84103369d745d3702f1412a7b6e9586d.ppt
- Количество слайдов: 48

Certificates and -Business E Chapter 5 CIM 3561 Internet Security for e-Commerce 1

Public Key Infrastructure (PKI) n n n In cryptography, a public key infrastructure (PKI) is an arrangement that binds public keys with respective user identities by means of a certificate authority (CA). The user identity must be unique for each CA. The binding is established through the registration and issuance process, which, depending on the level of assurance the binding has, may be carried out by software at a CA, or under human supervision. The PKI role that assures this binding is called the Registration Authority (RA). For each user, the user identity, the public key, their binding, validity conditions and other attributes are made unforgettable in public key certificates issued by the CA. 2

Public-Key Certification n n In cryptography, a public key certificate (or identity certificate) is an electronic document which incorporates a digital signature to bind together a public key with an identity — information such as the name of a person or an organization, their address, and so forth. The certificate can be used to verify that a public key belongs to an individual. In a typical public key infrastructure (PKI) scheme, the signature will be of a certificate authority (CA). In a web of trust scheme, the signature is of either the user (a self-signed certificate) or other users ("endorsements"). In either case, the signatures on a certificate are attestations by the certificate signer that the identity information and the public key belong together. 3

Key Management n n In cryptography, key management includes all of the provisions made in a cryptosystem design, in cryptographic protocols in that design, in user procedures, and so on, which are related to generation, exchange, storage, safeguarding, use, vetting, and replacement of keys. There is a distinction between key management, which concerns keys at the users' level (i. e. , passed between systems or users or both), and key scheduling which is usually taken to apply to the handling of key material within the operation of a cipher. 4
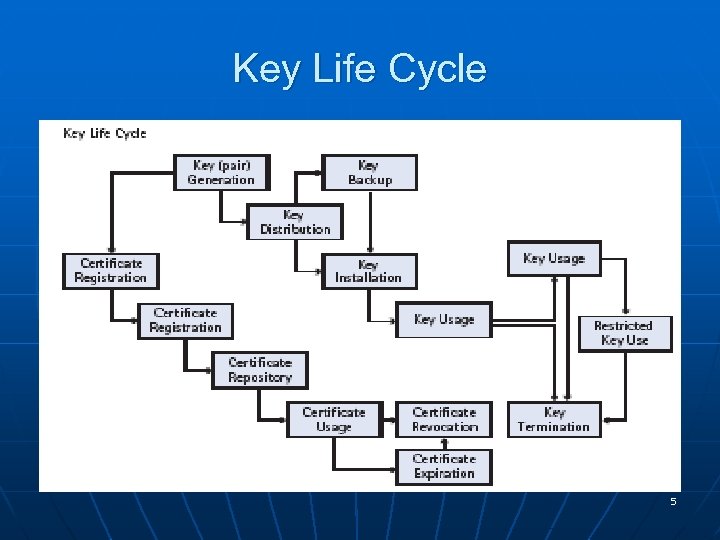
Key Life Cycle 5

PKI for typical e-Commerce enterprises n n Enterprise PKI systems are often closely tied to an enterprise's directory scheme, in which each employee's public key is often stored (embedded in a certificate), together with other personal details (phone number, email address, location, department, . . . ). Today's leading directory technology is LDAP and in fact, the most common certificate format (X. 509) stems from its use in LDAP's predecessor, the X. 500 directory schema. 6

Certification Policies n Certificate policies are, in the X. 509 version 3 digital certificate standard, the applications which a certifying CA declares a specific public/private key fit for. Typical certificate policies include: • digital signature of e-mail, aka S/MIME • encryption of data • verification of Web site identity • further issuance of certificates (delegation of authority) 7

The Current Environment n The Internet is the next big commercial medium 8

Requirements of Public-Key systems n SECRECY of the private key • Must be known only to owner • Key ownership = Identity n AVAILABILITY of the public key • Must be available to anyone • Requires a public directory 9
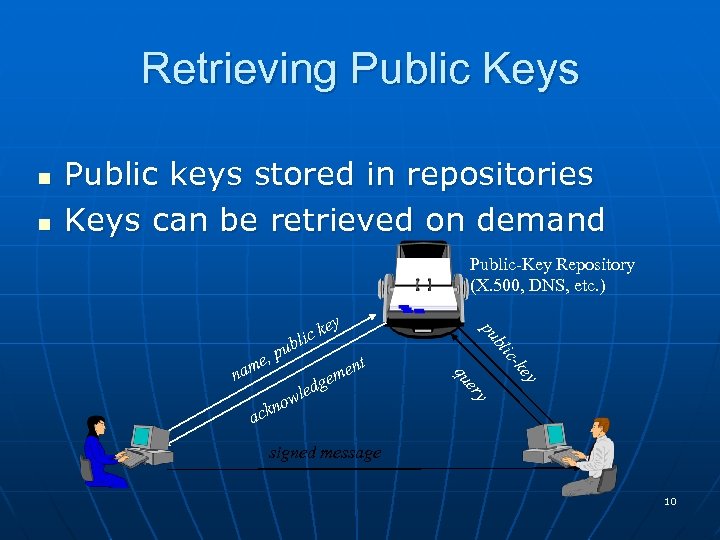
Retrieving Public Keys n n Public keys stored in repositories Keys can be retrieved on demand Public-Key Repository (X. 500, DNS, etc. ) y ke ic- bl y d le ow kn er ent gem qu na pu u e, p m ey ic k bl ac signed message 10
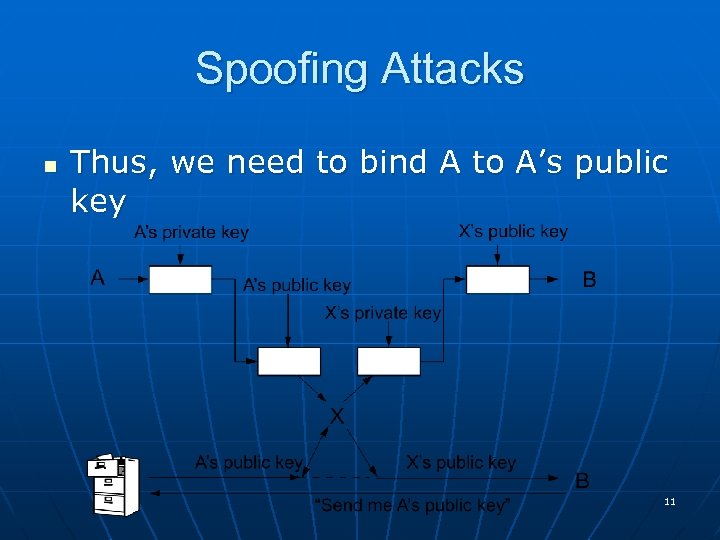
Spoofing Attacks n Thus, we need to bind A to A’s public key 11

Certification Authorities (CAs) n n In cryptography, a certificate authority or certification authority (CA) is an entity which issues digital certificates for use by other parties. It is an example of a trusted third party. CAs are characteristic of many public key infrastructure (PKI) schemes. Users send keys to a Certification Authority. CA then generates a certificate for the user, signed with the CA’s private key. 12

Certification Authorities (CAs) Users send keys to a Certification Authority. CA then generates a certificate for the user, signed with the CA’s private key. CA c te Certificate Repository (X. 500, DNS, etc. ) ce certificate ertifica e at signed message ic f rti y er qu name, public-key n 13
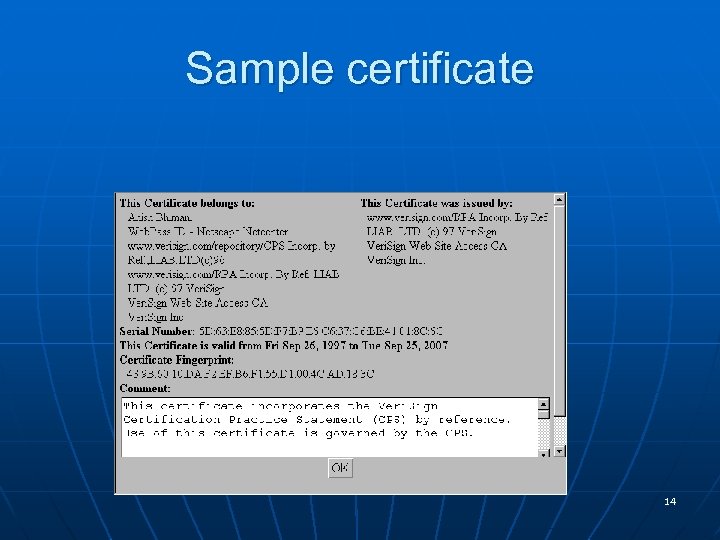
Sample certificate 14

Types of Certificates n Generic X. 509 certificates • The wonderful thing about standards. . . n n SSL certificates SET certificates S/MIME certificates app-specific certificates 15

X. 509 n n n ITU-T standard for certificates v 1 (1988): defined basic criteria v 2 (1992): added name flexibility v 3 (1993): added extensions Extensions • allow for inclusion of extra information in a certificate • e. g. , role & authorization information • can be marked “critical” or “non-critical” 16 16
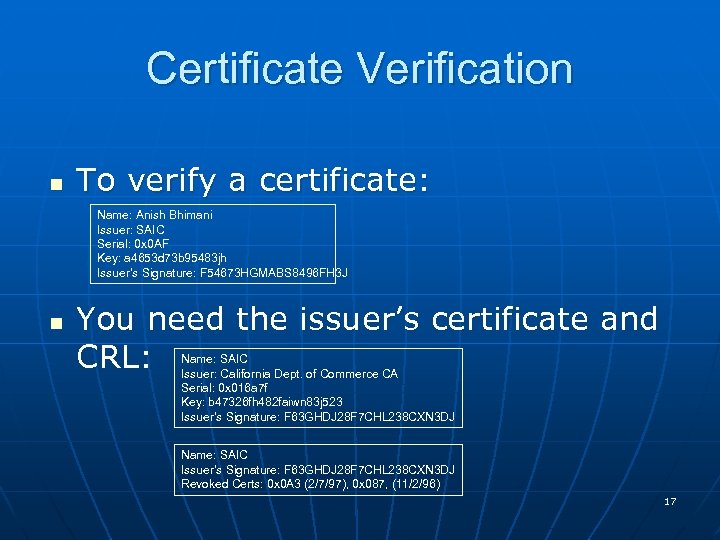
Certificate Verification n To verify a certificate: Name: Anish Bhimani Issuer: SAIC Serial: 0 x 0 AF Key: a 4653 d 73 b 95483 jh Issuer’s Signature: F 54673 HGMABS 8496 FH 3 J n You need the issuer’s certificate and CRL: Name: SAIC Issuer: California Dept. of Commerce CA Serial: 0 x 016 a 7 f Key: b 47326 fh 482 faiwn 83 j 523 Issuer’s Signature: F 63 GHDJ 28 F 7 CHL 238 CXN 3 DJ Name: SAIC Issuer’s Signature: F 63 GHDJ 28 F 7 CHL 238 CXN 3 DJ Revoked Certs: 0 x 0 A 3 (2/7/97), 0 x 087, (11/2/96) 17
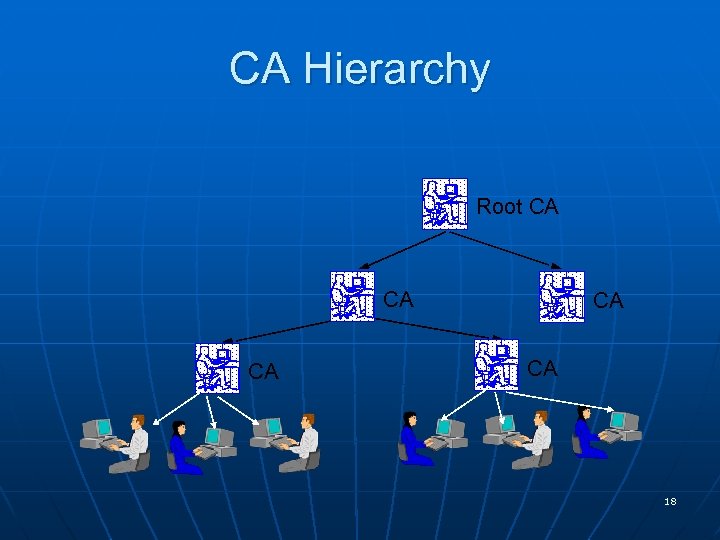
CA Hierarchy Root CA CA CA 18

Attribute Certificates n n X. 509 certificates are for identity What about authorization? • Access to systems • Purchasing powers • etc. n n n Attribute certificates convey that information Short-lived Frequently updated 19

Major Questions about PKI Deployment n n n What mechanisms do users have to trust each other? How can users protect the uniqueness of their private key? How can the privacy needs of individuals be balanced with the corporate need for information? What components of the PKI can be outsourced? Who is liable when problems occur? How can multiple applications work with each other? 20

Components of the PKI n n n n End Users Certification Authorities Registration Authorities Certificate Directories Root CA(s) Certification Practice Statements (CPS) Certificate Management Protocols & APIs Personal Security Environments (PSE) 21

Major Issues with CAs and RAs n n n n End Entity Registration Trust models Certification Practice Statement (CPS) Key management Certificate Revocation Publishing Issues Ownership and Maintenance 22

Registration n Registration Authority (RA) • verification of user info • policy enforcement • no liability • only handles registration, not reissuance, revocation, etc. • works with CA n Registration can be local, or outsourced 23
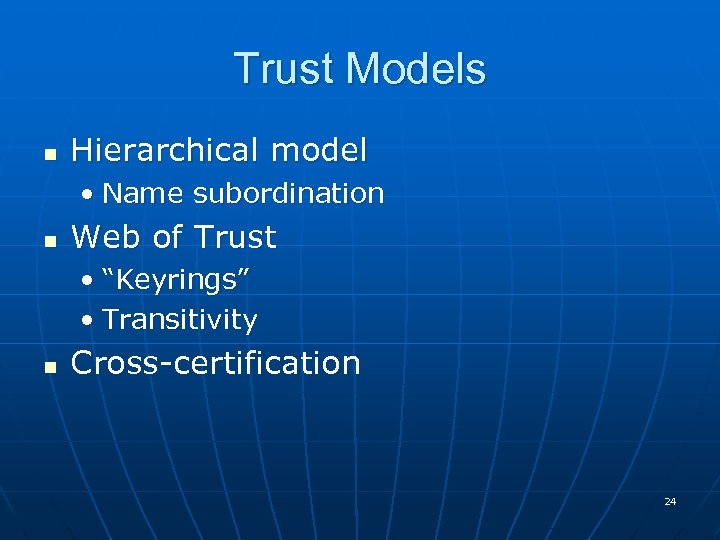
Trust Models n Hierarchical model • Name subordination n Web of Trust • “Keyrings” • Transitivity n Cross-certification 24
Hierarchical Trust n n First used by PEM Difficult to bootstrap 25
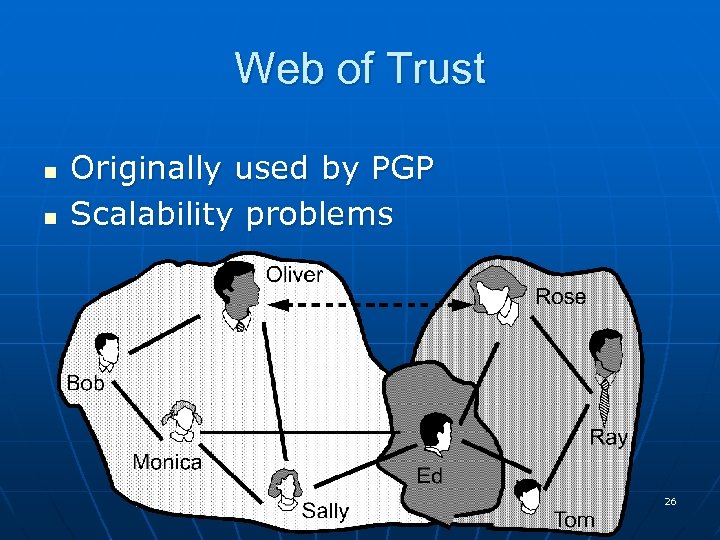
Web of Trust n n Originally used by PGP Scalability problems 26
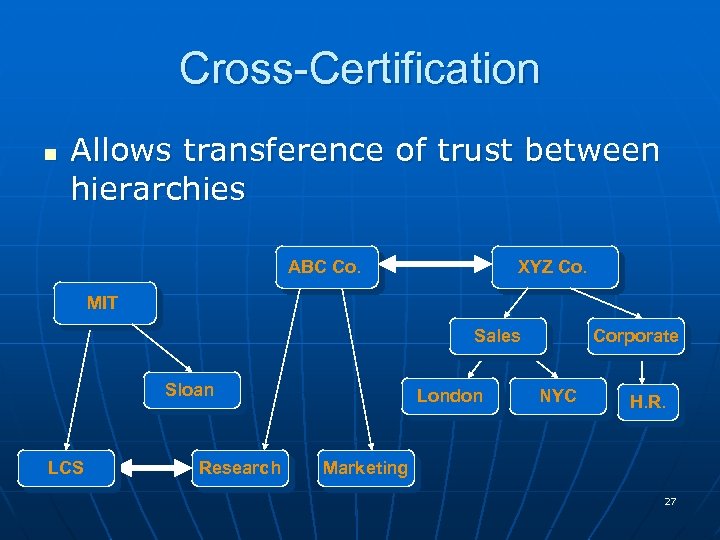
Cross-Certification n Allows transference of trust between hierarchies ABC Co. XYZ Co. MIT Sales Sloan LCS Research London Corporate NYC H. R. Marketing 27

Policy Issues n n n n Verification of Identity What is being certified? Validity Periods of Certificates CRL issuance / Certificate Revocation Publishing Re-issuance Scope of clientele All are presented in the Certification Practice Statement (CPS) 28

Certification Practice Statement n n Outlines the CA’s practices with regard to: • certificate issuance and user registration • certificate lifetimes and revocation • trust model and vetting process • certificate publishing practices Designed for a few purposes: • Awareness of customers • Limiting liability • Outlining procedures for personnel 29

Key management n Generation of key-pairs • CA, RA, end entity? n Storage of private keys at CA • smartcards, or on disk n Archival of keys 30

Certificate Revocation n n What constitutes revocation? Push/Pull model of CRLs Publishing Issues Real-time verification? Are CRLs the right model? 31

Revocation Models n Certificate Revocation Lists (CRLs) • Traditional model • Supported by Entrust, Verisign, most CAs n n n Certificate Revocation Trees (CRTs) On-line Certificate Status Protocol (OCSP) CRL Distribution Points (CDPs) 32

New Revocation Models n n On-line Certificate Status Protocol (OCSP) • IETF proposed protocol - introduced by Veri. Sign • real-time verification of certificates • OCSP responders - provide info to clients • acceptance suspended pending response Certificate Revocation Trees (Valicert) • Offers service and product for real-time verification • CRL “trees” - contained within product or at server 33

Certificate Validation and Revocation n n Currently not done by most applications Entrust. Direct - supports Web-based clients using CRLs Vali. Cert - toolkit and server support validation Entrust/Server - supports on-line check Veri. Sign Web site - allows for real-time checks 34

Ownership Issues n Running a CA takes resources • startup costs, capital costs • administrative resources • Additional insurance n Three options for running the CA: • Leverage existing CAs • Run your own CA / In-source the CA • Outsource to a third party 35

Leverage Existing CAs n n n Users already have certificates Your application accepts certs from other CAs Can be accomplished through: • cross-certification from local CA • acceptance of multiple certs within application • “web of trust” model 36

Leverage Existing CAs n Plenty of CAs out there • Users may already have certificates • Can leverage existing certificates n n User acceptance is higher However, • interoperability issues abound • CPSs may not be in tune • Trust levels may be different • Different extensions in use 37

Existing Root CAs n n n n n Veri. Sign hierarchy (4 classes) US Postal Service CA - pilot 1 Q 98 (? ) American Banking Association Digital Signature Trust Company Canada Post Commerce. Net RSA CAs (numerous) Keywitness Bel. Sign Thawte CA 38

Run your own CA n n Resource-intensive • Maintenance of CA system • Processing of registration info • Help-desk (24 x 7 or not? ) • Directory maintenance High-level of interaction among clients • Hard to manage large number of external users Storage-intensive Liability issues 39

Run your own CA n Consolidates internal applications • HR applications • Expense Voucher Systems • Benefits Applications n n Existing apps can be migrated Infrastructure in place for new applications 40

Existing CA products n n n n Veri. Sign Onsite Entrust/Server Entrust Web. CA, Entrust/Direct Microsoft Certificate Server Netscape Certificate Server Entegrity Web. Assure PGP Certificate Server Cert. Co Distributed Multi-Step Signing n n n Trade. Wave Trade. Authority GTE Cybertrust Motorola Cipher. Net System Xcert Software Sentry Baltimore Technologies Uni. Cert 41

Outsource the CA n Keep registration, outsource certification • Still have to do maintenance, lose power of signature • Will have to disclose client information to CA provider n Keep certification, outsource registration • Allows for widespread presence • Still maintain liability n Outsource both, maintain authority • Provider does all CA and RA maintenance • Applications are bound together by RA and sent to CA 42

CA Service Providers n n n n Veri. Sign On. Site GTE “Virtual CA” IBM “World Registry” Digital Signature Trust Entrust “in-sourcing” Tradewave “in-sourcing” “In-sourcing” growing in popularity 43

Certificate Directories n Lightweight Directory Access Protocol (LDAP) • runs on TCP/IP, new life into X. 500 n Gaining heavy industry support • Novell NDS • Microsoft, Netscape Directory Servers n Also included in client products • MSIE, Netscape Communicator • New Oak VPNs • etc. 44

Certificate Directories n n Assume directory is untrusted Certificates vouch for content Transport can be over untrusted channel X. 500 Standard • i. CL • ISOCOR • Control Data • X. 500 fits X. 509 certificates 45

Certificate Management Protocols n n n LDAP: certificate retrieval PKCS #10: certification requests S/MIME CRS: certification request syntax Cisco CMS: Certificate Management Syntax IETF CMP: Certificate Management Protocol (Entrust-based) 46

Certificate Management Protocols n n OCSP: On-line Certificate Status Protocol MIME types: • application/x-x 509 -user-cert: certificates • application/x-x 509 -ca-cert: CA certificate • more to come. . . n Netscape Certificate Extensions 47
Certificate Management Protocols n n n IETF PKIX • Part I: Certificate and CRL Profiles • Part III: Cert. Mgmt. Protocols (split into parts) • Part IV: Certificate Policy and Certification Practices Defines support for multiple transports: • HTTP, e-mail, TCP • OCSP: real-time certificate checks ANSI standards - Approved • X 9. 55 - Extensions to Public-Key Certificates and CRLs • X 9. 57 - Certificate Management In Ballot • X 9. 45 - Enhanced Mgmt. Controls using Attribute Certificates In Progress • X 9. 68 - Digital Certificates for High-Volume Financial Transactions 48
84103369d745d3702f1412a7b6e9586d.ppt