04f0bd549f250d2766fb399e9d54e8b3.ppt
- Количество слайдов: 33
 Chapter 13 Network Management Applications The management of networked information services involves both network and system resources. OSI defines network management as a five-layer architecture. We extended the model to include system management and present the integrated architecture in Figure 13. 1: L 5 business management L 4 Service management L 3 network management or system management L 2 element management or resource management L 1 network elements and system resources
Chapter 13 Network Management Applications The management of networked information services involves both network and system resources. OSI defines network management as a five-layer architecture. We extended the model to include system management and present the integrated architecture in Figure 13. 1: L 5 business management L 4 Service management L 3 network management or system management L 2 element management or resource management L 1 network elements and system resources
 13. 1 Configuration Management Configuration management in network management is normally used in the context of discovering network topology, mapping the network, and setting up configuration parameters in management agents and management systems. Network management in the broad sense also includes network provisioning, which includes network planning and design. Network provisioning is considered to be part of configuration management.
13. 1 Configuration Management Configuration management in network management is normally used in the context of discovering network topology, mapping the network, and setting up configuration parameters in management agents and management systems. Network management in the broad sense also includes network provisioning, which includes network planning and design. Network provisioning is considered to be part of configuration management.
 13. 1. 1 Network Provisioning Network provisioning, also called circuit provisioning in the telephone industry, is an automated process. A trunk (circuit from the originating switching center to the destination switching center) and a special service circuit (customized to meet customer specifications) are designed by application programs written in operation systems, Planning and inventory systems are integrated with design systems to build an overall system. Thus a circuit designed for the future automatically derives its turn-on date from the planning system and ensures that the components are available in the inventory system.
13. 1. 1 Network Provisioning Network provisioning, also called circuit provisioning in the telephone industry, is an automated process. A trunk (circuit from the originating switching center to the destination switching center) and a special service circuit (customized to meet customer specifications) are designed by application programs written in operation systems, Planning and inventory systems are integrated with design systems to build an overall system. Thus a circuit designed for the future automatically derives its turn-on date from the planning system and ensures that the components are available in the inventory system.
 13. 1. 2 Inventory Management An efficient database system is an essential part of an inventory management system. We need to be aware of the specification details associated with various components. The data should be accessible by means of different indices. Some of the obvious indices or access keys are the component description or part number, components that match a set of characteristics, components in use and in spare, and components to be freed-up for future use.
13. 1. 2 Inventory Management An efficient database system is an essential part of an inventory management system. We need to be aware of the specification details associated with various components. The data should be accessible by means of different indices. Some of the obvious indices or access keys are the component description or part number, components that match a set of characteristics, components in use and in spare, and components to be freed-up for future use.
 13. 1. 3 Network Topology Network management is based on knowledge of network topology. As a network grows, shrinks, or otherwise changes, network topology needs to be updated automatically. Such updating is done by the discovery application in the network management system. However, the scope of the discovery process needs to be constrained. For example, the arp command can discover any network component that responds with an IP address, which can then be mapped by the network management system. If the response includes workstations that are turned on only when they are in use, the network management system would indicate failure whenever they are off. Obviously, that is not desirable.
13. 1. 3 Network Topology Network management is based on knowledge of network topology. As a network grows, shrinks, or otherwise changes, network topology needs to be updated automatically. Such updating is done by the discovery application in the network management system. However, the scope of the discovery process needs to be constrained. For example, the arp command can discover any network component that responds with an IP address, which can then be mapped by the network management system. If the response includes workstations that are turned on only when they are in use, the network management system would indicate failure whenever they are off. Obviously, that is not desirable.
 Chapter 13 Network Management Applications Autodiscovery can be done by using the broadcast ping on each segment and following up with further SNMP queries to gather more details on the system. A more efficient method is to look at the ARP cache in the local router. The ARP cache table is large and contains the addresses of all the hosts and nodes used in recent communications. Use of this table also allows subsequent ARP queries to be sent to other routers. This process is continued until the desired information is obtained on all IP addresses defined by the scope of the autodiscovery procedure.
Chapter 13 Network Management Applications Autodiscovery can be done by using the broadcast ping on each segment and following up with further SNMP queries to gather more details on the system. A more efficient method is to look at the ARP cache in the local router. The ARP cache table is large and contains the addresses of all the hosts and nodes used in recent communications. Use of this table also allows subsequent ARP queries to be sent to other routers. This process is continued until the desired information is obtained on all IP addresses defined by the scope of the autodiscovery procedure.
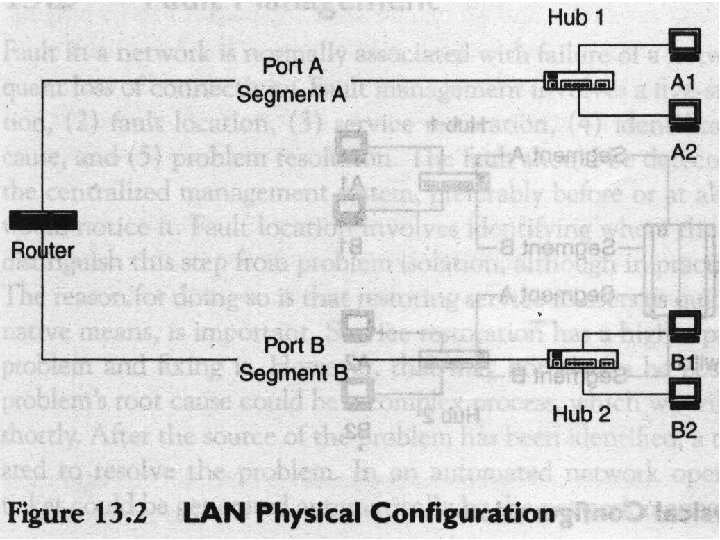

 13. 3 Performance Management Network performance is a nebulous term, which is hard to define or quantify in terms of global metrics. Performance management actually is (data) traffic management. It involves following data monitoring, problem isolation, performance tuning, analysis of statistical data for recognizing trends, and resource planning. 13. 3. 1 Performance Metrics The parameters that can be attributed to defining network performance on a global level are throughput, response time, network availability, and network reliability. The metrics of these parameters depend on what, when, and where the measurements are made.
13. 3 Performance Management Network performance is a nebulous term, which is hard to define or quantify in terms of global metrics. Performance management actually is (data) traffic management. It involves following data monitoring, problem isolation, performance tuning, analysis of statistical data for recognizing trends, and resource planning. 13. 3. 1 Performance Metrics The parameters that can be attributed to defining network performance on a global level are throughput, response time, network availability, and network reliability. The metrics of these parameters depend on what, when, and where the measurements are made.
 13. 3. 2 Data Monitoring Data monitoring in the network for abnormal performance behavior, such as a high collision rate in an Ethernet LAN and excessive packet drop because of overload, are detected by traps generated by agents and RMON. Performance-related issues are detected primarily with trap messages generated by RMON probes. Thresholds are set for important SNMP parameters in the RMON, which then generate alarms when the preset thresholds are crossed. For example, the parameters in the alarm group and the event group in the RMON MIB [RFC 1757] may be set for the object identifier to be monitored. The time interval over which the data are to be collected for calculation and the rising and falling thresholds are specified.
13. 3. 2 Data Monitoring Data monitoring in the network for abnormal performance behavior, such as a high collision rate in an Ethernet LAN and excessive packet drop because of overload, are detected by traps generated by agents and RMON. Performance-related issues are detected primarily with trap messages generated by RMON probes. Thresholds are set for important SNMP parameters in the RMON, which then generate alarms when the preset thresholds are crossed. For example, the parameters in the alarm group and the event group in the RMON MIB [RFC 1757] may be set for the object identifier to be monitored. The time interval over which the data are to be collected for calculation and the rising and falling thresholds are specified.
 13. 3. 4 Performance Statistics Performance statistics are used in tuning a network, validating a service level agreement(SLA), analyzing use trends, planning facilities, and functional accounting. Data are gathered by means of an RMON probe and an RMON MIB for statistics. To be accurate, statistics require large amounts of data sampling, which create overhead traffic on the network and thus have an impact on its performance. One of the enormous benefits of using an RMON probe for collecting statistical data is that it can be done locally without degrading overall network performance.
13. 3. 4 Performance Statistics Performance statistics are used in tuning a network, validating a service level agreement(SLA), analyzing use trends, planning facilities, and functional accounting. Data are gathered by means of an RMON probe and an RMON MIB for statistics. To be accurate, statistics require large amounts of data sampling, which create overhead traffic on the network and thus have an impact on its performance. One of the enormous benefits of using an RMON probe for collecting statistical data is that it can be done locally without degrading overall network performance.
 13. 5 Security Management Security management is both a technical and an administrative consideration in information management. It involves securing access to the network and information flowing in the network, access to data stored in the network, and manipulating the data stored and flowing through the network. The scope of the network and access to it not only covers an enterprise intranet network, but also the Internet. Another area of concern in secure communication is the use of mobile stations. You may be familiar with the embarrassing case of a politician's conversation from a car phone being intercepted by a third party traveling in an automobile. Although that was an analog signal, the same thing could happen in the case of a mobile digital station such as a hand-held stock trading device. An intruder could intercept messages and alter trade transactions either to benefit by them or to hurt the person sending or receiving them.
13. 5 Security Management Security management is both a technical and an administrative consideration in information management. It involves securing access to the network and information flowing in the network, access to data stored in the network, and manipulating the data stored and flowing through the network. The scope of the network and access to it not only covers an enterprise intranet network, but also the Internet. Another area of concern in secure communication is the use of mobile stations. You may be familiar with the embarrassing case of a politician's conversation from a car phone being intercepted by a third party traveling in an automobile. Although that was an analog signal, the same thing could happen in the case of a mobile digital station such as a hand-held stock trading device. An intruder could intercept messages and alter trade transactions either to benefit by them or to hurt the person sending or receiving them.
 13. 5. 1 Policies and Procedures The IETF workgroup that generated RFC 2196 defines a security policy as "a formal statement of the rules by which people who are given access to an organization's technology and information assets must abide. " An enterprise's policy should address both access and security breaches. Access concerns who is allowed to obtain information and from what source. SNMP management addresses this concern in terms of a community access policy for network management information. An enterprise's network access policy could allow all employees full access to the network. However, in most cases not everyone should have access to all network information, and thus accounts are established for employees to have access only to appropriate hosts and applications in those hosts. The access policy governing these accounts should be written so that all employees are fully aware of it.
13. 5. 1 Policies and Procedures The IETF workgroup that generated RFC 2196 defines a security policy as "a formal statement of the rules by which people who are given access to an organization's technology and information assets must abide. " An enterprise's policy should address both access and security breaches. Access concerns who is allowed to obtain information and from what source. SNMP management addresses this concern in terms of a community access policy for network management information. An enterprise's network access policy could allow all employees full access to the network. However, in most cases not everyone should have access to all network information, and thus accounts are established for employees to have access only to appropriate hosts and applications in those hosts. The access policy governing these accounts should be written so that all employees are fully aware of it.
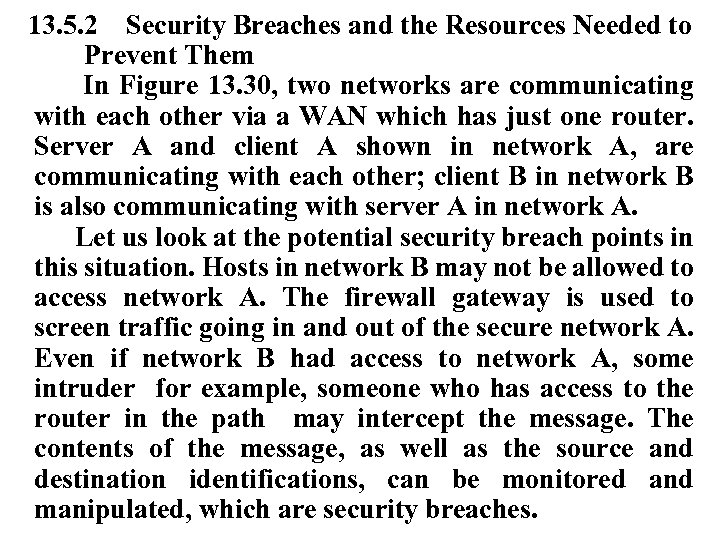 13. 5. 2 Security Breaches and the Resources Needed to Prevent Them In Figure 13. 30, two networks are communicating with each other via a WAN which has just one router. Server A and client A shown in network A, are communicating with each other; client B in network B is also communicating with server A in network A. Let us look at the potential security breach points in this situation. Hosts in network B may not be allowed to access network A. The firewall gateway is used to screen traffic going in and out of the secure network A. Even if network B had access to network A, some intruder for example, someone who has access to the router in the path may intercept the message. The contents of the message, as well as the source and destination identifications, can be monitored and manipulated, which are security breaches.
13. 5. 2 Security Breaches and the Resources Needed to Prevent Them In Figure 13. 30, two networks are communicating with each other via a WAN which has just one router. Server A and client A shown in network A, are communicating with each other; client B in network B is also communicating with server A in network A. Let us look at the potential security breach points in this situation. Hosts in network B may not be allowed to access network A. The firewall gateway is used to screen traffic going in and out of the secure network A. Even if network B had access to network A, some intruder for example, someone who has access to the router in the path may intercept the message. The contents of the message, as well as the source and destination identifications, can be monitored and manipulated, which are security breaches.
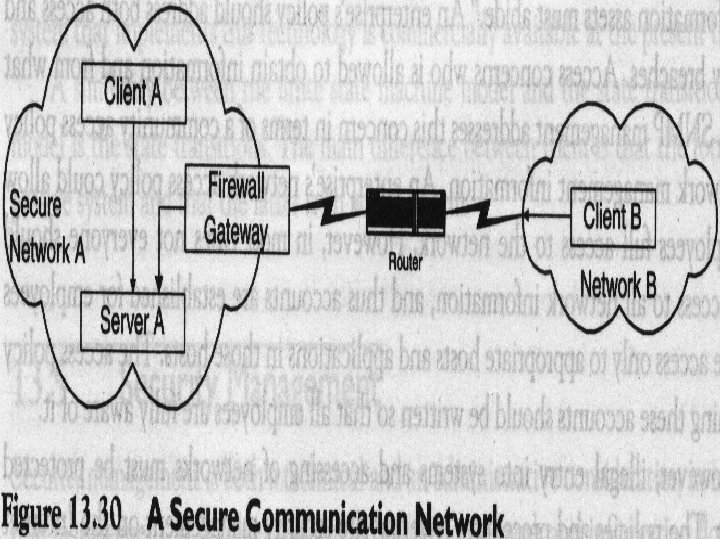
 Security breaches can occur in Internet and intranet environments in numerous ways. In most enterprises, authentication is limited to user identification and password. Authorization is limited to establishment of accounts (i. e. , who can log onto an application on a host). Besides normal breaches, special situations, as when a disgruntled employee embeds virus programs in an enterprise's programs and products, must be protected against. 13. 5. 3 Firewalls Firewall can protect a network from external attacks. It monitors and controls traffic into and out of a secure network. It can be implemented in a router, gateway, or special host: A firewall is normally located at the gateway to a network, but it may also be located at host access points.
Security breaches can occur in Internet and intranet environments in numerous ways. In most enterprises, authentication is limited to user identification and password. Authorization is limited to establishment of accounts (i. e. , who can log onto an application on a host). Besides normal breaches, special situations, as when a disgruntled employee embeds virus programs in an enterprise's programs and products, must be protected against. 13. 5. 3 Firewalls Firewall can protect a network from external attacks. It monitors and controls traffic into and out of a secure network. It can be implemented in a router, gateway, or special host: A firewall is normally located at the gateway to a network, but it may also be located at host access points.
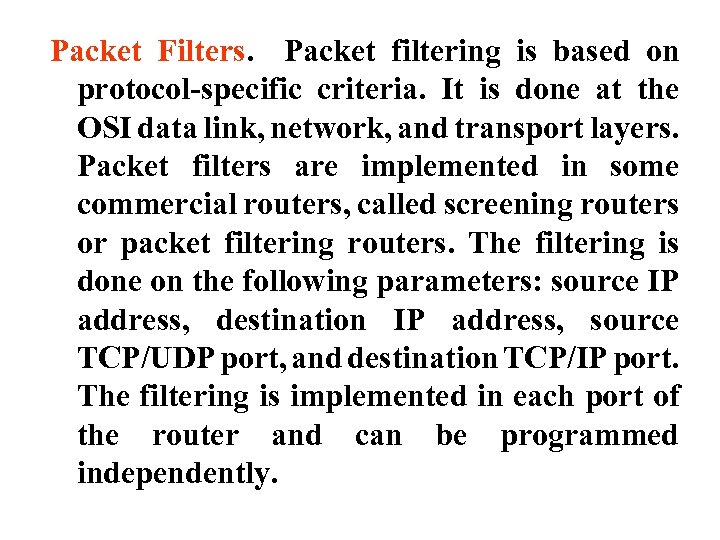 Packet Filters. Packet filtering is based on protocol-specific criteria. It is done at the OSI data link, network, and transport layers. Packet filters are implemented in some commercial routers, called screening routers or packet filtering routers. The filtering is done on the following parameters: source IP address, destination IP address, source TCP/UDP port, and destination TCP/IP port. The filtering is implemented in each port of the router and can be programmed independently.
Packet Filters. Packet filtering is based on protocol-specific criteria. It is done at the OSI data link, network, and transport layers. Packet filters are implemented in some commercial routers, called screening routers or packet filtering routers. The filtering is done on the following parameters: source IP address, destination IP address, source TCP/UDP port, and destination TCP/IP port. The filtering is implemented in each port of the router and can be programmed independently.
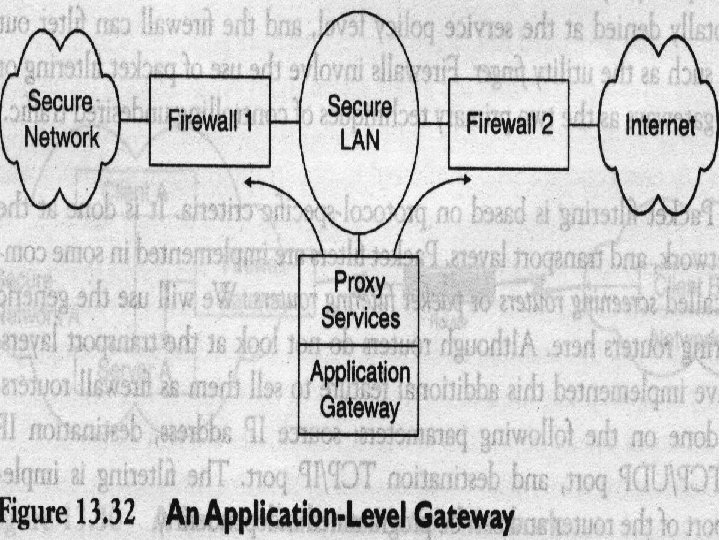
 Chapter 13 Network Management Applications Application-Level Gateway. An application-level gateway is used to overcome some of he problems identified for packet filtering. Figure 13. 32 shows the application gateway architecture. Firewalls 1 and 2 will forward data only if it is going to or coming from the application gateway. Thus a secured LAN is a gateway LAN. An application gateway behaves differently for each application, and filtering is handled by the proxy services in the gateway. For example, for FTP service
Chapter 13 Network Management Applications Application-Level Gateway. An application-level gateway is used to overcome some of he problems identified for packet filtering. Figure 13. 32 shows the application gateway architecture. Firewalls 1 and 2 will forward data only if it is going to or coming from the application gateway. Thus a secured LAN is a gateway LAN. An application gateway behaves differently for each application, and filtering is handled by the proxy services in the gateway. For example, for FTP service
 13. 5. 4 Cryptography For secure communication we need to ensure integrity protection and authentication validation, integrity protection makes sure that information has not been tampered with as it moves between source and destination. Authentication validation verifies originator identification. Cryptographic Communication. Cryptography deals with techniques of transmitting information from a sender to a receiver without any intermediary being able to decipher it. It is able to detect if somebody intercepted the information. If a letter written in a secret language were to be mailed in a sealed envelope--and if somebody tampered with it the receiver would detect the tampering.
13. 5. 4 Cryptography For secure communication we need to ensure integrity protection and authentication validation, integrity protection makes sure that information has not been tampered with as it moves between source and destination. Authentication validation verifies originator identification. Cryptographic Communication. Cryptography deals with techniques of transmitting information from a sender to a receiver without any intermediary being able to decipher it. It is able to detect if somebody intercepted the information. If a letter written in a secret language were to be mailed in a sealed envelope--and if somebody tampered with it the receiver would detect the tampering.
 Chapter 13 Network Management Applications Secret Key Cryptography. Two standard algorithms implement secret key cryptography. They are the Data Encryption Standard (DES) and the International Data Encryption Algorithm (IDEA). Both deal with 64 -bit message blocks and create the same size ciphertext. DES uses 56 -bit key and IDEA uses a 128 -bit key. DES is designed for efficient hardware implementation and consequently performs poorly if implemented in software. In contrast, IDEA functions efficiently in software implementations. Both DES and IDEA are based on the same principle of encryption. The bits in the plaintext block are rearranged several times, using a predetermined algorithm and the secret key. During decryption, the process is repeated in reverse for DES. Decryption is a bit more complicated for IDEA.
Chapter 13 Network Management Applications Secret Key Cryptography. Two standard algorithms implement secret key cryptography. They are the Data Encryption Standard (DES) and the International Data Encryption Algorithm (IDEA). Both deal with 64 -bit message blocks and create the same size ciphertext. DES uses 56 -bit key and IDEA uses a 128 -bit key. DES is designed for efficient hardware implementation and consequently performs poorly if implemented in software. In contrast, IDEA functions efficiently in software implementations. Both DES and IDEA are based on the same principle of encryption. The bits in the plaintext block are rearranged several times, using a predetermined algorithm and the secret key. During decryption, the process is repeated in reverse for DES. Decryption is a bit more complicated for IDEA.
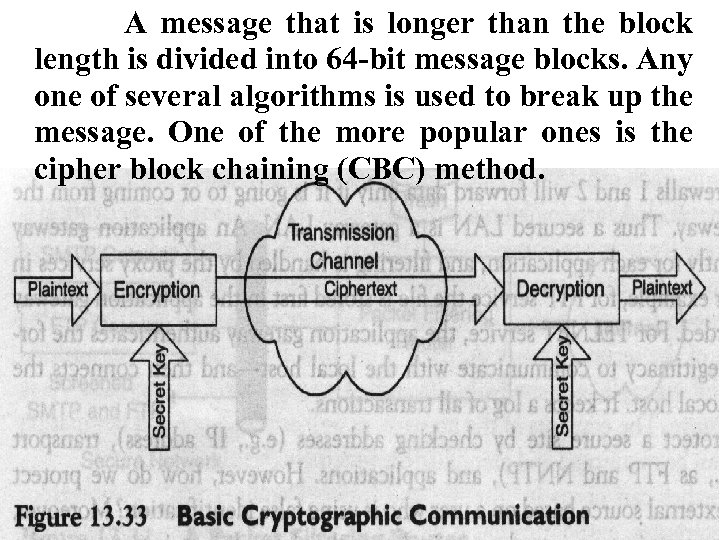 A message that is longer than the block length is divided into 64 -bit message blocks. Any one of several algorithms is used to break up the message. One of the more popular ones is the cipher block chaining (CBC) method.
A message that is longer than the block length is divided into 64 -bit message blocks. Any one of several algorithms is used to break up the message. One of the more popular ones is the cipher block chaining (CBC) method.
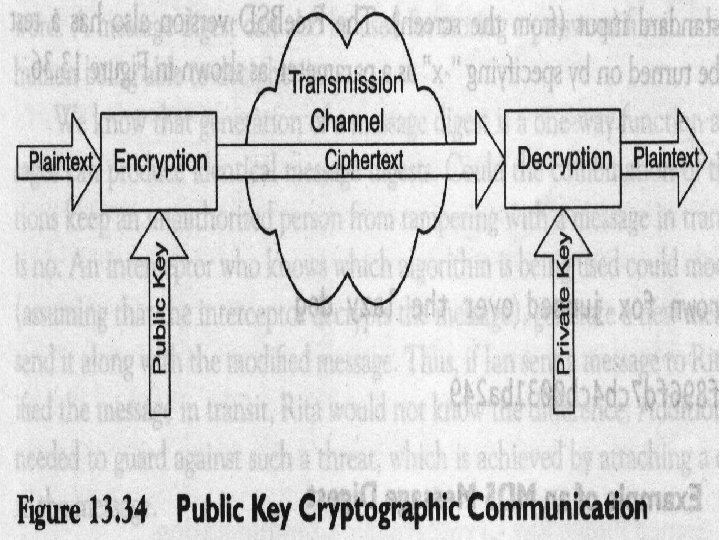
 Public Key Cryptography. In private key cryptography each pair of users must have a secret key. Public key cryptography overcomes the difficulty of having too many cryptography keys. The secret key cryptography is symmetric in that the same key is used for both encryption and decryption, but public key cryptography is asymmetric with a public key and a private key, which are different. Let us return to our lan, Rita, and Ted scenario to illustrate. In Figure 13. 34, the public key is lan's; it is the key that Rita, Ted, and everybody else (with whom lan wants to communicate) knows and uses to encrypt messages that they send to lan. The private key, which only lan knows, is the key that he uses to decrypt the messages. This scheme ensures secure communication between lan and the other communicators on a one-to-one basis. Rita's message to lan can be read only by lan and not by anyone else who has his public key because the public key cannot be used to decrypt the message.
Public Key Cryptography. In private key cryptography each pair of users must have a secret key. Public key cryptography overcomes the difficulty of having too many cryptography keys. The secret key cryptography is symmetric in that the same key is used for both encryption and decryption, but public key cryptography is asymmetric with a public key and a private key, which are different. Let us return to our lan, Rita, and Ted scenario to illustrate. In Figure 13. 34, the public key is lan's; it is the key that Rita, Ted, and everybody else (with whom lan wants to communicate) knows and uses to encrypt messages that they send to lan. The private key, which only lan knows, is the key that he uses to decrypt the messages. This scheme ensures secure communication between lan and the other communicators on a one-to-one basis. Rita's message to lan can be read only by lan and not by anyone else who has his public key because the public key cannot be used to decrypt the message.
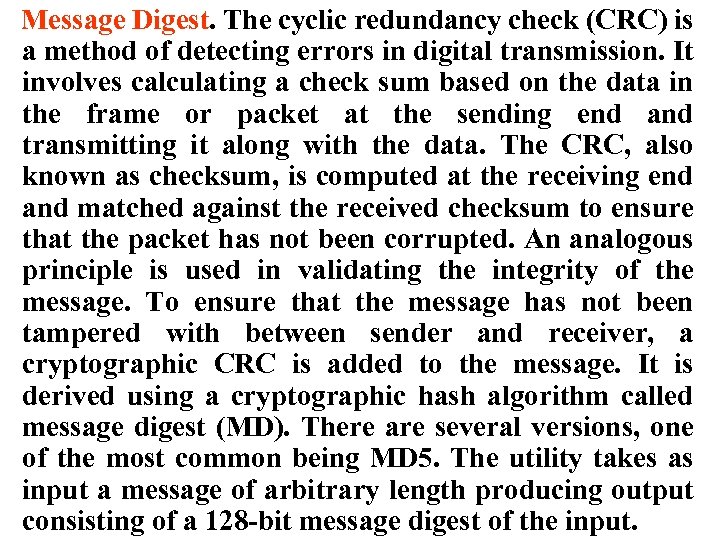 Message Digest. The cyclic redundancy check (CRC) is a method of detecting errors in digital transmission. It involves calculating a check sum based on the data in the frame or packet at the sending end and transmitting it along with the data. The CRC, also known as checksum, is computed at the receiving end and matched against the received checksum to ensure that the packet has not been corrupted. An analogous principle is used in validating the integrity of the message. To ensure that the message has not been tampered with between sender and receiver, a cryptographic CRC is added to the message. It is derived using a cryptographic hash algorithm called message digest (MD). There are several versions, one of the most common being MD 5. The utility takes as input a message of arbitrary length producing output consisting of a 128 -bit message digest of the input.
Message Digest. The cyclic redundancy check (CRC) is a method of detecting errors in digital transmission. It involves calculating a check sum based on the data in the frame or packet at the sending end and transmitting it along with the data. The CRC, also known as checksum, is computed at the receiving end and matched against the received checksum to ensure that the packet has not been corrupted. An analogous principle is used in validating the integrity of the message. To ensure that the message has not been tampered with between sender and receiver, a cryptographic CRC is added to the message. It is derived using a cryptographic hash algorithm called message digest (MD). There are several versions, one of the most common being MD 5. The utility takes as input a message of arbitrary length producing output consisting of a 128 -bit message digest of the input.
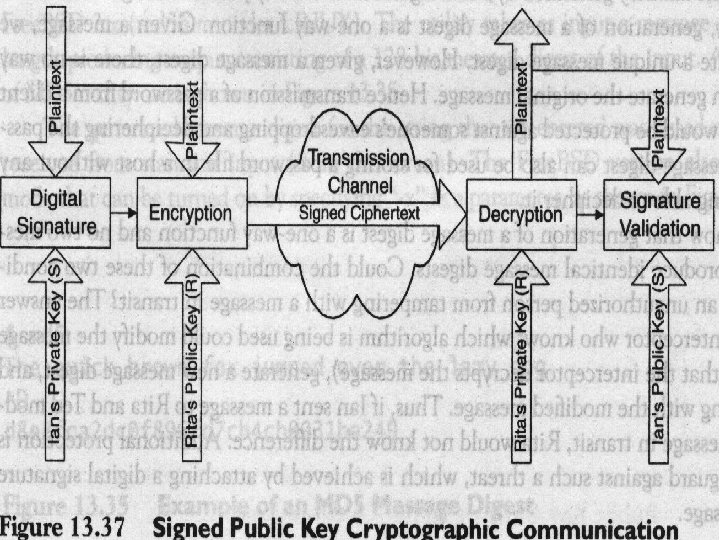
 Digital Signature. Digital signature can guarantee who sent the message. The use of signed public key cryptographic communication is illustrated in Fig. 13. 37. The digital signature is the reverse of public key cryptography. Ian create a digital signature using his private key (marked S for sender in parentheses in Figure 13. 37) and Rita could validate it by using Ian's public key. The digital signature depends on the message and the key. Let us suppose that lan is sending an e-mail message to Rita. A digital signature, which is a message digest, is generated by using any hash algorithm with the combined inputs of the plaintext message and Ian's private key. The digital signature is concatenated with the plaintext message and is encrypted by using Rita's public key (marked R for receiver in parentheses).
Digital Signature. Digital signature can guarantee who sent the message. The use of signed public key cryptographic communication is illustrated in Fig. 13. 37. The digital signature is the reverse of public key cryptography. Ian create a digital signature using his private key (marked S for sender in parentheses in Figure 13. 37) and Rita could validate it by using Ian's public key. The digital signature depends on the message and the key. Let us suppose that lan is sending an e-mail message to Rita. A digital signature, which is a message digest, is generated by using any hash algorithm with the combined inputs of the plaintext message and Ian's private key. The digital signature is concatenated with the plaintext message and is encrypted by using Rita's public key (marked R for receiver in parentheses).
 Chapter 13 Network Management Applications 13. 5. 5 Authentication and Authorization Authentication is verification of the user's identification, and authorization is the granting of access to the information. On the Internet, without security, a user's identification and password, which are used for authentication, can easily be captured by an intruder snooping on the LAN or WAN, Several secure mechanisms of varying complexity and sensitivity may be used for authentication purposes. Authorization for a particular service could be a simple read, write, read-write, or no-access. The privilege of using the service could be for an indefinite period, a finite period, or just for one-time use.
Chapter 13 Network Management Applications 13. 5. 5 Authentication and Authorization Authentication is verification of the user's identification, and authorization is the granting of access to the information. On the Internet, without security, a user's identification and password, which are used for authentication, can easily be captured by an intruder snooping on the LAN or WAN, Several secure mechanisms of varying complexity and sensitivity may be used for authentication purposes. Authorization for a particular service could be a simple read, write, read-write, or no-access. The privilege of using the service could be for an indefinite period, a finite period, or just for one-time use.
 13. 5. 6 Client/Server Authentication Systems We will consider four types of client/server environments and the implementation of authentication in each: a host/user environment, a ticket-granting system, an authentication server system, and authentication using a cryptographic function. Host/User Authentication. Both the traditional host and user validations for authentication are not very secure. They are also not convenient to use. Host authentication requires that certain hosts be validated by the server providing the service. The host names are administered by the server administrator. The server recognizes the host by the host address. If server S is authorized to serve a client host C, anyone who has an account in C could access the S. The server maintains the list of users associated with host C and allows access to the user.
13. 5. 6 Client/Server Authentication Systems We will consider four types of client/server environments and the implementation of authentication in each: a host/user environment, a ticket-granting system, an authentication server system, and authentication using a cryptographic function. Host/User Authentication. Both the traditional host and user validations for authentication are not very secure. They are also not convenient to use. Host authentication requires that certain hosts be validated by the server providing the service. The host names are administered by the server administrator. The server recognizes the host by the host address. If server S is authorized to serve a client host C, anyone who has an account in C could access the S. The server maintains the list of users associated with host C and allows access to the user.
 13. 5. 8 Protection of Networks from Virus Attacks In the current Internet environment, we cannot leave the subject of security without mentioning undesired and unexpected virus attacks on networks and hosts. These viruses are usually programs that, when executed, cause harm by making copies and inserting them into other programs. They contaminate networks by importing infected programs from outside sources, either on-line or via disks. The impact of virus infection manifests itself in many ways. The serious viruses prevent access to your hard disk by infecting the boot track, compromising your processor(an outside source controlling your computer), flooding your network with extraneous traffic that prevents your hosts from using it, and the like.
13. 5. 8 Protection of Networks from Virus Attacks In the current Internet environment, we cannot leave the subject of security without mentioning undesired and unexpected virus attacks on networks and hosts. These viruses are usually programs that, when executed, cause harm by making copies and inserting them into other programs. They contaminate networks by importing infected programs from outside sources, either on-line or via disks. The impact of virus infection manifests itself in many ways. The serious viruses prevent access to your hard disk by infecting the boot track, compromising your processor(an outside source controlling your computer), flooding your network with extraneous traffic that prevents your hosts from using it, and the like.
 13. 7 Report Management We have elected to treat report management as a special category, although it is not assigned a special functionality in the OSI classification. Reports for the various application functions--configuration, fault, performance, security, and accounting--could normally be addressed in sections dealing with those topics. We treat reports as a special category because a well-run network operations center often goes unnoticed. Attention usually is paid to it only when there is a crisis or the quality of service suffers for some reason. Thus generating, analyzing, and distributing various reports to appropriate groups when the network is running smoothly, is important to maintaining a well-funded, well-managed operations center. We can classify such reports as (1) planning and management reports, (2) system reports, and (3) user reports.
13. 7 Report Management We have elected to treat report management as a special category, although it is not assigned a special functionality in the OSI classification. Reports for the various application functions--configuration, fault, performance, security, and accounting--could normally be addressed in sections dealing with those topics. We treat reports as a special category because a well-run network operations center often goes unnoticed. Attention usually is paid to it only when there is a crisis or the quality of service suffers for some reason. Thus generating, analyzing, and distributing various reports to appropriate groups when the network is running smoothly, is important to maintaining a well-funded, well-managed operations center. We can classify such reports as (1) planning and management reports, (2) system reports, and (3) user reports.
 Chapter 13 Network Management Applications 13. 8 Policy-Based Management Policy plays an equally important, if not greater, role as the technical area. Without established policies and their implementation, the technical aspects of security management are not of much use. However, our focus here is not on administration, although that is important. Rather, it is with the technical aspects of policy implementation in network management. Figure 13. 43 is a policy management architecture proposed by [Lewis L 5] for network management. It consists of a domain space of objects, a rule space consisting of rules, a policy driver that controls actions to be taken, and action space that implements the actions and attributes of the network being controlled.
Chapter 13 Network Management Applications 13. 8 Policy-Based Management Policy plays an equally important, if not greater, role as the technical area. Without established policies and their implementation, the technical aspects of security management are not of much use. However, our focus here is not on administration, although that is important. Rather, it is with the technical aspects of policy implementation in network management. Figure 13. 43 is a policy management architecture proposed by [Lewis L 5] for network management. It consists of a domain space of objects, a rule space consisting of rules, a policy driver that controls actions to be taken, and action space that implements the actions and attributes of the network being controlled.
 13. 9 Service Level Management The development, establishment, and implementation of enterprise policy does not stop with decisions about the best and consistent use of management tools. The network, systems, and applications that run on them are there to serve customers, and customer satisfaction is essential to the success of the enterprise. Service level management is defined as the process of (1) identifying services and characteristics associated with them; (2) negotiating a service level agreement (SLA); (3) deploying agents to monitor and control network, system, and application component performance; and (4) producing service level reports. The characteristics associated with services are service parameters, service levels, component parameters, and component-toservice mappings. A service parameter is an index for the performance of a service. There is a one-to-many mapping between the service parameter and the underlying component parameters.
13. 9 Service Level Management The development, establishment, and implementation of enterprise policy does not stop with decisions about the best and consistent use of management tools. The network, systems, and applications that run on them are there to serve customers, and customer satisfaction is essential to the success of the enterprise. Service level management is defined as the process of (1) identifying services and characteristics associated with them; (2) negotiating a service level agreement (SLA); (3) deploying agents to monitor and control network, system, and application component performance; and (4) producing service level reports. The characteristics associated with services are service parameters, service levels, component parameters, and component-toservice mappings. A service parameter is an index for the performance of a service. There is a one-to-many mapping between the service parameter and the underlying component parameters.


