45b60080326645692e979c38a1202c56.ppt
- Количество слайдов: 50
 Ch. 7 Network Management CIS 187 Multilayer Switched Networks CCNP version 7 Rick Graziani Spring 2016
Ch. 7 Network Management CIS 187 Multilayer Switched Networks CCNP version 7 Rick Graziani Spring 2016
 Authentication, Authorization & Accounting l It is strongly recommended that network and administrative access security in the Cisco environment is based on a modular architecture that has three functional components: 1. authentication, 2. authorization 3. accounting also known as AAA l Using a Cisco AAA architecture enables consistent, systematic and scalable access security Rick Graziani graziani@cabrillo. edu 2
Authentication, Authorization & Accounting l It is strongly recommended that network and administrative access security in the Cisco environment is based on a modular architecture that has three functional components: 1. authentication, 2. authorization 3. accounting also known as AAA l Using a Cisco AAA architecture enables consistent, systematic and scalable access security Rick Graziani graziani@cabrillo. edu 2
 The Three Components of AAA l Authentication – “Who are you? ” Process of identifying a user before that user is allowed access to a protected resource. A user presents valid credentials, which are then compared with security information in a user database. In addition, authentication may offer other services depending on the security protocol selected, such as: an additional challenge and response, messaging support, or encryption. Rick Graziani graziani@cabrillo. edu 3
The Three Components of AAA l Authentication – “Who are you? ” Process of identifying a user before that user is allowed access to a protected resource. A user presents valid credentials, which are then compared with security information in a user database. In addition, authentication may offer other services depending on the security protocol selected, such as: an additional challenge and response, messaging support, or encryption. Rick Graziani graziani@cabrillo. edu 3
 The Three Components of AAA l Authorization – “What is this user allowed to do? ” After the user gains access to the network, authorization is performed. Control the level of access users have. Define which privileged EXEC commands are available to the user Control remote access (allowing the user to use protocols such as Point-to-Point Protocol [PPP] or Serial Line Internet Protocol [SLIP]). User capabilities are defined by a set of attribute-value (AV) pairs, which are associated with the user or the user’s group. These pairs may be stored locally on the device or on centralized TACACS+/RADIUS server(s). Rick Graziani graziani@cabrillo. edu 4
The Three Components of AAA l Authorization – “What is this user allowed to do? ” After the user gains access to the network, authorization is performed. Control the level of access users have. Define which privileged EXEC commands are available to the user Control remote access (allowing the user to use protocols such as Point-to-Point Protocol [PPP] or Serial Line Internet Protocol [SLIP]). User capabilities are defined by a set of attribute-value (AV) pairs, which are associated with the user or the user’s group. These pairs may be stored locally on the device or on centralized TACACS+/RADIUS server(s). Rick Graziani graziani@cabrillo. edu 4
 The Three Components of AAA l Accounting – “What have the users been doing on the network? ” Accounting is performed after authentication. Accounting enables you to collect information about the user activity and resource consumption. Log user logins Commands executed by the user, session durations, bytes transferred The network device sends this information in the form of attribute-value pairs to the accounting server. Therefore, user activity information from all devices in your network is located in one central place. l Authentication can be valid without authorization and accounting. l Authorization and accounting… l …however, cannot be performed without the authentication. Rick Graziani graziani@cabrillo. edu 5
The Three Components of AAA l Accounting – “What have the users been doing on the network? ” Accounting is performed after authentication. Accounting enables you to collect information about the user activity and resource consumption. Log user logins Commands executed by the user, session durations, bytes transferred The network device sends this information in the form of attribute-value pairs to the accounting server. Therefore, user activity information from all devices in your network is located in one central place. l Authentication can be valid without authorization and accounting. l Authorization and accounting… l …however, cannot be performed without the authentication. Rick Graziani graziani@cabrillo. edu 5
 Advantage to using AAA l Increased flexibility and control of access configuration: Beyond IOS passwords, AAA offers additional authorization flexibility on a per-command or per-interface level, which is unavailable with local credentials. l Scalability: Storing usernames and passwords in a local database on a device may be an appropriate solution for a small network with a small number of users. Larger networks, managing a large number of users on multiple devices becomes highly impractical and error-prone, with a lot of administrative burden. Single username by a number of network administrators results in the inability to track activities back to a single user. AAA model is the only solution that scales well. l Standardized authentication methods: AAA supports the RADIUS protocol, which is an industry open standard. l Multiple backup systems: You may specify multiple servers when configuring authentication options on the method list. In case of a server failure, the AAA engine on the device will continue to query the next server from the server group. 6
Advantage to using AAA l Increased flexibility and control of access configuration: Beyond IOS passwords, AAA offers additional authorization flexibility on a per-command or per-interface level, which is unavailable with local credentials. l Scalability: Storing usernames and passwords in a local database on a device may be an appropriate solution for a small network with a small number of users. Larger networks, managing a large number of users on multiple devices becomes highly impractical and error-prone, with a lot of administrative burden. Single username by a number of network administrators results in the inability to track activities back to a single user. AAA model is the only solution that scales well. l Standardized authentication methods: AAA supports the RADIUS protocol, which is an industry open standard. l Multiple backup systems: You may specify multiple servers when configuring authentication options on the method list. In case of a server failure, the AAA engine on the device will continue to query the next server from the server group. 6
 Authentication Options l Generally speaking, authentication is based on: Something the user knows (username and password) Something the user has (digital certificate issued by certification authority) Something the user is (biometrical scanners which can identify him by his fingerprint or eye retina) 7
Authentication Options l Generally speaking, authentication is based on: Something the user knows (username and password) Something the user has (digital certificate issued by certification authority) Something the user is (biometrical scanners which can identify him by his fingerprint or eye retina) 7
 Authentication Options l The authentication database may be stored either locally on a network device or on a centralized server. l It is best practice to have multiple methods of authentication in case the primary authentication is down or unreachable. l If the primary is down and no backup authentication method exists, you cannot access the network device in question. 8
Authentication Options l The authentication database may be stored either locally on a network device or on a centralized server. l It is best practice to have multiple methods of authentication in case the primary authentication is down or unreachable. l If the primary is down and no backup authentication method exists, you cannot access the network device in question. 8
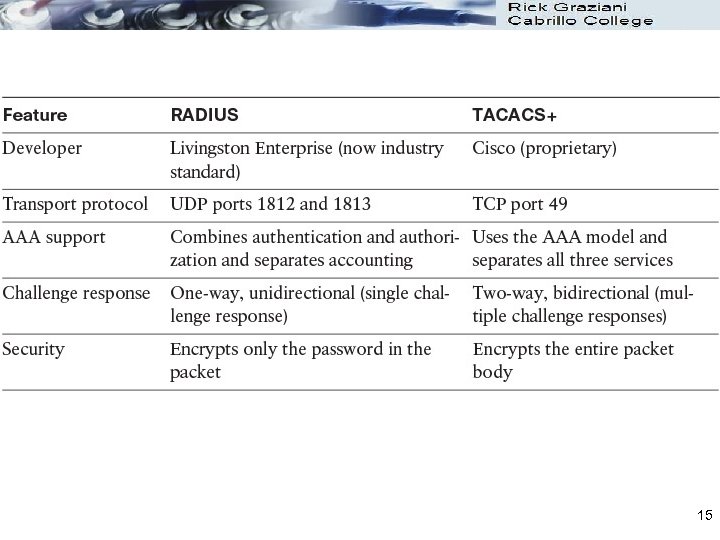
 AAA Protocols: RADIUS and TACACS+ l The best-known and best-used types of AAA protocols are TACACS+ RADIUS l TACACS+ and RADIUS have different features that make them suitable for different situations l RADIUS is maintained by a standard that was created by the IETF l TACACS+ is a proprietary Cisco Systems technology that encrypts data l Protocol: TACACS+ runs over TCP RADIUS runs over UDP l TACACS+ can control the authorization level of users; RADIUS cannot. Because TACACS+ separates authentication and authorization, it is possible to use TACACS+ for authorization and accounting, while using a different method for authentication, such as Kerberos. Rick Graziani graziani@cabrillo. edu 9
AAA Protocols: RADIUS and TACACS+ l The best-known and best-used types of AAA protocols are TACACS+ RADIUS l TACACS+ and RADIUS have different features that make them suitable for different situations l RADIUS is maintained by a standard that was created by the IETF l TACACS+ is a proprietary Cisco Systems technology that encrypts data l Protocol: TACACS+ runs over TCP RADIUS runs over UDP l TACACS+ can control the authorization level of users; RADIUS cannot. Because TACACS+ separates authentication and authorization, it is possible to use TACACS+ for authorization and accounting, while using a different method for authentication, such as Kerberos. Rick Graziani graziani@cabrillo. edu 9
 RADIUS Features l Radius is an IETF standard protocol - RFC 2865 l Uses UDP on standard port numbers (1812 and 1813; CSACS uses 1645 and 1646 by default) Rick Graziani graziani@cabrillo. edu 10
RADIUS Features l Radius is an IETF standard protocol - RFC 2865 l Uses UDP on standard port numbers (1812 and 1813; CSACS uses 1645 and 1646 by default) Rick Graziani graziani@cabrillo. edu 10
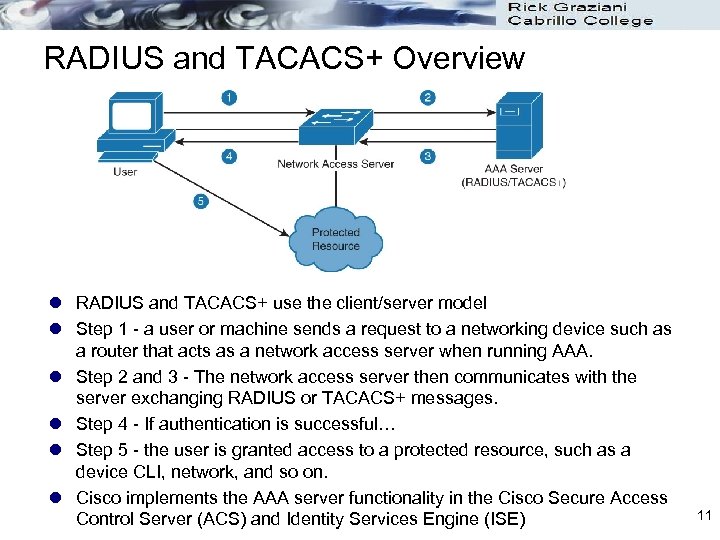 RADIUS and TACACS+ Overview l RADIUS and TACACS+ use the client/server model l Step 1 - a user or machine sends a request to a networking device such as a router that acts as a network access server when running AAA. l Step 2 and 3 - The network access server then communicates with the server exchanging RADIUS or TACACS+ messages. l Step 4 - If authentication is successful… l Step 5 - the user is granted access to a protected resource, such as a device CLI, network, and so on. l Cisco implements the AAA server functionality in the Cisco Secure Access Control Server (ACS) and Identity Services Engine (ISE) 11
RADIUS and TACACS+ Overview l RADIUS and TACACS+ use the client/server model l Step 1 - a user or machine sends a request to a networking device such as a router that acts as a network access server when running AAA. l Step 2 and 3 - The network access server then communicates with the server exchanging RADIUS or TACACS+ messages. l Step 4 - If authentication is successful… l Step 5 - the user is granted access to a protected resource, such as a device CLI, network, and so on. l Cisco implements the AAA server functionality in the Cisco Secure Access Control Server (ACS) and Identity Services Engine (ISE) 11
 TACACS+ Attributes and Features l The TACACS+ protocol is much more flexible than the RADIUS communication. l TACACS+ uses TCP on well-known port number 49 l TACACS+ establishes a dedicated TCP session for every AAA action l Cisco Secure ACS can use one persistent TCP session for all actions Rick Graziani graziani@cabrillo. edu 12
TACACS+ Attributes and Features l The TACACS+ protocol is much more flexible than the RADIUS communication. l TACACS+ uses TCP on well-known port number 49 l TACACS+ establishes a dedicated TCP session for every AAA action l Cisco Secure ACS can use one persistent TCP session for all actions Rick Graziani graziani@cabrillo. edu 12
 15
15
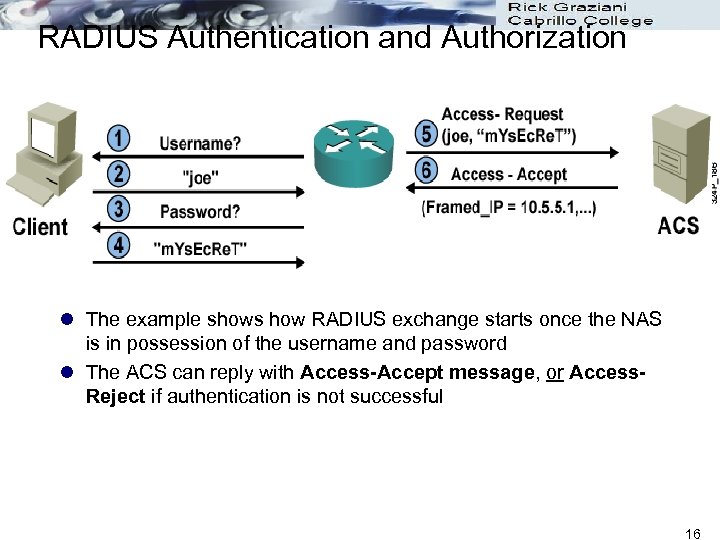 RADIUS Authentication and Authorization l The example shows how RADIUS exchange starts once the NAS is in possession of the username and password l The ACS can reply with Access-Accept message, or Access. Reject if authentication is not successful 16
RADIUS Authentication and Authorization l The example shows how RADIUS exchange starts once the NAS is in possession of the username and password l The ACS can reply with Access-Accept message, or Access. Reject if authentication is not successful 16
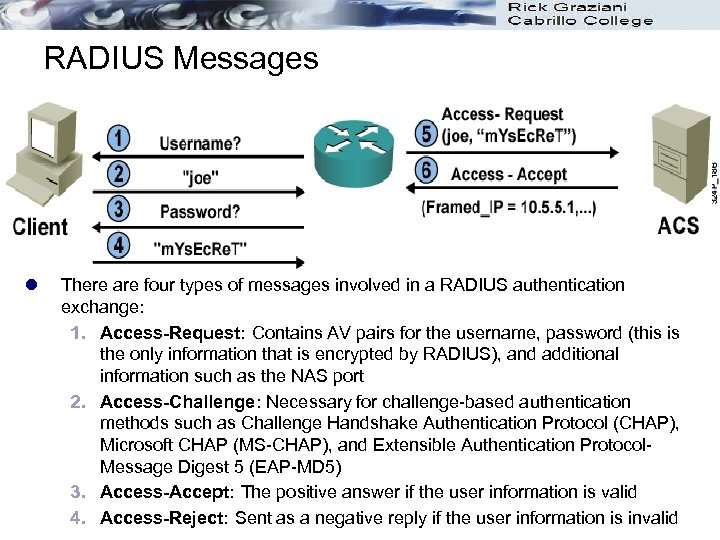 RADIUS Messages l There are four types of messages involved in a RADIUS authentication exchange: 1. Access-Request: Contains AV pairs for the username, password (this is the only information that is encrypted by RADIUS), and additional information such as the NAS port 2. Access-Challenge: Necessary for challenge-based authentication methods such as Challenge Handshake Authentication Protocol (CHAP), Microsoft CHAP (MS-CHAP), and Extensible Authentication Protocol. Message Digest 5 (EAP-MD 5) 3. Access-Accept: The positive answer if the user information is valid 4. Access-Reject: Sent as a negative reply if the user information is invalid
RADIUS Messages l There are four types of messages involved in a RADIUS authentication exchange: 1. Access-Request: Contains AV pairs for the username, password (this is the only information that is encrypted by RADIUS), and additional information such as the NAS port 2. Access-Challenge: Necessary for challenge-based authentication methods such as Challenge Handshake Authentication Protocol (CHAP), Microsoft CHAP (MS-CHAP), and Extensible Authentication Protocol. Message Digest 5 (EAP-MD 5) 3. Access-Accept: The positive answer if the user information is valid 4. Access-Reject: Sent as a negative reply if the user information is invalid
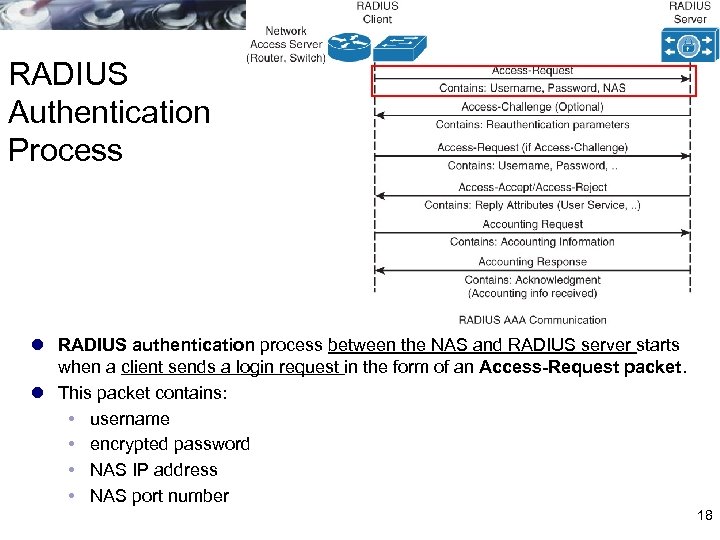 RADIUS Authentication Process l RADIUS authentication process between the NAS and RADIUS server starts when a client sends a login request in the form of an Access-Request packet. l This packet contains: username encrypted password NAS IP address NAS port number 18
RADIUS Authentication Process l RADIUS authentication process between the NAS and RADIUS server starts when a client sends a login request in the form of an Access-Request packet. l This packet contains: username encrypted password NAS IP address NAS port number 18
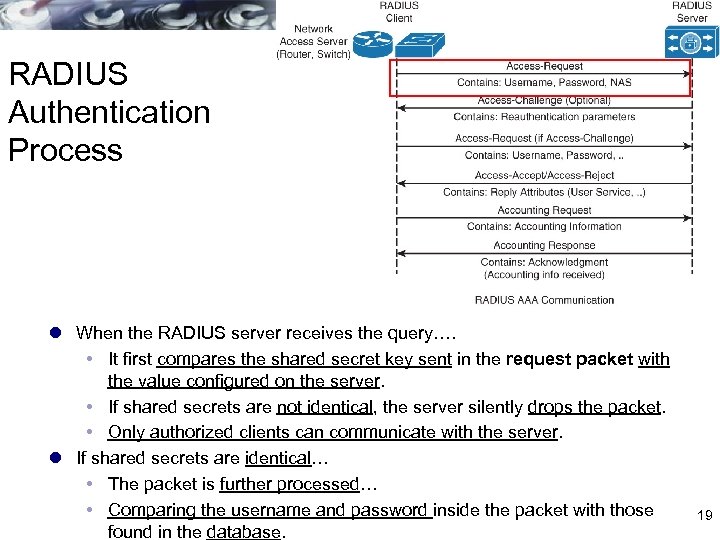 RADIUS Authentication Process l When the RADIUS server receives the query…. It first compares the shared secret key sent in the request packet with the value configured on the server. If shared secrets are not identical, the server silently drops the packet. Only authorized clients can communicate with the server. l If shared secrets are identical… The packet is further processed… Comparing the username and password inside the packet with those found in the database. 19
RADIUS Authentication Process l When the RADIUS server receives the query…. It first compares the shared secret key sent in the request packet with the value configured on the server. If shared secrets are not identical, the server silently drops the packet. Only authorized clients can communicate with the server. l If shared secrets are identical… The packet is further processed… Comparing the username and password inside the packet with those found in the database. 19
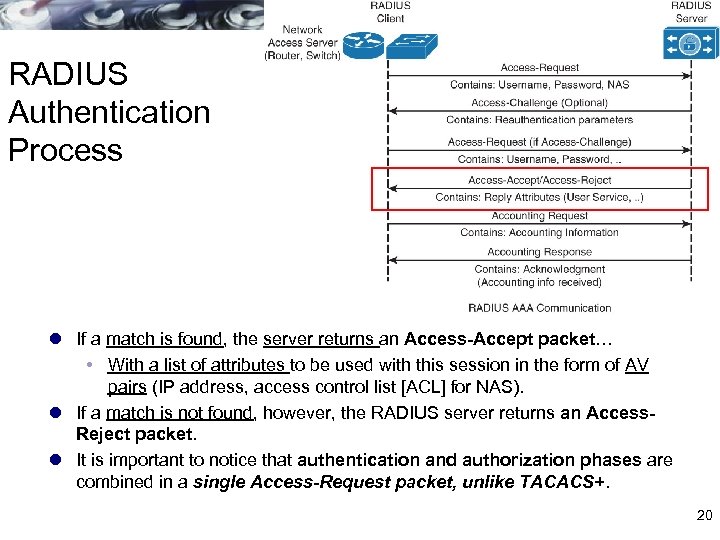 RADIUS Authentication Process l If a match is found, the server returns an Access-Accept packet… With a list of attributes to be used with this session in the form of AV pairs (IP address, access control list [ACL] for NAS). l If a match is not found, however, the RADIUS server returns an Access. Reject packet. l It is important to notice that authentication and authorization phases are combined in a single Access-Request packet, unlike TACACS+. 20
RADIUS Authentication Process l If a match is found, the server returns an Access-Accept packet… With a list of attributes to be used with this session in the form of AV pairs (IP address, access control list [ACL] for NAS). l If a match is not found, however, the RADIUS server returns an Access. Reject packet. l It is important to notice that authentication and authorization phases are combined in a single Access-Request packet, unlike TACACS+. 20
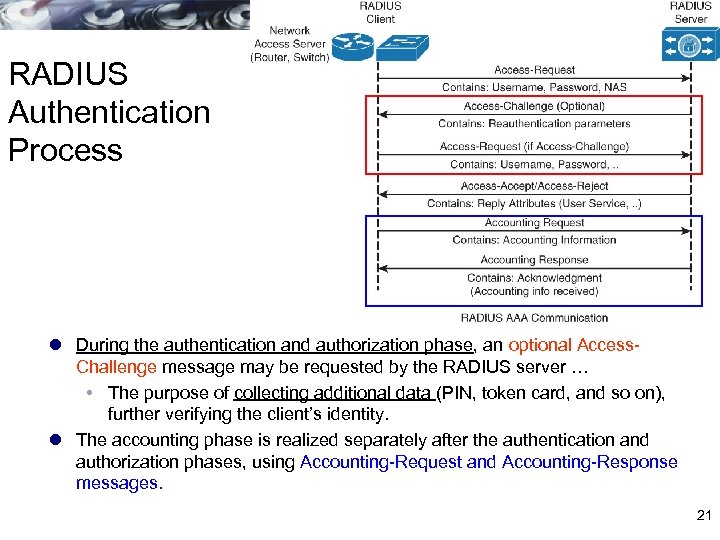 RADIUS Authentication Process l During the authentication and authorization phase, an optional Access. Challenge message may be requested by the RADIUS server … The purpose of collecting additional data (PIN, token card, and so on), further verifying the client’s identity. l The accounting phase is realized separately after the authentication and authorization phases, using Accounting-Request and Accounting-Response messages. 21
RADIUS Authentication Process l During the authentication and authorization phase, an optional Access. Challenge message may be requested by the RADIUS server … The purpose of collecting additional data (PIN, token card, and so on), further verifying the client’s identity. l The accounting phase is realized separately after the authentication and authorization phases, using Accounting-Request and Accounting-Response messages. 21
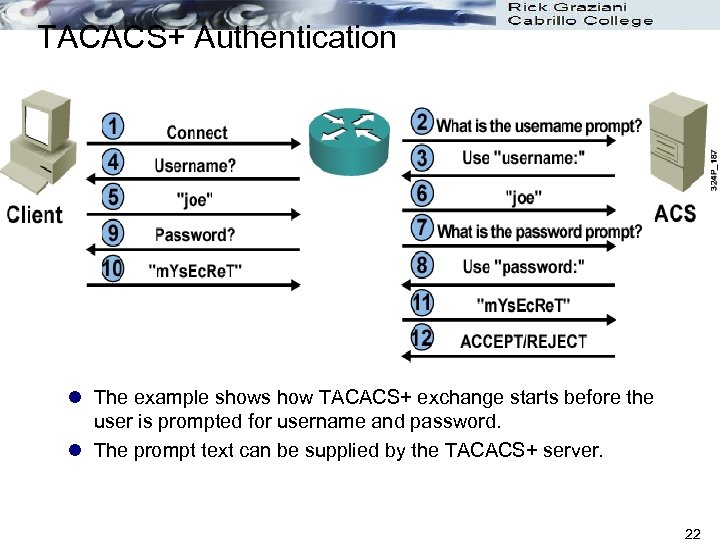 TACACS+ Authentication l The example shows how TACACS+ exchange starts before the user is prompted for username and password. l The prompt text can be supplied by the TACACS+ server. 22
TACACS+ Authentication l The example shows how TACACS+ exchange starts before the user is prompted for username and password. l The prompt text can be supplied by the TACACS+ server. 22
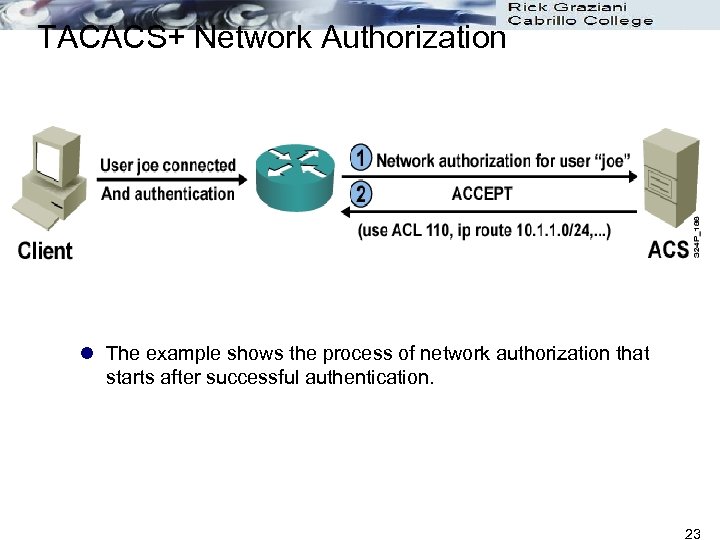 TACACS+ Network Authorization l The example shows the process of network authorization that starts after successful authentication. 23
TACACS+ Network Authorization l The example shows the process of network authorization that starts after successful authentication. 23
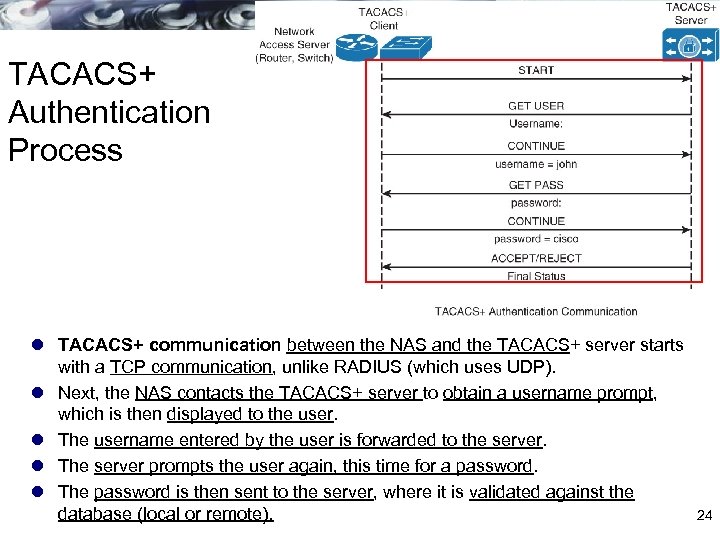 TACACS+ Authentication Process l TACACS+ communication between the NAS and the TACACS+ server starts with a TCP communication, unlike RADIUS (which uses UDP). l Next, the NAS contacts the TACACS+ server to obtain a username prompt, which is then displayed to the user. l The username entered by the user is forwarded to the server. l The server prompts the user again, this time for a password. l The password is then sent to the server, where it is validated against the database (local or remote). 24
TACACS+ Authentication Process l TACACS+ communication between the NAS and the TACACS+ server starts with a TCP communication, unlike RADIUS (which uses UDP). l Next, the NAS contacts the TACACS+ server to obtain a username prompt, which is then displayed to the user. l The username entered by the user is forwarded to the server. l The server prompts the user again, this time for a password. l The password is then sent to the server, where it is validated against the database (local or remote). 24
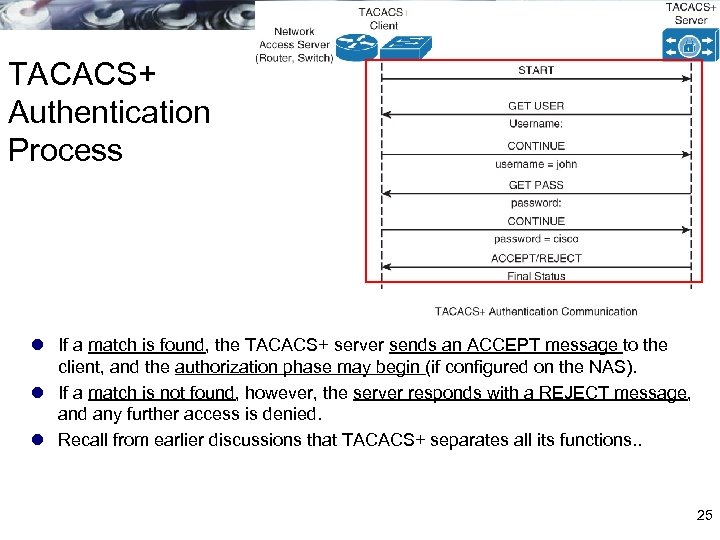 TACACS+ Authentication Process l If a match is found, the TACACS+ server sends an ACCEPT message to the client, and the authorization phase may begin (if configured on the NAS). l If a match is not found, however, the server responds with a REJECT message, and any further access is denied. l Recall from earlier discussions that TACACS+ separates all its functions. . 25
TACACS+ Authentication Process l If a match is found, the TACACS+ server sends an ACCEPT message to the client, and the authorization phase may begin (if configured on the NAS). l If a match is not found, however, the server responds with a REJECT message, and any further access is denied. l Recall from earlier discussions that TACACS+ separates all its functions. . 25
 Configuring AAA Switch(config)# aaa new-model Switch(config)# username User 123 secret Secretpwd • • • Globally enable AAA to allow the use of all AAA elements. This step is a prerequisite for all other AAA commands. AAA supports a variety of authentication options. For example, you can use external authentication servers such as RADIUS or TACACS+, or you may specify a local database. Despite these options, it is best practice to configure a local username, to serve as a backup, should all external servers fail. NOTE: The aaa new-model command immediately applies local authentication to all lines and interfaces (except console line con 0). To avoid being locked out of the router, it is a best practice to define a local username and password before starting the AAA configuration. 26
Configuring AAA Switch(config)# aaa new-model Switch(config)# username User 123 secret Secretpwd • • • Globally enable AAA to allow the use of all AAA elements. This step is a prerequisite for all other AAA commands. AAA supports a variety of authentication options. For example, you can use external authentication servers such as RADIUS or TACACS+, or you may specify a local database. Despite these options, it is best practice to configure a local username, to serve as a backup, should all external servers fail. NOTE: The aaa new-model command immediately applies local authentication to all lines and interfaces (except console line con 0). To avoid being locked out of the router, it is a best practice to define a local username and password before starting the AAA configuration. 26
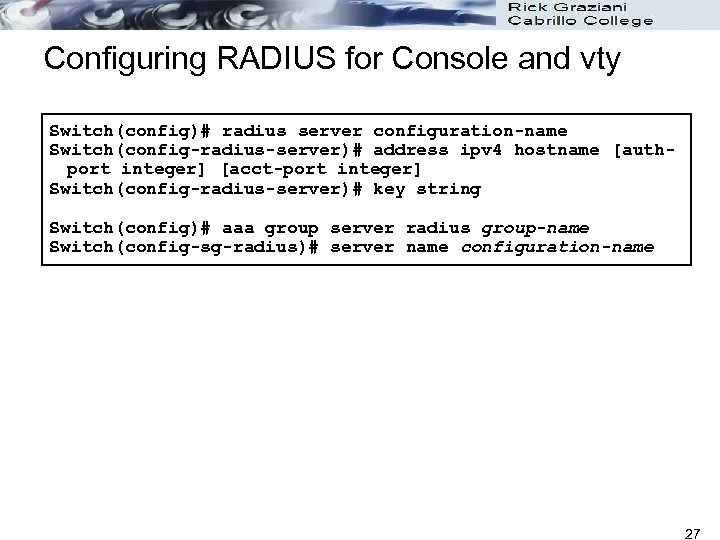 Configuring RADIUS for Console and vty Switch(config)# radius server configuration-name Switch(config-radius-server)# address ipv 4 hostname [authport integer] [acct-port integer] Switch(config-radius-server)# key string Switch(config)# aaa group server radius group-name Switch(config-sg-radius)# server name configuration-name 27
Configuring RADIUS for Console and vty Switch(config)# radius server configuration-name Switch(config-radius-server)# address ipv 4 hostname [authport integer] [acct-port integer] Switch(config-radius-server)# key string Switch(config)# aaa group server radius group-name Switch(config-sg-radius)# server name configuration-name 27
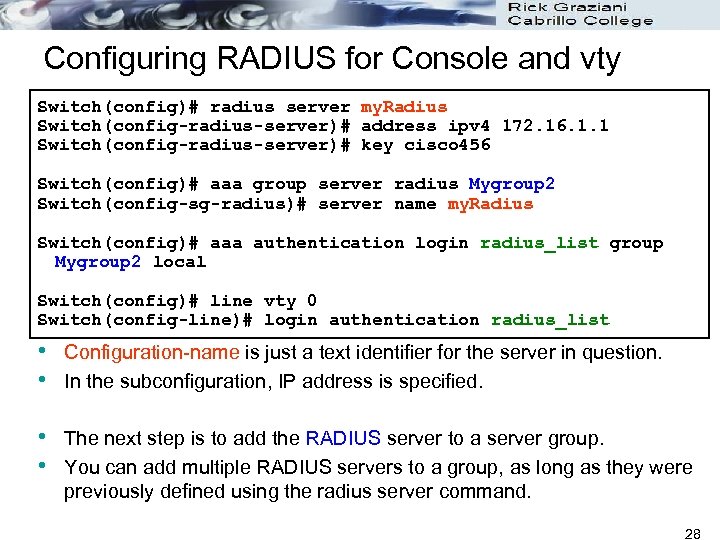 Configuring RADIUS for Console and vty Switch(config)# radius server my. Radius Switch(config-radius-server)# address ipv 4 172. 16. 1. 1 Switch(config-radius-server)# key cisco 456 Switch(config)# aaa group server radius Mygroup 2 Switch(config-sg-radius)# server name my. Radius Switch(config)# aaa authentication login radius_list group Mygroup 2 local Switch(config)# line vty 0 Switch(config-line)# login authentication radius_list • • Configuration-name is just a text identifier for the server in question. In the subconfiguration, IP address is specified. • • The next step is to add the RADIUS server to a server group. You can add multiple RADIUS servers to a group, as long as they were previously defined using the radius server command. 28
Configuring RADIUS for Console and vty Switch(config)# radius server my. Radius Switch(config-radius-server)# address ipv 4 172. 16. 1. 1 Switch(config-radius-server)# key cisco 456 Switch(config)# aaa group server radius Mygroup 2 Switch(config-sg-radius)# server name my. Radius Switch(config)# aaa authentication login radius_list group Mygroup 2 local Switch(config)# line vty 0 Switch(config-line)# login authentication radius_list • • Configuration-name is just a text identifier for the server in question. In the subconfiguration, IP address is specified. • • The next step is to add the RADIUS server to a server group. You can add multiple RADIUS servers to a group, as long as they were previously defined using the radius server command. 28
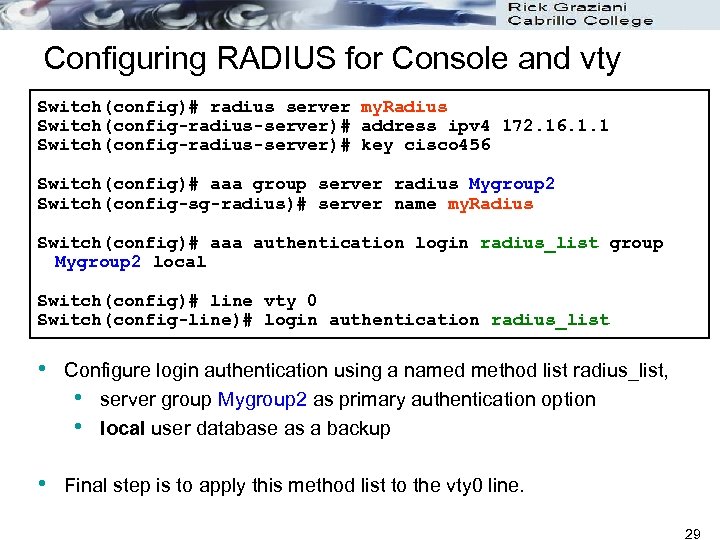 Configuring RADIUS for Console and vty Switch(config)# radius server my. Radius Switch(config-radius-server)# address ipv 4 172. 16. 1. 1 Switch(config-radius-server)# key cisco 456 Switch(config)# aaa group server radius Mygroup 2 Switch(config-sg-radius)# server name my. Radius Switch(config)# aaa authentication login radius_list group Mygroup 2 local Switch(config)# line vty 0 Switch(config-line)# login authentication radius_list • Configure login authentication using a named method list radius_list, • server group Mygroup 2 as primary authentication option • local user database as a backup • Final step is to apply this method list to the vty 0 line. 29
Configuring RADIUS for Console and vty Switch(config)# radius server my. Radius Switch(config-radius-server)# address ipv 4 172. 16. 1. 1 Switch(config-radius-server)# key cisco 456 Switch(config)# aaa group server radius Mygroup 2 Switch(config-sg-radius)# server name my. Radius Switch(config)# aaa authentication login radius_list group Mygroup 2 local Switch(config)# line vty 0 Switch(config-line)# login authentication radius_list • Configure login authentication using a named method list radius_list, • server group Mygroup 2 as primary authentication option • local user database as a backup • Final step is to apply this method list to the vty 0 line. 29
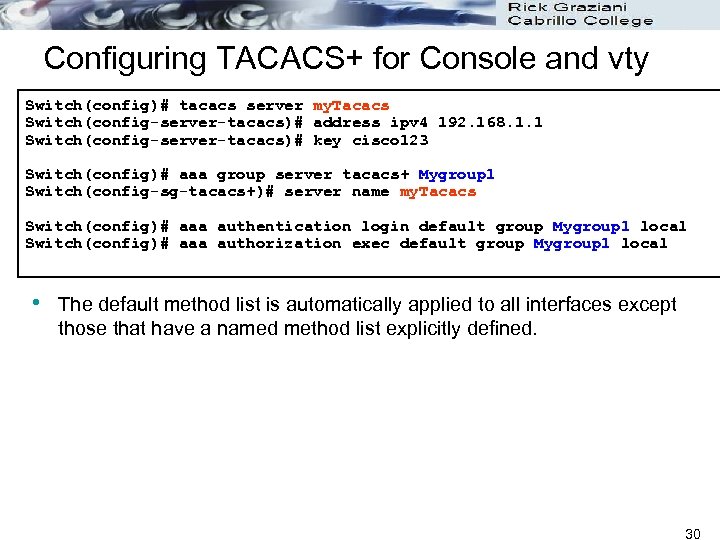 Configuring TACACS+ for Console and vty Switch(config)# tacacs server my. Tacacs Switch(config-server-tacacs)# address ipv 4 192. 168. 1. 1 Switch(config-server-tacacs)# key cisco 123 Switch(config)# aaa group server tacacs+ Mygroup 1 Switch(config-sg-tacacs+)# server name my. Tacacs Switch(config)# aaa authentication login default group Mygroup 1 local Switch(config)# aaa authorization exec default group Mygroup 1 local • The default method list is automatically applied to all interfaces except those that have a named method list explicitly defined. 30
Configuring TACACS+ for Console and vty Switch(config)# tacacs server my. Tacacs Switch(config-server-tacacs)# address ipv 4 192. 168. 1. 1 Switch(config-server-tacacs)# key cisco 123 Switch(config)# aaa group server tacacs+ Mygroup 1 Switch(config-sg-tacacs+)# server name my. Tacacs Switch(config)# aaa authentication login default group Mygroup 1 local Switch(config)# aaa authorization exec default group Mygroup 1 local • The default method list is automatically applied to all interfaces except those that have a named method list explicitly defined. 30
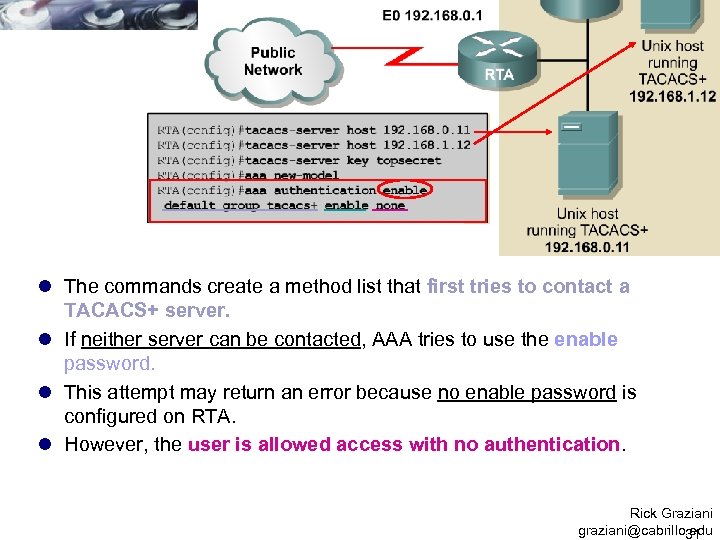 l The commands create a method list that first tries to contact a TACACS+ server. l If neither server can be contacted, AAA tries to use the enable password. l This attempt may return an error because no enable password is configured on RTA. l However, the user is allowed access with no authentication. Rick Graziani graziani@cabrillo. edu 31
l The commands create a method list that first tries to contact a TACACS+ server. l If neither server can be contacted, AAA tries to use the enable password. l This attempt may return an error because no enable password is configured on RTA. l However, the user is allowed access with no authentication. Rick Graziani graziani@cabrillo. edu 31
 AAA Authorization Switch(config)# aaa authorization-type list-name methodlist Switch(config)# line-type line-number Switch(config)# authorization {arap | commands level | exec | reverseaccess} list-name l AAA authorization goes beyond authentication to control what actions, commands, and so on a user is allowed to perform. l Step 1. Define a named list of authorization methods. l Step 2. Apply that list to one or more interfaces (except for the default method list). l Step 3. The first listed method is used. If it fails to respond, the second one is used, and so on until all listed methods are exhausted. Once the method list is exhausted, a failure message is logged. 32
AAA Authorization Switch(config)# aaa authorization-type list-name methodlist Switch(config)# line-type line-number Switch(config)# authorization {arap | commands level | exec | reverseaccess} list-name l AAA authorization goes beyond authentication to control what actions, commands, and so on a user is allowed to perform. l Step 1. Define a named list of authorization methods. l Step 2. Apply that list to one or more interfaces (except for the default method list). l Step 3. The first listed method is used. If it fails to respond, the second one is used, and so on until all listed methods are exhausted. Once the method list is exhausted, a failure message is logged. 32
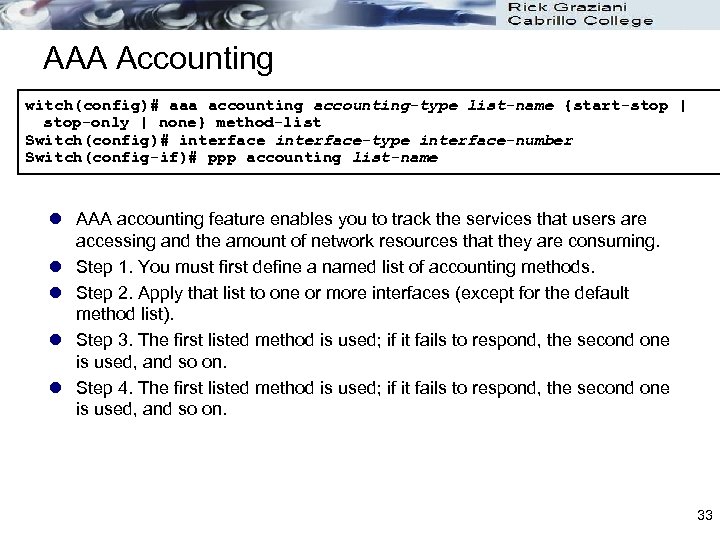 AAA Accounting witch(config)# aaa accounting-type list-name {start-stop | stop-only | none} method-list Switch(config)# interface-type interface-number Switch(config-if)# ppp accounting list-name l AAA accounting feature enables you to track the services that users are accessing and the amount of network resources that they are consuming. l Step 1. You must first define a named list of accounting methods. l Step 2. Apply that list to one or more interfaces (except for the default method list). l Step 3. The first listed method is used; if it fails to respond, the second one is used, and so on. l Step 4. The first listed method is used; if it fails to respond, the second one is used, and so on. 33
AAA Accounting witch(config)# aaa accounting-type list-name {start-stop | stop-only | none} method-list Switch(config)# interface-type interface-number Switch(config-if)# ppp accounting list-name l AAA accounting feature enables you to track the services that users are accessing and the amount of network resources that they are consuming. l Step 1. You must first define a named list of accounting methods. l Step 2. Apply that list to one or more interfaces (except for the default method list). l Step 3. The first listed method is used; if it fails to respond, the second one is used, and so on. l Step 4. The first listed method is used; if it fails to respond, the second one is used, and so on. 33
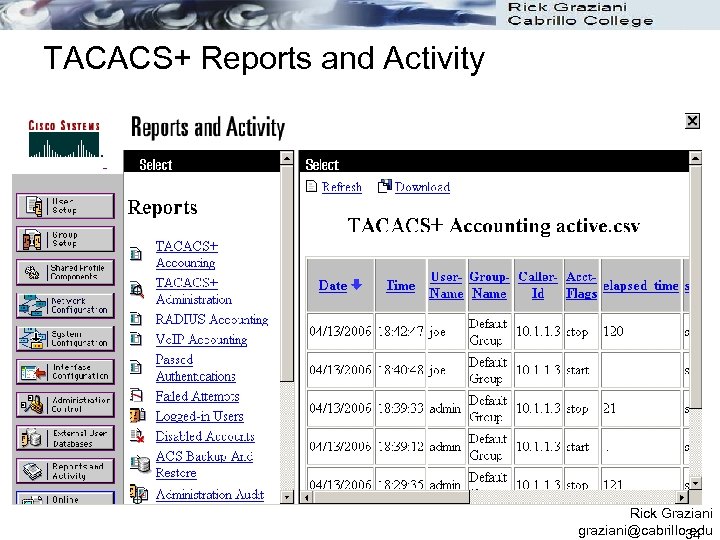 TACACS+ Reports and Activity Rick Graziani graziani@cabrillo. edu 34
TACACS+ Reports and Activity Rick Graziani graziani@cabrillo. edu 34
 Configuring AAA authorization
Configuring AAA authorization
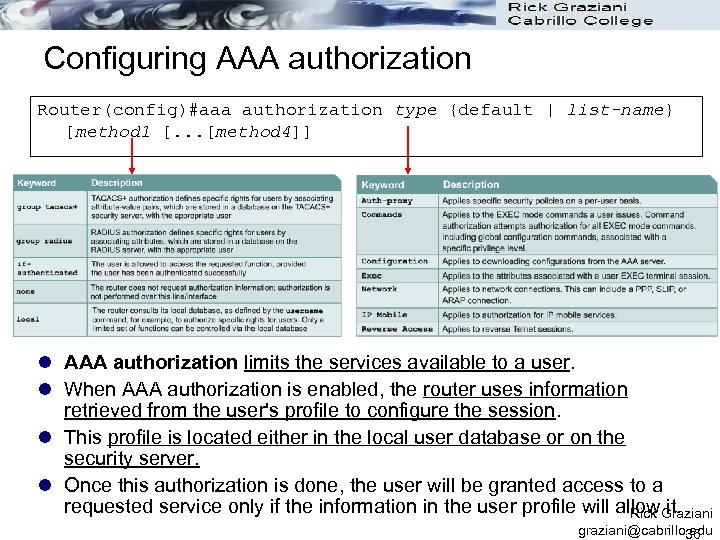 Configuring AAA authorization Router(config)#aaa authorization type {default | list-name} [method 1 [. . . [method 4]] l AAA authorization limits the services available to a user. l When AAA authorization is enabled, the router uses information retrieved from the user's profile to configure the session. l This profile is located either in the local user database or on the security server. l Once this authorization is done, the user will be granted access to a requested service only if the information in the user profile will allow. Graziani Rick it. graziani@cabrillo. edu 36
Configuring AAA authorization Router(config)#aaa authorization type {default | list-name} [method 1 [. . . [method 4]] l AAA authorization limits the services available to a user. l When AAA authorization is enabled, the router uses information retrieved from the user's profile to configure the session. l This profile is located either in the local user database or on the security server. l Once this authorization is done, the user will be granted access to a requested service only if the information in the user profile will allow. Graziani Rick it. graziani@cabrillo. edu 36
 Configuring AAA authorization Rick Graziani graziani@cabrillo. edu 37
Configuring AAA authorization Rick Graziani graziani@cabrillo. edu 37
 Configuring AAA authorization l Before AAA authorization can be configured, the following tasks must be performed: Enable AAA using the aaa new-model command. Configure AAA authentication. Authorization generally takes place after authentication and it relies on authentication to work properly. Configure the router as a TACACS+ or a RADIUS client, if necessary. Configure the local username/password database, if necessary. Use the username command to define the rights associated with specific use Rick Graziani graziani@cabrillo. edu 38
Configuring AAA authorization l Before AAA authorization can be configured, the following tasks must be performed: Enable AAA using the aaa new-model command. Configure AAA authentication. Authorization generally takes place after authentication and it relies on authentication to work properly. Configure the router as a TACACS+ or a RADIUS client, if necessary. Configure the local username/password database, if necessary. Use the username command to define the rights associated with specific use Rick Graziani graziani@cabrillo. edu 38
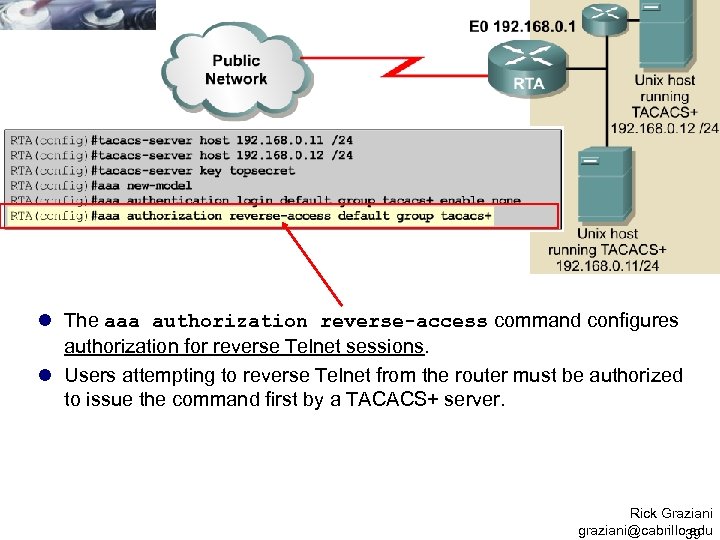 l The aaa authorization reverse-access command configures authorization for reverse Telnet sessions. l Users attempting to reverse Telnet from the router must be authorized to issue the command first by a TACACS+ server. Rick Graziani graziani@cabrillo. edu 39
l The aaa authorization reverse-access command configures authorization for reverse Telnet sessions. l Users attempting to reverse Telnet from the router must be authorized to issue the command first by a TACACS+ server. Rick Graziani graziani@cabrillo. edu 39
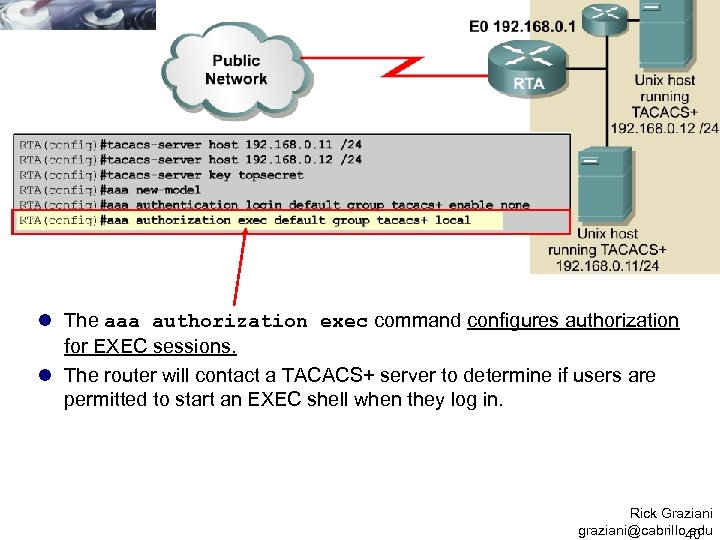 l The aaa authorization exec command configures authorization for EXEC sessions. l The router will contact a TACACS+ server to determine if users are permitted to start an EXEC shell when they log in. Rick Graziani graziani@cabrillo. edu 40
l The aaa authorization exec command configures authorization for EXEC sessions. l The router will contact a TACACS+ server to determine if users are permitted to start an EXEC shell when they log in. Rick Graziani graziani@cabrillo. edu 40
 IOS command privilege levels l The aaa authorization command can also be used to control exactly which commands a user is allowed to enter on the router. l Users can only enter commands at or beneath their privilege level. l All IOS router commands are assigned a privilege level from 0 to 15. There are three privilege levels on the router by default. l Routers use privilege levels even when AAA is not configured. l When a user opens an EXEC session using the console or a VTY, the user can issue any command in privilege level 1 and/or privilege level 0 by default. privilege level 1 – user mode privilege level 15 – priviledged (enable) mode l Once the user authenticates using the enable command enable password, that user has privilege level 15. Rick Graziani graziani@cabrillo. edu 41
IOS command privilege levels l The aaa authorization command can also be used to control exactly which commands a user is allowed to enter on the router. l Users can only enter commands at or beneath their privilege level. l All IOS router commands are assigned a privilege level from 0 to 15. There are three privilege levels on the router by default. l Routers use privilege levels even when AAA is not configured. l When a user opens an EXEC session using the console or a VTY, the user can issue any command in privilege level 1 and/or privilege level 0 by default. privilege level 1 – user mode privilege level 15 – priviledged (enable) mode l Once the user authenticates using the enable command enable password, that user has privilege level 15. Rick Graziani graziani@cabrillo. edu 41
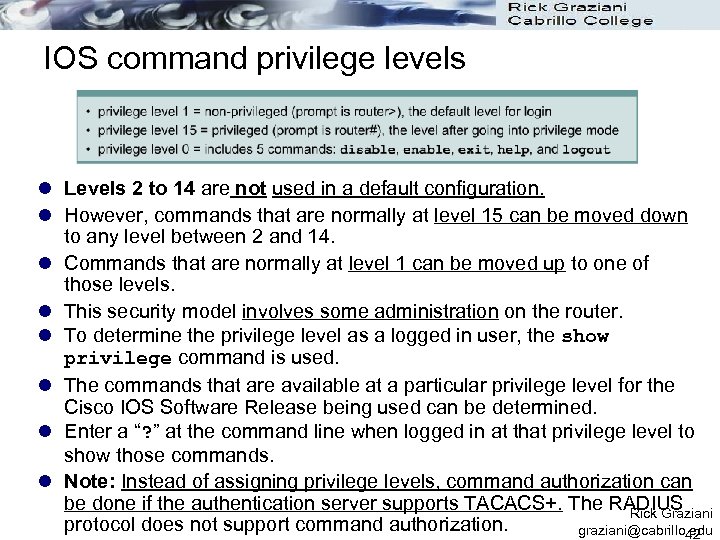 IOS command privilege levels l Levels 2 to 14 are not used in a default configuration. l However, commands that are normally at level 15 can be moved down to any level between 2 and 14. l Commands that are normally at level 1 can be moved up to one of those levels. l This security model involves some administration on the router. l To determine the privilege level as a logged in user, the show privilege command is used. l The commands that are available at a particular privilege level for the Cisco IOS Software Release being used can be determined. l Enter a “? ” at the command line when logged in at that privilege level to show those commands. l Note: Instead of assigning privilege levels, command authorization can be done if the authentication server supports TACACS+. The RADIUS Rick Graziani protocol does not support command authorization. graziani@cabrillo. edu 42
IOS command privilege levels l Levels 2 to 14 are not used in a default configuration. l However, commands that are normally at level 15 can be moved down to any level between 2 and 14. l Commands that are normally at level 1 can be moved up to one of those levels. l This security model involves some administration on the router. l To determine the privilege level as a logged in user, the show privilege command is used. l The commands that are available at a particular privilege level for the Cisco IOS Software Release being used can be determined. l Enter a “? ” at the command line when logged in at that privilege level to show those commands. l Note: Instead of assigning privilege levels, command authorization can be done if the authentication server supports TACACS+. The RADIUS Rick Graziani protocol does not support command authorization. graziani@cabrillo. edu 42
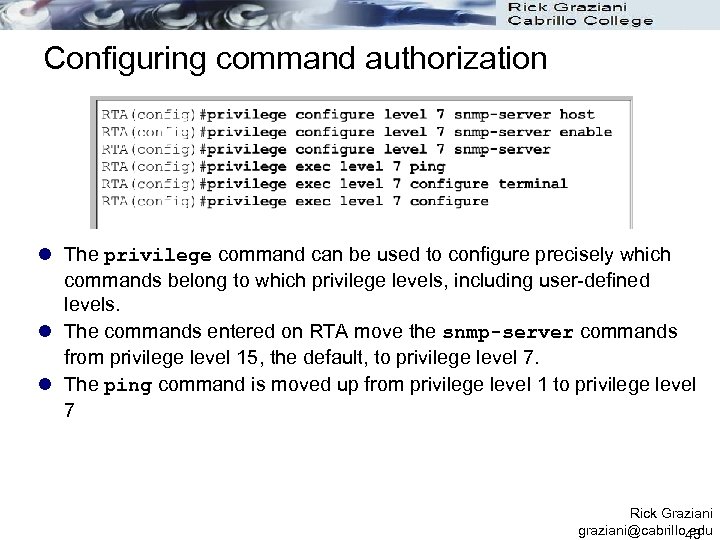 Configuring command authorization l The privilege command can be used to configure precisely which commands belong to which privilege levels, including user-defined levels. l The commands entered on RTA move the snmp-server commands from privilege level 15, the default, to privilege level 7. l The ping command is moved up from privilege level 1 to privilege level 7 Rick Graziani graziani@cabrillo. edu 43
Configuring command authorization l The privilege command can be used to configure precisely which commands belong to which privilege levels, including user-defined levels. l The commands entered on RTA move the snmp-server commands from privilege level 15, the default, to privilege level 7. l The ping command is moved up from privilege level 1 to privilege level 7 Rick Graziani graziani@cabrillo. edu 43
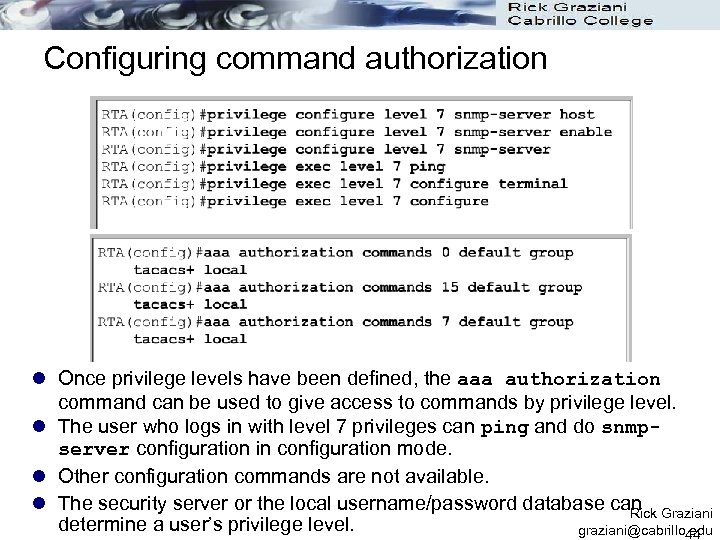 Configuring command authorization l Once privilege levels have been defined, the aaa authorization command can be used to give access to commands by privilege level. l The user who logs in with level 7 privileges can ping and do snmpserver configuration in configuration mode. l Other configuration commands are not available. l The security server or the local username/password database can Graziani Rick determine a user’s privilege level. graziani@cabrillo. edu 44
Configuring command authorization l Once privilege levels have been defined, the aaa authorization command can be used to give access to commands by privilege level. l The user who logs in with level 7 privileges can ping and do snmpserver configuration in configuration mode. l Other configuration commands are not available. l The security server or the local username/password database can Graziani Rick determine a user’s privilege level. graziani@cabrillo. edu 44
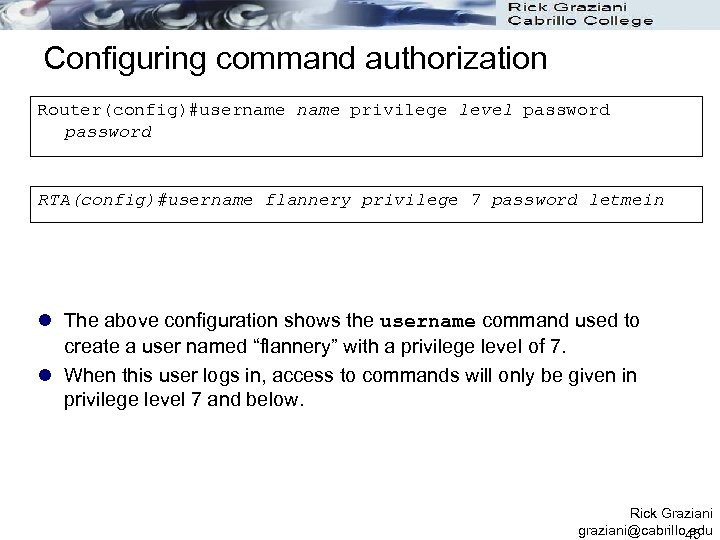 Configuring command authorization Router(config)#username privilege level password RTA(config)#username flannery privilege 7 password letmein l The above configuration shows the username command used to create a user named “flannery” with a privilege level of 7. l When this user logs in, access to commands will only be given in privilege level 7 and below. Rick Graziani graziani@cabrillo. edu 45
Configuring command authorization Router(config)#username privilege level password RTA(config)#username flannery privilege 7 password letmein l The above configuration shows the username command used to create a user named “flannery” with a privilege level of 7. l When this user logs in, access to commands will only be given in privilege level 7 and below. Rick Graziani graziani@cabrillo. edu 45
 Configuring AAA accounting
Configuring AAA accounting
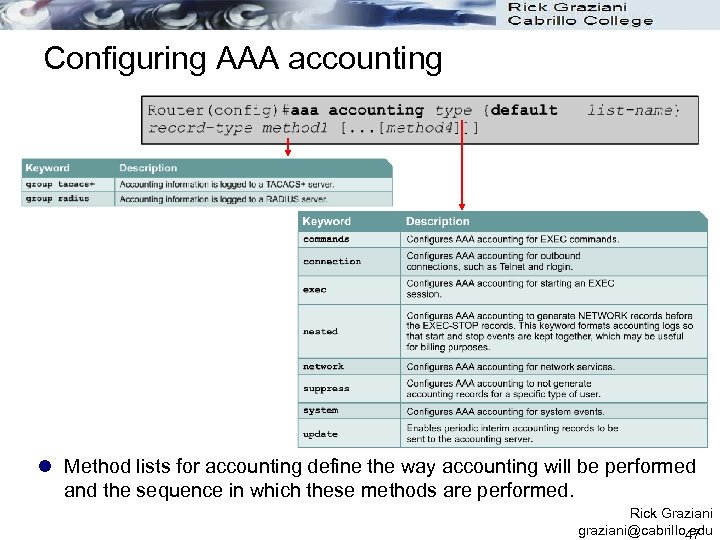 Configuring AAA accounting l Method lists for accounting define the way accounting will be performed and the sequence in which these methods are performed. Rick Graziani graziani@cabrillo. edu 47
Configuring AAA accounting l Method lists for accounting define the way accounting will be performed and the sequence in which these methods are performed. Rick Graziani graziani@cabrillo. edu 47
 Configuring AAA accounting l Accounting method lists are specific to the type of accounting being requested. l AAA supports the follow six different types of accounting. Network accounting provides information for all PPP, SLIP, or ARAP sessions, including packet and byte counts. EXEC accounting provides information about user EXEC terminal sessions of the network access server. Command accounting generates accounting records for all EXEC mode commands, including global configuration commands, associated with a specific privilege level. Connection accounting provides information about all outbound connections made from the network access server, such as Telnet, local-area transport (LAT), TN 3270, packet assembler/disassembler (PAD), and rlogin. System accounting provides information about system-level events. Resource accounting provides "start" and "stop" records for calls that have passed user authentication, and provides "stop" records for calls that fail to authenticate. Rick Graziani graziani@cabrillo. edu 48
Configuring AAA accounting l Accounting method lists are specific to the type of accounting being requested. l AAA supports the follow six different types of accounting. Network accounting provides information for all PPP, SLIP, or ARAP sessions, including packet and byte counts. EXEC accounting provides information about user EXEC terminal sessions of the network access server. Command accounting generates accounting records for all EXEC mode commands, including global configuration commands, associated with a specific privilege level. Connection accounting provides information about all outbound connections made from the network access server, such as Telnet, local-area transport (LAT), TN 3270, packet assembler/disassembler (PAD), and rlogin. System accounting provides information about system-level events. Resource accounting provides "start" and "stop" records for calls that have passed user authentication, and provides "stop" records for calls that fail to authenticate. Rick Graziani graziani@cabrillo. edu 48
 Configuring AAA accounting Rick Graziani graziani@cabrillo. edu 49
Configuring AAA accounting Rick Graziani graziani@cabrillo. edu 49
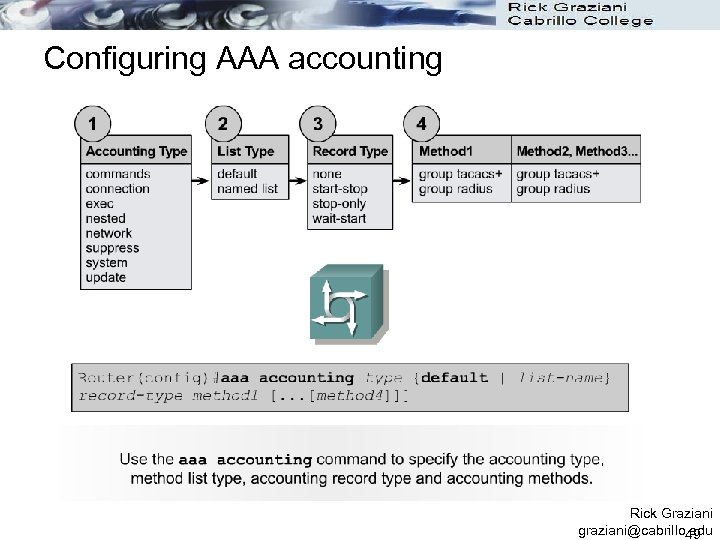
 Configuring AAA accounting l After specifying a named or default list, the accounting record type must be specified. The following are the four accounting record types: none start-stop stop-only wait-start l For minimal accounting, use the stop-only keyword. l This keyword instructs the specified method, RADIUS or TACACS+, to send a stop record accounting notice at the end of the requested user process. l For more accounting information, use the start-stop keyword to send a start accounting notice at the beginning of the requested event and a stop accounting notice at the end of the event. l Wait-start sends both a start and a stop accounting record to the accounting server. l However, if the wait-start keyword is used, the requested user service does not begin until the start accounting record is acknowledged. l A stop accounting record is also sent. l To stop all accounting activities on this line or interface, use the none keyword. Rick Graziani graziani@cabrillo. edu 50
Configuring AAA accounting l After specifying a named or default list, the accounting record type must be specified. The following are the four accounting record types: none start-stop stop-only wait-start l For minimal accounting, use the stop-only keyword. l This keyword instructs the specified method, RADIUS or TACACS+, to send a stop record accounting notice at the end of the requested user process. l For more accounting information, use the start-stop keyword to send a start accounting notice at the beginning of the requested event and a stop accounting notice at the end of the event. l Wait-start sends both a start and a stop accounting record to the accounting server. l However, if the wait-start keyword is used, the requested user service does not begin until the start accounting record is acknowledged. l A stop accounting record is also sent. l To stop all accounting activities on this line or interface, use the none keyword. Rick Graziani graziani@cabrillo. edu 50
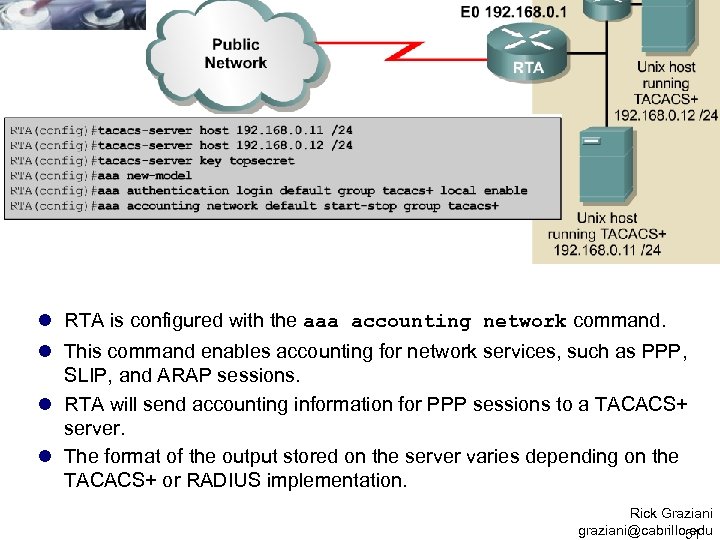 l RTA is configured with the aaa accounting network command. l This command enables accounting for network services, such as PPP, SLIP, and ARAP sessions. l RTA will send accounting information for PPP sessions to a TACACS+ server. l The format of the output stored on the server varies depending on the TACACS+ or RADIUS implementation. Rick Graziani graziani@cabrillo. edu 51
l RTA is configured with the aaa accounting network command. l This command enables accounting for network services, such as PPP, SLIP, and ARAP sessions. l RTA will send accounting information for PPP sessions to a TACACS+ server. l The format of the output stored on the server varies depending on the TACACS+ or RADIUS implementation. Rick Graziani graziani@cabrillo. edu 51
 Ch. 7 Network Management CIS 187 Multilayer Switched Networks CCNP version 7 Rick Graziani Spring 2016
Ch. 7 Network Management CIS 187 Multilayer Switched Networks CCNP version 7 Rick Graziani Spring 2016


