eabc0256378e762292b4bc5b268ca035.ppt
- Количество слайдов: 17

Chapter 19 Security

Agenda • Database Security • Countermeasure – Computer-based – Non-computer-based • Challenge over the Internet • Firewall • Web security

Database Security • Definition – Mechanisms to protect the database against intentional or accidental threats • Asset – – – • Hardware Software Communication network Database Individual (user, programmer, operator, administrator, and outsider) Threat – Theft and fraud • Consequence – – Loss of confidentiality Loss of privacy Loss of integrity Loss of availability
Countermeasures • Computer-based controls • Non-computer-based controls

Computer-based Controls - 1 • Authorization & authentication – Password and account number – Discretionary access control (grant and revoke) – Mandatory access control (object, security class, and clearance) • Virtual views

Computer-based Controls - 2 • Logs or journaling – Transaction log – Violation log • Check points • Integrity – – Domain Enterprise Entity Referential • Backup (redundant array of independent disks - RAID) & recovery • Audit

Computer-based Controls - 3 • Encryption or cryptosystem – Encryption key – Encryption algorithm – Decryption key – Decryption algorithm – Symmetric encryption (Data Encryption Standard (DES) – Asymmetric encryption (RSA)

Example of Encryption - I • Divide text into groups of 8 characters. Pad with blank at end as necessary • Select an 8 -characters key • Rearrange text by interchanging adjacent characters • Translate each character into an ordinal number with blank as 0, A as 1, B as 2… • Add the ordinal number of the key to the results • Divide the total by 27 and retain the remainder • Translate the remainder back into a character to yield the cipher text
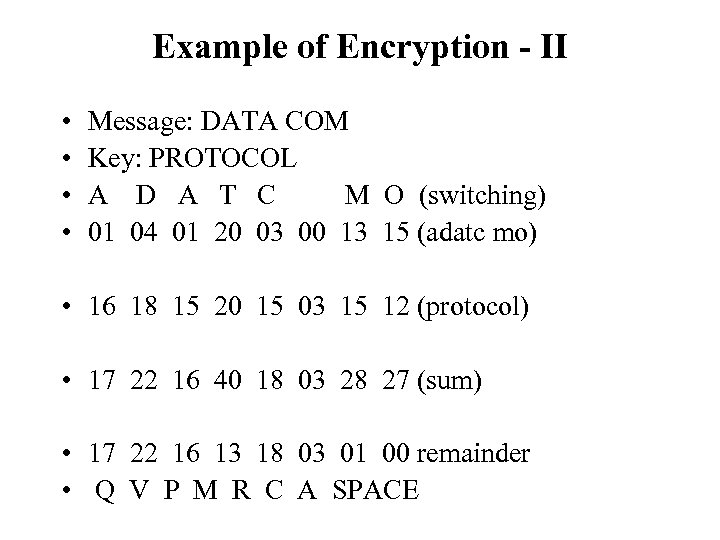
Example of Encryption - II • • Message: DATA COM Key: PROTOCOL A D A T C M O (switching) 01 04 01 20 03 00 13 15 (adatc mo) • 16 18 15 20 15 03 15 12 (protocol) • 17 22 16 40 18 03 28 27 (sum) • 17 22 16 13 18 03 01 00 remainder • Q V P M R C A SPACE

Example of Decryption - I • Divide cipher text into groups of eight characters. Pad with blanks at end as necessary • Translate each cipher text alphabetic character and the encryption key into an ordinal number • For each group, subtract the ordinal number of the key value from the ordinal number of the cipher text • Add 27 to any negative number • Translate the number back to alphabetic equivalents • Rearrange the text by interchanging adjacent characters
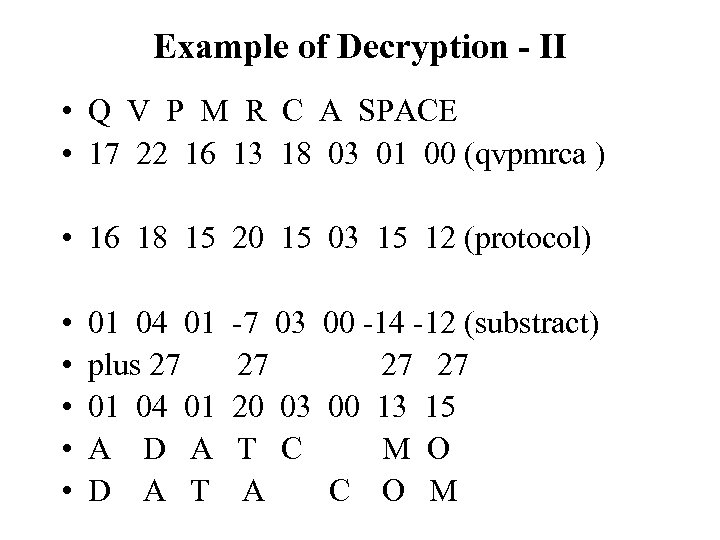
Example of Decryption - II • Q V P M R C A SPACE • 17 22 16 13 18 03 01 00 (qvpmrca ) • 16 18 15 20 15 03 15 12 (protocol) • • • 01 04 01 plus 27 01 04 01 A D A T -7 03 00 -14 -12 (substract) 27 27 27 20 03 00 13 15 T C M O A C O M

Non-Computer-based Controls • Security policy • Contingency plan – Person, phone no. , procedures – Site (cold, warm, or hot) • Personnel control – – Reference Termination Training Balance of duty • Escrow & maintenance agreements • Physical

Challenge over the Internet • Privacy (inaccessible except sender & receiver) • Integrity (no change during transmission) • Authenticity (genuine sender) • Non-fabrication (genuine receiver) • Non-repudiation (sender can not deny)
Firewall • Definition – A system to prevent unauthorized access to or from a private network • Types – Packet filter (difficult to configure and subject to IP spoofing) – Application gateway (degrade performance) – Circuit level gateway (TCP or User Datagram Protocol UDP) – Proxy server (performance & filtering)

Web Security • Message digest algorithms and digital signature • Digital signatures & Certificate Authority (CA) • Kerberos: centralized security server (certificate server • Secure Sockets Layer (SSL) for data & Secure HTTP (S-HTTP) for individual message • Secure Electronic Transaction (SET) for credit card & Secure Transaction Technology (STT) for bank payment

Points to Remember • Database Security • Countermeasure – Computer-based – Non-computer-based • Challenge over the Internet • Firewall • Web security

Assignment • Review chapters 5 -6, 11 -14, 19 • Read chapter 20 • Exam 3 – Date: • Project – Normalization and Corrected EER diagram due date: – SQL, corrected normalization, and EER diagram due date:
eabc0256378e762292b4bc5b268ca035.ppt