912d84968c41a35ceb385897a8d174c1.ppt
- Количество слайдов: 30

Case Study On Distributed Systems Security by Merv Wagner

Historical context: the evolution of security needs 1965 -75 1975 -89 1990 -99 Current Platforms Multi-user timesharing computers Distributed systems based on local networks The Internet, widearea services The Internet + mobile devices Shared resources Memory, files Local services (e. g. Email, web sites, NFS), local networks Internet commerce Distributed objects, mobile code Security requirements User identification and. Protection of services Strong security for authentication commercial transactions Access control for individual objects, secure mobile code Security management environment Single authority, single authorization database (e. g. /etc/ passwd) Per-activity authorities, groups with shared responsibilities Single authority, delegation, replicated authorization databases (e. g. NIS) Many authorities, no network-wide authorities
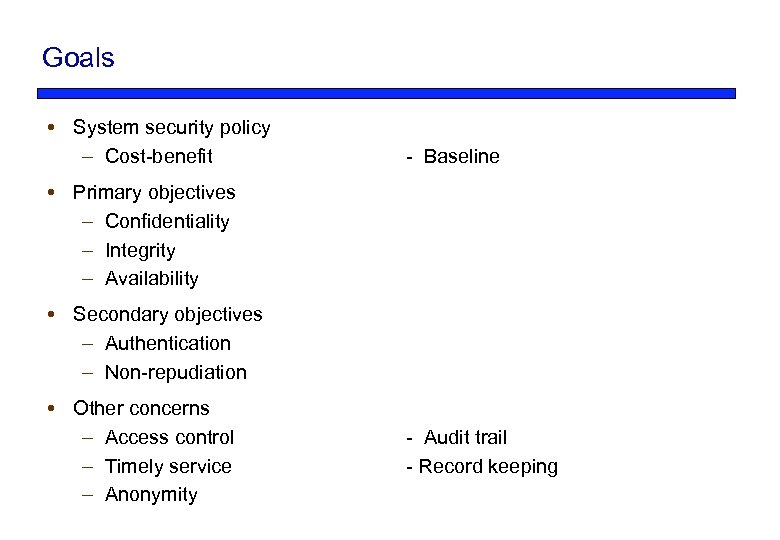
Goals System security policy – Cost-benefit - Baseline Primary objectives – Confidentiality – Integrity – Availability Secondary objectives – Authentication – Non-repudiation Other concerns – Access control – Timely service – Anonymity - Audit trail - Record keeping
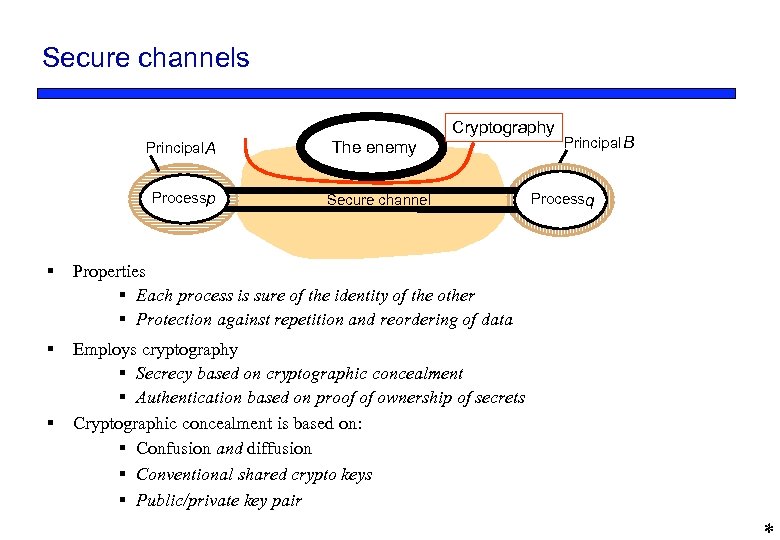
Secure channels Cryptography Principal A The enemy Processp Secure channel § Properties § Each process is sure of the identity of the other § Protection against repetition and reordering of data § Employs cryptography § Secrecy based on cryptographic concealment § Authentication based on proof of ownership of secrets Cryptographic concealment is based on: § Confusion and diffusion § Conventional shared crypto keys § Public/private key pair § Principal B Processq

Definitions Asymmetric algorithm – public/private key cryptography that utilizes a trap-door function, such as RSA Availability - system services are available when they are needed Certificate - an electronic document containing a statement signed by a principal Confidentiality - secrecy, information is only disclosed according to security policy Integrity - information is not destroyed or corrupted and the system performs data operations correctly DES - Data Encryption Standard adopted by National Bureau of Standards in 1977; famous cryptosystem that uses a 56 -bit secret key Digital Signature - emulates a conventional signature by using cryptography to verify to a third party that a message or document is produced by the signer RSA - Rivest, Shamir, Adleman encryption algorithm; first public-key cryptosystem; based on the use of trap door function of two very large prime numbers Symmetric algorithm – secret-key cryptography that uses a common key and a oneway encryption function, such as DES

Features Scenario 1: Secret communication with shared secret key Alice and Bob share a secret key KAB. 1. Alice uses KAB and an agreed encryption function E(KAB, M) to encrypt and send any number of messages {Mi}KAB to Bob. 2. Bob reads the encrypted messages using the corresponding decryption function D(KAB, M). Alice and Bob can go on using KAB as long as it is safe to assume that KAB has not been compromised. Issues: Key distribution: How can Alice send a shared key KAB to Bob securely? Freshness of communication: How does Bob know that any {Mi} isn’t a copy of an earlier encrypted message from Alice that was captured by Mallory and replayed later? *

Features Scenario 2: Authenticated communication with a server Bob is a file server; Sara is an authentication service. Sara shares secret key K A with Alice and secret key KB with Bob. 1. Alice sends an (unencrypted) message to Sara stating her identity and requesting a ticket for access to Bob. 2. Sara sends a response to Alice. {{Ticket}KB, KAB}KA. It is encrypted in KA and consists of a ticket (to be sent to Bob with each request for file access) encrypted in KB and a new secret key KAB. 3. Alice uses KA to decrypt the response. 4. Alice sends Bob a request R to access a file: {Ticket}KB, Alice, R. 5. The ticket is actually {KAB, Alice}KB. Bob uses KB to decrypt it, checks that Alice's name matches and then uses KAB to encrypt responses to Alice. A ticket is an encrypted item containing the identity of the principal to whom it is issued and a shared key for a communication session. This is a simplified version of the Needham and Schroeder (and Kerberos) protocol. *

Features Scenario 3: Authenticated communication with public keys Bob has a public/private key pair <KBpub, KBpriv> 1. Alice obtains a certificate that was signed by a trusted authority stating Bob's public key KBpub 2. Alice creates a new shared key KAB , encrypts it using KBpub using a public-key algorithm and sends the result to Bob. 3. Bob uses the corresponding private key KBpriv to decrypt it. (If they want to be sure that the message hasn't been tampered with, Alice can add an agreed value to it and Bob can check it. ) Mallory might intercept Alice’s initial request to a key distribution service for Bob’s public-key certificate and send a response containing his own public key. He can then intercept all the subsequent messages. *

Features Scenario 4: Digital signatures with secure digest function Alice wants to publish a document M in such a way that anyone can verify that it is from her. 1. Alice computes a fixed-length digest of the document Digest(M). 2. Alice encrypts the digest in her private key, appends it to M and makes the resulting signed document (M, {Digest(M)}KApriv) available to the intended users. 3. Bob obtains the signed document, extracts M and computes Digest(M). 4. Bob uses Alice's public key to decrypt {Digest(M)}KApriv and compares it with his computed digest. If they match, Alice's signature is verified. Digest is a compressed form of the plaintext message *

Features X 509 Certificate format Certificate: a statement signed by an appropriate authority. Certificates require: • An agreed standard format • Agreement on the construction of chains of trust • Expiry dates, so that certificates can be revoked. Subject Distinguished Name, Public Key Issuer Distinguished Name, Signature Period of validity Not Before Date, Not After Date Administrative information Version, Serial Number Extended Information

Certificates as credentials Certificates can act as credentials – Evidence for a principal's right to access a resource The two certificates shown could act as credentials for Alice to operate on her bank account – She would need to add her public key certificate *
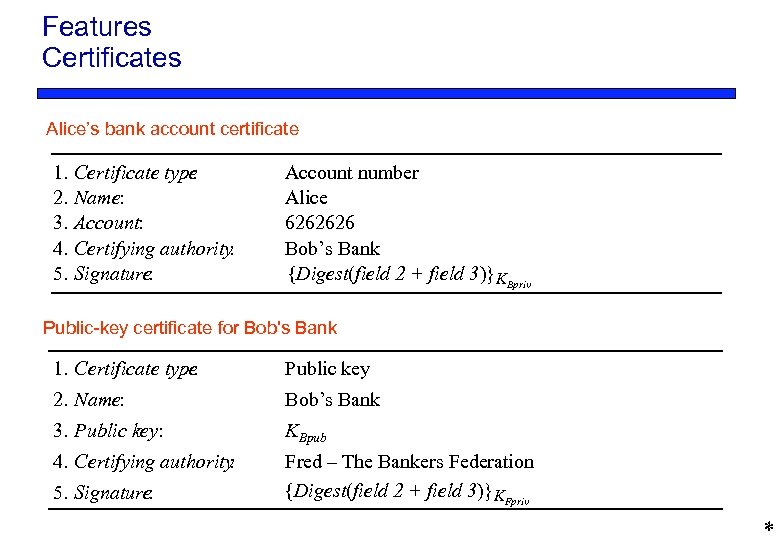
Features Certificates Alice’s bank account certificate 1. 2. 3. 4. 5. Certificate type : Name: Account: Certifying authority : Signature : Account number Alice 6262626 Bob’s Bank {Digest(field 2 + field 3)}KBpriv Public-key certificate for Bob's Bank 1. Certificate type : Public key 2. Name: Bob’s Bank 3. Public key: KBpub 4. Certifying authority : Fred – The Bankers Federation {Digest(field 2 + field 3)} KFpriv 5. Signature : *
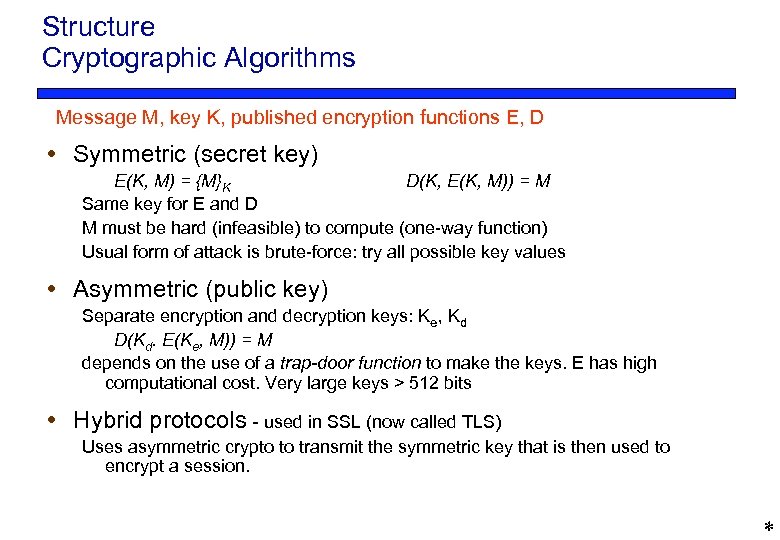
Structure Cryptographic Algorithms Message M, key K, published encryption functions E, D Symmetric (secret key) E(K, M) = {M}K D(K, E(K, M)) = M Same key for E and D M must be hard (infeasible) to compute (one-way function) Usual form of attack is brute-force: try all possible key values Asymmetric (public key) Separate encryption and decryption keys: Ke, Kd D(Kd. E(Ke, M)) = M depends on the use of a trap-door function to make the keys. E has high computational cost. Very large keys > 512 bits Hybrid protocols - used in SSL (now called TLS) Uses asymmetric crypto to transmit the symmetric key that is then used to encrypt a session. *
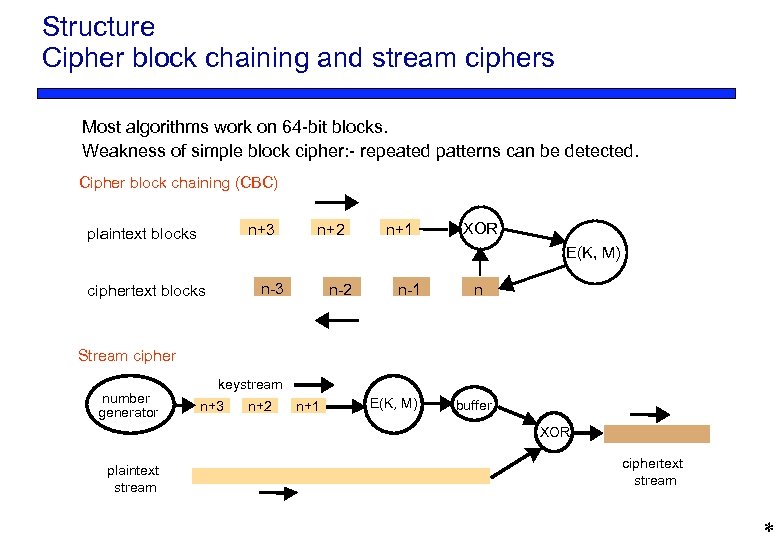
Structure Cipher block chaining and stream ciphers Most algorithms work on 64 -bit blocks. Weakness of simple block cipher: - repeated patterns can be detected. Cipher block chaining (CBC) n+3 plaintext blocks n+2 n+1 XOR E(K, M) n-3 ciphertext blocks n-2 n-1 n Stream cipher number generator keystream n+3 n+2 n+1 E(K, M) buffer XOR plaintext stream ciphertext stream *
Symmetric encryption algorithms These are all programs that perform confusion and diffusion operations on blocks of binary data DES: The US Data Encryption Standard (1977). No longer strong in its original form. 56 -bit key Triple-DES: applies DES three times with two different keys. 112 -bit key AES: A proposed US Advanced Encryption Standard (1997). 128/256 -bit key. *
Asymmetric encryption algorithms Depend on the use of trap-door functions A trap-door function is a one-way function with a secret exit - e. g. product of two large numbers; easy to multiply, very hard to factor RSA: The first practical algorithm (Rivest, Shamir and Adelman 1978) and still the most frequently used. Key length is variable, 512 -2048 bits. Asymmetric algorithms are ~1000 x slower and are therefore not practical for bulk encryption, but their other properties make them ideal for key distribution and for authentication uses. *

Implementation Digital signatures Requirement: – To authenticate stored document files as well as messages – To protect against forgery – To prevent the signer from repudiating a signed document (denying their responsibility) Encryption of a document in a secret key constitutes a signature - Impossible for others to perform without knowledge of the key Strong authentication of document Strong protection against forgery Weak against repudiation (signer could claim key was compromised) *
Implementation Secure digest functions - Encrypted text of document makes an impractically long signature - So we encrypt a secure digest instead - Secure digest function computes a fixed-length hash H(M) that characterizes the document M - H(M) should be: - Fast to compute - Hard to invert - MD 5: Developed by Rivest (1992). Computes a 128 -bit digest - SHA: (1995) based on Rivest's MD 4 but made more secure by producing a 160 -bit digest *
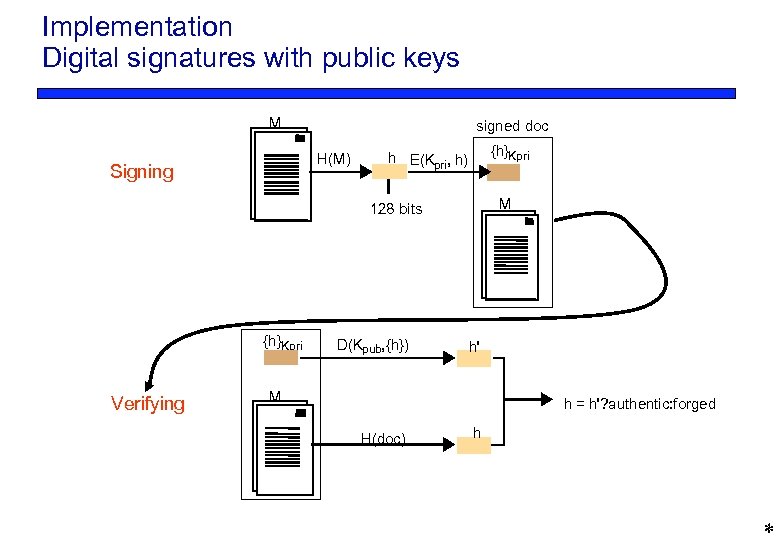
Implementation Digital signatures with public keys M signed doc H(M) Signing {h}Kpri h E(Kpri, h) M 128 bits {h}Kpri Verifying D(Kpub, {h}) h' M h = h'? authentic: forged H(doc) h *
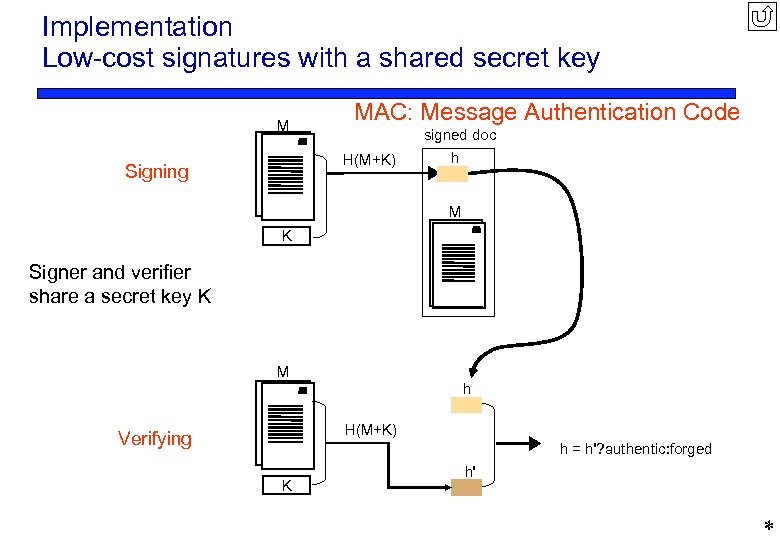
Implementation Low-cost signatures with a shared secret key M MAC: Message Authentication Code signed doc H(M+K) Signing h M K Signer and verifier share a secret key K M h H(M+K) Verifying h = h'? authentic: forged K h' *
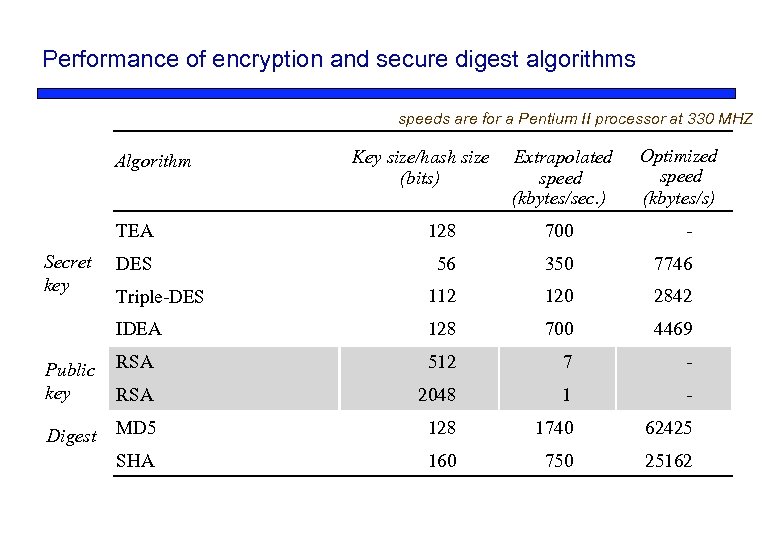
Performance of encryption and secure digest algorithms speeds are for a Pentium II processor at 330 MHZ Algorithm Key size/hash size (bits) Extrapolated speed (kbytes/sec. ) Optimized speed (kbytes/s) TEA 128 700 - DES 56 350 7746 Triple-DES 112 120 2842 IDEA 128 700 4469 Public key RSA 512 7 - RSA 2048 1 - Digest MD 5 128 1740 62425 SHA 160 750 25162 Secret key

Application Kerberos authentication and key distribution service Secures communication with servers on a local network – Developed at MIT in the 1980 s to provide security across a large campus network > 5000 users – Based on Needham - Schroeder protocol Standardized and now included in many operating systems – Internet RFC 1510, OSF DCE – BSD UNIX, Linux, Windows 2000, NT, XP, etc. – Available from MIT Kerberos server creates a shared secret key for any required server and sends it (encrypted) to the user's computer User's password is the initial secret shared with Kerberos *
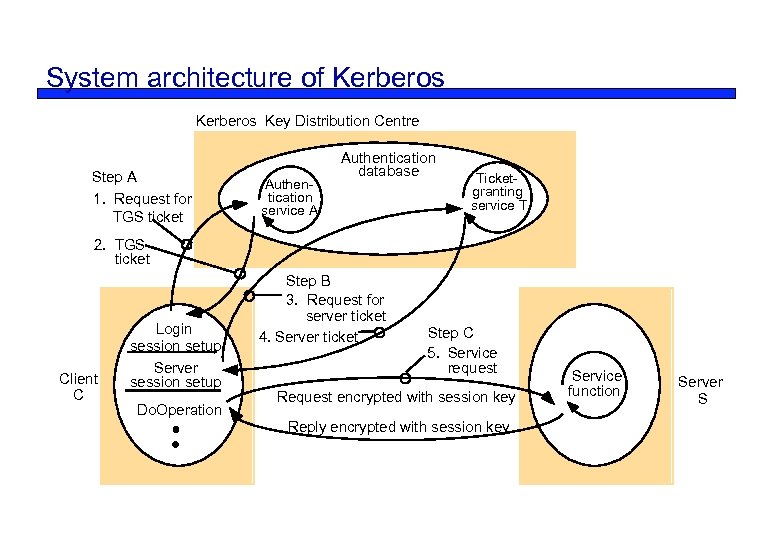
System architecture of Kerberos Key Distribution Centre Step A 1. Request for TGS ticket Authentication service A Authentication database Ticketgranting service T 2. TGS ticket Client C Login session setup Server session setup Do. Operation Step B 3. Request for server ticket 4. Server ticket Step C 5. Service request Request encrypted with session key Reply encrypted with session key Service function Server S

Application Secure Socket Layer (SSL) Key distribution and secure channels for internet commerce – Hybrid protocol; depends on public-key cryptography – Originally developed by Netscape Corporation (1994) – Extended and adopted as an Internet standard with the name Transport Level Security (TLS) – Provides the security in all web servers and browsers and in secure versions of Telnet, FTP and other network applications Design requirements – Secure communication without prior negotiation or help from 3 rd parties – Free choice of crypto algorithms by client and server – communication in each direction can be authenticated, encrypted or both
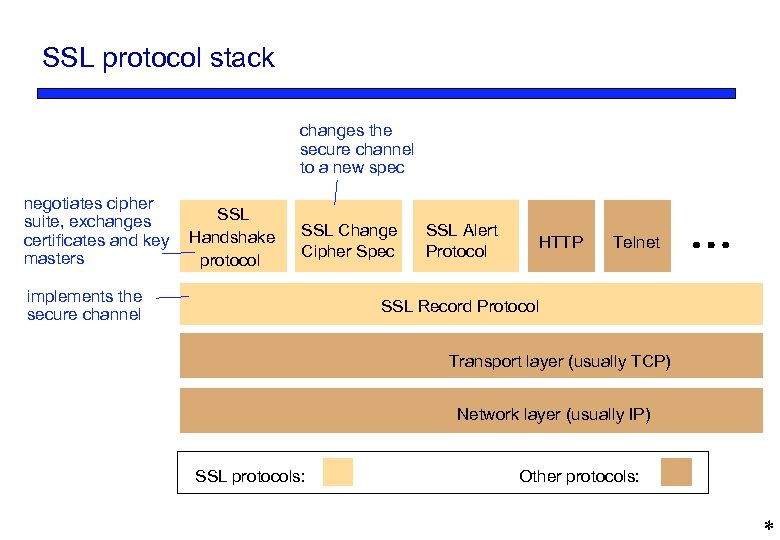
SSL protocol stack changes the secure channel to a new spec negotiates cipher suite, exchanges certificates and key masters SSL Handshake protocol SSL Change Cipher Spec implements the secure channel SSL Alert Protocol HTTP Telnet SSL Record Protocol Transport layer (usually TCP) Network layer (usually IP) SSL protocols: Other protocols: *
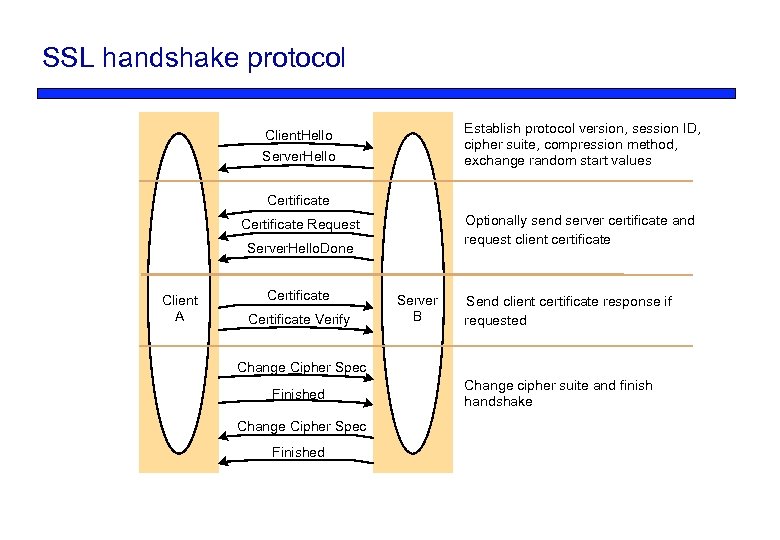
SSL handshake protocol Establish protocol version, session ID, cipher suite, compression method, exchange random start values Client. Hello Server. Hello Certificate Optionally send server certificate and request client certificate Certificate Request Server. Hello. Done Client A Certificate Verify Server B Send client certificate response if requested Change Cipher Spec Finished Change cipher suite and finish handshake
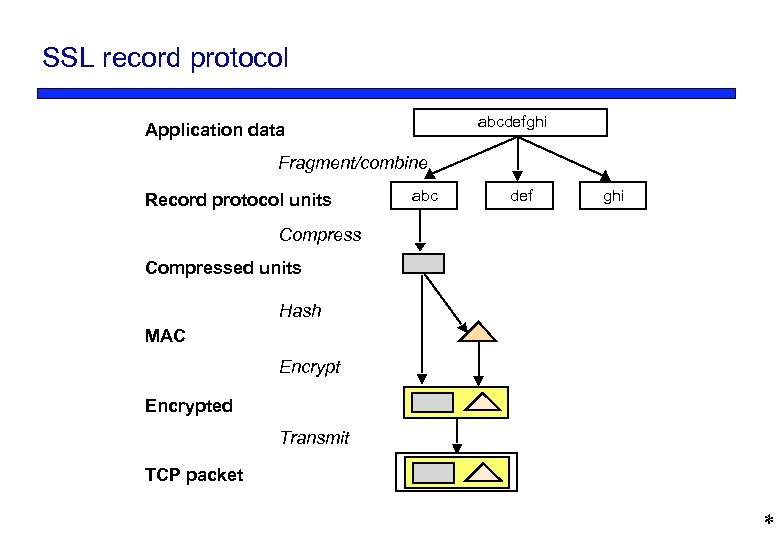
SSL record protocol abcdefghi Application data Fragment/combine Record protocol units abc def ghi Compressed units Hash MAC Encrypted Transmit TCP packet *

Significance Distributed systems require increased security Goal of confidentiality, integrity and availability New systems must build security in during design Cryptographic algorithms are means to achieve distributed security – Secret-key (symmetric) - DES – Public/private key (asymmetric) – RSA Need for increased bit length of keys to maintain cryptographic security Digital signatures/Certificates Kerboros/Secure Socket Layer More Internet communications will be secure in the future

Summary Essential to protect the information in distributed systems Achieved by access control mechanisms and secure channels Public-key and secret-key cryptography provide the basis for authentication and secure communication Kerberos and SSL are widely-used system components that support secure and authenticated communication *

References Anderson, James P. ; "Computer Security Technology Planning Study"; ESD-TR-73 -51, Vol I; Electronic Systems Division, Air Force Systems Command; Hanscom AFB, MA; Oct 1972. Brassard, Gilles; Modern Cryptology A Tutorial; Springer-Verlag; New York; 1988. Coulouris, George; Dollimore, Jean; Kindberg, Tim; "Teaching Material Slides"; Based on: Distributed Systems Concepts and Design; Pearson Education Ltd; Harlow, England; 2001. Coulouris, George; Dollimore, Jean; Kindberg, Tim; Distributed Systems Concepts and Design; Pearson Education Ltd; Harlow, England; 2001. Lampson, B. W. ; "Dynamic Protection Structures"; AFIPS Conf. Proc. 35; FJCC; 1969, pg 2738. Langsford, Alwyn; Moffett, Jonathan D. ; Distributed Systems Management; Addison. Wesley; Wokingham, England; 1993. Moreno, April L. ; "Distributed Systems Security: Java, CORBA, and COM+"; SANS Institute Information Security Reading Room; http: //www. sans. org; Sept 14, 2002. Summers, Rita C. ; Secure Computing Threats and Safeguards; Mc. Graw-Hill; New York; 1997. Weissman, Clark; "Security Controls in the ADEPT-50 Timesharing System"; AFIPS Conf. Proc. 35; FJCC; 1969, pg 119 -133.
912d84968c41a35ceb385897a8d174c1.ppt