e7ed7fa40c2019b71a6d4591c9a144d9.ppt
- Количество слайдов: 18
 Certificate Profile Revisited ‘certificates considered harmful’ David Groep, TAGPMA Ottawa meeting, July 2006
Certificate Profile Revisited ‘certificates considered harmful’ David Groep, TAGPMA Ottawa meeting, July 2006
 Brief History and Background · In the Beginning was Mike Helm · Grid Certificate Extensions Profile (CAOPS-WG Community Practice Doc) · March 2003 (GGF 10) · List of attributes/extensions and their associated questions · Was probably too early, and did not progress much (due to lack of community interest at the time? ) · Growth of the CA distribution and Grid deployment · without practical guidance for CAs · many extensions used (or omitted), inconsistent use · ‘liberal’ interpretation of relevant standards (both by the CAs and by middleware) David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 2
Brief History and Background · In the Beginning was Mike Helm · Grid Certificate Extensions Profile (CAOPS-WG Community Practice Doc) · March 2003 (GGF 10) · List of attributes/extensions and their associated questions · Was probably too early, and did not progress much (due to lack of community interest at the time? ) · Growth of the CA distribution and Grid deployment · without practical guidance for CAs · many extensions used (or omitted), inconsistent use · ‘liberal’ interpretation of relevant standards (both by the CAs and by middleware) David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 2
 Some examples: serial. Number. RDN · serial. Number RDN attribute in the subject name · originally supposed to be a hardware s/n · standard meaning extended to include unique identifiers also for persons · one un-named CA managed to convince Open. CA to have the certificate s/n embedded in the subject DN ! (so much for renew/rekey with the same DN …) · Attribute also suffered name confusion in Open. SSL · Open. SSL <= 0. 9. 7? : OID represented as “SN” (sic!) · Opens. SSL > 0. 9. 7? : represented as “serial. Number” (correct) · since typical DN comparison in the grid is based on the string representation · subscriber is left frustrated · issue is raised over and over again in grid support channels · the CA package distributor (me) get complaints for “non-functioning CAs” David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 3
Some examples: serial. Number. RDN · serial. Number RDN attribute in the subject name · originally supposed to be a hardware s/n · standard meaning extended to include unique identifiers also for persons · one un-named CA managed to convince Open. CA to have the certificate s/n embedded in the subject DN ! (so much for renew/rekey with the same DN …) · Attribute also suffered name confusion in Open. SSL · Open. SSL <= 0. 9. 7? : OID represented as “SN” (sic!) · Opens. SSL > 0. 9. 7? : represented as “serial. Number” (correct) · since typical DN comparison in the grid is based on the string representation · subscriber is left frustrated · issue is raised over and over again in grid support channels · the CA package distributor (me) get complaints for “non-functioning CAs” David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 3
 Some examples: LDAP server certs · some clients (in this case Open. LDAP) check for the appropriate extensions in the server cert · extended. Key. Usage: server. Auth OR ns. Cert. Type: server · one of these must be present, or open. LDAP will fail · but some grid middleware can live without having either set, and then allow all usage (setting either attribute but not allowing server use correctly makes the middleware reject such a server, though) · so it’s not obvious to CAs to they should include extended. Key. Usage, since the EE certs initially ‘appear to work’ David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 4
Some examples: LDAP server certs · some clients (in this case Open. LDAP) check for the appropriate extensions in the server cert · extended. Key. Usage: server. Auth OR ns. Cert. Type: server · one of these must be present, or open. LDAP will fail · but some grid middleware can live without having either set, and then allow all usage (setting either attribute but not allowing server use correctly makes the middleware reject such a server, though) · so it’s not obvious to CAs to they should include extended. Key. Usage, since the EE certs initially ‘appear to work’ David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 4
 Aims · Document · described each relevant attribute/extension · what is does (be it good or harm) to the major pieces of (grid) software · guidance for new CAs · define (for already accredited CAs) what must be changed · also: make clear to our software development community where we expect the software to actually adhere to standards · Initial draft out there. Planned updates: · rewrite to use RFC 2119 language everywhere · cover more attributes/extensions · Groep – davidg@eugridpma. org David example and input on what actually works and is in use - 5 Cert Profile, TAGPMA Ottawa – July 2006
Aims · Document · described each relevant attribute/extension · what is does (be it good or harm) to the major pieces of (grid) software · guidance for new CAs · define (for already accredited CAs) what must be changed · also: make clear to our software development community where we expect the software to actually adhere to standards · Initial draft out there. Planned updates: · rewrite to use RFC 2119 language everywhere · cover more attributes/extensions · Groep – davidg@eugridpma. org David example and input on what actually works and is in use - 5 Cert Profile, TAGPMA Ottawa – July 2006
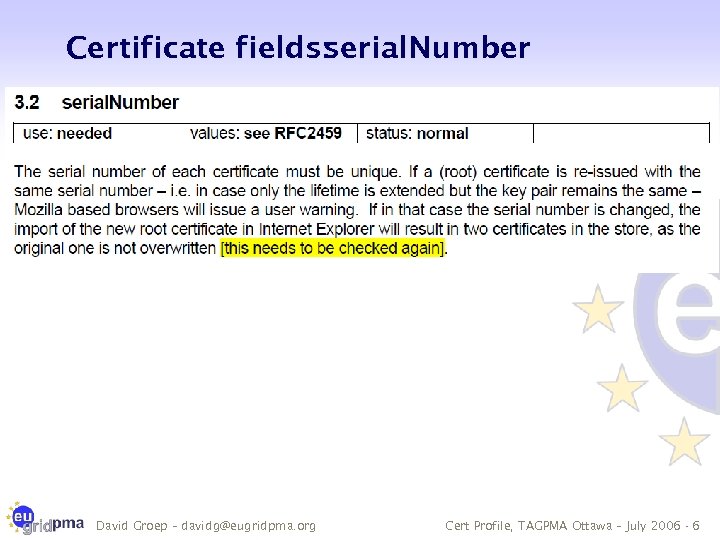 Certificate fields: serial. Number David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 6
Certificate fields: serial. Number David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 6
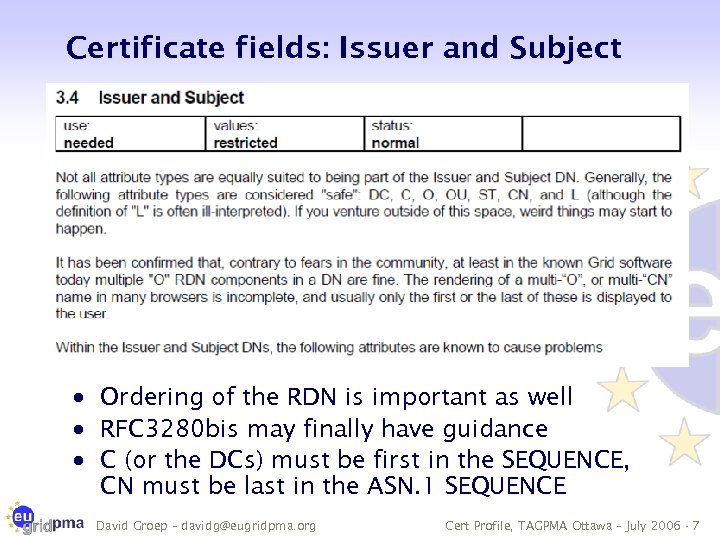 Certificate fields: Issuer and Subject · Ordering of the RDN is important as well · RFC 3280 bis may finally have guidance · C (or the DCs) must be first in the SEQUENCE, CN must be last in the ASN. 1 SEQUENCE David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 7
Certificate fields: Issuer and Subject · Ordering of the RDN is important as well · RFC 3280 bis may finally have guidance · C (or the DCs) must be first in the SEQUENCE, CN must be last in the ASN. 1 SEQUENCE David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 7
 Subject, Issuer ordering · New 3280 bis draft might have some guidance · anyway, never start the SEQUENCE with CN … David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 8
Subject, Issuer ordering · New 3280 bis draft might have some guidance · anyway, never start the SEQUENCE with CN … David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 8
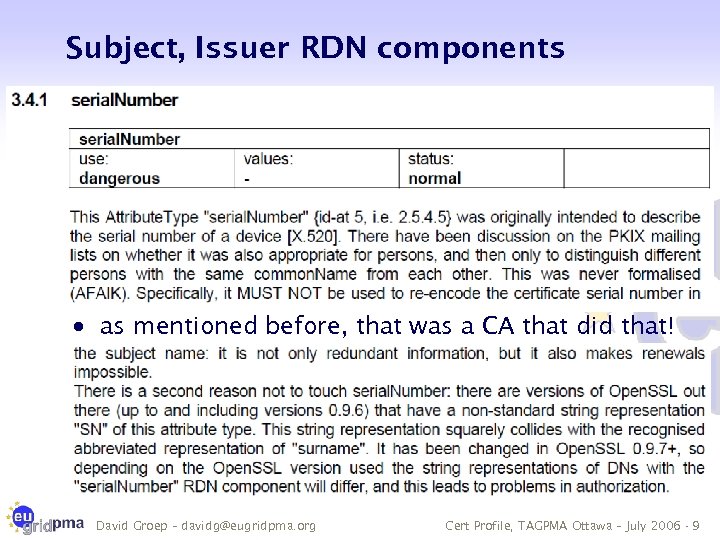 Subject, Issuer RDN components · as mentioned before, that was a CA that did that! David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 9
Subject, Issuer RDN components · as mentioned before, that was a CA that did that! David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 9
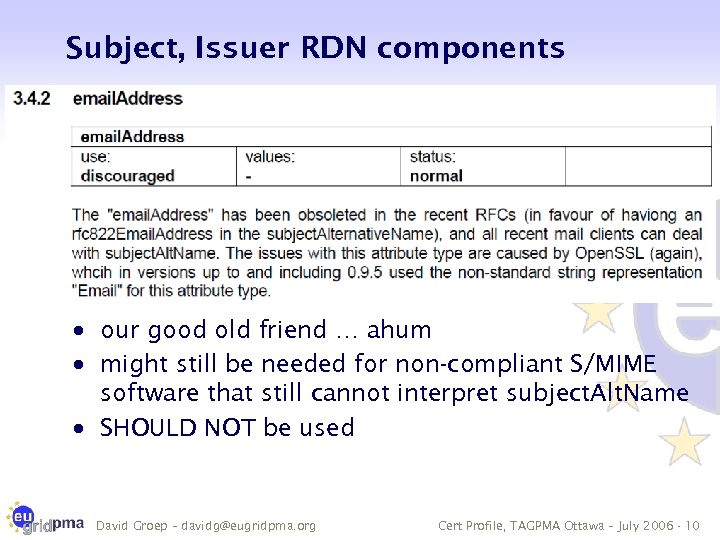 Subject, Issuer RDN components · our good old friend … ahum · might still be needed for non-compliant S/MIME software that still cannot interpret subject. Alt. Name · SHOULD NOT be used David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 10
Subject, Issuer RDN components · our good old friend … ahum · might still be needed for non-compliant S/MIME software that still cannot interpret subject. Alt. Name · SHOULD NOT be used David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 10
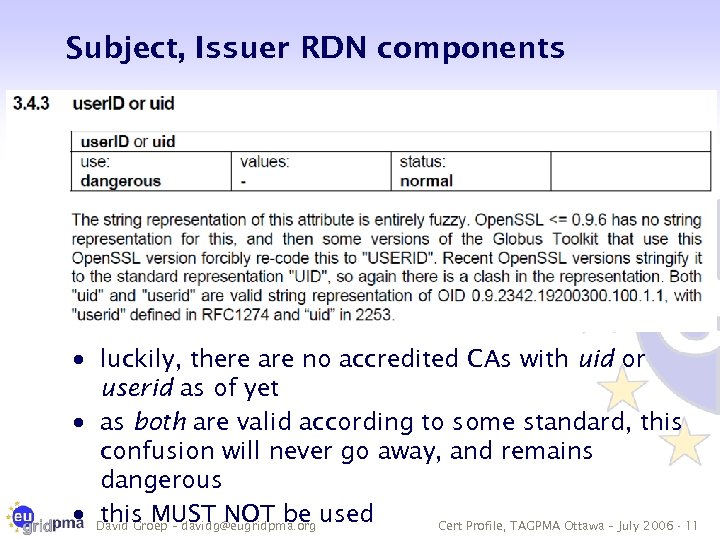 Subject, Issuer RDN components · luckily, there are no accredited CAs with uid or userid as of yet · as both are valid according to some standard, this confusion will never go away, and remains dangerous · David Groep – davidg@eugridpma. org used this MUST NOT be Cert Profile, TAGPMA Ottawa – July 2006 - 11
Subject, Issuer RDN components · luckily, there are no accredited CAs with uid or userid as of yet · as both are valid according to some standard, this confusion will never go away, and remains dangerous · David Groep – davidg@eugridpma. org used this MUST NOT be Cert Profile, TAGPMA Ottawa – July 2006 - 11
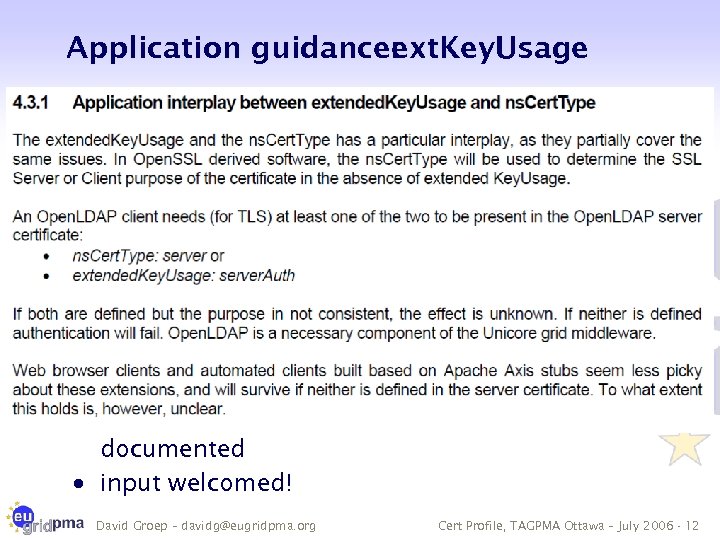 Application guidance: ext. Key. Usage · more of these will be there, and should be documented · input welcomed! David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 12
Application guidance: ext. Key. Usage · more of these will be there, and should be documented · input welcomed! David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 12
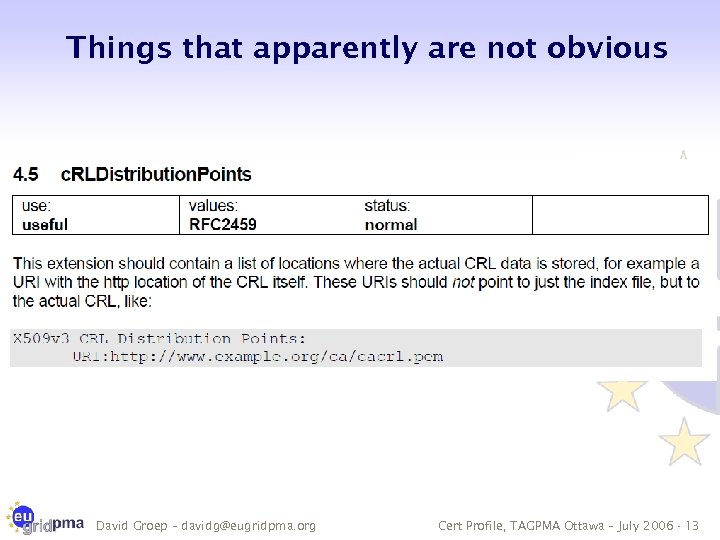 Things that apparently are not obvious David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 13
Things that apparently are not obvious David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 13
 Venturing into Java may reveal unexpected quirks David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 14
Venturing into Java may reveal unexpected quirks David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 14
 Guidance · CA root/subordinate certificates · best to keep minimal · basic. Constraints = critical, CA: TRUE · key. Usage = critical, key. Cert. Sign, c. RLSign · that’s all that is actually needed · policy oid looks nice, but will certainly become out-ofdate soon · CRL Distribution Points is intended for EE certs David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 15
Guidance · CA root/subordinate certificates · best to keep minimal · basic. Constraints = critical, CA: TRUE · key. Usage = critical, key. Cert. Sign, c. RLSign · that’s all that is actually needed · policy oid looks nice, but will certainly become out-ofdate soon · CRL Distribution Points is intended for EE certs David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 15
 Guidance EE certificates · needed by profile or software · basic. Constraints = critical, CA: FALSE (but …) · key. Usage = critical, digital. Signature, key. Encipherment, data. Encipherment (digital Signature needed for, e. g. S/MIME rekeying mails) · c. RLDistribution. Points with a URL · certificate. Policies: at least one OID, but more in the near future (for the IGTF AP, 1 SCPs, …) · extended. Key. Usage = {client, server}Auth (or ns. Cert. Type=SSL{Server, Client}, but that one is obsolete) needed for, e. g. Open. LDAP · more extended. Key. Usage might be needed or useful for user certs, more testing is required David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 16
Guidance EE certificates · needed by profile or software · basic. Constraints = critical, CA: FALSE (but …) · key. Usage = critical, digital. Signature, key. Encipherment, data. Encipherment (digital Signature needed for, e. g. S/MIME rekeying mails) · c. RLDistribution. Points with a URL · certificate. Policies: at least one OID, but more in the near future (for the IGTF AP, 1 SCPs, …) · extended. Key. Usage = {client, server}Auth (or ns. Cert. Type=SSL{Server, Client}, but that one is obsolete) needed for, e. g. Open. LDAP · more extended. Key. Usage might be needed or useful for user certs, more testing is required David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 16
 To do · document is certainly not complete · v 0. 4 (on the web soon) has been updated to better reflect the 3280 bis draft · much more input needed · text · but also application testing · in-depth discussion on a complete draft @ GGF 18? David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 17
To do · document is certainly not complete · v 0. 4 (on the web soon) has been updated to better reflect the 3280 bis draft · much more input needed · text · but also application testing · in-depth discussion on a complete draft @ GGF 18? David Groep – davidg@eugridpma. org Cert Profile, TAGPMA Ottawa – July 2006 - 17
 · Q&D
· Q&D


