c07cc564615a57b7f19c72ac50e5f0e9.ppt
- Количество слайдов: 25
 CD Lifecycle & Data Spill Solutions Omar J. Fakhri Ph: (727) 505 -4701 1
CD Lifecycle & Data Spill Solutions Omar J. Fakhri Ph: (727) 505 -4701 1
 Overview • Need • Scalable Solutions – Phase I Cradle-to-Grave Lifecycle CD Tracking; a. Authenticate & Issue b. Authenticate & Transfer c. Authenticate & Destroy – Phase II Secure Storage Of CDs – Phase III Spill-Resistant Network With Bar-coding a. General User Desktops b. Communal desktops with Same-Level CD burning c. Five-Step Process for High-Low Data Transfer • Wrap up 2
Overview • Need • Scalable Solutions – Phase I Cradle-to-Grave Lifecycle CD Tracking; a. Authenticate & Issue b. Authenticate & Transfer c. Authenticate & Destroy – Phase II Secure Storage Of CDs – Phase III Spill-Resistant Network With Bar-coding a. General User Desktops b. Communal desktops with Same-Level CD burning c. Five-Step Process for High-Low Data Transfer • Wrap up 2
 FBI Strategic Objective: IVA. 1 Protect the FBI from compromise of its employees. “Security and counterintelligence professionals generally agree that the most significant threat to an organization’s internal security is betrayal by a trusted insider. ” (Page 84) The Webster Commission’s Report “…The FBI should study the feasibility of bar coding particularly sensitive classified material, such as asset files, to facilitate control and tracking. ” (Page 78) 3
FBI Strategic Objective: IVA. 1 Protect the FBI from compromise of its employees. “Security and counterintelligence professionals generally agree that the most significant threat to an organization’s internal security is betrayal by a trusted insider. ” (Page 84) The Webster Commission’s Report “…The FBI should study the feasibility of bar coding particularly sensitive classified material, such as asset files, to facilitate control and tracking. ” (Page 78) 3
 Phase I Cradle-to-Grave Lifecycle CD Tracking • Phase I a. Authenticate & Issue • Phase I b. Authenticate & Transfer • Phase I c. Authenticate & Destroy 4
Phase I Cradle-to-Grave Lifecycle CD Tracking • Phase I a. Authenticate & Issue • Phase I b. Authenticate & Transfer • Phase I c. Authenticate & Destroy 4
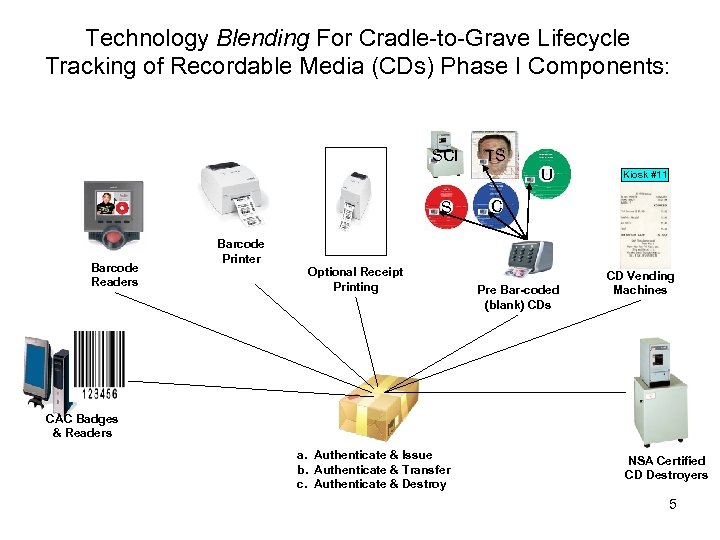 Technology Blending For Cradle-to-Grave Lifecycle Tracking of Recordable Media (CDs) Phase I Components: SCI TS U S Barcode Readers Kiosk #11 C Barcode Printer Optional Receipt Printing Pre Bar-coded (blank) CDs CD Vending Machines CAC Badges & Readers a. Authenticate & Issue b. Authenticate & Transfer c. Authenticate & Destroy NSA Certified CD Destroyers 5
Technology Blending For Cradle-to-Grave Lifecycle Tracking of Recordable Media (CDs) Phase I Components: SCI TS U S Barcode Readers Kiosk #11 C Barcode Printer Optional Receipt Printing Pre Bar-coded (blank) CDs CD Vending Machines CAC Badges & Readers a. Authenticate & Issue b. Authenticate & Transfer c. Authenticate & Destroy NSA Certified CD Destroyers 5
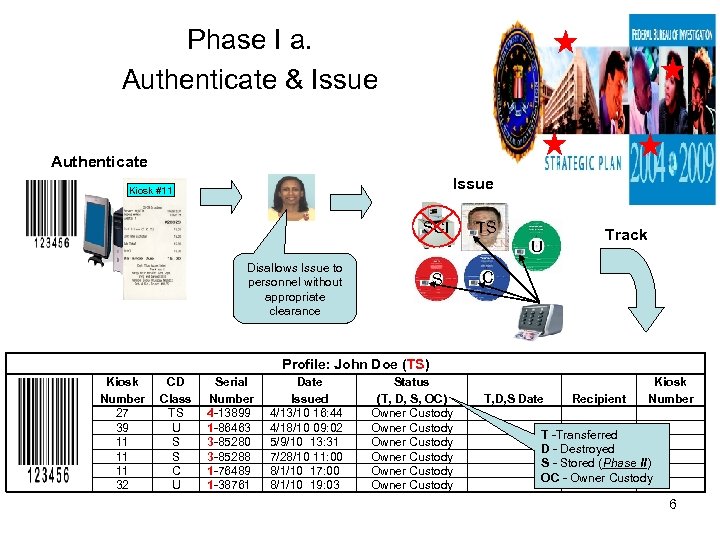 Phase I a. Authenticate & Issue Authenticate Issue Kiosk #11 SCI TS U Disallows Issue to personnel without appropriate clearance S Track C Profile: John Doe (TS) Kiosk Number 27 39 11 11 11 32 CD Class TS U S S C U Serial Number 4 -13899 1 -86463 3 -85280 3 -85288 1 -76489 1 -38761 Date Issued 4/13/10 16: 44 4/18/10 09: 02 5/9/10 13: 31 7/28/10 11: 00 8/1/10 17: 00 8/1/10 19: 03 Status (T, D, S, OC) Owner Custody Owner Custody T, D, S Date Recipient Kiosk Number T -Transferred D - Destroyed S - Stored (Phase II) OC - Owner Custody 6
Phase I a. Authenticate & Issue Authenticate Issue Kiosk #11 SCI TS U Disallows Issue to personnel without appropriate clearance S Track C Profile: John Doe (TS) Kiosk Number 27 39 11 11 11 32 CD Class TS U S S C U Serial Number 4 -13899 1 -86463 3 -85280 3 -85288 1 -76489 1 -38761 Date Issued 4/13/10 16: 44 4/18/10 09: 02 5/9/10 13: 31 7/28/10 11: 00 8/1/10 17: 00 8/1/10 19: 03 Status (T, D, S, OC) Owner Custody Owner Custody T, D, S Date Recipient Kiosk Number T -Transferred D - Destroyed S - Stored (Phase II) OC - Owner Custody 6
 Phase I Cradle-to-Grave Lifecycle CD Tracking • Phase I a. Authenticate & Issue • Phase I b. Authenticate & Transfer • Phase I c. Authenticate & Destroy 7
Phase I Cradle-to-Grave Lifecycle CD Tracking • Phase I a. Authenticate & Issue • Phase I b. Authenticate & Transfer • Phase I c. Authenticate & Destroy 7
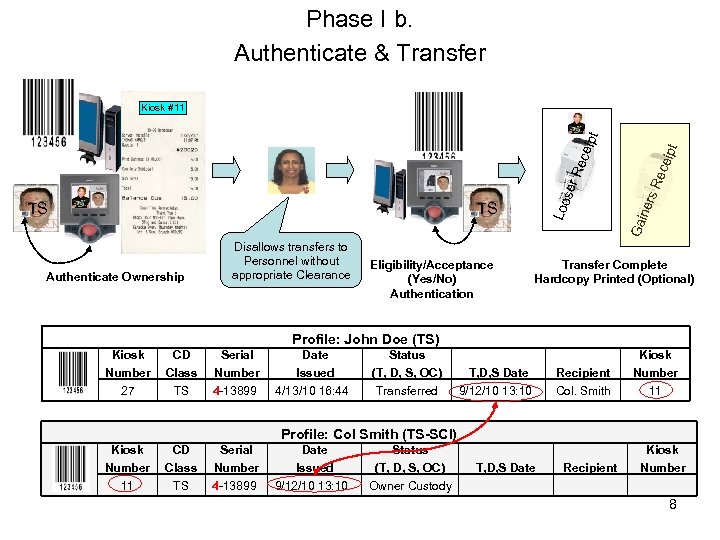 Phase I b. Authenticate & Transfer Authenticate Ownership Disallows transfers to Personnel without appropriate Clearance Eligibility/Acceptance (Yes/No) Authentication ece rs R ine Ga TS Loo TS ser Rec e ipt Kiosk #11 Transfer Complete Hardcopy Printed (Optional) Profile: John Doe (TS) Kiosk Number 27 CD Class TS Serial Number 4 -13899 Date Issued 4/13/10 16: 44 Status (T, D, S, OC) Transferred T, D, S Date 9/12/10 13: 10 Recipient Col. Smith Kiosk Number 11 Profile: Col Smith (TS-SCI) Kiosk Number 11 CD Class TS Serial Number 4 -13899 Date Issued 9/12/10 13: 10 Status (T, D, S, OC) Owner Custody T, D, S Date Recipient Kiosk Number 8
Phase I b. Authenticate & Transfer Authenticate Ownership Disallows transfers to Personnel without appropriate Clearance Eligibility/Acceptance (Yes/No) Authentication ece rs R ine Ga TS Loo TS ser Rec e ipt Kiosk #11 Transfer Complete Hardcopy Printed (Optional) Profile: John Doe (TS) Kiosk Number 27 CD Class TS Serial Number 4 -13899 Date Issued 4/13/10 16: 44 Status (T, D, S, OC) Transferred T, D, S Date 9/12/10 13: 10 Recipient Col. Smith Kiosk Number 11 Profile: Col Smith (TS-SCI) Kiosk Number 11 CD Class TS Serial Number 4 -13899 Date Issued 9/12/10 13: 10 Status (T, D, S, OC) Owner Custody T, D, S Date Recipient Kiosk Number 8
 Phase I Cradle-to-Grave Lifecycle CD Tracking • Phase I a. Authenticate & Issue • Phase I b. Authenticate & Transfer • Phase I c. Authenticate & Destroy 9
Phase I Cradle-to-Grave Lifecycle CD Tracking • Phase I a. Authenticate & Issue • Phase I b. Authenticate & Transfer • Phase I c. Authenticate & Destroy 9
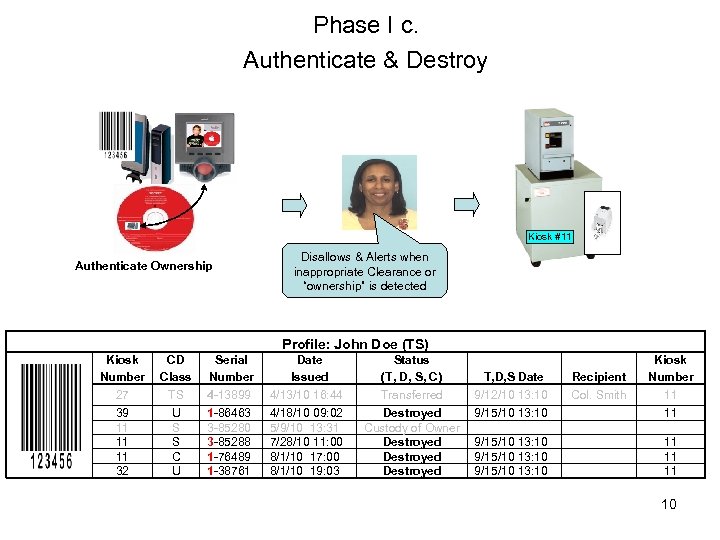 Phase I c. Authenticate & Destroy Kiosk #11 Authenticate Ownership Disallows & Alerts when inappropriate Clearance or “ownership” is detected Profile: John Doe (TS) Kiosk Number 27 39 11 11 11 32 CD Class TS U S S C U Serial Number 4 -13899 1 -86463 3 -85280 3 -85288 1 -76489 1 -38761 Date Issued 4/13/10 16: 44 4/18/10 09: 02 5/9/10 13: 31 7/28/10 11: 00 8/1/10 17: 00 8/1/10 19: 03 Status (T, D, S, C) Transferred Destroyed Custody of Owner Destroyed T, D, S Date 9/12/10 13: 10 9/15/10 13: 10 Recipient Col. Smith Kiosk Number 11 11 11 10
Phase I c. Authenticate & Destroy Kiosk #11 Authenticate Ownership Disallows & Alerts when inappropriate Clearance or “ownership” is detected Profile: John Doe (TS) Kiosk Number 27 39 11 11 11 32 CD Class TS U S S C U Serial Number 4 -13899 1 -86463 3 -85280 3 -85288 1 -76489 1 -38761 Date Issued 4/13/10 16: 44 4/18/10 09: 02 5/9/10 13: 31 7/28/10 11: 00 8/1/10 17: 00 8/1/10 19: 03 Status (T, D, S, C) Transferred Destroyed Custody of Owner Destroyed T, D, S Date 9/12/10 13: 10 9/15/10 13: 10 Recipient Col. Smith Kiosk Number 11 11 11 10
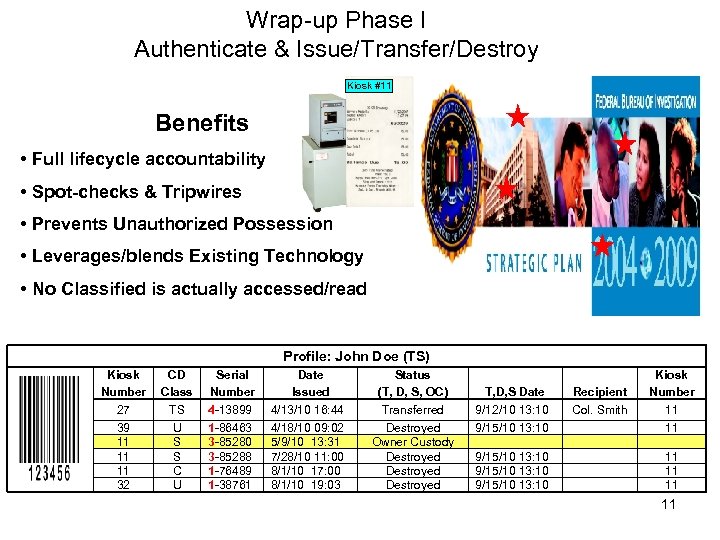 Wrap-up Phase I Authenticate & Issue/Transfer/Destroy Kiosk #11 Benefits • Full lifecycle accountability • Spot-checks & Tripwires • Prevents Unauthorized Possession • Leverages/blends Existing Technology • No Classified is actually accessed/read Profile: John Doe (TS) Kiosk Number 27 39 11 11 11 32 CD Class TS U S S C U Serial Number 4 -13899 1 -86463 3 -85280 3 -85288 1 -76489 1 -38761 Date Issued 4/13/10 16: 44 4/18/10 09: 02 5/9/10 13: 31 7/28/10 11: 00 8/1/10 17: 00 8/1/10 19: 03 Status (T, D, S, OC) Transferred Destroyed Owner Custody Destroyed T, D, S Date 9/12/10 13: 10 9/15/10 13: 10 Recipient Col. Smith Kiosk Number 11 11 11
Wrap-up Phase I Authenticate & Issue/Transfer/Destroy Kiosk #11 Benefits • Full lifecycle accountability • Spot-checks & Tripwires • Prevents Unauthorized Possession • Leverages/blends Existing Technology • No Classified is actually accessed/read Profile: John Doe (TS) Kiosk Number 27 39 11 11 11 32 CD Class TS U S S C U Serial Number 4 -13899 1 -86463 3 -85280 3 -85288 1 -76489 1 -38761 Date Issued 4/13/10 16: 44 4/18/10 09: 02 5/9/10 13: 31 7/28/10 11: 00 8/1/10 17: 00 8/1/10 19: 03 Status (T, D, S, OC) Transferred Destroyed Owner Custody Destroyed T, D, S Date 9/12/10 13: 10 9/15/10 13: 10 Recipient Col. Smith Kiosk Number 11 11 11
 Phase II Storage 12
Phase II Storage 12
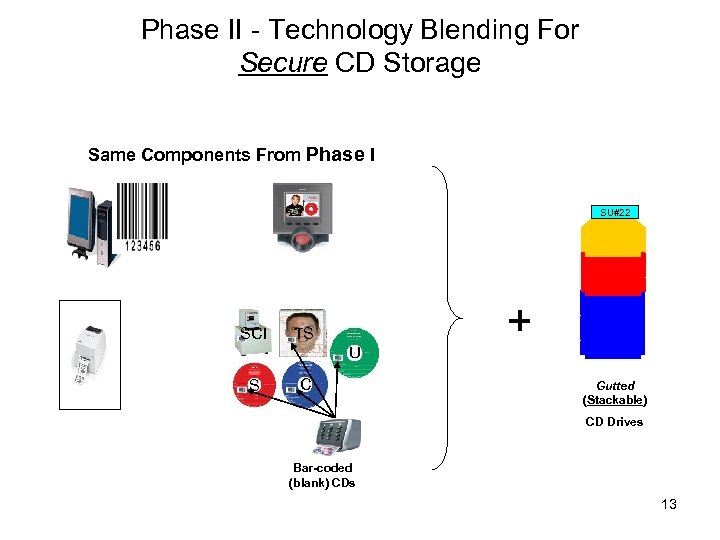 Phase II - Technology Blending For Secure CD Storage Same Components From Phase I SU#22 SCI TS U S C + Gutted (Stackable) CD Drives Bar-coded (blank) CDs 13
Phase II - Technology Blending For Secure CD Storage Same Components From Phase I SU#22 SCI TS U S C + Gutted (Stackable) CD Drives Bar-coded (blank) CDs 13
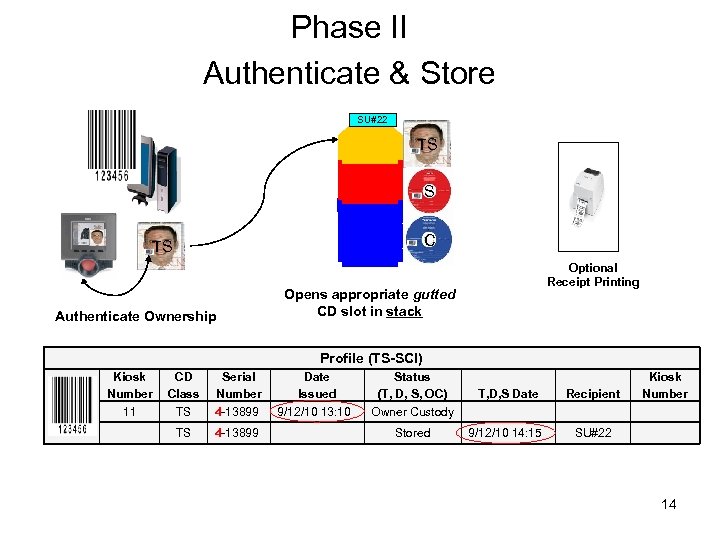 Phase II Authenticate & Store SU#22 TS S C TS Authenticate Ownership Optional Receipt Printing Opens appropriate gutted CD slot in stack Profile (TS-SCI) Kiosk Number 11 CD Class TS Serial Number 4 -13899 TS 4 -13899 Date Issued 9/12/10 13: 10 Status (T, D, S, OC) Owner Custody T, D, S Date Recipient Stored 9/12/10 14: 15 Kiosk Number SU#22 14
Phase II Authenticate & Store SU#22 TS S C TS Authenticate Ownership Optional Receipt Printing Opens appropriate gutted CD slot in stack Profile (TS-SCI) Kiosk Number 11 CD Class TS Serial Number 4 -13899 TS 4 -13899 Date Issued 9/12/10 13: 10 Status (T, D, S, OC) Owner Custody T, D, S Date Recipient Stored 9/12/10 14: 15 Kiosk Number SU#22 14
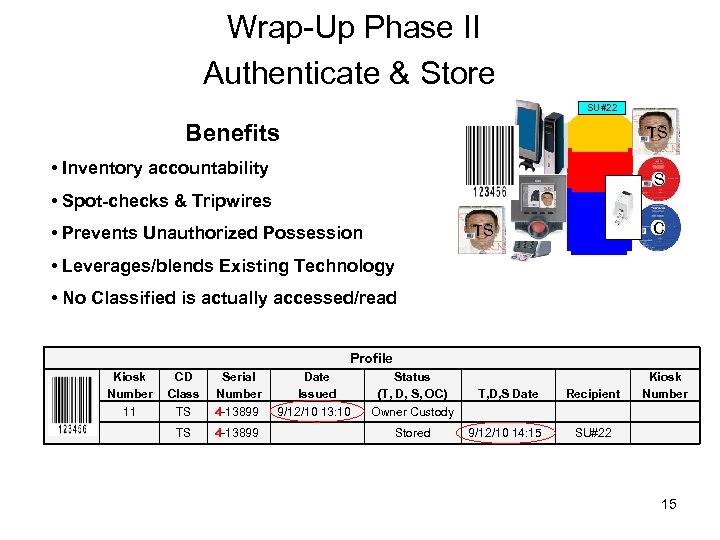 Wrap-Up Phase II Authenticate & Store SU#22 Benefits TS • Inventory accountability S • Spot-checks & Tripwires C TS • Prevents Unauthorized Possession • Leverages/blends Existing Technology • No Classified is actually accessed/read Profile Kiosk Number 11 CD Class TS Serial Number 4 -13899 TS 4 -13899 Date Issued 9/12/10 13: 10 Status (T, D, S, OC) Owner Custody T, D, S Date Recipient Stored 9/12/10 14: 15 Kiosk Number SU#22 15
Wrap-Up Phase II Authenticate & Store SU#22 Benefits TS • Inventory accountability S • Spot-checks & Tripwires C TS • Prevents Unauthorized Possession • Leverages/blends Existing Technology • No Classified is actually accessed/read Profile Kiosk Number 11 CD Class TS Serial Number 4 -13899 TS 4 -13899 Date Issued 9/12/10 13: 10 Status (T, D, S, OC) Owner Custody T, D, S Date Recipient Stored 9/12/10 14: 15 Kiosk Number SU#22 15
 Phase III Spill-Resistant Network 16
Phase III Spill-Resistant Network 16
 Phase III Spill-Resistant Network All CD Readers and CD Writers Require Barcode Reader to Access Drive a. General User Desktop CD Readers Integrated With Barcode Reader b. Communal Desktops with Same-Level CD Burners c. Centralized High-Low CD Burner Process a. , b. , & c. should be deployed together 17
Phase III Spill-Resistant Network All CD Readers and CD Writers Require Barcode Reader to Access Drive a. General User Desktop CD Readers Integrated With Barcode Reader b. Communal Desktops with Same-Level CD Burners c. Centralized High-Low CD Burner Process a. , b. , & c. should be deployed together 17
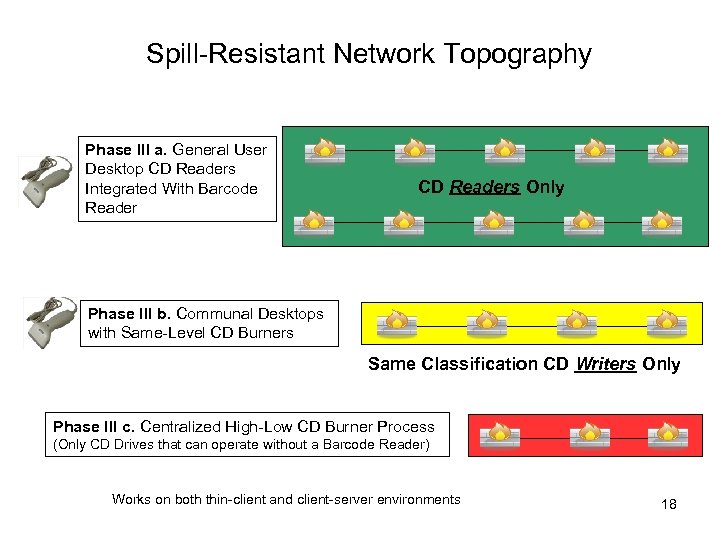 Spill-Resistant Network Topography Phase III a. General User Desktop CD Readers Integrated With Barcode Reader CD Readers Only Phase III b. Communal Desktops with Same-Level CD Burners Same Classification CD Writers Only Phase III c. Centralized High-Low CD Burner Process (Only CD Drives that can operate without a Barcode Reader) Works on both thin-client and client-server environments 18
Spill-Resistant Network Topography Phase III a. General User Desktop CD Readers Integrated With Barcode Reader CD Readers Only Phase III b. Communal Desktops with Same-Level CD Burners Same Classification CD Writers Only Phase III c. Centralized High-Low CD Burner Process (Only CD Drives that can operate without a Barcode Reader) Works on both thin-client and client-server environments 18
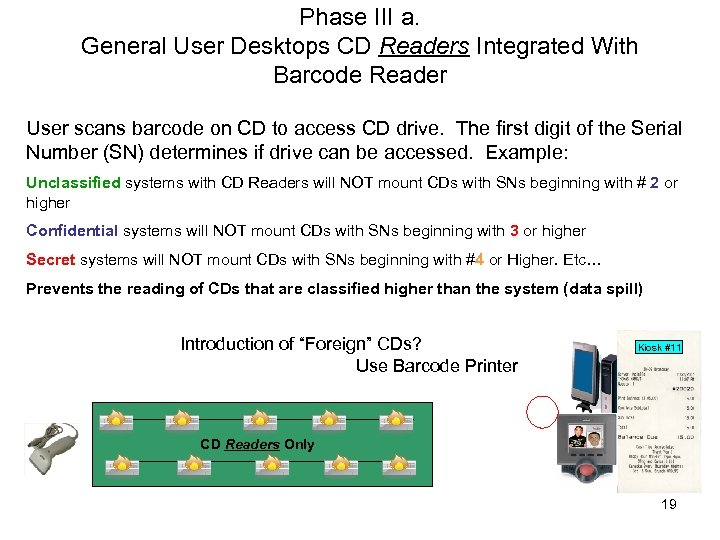 Phase III a. General User Desktops CD Readers Integrated With Barcode Reader User scans barcode on CD to access CD drive. The first digit of the Serial Number (SN) determines if drive can be accessed. Example: Unclassified systems with CD Readers will NOT mount CDs with SNs beginning with # 2 or higher Confidential systems will NOT mount CDs with SNs beginning with 3 or higher Secret systems will NOT mount CDs with SNs beginning with #4 or Higher. Etc… Prevents the reading of CDs that are classified higher than the system (data spill) Introduction of “Foreign” CDs? Use Barcode Printer Kiosk #11 CD Readers Only 19
Phase III a. General User Desktops CD Readers Integrated With Barcode Reader User scans barcode on CD to access CD drive. The first digit of the Serial Number (SN) determines if drive can be accessed. Example: Unclassified systems with CD Readers will NOT mount CDs with SNs beginning with # 2 or higher Confidential systems will NOT mount CDs with SNs beginning with 3 or higher Secret systems will NOT mount CDs with SNs beginning with #4 or Higher. Etc… Prevents the reading of CDs that are classified higher than the system (data spill) Introduction of “Foreign” CDs? Use Barcode Printer Kiosk #11 CD Readers Only 19
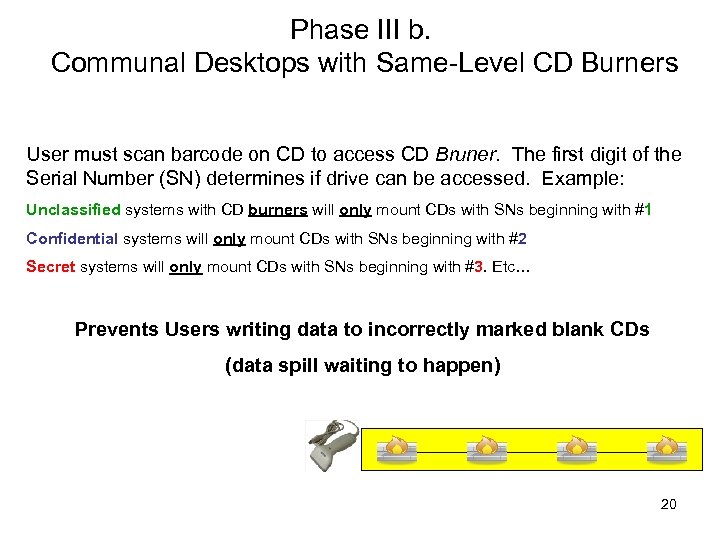 Phase III b. Communal Desktops with Same-Level CD Burners User must scan barcode on CD to access CD Bruner. The first digit of the Serial Number (SN) determines if drive can be accessed. Example: Unclassified systems with CD burners will only mount CDs with SNs beginning with #1 Confidential systems will only mount CDs with SNs beginning with #2 Secret systems will only mount CDs with SNs beginning with #3. Etc… Prevents Users writing data to incorrectly marked blank CDs (data spill waiting to happen) 20
Phase III b. Communal Desktops with Same-Level CD Burners User must scan barcode on CD to access CD Bruner. The first digit of the Serial Number (SN) determines if drive can be accessed. Example: Unclassified systems with CD burners will only mount CDs with SNs beginning with #1 Confidential systems will only mount CDs with SNs beginning with #2 Secret systems will only mount CDs with SNs beginning with #3. Etc… Prevents Users writing data to incorrectly marked blank CDs (data spill waiting to happen) 20
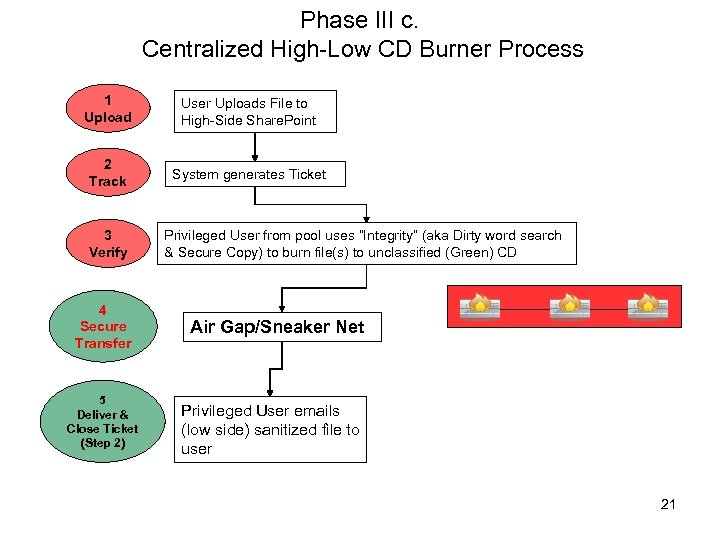 Phase III c. Centralized High-Low CD Burner Process 1 Upload User Uploads File to High-Side Share. Point 2 Track System generates Ticket 3 Verify 4 Secure Transfer 5 Deliver & Close Ticket (Step 2) Privileged User from pool uses “Integrity” (aka Dirty word search & Secure Copy) to burn file(s) to unclassified (Green) CD Air Gap/Sneaker Net Privileged User emails (low side) sanitized file to user 21
Phase III c. Centralized High-Low CD Burner Process 1 Upload User Uploads File to High-Side Share. Point 2 Track System generates Ticket 3 Verify 4 Secure Transfer 5 Deliver & Close Ticket (Step 2) Privileged User from pool uses “Integrity” (aka Dirty word search & Secure Copy) to burn file(s) to unclassified (Green) CD Air Gap/Sneaker Net Privileged User emails (low side) sanitized file to user 21
 Wrap-Up Phase I Cradle-to-Grave Lifecycle CD Tracking Phase II Secure Storage Phase III Spill-Resistant Network With Bar-coding Kiosk #11 22
Wrap-Up Phase I Cradle-to-Grave Lifecycle CD Tracking Phase II Secure Storage Phase III Spill-Resistant Network With Bar-coding Kiosk #11 22
 Benefits • Provides Scalable lifecycle Cradle-to-Grave tracking of CDs • Fully Automated • Custody Transfers • Employee out-processing flagging lost data • Prevents unauthorized possession and secure Storage • Facilitates Trend Analysis • Facilitates secure High-Low Data Transfers & Prevents Data Spills • Never actually “Reads” Classified Data • Blends Existing COTS Technology • Adds “Depth” to existing cybersecurity capabilities - keeping data secure even after it leaves the network. 23
Benefits • Provides Scalable lifecycle Cradle-to-Grave tracking of CDs • Fully Automated • Custody Transfers • Employee out-processing flagging lost data • Prevents unauthorized possession and secure Storage • Facilitates Trend Analysis • Facilitates secure High-Low Data Transfers & Prevents Data Spills • Never actually “Reads” Classified Data • Blends Existing COTS Technology • Adds “Depth” to existing cybersecurity capabilities - keeping data secure even after it leaves the network. 23
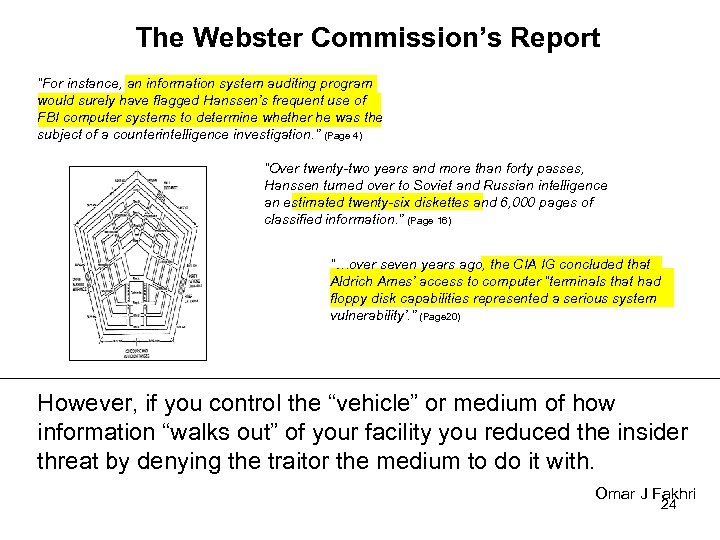 The Webster Commission’s Report “For instance, an information system auditing program would surely have flagged Hanssen’s frequent use of FBI computer systems to determine whether he was the subject of a counterintelligence investigation. ” (Page 4) “Over twenty-two years and more than forty passes, Hanssen turned over to Soviet and Russian intelligence an estimated twenty-six diskettes and 6, 000 pages of classified information. ” (Page 16) “…over seven years ago, the CIA IG concluded that Aldrich Ames’ access to computer “terminals that had floppy disk capabilities represented a serious system vulnerability’. ” (Page 20) However, if you control the “vehicle” or medium of how information “walks out” of your facility you reduced the insider threat by denying the traitor the medium to do it with. Omar J Fakhri 24
The Webster Commission’s Report “For instance, an information system auditing program would surely have flagged Hanssen’s frequent use of FBI computer systems to determine whether he was the subject of a counterintelligence investigation. ” (Page 4) “Over twenty-two years and more than forty passes, Hanssen turned over to Soviet and Russian intelligence an estimated twenty-six diskettes and 6, 000 pages of classified information. ” (Page 16) “…over seven years ago, the CIA IG concluded that Aldrich Ames’ access to computer “terminals that had floppy disk capabilities represented a serious system vulnerability’. ” (Page 20) However, if you control the “vehicle” or medium of how information “walks out” of your facility you reduced the insider threat by denying the traitor the medium to do it with. Omar J Fakhri 24
 Questions? 25
Questions? 25


