 Chapter 10: Cipher Techniques Slide #10 -1
Chapter 10: Cipher Techniques Slide #10 -1
 Overview Slide #10 -2
Overview Slide #10 -2
 Problems Slide #10 -3
Problems Slide #10 -3
 Attack #1: Precomputation Slide #10 -4
Attack #1: Precomputation Slide #10 -4
 Example Slide #10 -5
Example Slide #10 -5
 May Not Be Obvious Slide #10 -6
May Not Be Obvious Slide #10 -6
 Misordered Blocks Slide #10 -7
Misordered Blocks Slide #10 -7
 Notes Slide #10 -8
Notes Slide #10 -8
 Statistical Regularities Slide #10 -9
Statistical Regularities Slide #10 -9
 What These Mean Slide #10 -10
What These Mean Slide #10 -10
 Stream, Block Ciphers Slide #10 -11
Stream, Block Ciphers Slide #10 -11
 Examples Slide #10 -12
Examples Slide #10 -12
 Stream Ciphers Slide #10 -13
Stream Ciphers Slide #10 -13
 Synchronous Stream Ciphers Slide #10 -14
Synchronous Stream Ciphers Slide #10 -14
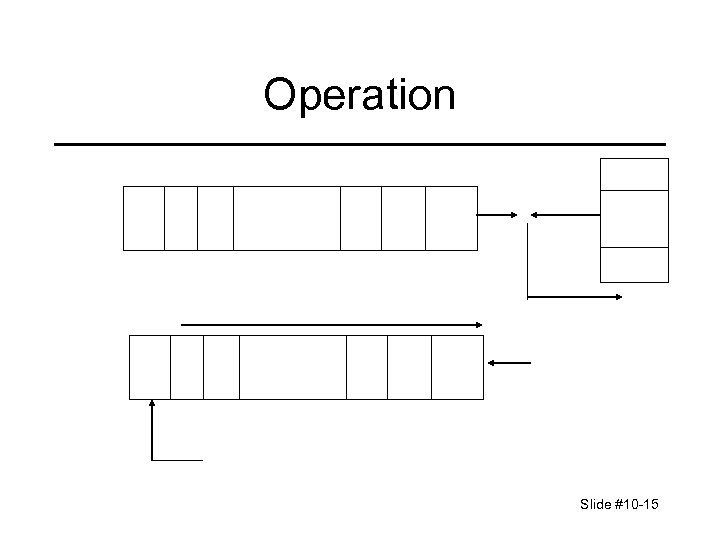 Operation Slide #10 -15
Operation Slide #10 -15
 Example Slide #10 -16
Example Slide #10 -16
 NLFSR Slide #10 -17
NLFSR Slide #10 -17
 Example Slide #10 -18
Example Slide #10 -18
 Eliminating Linearity Slide #10 -19
Eliminating Linearity Slide #10 -19
 Self-Synchronous Stream Cipher Slide #10 -20
Self-Synchronous Stream Cipher Slide #10 -20
 Another Example Slide #10 -21
Another Example Slide #10 -21
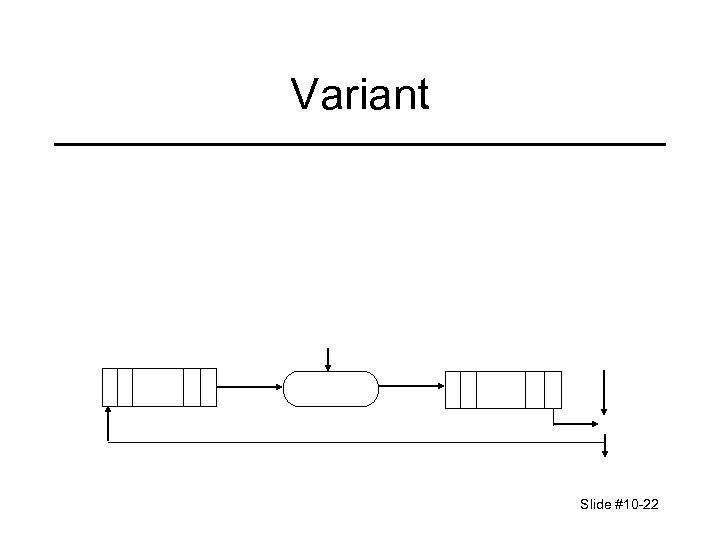 Variant Slide #10 -22
Variant Slide #10 -22
 Block Ciphers Slide #10 -23
Block Ciphers Slide #10 -23
 Solutions Slide #10 -24
Solutions Slide #10 -24
 Multiple Encryption Slide #10 -25
Multiple Encryption Slide #10 -25
 Networks and Cryptography Slide #10 -26
Networks and Cryptography Slide #10 -26
 Link and End-to-End Protocols Slide #10 -27
Link and End-to-End Protocols Slide #10 -27
 Encryption Slide #10 -28
Encryption Slide #10 -28
 Examples Slide #10 -29
Examples Slide #10 -29
 Cryptographic Considerations Slide #10 -30
Cryptographic Considerations Slide #10 -30
 Traffic Analysis Slide #10 -31
Traffic Analysis Slide #10 -31
 Example Protocols Slide #10 -32
Example Protocols Slide #10 -32
 Goals of PEM Slide #10 -33
Goals of PEM Slide #10 -33
 Message Handling System Slide #10 -34
Message Handling System Slide #10 -34
 Design Principles Slide #10 -35
Design Principles Slide #10 -35
 Basic Design: Keys Slide #10 -36
Basic Design: Keys Slide #10 -36
 Basic Design: Sending Slide #10 -37
Basic Design: Sending Slide #10 -37
 Basic Design: Integrity Slide #10 -38
Basic Design: Integrity Slide #10 -38
 Basic Design: Everything Slide #10 -39
Basic Design: Everything Slide #10 -39
 Practical Considerations Slide #10 -40
Practical Considerations Slide #10 -40
 Problem Slide #10 -41
Problem Slide #10 -41
 PEM vs. PGP Slide #10 -42
PEM vs. PGP Slide #10 -42
 IPsec Slide #10 -43
IPsec Slide #10 -43
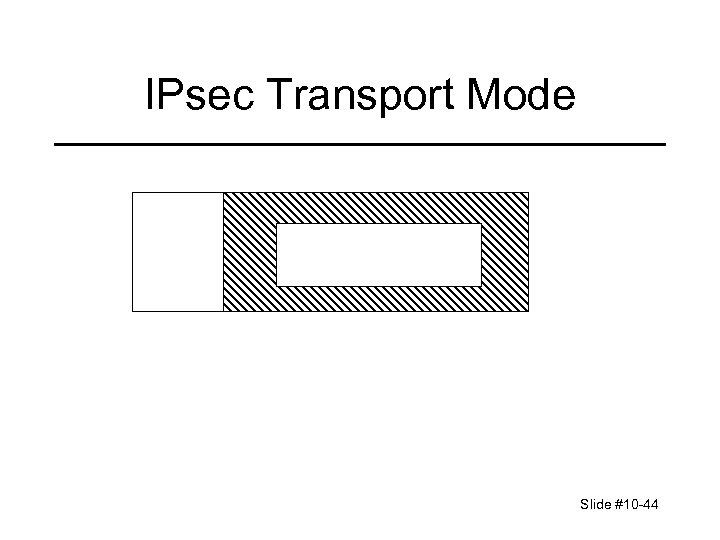 IPsec Transport Mode Slide #10 -44
IPsec Transport Mode Slide #10 -44
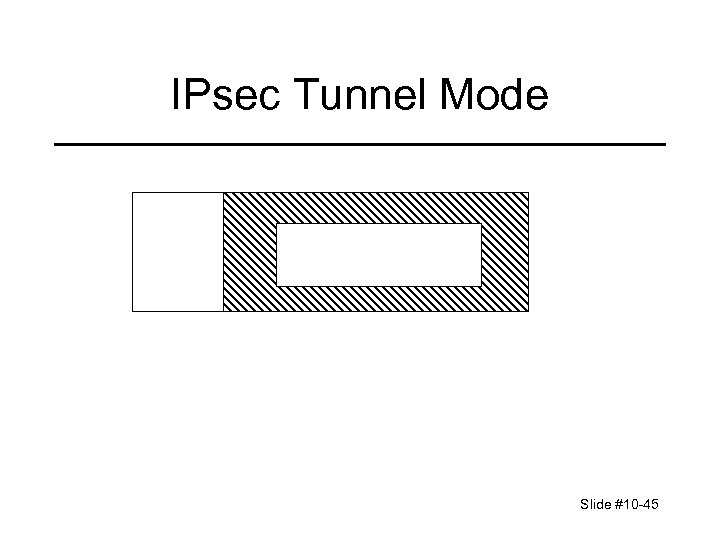 IPsec Tunnel Mode Slide #10 -45
IPsec Tunnel Mode Slide #10 -45
 IPsec Protocols Slide #10 -46
IPsec Protocols Slide #10 -46
 IPsec Architecture Slide #10 -47
IPsec Architecture Slide #10 -47
 Example Slide #10 -48
Example Slide #10 -48
 IPsec Architecture Slide #10 -49
IPsec Architecture Slide #10 -49
 SA Database (SAD) Slide #10 -50
SA Database (SAD) Slide #10 -50
 SAD Fields Slide #10 -51
SAD Fields Slide #10 -51
 IPsec Architecture Slide #10 -52
IPsec Architecture Slide #10 -52
 SA Bundles and Nesting Slide #10 -53
SA Bundles and Nesting Slide #10 -53
 Example: Nested Tunnels Slide #10 -54
Example: Nested Tunnels Slide #10 -54
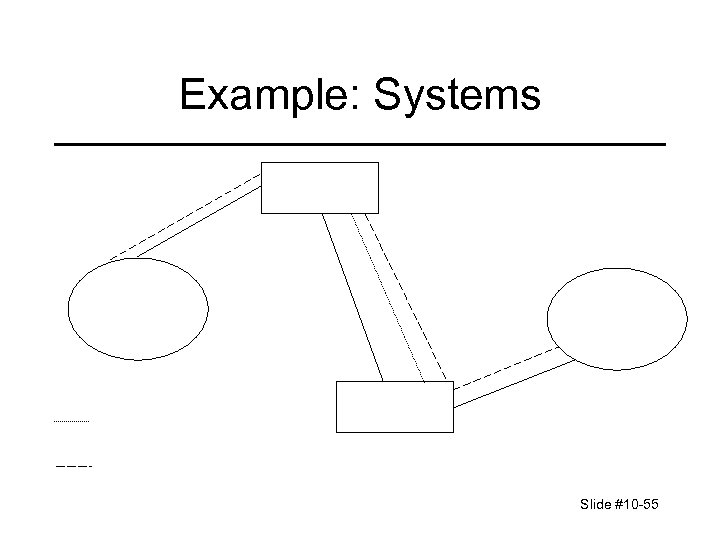 Example: Systems Slide #10 -55
Example: Systems Slide #10 -55
 Example: Packets Slide #10 -56
Example: Packets Slide #10 -56
 AH Protocol Slide #10 -57
AH Protocol Slide #10 -57
 Sender Slide #10 -58
Sender Slide #10 -58
 Recipient Slide #10 -59
Recipient Slide #10 -59
 Recipient, Using Antireplay Slide #10 -60
Recipient, Using Antireplay Slide #10 -60
 AH Miscellany Slide #10 -61
AH Miscellany Slide #10 -61
 ESP Protocol Slide #10 -62
ESP Protocol Slide #10 -62
 Sender Slide #10 -63
Sender Slide #10 -63
 Recipient Slide #10 -64
Recipient Slide #10 -64
 Recipient Slide #10 -65
Recipient Slide #10 -65
 ESP Miscellany Slide #10 -66
ESP Miscellany Slide #10 -66
 More ESP Miscellany Slide #10 -67
More ESP Miscellany Slide #10 -67
 Which to Use: PEM, IPsec Slide #10 -68
Which to Use: PEM, IPsec Slide #10 -68
 Key Points Slide #10 -69
Key Points Slide #10 -69