da7bc60962131c9ded3004805d12832b.ppt
- Количество слайдов: 105
 Chapter 13 Network Management Applications
Chapter 13 Network Management Applications
 Network and Systems Management
Network and Systems Management
 Management Applications • OSI Model • Configuration • Fault • Performance • Security • Accounting • Reports • Service Level Management • Policy-based management
Management Applications • OSI Model • Configuration • Fault • Performance • Security • Accounting • Reports • Service Level Management • Policy-based management
 Configuration Management • Network Provisioning • Inventory Management • Equipment • Facilities • Network Topology • Database Considerations
Configuration Management • Network Provisioning • Inventory Management • Equipment • Facilities • Network Topology • Database Considerations
 Network Provisioning • Provisioning of network resources • Design • Installation and maintenance • Circuit-switched network • Packet-switched network, configuration for • Protocol • Performance • Qo. S • ATM networks
Network Provisioning • Provisioning of network resources • Design • Installation and maintenance • Circuit-switched network • Packet-switched network, configuration for • Protocol • Performance • Qo. S • ATM networks
 Network Topology • Manual • Auto-discovery by NMS using • Broadcast ping • ARP table in devices • Mapping of network • Layout • Layering • Views • Physical • Logical
Network Topology • Manual • Auto-discovery by NMS using • Broadcast ping • ARP table in devices • Mapping of network • Layout • Layering • Views • Physical • Logical
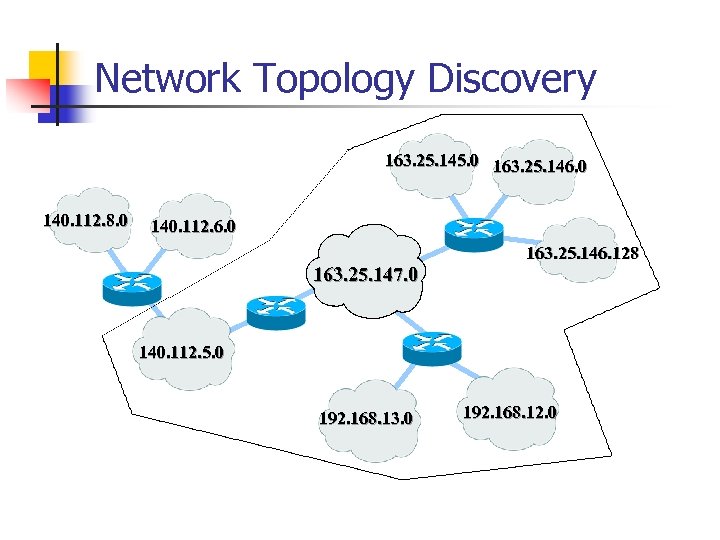 Network Topology Discovery 163. 25. 145. 0 163. 25. 146. 0 140. 112. 8. 0 140. 112. 6. 0 163. 25. 147. 0 163. 25. 146. 128 140. 112. 5. 0 192. 168. 13. 0 192. 168. 12. 0
Network Topology Discovery 163. 25. 145. 0 163. 25. 146. 0 140. 112. 8. 0 140. 112. 6. 0 163. 25. 147. 0 163. 25. 146. 128 140. 112. 5. 0 192. 168. 13. 0 192. 168. 12. 0
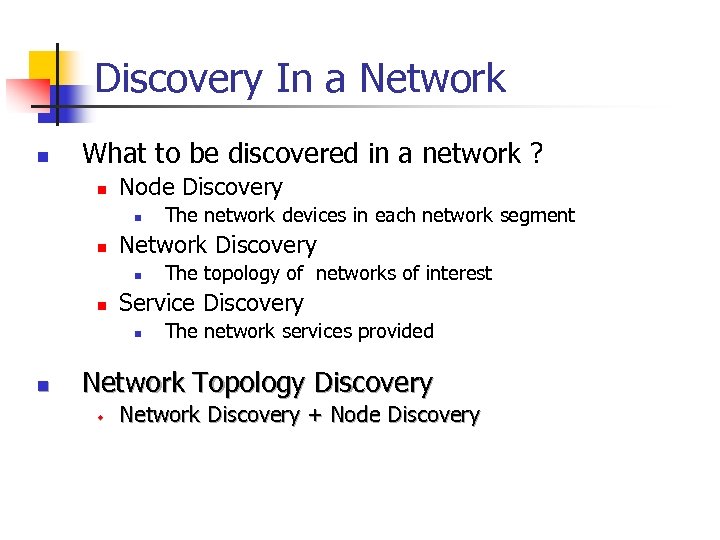 Discovery In a Network n What to be discovered in a network ? n Node Discovery n n Network Discovery n n The topology of networks of interest Service Discovery n n The network devices in each network segment The network services provided Network Topology Discovery w Network Discovery + Node Discovery
Discovery In a Network n What to be discovered in a network ? n Node Discovery n n Network Discovery n n The topology of networks of interest Service Discovery n n The network devices in each network segment The network services provided Network Topology Discovery w Network Discovery + Node Discovery
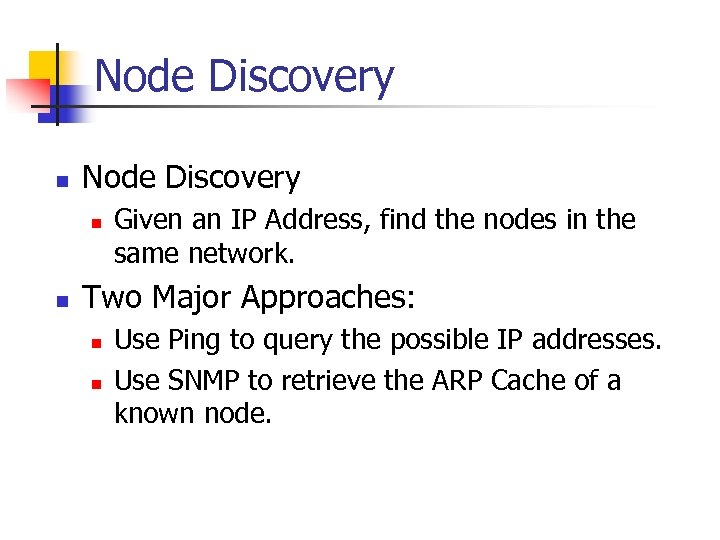 Node Discovery n n Given an IP Address, find the nodes in the same network. Two Major Approaches: n n Use Ping to query the possible IP addresses. Use SNMP to retrieve the ARP Cache of a known node.
Node Discovery n n Given an IP Address, find the nodes in the same network. Two Major Approaches: n n Use Ping to query the possible IP addresses. Use SNMP to retrieve the ARP Cache of a known node.
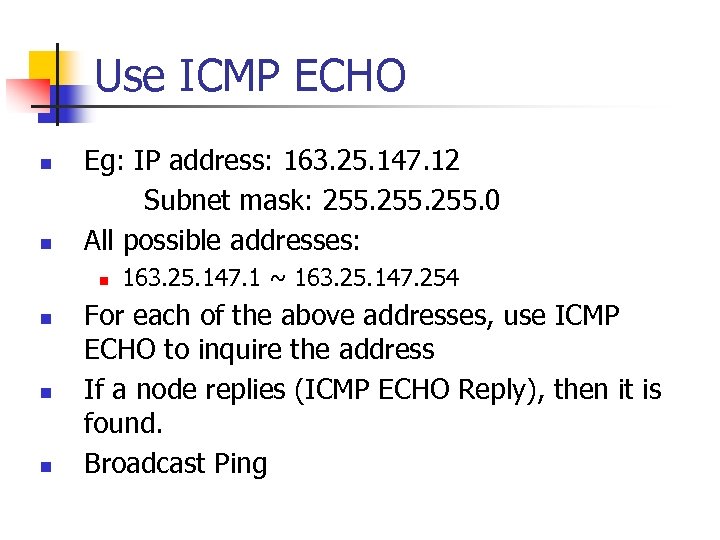 Use ICMP ECHO n n Eg: IP address: 163. 25. 147. 12 Subnet mask: 255. 0 All possible addresses: n n 163. 25. 147. 1 ~ 163. 25. 147. 254 For each of the above addresses, use ICMP ECHO to inquire the address If a node replies (ICMP ECHO Reply), then it is found. Broadcast Ping
Use ICMP ECHO n n Eg: IP address: 163. 25. 147. 12 Subnet mask: 255. 0 All possible addresses: n n 163. 25. 147. 1 ~ 163. 25. 147. 254 For each of the above addresses, use ICMP ECHO to inquire the address If a node replies (ICMP ECHO Reply), then it is found. Broadcast Ping
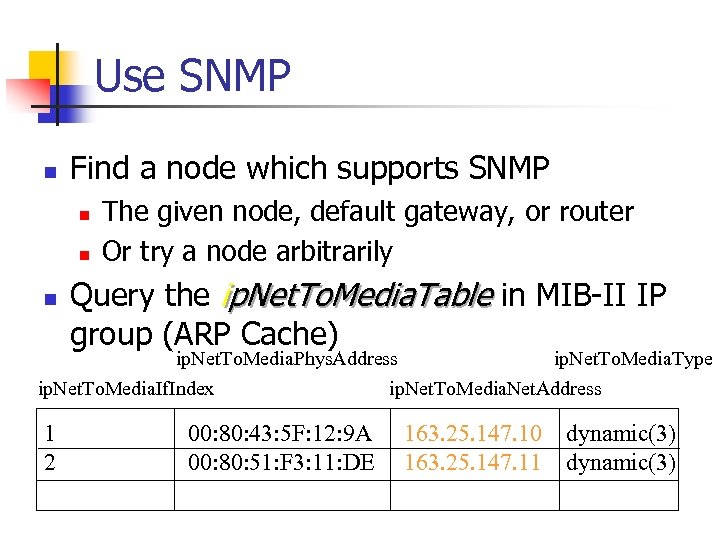 Use SNMP n Find a node which supports SNMP n n n The given node, default gateway, or router Or try a node arbitrarily Query the ip. Net. To. Media. Table in MIB-II IP group (ARP Cache) ip. Net. To. Media. Phys. Address ip. Net. To. Media. Type ip. Net. To. Media. If. Index ip. Net. To. Media. Net. Address 1 2 00: 80: 43: 5 F: 12: 9 A 00: 80: 51: F 3: 11: DE 163. 25. 147. 10 163. 25. 147. 11 dynamic(3)
Use SNMP n Find a node which supports SNMP n n n The given node, default gateway, or router Or try a node arbitrarily Query the ip. Net. To. Media. Table in MIB-II IP group (ARP Cache) ip. Net. To. Media. Phys. Address ip. Net. To. Media. Type ip. Net. To. Media. If. Index ip. Net. To. Media. Net. Address 1 2 00: 80: 43: 5 F: 12: 9 A 00: 80: 51: F 3: 11: DE 163. 25. 147. 10 163. 25. 147. 11 dynamic(3)
 Network Discovery n n Key Issue: n n Find the networks of interest with their interconnections Given a network, what are the networks directly connected with it ? Major Approach n Use SNMP to retrieve the routing table of a router.
Network Discovery n n Key Issue: n n Find the networks of interest with their interconnections Given a network, what are the networks directly connected with it ? Major Approach n Use SNMP to retrieve the routing table of a router.
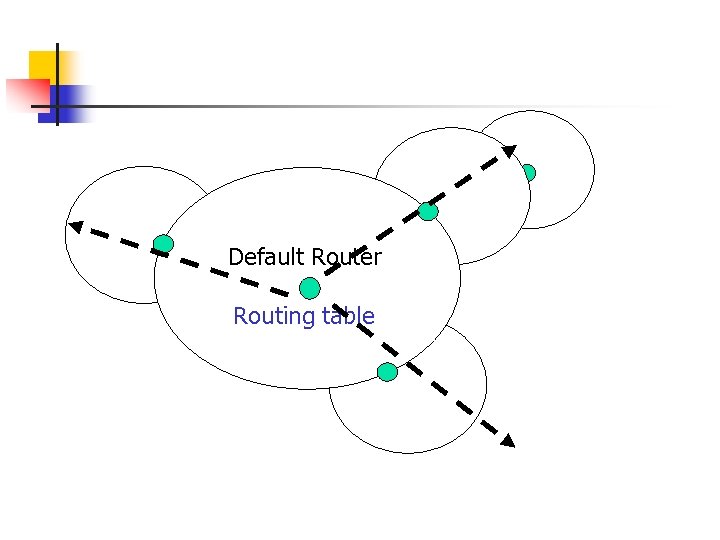 Default Router Routing table
Default Router Routing table

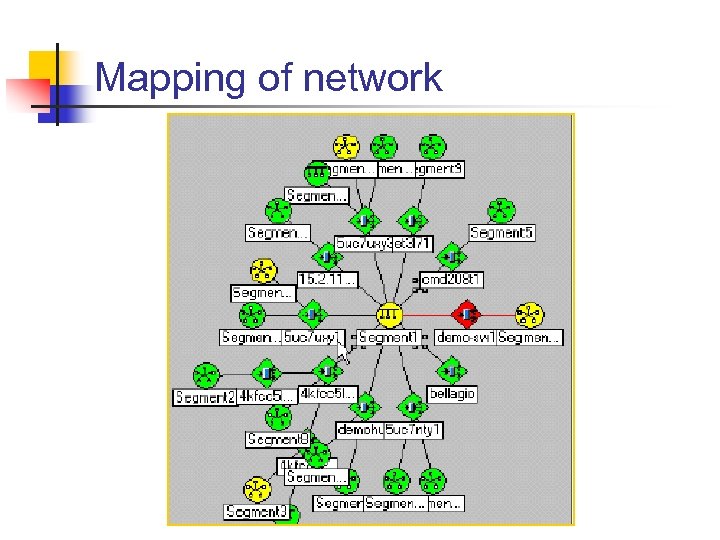 Mapping of network
Mapping of network
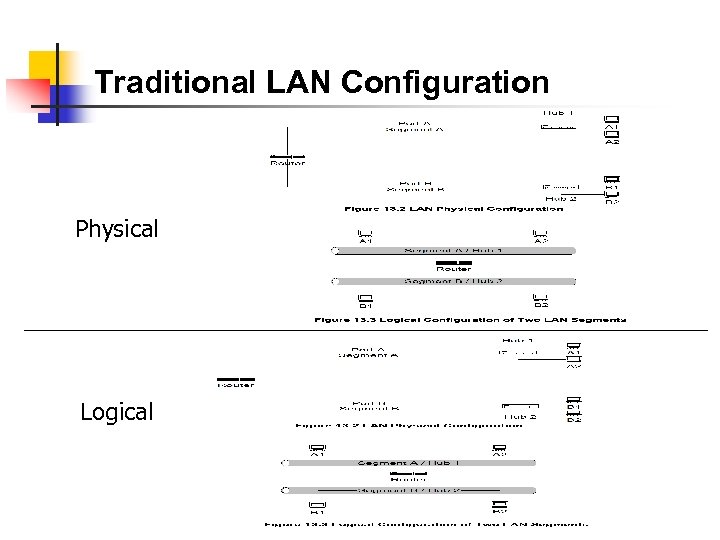 Traditional LAN Configuration Physical Logical
Traditional LAN Configuration Physical Logical
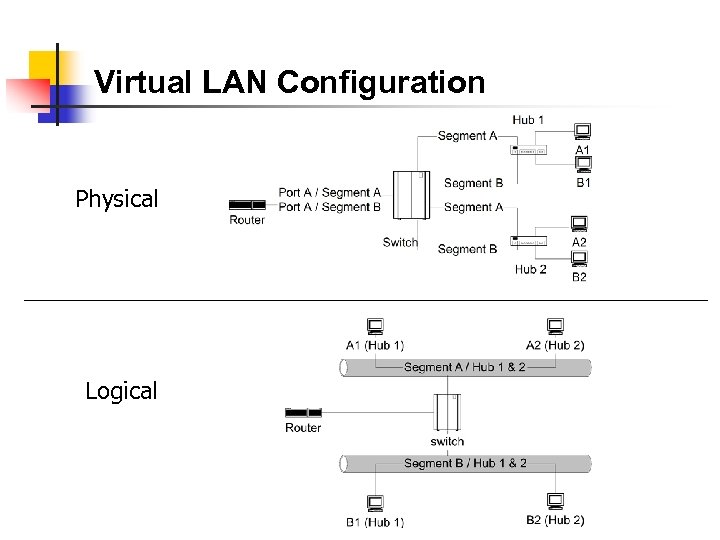 Virtual LAN Configuration Physical Logical
Virtual LAN Configuration Physical Logical
 Fault Management • • • Fault is a failure of a network component Results in loss of connectivity Fault management involves: • Fault detection • Polling • Traps: link. Down, egp. Neighbor. Loss • Fault location • Detect all components failed and trace down the tree topology to the source • Fault isolation by network and SNMP tools • Use artificial intelligence / correlation techniques • Restoration of service • Identification of root cause of the problem • Problem resolution
Fault Management • • • Fault is a failure of a network component Results in loss of connectivity Fault management involves: • Fault detection • Polling • Traps: link. Down, egp. Neighbor. Loss • Fault location • Detect all components failed and trace down the tree topology to the source • Fault isolation by network and SNMP tools • Use artificial intelligence / correlation techniques • Restoration of service • Identification of root cause of the problem • Problem resolution
 Performance Management • Tools • Protocol analyzers • RMON • MRTG • Performance Metrics • Data Monitoring • Problem Isolation • Performance Statistics
Performance Management • Tools • Protocol analyzers • RMON • MRTG • Performance Metrics • Data Monitoring • Problem Isolation • Performance Statistics
 Performance Metrics • Macro-level • Throughput • Response time • Availability • Reliability • Micro-level • Bandwidth • Utilization • Error rate • Peak load • Average load
Performance Metrics • Macro-level • Throughput • Response time • Availability • Reliability • Micro-level • Bandwidth • Utilization • Error rate • Peak load • Average load
 Traffic Flow Measurement Network Characterization Four levels defined by IETF (RFC 2063)
Traffic Flow Measurement Network Characterization Four levels defined by IETF (RFC 2063)
 Network Flow Measurements • Three measurement entities: • Meters gather data and build tables • Meter readers collect data from meters • Managers oversee the operation • Meter MIB (RFC 2064) • Netra. Met - an implementation(RFC 2123)
Network Flow Measurements • Three measurement entities: • Meters gather data and build tables • Meter readers collect data from meters • Managers oversee the operation • Meter MIB (RFC 2064) • Netra. Met - an implementation(RFC 2123)
 Data Monitoring and Problem Isolation • • Data monitoring • Normal behavior • Abnormal behavior (e. g. , excessive collisions, high packet loss, etc) • Set up traps (e. g. , parameters in alarm group in RMON on object identifier of interest) • Set up alarms for criticality • Manual and automatic clearing of alarms Problem isolation • Manual mode using network and SNMP tools • Problems in multiple components needs tracking down the topology • Automated mode using correlation technology
Data Monitoring and Problem Isolation • • Data monitoring • Normal behavior • Abnormal behavior (e. g. , excessive collisions, high packet loss, etc) • Set up traps (e. g. , parameters in alarm group in RMON on object identifier of interest) • Set up alarms for criticality • Manual and automatic clearing of alarms Problem isolation • Manual mode using network and SNMP tools • Problems in multiple components needs tracking down the topology • Automated mode using correlation technology
 Performance Statistics • Traffic statistics • Error statistics • Used in • Qo. S tracking • Performance tuning • Validation of SLA (Service Level Agreement) • Trend analysis • Facility planning • Functional accounting
Performance Statistics • Traffic statistics • Error statistics • Used in • Qo. S tracking • Performance tuning • Validation of SLA (Service Level Agreement) • Trend analysis • Facility planning • Functional accounting
 Event Correlation Techniques 1. Basic elements 1. Detection and filtering of events 2. Correlation of observed events using AI 3. Localize the source of the problem 4. Identify the cause of the problem 2. Techniques 1. Rule-based reasoning 2. Model-based reasoning 3. Case-based reasoning 4. Codebook correlation model 5. State transition graph model 6. Finite state machine model
Event Correlation Techniques 1. Basic elements 1. Detection and filtering of events 2. Correlation of observed events using AI 3. Localize the source of the problem 4. Identify the cause of the problem 2. Techniques 1. Rule-based reasoning 2. Model-based reasoning 3. Case-based reasoning 4. Codebook correlation model 5. State transition graph model 6. Finite state machine model
 Rule-Based Reasoning
Rule-Based Reasoning
 Rule-Based Reasoning • Knowledge base contains expert knowledge on problem symptoms and actions to be taken if then condition action • Working memory contains topological and state information of the network; recognizes system going into faulty state • Inference engine in cooperation with knowledge base decides on the action to be taken • Knowledge executes the action
Rule-Based Reasoning • Knowledge base contains expert knowledge on problem symptoms and actions to be taken if then condition action • Working memory contains topological and state information of the network; recognizes system going into faulty state • Inference engine in cooperation with knowledge base decides on the action to be taken • Knowledge executes the action
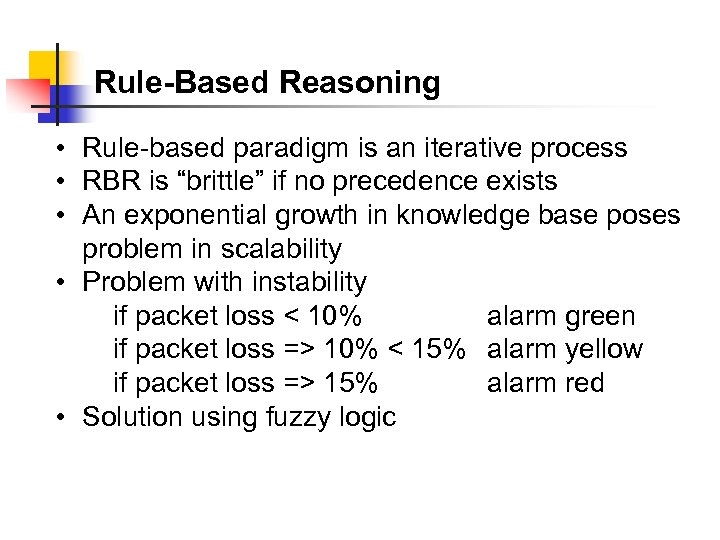 Rule-Based Reasoning • Rule-based paradigm is an iterative process • RBR is “brittle” if no precedence exists • An exponential growth in knowledge base poses problem in scalability • Problem with instability if packet loss < 10% alarm green if packet loss => 10% < 15% alarm yellow if packet loss => 15% alarm red • Solution using fuzzy logic
Rule-Based Reasoning • Rule-based paradigm is an iterative process • RBR is “brittle” if no precedence exists • An exponential growth in knowledge base poses problem in scalability • Problem with instability if packet loss < 10% alarm green if packet loss => 10% < 15% alarm yellow if packet loss => 15% alarm red • Solution using fuzzy logic
 Configuration for RBR Example
Configuration for RBR Example
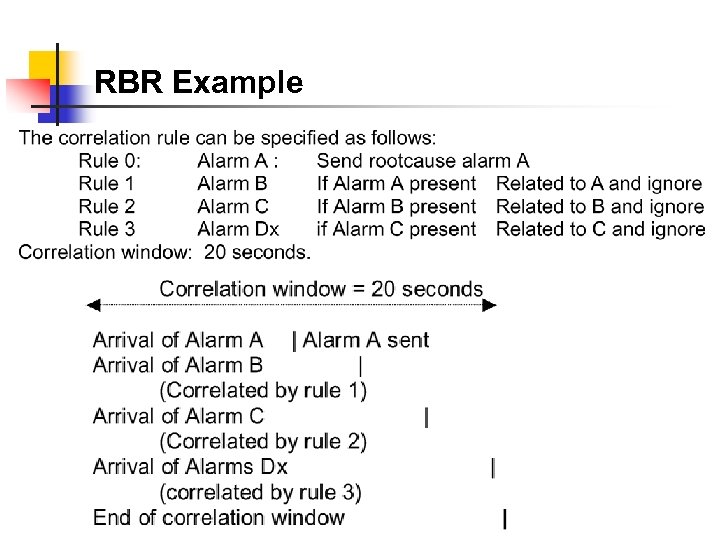 RBR Example
RBR Example
 Model-Based Reasoning
Model-Based Reasoning
 Model-Based Reasoning • Object-oriented model • Model is a representation of the component it models • Model has attributes and relations to other models • Relationship between objects reflected in a similar relationship between models
Model-Based Reasoning • Object-oriented model • Model is a representation of the component it models • Model has attributes and relations to other models • Relationship between objects reflected in a similar relationship between models
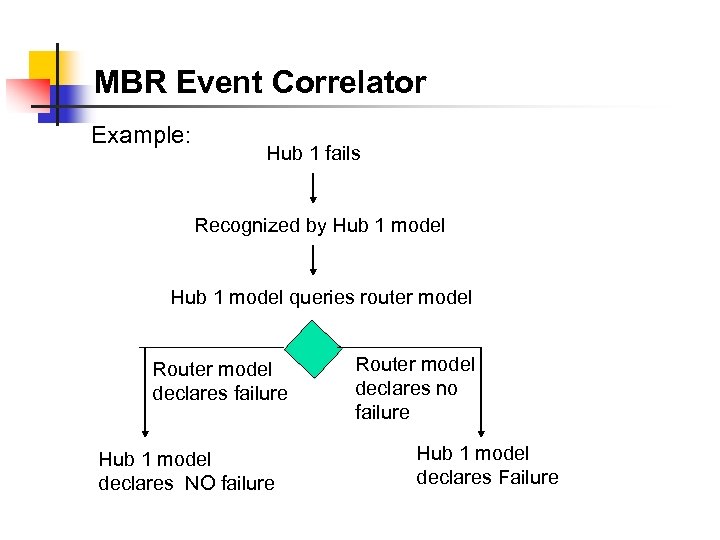 MBR Event Correlator Example: Hub 1 fails Recognized by Hub 1 model queries router model Router model declares failure Hub 1 model declares NO failure Router model declares no failure Hub 1 model declares Failure
MBR Event Correlator Example: Hub 1 fails Recognized by Hub 1 model queries router model Router model declares failure Hub 1 model declares NO failure Router model declares no failure Hub 1 model declares Failure
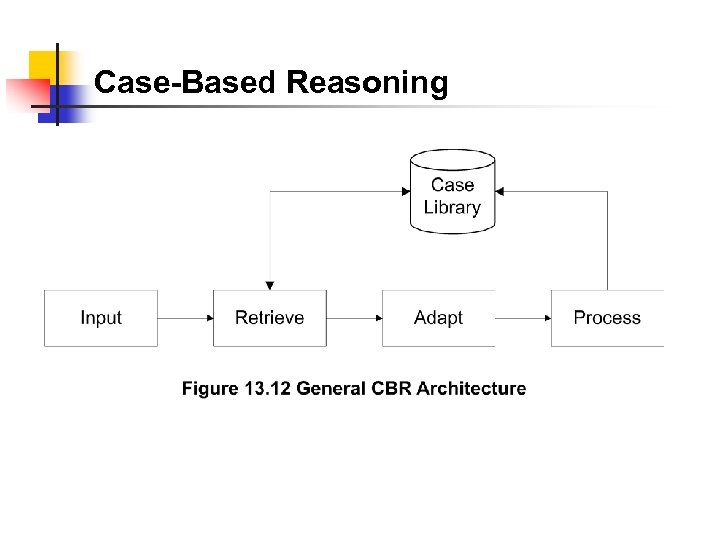 Case-Based Reasoning
Case-Based Reasoning
 Case-Based Reasoning • Unit of knowledge • RBR rule • CBR case • CBR based on the case experienced before; extend to the current situation by adaptation • Three adaptation schemes • Parameterized adaptation • Abstraction / re-specialization adaptation • Critic-based adaptation
Case-Based Reasoning • Unit of knowledge • RBR rule • CBR case • CBR based on the case experienced before; extend to the current situation by adaptation • Three adaptation schemes • Parameterized adaptation • Abstraction / re-specialization adaptation • Critic-based adaptation
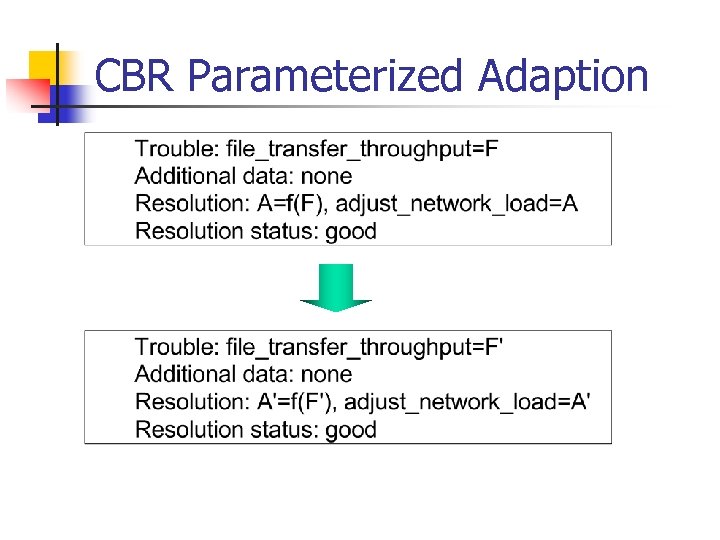 CBR Parameterized Adaption
CBR Parameterized Adaption
 CBR: Abstraction / Re-specialization
CBR: Abstraction / Re-specialization
 CBR: Critic-Based Adaptation • Human expertise introduces a new case
CBR: Critic-Based Adaptation • Human expertise introduces a new case
 CBR-Based CRITTER
CBR-Based CRITTER
 Codebook Correlation Model: Generic Architecture
Codebook Correlation Model: Generic Architecture
 Codebook Correlation Model • Yemini, et. al. proposed this model • Monitors capture alarm events • Configuration model contains the configuration of the network • Event model represents events and their causal relationships • Correlator correlates alarm events with event model and determines the problem that caused the events
Codebook Correlation Model • Yemini, et. al. proposed this model • Monitors capture alarm events • Configuration model contains the configuration of the network • Event model represents events and their causal relationships • Correlator correlates alarm events with event model and determines the problem that caused the events
 Codebook Approach • Correlation algorithms based upon coding approach to event correlation • Problem events viewed as messages generated by a system and encoded in sets of alarms • Correlator decodes the problem messages to identify the problems
Codebook Approach • Correlation algorithms based upon coding approach to event correlation • Problem events viewed as messages generated by a system and encoded in sets of alarms • Correlator decodes the problem messages to identify the problems
 Two phases of Codebook Approaches 1. Codebook selection phase: Problems to be monitored identified and the symptoms they generate are associated with the problem. This generates codebook (problem-symptom matrix) 2. Correlator compares alarm events with codebook and identifies the problem.
Two phases of Codebook Approaches 1. Codebook selection phase: Problems to be monitored identified and the symptoms they generate are associated with the problem. This generates codebook (problem-symptom matrix) 2. Correlator compares alarm events with codebook and identifies the problem.
 Causality Graph
Causality Graph
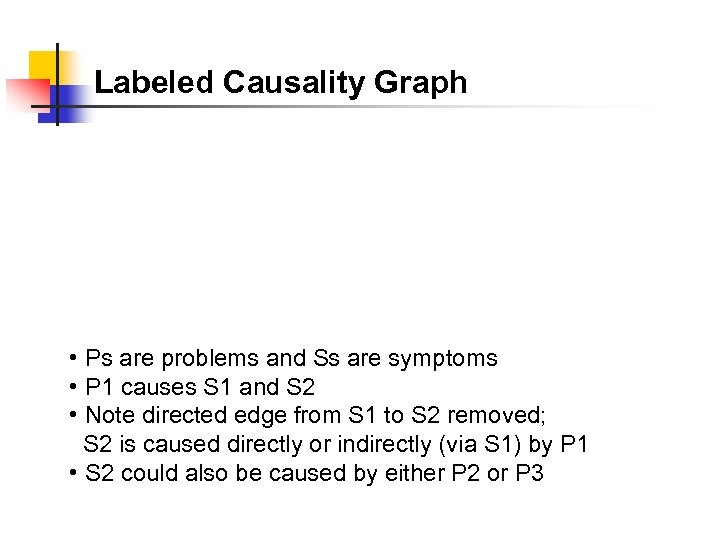 Labeled Causality Graph • Ps are problems and Ss are symptoms • P 1 causes S 1 and S 2 • Note directed edge from S 1 to S 2 removed; S 2 is caused directly or indirectly (via S 1) by P 1 • S 2 could also be caused by either P 2 or P 3
Labeled Causality Graph • Ps are problems and Ss are symptoms • P 1 causes S 1 and S 2 • Note directed edge from S 1 to S 2 removed; S 2 is caused directly or indirectly (via S 1) by P 1 • S 2 could also be caused by either P 2 or P 3
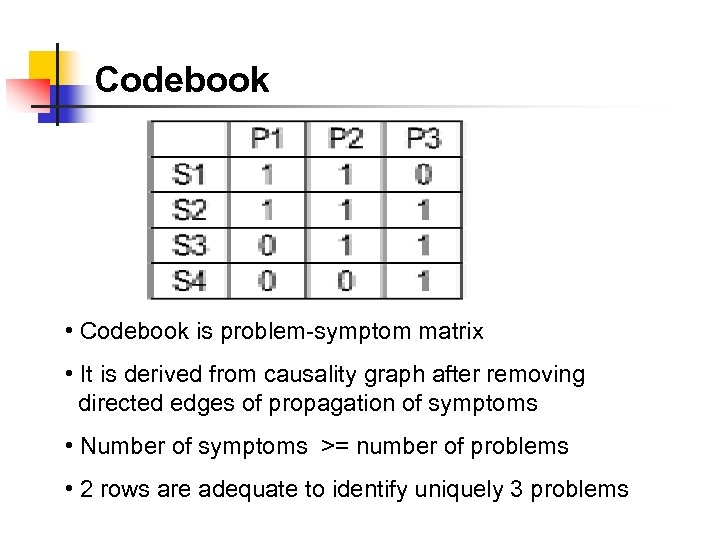 Codebook • Codebook is problem-symptom matrix • It is derived from causality graph after removing directed edges of propagation of symptoms • Number of symptoms >= number of problems • 2 rows are adequate to identify uniquely 3 problems
Codebook • Codebook is problem-symptom matrix • It is derived from causality graph after removing directed edges of propagation of symptoms • Number of symptoms >= number of problems • 2 rows are adequate to identify uniquely 3 problems
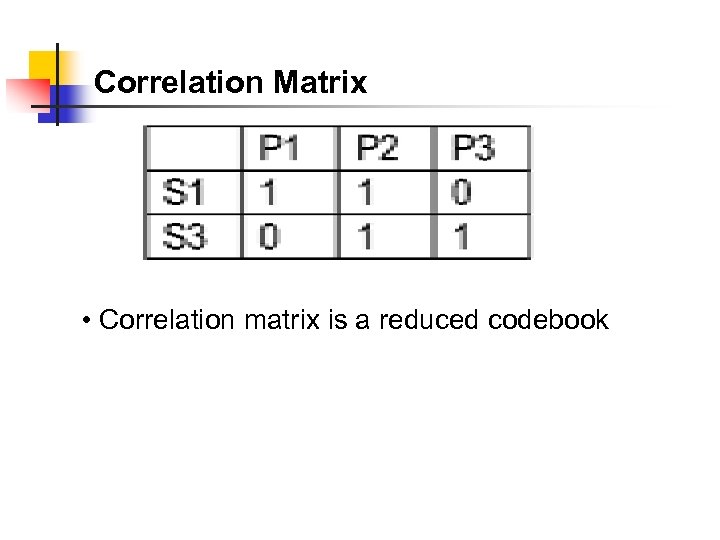 Correlation Matrix • Correlation matrix is a reduced codebook
Correlation Matrix • Correlation matrix is a reduced codebook
 Correlation Graph
Correlation Graph
 State Transition Model
State Transition Model
 State Transition Model Example
State Transition Model Example
 State Transition Graph
State Transition Graph
 Finite State Machine Model
Finite State Machine Model
 Finite State Machine Model • Finite state machine model is a passive system; state transition graph model is an active system • An observer agent is present in each node and reports abnormalities, such as a Web agent • A central system correlates events reported by the agents • Failure is detected by a node entering an illegal state
Finite State Machine Model • Finite state machine model is a passive system; state transition graph model is an active system • An observer agent is present in each node and reports abnormalities, such as a Web agent • A central system correlates events reported by the agents • Failure is detected by a node entering an illegal state
 Security Management • • • Security threats Policies and Procedures Resources to prevent security breaches Firewalls Cryptography Authentication and Authorization Client/Server authentication system Message transfer security Network protection security
Security Management • • • Security threats Policies and Procedures Resources to prevent security breaches Firewalls Cryptography Authentication and Authorization Client/Server authentication system Message transfer security Network protection security
 Security Threats • Modification of information: Contents modified by information unauthorized user, does not include address change • Masquerade: change of originating address by Masquerade unauthorized user • Message Stream Modification: Fragments of message Modification altered by an unauthorized user to modify the meaning of the message • Disclosure • Eavesdropping • Disclosure does not require interception of message • Denial of service and traffic analysis are not considered as threats.
Security Threats • Modification of information: Contents modified by information unauthorized user, does not include address change • Masquerade: change of originating address by Masquerade unauthorized user • Message Stream Modification: Fragments of message Modification altered by an unauthorized user to modify the meaning of the message • Disclosure • Eavesdropping • Disclosure does not require interception of message • Denial of service and traffic analysis are not considered as threats.
 Security Threats
Security Threats
 Polices and Procedures
Polices and Procedures
 Secured Communication Network No Security Breaches ? • Firewall secures traffic in and out of Network A • Security breach could occur by intercepting the message going from B to A, even if B has permission to access Network A • Most systems implement authentication with user id and password • Authorization is by establishment of accounts
Secured Communication Network No Security Breaches ? • Firewall secures traffic in and out of Network A • Security breach could occur by intercepting the message going from B to A, even if B has permission to access Network A • Most systems implement authentication with user id and password • Authorization is by establishment of accounts
 Firewalls • • Protects a network from external attacks Controls traffic in and out of a secure network Could be implemented in a router, gateway, or a special host Benefits • Reduces risks of access to hosts • Controlled access • Eliminates annoyance to the users • Protects privacy • Hierarchical implementation of policy and technology
Firewalls • • Protects a network from external attacks Controls traffic in and out of a secure network Could be implemented in a router, gateway, or a special host Benefits • Reduces risks of access to hosts • Controlled access • Eliminates annoyance to the users • Protects privacy • Hierarchical implementation of policy and technology
 Packet Filtering Firewall
Packet Filtering Firewall
 Packet Filtering • Uses protocol specific criteria at DLC, network, and transport layers • Implemented in routers - called screening router or packet filtering routers • Filtering parameters: • Source and/or destination IP address • Source and/or destination TCP/UDP port address, such as ftp port 21 • Multistage screening - address and protocol • Works best when rules are simple
Packet Filtering • Uses protocol specific criteria at DLC, network, and transport layers • Implemented in routers - called screening router or packet filtering routers • Filtering parameters: • Source and/or destination IP address • Source and/or destination TCP/UDP port address, such as ftp port 21 • Multistage screening - address and protocol • Works best when rules are simple
 Application Level Gateway DMZ (De-Militarized Zone)
Application Level Gateway DMZ (De-Militarized Zone)
 Cryptography • • Secure communication requires • Integrity protection: ensuring that the message is not tampered with • Authentication validation: ensures the originator identification Security threats • Modification of information • Masquerade • Message stream modification • Disclosure Hardware and software solutions Most secure communication is software based
Cryptography • • Secure communication requires • Integrity protection: ensuring that the message is not tampered with • Authentication validation: ensures the originator identification Security threats • Modification of information • Masquerade • Message stream modification • Disclosure Hardware and software solutions Most secure communication is software based
 資訊 安全之重點 n n n 機密性 (Confidentiality) 真實性 (Authentication) 完整性 (Integrity) 不可否認性 (Non-repudiation) 存取控制 (Access control) 可用性 (Availability)
資訊 安全之重點 n n n 機密性 (Confidentiality) 真實性 (Authentication) 完整性 (Integrity) 不可否認性 (Non-repudiation) 存取控制 (Access control) 可用性 (Availability)
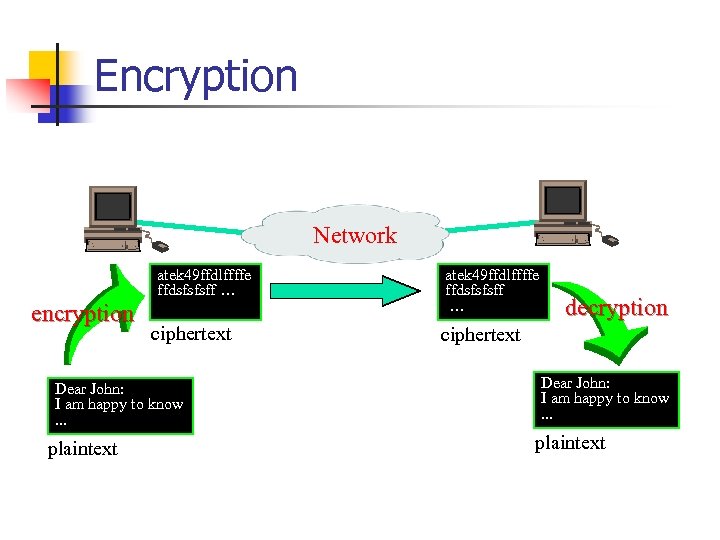 Encryption Network atek 49 ffdlffffe ffdsfsfsff … encryption ciphertext Dear John: I am happy to know. . . plaintext atek 49 ffdlffffe ffdsfsfsff … decryption ciphertext Dear John: I am happy to know. . . plaintext
Encryption Network atek 49 ffdlffffe ffdsfsfsff … encryption ciphertext Dear John: I am happy to know. . . plaintext atek 49 ffdlffffe ffdsfsfsff … decryption ciphertext Dear John: I am happy to know. . . plaintext
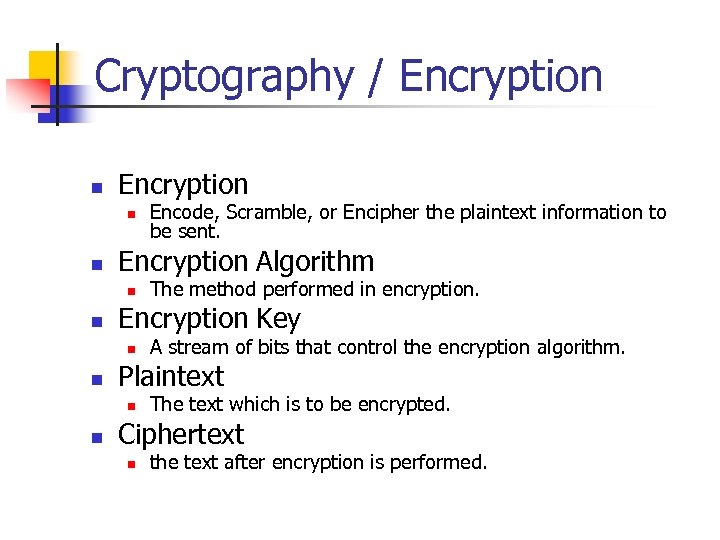 Cryptography / Encryption n n Encryption Algorithm n n A stream of bits that control the encryption algorithm. Plaintext n n The method performed in encryption. Encryption Key n n Encode, Scramble, or Encipher the plaintext information to be sent. The text which is to be encrypted. Ciphertext n the text after encryption is performed.
Cryptography / Encryption n n Encryption Algorithm n n A stream of bits that control the encryption algorithm. Plaintext n n The method performed in encryption. Encryption Key n n Encode, Scramble, or Encipher the plaintext information to be sent. The text which is to be encrypted. Ciphertext n the text after encryption is performed.
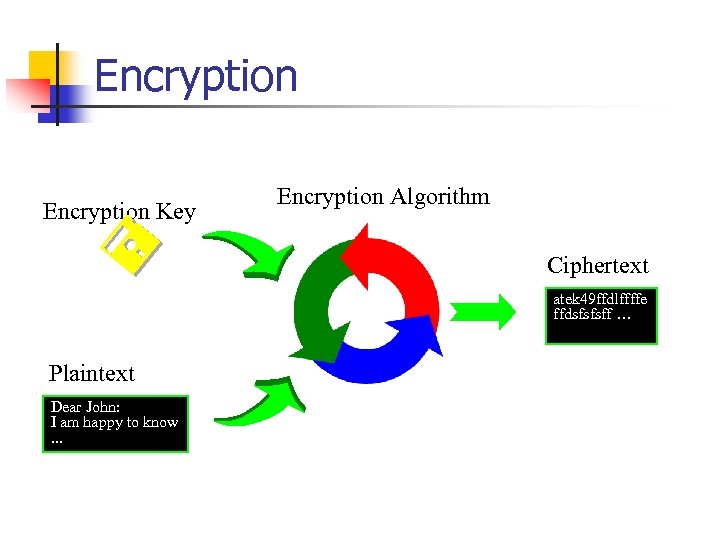 Encryption Key Encryption Algorithm Ciphertext atek 49 ffdlffffe ffdsfsfsff … Plaintext Dear John: I am happy to know. . .
Encryption Key Encryption Algorithm Ciphertext atek 49 ffdlffffe ffdsfsfsff … Plaintext Dear John: I am happy to know. . .
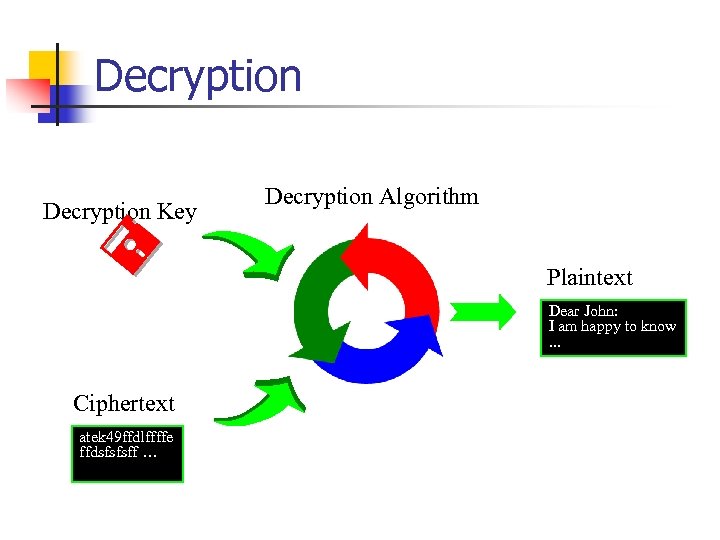 Decryption Key Decryption Algorithm Plaintext Dear John: I am happy to know. . . Ciphertext atek 49 ffdlffffe ffdsfsfsff …
Decryption Key Decryption Algorithm Plaintext Dear John: I am happy to know. . . Ciphertext atek 49 ffdlffffe ffdsfsfsff …
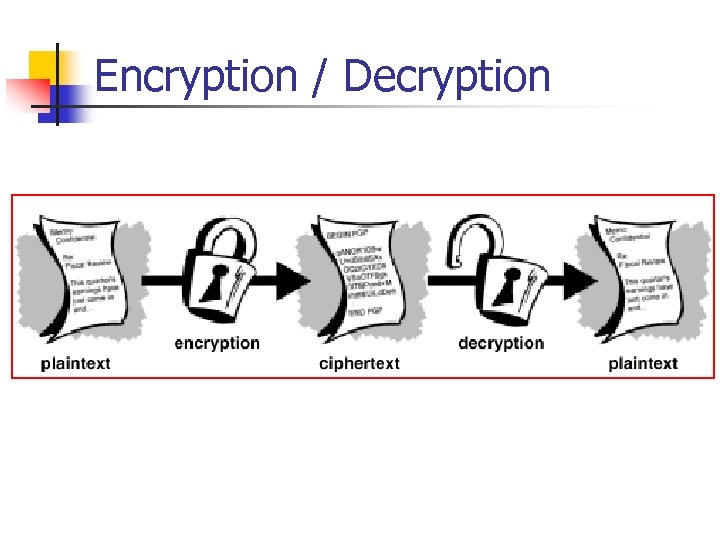 Encryption / Decryption
Encryption / Decryption
 Encryption Techniques n Private Key Encryption n Encryption Key = Decryption Key Also called Symmetric-Key Encryption, Secret-Key Encryption, or Conventional Cryptography. Encryption Public Key Encryption n n Encryption Key Decryption Key Also called Asymmetric Encryption
Encryption Techniques n Private Key Encryption n Encryption Key = Decryption Key Also called Symmetric-Key Encryption, Secret-Key Encryption, or Conventional Cryptography. Encryption Public Key Encryption n n Encryption Key Decryption Key Also called Asymmetric Encryption
 Private Key Encryption: - DES (Data Encryption Standard) n n n Adopted by U. S. Federal Government. Both the sender and receiver must know the same secret key code to encrypt and decrypt messages with DES Operates on 64 -bit blocks with a 56 -bit key DES is a fast encryption scheme and works well for bulk encryption. Issues: n How to deliver the key to the sender safely?
Private Key Encryption: - DES (Data Encryption Standard) n n n Adopted by U. S. Federal Government. Both the sender and receiver must know the same secret key code to encrypt and decrypt messages with DES Operates on 64 -bit blocks with a 56 -bit key DES is a fast encryption scheme and works well for bulk encryption. Issues: n How to deliver the key to the sender safely?
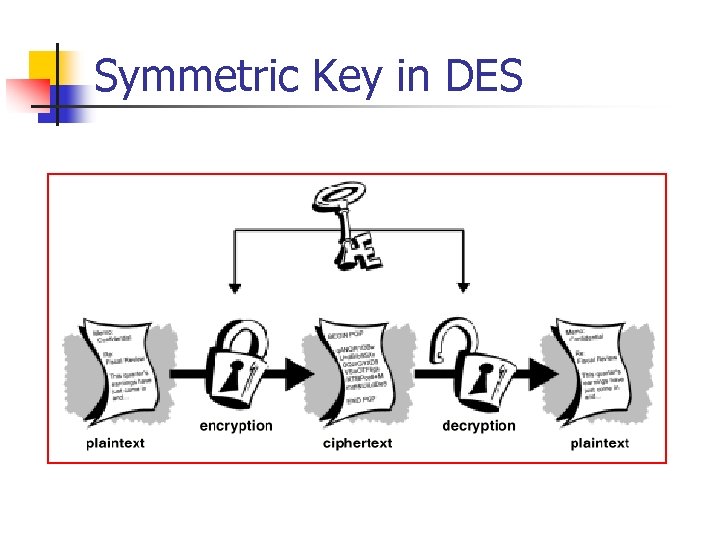 Symmetric Key in DES
Symmetric Key in DES
 Other Symmetric Key Encryption Techniques n 3 DES n n n Triple DES RC 2, RC 4 IDEA n International Data Encryption Algorithm
Other Symmetric Key Encryption Techniques n 3 DES n n n Triple DES RC 2, RC 4 IDEA n International Data Encryption Algorithm
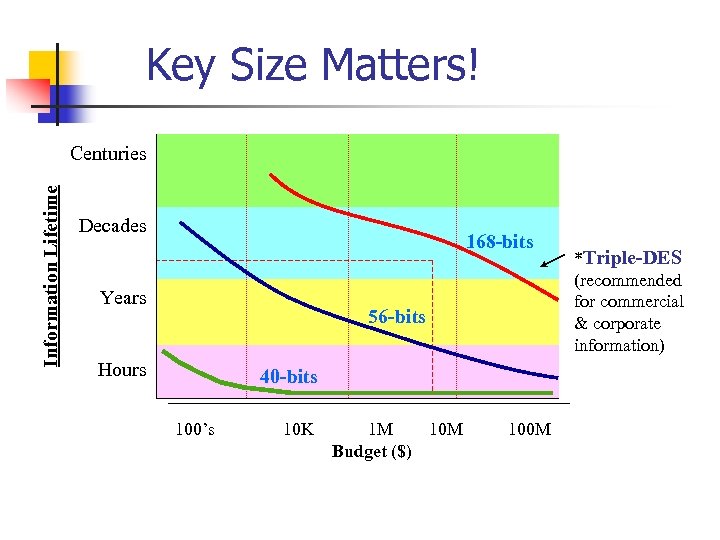 Key Size Matters! Information Lifetime Centuries Decades 168 -bits Years 56 -bits Hours 40 -bits 100’s 10 K 1 M 10 M Budget ($) 100 M *Triple-DES (recommended for commercial & corporate information)
Key Size Matters! Information Lifetime Centuries Decades 168 -bits Years 56 -bits Hours 40 -bits 100’s 10 K 1 M 10 M Budget ($) 100 M *Triple-DES (recommended for commercial & corporate information)
 Public Key Encryption: RSA n n The public key is disseminated as widely as possible. The secrete key is only known by the receiver. Named after its inventors Ron Rivest, Adi Shamir, and Leonard Adleman RSA is well established as a de facto standard RSA is fine for encrypting small messages
Public Key Encryption: RSA n n The public key is disseminated as widely as possible. The secrete key is only known by the receiver. Named after its inventors Ron Rivest, Adi Shamir, and Leonard Adleman RSA is well established as a de facto standard RSA is fine for encrypting small messages
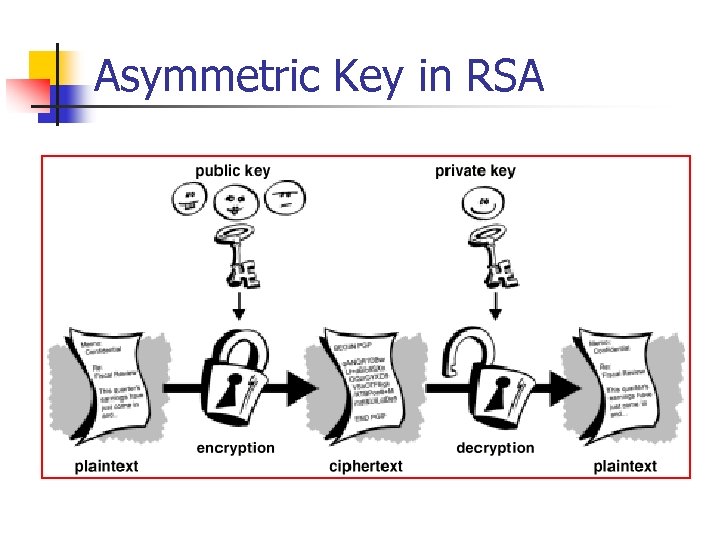 Asymmetric Key in RSA
Asymmetric Key in RSA
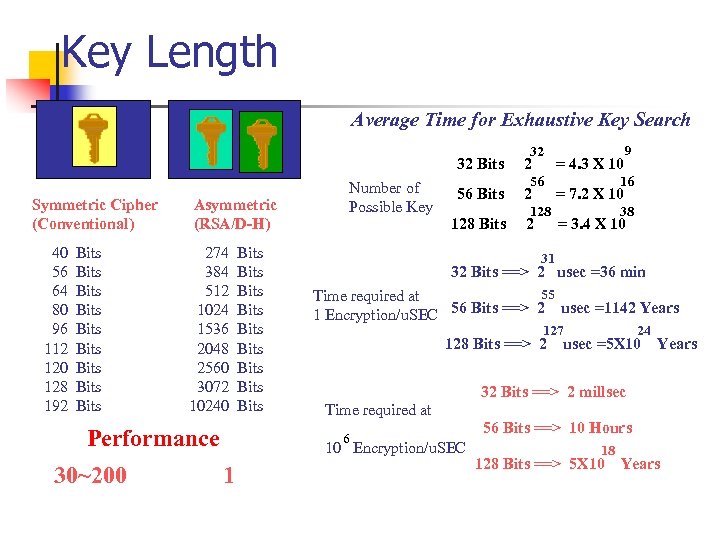 Key Length Average Time for Exhaustive Key Search 32 32 Bits Symmetric Cipher (Conventional) 40 56 64 80 96 112 120 128 192 Bits Bits Bits Asymmetric (RSA/D-H) 274 384 512 1024 1536 2048 2560 3072 10240 Performance 30~200 Bits Bits Bits Number of Possible Key 2 56 Bits 2 128 16 = 7. 2 X 10 38 = 3. 4 X 10 31 32 Bits ==> 2 usec =36 min 55 Time required at 1 Encryption/u. SEC 56 Bits ==> 2 usec =1142 Years 127 128 Bits ==> 2 24 usec =5 X 10 Years 32 Bits ==> 2 millsec Time required at 6 10 Encryption/u. SEC 1 56 = 4. 3 X 10 9 56 Bits ==> 10 Hours 18 128 Bits ==> 5 X 10 Years
Key Length Average Time for Exhaustive Key Search 32 32 Bits Symmetric Cipher (Conventional) 40 56 64 80 96 112 120 128 192 Bits Bits Bits Asymmetric (RSA/D-H) 274 384 512 1024 1536 2048 2560 3072 10240 Performance 30~200 Bits Bits Bits Number of Possible Key 2 56 Bits 2 128 16 = 7. 2 X 10 38 = 3. 4 X 10 31 32 Bits ==> 2 usec =36 min 55 Time required at 1 Encryption/u. SEC 56 Bits ==> 2 usec =1142 Years 127 128 Bits ==> 2 24 usec =5 X 10 Years 32 Bits ==> 2 millsec Time required at 6 10 Encryption/u. SEC 1 56 = 4. 3 X 10 9 56 Bits ==> 10 Hours 18 128 Bits ==> 5 X 10 Years
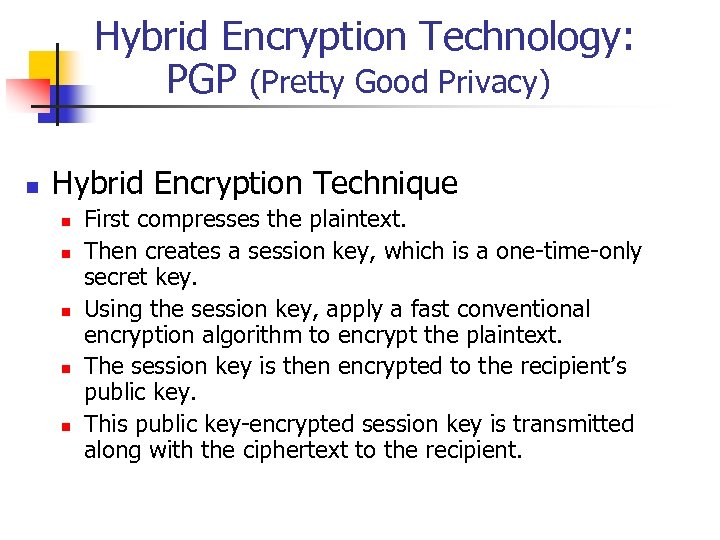 Hybrid Encryption Technology: PGP (Pretty Good Privacy) n Hybrid Encryption Technique n n n First compresses the plaintext. Then creates a session key, which is a one-time-only secret key. Using the session key, apply a fast conventional encryption algorithm to encrypt the plaintext. The session key is then encrypted to the recipient’s public key. This public key-encrypted session key is transmitted along with the ciphertext to the recipient.
Hybrid Encryption Technology: PGP (Pretty Good Privacy) n Hybrid Encryption Technique n n n First compresses the plaintext. Then creates a session key, which is a one-time-only secret key. Using the session key, apply a fast conventional encryption algorithm to encrypt the plaintext. The session key is then encrypted to the recipient’s public key. This public key-encrypted session key is transmitted along with the ciphertext to the recipient.
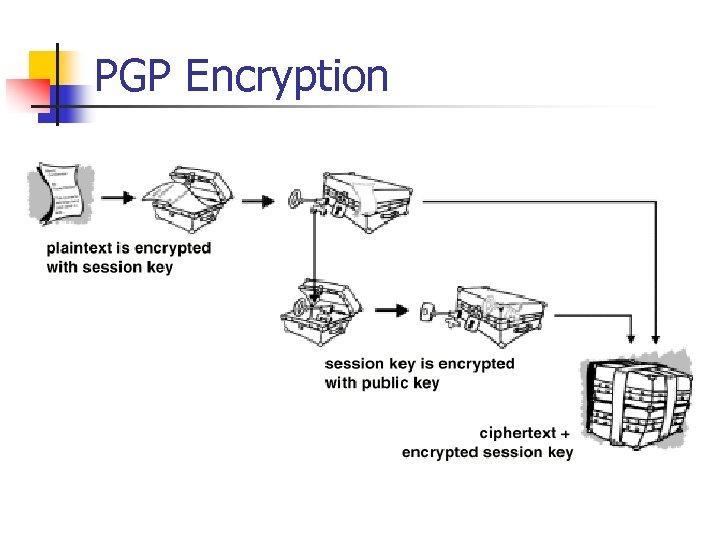 PGP Encryption
PGP Encryption
 PGP Decryption n n The recipient uses its private key to recover the temporary session key Use the session key to decrypt the conventionally-encrypted ciphertext.
PGP Decryption n n The recipient uses its private key to recover the temporary session key Use the session key to decrypt the conventionally-encrypted ciphertext.
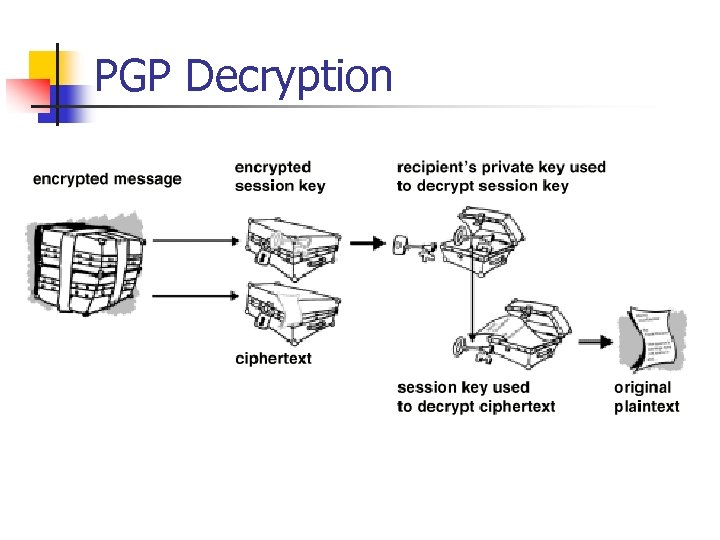 PGP Decryption
PGP Decryption
 Message Digest • • Message digest is a cryptographic hash algorithm added to a message One-way function Analogy with CRC If the message is tampered with the message digest at the receiving end fails to validate MD 5 (used in SNMPv 3) commonly used MD MD 5 takes a message of arbitrary length (32 -Byte) blocks and generates 128 -bit message digest SHS (Secured Hash Standard) message digest proposed by NIST handles 264 bits and generates 160 -bit output
Message Digest • • Message digest is a cryptographic hash algorithm added to a message One-way function Analogy with CRC If the message is tampered with the message digest at the receiving end fails to validate MD 5 (used in SNMPv 3) commonly used MD MD 5 takes a message of arbitrary length (32 -Byte) blocks and generates 128 -bit message digest SHS (Secured Hash Standard) message digest proposed by NIST handles 264 bits and generates 160 -bit output
 Digital Signatures n n Digital signatures enable the recipient of information to verify the authenticity of the information’s origin, and also verify that the information is intact. Public key digital signatures provide n n authentication data integrity non-repudiation Technique: public key cryptography n Signature created using private key and validated using public key
Digital Signatures n n Digital signatures enable the recipient of information to verify the authenticity of the information’s origin, and also verify that the information is intact. Public key digital signatures provide n n authentication data integrity non-repudiation Technique: public key cryptography n Signature created using private key and validated using public key
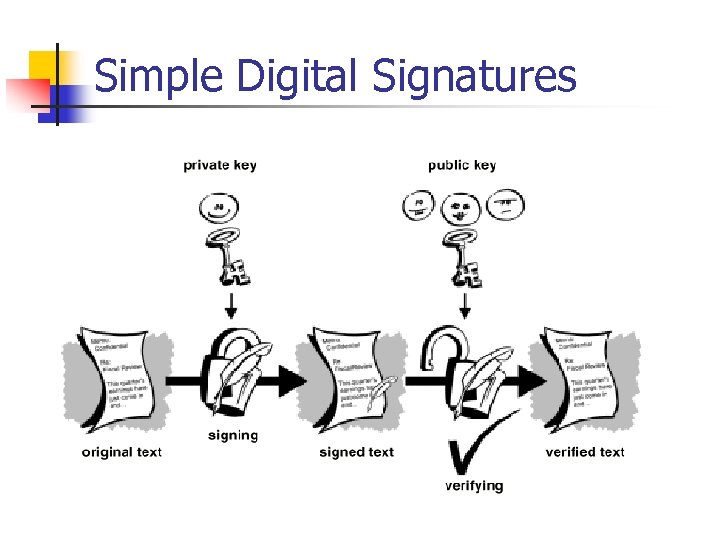 Simple Digital Signatures
Simple Digital Signatures
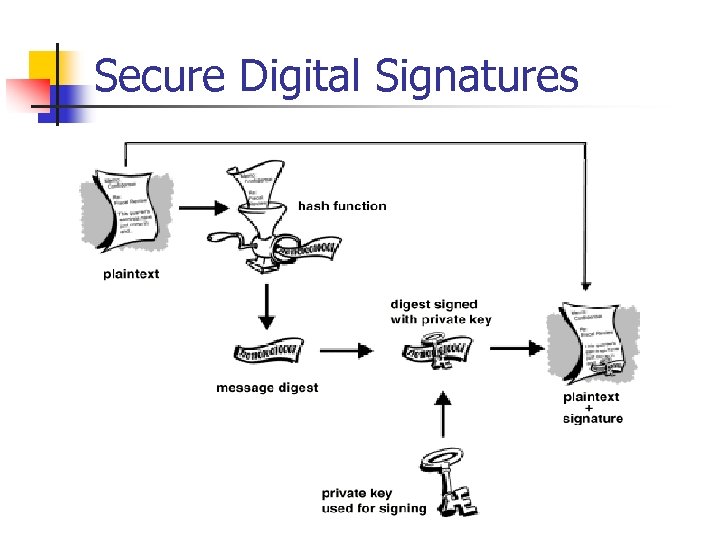 Secure Digital Signatures
Secure Digital Signatures
 Authentication and Authorization • Authentication verifies user identification • Client/server environment • Host/User Authentication • Ticket-granting system • Authentication server system • Cryptographic authentication • Messaging environment • e-mail • e-commerce • Authorization grants access to information • Read, read-write, no-access • Indefinite period, one-time use
Authentication and Authorization • Authentication verifies user identification • Client/server environment • Host/User Authentication • Ticket-granting system • Authentication server system • Cryptographic authentication • Messaging environment • e-mail • e-commerce • Authorization grants access to information • Read, read-write, no-access • Indefinite period, one-time use
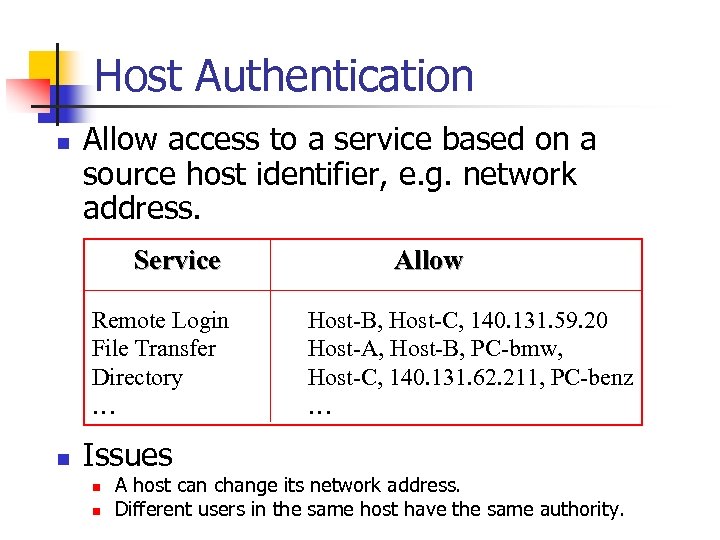 Host Authentication n Allow access to a service based on a source host identifier, e. g. network address. Service Remote Login File Transfer Directory … n Issues n n Allow Host-B, Host-C, 140. 131. 59. 20 Host-A, Host-B, PC-bmw, Host-C, 140. 131. 62. 211, PC-benz … A host can change its network address. Different users in the same host have the same authority.
Host Authentication n Allow access to a service based on a source host identifier, e. g. network address. Service Remote Login File Transfer Directory … n Issues n n Allow Host-B, Host-C, 140. 131. 59. 20 Host-A, Host-B, PC-bmw, Host-C, 140. 131. 62. 211, PC-benz … A host can change its network address. Different users in the same host have the same authority.
 User Authentication n n Enable service to identify each user before allowing that user access. Password Mechanism n n n Generally, passwords are transferred on the network without any encryption. Use encrypted passwords. Users tend to make passwords easy to remember. If the passwords are not common words, users will write them down. Host Authentication + User Authentication
User Authentication n n Enable service to identify each user before allowing that user access. Password Mechanism n n n Generally, passwords are transferred on the network without any encryption. Use encrypted passwords. Users tend to make passwords easy to remember. If the passwords are not common words, users will write them down. Host Authentication + User Authentication
 Ticket-granting system
Ticket-granting system
 Ticket-granting system 1. Used in client/server authentication system 2. Kerberos developed by MIT 3. Steps: 1. User logs on to client workstation 2. Login request sent to authentication server 3. Auth. Server checks ACL, grants encrypted ticket to client 4. Client obtains from TGS service-granting ticket and session key 5. Appl. Server validates ticket and session key, and then provides service
Ticket-granting system 1. Used in client/server authentication system 2. Kerberos developed by MIT 3. Steps: 1. User logs on to client workstation 2. Login request sent to authentication server 3. Auth. Server checks ACL, grants encrypted ticket to client 4. Client obtains from TGS service-granting ticket and session key 5. Appl. Server validates ticket and session key, and then provides service
 Authentication Server
Authentication Server
 Authentication Server • Architecture of Novell LAN • Authentication server does not issue ticket • Login and password not sent from client workstation • User sends id to central authentication server • Authentication server acts as proxy agent to the client and authenticates the user with the application server • Process transparent to the user
Authentication Server • Architecture of Novell LAN • Authentication server does not issue ticket • Login and password not sent from client workstation • User sends id to central authentication server • Authentication server acts as proxy agent to the client and authenticates the user with the application server • Process transparent to the user
 Message Transfer Security • Messaging one-way communication • Secure message needs to be authenticated and secured • Three secure mail systems • Privacy Enhanced Mail (PEM) • Pretty Good Privacy (PGP) • X-400: OSI specifications that define framework; not implementation specific
Message Transfer Security • Messaging one-way communication • Secure message needs to be authenticated and secured • Three secure mail systems • Privacy Enhanced Mail (PEM) • Pretty Good Privacy (PGP) • X-400: OSI specifications that define framework; not implementation specific
 Privacy Enhanced Mail • Developed by IETF (RFC 1421 - 1424) • End-to-end cryptography • Provides • Confidentiality • Authentication • Message integrity assurance • Nonrepudiation of origin • Data encryption key (DEK) could be secret or public key-based originator and receiver agreed upon method • PEM processes based on cryptography and message encoding • MIC-CLEAR (Message Integrity Code-CLEAR) • MIC-ONLY • ENCRYPTED
Privacy Enhanced Mail • Developed by IETF (RFC 1421 - 1424) • End-to-end cryptography • Provides • Confidentiality • Authentication • Message integrity assurance • Nonrepudiation of origin • Data encryption key (DEK) could be secret or public key-based originator and receiver agreed upon method • PEM processes based on cryptography and message encoding • MIC-CLEAR (Message Integrity Code-CLEAR) • MIC-ONLY • ENCRYPTED
 DEK = Data Encryption Key IK = Interexchange Key MIC = Message Integrity Code PEM Processes
DEK = Data Encryption Key IK = Interexchange Key MIC = Message Integrity Code PEM Processes
 Use of PGP in E-mail
Use of PGP in E-mail
 SNMPv 3 Security
SNMPv 3 Security
 SNMPv 3 Security • • • Authentication key equivalent to DEK in PEM or private key in PGP Authentication key generated using user password and SNMP engine id Authentication key may be used to encrypt message USM prepares the whole message including scoped PDU HMAC, equivalent of signature in PEM and PGP, generated using authentication key and the whole message Authentication module provided with authentication key and HMAC to process incoming message
SNMPv 3 Security • • • Authentication key equivalent to DEK in PEM or private key in PGP Authentication key generated using user password and SNMP engine id Authentication key may be used to encrypt message USM prepares the whole message including scoped PDU HMAC, equivalent of signature in PEM and PGP, generated using authentication key and the whole message Authentication module provided with authentication key and HMAC to process incoming message
 Virus Attacks • Executable programs that make copies and insert them into other programs • Attacks hosts and routers • Attack infects boot track, compromises cpu, floods network traffic, etc. • Prevention is by identifying the pattern of the virus and implementing protection in virus checkers
Virus Attacks • Executable programs that make copies and insert them into other programs • Attacks hosts and routers • Attack infects boot track, compromises cpu, floods network traffic, etc. • Prevention is by identifying the pattern of the virus and implementing protection in virus checkers
 Accounting Management • • • Least developed Usage of resources Hidden cost of IT usage (libraries) Functional accounting Business application
Accounting Management • • • Least developed Usage of resources Hidden cost of IT usage (libraries) Functional accounting Business application
 Report Management
Report Management

 Policy-Based Management
Policy-Based Management
 Policy-Based Management • Domain space consists of objects (alarms with attributes) • Rule space consists of rules (if-then) • Policy Driver controls action to be taken • Distinction between policy and rule; policy assigns responsibility and accountability • Action Space implements actions
Policy-Based Management • Domain space consists of objects (alarms with attributes) • Rule space consists of rules (if-then) • Policy Driver controls action to be taken • Distinction between policy and rule; policy assigns responsibility and accountability • Action Space implements actions
 Service Level Management • SLA management of service equivalent to Qo. S of network • SLA defines • Identification of services and characteristics • Negotiation of SLA • Deployment of agents to monitor and control • Generation of reports • SLA characteristics • Service parameters • Service levels • Component parameters • Component-to-service mappings
Service Level Management • SLA management of service equivalent to Qo. S of network • SLA defines • Identification of services and characteristics • Negotiation of SLA • Deployment of agents to monitor and control • Generation of reports • SLA characteristics • Service parameters • Service levels • Component parameters • Component-to-service mappings


