64615a8a61a29d555a7a8d027d825e4d.ppt
- Количество слайдов: 27

Certicom Mobile. Trust™: PKI for Mobile and Wireless Systems John Kennedy Director of PKI Product Marketing jkennedy@certicom. com April, 2000

Presentation Overview • Wireless and Mobile PKI Requirements, Demand, and Growth Opportunity • Certicom’s Mobile. Trust™ Initiative • Open Challenges

Certicom’s Mission Security for mobile e-business Certicom enables mobile e-commerce and ebusiness applications like shopping, banking, brokerage, email, payments, and healthcare

Market Size Mobile market growth is phenomenal u $66 b in wireless e-commerce in 2003 (IDC) u 1 b mobile phones by 2003
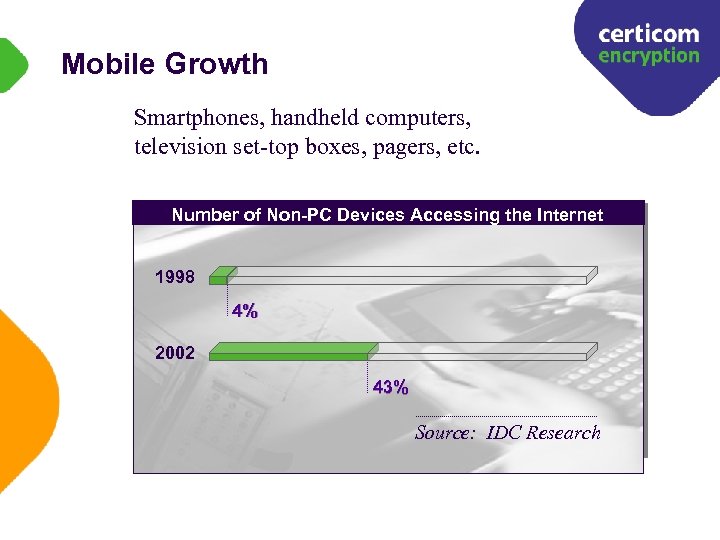
Mobile Growth Smartphones, handheld computers, television set-top boxes, pagers, etc. Number of Non-PC Devices Accessing the Internet 1998 4% 2002 43% Source: IDC Research

Mobile Enterprise Connectivity Objective: Extend enterprise data to a mobile sales force Motivation: u u u Faster feedback Better decisions Lower costs Challenges: u u u The best info is the most sensitive Existing data frameworks Form factors

Wireless e-Commerce Objective: Enable banking, stock trading, and online shopping anywhere and any time. Motivation: u u u PC use saturated at 30% Availability = more transactions Service differentiation n n Consumer impulse buying Trader alerts Challenges: u u Fraud (user authentication) Privacy (consumer behavior tracking)

Mobile Devices Objective: Web-enable the rest of the world Motivation: u u u Non-PC Web devices expected to reach 43% by 2002 New services, transaction-based revenues Customer loyalty and management Challenges u u u Low cost, low margin devices Need the same security as PCs Require better packaging, reliability and support than PCs

Where is strong authentication and user accountability needed? • • Secure Stock Trading On-line Banking Enterprise Data Access. Secure Messaging Healthcare Mobile Lifestyle, Personal Info Mobile phones, pagers, and PDA’s will be platforms of choice.

Certicom Security Solutions for Mobile Environments • ECC-based signing from mobile devices in wireless networks. • ECC-based security protocols with strong server and strong client authentication.

Certicom Mobile Security Technology Licensees Palm Computing Avant. Go Puma Riverbed Advance Systems Extended Systems Confinity Infowave Qualcomm RIM 724 Solutions Aether Systems Newcom e. Physician i. Scribe Planet. RX Sybase Bell South Motorola JP Systems

Certicom OEM Customer Requirements • “We love your ECC-based crypto and security protocol technology. ” • “We want the PKI-based identity management infrastructure. ” • “PKI is too expensive or too complicated to build ourselves. ” • If we build it, they will come…

Mobile. Trust™ Goals • Mobile. Trust™ announced Jan. 2000 • Deliver a full suite of PKI products and services for mobile and wireless markets. • Develop a set of ECC-based certification authorities. • Address an unaddressed market with tremendous growth potential.
Certicom PKI Product Set Mobile. Trust™ u u Outsourced Certification Authority (CA) service Accompanied by semi-custom RA, client/server toolkits, PKI integration services Trustpoint® PKI Technology Base u u PKI toolkits for OEM developers CA, RA, EE, RP applications and components in Java and C++

Mobile. Trust™ - Complete Mobile Security Solutions Mobile. Trust CA Service u Run by Certicom for OEM customers, service operators, enterprises and end users Mobile. Trust RA Platform u Run by enterprise to administer certificates. Calls on Mobile. Trust CA to issue certificates Client and Server Security Toolkits u PKI Clients (EE/RP functions), SSL Plus, WTLS Plus, and other Certicom security products. Mobile. Trust PKI Integration Services u Expert consulting and PKI Integration to fit Mobile. Trust to existing business logic and information systems
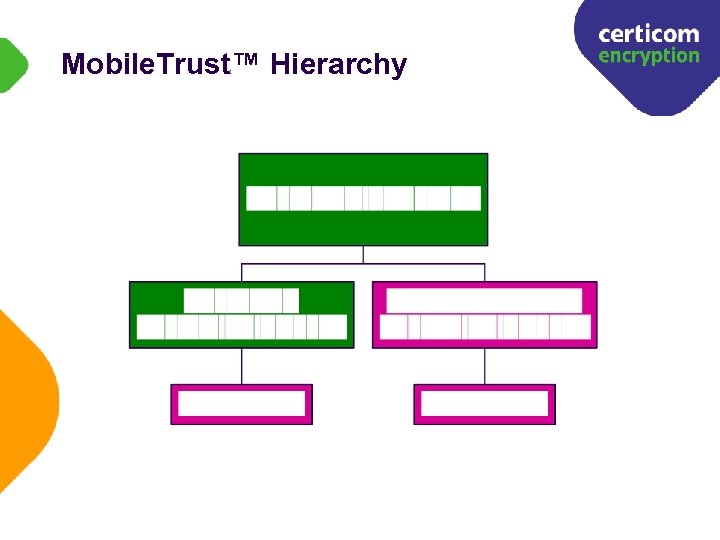
Mobile. Trust™ Hierarchy
Mobile. Trust Features Standards compliance u ANSI X 9. 62 ECDSA (signature standard) u IETF PKIX (X. 509, CMP, CRMF) u WAP PKI (cert profiles, protocols) u LDAP-accessible repositories

Mobile. Trust Features (continued) Assurance u SAS-70 (service reliability audit) u FIPS 140 -1 Level 3, 4 (security environment) u NIST and ABA ISC PKI Security Guidelines

Mobile. Trust Features (continued) Interoperability u u u Is “Interoperable Security Components” an oxymoron? Customer want to choose best-of-class PKI components. PKI investment preservation. Interoperability is good for overall PKI market growth. Interoperability cost/value not always wellunderstood. Participation in PKI Forum, Radicchio, other fora.

Mobile. Trust Features (continued) Scalability u u u Immediate need is server certificates Long-term emphasis is on client certificates We anticipate 100: 1 - 1000: 1 ratio of client certificates to server certificates. Scalability requirements drive database, directory, and RA distributability needs. Mobile. Trust being designed to handle 100 million certificates/year.

Mobile. Trust™ Registration Authorities • Based upon Trustpoint™ CA/RA Java Beanbased policy engine architecture. • Anticipates need for customization to accommodate unique identity capture and vetting requirements • Communicates with end-entities using PKIX CMP, WAP, and PKCS-10 based protocols

PKI Client GUI - security icons, locks, etc. Security Protocols: *E-commerce wallet *SSL Plus *Text Signing *IPSEC Plus *WTLS Plus Certificate Protocols: *Palm VII OPP Request, Revoke, Renew Basic Cryptography: Key Store: ECC, RSA, DES, RC 4, SHA 1, Secret keys and Certificates etc

PKI Client Platforms Palm platform devices u Palm, Nokia, Sony, TRG, Handspring Cell Phones Paging devices u RIM, Bellsouth networks Embedded Systems

Mobile PKI Special Requirements • Ultra-thin clients, mobile code • Integration with wireless-friendly security protocols. (e. g. , WTLS) • Roaming identity services • Platform and channel heterogeneity.

Mobile Security Challenges • Better authentication protocols u User assertive -- mutual authentication by default. • Client authentication at multiple layers. • End-point security: secure O/S, trusted path, platform integrity. • End-to-end security instead of gateways and proxies. • Secure audit capability at client.
Mobile. Trust™ Summary Managed Certificate Services Features u u u CA Service for industry standard elliptic curve certificates Benefits u u 100% Java-based RA platform Compatibility with SSL Plus and WTLS Plus products PKI client software for handhelds OEM and Enterprise integration services u Guaranteed PKI service: 24 x 7 operation Signed business transactions on mobile systems in wireless networks Rapid time-to-market for mobile e-business applications

Questions?
64615a8a61a29d555a7a8d027d825e4d.ppt