ba623731bfd19874519fb62224fad19a.ppt
- Количество слайдов: 27
 Chapter 15 Electronic Mail Security – Part II Data & Network Security Spring 2006 Dr. Jalili
Chapter 15 Electronic Mail Security – Part II Data & Network Security Spring 2006 Dr. Jalili
 Agenda In the previous session, we’ve studied PGP. In this session, other email security standards will be studied. n PEM n S/MIME n RFC 822 n MIME n 2
Agenda In the previous session, we’ve studied PGP. In this session, other email security standards will be studied. n PEM n S/MIME n RFC 822 n MIME n 2
 Phil’s feelings …a week before PGP's first release, I discovered the existence of another email encryption standard called Privacy Enhanced Mail (PEM), which was backed by several big companies, as well as RSA Data Security. n I didn't like PEM's design, for several reasons… n 3
Phil’s feelings …a week before PGP's first release, I discovered the existence of another email encryption standard called Privacy Enhanced Mail (PEM), which was backed by several big companies, as well as RSA Data Security. n I didn't like PEM's design, for several reasons… n 3
 Why not PEM? ! 1. 2. PEM used 56 -bit DES to encrypt Not an issue messages, which I did nottoday as regard strong cryptography. PEM absolutely required every message to be signed, and revealed the signature outside the encryption envelope, so that the message did not have to be decrypted to reveal who signed it. 4
Why not PEM? ! 1. 2. PEM used 56 -bit DES to encrypt Not an issue messages, which I did nottoday as regard strong cryptography. PEM absolutely required every message to be signed, and revealed the signature outside the encryption envelope, so that the message did not have to be decrypted to reveal who signed it. 4
 PEM Standard n PEM is described in RFCs 1421 -1424: Privacy Enhancement for Internet Electronic Mail (1993): 1. 2. 3. 4. Part I: Message Encryption and Authentication Procedures; Part II: Certificate-Based Key Management; Part III: Algorithms, Modes, and Identifiers; Part IV: Key Certification and Related Services. 5
PEM Standard n PEM is described in RFCs 1421 -1424: Privacy Enhancement for Internet Electronic Mail (1993): 1. 2. 3. 4. Part I: Message Encryption and Authentication Procedures; Part II: Certificate-Based Key Management; Part III: Algorithms, Modes, and Identifiers; Part IV: Key Certification and Related Services. 5
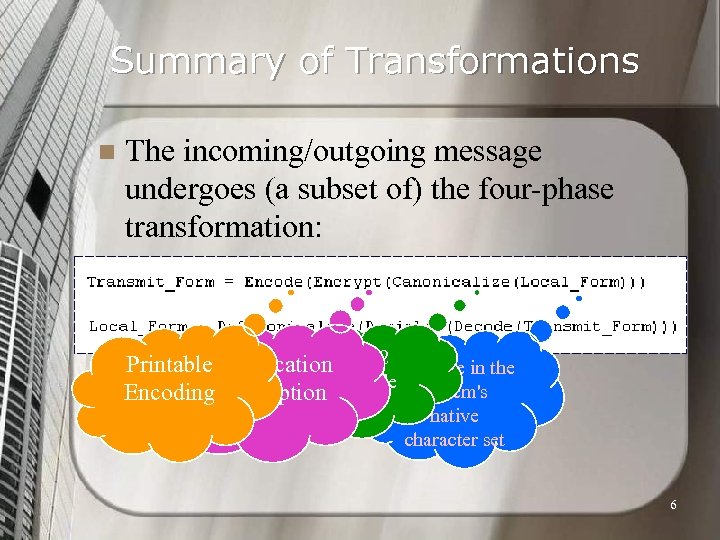 Summary of Transformations n The incoming/outgoing message undergoes (a subset of) the four-phase transformation: RFC Printable Authentication 822 Message in the compatible system's Encoding Encryption & native character set 6
Summary of Transformations n The incoming/outgoing message undergoes (a subset of) the four-phase transformation: RFC Printable Authentication 822 Message in the compatible system's Encoding Encryption & native character set 6
 PEM Encapsulation Adopted from RFC 934 encapsulation mechanism. n Uses Encapsulation Boundaries (EBs): n -----BEGIN PRIVACY-ENHANCED MESSAGE-----END PRIVACY-ENHANCED MESSAGE----- 7
PEM Encapsulation Adopted from RFC 934 encapsulation mechanism. n Uses Encapsulation Boundaries (EBs): n -----BEGIN PRIVACY-ENHANCED MESSAGE-----END PRIVACY-ENHANCED MESSAGE----- 7
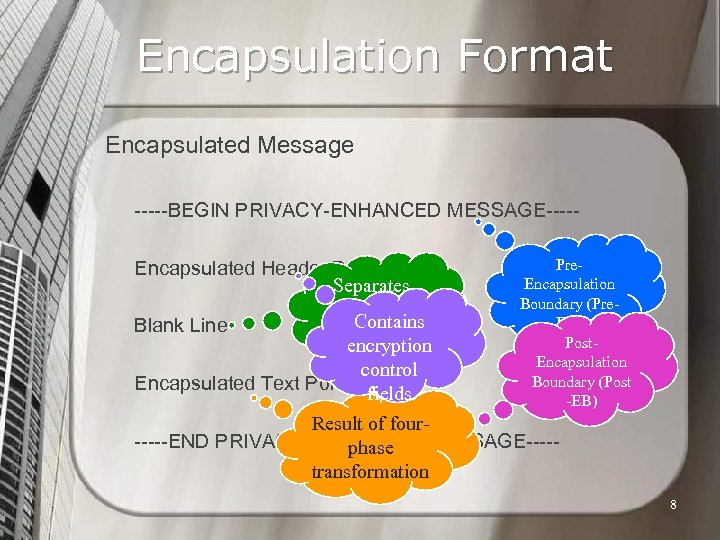 Encapsulation Format Encapsulated Message -----BEGIN PRIVACY-ENHANCED MESSAGE----Encapsulated Header Portion Separates Header & Contains Blank Line Body encryption control Encapsulated Text Portion fields Pre. Encapsulation Boundary (Pre. EB) Post. Encapsulation Boundary (Post -EB) Result of four-----END PRIVACY-ENHANCED MESSAGE----phase transformation 8
Encapsulation Format Encapsulated Message -----BEGIN PRIVACY-ENHANCED MESSAGE----Encapsulated Header Portion Separates Header & Contains Blank Line Body encryption control Encapsulated Text Portion fields Pre. Encapsulation Boundary (Pre. EB) Post. Encapsulation Boundary (Post -EB) Result of four-----END PRIVACY-ENHANCED MESSAGE----phase transformation 8
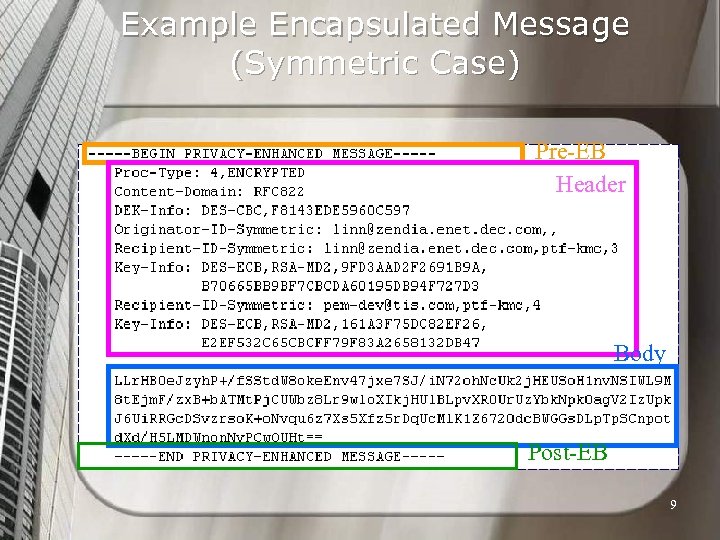 Example Encapsulated Message (Symmetric Case) Pre-EB Header Body Post-EB 9
Example Encapsulated Message (Symmetric Case) Pre-EB Header Body Post-EB 9
 Proc-Type Field n Identifies the type of processing performed on the transmitted message: ENCRYPTED; n MIC-ONLY; n MIC-CLEAR; n CRL; n Content-Domain Field; n DEK-Info Field; n MIC: Message Integrity Check DEK: Data Encrypting Keys 10
Proc-Type Field n Identifies the type of processing performed on the transmitted message: ENCRYPTED; n MIC-ONLY; n MIC-CLEAR; n CRL; n Content-Domain Field; n DEK-Info Field; n MIC: Message Integrity Check DEK: Data Encrypting Keys 10
 PEM Algorithms 11
PEM Algorithms 11
 PEM, Today, PEM is not used as a mail security/privacy tool anymore. n But, as stated in RFC 2315 (PKCS #7: Cryptographic Message Syntax v 1. 5), PEM & PKCS #7 are totally compatible. PKCS#7 messages can be converted into PEM messages without any cryptographic operations. n 12
PEM, Today, PEM is not used as a mail security/privacy tool anymore. n But, as stated in RFC 2315 (PKCS #7: Cryptographic Message Syntax v 1. 5), PEM & PKCS #7 are totally compatible. PKCS#7 messages can be converted into PEM messages without any cryptographic operations. n 12
 S/MIME Before studying S/MIME, one must first understand what RFC 822 & MIME are. n RFC 822 defines a format for text messages that are sent using electronic mail. n Consists of envelope & contents. n The content includes a set of header fields that may be used by the mail system to create the envelope. n 13
S/MIME Before studying S/MIME, one must first understand what RFC 822 & MIME are. n RFC 822 defines a format for text messages that are sent using electronic mail. n Consists of envelope & contents. n The content includes a set of header fields that may be used by the mail system to create the envelope. n 13
 RFC 822 Message Format Date: Tue, 9 May 2006 10: 37: 17 (EST) From: “Mahmood Ahmadinejad”
RFC 822 Message Format Date: Tue, 9 May 2006 10: 37: 17 (EST) From: “Mahmood Ahmadinejad”
 RFC 822 SMTP limitations 1. 2. 3. 4. 5. 6. Binary object transfer; 1. Handling Non-ASCII-7 encoding; CRLF; 2. 76 -Character lines; Message size limitations; spaces; 3. Trailing white 4. Padding of lines; ASCII-to-EBCDIC translation; 5. Handling Tab characters. SMTP gateways to X. 400 email networks can’t handle non-textual X. 400 messages; Some SMTP implementations inconsistent with RFC 821 SMTP. 15
RFC 822 SMTP limitations 1. 2. 3. 4. 5. 6. Binary object transfer; 1. Handling Non-ASCII-7 encoding; CRLF; 2. 76 -Character lines; Message size limitations; spaces; 3. Trailing white 4. Padding of lines; ASCII-to-EBCDIC translation; 5. Handling Tab characters. SMTP gateways to X. 400 email networks can’t handle non-textual X. 400 messages; Some SMTP implementations inconsistent with RFC 821 SMTP. 15
 MIME RFCs 2821 -2822 obsolete RFCs 821822. n MIME =Multipurpose Internet Mail Extensions. n An extension to the RFC 822 framework. n Intended to address some of the problems and limitations of the use of SMTP. n 16
MIME RFCs 2821 -2822 obsolete RFCs 821822. n MIME =Multipurpose Internet Mail Extensions. n An extension to the RFC 822 framework. n Intended to address some of the problems and limitations of the use of SMTP. n 16
 MIME RFCs n MIME is discussed in RFCs 2045 -2049: 2045: Format of Internet Message Bodies; n 2046: Media Types; n 2047: Message Header Extensions for Non. ASCII Text; n 2048: Registration Procedures; n 2049: Conformance Criteria and Examples; n 17
MIME RFCs n MIME is discussed in RFCs 2045 -2049: 2045: Format of Internet Message Bodies; n 2046: Media Types; n 2047: Message Header Extensions for Non. ASCII Text; n 2048: Registration Procedures; n 2049: Conformance Criteria and Examples; n 17
 MIME Specification 1. 2. 3. Five new message header fields are defined, which may be included in an RFC 822 header. A number of content formats for multimedia electronic mail are defined. Transfer encodings are defined that enable the conversion of any content format into a form that is protected from alteration by the mail system. 18
MIME Specification 1. 2. 3. Five new message header fields are defined, which may be included in an RFC 822 header. A number of content formats for multimedia electronic mail are defined. Transfer encodings are defined that enable the conversion of any content format into a form that is protected from alteration by the mail system. 18
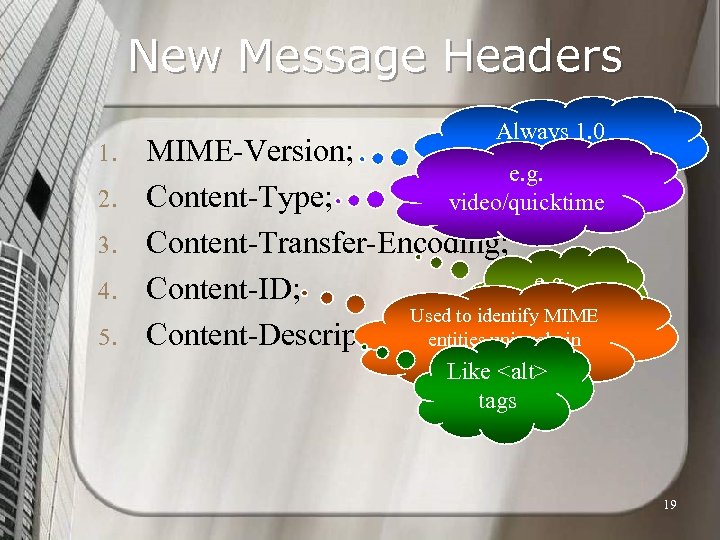 New Message Headers 1. 2. 3. 4. 5. Always 1. 0 RFCs 2045 -2046 e. g. video/quicktime MIME-Version; Content-Type; Content-Transfer-Encoding; e. g. Content-ID; binary Used to identify MIME Content-Description. entities uniquely in multiple
New Message Headers 1. 2. 3. 4. 5. Always 1. 0 RFCs 2045 -2046 e. g. video/quicktime MIME-Version; Content-Type; Content-Transfer-Encoding; e. g. Content-ID; binary Used to identify MIME Content-Description. entities uniquely in multiple
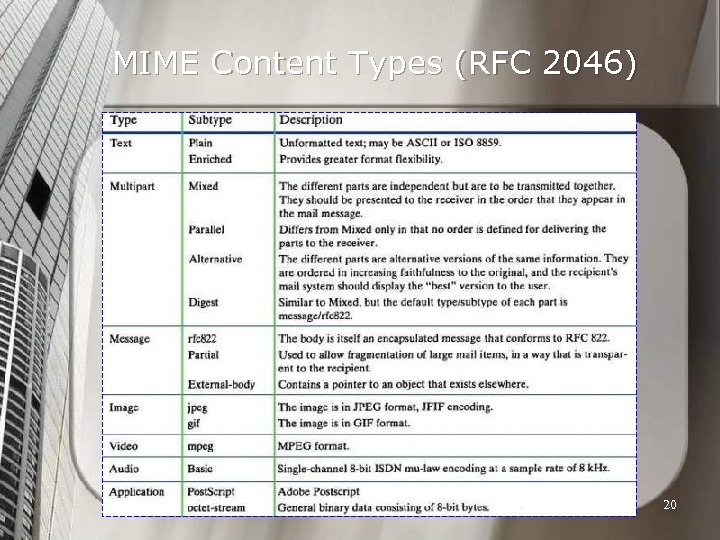 MIME Content Types (RFC 2046) 20
MIME Content Types (RFC 2046) 20
 Sample MIME Message From: “Mahmood Ahmadinejad”
Sample MIME Message From: “Mahmood Ahmadinejad”
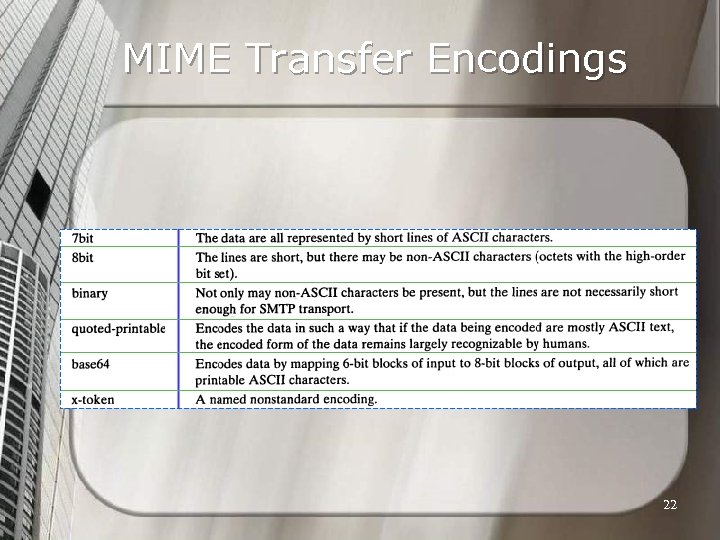 MIME Transfer Encodings 22
MIME Transfer Encodings 22
 Canonical Form An important concept in MIME and S/MIME. n Canonical form is a format, appropriate to the content type, that is standardized for use between systems. n May involve character set and EOL conversion, transformation of audio data, compression, etc. n 23
Canonical Form An important concept in MIME and S/MIME. n Canonical form is a format, appropriate to the content type, that is standardized for use between systems. n May involve character set and EOL conversion, transformation of audio data, compression, etc. n 23
 S/MIME n n Secure MIME (RFCs 2632 -2634). Both message & Provides four functions: signature are 1. 2. 3. 4. encoded using Enveloped data; Base 64. Signed data; Clear-Signed data; Signed & Enveloped data. Only signature is encoded using Base 64. 24
S/MIME n n Secure MIME (RFCs 2632 -2634). Both message & Provides four functions: signature are 1. 2. 3. 4. encoded using Enveloped data; Base 64. Signed data; Clear-Signed data; Signed & Enveloped data. Only signature is encoded using Base 64. 24
 S/MIME Algorithms DSS: preferred for digital signature. n DH (El. Gamal): preferred for session key encryption. n RSA: signing and/or encryption. n 3 DES/RC 2 (40 bits): message encryption. n SHA-1/MD 5: digest. n RFC 2119 n There are some RULES for algorithm selection (MUST/SHOULD). 25
S/MIME Algorithms DSS: preferred for digital signature. n DH (El. Gamal): preferred for session key encryption. n RSA: signing and/or encryption. n 3 DES/RC 2 (40 bits): message encryption. n SHA-1/MD 5: digest. n RFC 2119 n There are some RULES for algorithm selection (MUST/SHOULD). 25
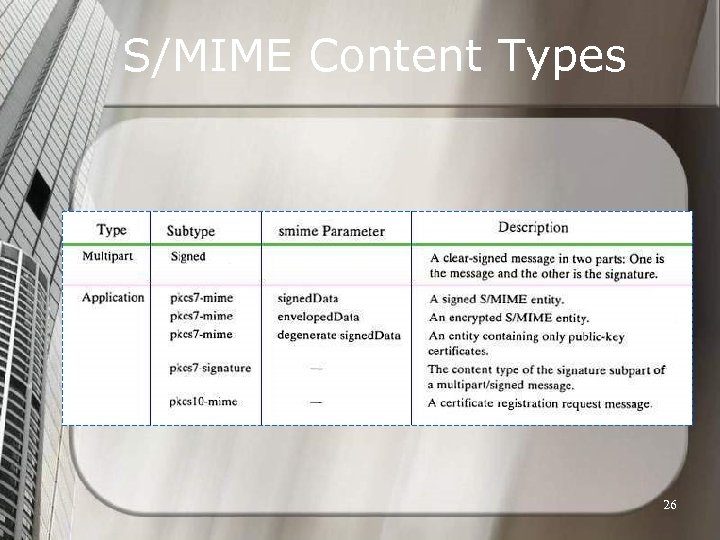 S/MIME Content Types 26
S/MIME Content Types 26
 S/MIME Certificate Processing S/MIME uses public-key certificates that conform to X. 509 v 3. n The key-management scheme used by S/MIME is in some ways a hybrid between a strict X. 509 certification hierarchy and PGP's web of trust. n PGP is suitable for personal use, while S/MIME is appropriate for commercial use. n 27
S/MIME Certificate Processing S/MIME uses public-key certificates that conform to X. 509 v 3. n The key-management scheme used by S/MIME is in some ways a hybrid between a strict X. 509 certification hierarchy and PGP's web of trust. n PGP is suitable for personal use, while S/MIME is appropriate for commercial use. n 27


