link. Defines the following: a) Physical characteristics of EIA interfaces and medium. b) Bit representation: encoding/decoding, electrical/optical. c) Data rate: (b/s) bit TX duration. d) Bits synch: sender and receiver clock synch and same data rate. e) Line configuration: Point-to-point, Multipoint f) Physical Topology: Mesh, ring, bus, and hybrid. g) Transfer mode: Simplex, Fid, and Hid
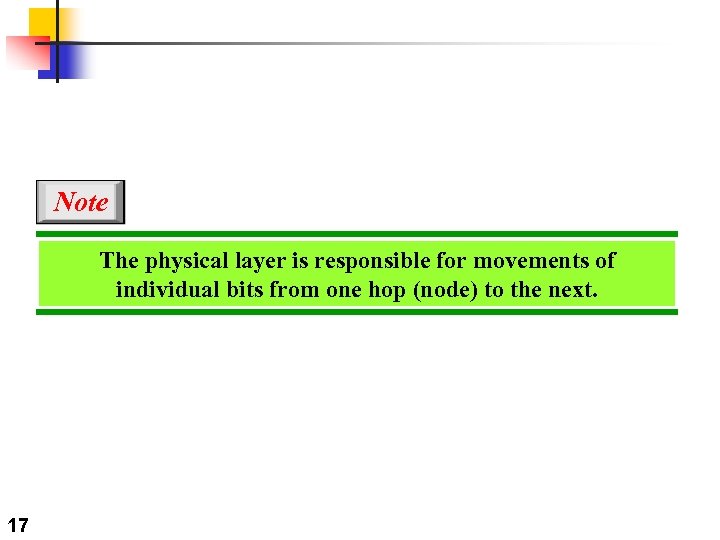 Note The physical layer is responsible for movements of individual bits from one hop (node) to the next. 17
Note The physical layer is responsible for movements of individual bits from one hop (node) to the next. 17
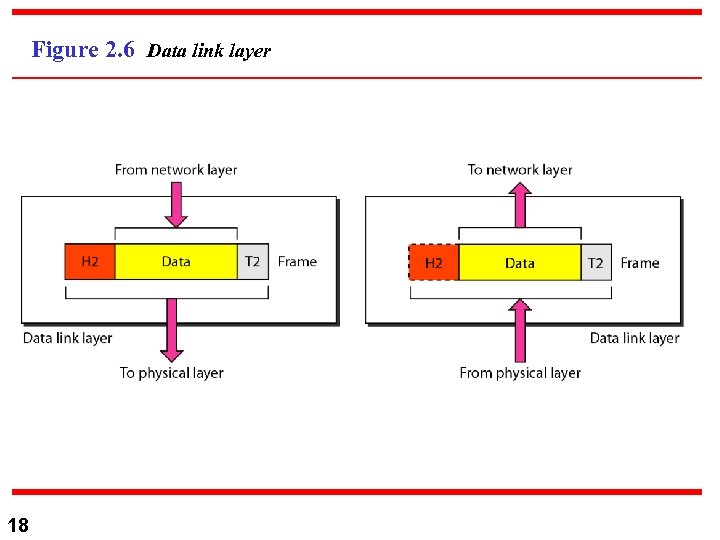 Figure 2. 6 Data link layer 18
Figure 2. 6 Data link layer 18
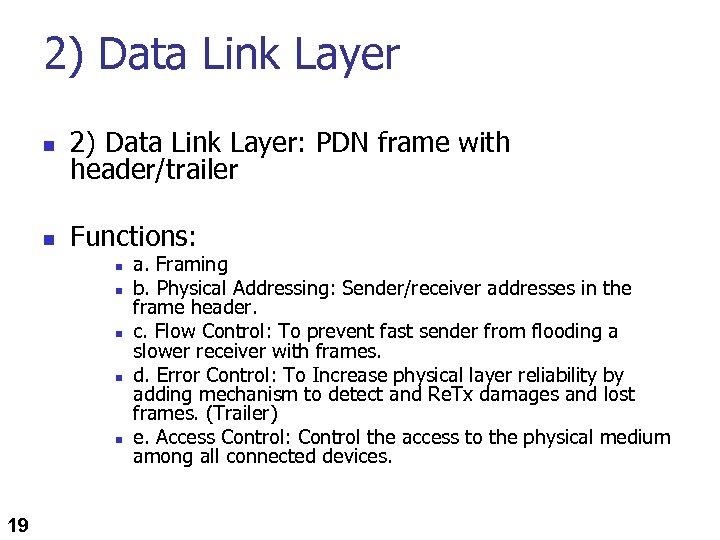 2) Data Link Layer n 2) Data Link Layer: PDN frame with header/trailer n Functions: n n n 19 a. Framing b. Physical Addressing: Sender/receiver addresses in the frame header. c. Flow Control: To prevent fast sender from flooding a slower receiver with frames. d. Error Control: To Increase physical layer reliability by adding mechanism to detect and Re. Tx damages and lost frames. (Trailer) e. Access Control: Control the access to the physical medium among all connected devices.
2) Data Link Layer n 2) Data Link Layer: PDN frame with header/trailer n Functions: n n n 19 a. Framing b. Physical Addressing: Sender/receiver addresses in the frame header. c. Flow Control: To prevent fast sender from flooding a slower receiver with frames. d. Error Control: To Increase physical layer reliability by adding mechanism to detect and Re. Tx damages and lost frames. (Trailer) e. Access Control: Control the access to the physical medium among all connected devices.
 Note The data link layer is responsible for moving frames from one hop (node) to the next. 20
Note The data link layer is responsible for moving frames from one hop (node) to the next. 20
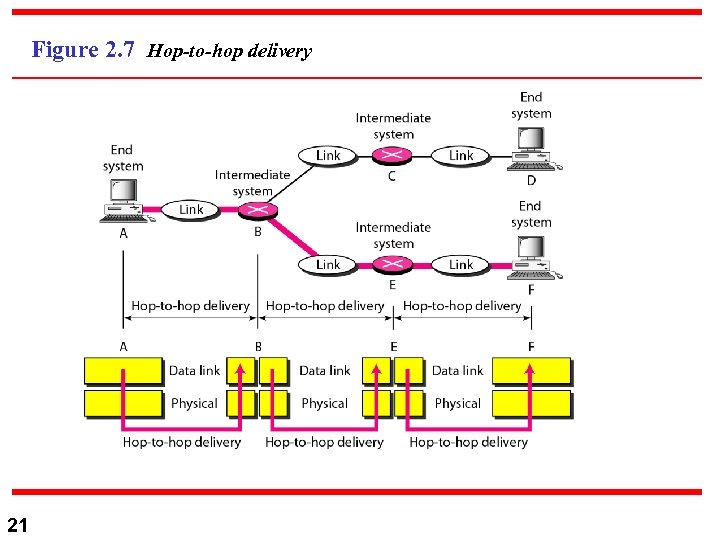 Figure 2. 7 Hop-to-hop delivery 21
Figure 2. 7 Hop-to-hop delivery 21
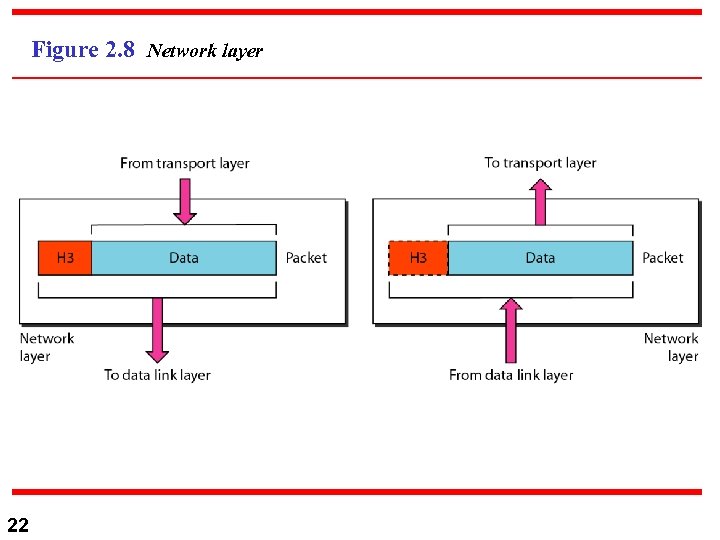 Figure 2. 8 Network layer 22
Figure 2. 8 Network layer 22
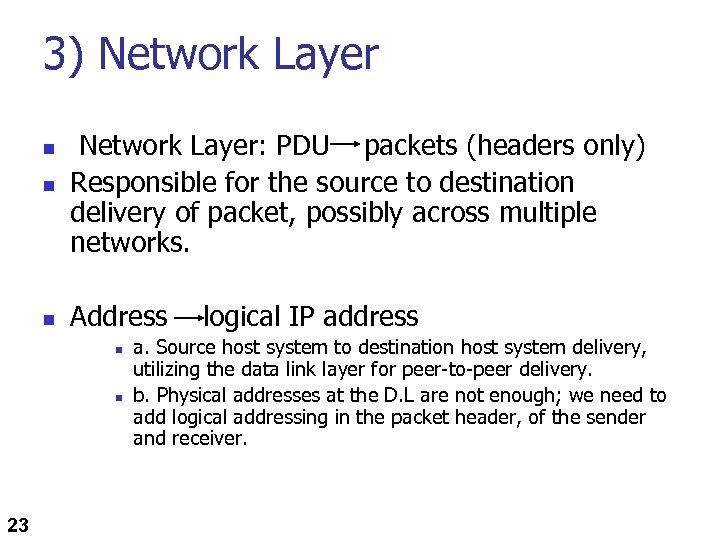 3) Network Layer n Network Layer: PDU packets (headers only) Responsible for the source to destination delivery of packet, possibly across multiple networks. n Address n n n 23 logical IP address a. Source host system to destination host system delivery, utilizing the data link layer for peer-to-peer delivery. b. Physical addresses at the D. L are not enough; we need to add logical addressing in the packet header, of the sender and receiver.
3) Network Layer n Network Layer: PDU packets (headers only) Responsible for the source to destination delivery of packet, possibly across multiple networks. n Address n n n 23 logical IP address a. Source host system to destination host system delivery, utilizing the data link layer for peer-to-peer delivery. b. Physical addresses at the D. L are not enough; we need to add logical addressing in the packet header, of the sender and receiver.
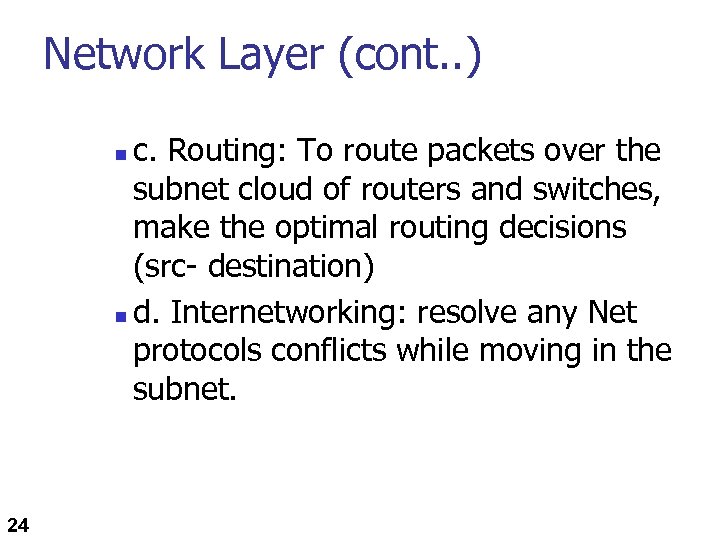 Network Layer (cont. . ) c. Routing: To route packets over the subnet cloud of routers and switches, make the optimal routing decisions (src- destination) n d. Internetworking: resolve any Net protocols conflicts while moving in the subnet. n 24
Network Layer (cont. . ) c. Routing: To route packets over the subnet cloud of routers and switches, make the optimal routing decisions (src- destination) n d. Internetworking: resolve any Net protocols conflicts while moving in the subnet. n 24
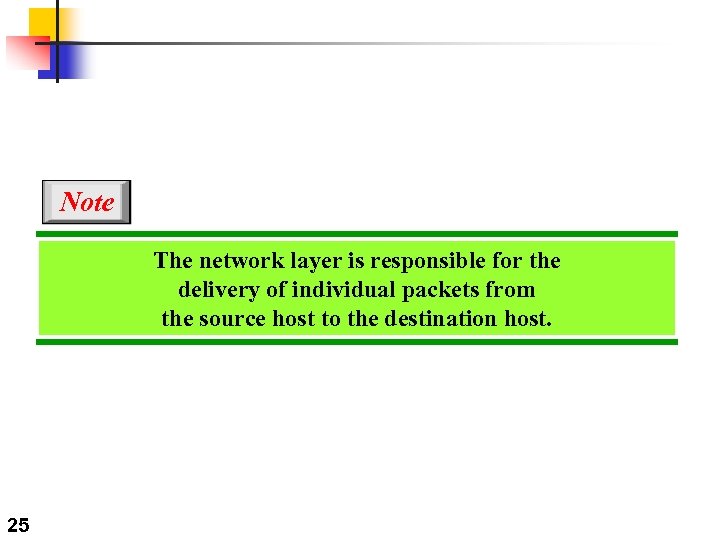 Note The network layer is responsible for the delivery of individual packets from the source host to the destination host. 25
Note The network layer is responsible for the delivery of individual packets from the source host to the destination host. 25
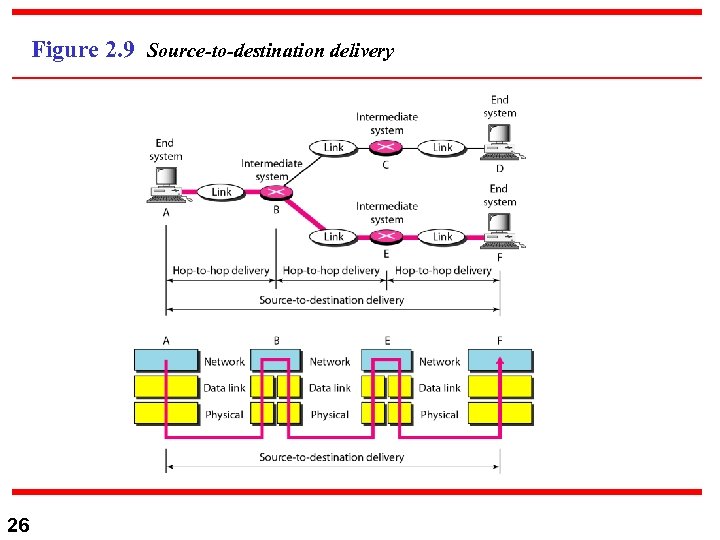 Figure 2. 9 Source-to-destination delivery 26
Figure 2. 9 Source-to-destination delivery 26
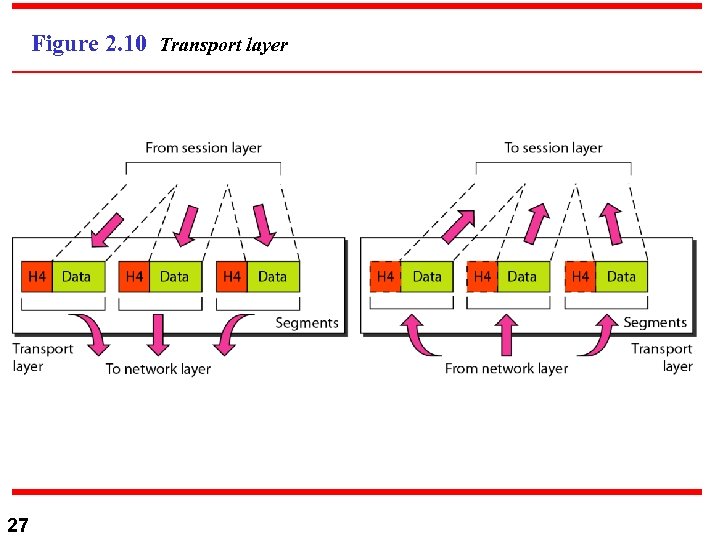 Figure 2. 10 Transport layer 27
Figure 2. 10 Transport layer 27
 4) Transport Layer: n n 28 The most important layer since it abstracts the complete details of the subnet to the user. It communicates a meaningful data unit called message (group of related packets) between users over the subnet trying for the most optimal utilization of the subnet.
4) Transport Layer: n n 28 The most important layer since it abstracts the complete details of the subnet to the user. It communicates a meaningful data unit called message (group of related packets) between users over the subnet trying for the most optimal utilization of the subnet.
 4) Transport Layer: (cont. . ) n n Responsibilities: a) Service Access Point Addressing: (SAP) The network logical address is for src_sys to destination not src_user_process to destination_user_process, hence we need another address mechanism => SAP addresses within the same system for user message delivery. 29
4) Transport Layer: (cont. . ) n n Responsibilities: a) Service Access Point Addressing: (SAP) The network logical address is for src_sys to destination not src_user_process to destination_user_process, hence we need another address mechanism => SAP addresses within the same system for user message delivery. 29
 Transport Layer: (cont. . ) n b) Segmentation and reassembly: of segments=> packets A Process (user) message is divided into segments (if needed) each with n seg. Sequence number to aid in assembly (incorrect order) related segments into the original message at the destination/transportation layer. 30
Transport Layer: (cont. . ) n b) Segmentation and reassembly: of segments=> packets A Process (user) message is divided into segments (if needed) each with n seg. Sequence number to aid in assembly (incorrect order) related segments into the original message at the destination/transportation layer. 30
 Transport Layer: (cont. . ) n n n c) Connection control: 1) Connection reliable service (-no ACK, -no guarantee) 2) Connectionless unreliable service n n 31 • In connection oriented TCP, guarantees delivery in order with ACK of segments. d) Flow Control: As in the data Link Layer but all the message level “end-users”.
Transport Layer: (cont. . ) n n n c) Connection control: 1) Connection reliable service (-no ACK, -no guarantee) 2) Connectionless unreliable service n n 31 • In connection oriented TCP, guarantees delivery in order with ACK of segments. d) Flow Control: As in the data Link Layer but all the message level “end-users”.
 Transport Layer: (cont. . ) n n 32 e) Error Control: Like the DLL, but process_to_process delivery of messages. Errors(damaged, loss or duplicate)cause re. Transmission of messages.
Transport Layer: (cont. . ) n n 32 e) Error Control: Like the DLL, but process_to_process delivery of messages. Errors(damaged, loss or duplicate)cause re. Transmission of messages.
 Note The transport layer is responsible for the delivery of a message from one process to another. 33
Note The transport layer is responsible for the delivery of a message from one process to another. 33
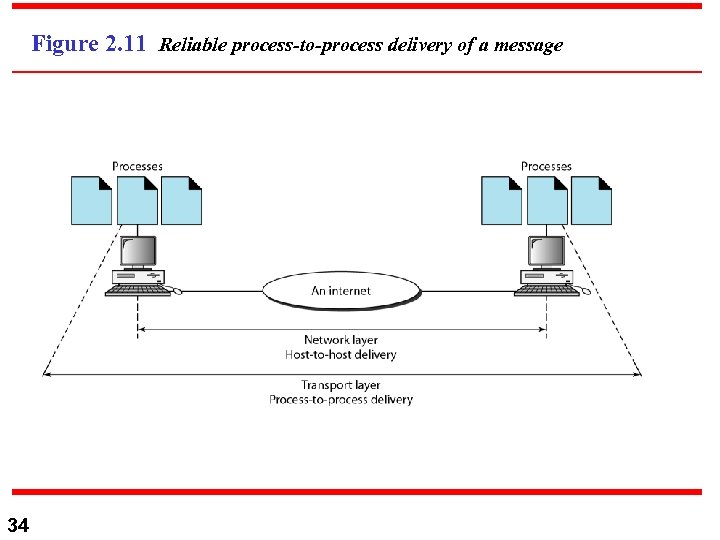 Figure 2. 11 Reliable process-to-process delivery of a message 34
Figure 2. 11 Reliable process-to-process delivery of a message 34
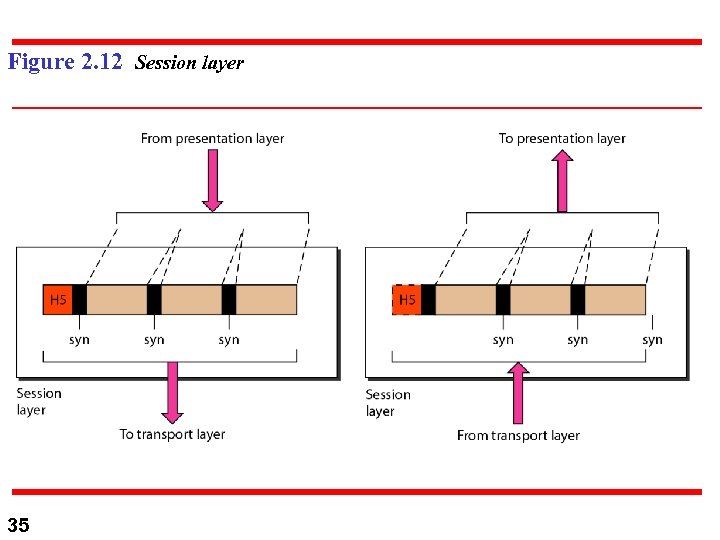 Figure 2. 12 Session layer 35
Figure 2. 12 Session layer 35
 5) Session Layer: n n Session Layer: ( Nwk dialog controller) It established, maintain and synchronizes the interaction among communicating system. n n 36 a. Dialog Controls H/Duplex or F/Duplex b. Synchronization: Checkpoints are added to data streams for dividing into units of independent ACK. Communication robustness in case of crashes.
5) Session Layer: n n Session Layer: ( Nwk dialog controller) It established, maintain and synchronizes the interaction among communicating system. n n 36 a. Dialog Controls H/Duplex or F/Duplex b. Synchronization: Checkpoints are added to data streams for dividing into units of independent ACK. Communication robustness in case of crashes.
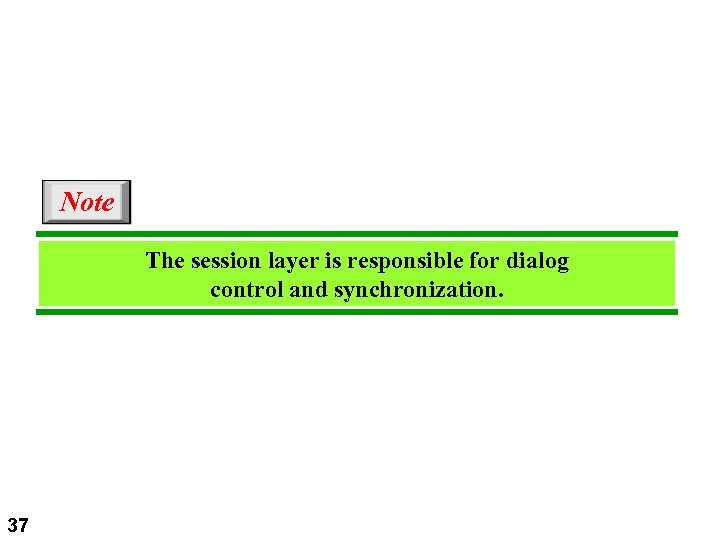 Note The session layer is responsible for dialog control and synchronization. 37
Note The session layer is responsible for dialog control and synchronization. 37
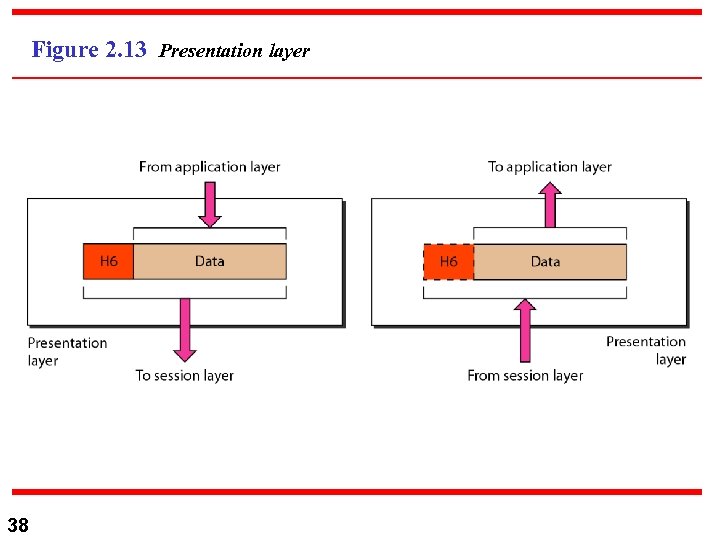 Figure 2. 13 Presentation layer 38
Figure 2. 13 Presentation layer 38
 Note The presentation layer is responsible for translation, compression, and encryption. 39
Note The presentation layer is responsible for translation, compression, and encryption. 39
 6) Presentation Layer n n 40 Presentation Layer: a. Translation: ASCII, --. EBCDIC. Abstract syntax notation (ASN). b. Encryption: To secure information Tx for privacy c. Compression: For efficient utilization of bandwidth.
6) Presentation Layer n n 40 Presentation Layer: a. Translation: ASCII, --. EBCDIC. Abstract syntax notation (ASN). b. Encryption: To secure information Tx for privacy c. Compression: For efficient utilization of bandwidth.
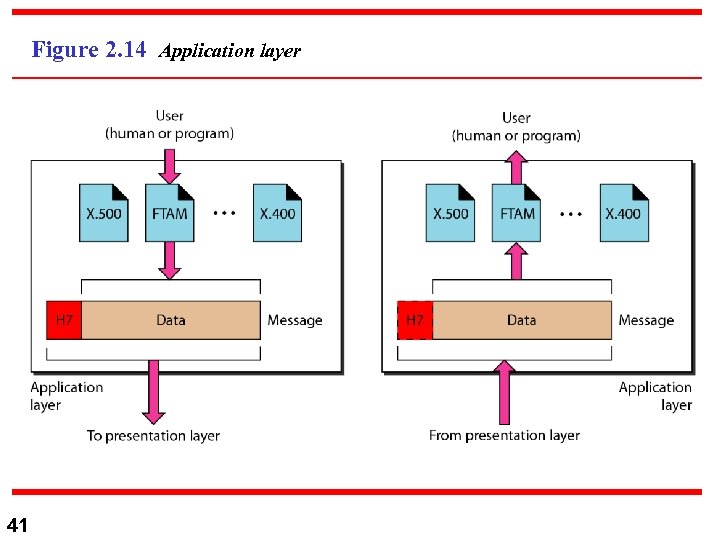 Figure 2. 14 Application layer 41
Figure 2. 14 Application layer 41
 Note The application layer is responsible for providing services to the user. 42
Note The application layer is responsible for providing services to the user. 42
 7) Application Layer: n n n 43 Application Layer: 1) Virtual terminal”putty”to allow remote logins (emulations) 2) File transfer , access, and management 3) Mail Service, 4) Directory service. SMTP, FTP, HTTP, DNS, SNMP, TELNET.
7) Application Layer: n n n 43 Application Layer: 1) Virtual terminal”putty”to allow remote logins (emulations) 2) File transfer , access, and management 3) Mail Service, 4) Directory service. SMTP, FTP, HTTP, DNS, SNMP, TELNET.
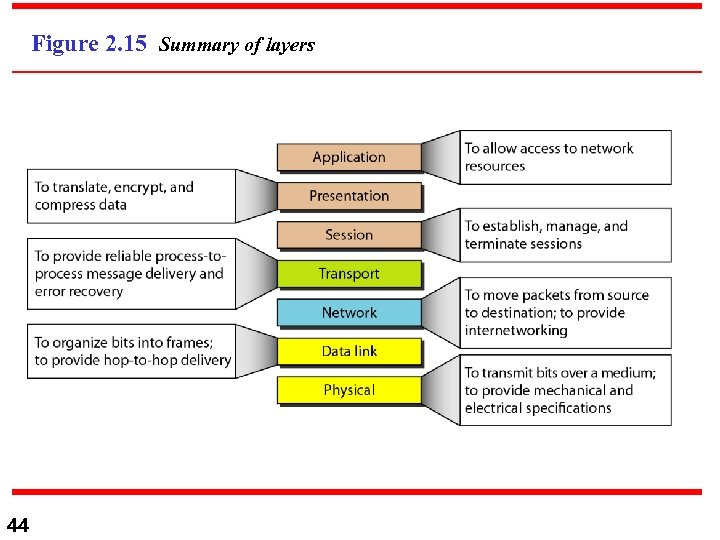 Figure 2. 15 Summary of layers 44
Figure 2. 15 Summary of layers 44
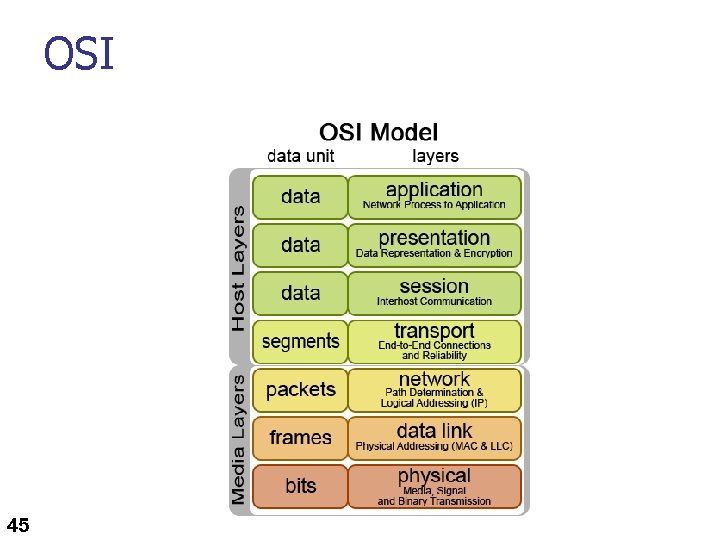 OSI 45
OSI 45
 2 -4 TCP/IP PROTOCOL SUITE The layers in the TCP/IP protocol suite do not exactly match those in the OSI model. The original TCP/IP protocol suite was defined as having four layers: host-tonetwork, internet, transport, and application. However, when TCP/IP is compared to OSI, we can say that the TCP/IP protocol suite is made of five layers: physical, data link, network, transport, and application. Topics discussed in this section: Physical and Data Link Layers Network Layer Transport Layer Application Layer 46
2 -4 TCP/IP PROTOCOL SUITE The layers in the TCP/IP protocol suite do not exactly match those in the OSI model. The original TCP/IP protocol suite was defined as having four layers: host-tonetwork, internet, transport, and application. However, when TCP/IP is compared to OSI, we can say that the TCP/IP protocol suite is made of five layers: physical, data link, network, transport, and application. Topics discussed in this section: Physical and Data Link Layers Network Layer Transport Layer Application Layer 46
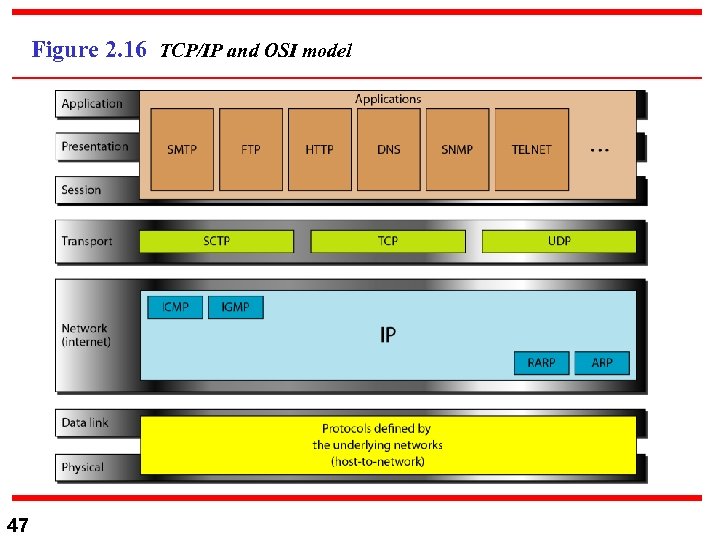 Figure 2. 16 TCP/IP and OSI model 47
Figure 2. 16 TCP/IP and OSI model 47
 n n n 48 1) Physical Layer: Very Vague, it can be LAN, MAN, WAN. 2) Network Layer: Internet Protocol (IP) is used best-effortdelivery unreliable connectionless datagram protocol (no end control flow). At the network layer there are other protocol to help the poor IP: a) Address Resolution Protocol: physical (MAC) logical (IP)
n n n 48 1) Physical Layer: Very Vague, it can be LAN, MAN, WAN. 2) Network Layer: Internet Protocol (IP) is used best-effortdelivery unreliable connectionless datagram protocol (no end control flow). At the network layer there are other protocol to help the poor IP: a) Address Resolution Protocol: physical (MAC) logical (IP)
 n n n 49 Address translation. b) Internet Control Msg Protocol (ICMP): Help in reporting any failure/congestion of a subnet part(s), aiding in the subnet robustness. c) Internet Group Msg Protocol (IGMP) Single source broadcasts to multi group destinations.
n n n 49 Address translation. b) Internet Control Msg Protocol (ICMP): Help in reporting any failure/congestion of a subnet part(s), aiding in the subnet robustness. c) Internet Group Msg Protocol (IGMP) Single source broadcasts to multi group destinations.
 n 50 3) Transport Layer: Proc-to-Proc client/server. A) User Datagram Protocol: UDP --- Connectionless unreliable Transport Protocol, with very limited error checking (checksum) --- No error/ flow control
n 50 3) Transport Layer: Proc-to-Proc client/server. A) User Datagram Protocol: UDP --- Connectionless unreliable Transport Protocol, with very limited error checking (checksum) --- No error/ flow control
 n B) Transmission Control Protocol: TCP ---Reliable connection oriented (stream) transport protocol. ---Establishes connection src_dest, before data Tx. ---Ordered/ ACK segment Tx with segment numbers. n C) Stream Control Tx Protocol: n n n SCTP Connection oriented reliable transport protocol to supports voice IP (Internet telephony) combining the best of UDP and TCP 51
n B) Transmission Control Protocol: TCP ---Reliable connection oriented (stream) transport protocol. ---Establishes connection src_dest, before data Tx. ---Ordered/ ACK segment Tx with segment numbers. n C) Stream Control Tx Protocol: n n n SCTP Connection oriented reliable transport protocol to supports voice IP (Internet telephony) combining the best of UDP and TCP 51
 2 -5 ADDRESSING Four levels of addresses are used in an internet employing the TCP/IP protocols: physical, logical, port, and specific. Topics discussed in this section: Physical Addresses Logical Addresses Port Addresses Specific Addresses 52
2 -5 ADDRESSING Four levels of addresses are used in an internet employing the TCP/IP protocols: physical, logical, port, and specific. Topics discussed in this section: Physical Addresses Logical Addresses Port Addresses Specific Addresses 52
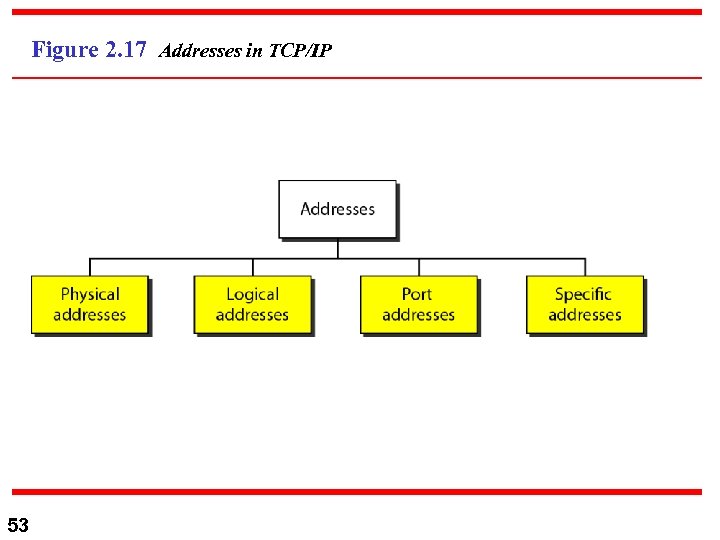 Figure 2. 17 Addresses in TCP/IP 53
Figure 2. 17 Addresses in TCP/IP 53
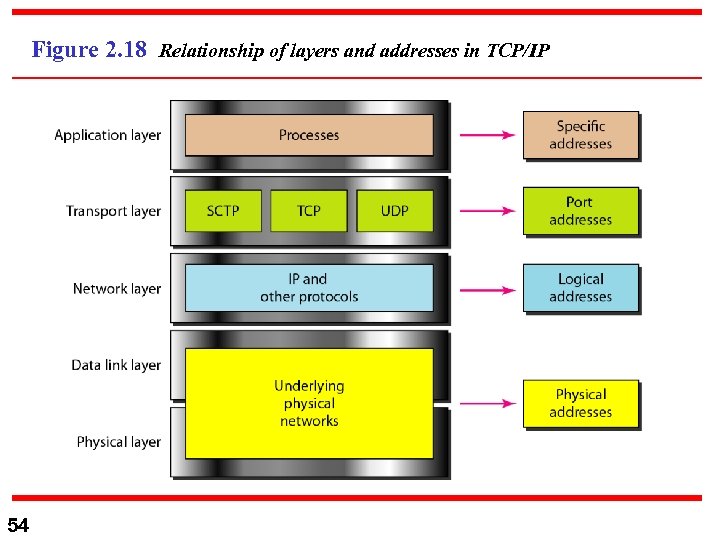 Figure 2. 18 Relationship of layers and addresses in TCP/IP 54
Figure 2. 18 Relationship of layers and addresses in TCP/IP 54
 Physical Address n n n 55 Physical address (Link address) is the address of a node as defined by its LAN or WAN. Lowest level address Have authority over the LAN or WAN nwks. The size and format of these addresses vary depending on the nwk. Eg : Ethernet uses 6 -byte physical address.
Physical Address n n n 55 Physical address (Link address) is the address of a node as defined by its LAN or WAN. Lowest level address Have authority over the LAN or WAN nwks. The size and format of these addresses vary depending on the nwk. Eg : Ethernet uses 6 -byte physical address.
 Example 2. 1 In Figure 2. 19 a node with physical address 10 sends a frame to a node with physical address 87. The two nodes are connected by a link (bus topology LAN). As the figure shows, the computer with physical address 10 is the sender, and the computer with physical address 87 is the receiver. 56
Example 2. 1 In Figure 2. 19 a node with physical address 10 sends a frame to a node with physical address 87. The two nodes are connected by a link (bus topology LAN). As the figure shows, the computer with physical address 10 is the sender, and the computer with physical address 87 is the receiver. 56
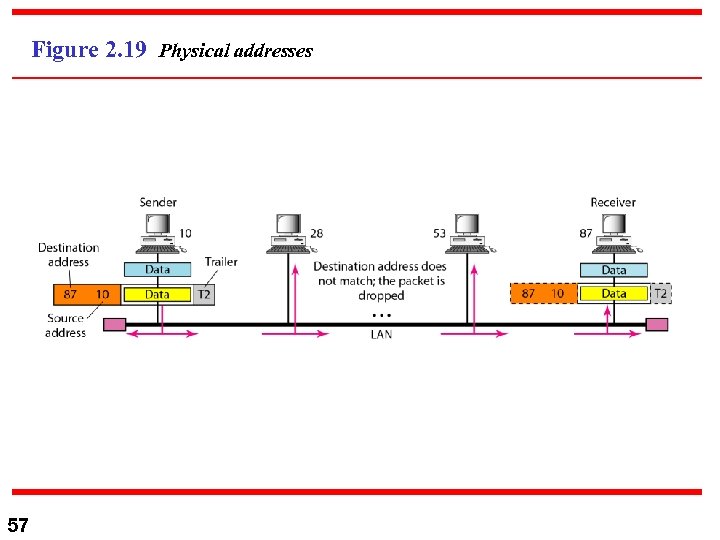 Figure 2. 19 Physical addresses 57
Figure 2. 19 Physical addresses 57
 Example 2. 2 As we will see in Chapter 13, most local-area networks use a 48 -bit (6 -byte) physical address written as 12 hexadecimal digits; every byte (2 hexadecimal digits) is separated by a colon, as shown below: 07: 01: 02: 01: 2 C: 4 B A 6 -byte (12 hexadecimal digits) physical address. 58
Example 2. 2 As we will see in Chapter 13, most local-area networks use a 48 -bit (6 -byte) physical address written as 12 hexadecimal digits; every byte (2 hexadecimal digits) is separated by a colon, as shown below: 07: 01: 02: 01: 2 C: 4 B A 6 -byte (12 hexadecimal digits) physical address. 58
 Logical Address n n 59 Necessary for universal communications that are independent of underlying physical networks. Different nwks can have different address format. An address defined in network layer. Logical address in the internet is 32 -bit address
Logical Address n n 59 Necessary for universal communications that are independent of underlying physical networks. Different nwks can have different address format. An address defined in network layer. Logical address in the internet is 32 -bit address
 Example 2. 3 Figure 2. 20 shows a part of an internet with two routers connecting three LANs. Each device (computer or router) has a pair of addresses (logical and physical) for each connection. In this case, each computer is connected to only one link and therefore has only one pair of addresses. Each router, however, is connected to three networks (only two are shown in the figure). So each router has three pairs of addresses, one for each connection. 60
Example 2. 3 Figure 2. 20 shows a part of an internet with two routers connecting three LANs. Each device (computer or router) has a pair of addresses (logical and physical) for each connection. In this case, each computer is connected to only one link and therefore has only one pair of addresses. Each router, however, is connected to three networks (only two are shown in the figure). So each router has three pairs of addresses, one for each connection. 60
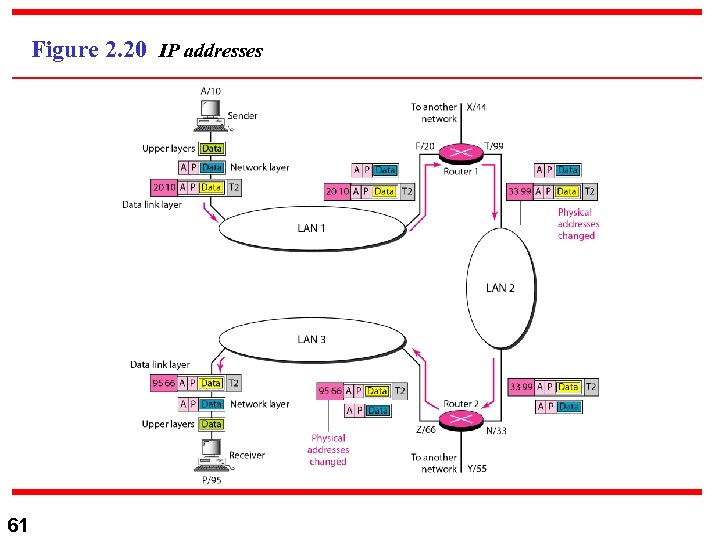 Figure 2. 20 IP addresses 61
Figure 2. 20 IP addresses 61
 Port addresses n n 62 A method is needed to label the different processes. ( addresses are needed) Process communicating with another process eg : Comp. A can communicate with comp. C by using TELNET. At the same time comp. A communicate with comp. B by using FTP
Port addresses n n 62 A method is needed to label the different processes. ( addresses are needed) Process communicating with another process eg : Comp. A can communicate with comp. C by using TELNET. At the same time comp. A communicate with comp. B by using FTP
 Example 2. 4 Figure 2. 21 shows two computers communicating via the Internet. The sending computer is running three processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to hop, logical and port addresses remain the same from the source to destination. 63
Example 2. 4 Figure 2. 21 shows two computers communicating via the Internet. The sending computer is running three processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to hop, logical and port addresses remain the same from the source to destination. 63
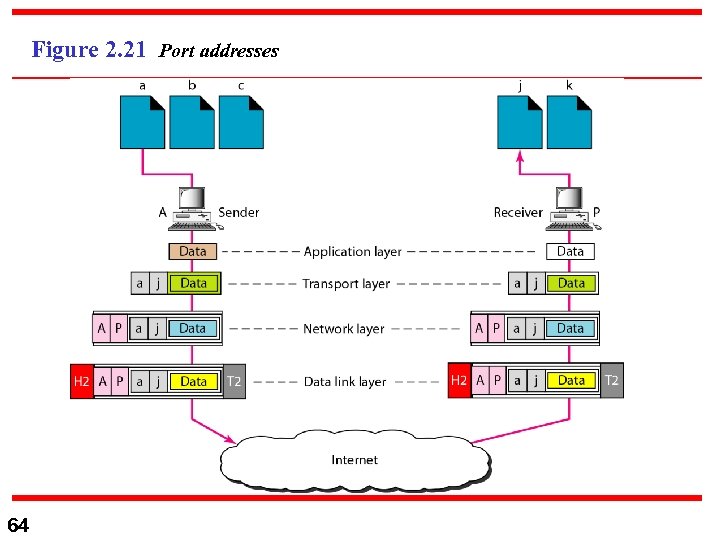 Figure 2. 21 Port addresses 64
Figure 2. 21 Port addresses 64
 Note The physical addresses will change from hop to hop, but the logical addresses usually remain the same. 65
Note The physical addresses will change from hop to hop, but the logical addresses usually remain the same. 65
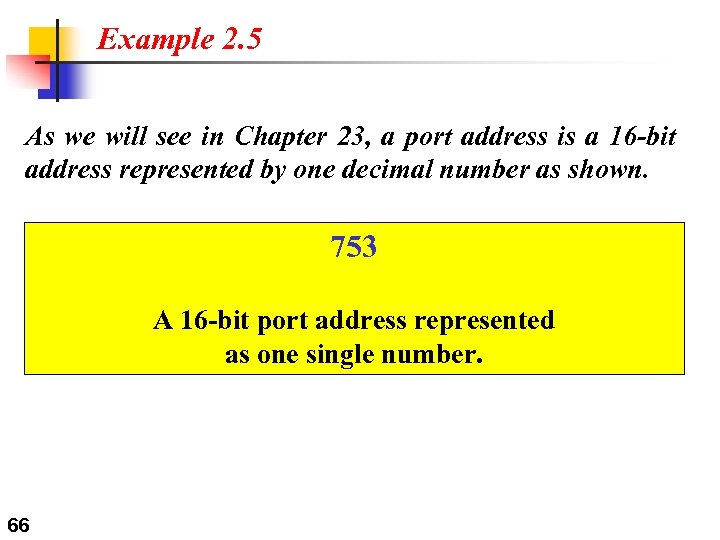 Example 2. 5 As we will see in Chapter 23, a port address is a 16 -bit address represented by one decimal number as shown. 753 A 16 -bit port address represented as one single number. 66
Example 2. 5 As we will see in Chapter 23, a port address is a 16 -bit address represented by one decimal number as shown. 753 A 16 -bit port address represented as one single number. 66
 Note The physical addresses change from hop to hop, but the logical and port addresses usually remain the same. 67
Note The physical addresses change from hop to hop, but the logical and port addresses usually remain the same. 67


