7fea7a0cb0a88073798b97020984297f.ppt
- Количество слайдов: 63

Certificate Systems, Public Key Infrastructures and Email Security 1
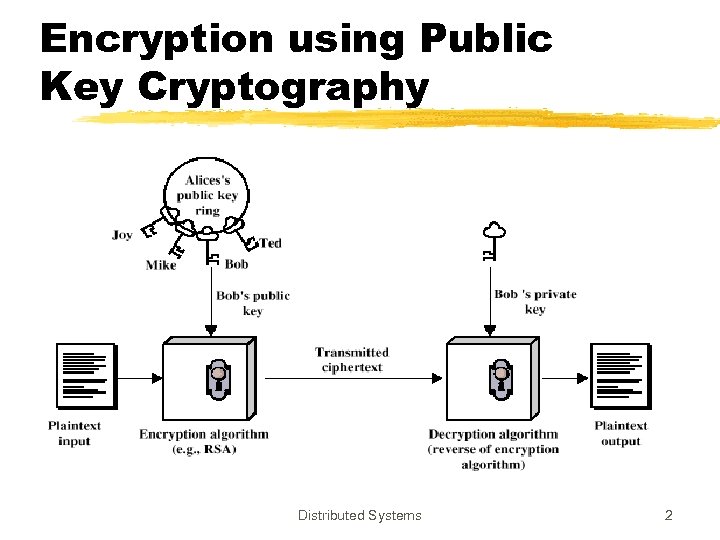
Encryption using Public Key Cryptography Distributed Systems 2
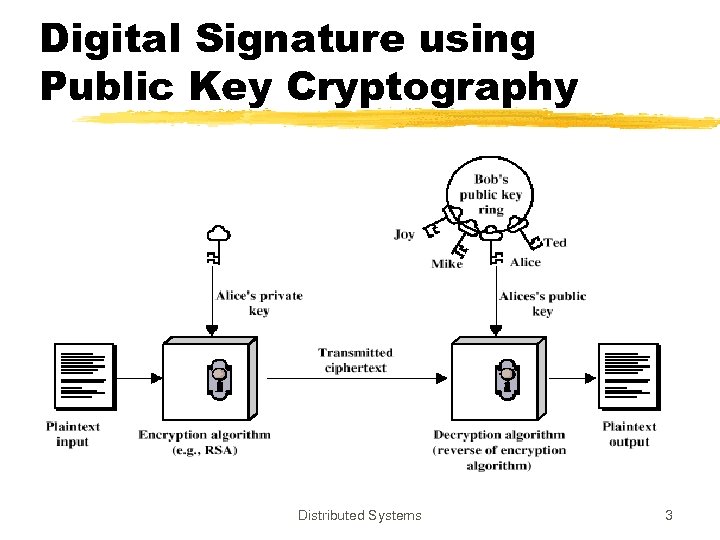
Digital Signature using Public Key Cryptography Distributed Systems 3
Public Key Distribution z. Finding out correct public key of an entity z. Possible attacks yname spoofing: a person can identify himself using a bogus name ydenial of service: the legitimate user cannot decrypt messages sent to him Distributed Systems 4

Public Key Distribution z. Face to face public key exchange ymost primitive, but secure method ynot convenient z. Public announcement yvia newsgroups, web pages, etc. ysubject to forgeries yhard to determine the liar Distributed Systems 5
Public Key Distribution z. Diffie - Hellman (1976) proposed the “public file” concept ypublic-key directory ycommonly accessible xshould be online always yno unauthorized modification ysecure and authenticated communication between directory and user is a must Distributed Systems 6

Public Key Distribution z. Popek - Kline (1979) proposed “trusted Public Key Authorities” y. Public key authorities know public keys of the entities and distribute them on-demand basis yon-line protocol (disadvantage) Distributed Systems 7
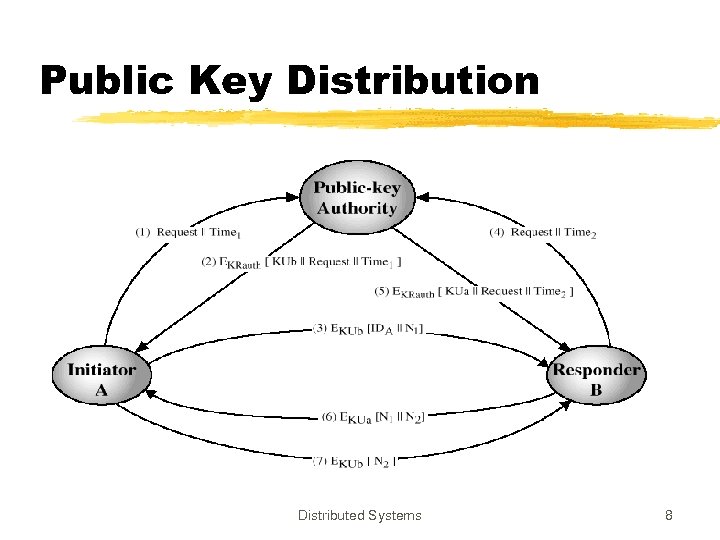
Public Key Distribution Distributed Systems 8

Certificates z. Kohnfelder (1978) proposed “certificates” as yet another public-key distribution method z. Binding between the public-key and its owner z. Issued (digitally signed) by the Certificate Authority (CA) z. Off-line process Distributed Systems 9

Certificates z. Certificates are verified by the verifiers to find out correct public key of the target entity z. In order to verify a certificate, the verifier ymust know the public key of the CA ymust trust the CA z. Certificate verification is the verification of the signature on certificate Distributed Systems 10
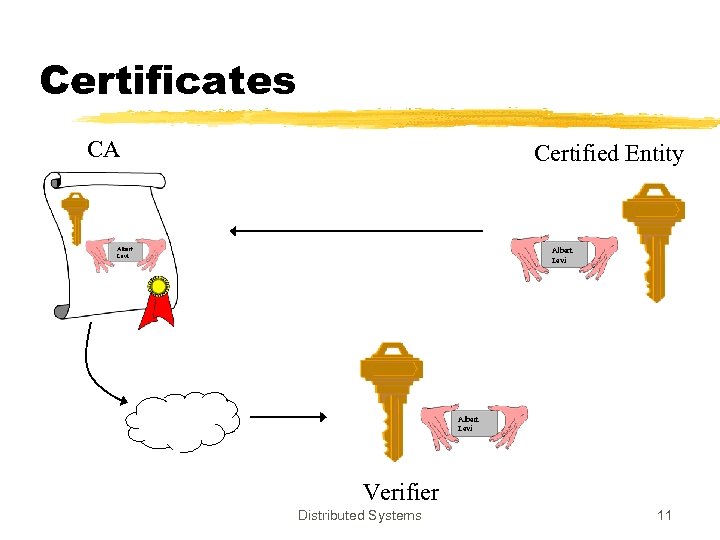
Certificates CA Certified Entity Albert Levi Verifier Distributed Systems 11
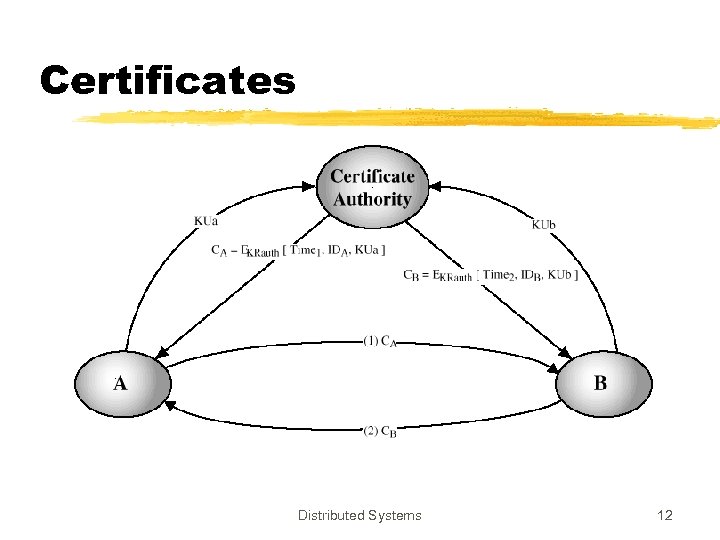
Certificates Distributed Systems 12

Issues Related Certificates z. CA certification policies (Certificate Practice Statement) yhow reliable is the CA? ycertification policies describe the methodology of certificate issuance y. ID-control practices xloose control: only email address xtight control: apply in person and submit picture IDs and/or hard documentation Distributed Systems 13

Issues Related Certificates z. TRUST yverifiers must trust CAs y. CAs need not trust the certified entities ycertified entity need not trust its CA, unless it is not the verifier z. What is “trust” in certification systems? y. Answer to the question: “How correct is the certificate information? ” yrelated to certification policies Distributed Systems 14
Issues Related Certificates z. Certificate types y. ID certificates (for authentication) xdiscussed here yauthorization certificates xno identity xbinding between public key and authorization info z. Certificate storage and distribution yalong with a signed message ydistributed directories ycentralized databases Distributed Systems 15
Issues Related Certificates z. Certificate Revocation ycertificates have lifetimes, but they may be revoked before the expiration time y. Reasons: xcertificate holder key compromise/lost x. CA key compromise xend of contract (e. g. certificates for employees) y. Certificate Revocation Lists (CRLs) hold the list of certificates that are not expired but revoked Distributed Systems 16

Real World Analogies z. Is a certificate an “electronic identity”? z. Concerns ya certificate is a binding between an identity and a key, not a binding between an identity and a real person yone must submit its certificate to identify itself, but submission is not sufficient, the key must be used in a protocol yanyone can submit someone else’s certificate Distributed Systems 17

Real World Analogies z. Result: Certificates are not picture IDs z. So, what is the real world analogy for certificates? y. Endorsed document/card that serves as a binding between the identity and signature yfor example, “credit-cards” Distributed Systems 18
Public Key Infrastructure (PKI) z. PKI is a complete system and defined mechanisms for certificates ycertificate issuance revocation storage distribution Distributed Systems 19

PKI z. Business Practice: Issue certificates and make money yseveral CAs z. Several CAs are also necessary due to political, geographical and trust reasons z 3 interconnection models yhierarchical ycross certificates yhybrid Distributed Systems 20
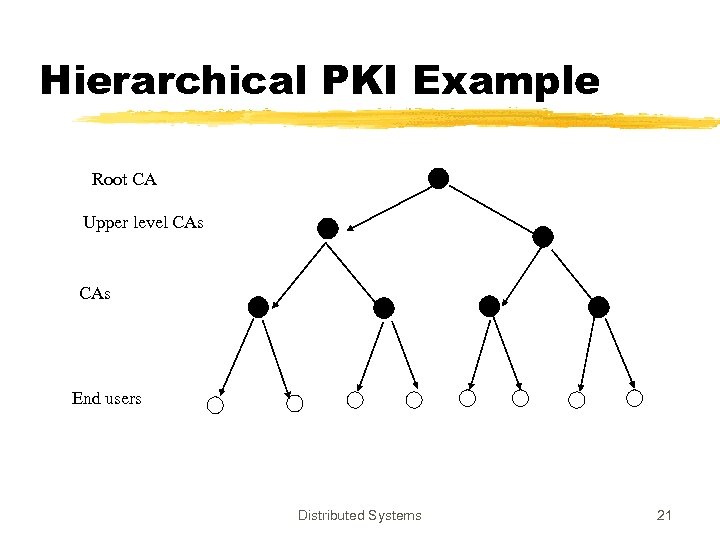
Hierarchical PKI Example Root CA Upper level CAs End users Distributed Systems 21
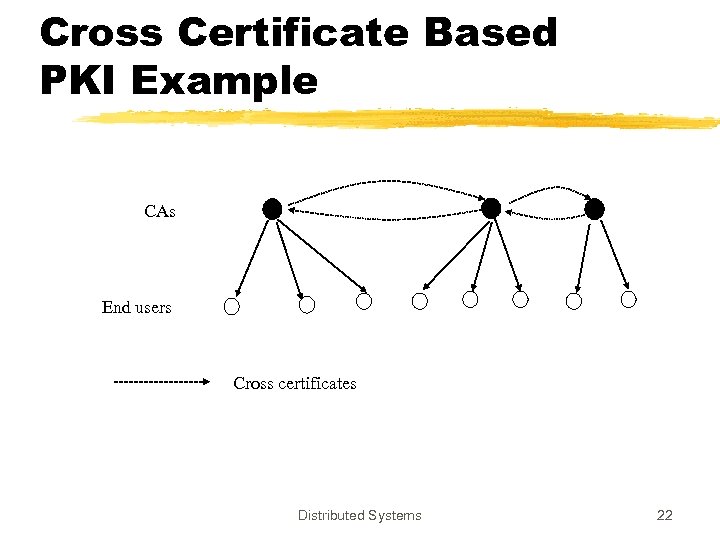
Cross Certificate Based PKI Example CAs End users Cross certificates Distributed Systems 22
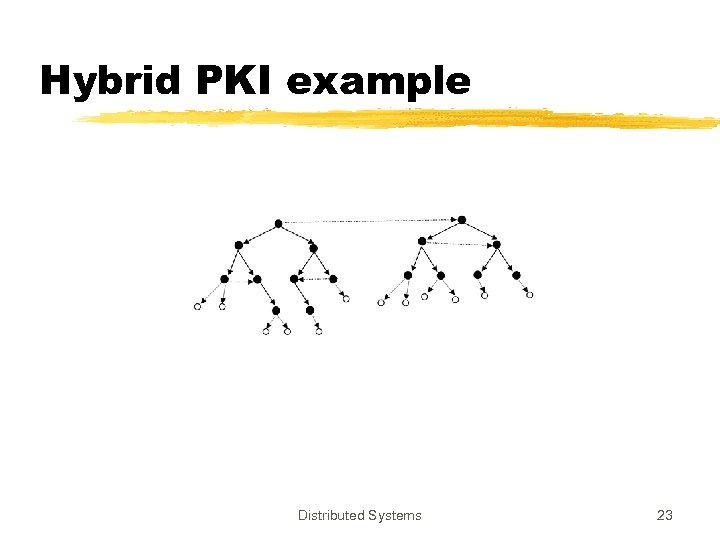
Hybrid PKI example Distributed Systems 23
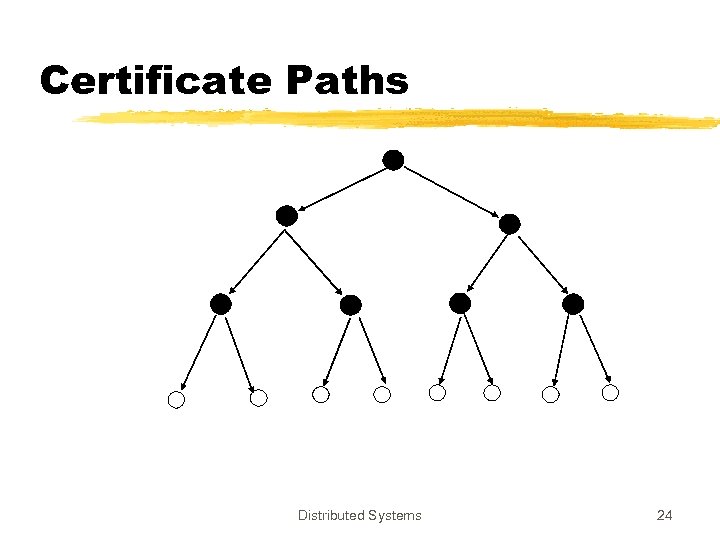
Certificate Paths Distributed Systems 24
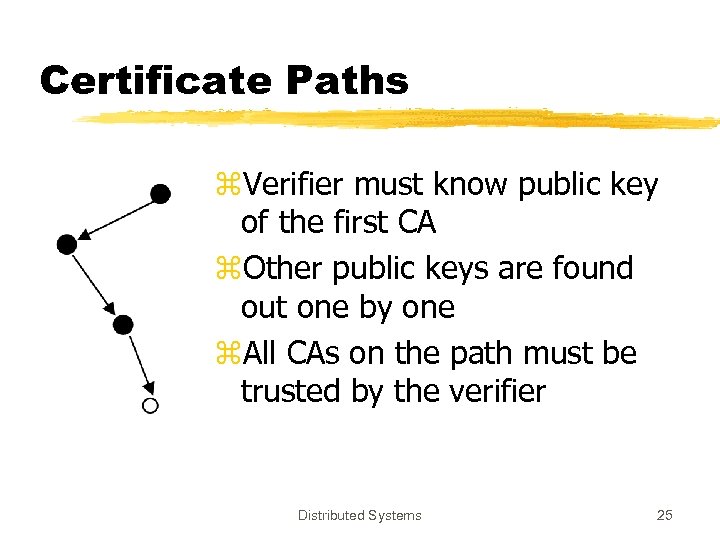
Certificate Paths z. Verifier must know public key of the first CA z. Other public keys are found out one by one z. All CAs on the path must be trusted by the verifier Distributed Systems 25
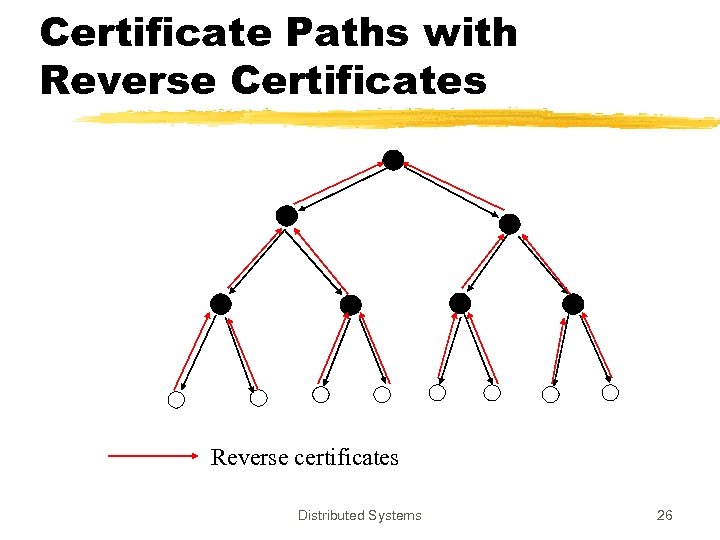
Certificate Paths with Reverse Certificates Reverse certificates Distributed Systems 26

Organization-wide PKI z. Local PKI for organizations ymay have global connections, but the registration facilities remain local yeasy to operate yless managerial difficulties Distributed Systems 27
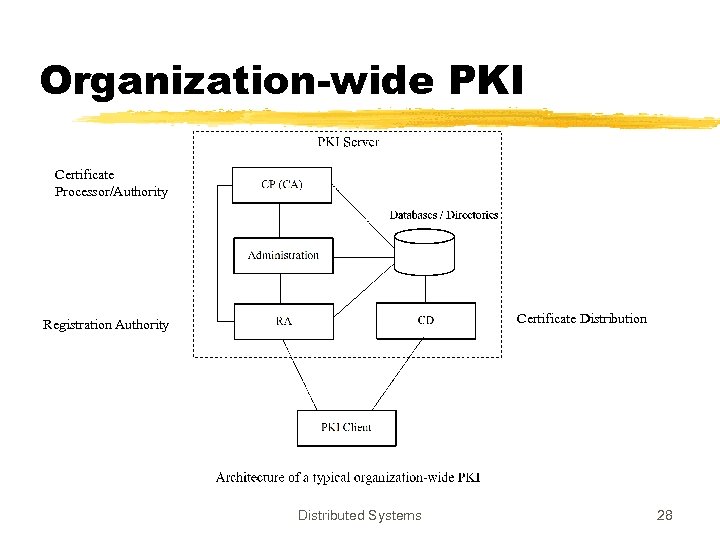
Organization-wide PKI Certificate Processor/Authority Certificate Distribution Registration Authority Distributed Systems 28
Hosted vs. Standalone PKI z. Hosted PKI y. PKI vendor acts as CA y. PKI owner is the RA z. Standalone PKI y. PKI owner is both RA and CA Distributed Systems 29
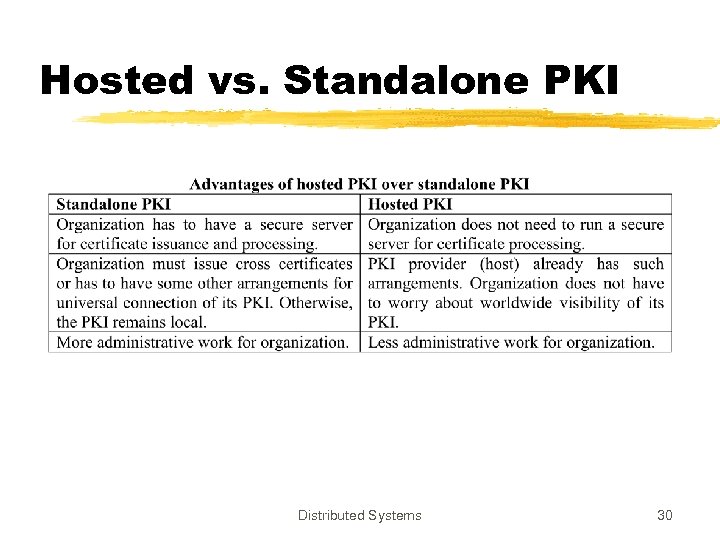
Hosted vs. Standalone PKI Distributed Systems 30
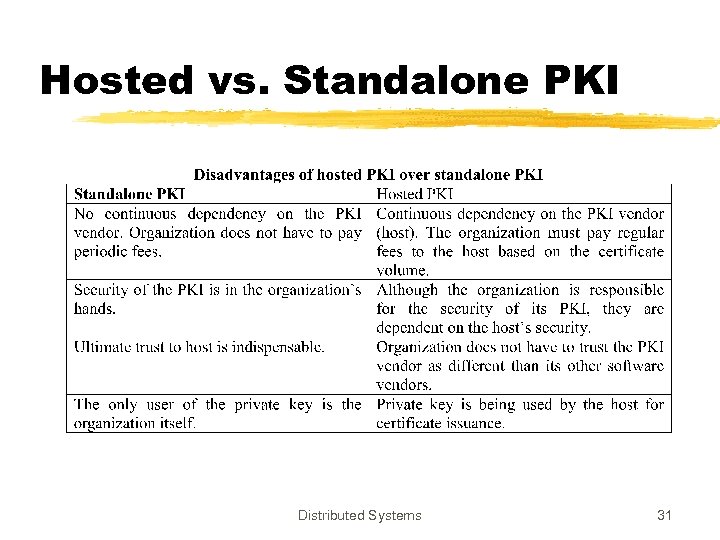
Hosted vs. Standalone PKI Distributed Systems 31
X. 509 z. ITU standard z. ISO 9495 -2 is the equivalent ISO standard z. Defines certificate structure, not PKI z. Also defines authentication protocols z. Identity certificates z. Supports both hierarchical model and cross certificates z. End users cannot be CAs Distributed Systems 32
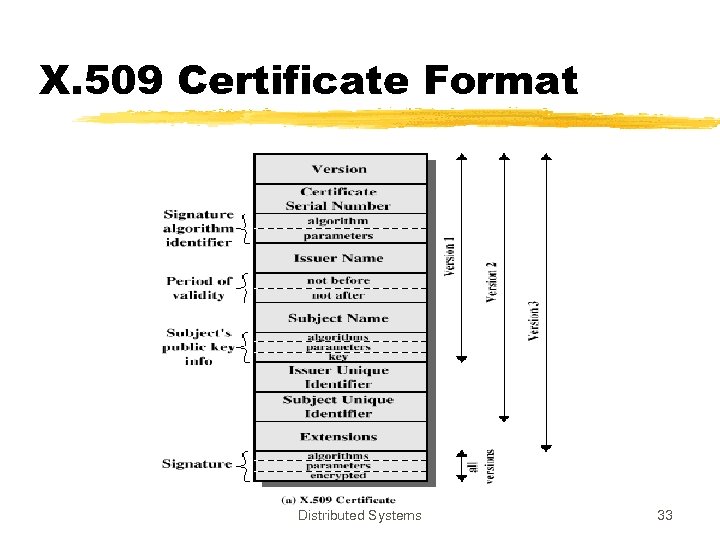
X. 509 Certificate Format Distributed Systems 33

X. 509 v 3 Extensions z. Alternative names z. Policy Identifiers y. Trust issue z. Restrictions based one ypath length ypolicy identifiers ynames z. No blind trust to CAs Distributed Systems 34

Some X. 509 based PKIs z. Privacy Enhanced Mail (PEM) yhierarchical, no cross certificates yfirst but discontinued z. Secure Electronic Transaction y. PKI for electronic payment ysecure but not widely deployed z. PKIX ygeneral purpose X. 509 based PKI Distributed Systems 35
DNSSEC z. Security extension to DNS z. Not X. 509 based, but hierarchical (uses existing DNS topology) z. Distributed z. Provides yauthentication of domain information ystorage and distribution of certificates z. Good and practical system Distributed Systems 36
SSL (Secure Socket Layer) z. Security layer over TCP/IP zmostly for HTTP connections zencrypted and authenticated sessions between web servers and web browsers (clients) z. Not a perfect solution, but a convenient solution Distributed Systems 37

SSL (Secure Socket Layer) z. Certificate based systems yweb servers must have certificate yclient certificate is optional z. CA certificates are embedded in browsers z. You trust them (by default), because browser company says so ! z. The worst, but the most practical !!! Distributed Systems 38

Using SSL for HTTP Connections z. By using SSL we can ymake sure about the server’s name (assuming the CA of the server is trusted) xauthentication ymake sure that nobody can see the traffic between client and server xconfidentiality Distributed Systems 39
Using SSL for HTTP Connections z. By using SSL we can NOT yprovide perfect privacy xserver sees all information that client provides ximportant in e-payment: merchant sees the card number and name yprovide non-repudiation xboth parties knows the session key xin e-payment: charge-back cost for merchant’s Distributed Systems 40

PGP (Pretty Good Privacy) z. Effort of Phil Zimmermann z. Strong cryptography yfree of government control z. Has not started as a standardization effort z. Controversial international version z. Most widely used security software z. Unique certificate and PKI Distributed Systems 41

PGP (Pretty Good Privacy) z. Free personal use z. Source code available yvery important for “paranoids” z. Multi-platform software z. Basically “file” encryption/signing software z. Now it has plug-ins for some E-mail client programs Distributed Systems 42
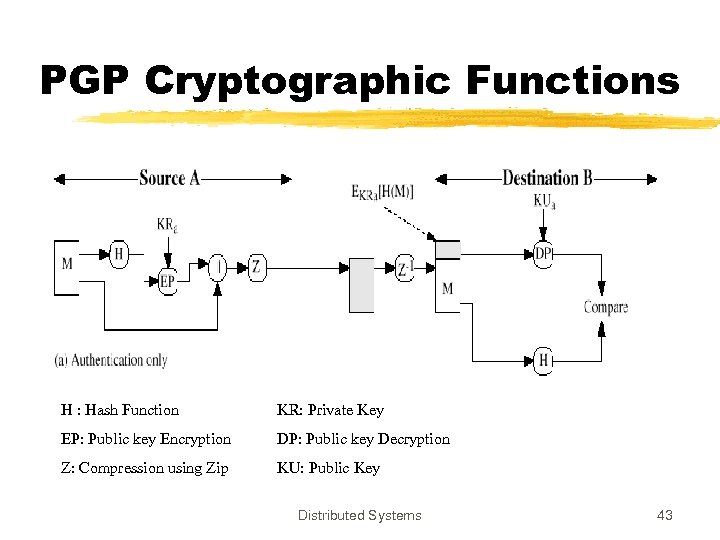
PGP Cryptographic Functions H : Hash Function KR: Private Key EP: Public key Encryption DP: Public key Decryption Z: Compression using Zip KU: Public Key Distributed Systems 43
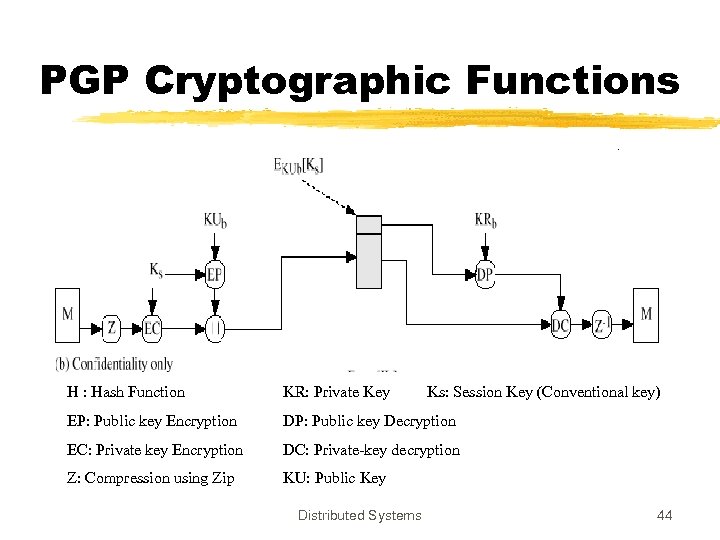
PGP Cryptographic Functions H : Hash Function KR: Private Key EP: Public key Encryption DP: Public key Decryption EC: Private key Encryption DC: Private-key decryption Z: Compression using Zip KU: Public Key Distributed Systems Ks: Session Key (Conventional key) 44
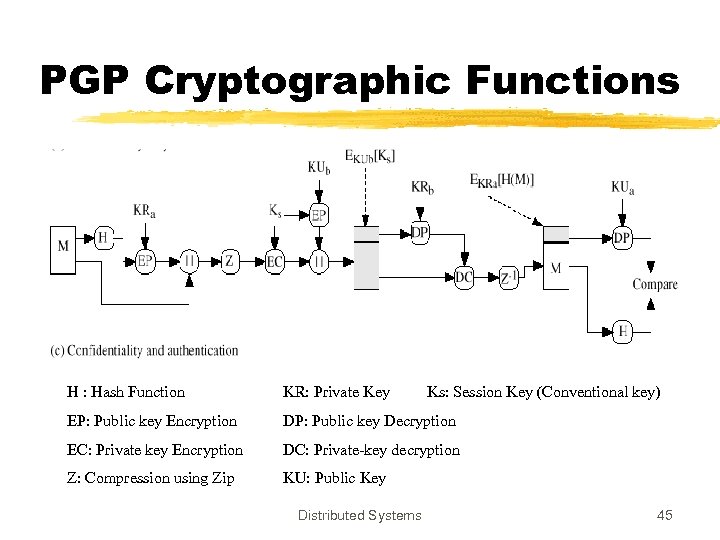
PGP Cryptographic Functions H : Hash Function KR: Private Key EP: Public key Encryption DP: Public key Decryption EC: Private key Encryption DC: Private-key decryption Z: Compression using Zip KU: Public Key Distributed Systems Ks: Session Key (Conventional key) 45
Encoding in PGP z. Binary data must be encoded for e-mail compatibility z. Radix-64 conversion ybinary data is grouped 6 -bit by 6 -bit yeach 6 -bit group is converted to a printable ASCII character (table look-up) yinflates the data 33% y. Radix-64 applied to after encryption/signing Distributed Systems 46
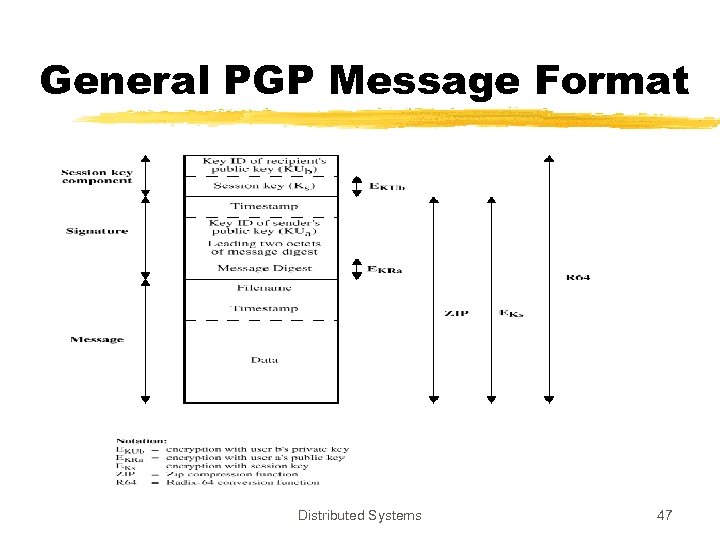
General PGP Message Format Distributed Systems 47

Key Management in PGP z. Public keys are not attached to messages z. Instead Public key identifiers are put in messages z. Recipient should know/find out sender’s public-key ypersonal exchange y. PGP public key servers xdo not trust the authenticity of the keys there Distributed Systems 48

Key Management in PGP z 2 local “Key Rings” yprivate key ring xto keep your private keys ypublic key ring xto keep yours and other people’s public keys Distributed Systems 49

Private Key Ring z. Private-key Ring is a table for the private keys z. Private keys are stored in encrypted form y. Encryption key is derived from passphrase z. The keys in private-key ring are ultimately trusted z. Question: How can we determine whether or not correct passphrase is entered? Distributed Systems 50

Public-key Ring z. Table for locally known public keys z. Also contains trust information y. PGP user specifies his/her trusted CAs xtwo levels of trusts to CAs ybeing in public-key ring does not mean its legitimacy xa public-key signed by a key in private-key ring is legit xotherwise CAs signatures are checked • complicated scheme Distributed Systems 51
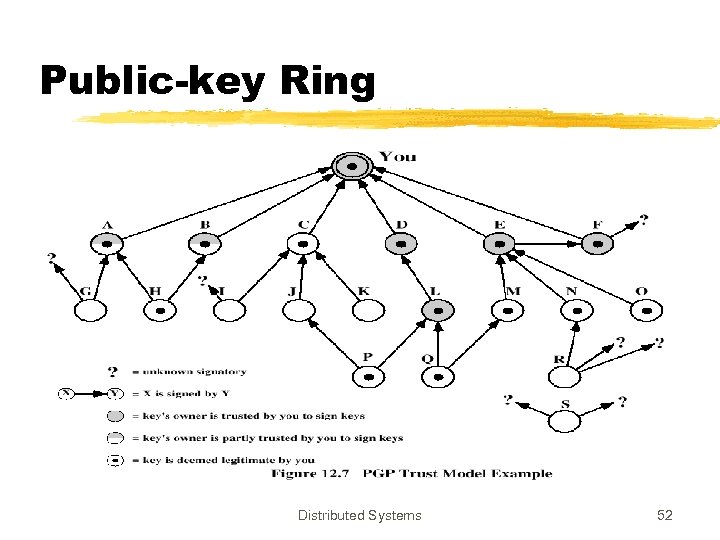
Public-key Ring Distributed Systems 52

PKI of PGP z. Global public-key ring z. PKI from scratch z. Public-keys are certificates are posted in public-key servers z. Thousands of users z. No boss, no governing body Distributed Systems 53
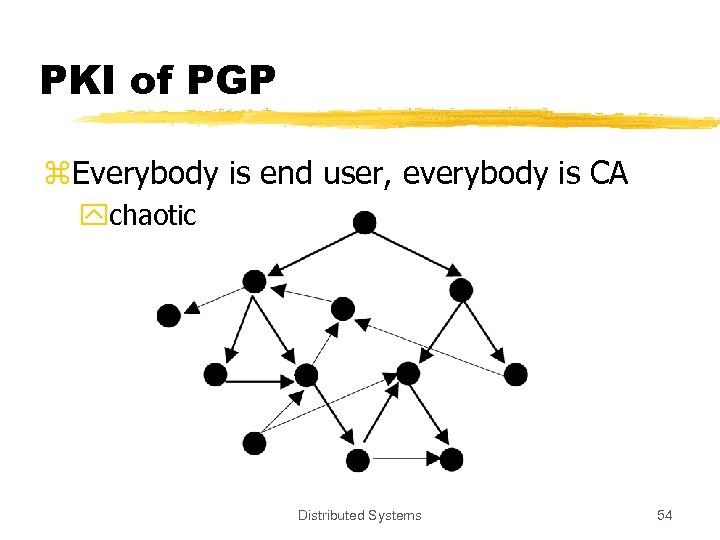
PKI of PGP z. Everybody is end user, everybody is CA ychaotic Distributed Systems 54

S/MIME z. A standard way for email encryption and signing z. IETF standard z. Industry support ycommercial reasons z. Not a standalone software, a system that is to be supported by email clients Distributed Systems 55

History of E-mail z. RFC 822 yonly ASCII messages z. MIME (Multipurpose Internet Mail Extensions) ycontent type x. Almost any of information can appear in an email message z. S/MIME: Secure MIME xnew content types, like signature, encrypted data Distributed Systems 56
S/MIME z. General functionality is similar to PGP ydigital signature xthe hash of message is signed yencrypted data (enveloped data) xa conventional session key is used to encrypt the data xthat key is encrypted by the recipient’s public key z. The difference between S/MIME and PGP is certificate management Distributed Systems 57

Certificate Management in S/MIME z. CA-centered system like SSL z. An ordinary user is not aware of the CAs that he/she trusts z. CA certificates come with the client software z. Certificates are sent along with the signed messages in S/MIME (unlike PGP) Distributed Systems 58

Certificate Management in S/MIME z. One should get a certificate from a CA in order to send signed messages z. Verisign Certificates y. Class 1 y. Class 2 y. Class 3 Increased Security Harder to issue Distributed Systems 59

What’s Wrong? z. Loose control for Class 1 certificates for commercial reasons yvisibility ymarket share z. The system becomes less secure for the name of security Distributed Systems 60

What should be done? z. Class 1 certificates must be discontinued z. All certificate must be issued with a personal presence requirement or by the approval of trusted registration authorities Distributed Systems 61

Discussion on Personal Certificates (SSL) z. Certificates ruin your privacy z. Do you really need a certificate? y. Do you want to get caught when you are at a specific website? y. Do you want spammers to get your email address? y. Do you want companies to learn your favorites? Distributed Systems 62

Discussion on Personal Certificates (S/MIME) z. There is no wide use of certificates z. Only few email clients are supporting S/MIME z. Interoperability problems among the email client programs Distributed Systems 63
7fea7a0cb0a88073798b97020984297f.ppt