ba50ee1e1b189d32fa90f56c715b1c09.ppt
- Количество слайдов: 32
 Case Study GRC Implementation - A User Perspective Wendy K. Roberts, CPA, CIA Adil Khan, GRC Client Director, Fulcrum. Way Hari Radhakrishnan, IT Consultant, Control Solutions January 21, 2009
Case Study GRC Implementation - A User Perspective Wendy K. Roberts, CPA, CIA Adil Khan, GRC Client Director, Fulcrum. Way Hari Radhakrishnan, IT Consultant, Control Solutions January 21, 2009
 Agenda • • • Introduction GRC Objectives Selection Process – Research and Approach About Fulcrum. Way Controls Survey Controls Framework Application Controls Best Practices GRC Monitor Implementation Compliance Best Practices GRC Manager Implementation
Agenda • • • Introduction GRC Objectives Selection Process – Research and Approach About Fulcrum. Way Controls Survey Controls Framework Application Controls Best Practices GRC Monitor Implementation Compliance Best Practices GRC Manager Implementation
 About Our Company • Harris Stratex Networks, Inc. is a leading provider in backhaul solutions for mobility and broadband networks. We serve all global markets, including mobile network operators, public safety agencies, private network operators, utility and transportation companies, government agencies and broadcasters. With customers in more than 135 countries, Harris Stratex Networks is recognized around the world for innovative, best-in-class wireless networking solutions and services. Company Presentation - How to use this template 3
About Our Company • Harris Stratex Networks, Inc. is a leading provider in backhaul solutions for mobility and broadband networks. We serve all global markets, including mobile network operators, public safety agencies, private network operators, utility and transportation companies, government agencies and broadcasters. With customers in more than 135 countries, Harris Stratex Networks is recognized around the world for innovative, best-in-class wireless networking solutions and services. Company Presentation - How to use this template 3
 Objective for a GRC Tool • Obtain a versatile tool that could be used WW – Move away from spreadsheets and word documents to a more automated environment. – A product that could grow with the company. – Be used for SOX 302 and 404 Certification. – Supported Control Self Assessment testing. – Used to enhance the testing and reporting for Internal Audit. – Provide a central database for compliance use such as Code of Conduct and policy management. – Incorporate other compliance programs such as ISO and EH&S. Company Presentation - How to use this template 4
Objective for a GRC Tool • Obtain a versatile tool that could be used WW – Move away from spreadsheets and word documents to a more automated environment. – A product that could grow with the company. – Be used for SOX 302 and 404 Certification. – Supported Control Self Assessment testing. – Used to enhance the testing and reporting for Internal Audit. – Provide a central database for compliance use such as Code of Conduct and policy management. – Incorporate other compliance programs such as ISO and EH&S. Company Presentation - How to use this template 4
 Research and Approach • Gartner Report - Magic Quadrant for Finance Governance, Risk and Compliance Management Software, 2007. Published February 1, 2007. – Research for the tool began in July 2007. – Developed an analysis matrix with 32 criteria points. – Use of the magic quadrant to select vendors based on criteria and objectives of the company. – Six vendors chosen which met the most criteria points. – Demos performed with executive management. – Top two vendors were asked for RFPs. Company Presentation - How to use this template 5
Research and Approach • Gartner Report - Magic Quadrant for Finance Governance, Risk and Compliance Management Software, 2007. Published February 1, 2007. – Research for the tool began in July 2007. – Developed an analysis matrix with 32 criteria points. – Use of the magic quadrant to select vendors based on criteria and objectives of the company. – Six vendors chosen which met the most criteria points. – Demos performed with executive management. – Top two vendors were asked for RFPs. Company Presentation - How to use this template 5
 Research and Approach • Decision for purchase of tool – Top two vendors were presented to a steering committee. – Recommendation was made for Oracle GRC Manager as the tool of choice. – Presented to the Board of Directors for approval. – Approval obtained in January 2008. Company Presentation - How to use this template 6
Research and Approach • Decision for purchase of tool – Top two vendors were presented to a steering committee. – Recommendation was made for Oracle GRC Manager as the tool of choice. – Presented to the Board of Directors for approval. – Approval obtained in January 2008. Company Presentation - How to use this template 6
 Implementation of GRC Monitor • Tool used to analyze Segregation of Duties (SOD) violations in Oracle – On-demand service commenced in February 2008. – Developed over 400 business rules which represented best practices in the industry. – Design of a risk matrix using High-Medium-Low risks for Oracle modules GL, AP, AR, FA. – Remediation of violations for high risks completed in June 2008 (FY 08 Year End). – Medium and low risks violations being completed for FY 09 by the end of January 2009. Company Presentation - How to use this template 7
Implementation of GRC Monitor • Tool used to analyze Segregation of Duties (SOD) violations in Oracle – On-demand service commenced in February 2008. – Developed over 400 business rules which represented best practices in the industry. – Design of a risk matrix using High-Medium-Low risks for Oracle modules GL, AP, AR, FA. – Remediation of violations for high risks completed in June 2008 (FY 08 Year End). – Medium and low risks violations being completed for FY 09 by the end of January 2009. Company Presentation - How to use this template 7
 Implementation of GRC Manager • Tool used to address policy management, 302 quarterly certifications and 404 SOX compliance – Implementation began mid-October with completion estimated to be March 2009. – Policy management and 302 quarterly certification using Stellant Content Manager in GRC. – Use of GRC Manager for SOX 404 Certification and Control Self Assessment and Internal Audit testing. – Developing on-line training using Oracle User Productivity Kit (UPK). Company Presentation - How to use this template 8
Implementation of GRC Manager • Tool used to address policy management, 302 quarterly certifications and 404 SOX compliance – Implementation began mid-October with completion estimated to be March 2009. – Policy management and 302 quarterly certification using Stellant Content Manager in GRC. – Use of GRC Manager for SOX 404 Certification and Control Self Assessment and Internal Audit testing. – Developing on-line training using Oracle User Productivity Kit (UPK). Company Presentation - How to use this template 8
 About Fulcrum. Way: is the #1 provider of Governance, Risk and Compliance Expertise, Solutions and Software Services for Oracle enterprise customers. Expertise: Risk Management, Compliance, IT Audit, Internal Controls, Financial Reporting and GRC Software implementation consulting services. Since 2003, we have successfully assisted over one hundred Fortune-500 to Middle Market companies across all major industry segments. Solutions: Oracle certified Systems Integrator and ISV member of the Oracle Partner Network. Fulcrum. Way solution are built on software technologies from Oracle Corporation. Fulcrum. Way GRC Solutions are the #1 choice of Oracle customers. Software Services: We enable organizations to assess Financial, Operational and Information Technology risks, monitor internal controls and optimize business processes. Auditors, Risk Managers and Business Process Owners can access a wide range of web based services over a secure internet connection to Fulcrum. Way GRCMONITOR® (https: //www. grcmonitor. com) Software as a Service (Saa. S) platform. Privately Held Delaware corporation with US presence in: New York, Texas and California International Presence in UK and India www. fulcrumway. com
About Fulcrum. Way: is the #1 provider of Governance, Risk and Compliance Expertise, Solutions and Software Services for Oracle enterprise customers. Expertise: Risk Management, Compliance, IT Audit, Internal Controls, Financial Reporting and GRC Software implementation consulting services. Since 2003, we have successfully assisted over one hundred Fortune-500 to Middle Market companies across all major industry segments. Solutions: Oracle certified Systems Integrator and ISV member of the Oracle Partner Network. Fulcrum. Way solution are built on software technologies from Oracle Corporation. Fulcrum. Way GRC Solutions are the #1 choice of Oracle customers. Software Services: We enable organizations to assess Financial, Operational and Information Technology risks, monitor internal controls and optimize business processes. Auditors, Risk Managers and Business Process Owners can access a wide range of web based services over a secure internet connection to Fulcrum. Way GRCMONITOR® (https: //www. grcmonitor. com) Software as a Service (Saa. S) platform. Privately Held Delaware corporation with US presence in: New York, Texas and California International Presence in UK and India www. fulcrumway. com
 Fulcrum Credentials Media and Financial Services Life Sciences Retail Entertainment Readers Digest Natural Resources High Technology Industrial Manufacturing Defense/ Aerospace Healthcare Construction Food
Fulcrum Credentials Media and Financial Services Life Sciences Retail Entertainment Readers Digest Natural Resources High Technology Industrial Manufacturing Defense/ Aerospace Healthcare Construction Food
 Fulcrum. Point Insight Thought Leadership - Events • Compliance Week Magazine Healthcare Firm Aligns Compliance Efforts, Cuts Costs • Economist Magazine –Compliance Guide for Enterprise Systems • POD Cast – How Automating the Enterprise Risk Management Process helps organizations comply with regulations • OAUG - Impact of AS 5 for Oracle Enterprise Customers • IIA – Top Five Reasons for Automating Application Controls • Oracle Open World – Annual GRC Dinner, GE and Birds Eye Case Study • Web casts – GRC Best Practices, Trends and Expert Insight.
Fulcrum. Point Insight Thought Leadership - Events • Compliance Week Magazine Healthcare Firm Aligns Compliance Efforts, Cuts Costs • Economist Magazine –Compliance Guide for Enterprise Systems • POD Cast – How Automating the Enterprise Risk Management Process helps organizations comply with regulations • OAUG - Impact of AS 5 for Oracle Enterprise Customers • IIA – Top Five Reasons for Automating Application Controls • Oracle Open World – Annual GRC Dinner, GE and Birds Eye Case Study • Web casts – GRC Best Practices, Trends and Expert Insight.
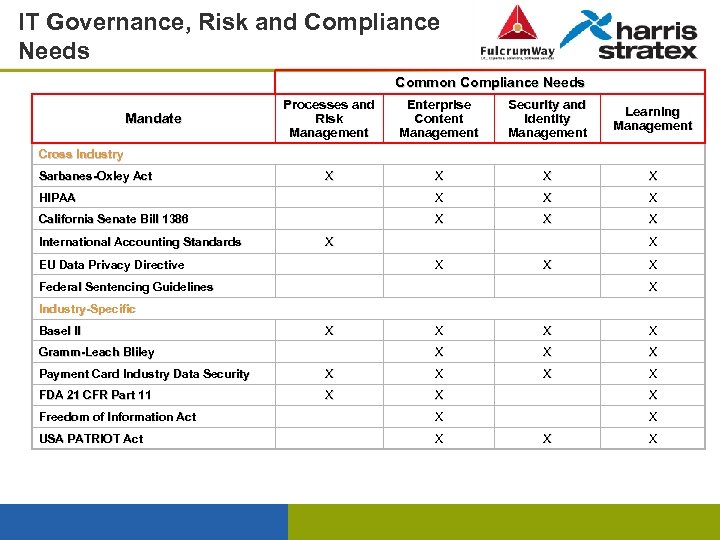 IT Governance, Risk and Compliance Needs Common Compliance Needs Processes and Risk Management Enterprise Content Management Security and Identity Management Learning Management X X HIPAA X X X California Senate Bill 1386 X X X Mandate Cross Industry Sarbanes-Oxley Act International Accounting Standards X EU Data Privacy Directive X X X Federal Sentencing Guidelines X X Industry-Specific Basel II X X Gramm-Leach Bliley X X X Payment Card Industry Data Security X X FDA 21 CFR Part 11 X X X Freedom of Information Act X X USA PATRIOT Act X X X
IT Governance, Risk and Compliance Needs Common Compliance Needs Processes and Risk Management Enterprise Content Management Security and Identity Management Learning Management X X HIPAA X X X California Senate Bill 1386 X X X Mandate Cross Industry Sarbanes-Oxley Act International Accounting Standards X EU Data Privacy Directive X X X Federal Sentencing Guidelines X X Industry-Specific Basel II X X Gramm-Leach Bliley X X X Payment Card Industry Data Security X X FDA 21 CFR Part 11 X X X Freedom of Information Act X X USA PATRIOT Act X X X
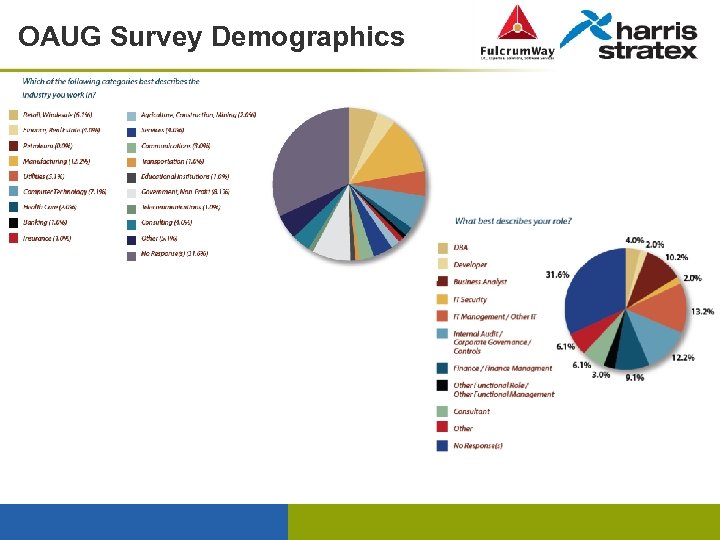 OAUG Survey Demographics
OAUG Survey Demographics
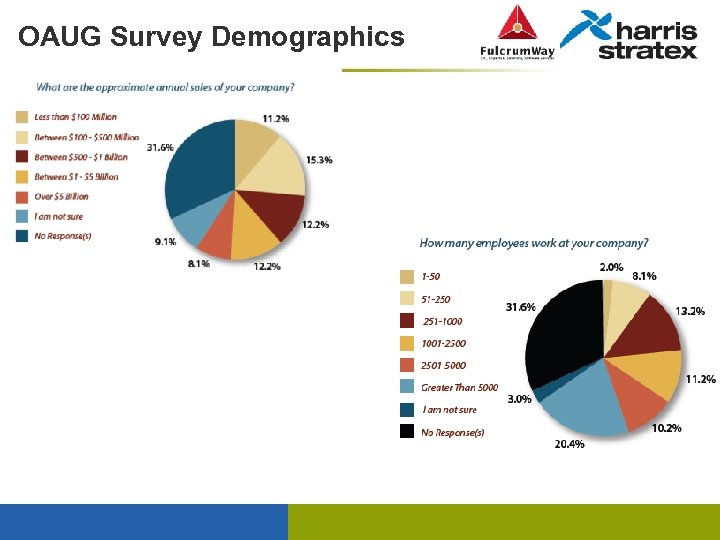 OAUG Survey Demographics
OAUG Survey Demographics
 Application Survey Questions There were 20 scenarios presented and each scenario included two questions: Identify the awareness of the Determine likelihood of implemented deficiency: if Oracle provided a solution: My company was not aware of this risk My company is aware of this risk, but has chosen not to address it yet My company is aware of this risk and has chosen to accept the risk My company is aware of this risk and has addressed it via a manual control My company is aware of this risk and has implemented a customization / extension I am not qualified to address this risk My company does not use this functionality Other Would likely not implement because we don't agree with the risks Would likely not implement because we already addressed via a Customization Would likely not implement because we have chosen to accept the risks Would likely implement it because we have not addressed the issue Would likely implement it because we would rather replace our customization I am not able to know what our company would do Other
Application Survey Questions There were 20 scenarios presented and each scenario included two questions: Identify the awareness of the Determine likelihood of implemented deficiency: if Oracle provided a solution: My company was not aware of this risk My company is aware of this risk, but has chosen not to address it yet My company is aware of this risk and has chosen to accept the risk My company is aware of this risk and has addressed it via a manual control My company is aware of this risk and has implemented a customization / extension I am not qualified to address this risk My company does not use this functionality Other Would likely not implement because we don't agree with the risks Would likely not implement because we already addressed via a Customization Would likely not implement because we have chosen to accept the risks Would likely implement it because we have not addressed the issue Would likely implement it because we would rather replace our customization I am not able to know what our company would do Other
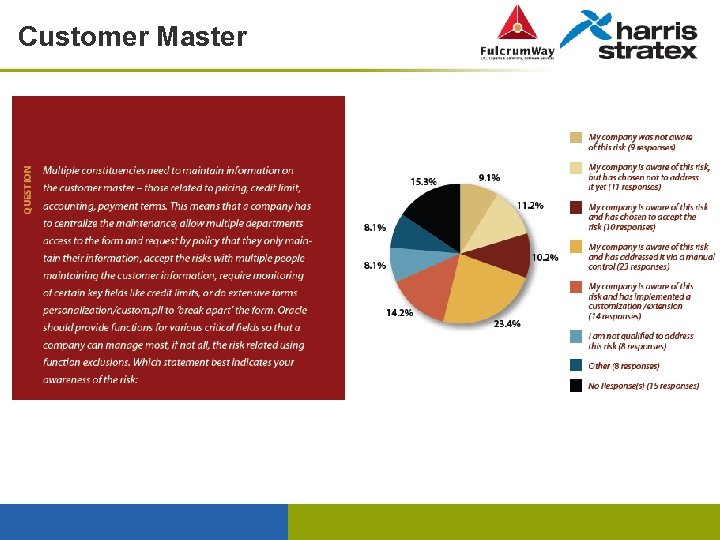 Customer Master
Customer Master
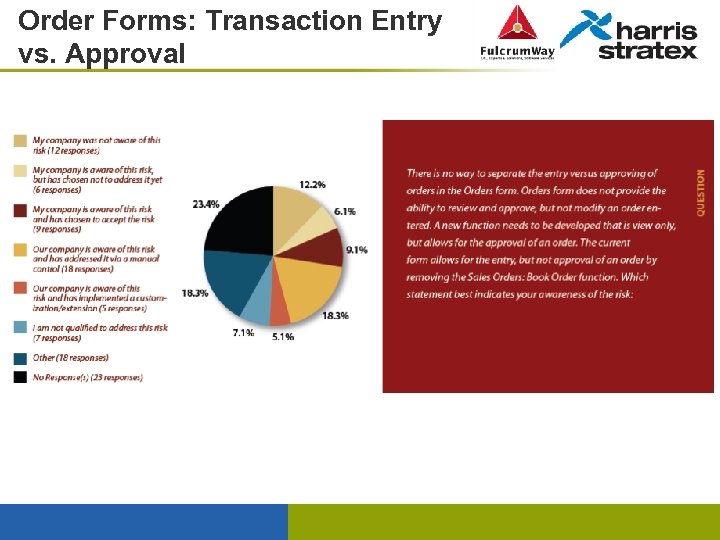 Order Forms: Transaction Entry vs. Approval
Order Forms: Transaction Entry vs. Approval
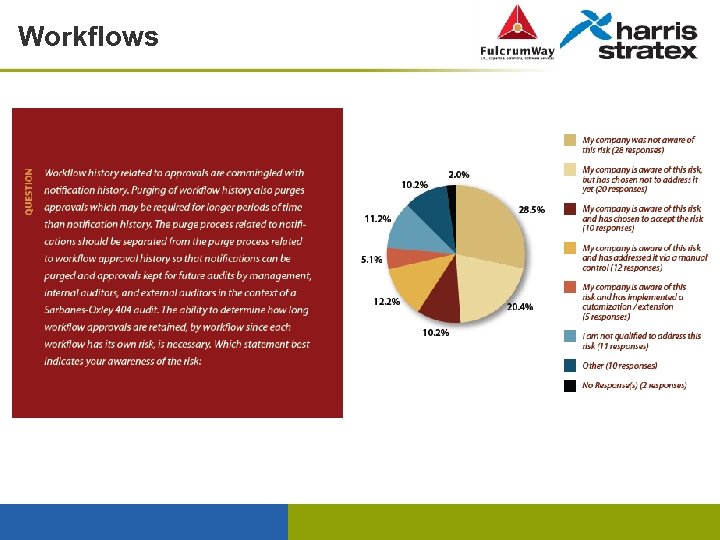 Workflows
Workflows
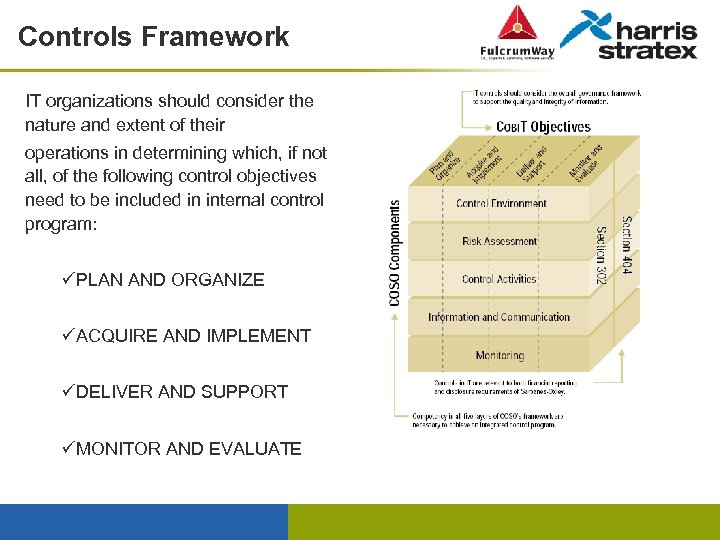 Controls Framework IT organizations should consider the nature and extent of their operations in determining which, if not all, of the following control objectives need to be included in internal control program: üPLAN AND ORGANIZE üACQUIRE AND IMPLEMENT üDELIVER AND SUPPORT üMONITOR AND EVALUATE
Controls Framework IT organizations should consider the nature and extent of their operations in determining which, if not all, of the following control objectives need to be included in internal control program: üPLAN AND ORGANIZE üACQUIRE AND IMPLEMENT üDELIVER AND SUPPORT üMONITOR AND EVALUATE
 What are Application Controls? • Application controls apply to the business processes they support. These controls are designed within the application to prevent or detect unauthorized transactions. When combined with manual controls, as necessary, application controls ensure completeness, accuracy, authorization and validity of processing transactions • Control objectives can be supported with automated application controls. They are most effective in integrated ERP environments, such as SAP, People. Soft, Oracle, JD Edwards and others. q. Orders are processed only within approved customer credit limits. q. Orders are approved by management as to prices and terms of sale. q. Purchase orders are placed only for approved requisitions. q. Purchase orders are accurately entered. q. All purchase orders issued are input and processed. q. All recorded production costs are consistent with actual direct and indirect expenses associated with production. q. All direct and indirect expenses associated with production are recorded as production costs.
What are Application Controls? • Application controls apply to the business processes they support. These controls are designed within the application to prevent or detect unauthorized transactions. When combined with manual controls, as necessary, application controls ensure completeness, accuracy, authorization and validity of processing transactions • Control objectives can be supported with automated application controls. They are most effective in integrated ERP environments, such as SAP, People. Soft, Oracle, JD Edwards and others. q. Orders are processed only within approved customer credit limits. q. Orders are approved by management as to prices and terms of sale. q. Purchase orders are placed only for approved requisitions. q. Purchase orders are accurately entered. q. All purchase orders issued are input and processed. q. All recorded production costs are consistent with actual direct and indirect expenses associated with production. q. All direct and indirect expenses associated with production are recorded as production costs.
 Risk Assessment • The IT organization has an entity-level and activity-level risk assessment framework, which is used periodically to assess information risk to achieving business objectives. • Management’s risk assessment framework focuses on the examination of the essential elements of risk and the cause and effect relationship among them. • A risk assessment framework exists and considers the risk assessment probability and likelihood of threats. • The IT organization’s risk assessment framework measures the impact of risks according to qualitative and quantitative criteria. • The IT organization’s risk assessment framework is designed to support cost-effective controls to mitigate exposure to risks on a continuing basis, including risk avoidance, mitigation or acceptance. • A comprehensive security assessment is performed for critical systems and locations based on their relative priority.
Risk Assessment • The IT organization has an entity-level and activity-level risk assessment framework, which is used periodically to assess information risk to achieving business objectives. • Management’s risk assessment framework focuses on the examination of the essential elements of risk and the cause and effect relationship among them. • A risk assessment framework exists and considers the risk assessment probability and likelihood of threats. • The IT organization’s risk assessment framework measures the impact of risks according to qualitative and quantitative criteria. • The IT organization’s risk assessment framework is designed to support cost-effective controls to mitigate exposure to risks on a continuing basis, including risk avoidance, mitigation or acceptance. • A comprehensive security assessment is performed for critical systems and locations based on their relative priority.
 Control Activities An organization has and does the following: • A system development life cycle methodology that considers security, availability and processing integrity requirements of the organization. This ensures that information systems are designed to include application controls that support complete, accurate, authorized and valid transaction processing. • An acquisition and planning process that aligns with its overall strategic direction. • Acquires software in accordance with its acquisition and planning process. • Procedures ensure that system software is installed and maintained in accordance with the organization’s requirements. • Procedures ensure that system software changes are controlled in line with the organization’s change management procedures. • Ensures that the implementation of system software do not jeopardize the security of the data.
Control Activities An organization has and does the following: • A system development life cycle methodology that considers security, availability and processing integrity requirements of the organization. This ensures that information systems are designed to include application controls that support complete, accurate, authorized and valid transaction processing. • An acquisition and planning process that aligns with its overall strategic direction. • Acquires software in accordance with its acquisition and planning process. • Procedures ensure that system software is installed and maintained in accordance with the organization’s requirements. • Procedures ensure that system software changes are controlled in line with the organization’s change management procedures. • Ensures that the implementation of system software do not jeopardize the security of the data.
 Control Monitoring • Changes to IT systems and applications are performed and designed to meet the expectations of users. • IT management monitors its delivery of services to identify shortfalls and responds with actionable plans to improve. • IT management monitors the effectiveness of internal controls Monitoring in the normal course of operations through management and supervisory activities, comparisons and benchmarks. • Serious deviations in the operation of internal control, Monitoring including major security, availability and processing integrity events, are reported to senior management. • Internal control assessments are performed periodically, using Monitoring self-assessment or independent audit, to examine whether internal controls are operating satisfactorily.
Control Monitoring • Changes to IT systems and applications are performed and designed to meet the expectations of users. • IT management monitors its delivery of services to identify shortfalls and responds with actionable plans to improve. • IT management monitors the effectiveness of internal controls Monitoring in the normal course of operations through management and supervisory activities, comparisons and benchmarks. • Serious deviations in the operation of internal control, Monitoring including major security, availability and processing integrity events, are reported to senior management. • Internal control assessments are performed periodically, using Monitoring self-assessment or independent audit, to examine whether internal controls are operating satisfactorily.
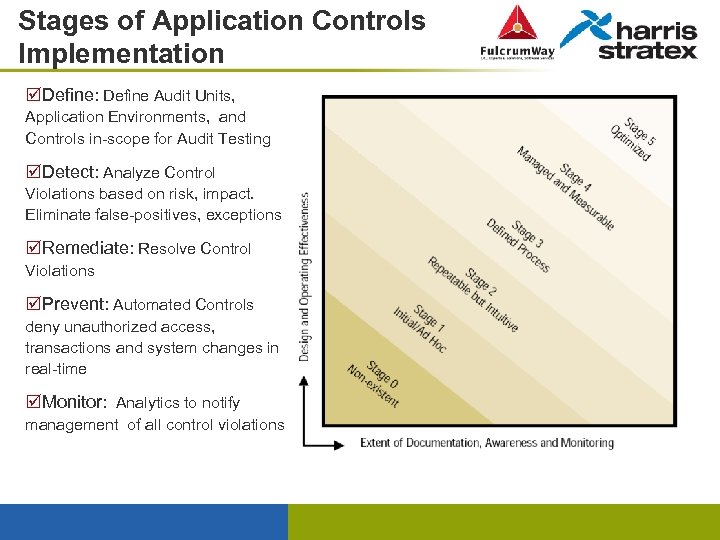 Stages of Application Controls Implementation þDefine: Define Audit Units, Application Environments, and Controls in-scope for Audit Testing þDetect: Analyze Control Violations based on risk, impact. Eliminate false-positives, exceptions þRemediate: Resolve Control Violations þPrevent: Automated Controls deny unauthorized access, transactions and system changes in real-time þMonitor: Analytics to notify management of all control violations
Stages of Application Controls Implementation þDefine: Define Audit Units, Application Environments, and Controls in-scope for Audit Testing þDetect: Analyze Control Violations based on risk, impact. Eliminate false-positives, exceptions þRemediate: Resolve Control Violations þPrevent: Automated Controls deny unauthorized access, transactions and system changes in real-time þMonitor: Analytics to notify management of all control violations
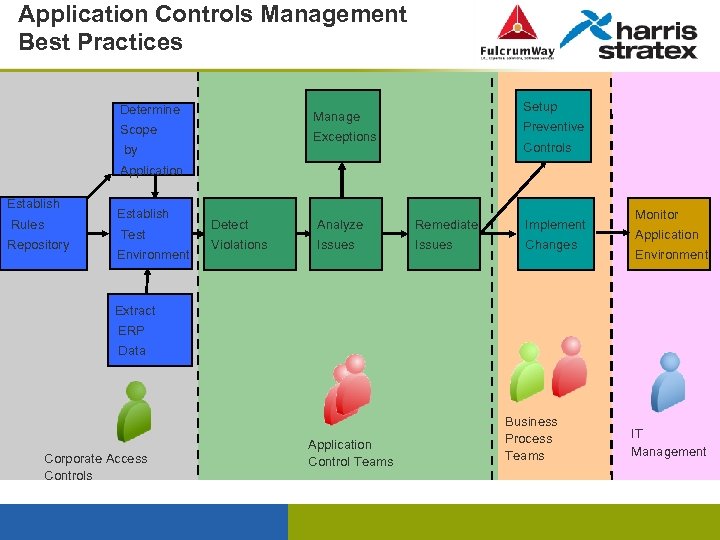 Application Controls Management Best Practices Determine Setup Manage Scope Preventive Exceptions by Controls Application Establish Rules Repository Establish Test Environment Detect Analyze Remediate Implement Violations Issues Changes Monitor Application Environment Extract ERP Data Corporate Access Controls Application Control Teams Business Process Teams IT Management
Application Controls Management Best Practices Determine Setup Manage Scope Preventive Exceptions by Controls Application Establish Rules Repository Establish Test Environment Detect Analyze Remediate Implement Violations Issues Changes Monitor Application Environment Extract ERP Data Corporate Access Controls Application Control Teams Business Process Teams IT Management
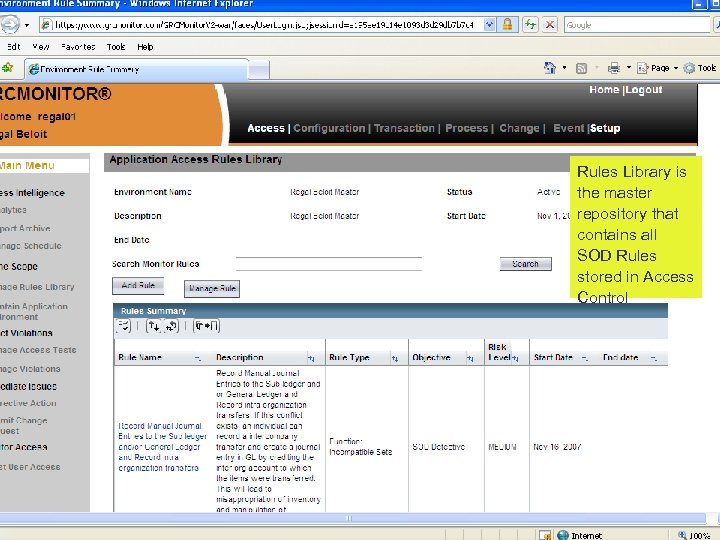 Rules Library is the master repository that contains all SOD Rules stored in Access Control
Rules Library is the master repository that contains all SOD Rules stored in Access Control
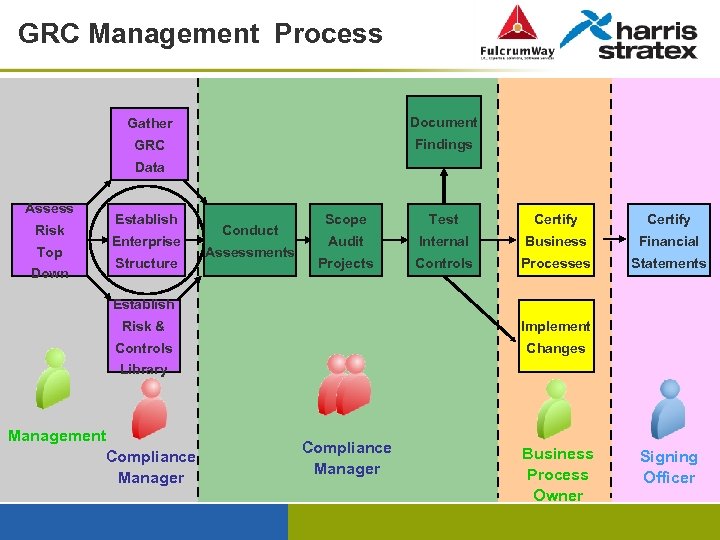 GRC Management Process Gather Document GRC Findings Data Assess Risk Top Down Establish Enterprise Structure Conduct Assessments Scope Test Certify Audit Internal Business Financial Projects Controls Processes Statements Establish Risk & Implement Controls Changes Library Management Compliance Manager Business Process Owner Signing Officer
GRC Management Process Gather Document GRC Findings Data Assess Risk Top Down Establish Enterprise Structure Conduct Assessments Scope Test Certify Audit Internal Business Financial Projects Controls Processes Statements Establish Risk & Implement Controls Changes Library Management Compliance Manager Business Process Owner Signing Officer
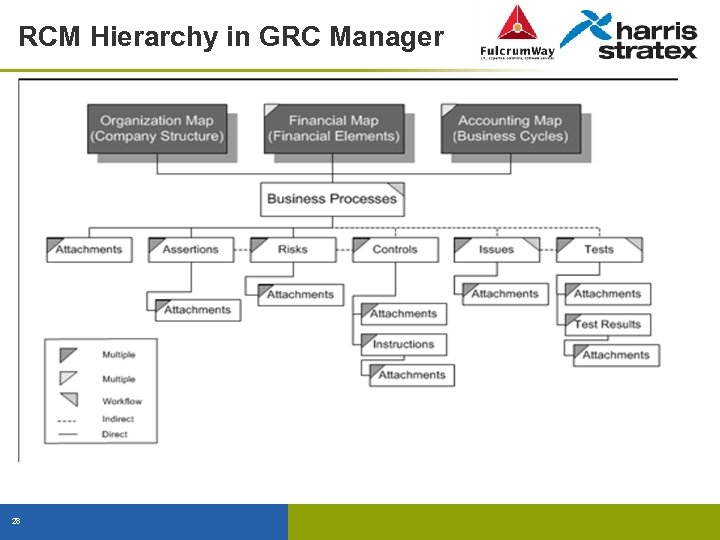 RCM Hierarchy in GRC Manager 28
RCM Hierarchy in GRC Manager 28
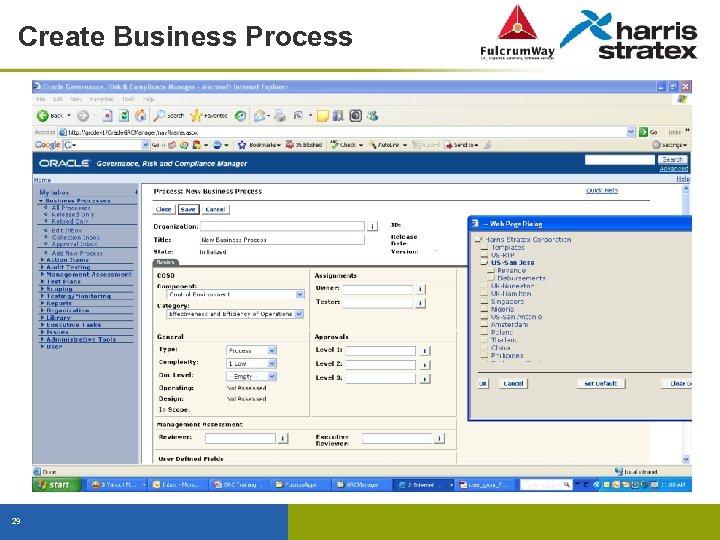 Create Business Process 29
Create Business Process 29
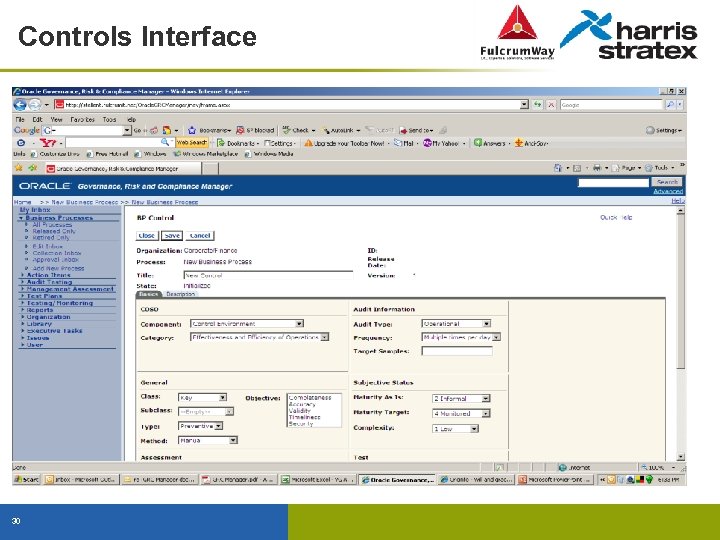 Controls Interface 30
Controls Interface 30
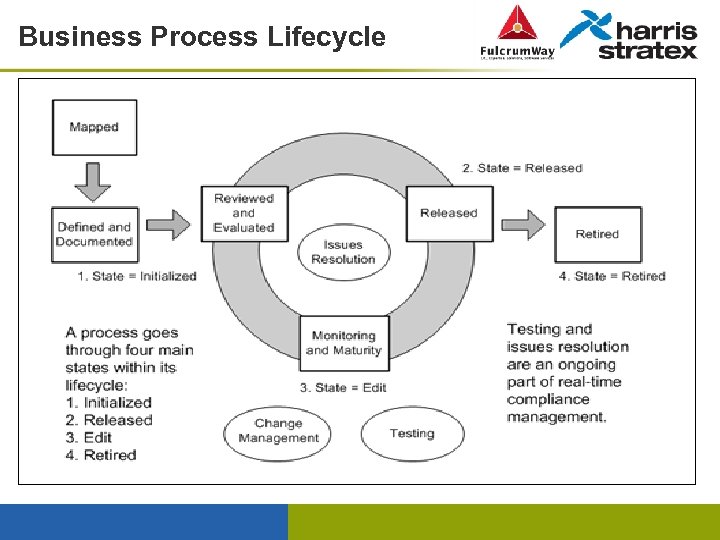 Business Process Lifecycle
Business Process Lifecycle
 Questions ?
Questions ?


