af0d76134e525a4e897638ecf8187947.ppt
- Количество слайдов: 59
 Chapter 12 Computer Programming
Chapter 12 Computer Programming
 1 Chapter Contents 2ïSection A: Programming Basics ïSection B: Procedural Programming ïSection C: Object-Oriented Programming ïSection D: Declarative Programming ïSection E: Secure Programming Chapter 12: Computer Programming 2
1 Chapter Contents 2ïSection A: Programming Basics ïSection B: Procedural Programming ïSection C: Object-Oriented Programming ïSection D: Declarative Programming ïSection E: Secure Programming Chapter 12: Computer Programming 2
 1 Programming Basics 2 A SECTION ïComputer Programming and Software Engineering ïProgramming Languages and Paradigms ïProgram Planning ïProgram Coding ïProgram Testing and Documentation ïProgramming Tools Chapter 12: Computer Programming 3
1 Programming Basics 2 A SECTION ïComputer Programming and Software Engineering ïProgramming Languages and Paradigms ïProgram Planning ïProgram Coding ïProgram Testing and Documentation ïProgramming Tools Chapter 12: Computer Programming 3
 1 Computer Programming and Software Engineering 2ïThe instructions that make up a computer program are sometimes referred to as code ïPrograms can have millions of lines of code – Developed by computer programmers • Computer programming Chapter 12: Computer Programming 4
1 Computer Programming and Software Engineering 2ïThe instructions that make up a computer program are sometimes referred to as code ïPrograms can have millions of lines of code – Developed by computer programmers • Computer programming Chapter 12: Computer Programming 4
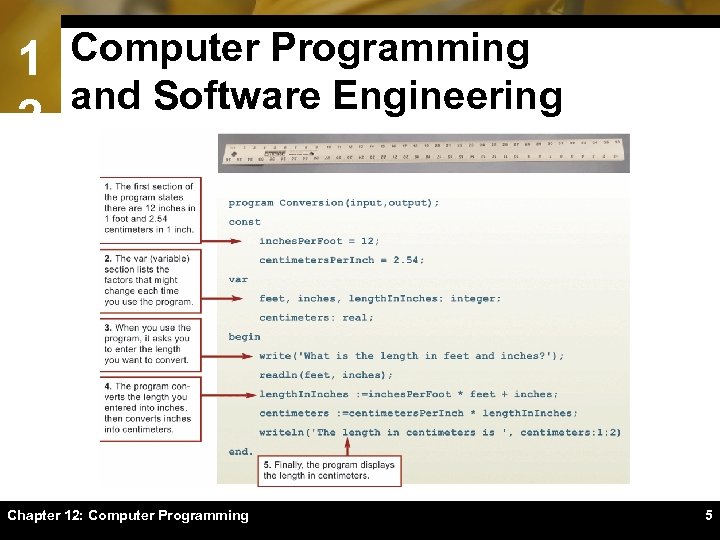 1 Computer Programming and Software Engineering 2 Chapter 12: Computer Programming 5
1 Computer Programming and Software Engineering 2 Chapter 12: Computer Programming 5
 1 Programming Languages and Paradigms 2ïProgramming languages are made up of keywords and grammar rules designed for creating computer instructions – Keywords can be combined with parameters ïLow-level languages typically include commands specific to a particular CPU or microprocessor family ïHigh-level languages use command words and grammar based on human languages Chapter 12: Computer Programming 6
1 Programming Languages and Paradigms 2ïProgramming languages are made up of keywords and grammar rules designed for creating computer instructions – Keywords can be combined with parameters ïLow-level languages typically include commands specific to a particular CPU or microprocessor family ïHigh-level languages use command words and grammar based on human languages Chapter 12: Computer Programming 6
 1 Programming Languages and Paradigms 2ïFirst-generation languages – Machine language ïSecond-generation languages – Assembly language ïThird-generation languages – Easy-to-remember command words Chapter 12: Computer Programming 7
1 Programming Languages and Paradigms 2ïFirst-generation languages – Machine language ïSecond-generation languages – Assembly language ïThird-generation languages – Easy-to-remember command words Chapter 12: Computer Programming 7
 1 Programming Languages and Paradigms 2ïFourth-generation languages – More closely resembles human language ïFifth-generation languages – Based on a declarative programming paradigm ïThe programming paradigm refers to a way of conceptualizing and structuring the tasks a computer performs Chapter 12: Computer Programming 8
1 Programming Languages and Paradigms 2ïFourth-generation languages – More closely resembles human language ïFifth-generation languages – Based on a declarative programming paradigm ïThe programming paradigm refers to a way of conceptualizing and structuring the tasks a computer performs Chapter 12: Computer Programming 8
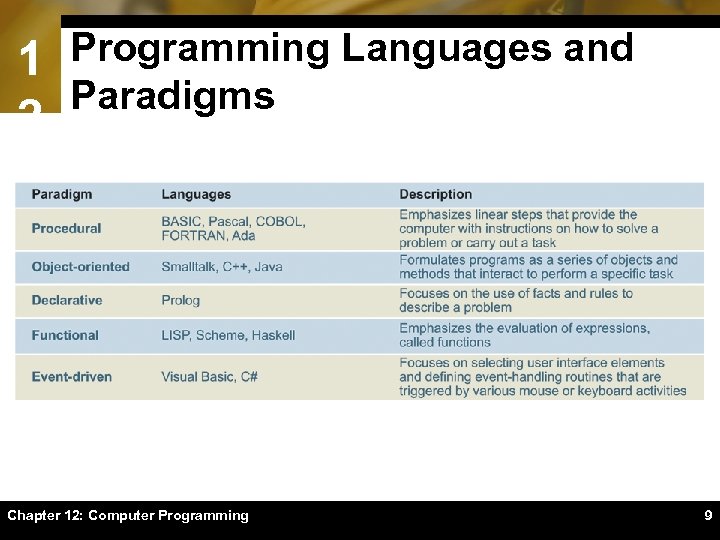 1 Programming Languages and Paradigms 2 Chapter 12: Computer Programming 9
1 Programming Languages and Paradigms 2 Chapter 12: Computer Programming 9
 1 Program Planning 2ïThe problem statement defines certain elements that must be manipulated to achieve a result or goal ïYou accept assumptions as true to proceed with program planning ïKnown information helps the computer to solve a problem ïVariables vs. constants Chapter 12: Computer Programming 10
1 Program Planning 2ïThe problem statement defines certain elements that must be manipulated to achieve a result or goal ïYou accept assumptions as true to proceed with program planning ïKnown information helps the computer to solve a problem ïVariables vs. constants Chapter 12: Computer Programming 10
 1 Program Planning 2ïProblem statement: Assuming that there are two pizzas to compare, that both pizzas contain the same toppings, and that the pizzas could be round or square, and given the prices, shapes, and sizes of the two pizzas, the computer will print a message indicating which pizza has the lower price per square inch Chapter 12: Computer Programming 11
1 Program Planning 2ïProblem statement: Assuming that there are two pizzas to compare, that both pizzas contain the same toppings, and that the pizzas could be round or square, and given the prices, shapes, and sizes of the two pizzas, the computer will print a message indicating which pizza has the lower price per square inch Chapter 12: Computer Programming 11
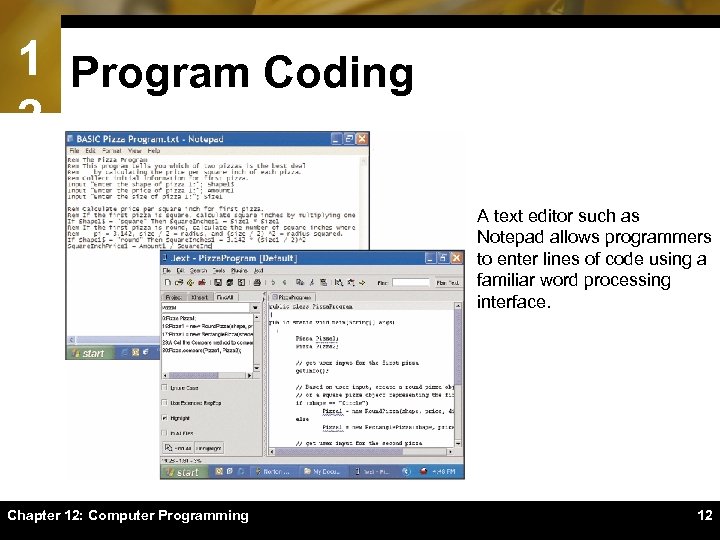 1 Program Coding 2 A text editor such as Notepad allows programmers to enter lines of code using a familiar word processing interface. Chapter 12: Computer Programming 12
1 Program Coding 2 A text editor such as Notepad allows programmers to enter lines of code using a familiar word processing interface. Chapter 12: Computer Programming 12
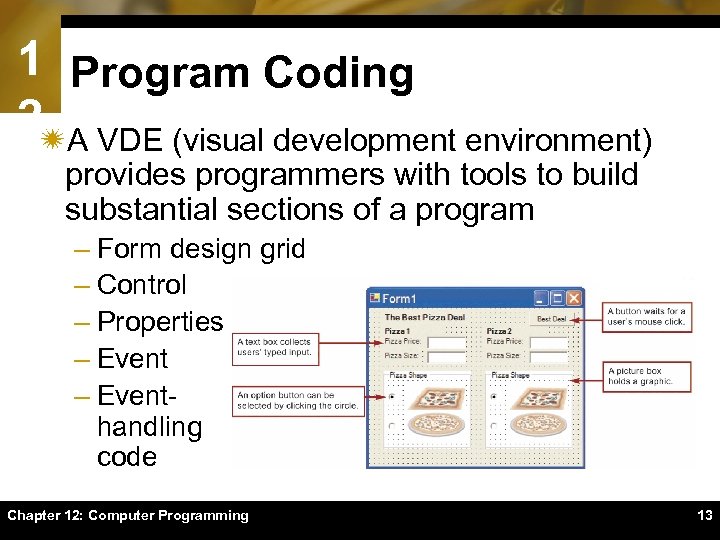 1 Program Coding 2ïA VDE (visual development environment) provides programmers with tools to build substantial sections of a program – Form design grid – Control – Properties – Eventhandling code Chapter 12: Computer Programming 13
1 Program Coding 2ïA VDE (visual development environment) provides programmers with tools to build substantial sections of a program – Form design grid – Control – Properties – Eventhandling code Chapter 12: Computer Programming 13
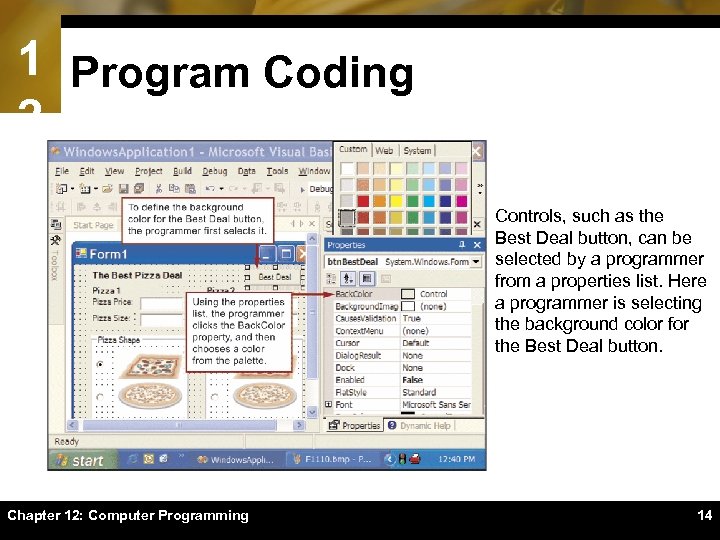 1 Program Coding 2 Controls, such as the Best Deal button, can be selected by a programmer from a properties list. Here a programmer is selecting the background color for the Best Deal button. Chapter 12: Computer Programming 14
1 Program Coding 2 Controls, such as the Best Deal button, can be selected by a programmer from a properties list. Here a programmer is selecting the background color for the Best Deal button. Chapter 12: Computer Programming 14
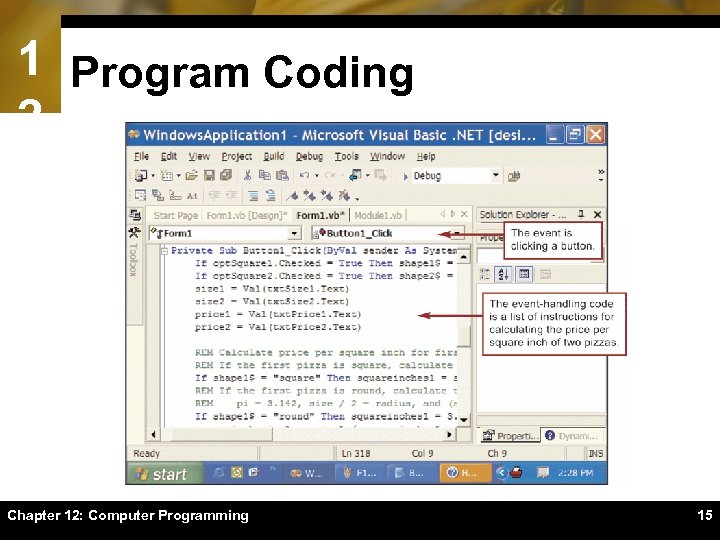 1 Program Coding 2 Chapter 12: Computer Programming 15
1 Program Coding 2 Chapter 12: Computer Programming 15
 1 Program Testing and Documentation 2ïA computer program must be tested to ensure that it works correctly ïProgram errors include – Syntax errors – Runtime errors – Logic errors ïA debugger can help a programmer read through lines of code and solve problems Chapter 12: Computer Programming 16
1 Program Testing and Documentation 2ïA computer program must be tested to ensure that it works correctly ïProgram errors include – Syntax errors – Runtime errors – Logic errors ïA debugger can help a programmer read through lines of code and solve problems Chapter 12: Computer Programming 16
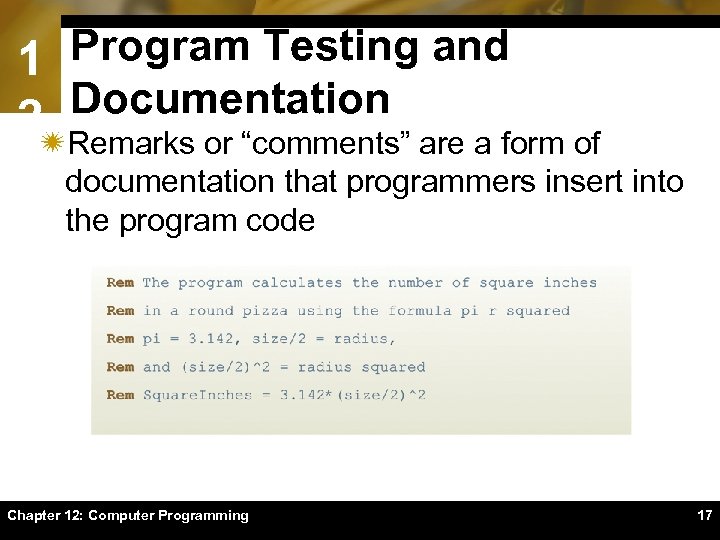 1 Program Testing and Documentation 2ïRemarks or “comments” are a form of documentation that programmers insert into the program code Chapter 12: Computer Programming 17
1 Program Testing and Documentation 2ïRemarks or “comments” are a form of documentation that programmers insert into the program code Chapter 12: Computer Programming 17
 1 Programming Tools 2ïAn SDK (software development kit) is a collection of language-specific programming tools that enables a programmer to develop applications for a specific computer platform ïAn IDE (integrated development environment) is a type of SDK that packages a set of development tools into a sleek programming application Chapter 12: Computer Programming 18
1 Programming Tools 2ïAn SDK (software development kit) is a collection of language-specific programming tools that enables a programmer to develop applications for a specific computer platform ïAn IDE (integrated development environment) is a type of SDK that packages a set of development tools into a sleek programming application Chapter 12: Computer Programming 18
 1 Programming Tools 2ï A component is a prewritten module, typically designed to accomplish a specific task ï An API is a set of application program or operating system functions that programmers can access from within the programs they create ï C and C++ are the most popular programming languages ï Particle renderers – Pathfinder algorithms Chapter 12: Computer Programming 19
1 Programming Tools 2ï A component is a prewritten module, typically designed to accomplish a specific task ï An API is a set of application program or operating system functions that programmers can access from within the programs they create ï C and C++ are the most popular programming languages ï Particle renderers – Pathfinder algorithms Chapter 12: Computer Programming 19
 B SECTION 1 Procedural Programming 2 ïAlgorithms ïExpressing an Algorithm ïSequence, Selection, and Repetition Controls ïProcedural Languages and Applications Chapter 12: Computer Programming 20
B SECTION 1 Procedural Programming 2 ïAlgorithms ïExpressing an Algorithm ïSequence, Selection, and Repetition Controls ïProcedural Languages and Applications Chapter 12: Computer Programming 20
 1 Algorithms 2ïSet of steps for carrying out a task that can be written down and implemented ïStart by recording the steps you take to solve the problem manually ïSpecify how to manipulate information ïSpecify what the algorithm should display as a solution Chapter 12: Computer Programming 21
1 Algorithms 2ïSet of steps for carrying out a task that can be written down and implemented ïStart by recording the steps you take to solve the problem manually ïSpecify how to manipulate information ïSpecify what the algorithm should display as a solution Chapter 12: Computer Programming 21
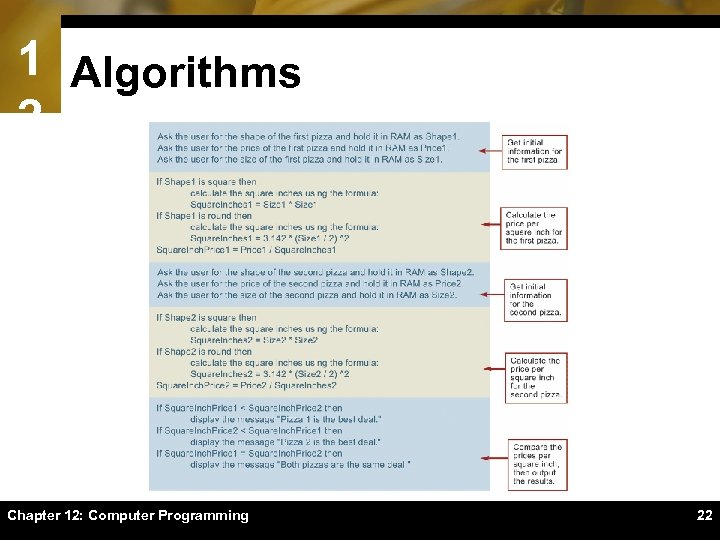 1 Algorithms 2 Chapter 12: Computer Programming 22
1 Algorithms 2 Chapter 12: Computer Programming 22
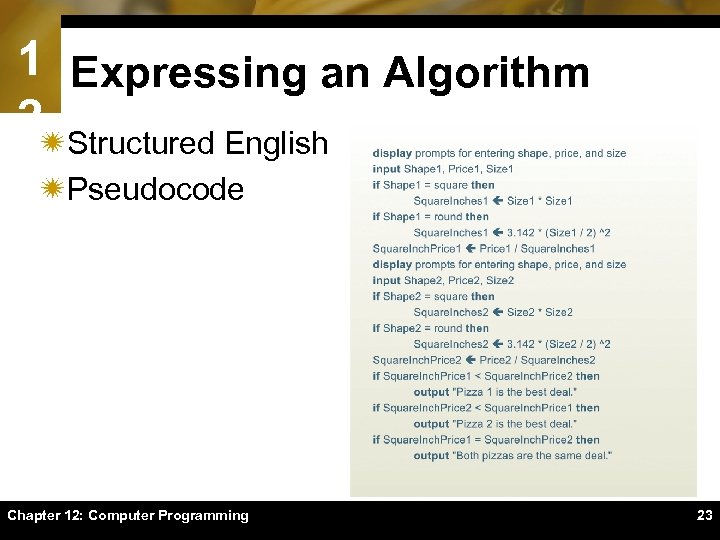 1 Expressing an Algorithm 2ïStructured English ïPseudocode Chapter 12: Computer Programming 23
1 Expressing an Algorithm 2ïStructured English ïPseudocode Chapter 12: Computer Programming 23
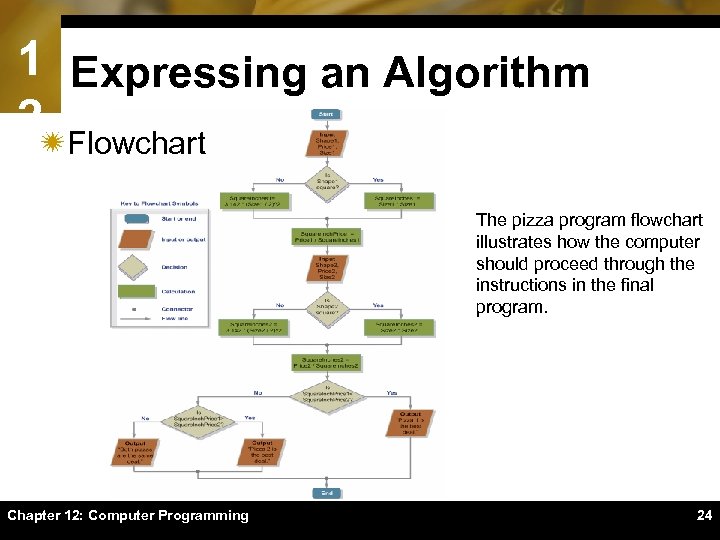 1 Expressing an Algorithm 2ïFlowchart The pizza program flowchart illustrates how the computer should proceed through the instructions in the final program. Chapter 12: Computer Programming 24
1 Expressing an Algorithm 2ïFlowchart The pizza program flowchart illustrates how the computer should proceed through the instructions in the final program. Chapter 12: Computer Programming 24
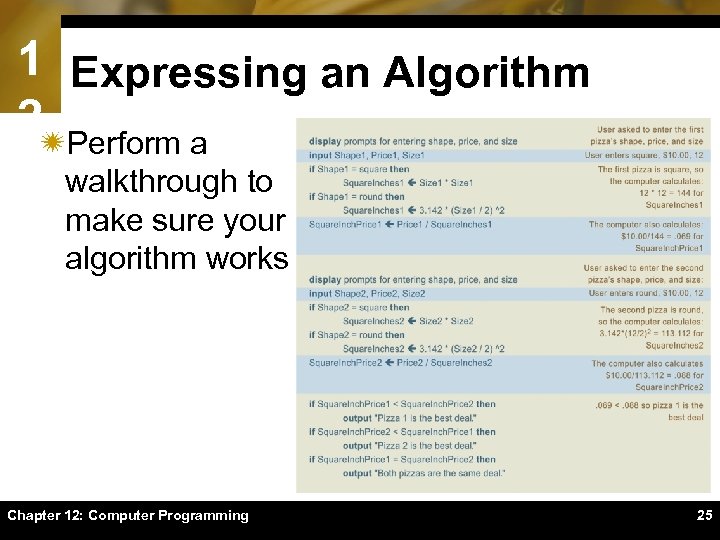 1 Expressing an Algorithm 2ïPerform a walkthrough to make sure your algorithm works Chapter 12: Computer Programming 25
1 Expressing an Algorithm 2ïPerform a walkthrough to make sure your algorithm works Chapter 12: Computer Programming 25
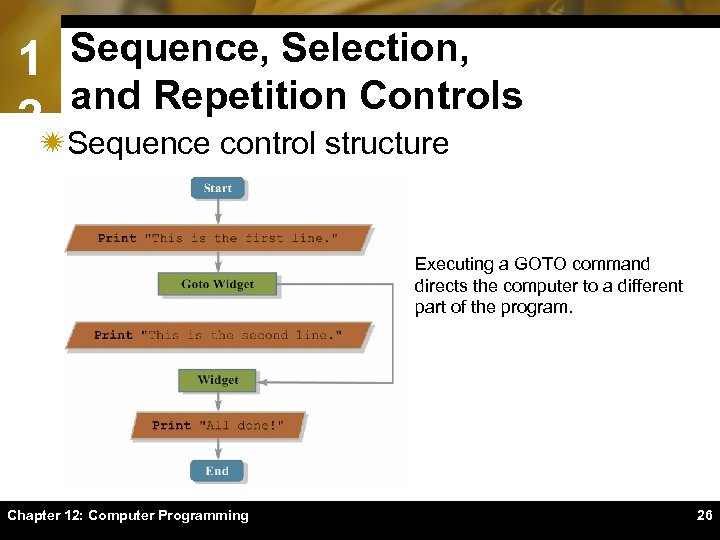 1 Sequence, Selection, and Repetition Controls 2ïSequence control structure Executing a GOTO command directs the computer to a different part of the program. Chapter 12: Computer Programming 26
1 Sequence, Selection, and Repetition Controls 2ïSequence control structure Executing a GOTO command directs the computer to a different part of the program. Chapter 12: Computer Programming 26
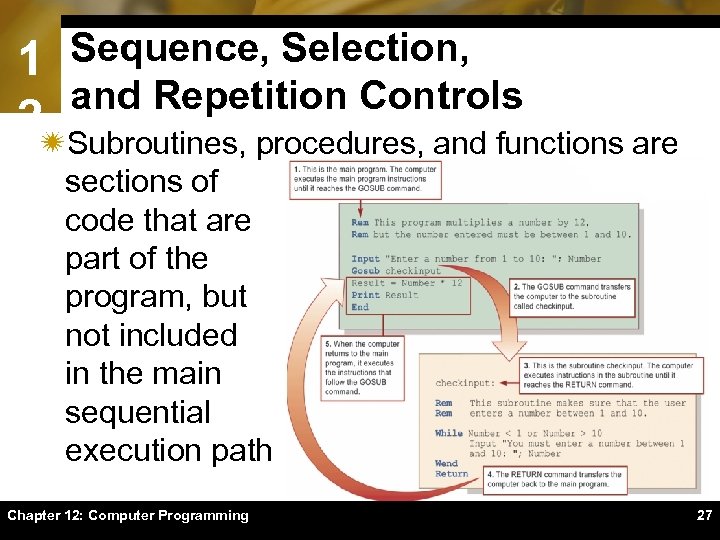 1 Sequence, Selection, and Repetition Controls 2ïSubroutines, procedures, and functions are sections of code that are part of the program, but not included in the main sequential execution path Chapter 12: Computer Programming 27
1 Sequence, Selection, and Repetition Controls 2ïSubroutines, procedures, and functions are sections of code that are part of the program, but not included in the main sequential execution path Chapter 12: Computer Programming 27
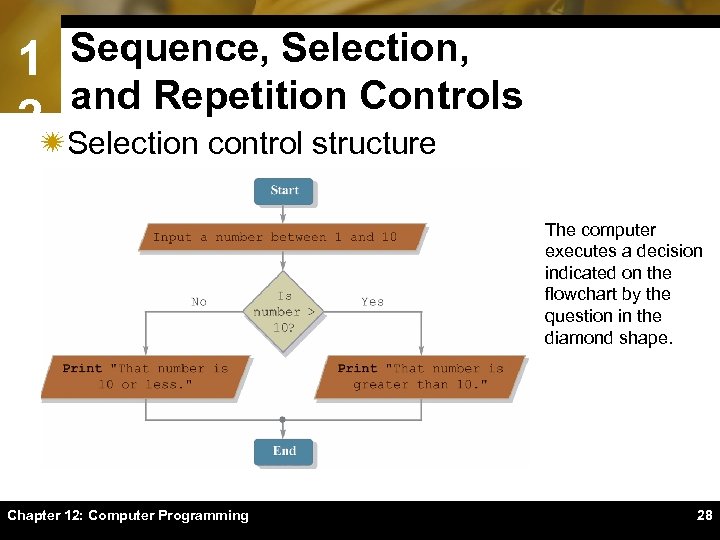 1 Sequence, Selection, and Repetition Controls 2ïSelection control structure The computer executes a decision indicated on the flowchart by the question in the diamond shape. Chapter 12: Computer Programming 28
1 Sequence, Selection, and Repetition Controls 2ïSelection control structure The computer executes a decision indicated on the flowchart by the question in the diamond shape. Chapter 12: Computer Programming 28
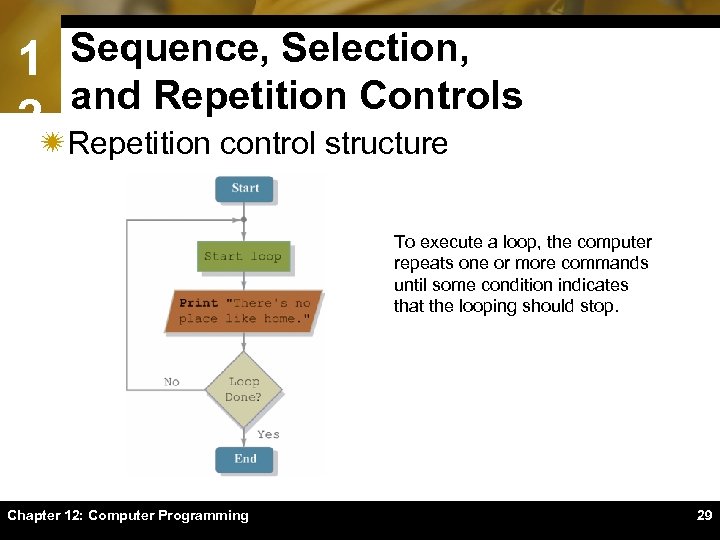 1 Sequence, Selection, and Repetition Controls 2ïRepetition control structure To execute a loop, the computer repeats one or more commands until some condition indicates that the looping should stop. Chapter 12: Computer Programming 29
1 Sequence, Selection, and Repetition Controls 2ïRepetition control structure To execute a loop, the computer repeats one or more commands until some condition indicates that the looping should stop. Chapter 12: Computer Programming 29
 1 Procedural Languages and Applications 2ïPopular procedural languages include FORTRAN, COBOL, FORTH, APL, ALGOL, PL/1, Pascal, C, Ada, and BASIC ïThe procedural approach is best used for problems that can be solved by following a step-by-step algorithm – Does not fit well with certain types of problems ïProduces programs that run quickly and efficiently Chapter 12: Computer Programming 30
1 Procedural Languages and Applications 2ïPopular procedural languages include FORTRAN, COBOL, FORTH, APL, ALGOL, PL/1, Pascal, C, Ada, and BASIC ïThe procedural approach is best used for problems that can be solved by following a step-by-step algorithm – Does not fit well with certain types of problems ïProduces programs that run quickly and efficiently Chapter 12: Computer Programming 30
 C SECTION 1 Object-Oriented Programming 2 ïObjects and Classes ïInheritance ïMethods and Messages ïObject-oriented Program Structure ïObject-oriented Languages and Applications Chapter 12: Computer Programming 31
C SECTION 1 Object-Oriented Programming 2 ïObjects and Classes ïInheritance ïMethods and Messages ïObject-oriented Program Structure ïObject-oriented Languages and Applications Chapter 12: Computer Programming 31
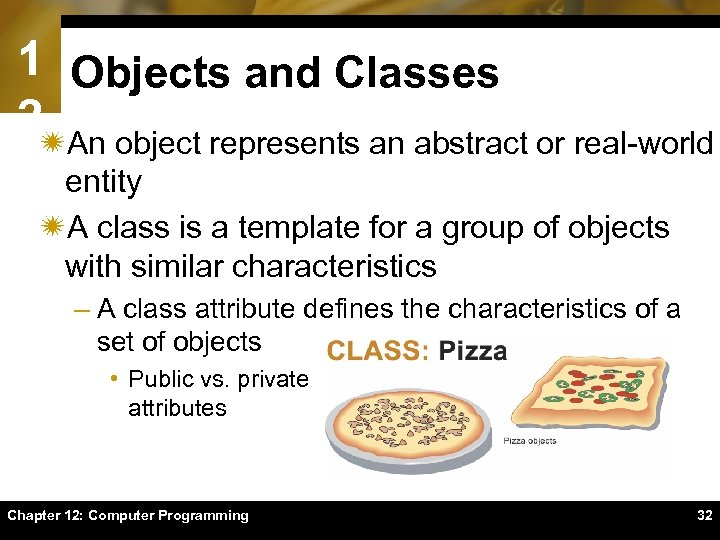 1 Objects and Classes 2ïAn object represents an abstract or real-world entity ïA class is a template for a group of objects with similar characteristics – A class attribute defines the characteristics of a set of objects • Public vs. private attributes Chapter 12: Computer Programming 32
1 Objects and Classes 2ïAn object represents an abstract or real-world entity ïA class is a template for a group of objects with similar characteristics – A class attribute defines the characteristics of a set of objects • Public vs. private attributes Chapter 12: Computer Programming 32
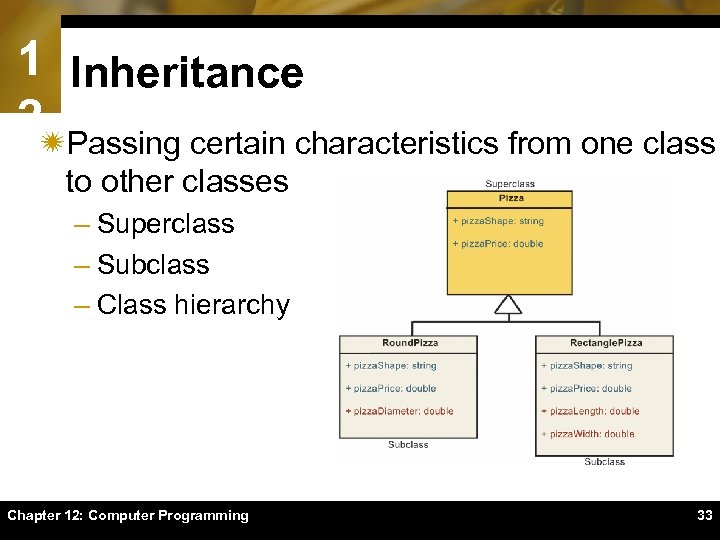 1 Inheritance 2ïPassing certain characteristics from one class to other classes – Superclass – Subclass – Class hierarchy Chapter 12: Computer Programming 33
1 Inheritance 2ïPassing certain characteristics from one class to other classes – Superclass – Subclass – Class hierarchy Chapter 12: Computer Programming 33
 1 Methods and Messages 2ïA method is a segment of code that defines an action – Collect input, perform calculations, etc. – A method is activated by a message – Can be defined along with the class they affect ïPolymorphism refers to the ability to redefine a method in a subclass – Helps simplify program code Chapter 12: Computer Programming 34
1 Methods and Messages 2ïA method is a segment of code that defines an action – Collect input, perform calculations, etc. – A method is activated by a message – Can be defined along with the class they affect ïPolymorphism refers to the ability to redefine a method in a subclass – Helps simplify program code Chapter 12: Computer Programming 34
 1 Object-Oriented Program Structure 2 Chapter 12: Computer Programming 35
1 Object-Oriented Program Structure 2 Chapter 12: Computer Programming 35
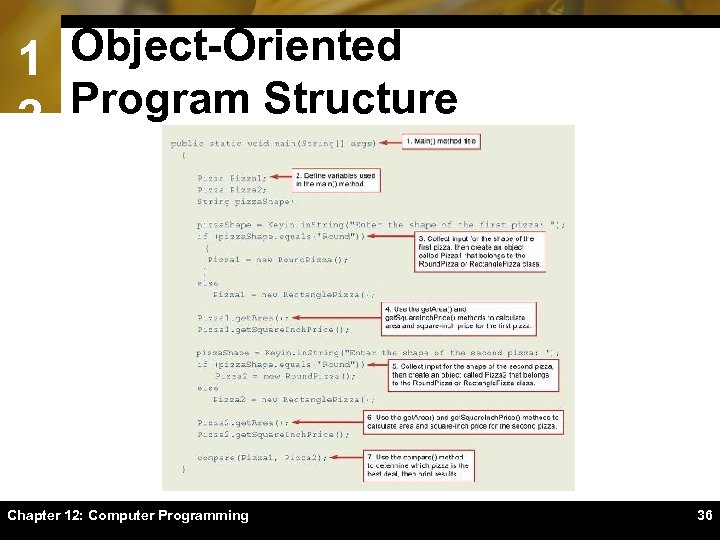 1 Object-Oriented Program Structure 2 Chapter 12: Computer Programming 36
1 Object-Oriented Program Structure 2 Chapter 12: Computer Programming 36
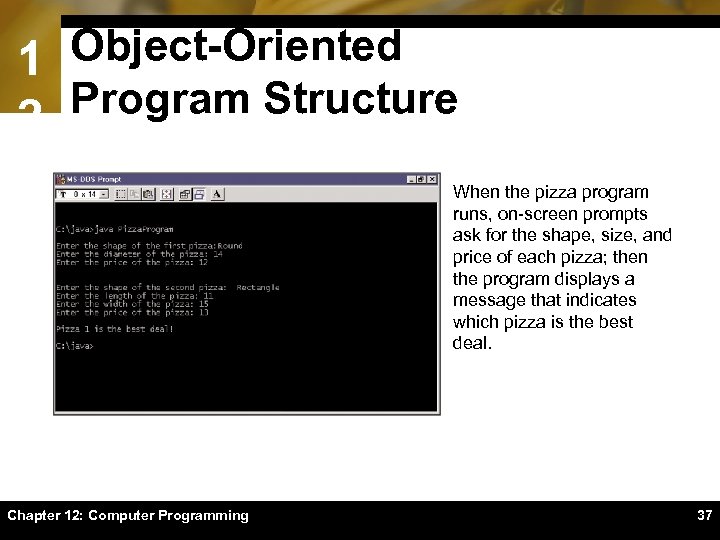 1 Object-Oriented Program Structure 2 When the pizza program runs, on-screen prompts ask for the shape, size, and price of each pizza; then the program displays a message that indicates which pizza is the best deal. Chapter 12: Computer Programming 37
1 Object-Oriented Program Structure 2 When the pizza program runs, on-screen prompts ask for the shape, size, and price of each pizza; then the program displays a message that indicates which pizza is the best deal. Chapter 12: Computer Programming 37
 1 Object-Oriented Languages and Applications 2ï SIMULA was believed to be the first object-oriented computer language ï The Dynabook project was the second major development in object-oriented languages ï Popular object-oriented languages today are Ada 95, C++, Visual Basic, and C# ï The OO paradigm results in decreased runtime efficiency, but allows encapsulation, which hides the internal details of objects and their methods Chapter 12: Computer Programming 38
1 Object-Oriented Languages and Applications 2ï SIMULA was believed to be the first object-oriented computer language ï The Dynabook project was the second major development in object-oriented languages ï Popular object-oriented languages today are Ada 95, C++, Visual Basic, and C# ï The OO paradigm results in decreased runtime efficiency, but allows encapsulation, which hides the internal details of objects and their methods Chapter 12: Computer Programming 38
 D SECTION 1 Declarative Programming 2 ïThe Declarative Paradigm ïProlog Facts ïProlog Rules ïInput Capabilities ïDeclarative Languages and Applications Chapter 12: Computer Programming 39
D SECTION 1 Declarative Programming 2 ïThe Declarative Paradigm ïProlog Facts ïProlog Rules ïInput Capabilities ïDeclarative Languages and Applications Chapter 12: Computer Programming 39
 1 The Declarative Paradigm 2ïAttempts to describe a problem without specifying exactly how to arrive at a solution – A fact is a statement for solving a problem – Rules describe the relationship between facts Chapter 12: Computer Programming 40
1 The Declarative Paradigm 2ïAttempts to describe a problem without specifying exactly how to arrive at a solution – A fact is a statement for solving a problem – Rules describe the relationship between facts Chapter 12: Computer Programming 40
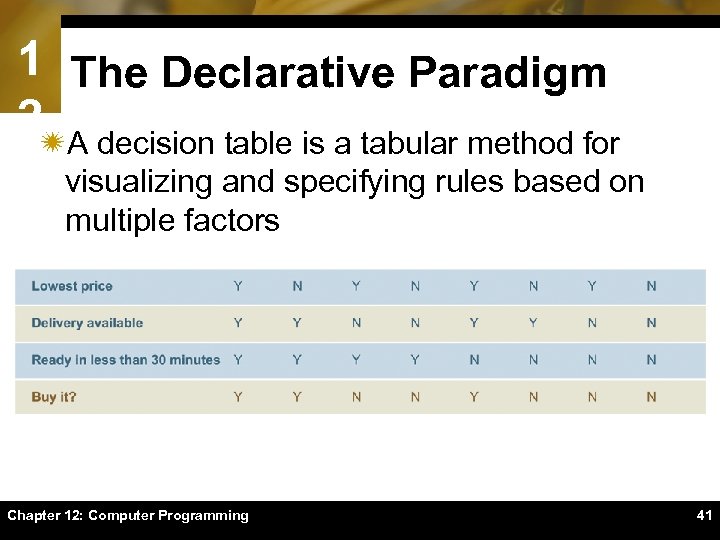 1 The Declarative Paradigm 2ïA decision table is a tabular method for visualizing and specifying rules based on multiple factors Chapter 12: Computer Programming 41
1 The Declarative Paradigm 2ïA decision table is a tabular method for visualizing and specifying rules based on multiple factors Chapter 12: Computer Programming 41
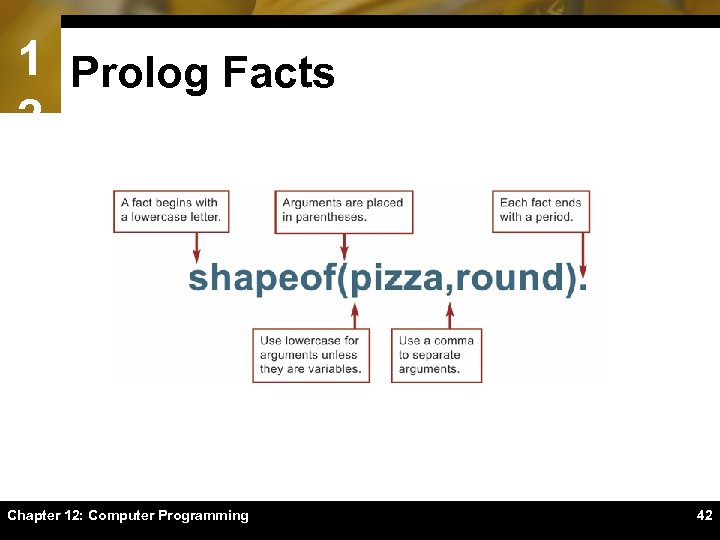 1 Prolog Facts 2 Chapter 12: Computer Programming 42
1 Prolog Facts 2 Chapter 12: Computer Programming 42
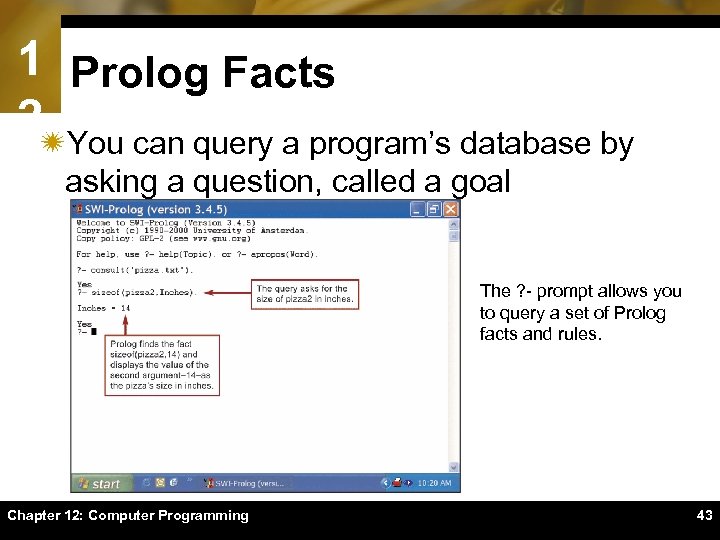 1 Prolog Facts 2ïYou can query a program’s database by asking a question, called a goal The ? - prompt allows you to query a set of Prolog facts and rules. Chapter 12: Computer Programming 43
1 Prolog Facts 2ïYou can query a program’s database by asking a question, called a goal The ? - prompt allows you to query a set of Prolog facts and rules. Chapter 12: Computer Programming 43
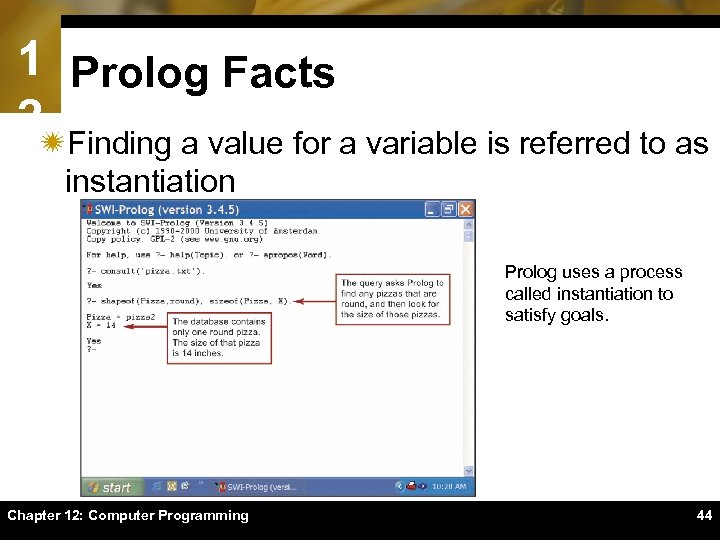 1 Prolog Facts 2ïFinding a value for a variable is referred to as instantiation Prolog uses a process called instantiation to satisfy goals. Chapter 12: Computer Programming 44
1 Prolog Facts 2ïFinding a value for a variable is referred to as instantiation Prolog uses a process called instantiation to satisfy goals. Chapter 12: Computer Programming 44
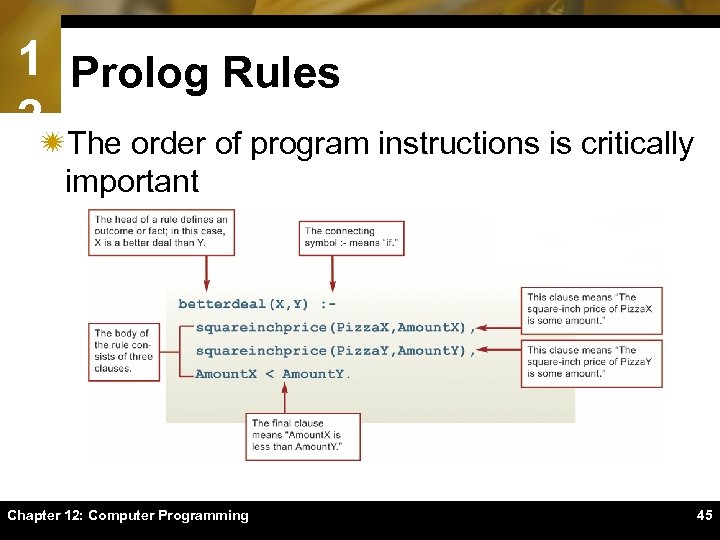 1 Prolog Rules 2ïThe order of program instructions is critically important Chapter 12: Computer Programming 45
1 Prolog Rules 2ïThe order of program instructions is critically important Chapter 12: Computer Programming 45
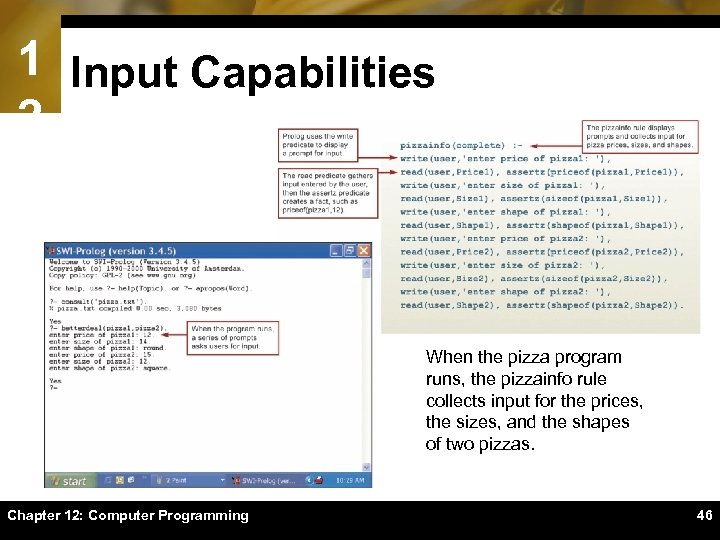 1 Input Capabilities 2 When the pizza program runs, the pizzainfo rule collects input for the prices, the sizes, and the shapes of two pizzas. Chapter 12: Computer Programming 46
1 Input Capabilities 2 When the pizza program runs, the pizzainfo rule collects input for the prices, the sizes, and the shapes of two pizzas. Chapter 12: Computer Programming 46
 1 Declarative Languages and Applications 2ïDeclarative programming languages are most suitable for problems that pertain to words and concepts rather than to numbers – Highly effective programming environment – Not commonly used for production applications – Minimal input and output capabilities – Poor performance on today’s personal computer architecture Chapter 12: Computer Programming 47
1 Declarative Languages and Applications 2ïDeclarative programming languages are most suitable for problems that pertain to words and concepts rather than to numbers – Highly effective programming environment – Not commonly used for production applications – Minimal input and output capabilities – Poor performance on today’s personal computer architecture Chapter 12: Computer Programming 47
 1 Secure Programming 2 E SECTION ïBlack Hat Exploits ïSecure Software Development ïMitigation Chapter 12: Computer Programming 48
1 Secure Programming 2 E SECTION ïBlack Hat Exploits ïSecure Software Development ïMitigation Chapter 12: Computer Programming 48
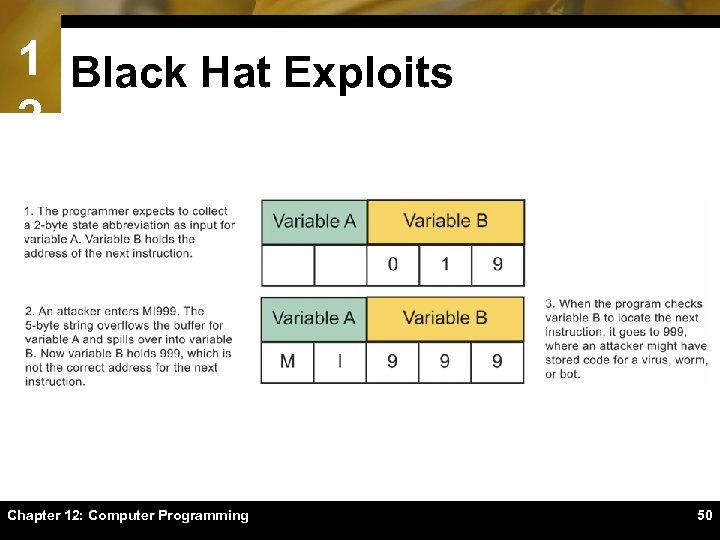
 1 Black Hat Exploits 2ïToday’s operating systems, utilities, and application software full of defects that create security holes, which are exploited by black hats ïA buffer overflow (also called a buffer overrun) is a condition in which data in memory exceeds its expected boundaries and flows into memory areas intended for use by other data Chapter 12: Computer Programming 49
1 Black Hat Exploits 2ïToday’s operating systems, utilities, and application software full of defects that create security holes, which are exploited by black hats ïA buffer overflow (also called a buffer overrun) is a condition in which data in memory exceeds its expected boundaries and flows into memory areas intended for use by other data Chapter 12: Computer Programming 49
 1 Black Hat Exploits 2 Chapter 12: Computer Programming 50
1 Black Hat Exploits 2 Chapter 12: Computer Programming 50
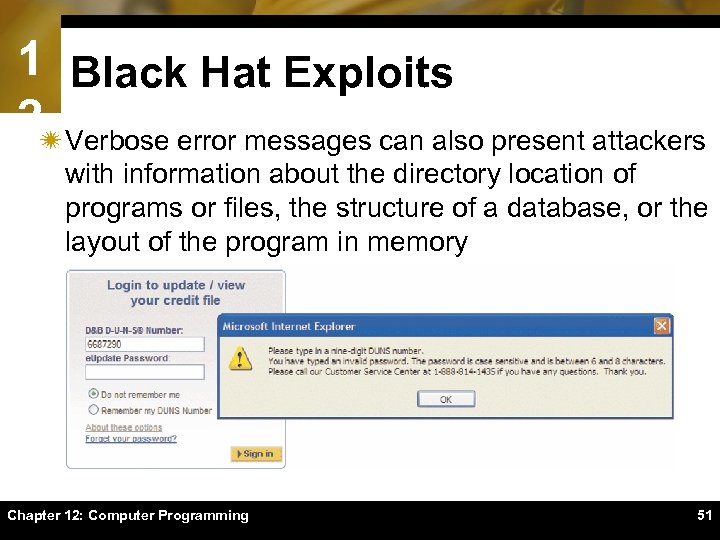 1 Black Hat Exploits 2ï Verbose error messages can also present attackers with information about the directory location of programs or files, the structure of a database, or the layout of the program in memory Chapter 12: Computer Programming 51
1 Black Hat Exploits 2ï Verbose error messages can also present attackers with information about the directory location of programs or files, the structure of a database, or the layout of the program in memory Chapter 12: Computer Programming 51
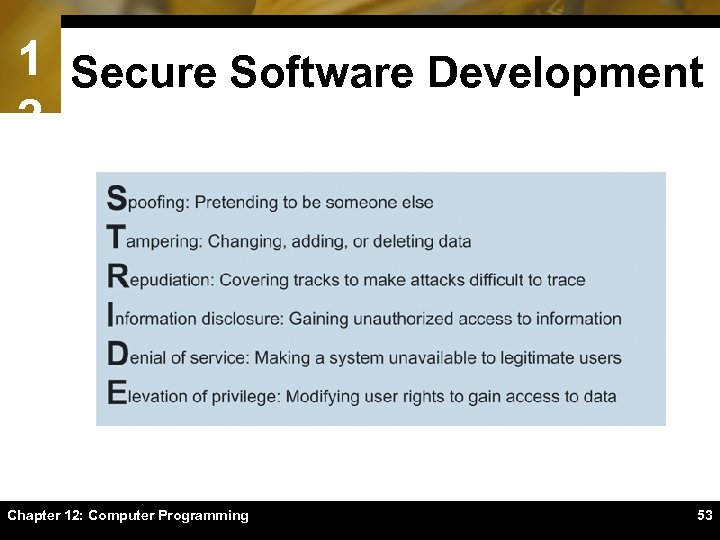
 1 Secure Software Development 2ïMost software security problems can be traced back to defects that programmers unintentionally introduce in software during design and development ïFormal methods help programmers apply rigorous logical and mathematical models to software design, coding, testing, and verification ïThreat modeling (risk analysis) Chapter 12: Computer Programming 52
1 Secure Software Development 2ïMost software security problems can be traced back to defects that programmers unintentionally introduce in software during design and development ïFormal methods help programmers apply rigorous logical and mathematical models to software design, coding, testing, and verification ïThreat modeling (risk analysis) Chapter 12: Computer Programming 52
 1 Secure Software Development 2 Chapter 12: Computer Programming 53
1 Secure Software Development 2 Chapter 12: Computer Programming 53
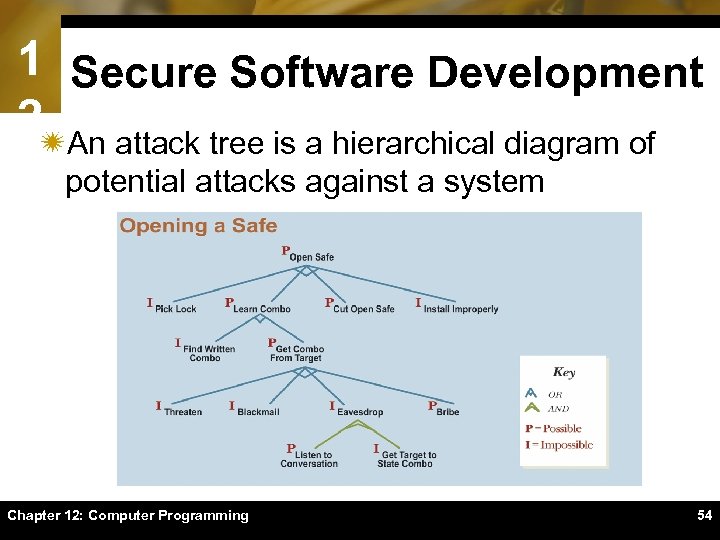 1 Secure Software Development 2ïAn attack tree is a hierarchical diagram of potential attacks against a system Chapter 12: Computer Programming 54
1 Secure Software Development 2ïAn attack tree is a hierarchical diagram of potential attacks against a system Chapter 12: Computer Programming 54
 1 Secure Software Development 2ïDefensive programming (also referred to as secure programming) is an approach to software development in which programmers anticipate what might go wrong as their programs run and take steps to smoothly handle those situations – Source code walkthroughs – Simplification – Filtering input Chapter 12: Computer Programming 55
1 Secure Software Development 2ïDefensive programming (also referred to as secure programming) is an approach to software development in which programmers anticipate what might go wrong as their programs run and take steps to smoothly handle those situations – Source code walkthroughs – Simplification – Filtering input Chapter 12: Computer Programming 55
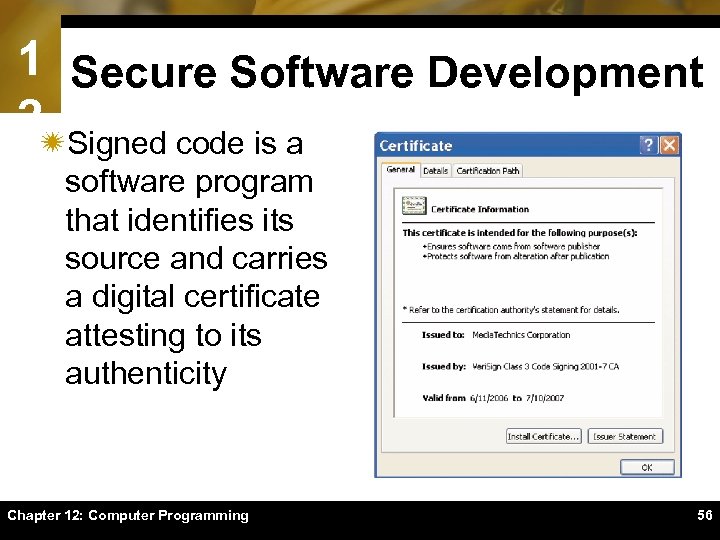 1 Secure Software Development 2ïSigned code is a software program that identifies its source and carries a digital certificate attesting to its authenticity Chapter 12: Computer Programming 56
1 Secure Software Development 2ïSigned code is a software program that identifies its source and carries a digital certificate attesting to its authenticity Chapter 12: Computer Programming 56
 1 Mitigation 2ïDespite defensive programming and other tactics to produce secure software, some defects inevitably remain undiscovered in products that end up in the consumers’ hands When bugs are discovered, the programmer’s remaining line of defense is to produce a bug fix, or patch Chapter 12: Computer Programming 57
1 Mitigation 2ïDespite defensive programming and other tactics to produce secure software, some defects inevitably remain undiscovered in products that end up in the consumers’ hands When bugs are discovered, the programmer’s remaining line of defense is to produce a bug fix, or patch Chapter 12: Computer Programming 57
 1 Mitigation 2ïTake the following steps to avoid security problems that stem from software defects – Select applications from software publishers with a good security track record – Watch for patches and apply them – Consider using open source software, which has been extensively reviewed by the programming community – Keep your firewall and antivirus software deployed and up-to-date Chapter 12: Computer Programming 58
1 Mitigation 2ïTake the following steps to avoid security problems that stem from software defects – Select applications from software publishers with a good security track record – Watch for patches and apply them – Consider using open source software, which has been extensively reviewed by the programming community – Keep your firewall and antivirus software deployed and up-to-date Chapter 12: Computer Programming 58
 Chapter 12 Complete Computer Programming
Chapter 12 Complete Computer Programming


