25fdd9108b1c04b0564ef3f71a41c4c5.ppt
- Количество слайдов: 82
 Ch 7: Identifying Advanced Attacks Comp. TIA Security+: Get Certified Get Ahead: SY 0 -401 Study Guide Darril Gibson
Ch 7: Identifying Advanced Attacks Comp. TIA Security+: Get Certified Get Ahead: SY 0 -401 Study Guide Darril Gibson
 Comparing Common Attacks
Comparing Common Attacks
 Spoofing Pretending to be someone else MAC address spoofing to get onto wireless networks Smurf attack spoofs source IP Email sent with spoofed "From" address
Spoofing Pretending to be someone else MAC address spoofing to get onto wireless networks Smurf attack spoofs source IP Email sent with spoofed "From" address
 Denial of Service (Do. S) Makes system unavailable to users D 0 S is from a single source DDo. S is from many sources
Denial of Service (Do. S) Makes system unavailable to users D 0 S is from a single source DDo. S is from many sources
 Distributed Denial of Service (DDo. S) Many computers attack a target simultaneously Botnets with thousands of zombies are common Can be very difficult to stop "Slashdot effect" can resemble a DDo. S, if thousands of real customers visit your page simultaneously
Distributed Denial of Service (DDo. S) Many computers attack a target simultaneously Botnets with thousands of zombies are common Can be very difficult to stop "Slashdot effect" can resemble a DDo. S, if thousands of real customers visit your page simultaneously
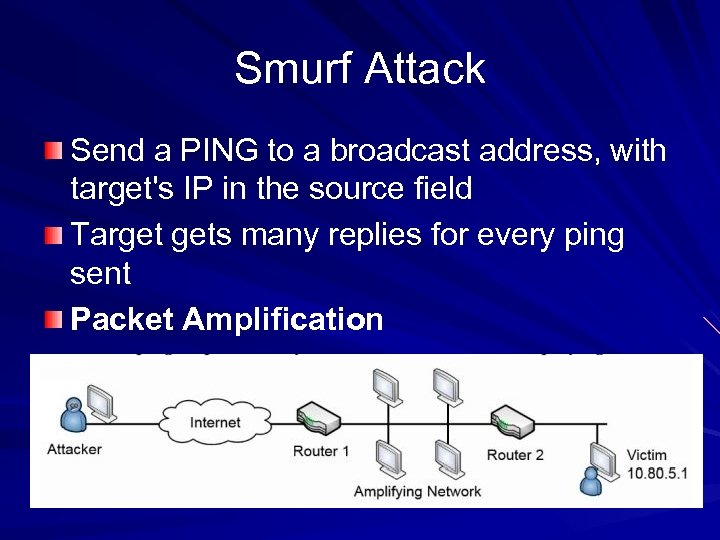 Smurf Attack Send a PING to a broadcast address, with target's IP in the source field Target gets many replies for every ping sent Packet Amplification
Smurf Attack Send a PING to a broadcast address, with target's IP in the source field Target gets many replies for every ping sent Packet Amplification
 SYN Flood TCP handshake: SYN, SYN/ACK, ACK Each SYN sent burdens the server because it has to calculate the SYN/ACK and remember to wait for the ACK SYN floods are more effective than other packets, such as pings, at Do. S
SYN Flood TCP handshake: SYN, SYN/ACK, ACK Each SYN sent burdens the server because it has to calculate the SYN/ACK and remember to wait for the ACK SYN floods are more effective than other packets, such as pings, at Do. S
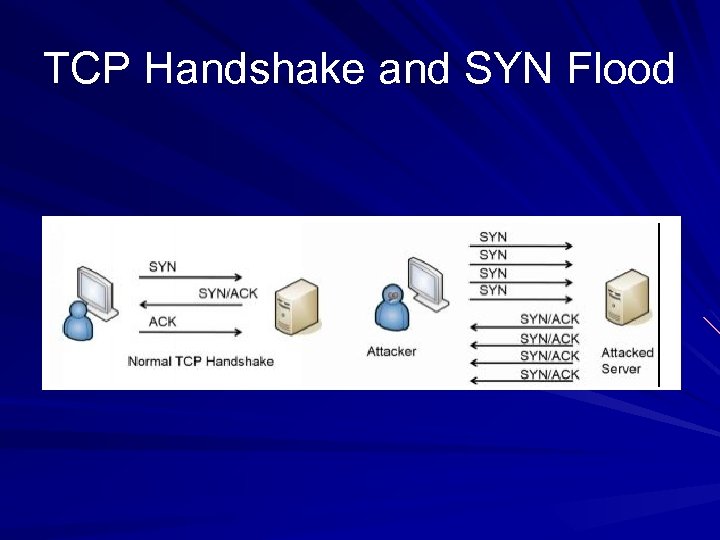 TCP Handshake and SYN Flood
TCP Handshake and SYN Flood
 Flood Guard Techniques Defend against SYN floods Block source IP addresses that send too many SYNs – But attacker can randomize the source IP Shorten timeout for half-open connection – But you may lose some real users SYN Cookies – A way to more efficiently process half-open connections
Flood Guard Techniques Defend against SYN floods Block source IP addresses that send too many SYNs – But attacker can randomize the source IP Shorten timeout for half-open connection – But you may lose some real users SYN Cookies – A way to more efficiently process half-open connections
 Botnet Zombie computers are infected with malware Under control of a bot herder Command Control (C&C) server C&C traffic can be detected in firewall logs Connections can be seen on a zombie with netstat
Botnet Zombie computers are infected with malware Under control of a bot herder Command Control (C&C) server C&C traffic can be detected in firewall logs Connections can be seen on a zombie with netstat
 IRC (Internet Relay Chat) An early chat service Used to control many older botnets Blocked at many companies now
IRC (Internet Relay Chat) An early chat service Used to control many older botnets Blocked at many companies now
 Botnet Attacks Download additional malware, such as keyloggers Launch DDo. S attacks Send spam email
Botnet Attacks Download additional malware, such as keyloggers Launch DDo. S attacks Send spam email
 XMAS Scan Sends TCP packets with many flags set Used to identify the server's OS, not to bring it down
XMAS Scan Sends TCP packets with many flags set Used to identify the server's OS, not to bring it down
 Man in the Middle (MITM) Intercept traffic "Active eavesdropping" Can insert malicious code into traffic stream ARP Poisoning redirects traffic to put the attacker in the middle Kerberos prevents MITM attacks with mutual authentication and a trusted authentication server (link Ch 7 a)
Man in the Middle (MITM) Intercept traffic "Active eavesdropping" Can insert malicious code into traffic stream ARP Poisoning redirects traffic to put the attacker in the middle Kerberos prevents MITM attacks with mutual authentication and a trusted authentication server (link Ch 7 a)
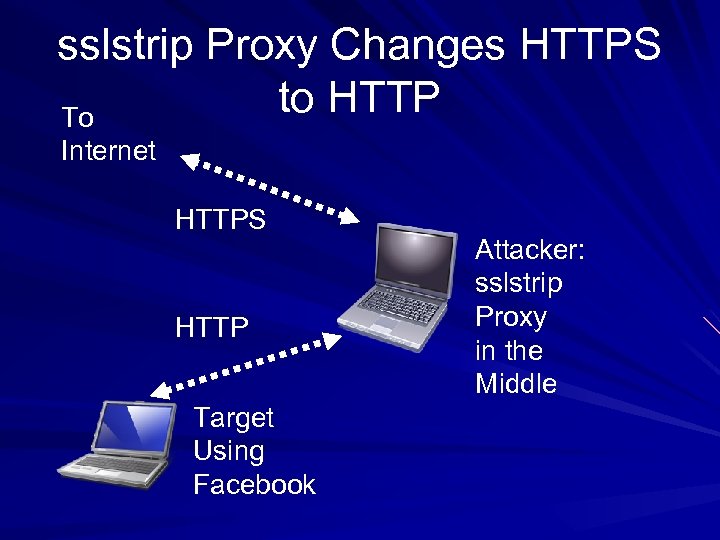 sslstrip Proxy Changes HTTPS to HTTP To Internet HTTPS HTTP Target Using Facebook Attacker: sslstrip Proxy in the Middle
sslstrip Proxy Changes HTTPS to HTTP To Internet HTTPS HTTP Target Using Facebook Attacker: sslstrip Proxy in the Middle
 Replay Attacker captures network packets and replays them to impersonate a client Countermeasures – Kerberos – HTTPS – Secure cookies
Replay Attacker captures network packets and replays them to impersonate a client Countermeasures – Kerberos – HTTPS – Secure cookies
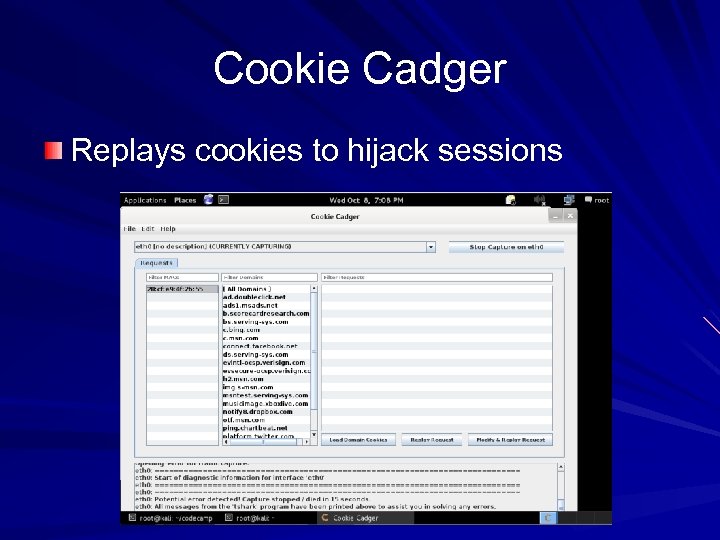 Cookie Cadger Replays cookies to hijack sessions
Cookie Cadger Replays cookies to hijack sessions
 Password Attacks Online attack – Try to guess password in a live online system – Best defense: account lockout policy Offline attack – Capture a database or packets – Guess passwords to match the data – Used for WPA cracking
Password Attacks Online attack – Try to guess password in a live online system – Best defense: account lockout policy Offline attack – Capture a database or packets – Guess passwords to match the data – Used for WPA cracking
 Brute Force Attack Uses every combination of characters Very slow for longer passwords – Typically 80 x slower for each added character
Brute Force Attack Uses every combination of characters Very slow for longer passwords – Typically 80 x slower for each added character
 Dictionary Attack Use a list of common passwords Very effective because so many real password lists have been published
Dictionary Attack Use a list of common passwords Very effective because so many real password lists have been published
 Password Hashes Many systems no longer store plaintext password Hash value is stored instead – Windows uses MD 4, others use MD 5 or SHA 1 or SHA-2 Hashes can be cracked with dictionary or brute-force attacks
Password Hashes Many systems no longer store plaintext password Hash value is stored instead – Windows uses MD 4, others use MD 5 or SHA 1 or SHA-2 Hashes can be cracked with dictionary or brute-force attacks
 Hash Collisions If two different passwords create the same hash, that is called a collision A strong hash function should have no known collisions – Collisions always exist, but they should be so rare that they can never be found
Hash Collisions If two different passwords create the same hash, that is called a collision A strong hash function should have no known collisions – Collisions always exist, but they should be so rare that they can never be found
 Birthday Attack If 23 people compare their birthdays, month and day – Most likely, two birthdays are the same – Because there are 23*22/2 pairs of people Hash collisions follow the same logic A 128 -bit hash will have a collision after 2^64 guesses A 160 -bit hash will have a collision after 2^80 guesses
Birthday Attack If 23 people compare their birthdays, month and day – Most likely, two birthdays are the same – Because there are 23*22/2 pairs of people Hash collisions follow the same logic A 128 -bit hash will have a collision after 2^64 guesses A 160 -bit hash will have a collision after 2^80 guesses
 Rainbow Table Attack Also called time-memory tradeoff A large table of precomputed hash values is stored in RAM Brute-force attack is faster because it looks up hashes instead of calculating them
Rainbow Table Attack Also called time-memory tradeoff A large table of precomputed hash values is stored in RAM Brute-force attack is faster because it looks up hashes instead of calculating them
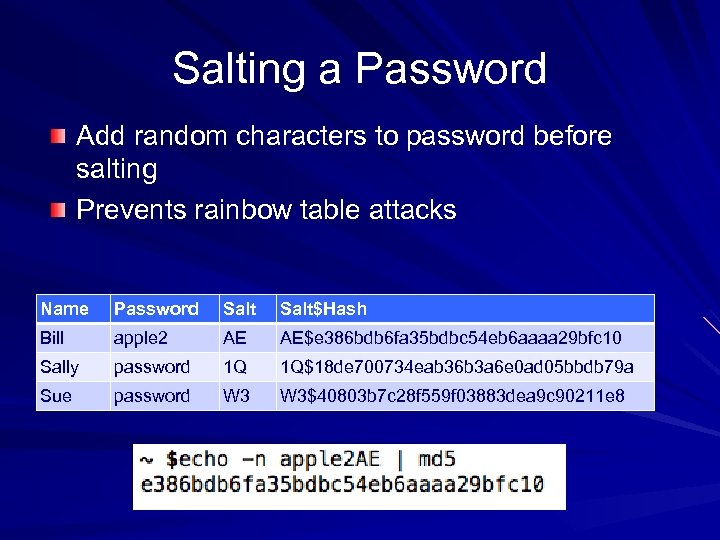 Salting a Password Add random characters to password before salting Prevents rainbow table attacks Name Password Salt$Hash Bill apple 2 AE AE$e 386 bdb 6 fa 35 bdbc 54 eb 6 aaaa 29 bfc 10 Sally password 1 Q 1 Q$18 de 700734 eab 36 b 3 a 6 e 0 ad 05 bbdb 79 a Sue password W 3$40803 b 7 c 28 f 559 f 03883 dea 9 c 90211 e 8
Salting a Password Add random characters to password before salting Prevents rainbow table attacks Name Password Salt$Hash Bill apple 2 AE AE$e 386 bdb 6 fa 35 bdbc 54 eb 6 aaaa 29 bfc 10 Sally password 1 Q 1 Q$18 de 700734 eab 36 b 3 a 6 e 0 ad 05 bbdb 79 a Sue password W 3$40803 b 7 c 28 f 559 f 03883 dea 9 c 90211 e 8
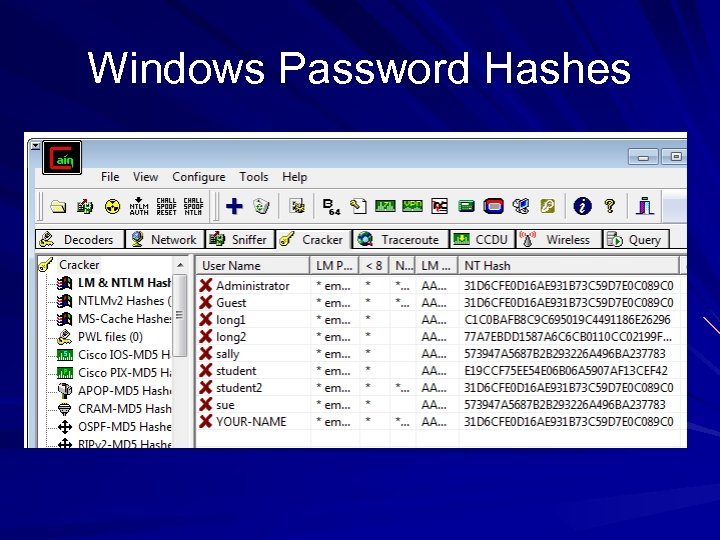 Windows Password Hashes
Windows Password Hashes
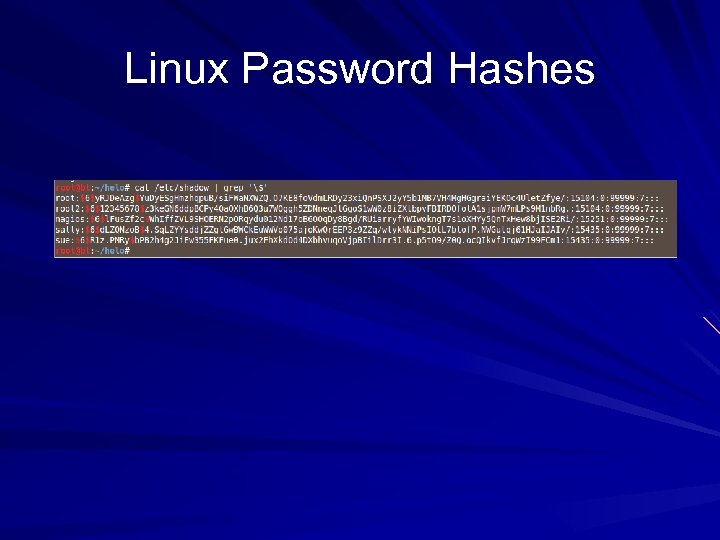 Linux Password Hashes
Linux Password Hashes
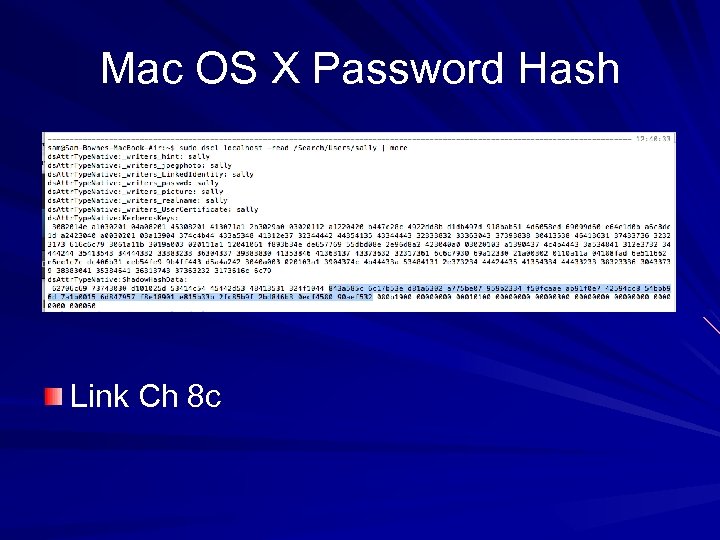 Mac OS X Password Hash Link Ch 8 c
Mac OS X Password Hash Link Ch 8 c
 Hybrid Attacks Combine dictionary and brute force attacks Modify dictionary words – Dictionary has "apple" – So try "Apple", "APPLE", "4 pp 13", "apple 1", etc.
Hybrid Attacks Combine dictionary and brute force attacks Modify dictionary words – Dictionary has "apple" – So try "Apple", "APPLE", "4 pp 13", "apple 1", etc.
 DNS Servers Resolve domain names like www. ccsf. edu to IP addresses like 147. 144. 1. 212 – Results are held in a cache for a few minutes on each client Reverse DNS finds domain names from IP addresses – Sometimes used to block spam, making sure the IP address matches the "From" email address
DNS Servers Resolve domain names like www. ccsf. edu to IP addresses like 147. 144. 1. 212 – Results are held in a cache for a few minutes on each client Reverse DNS finds domain names from IP addresses – Sometimes used to block spam, making sure the IP address matches the "From" email address
 DNS Attacks DNS Cache Poisoning – Like ARP poisoning, tricks the target machine into resolving domain names to incorrect IP addresses Pharming – Changing the hosts file to redirect traffic to a spoofed website DNS Cache Snooping – Can find out what sites people have been visiting
DNS Attacks DNS Cache Poisoning – Like ARP poisoning, tricks the target machine into resolving domain names to incorrect IP addresses Pharming – Changing the hosts file to redirect traffic to a spoofed website DNS Cache Snooping – Can find out what sites people have been visiting
 ARP Request and Reply n Client wants to find Gateway n ARP Request: Who has 192. 168. 2. 1? n ARP Reply: n MAC: 00 -30 -bd-02 -ed-7 b has 192. 168. 2. 1 ARP Request ARP Reply Client Gateway Facebook. com
ARP Request and Reply n Client wants to find Gateway n ARP Request: Who has 192. 168. 2. 1? n ARP Reply: n MAC: 00 -30 -bd-02 -ed-7 b has 192. 168. 2. 1 ARP Request ARP Reply Client Gateway Facebook. com
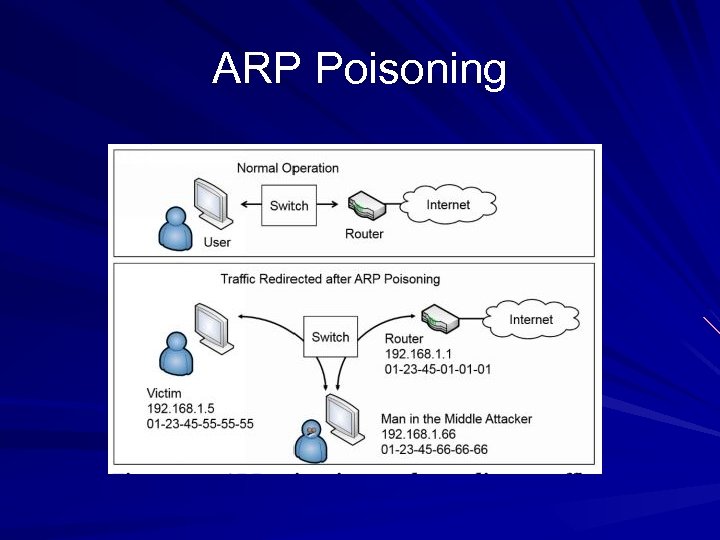 ARP Poisoning
ARP Poisoning
 ARP Poisoning Redirects Traffic at Layer 2 Sends a lot of false ARP packets on the LAN Can be easily detected De. Caffienate. ID by Iron. Geek – http: //k 78. sl. pt
ARP Poisoning Redirects Traffic at Layer 2 Sends a lot of false ARP packets on the LAN Can be easily detected De. Caffienate. ID by Iron. Geek – http: //k 78. sl. pt
 ARP Poisoning Do. S Attacker can change MAC address of the gateway to a bogus value This renders the Internet unavailable
ARP Poisoning Do. S Attacker can change MAC address of the gateway to a bogus value This renders the Internet unavailable
 Typosquatting/URL Hijacking Purchasing a domain close to a real one – Like yahooo. com or hushmali. com At the domain, put – Site containing ads or malware – Phishing site that looks like the real page – Insulting or offensive page to motivate the real site to buy the domain
Typosquatting/URL Hijacking Purchasing a domain close to a real one – Like yahooo. com or hushmali. com At the domain, put – Site containing ads or malware – Phishing site that looks like the real page – Insulting or offensive page to motivate the real site to buy the domain
 Watering Hole Attacks Put up or find a page of interest to the targets Put drive-by download malware on that page Visitors get infected with RAT (Remote Access Trojan)
Watering Hole Attacks Put up or find a page of interest to the targets Put drive-by download malware on that page Visitors get infected with RAT (Remote Access Trojan)
 Zero Day Attacks Exploit an undocumented vulnerability No vendor patch available Attackers can get in easily until the 0 -day is detected and patched 0 -days sell for highi prices at exploit brokers
Zero Day Attacks Exploit an undocumented vulnerability No vendor patch available Attackers can get in easily until the 0 -day is detected and patched 0 -days sell for highi prices at exploit brokers
 Web Browser Concerns Malicious add-ons Cookies – May contain private data – May be used in replay attacks Session Hijacking – Old version: Inject packets into a TCP session – New version: Replay authentication cookies – Technical name: Cross-Site Request Forgery (CSRF or XSRF)
Web Browser Concerns Malicious add-ons Cookies – May contain private data – May be used in replay attacks Session Hijacking – Old version: Inject packets into a TCP session – New version: Replay authentication cookies – Technical name: Cross-Site Request Forgery (CSRF or XSRF)
 Flash Cookies and LSOs Flash cookies are created by Adobe Flash Player – Also called Local Shared Objects Stored in multiple locations Difficult to delete
Flash Cookies and LSOs Flash cookies are created by Adobe Flash Player – Also called Local Shared Objects Stored in multiple locations Difficult to delete
 Deletes Google cookies Link Ch 7 c
Deletes Google cookies Link Ch 7 c
 Securing Applications
Securing Applications
 Basic Application Hardening Steps Harden the server itself – Disable unnecessary services – Disable default accounts – Change passwords Follow vendor guidelines for application Change default passwords Disable unnecessary accounts Eliminate backdoors
Basic Application Hardening Steps Harden the server itself – Disable unnecessary services – Disable default accounts – Change passwords Follow vendor guidelines for application Change default passwords Disable unnecessary accounts Eliminate backdoors
 Software Development Life Cycle SDLC models – Waterfall – Spiral – V-Shaped – Rapid Application Model
Software Development Life Cycle SDLC models – Waterfall – Spiral – V-Shaped – Rapid Application Model
 Software Development Life Cycle Goals Requirements and design identification Secure code review – at many stages of development Testing – Best technique is black-box testing by external experts – "Black box" means they don't know any internal details of the application
Software Development Life Cycle Goals Requirements and design identification Secure code review – at many stages of development Testing – Best technique is black-box testing by external experts – "Black box" means they don't know any internal details of the application
 Performing Input Validation Checking data for validity before using it Never trust anything that came from the user! Error-handling routines should be friendly and helpful but not disclose too much information
Performing Input Validation Checking data for validity before using it Never trust anything that came from the user! Error-handling routines should be friendly and helpful but not disclose too much information
 Input Attacks All these attacks can be prevented with input validation – Buffer overflow Input too long – SQL injection Input misinterpreted as code and executed – Cross-site scripting Input misinterpreted as code and executed
Input Attacks All these attacks can be prevented with input validation – Buffer overflow Input too long – SQL injection Input misinterpreted as code and executed – Cross-site scripting Input misinterpreted as code and executed
 Understanding Secure Coding Concepts
Understanding Secure Coding Concepts
 Input Validation Don't use data that came from external sources, such as the user, without cleaning it first Only allow proper characters, such as digits in a Zip code Range checking: only accept values in allowed range (such as 9 -digit SSNs) Limit length Remove special characters like < " %
Input Validation Don't use data that came from external sources, such as the user, without cleaning it first Only allow proper characters, such as digits in a Zip code Range checking: only accept values in allowed range (such as 9 -digit SSNs) Limit length Remove special characters like < " %
 Client-side and Server-side Validation Using Javascript to validate input on the client-side is common but inadequate Server-side validation must also be performed – Because client can bypass client-side validation by using a proxy or disabling scripting
Client-side and Server-side Validation Using Javascript to validate input on the client-side is common but inadequate Server-side validation must also be performed – Because client can bypass client-side validation by using a proxy or disabling scripting
 Avoiding Race Conditions Two programs may use the same resource at the same time – Such as a file in the /tmp folder There is a race to see which program gets it first Exploits work by "winning the race"
Avoiding Race Conditions Two programs may use the same resource at the same time – Such as a file in the /tmp folder There is a race to see which program gets it first Exploits work by "winning the race"
 Error and Exception Handling If an application doesn't capture an error properly Error messages fail to system defaults These frequently give out too much information to an attacker Details should be logged, but hot shown to the user
Error and Exception Handling If an application doesn't capture an error properly Error messages fail to system defaults These frequently give out too much information to an attacker Details should be logged, but hot shown to the user
 Identifying Application Attacks
Identifying Application Attacks
 Web Servers Apache – Most popular Web server – Free, can run on Unix, Linux or Windows IIS (Internet Information Systems) – Microsoft's Web server – Used by large companies on Windows Servers nginx – More efficient than Apache, growing in popularity
Web Servers Apache – Most popular Web server – Free, can run on Unix, Linux or Windows IIS (Internet Information Systems) – Microsoft's Web server – Used by large companies on Windows Servers nginx – More efficient than Apache, growing in popularity
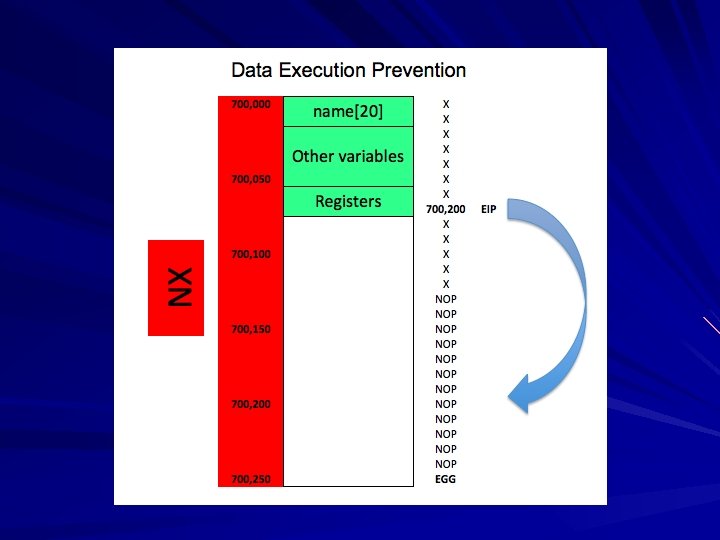
 Buffer Overflows Application reserves some space for a variable, such as a username of 30 characters Attacker puts in a longer name, such as 1000 characters Overwrites memory locations with injected code Can cause Do. S or Remote Execution
Buffer Overflows Application reserves some space for a variable, such as a username of 30 characters Attacker puts in a longer name, such as 1000 characters Overwrites memory locations with injected code Can cause Do. S or Remote Execution
 NOP Sled Attacker puts a string of No Operation (NOP) commands before the "egg" Egg is code that connects back to the attacker for remote control This makes attacks more likely to succeed, because it's easier to predict where the injected code is
NOP Sled Attacker puts a string of No Operation (NOP) commands before the "egg" Egg is code that connects back to the attacker for remote control This makes attacks more likely to succeed, because it's easier to predict where the injected code is
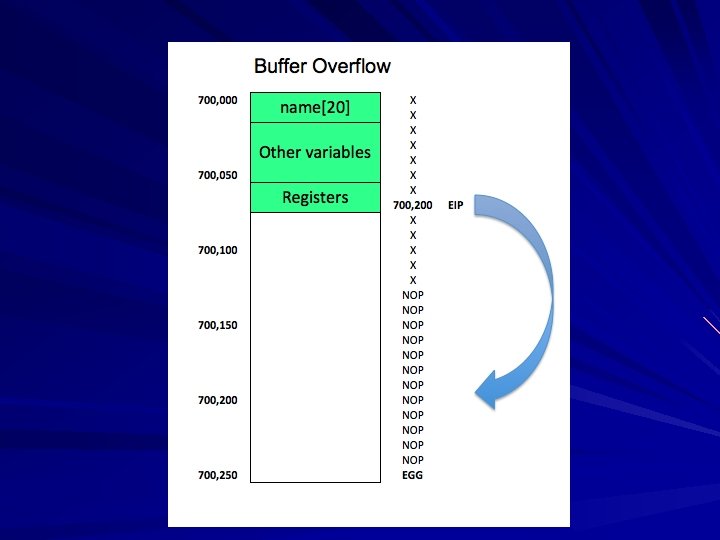
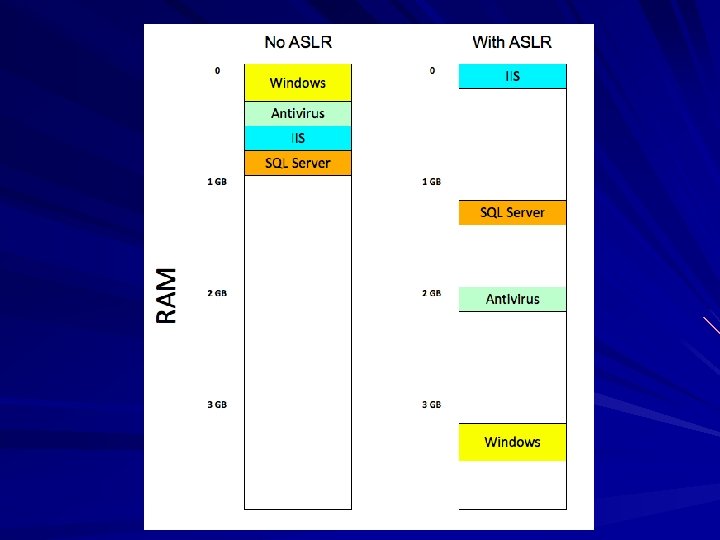
 Buffer Overflow Defenses 59
Buffer Overflow Defenses 59
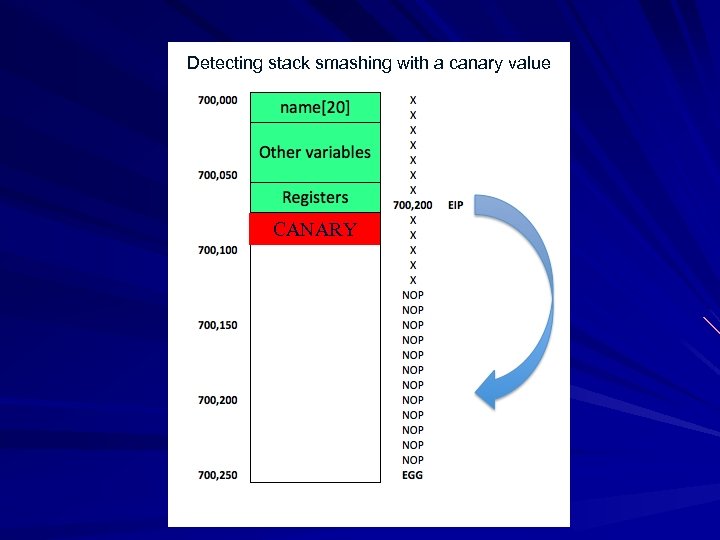 Detecting stack smashing with a canary value CANARY
Detecting stack smashing with a canary value CANARY
 Integer Overflow Large numbers can be misinterpreted by computers as negative numbers This can long strings to bypass filters Results similar to a buffer overflow
Integer Overflow Large numbers can be misinterpreted by computers as negative numbers This can long strings to bypass filters Results similar to a buffer overflow
 SQL Queries
SQL Queries
 SQL Code SELECT * From Books where Author = 'Darril Gibson' • * is a wildcard that returns every column in a table • Books is the Table Name • Author is a column name • 'Darril Gibson' contains input from the user
SQL Code SELECT * From Books where Author = 'Darril Gibson' • * is a wildcard that returns every column in a table • Books is the Table Name • Author is a column name • 'Darril Gibson' contains input from the user
 SQL Injection SELECT * From Books where Author = 'darril gibson' OR 'a' = 'a' • Condition is always true • This would dump all the data in the Books table
SQL Injection SELECT * From Books where Author = 'darril gibson' OR 'a' = 'a' • Condition is always true • This would dump all the data in the Books table
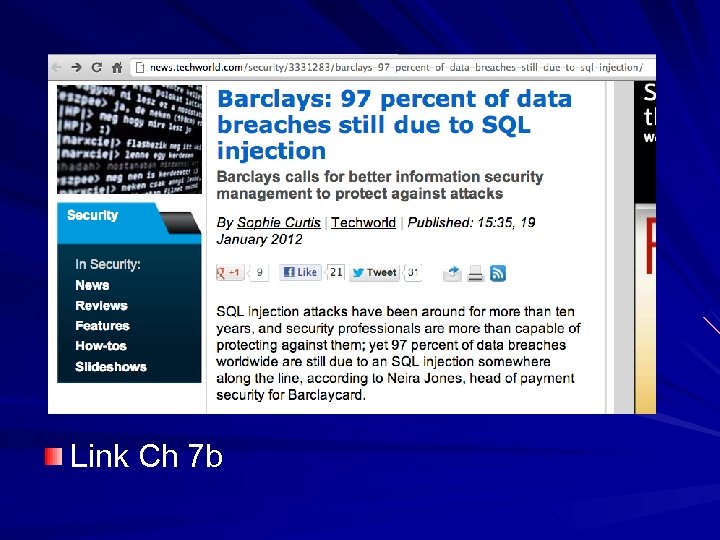 Link Ch 7 b
Link Ch 7 b
 SQL Injection Effects Expose data Add or alter data Delete data Run shell commands Gain control of the server Plant malware on Websites
SQL Injection Effects Expose data Add or alter data Delete data Run shell commands Gain control of the server Plant malware on Websites
 Be Careful Don't try SQL injection on real websites Use safe training tools like Web. Goat amd SQLol Image from http: //opinitimoreg. blogspot. com/2012/08/civil-society-does-not-agree-that-ex. html
Be Careful Don't try SQL injection on real websites Use safe training tools like Web. Goat amd SQLol Image from http: //opinitimoreg. blogspot. com/2012/08/civil-society-does-not-agree-that-ex. html
 Protecting Against SQL Injection Attacks Input Validation – Blacklisting: Remove characters like ' and " Not very effective – Whitelisting: Allow only "safe" characters Better but still not the best defenst – Parameterized Queries (also called "Stored Procedures") Data is treated separately from code No data can be executed This is the safest technique
Protecting Against SQL Injection Attacks Input Validation – Blacklisting: Remove characters like ' and " Not very effective – Whitelisting: Allow only "safe" characters Better but still not the best defenst – Parameterized Queries (also called "Stored Procedures") Data is treated separately from code No data can be executed This is the safest technique
 XML Injection Many databases use XML (e. Xtensible Markup Language) to input or export data XML is plaintext, with data tags like HTML –
XML Injection Many databases use XML (e. Xtensible Markup Language) to input or export data XML is plaintext, with data tags like HTML –
 No. SQL v. SQL Databases No. SQL databases are more flexible than SQL databases Can store documents, key-value pairs, or graphs No. SQL databases are also subject to command-injection attacks
No. SQL v. SQL Databases No. SQL databases are more flexible than SQL databases Can store documents, key-value pairs, or graphs No. SQL databases are also subject to command-injection attacks
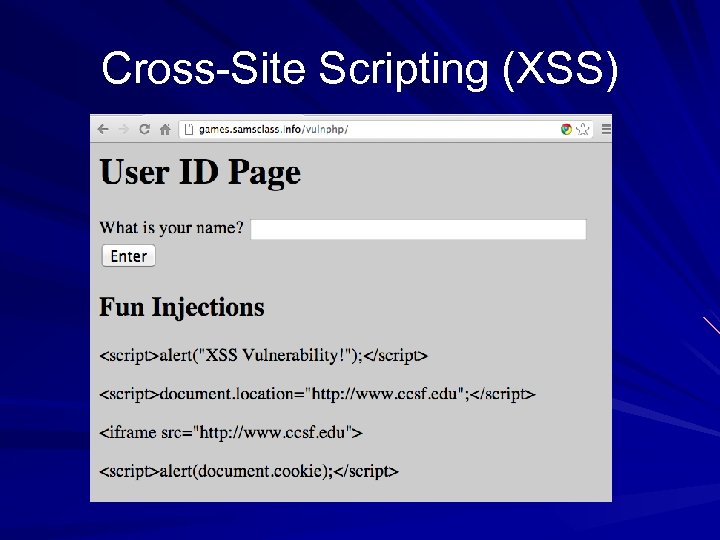 Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS)
 Cross-Site Scripting Code from one site runs on another site Possible Effects – Read cookies from other browser tabs – Take action on other tabs, like making purchases or Facebook posts – Add malware to page – Redirect page
Cross-Site Scripting Code from one site runs on another site Possible Effects – Read cookies from other browser tabs – Take action on other tabs, like making purchases or Facebook posts – Add malware to page – Redirect page
 XSS Countermeasures One common type of XSS embeds the attack in a link and emails it to victims Not clicking on suspicious links can prevent the attack Best solution is for the website designer to validate input – Replace < with < , and so on for other symbols
XSS Countermeasures One common type of XSS embeds the attack in a link and emails it to victims Not clicking on suspicious links can prevent the attack Best solution is for the website designer to validate input – Replace < with < , and so on for other symbols
 Cross-Site Request Forgery (XSRF) Attack tricks user into performing a action on a website, when they click a URL like this – http: //facebook. com? add_friend=hacker Can take an action on any site where the user is already logged in Gmail, Facebook, Twitter, Amazon, etc.
Cross-Site Request Forgery (XSRF) Attack tricks user into performing a action on a website, when they click a URL like this – http: //facebook. com? add_friend=hacker Can take an action on any site where the user is already logged in Gmail, Facebook, Twitter, Amazon, etc.
 XSRF Countermeasures Users can avoid clicking on phishy links Developers can help by making users authenticate before risky actions, or by making sessions expire quickly
XSRF Countermeasures Users can avoid clicking on phishy links Developers can help by making users authenticate before risky actions, or by making sessions expire quickly
 Directory Traversal http: //samsclass. info/125/proj 11/. . / Is the same as http: //samsclass. info/ Because. . /goes UP a directory At vulnerable sites, you can exit the Web page directory and reveal the file system http: //samsclass. info/. . /etc/passwd Would reveal user names
Directory Traversal http: //samsclass. info/125/proj 11/. . / Is the same as http: //samsclass. info/ Because. . /goes UP a directory At vulnerable sites, you can exit the Web page directory and reveal the file system http: //samsclass. info/. . /etc/passwd Would reveal user names
 Command Injection If an attacker can traverse to executable files, they can be executed from the browser's URL bar http: //samsclass. info/. . /windows/syste m 32/cmd. exe? c+dir+c: – Displays a directory in the browser Countermeasure: input validation, use of directory permissions
Command Injection If an attacker can traverse to executable files, they can be executed from the browser's URL bar http: //samsclass. info/. . /windows/syste m 32/cmd. exe? c+dir+c: – Displays a directory in the browser Countermeasure: input validation, use of directory permissions
 LDAP Injection Lightqeight Directory Access Protocol is used in Windows domains LDAP injection allows an attacker to query and modify information in Active Directory
LDAP Injection Lightqeight Directory Access Protocol is used in Windows domains LDAP injection allows an attacker to query and modify information in Active Directory
 Transitive Access and Client-side Attacks Database server trusts the Web server and answers its queries Attacker needs to use the Web server to attack the database server This is called transitive access Penetration testers call it pivoting
Transitive Access and Client-side Attacks Database server trusts the Web server and answers its queries Attacker needs to use the Web server to attack the database server This is called transitive access Penetration testers call it pivoting
 Fuzzing Sending random data to a program If it crashes, that indicates a Do. S vulnerability Analyzing the crash may result in a remote code execution vulnerability as well
Fuzzing Sending random data to a program If it crashes, that indicates a Do. S vulnerability Analyzing the crash may result in a remote code execution vulnerability as well


