487878414a2fd4d14d34afc6c2b80756.ppt
- Количество слайдов: 18

Caribbean Cyber Security: “The Time for ACTION is NOW” WWW. CARIBBEANCSC. COM

Agenda • • • Global Cyber Security “Reality Check” Caribbean Cyber Crime Trends: 2013 & Beyond Caribbean Distribution of Targets Current Cyber Threat Sources Understanding Our Regional Cyber Security Posture Keeping the Right “BALANCE” The Global Cyber Security Response Profile of a HACKED system Recommended Action Plan (Public & Private Sectors) CCSC Support Services About the Caribbean Cyber Security Center (CCSC) • Mission, Vision, Value • Our Team • Implications for the Caribbean in Staying The Current “Unsecure” Course
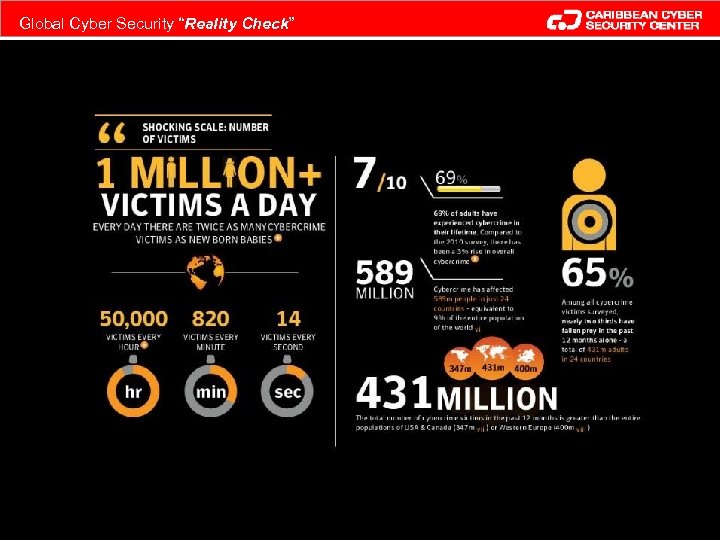
Global Cyber Security “Reality Check”
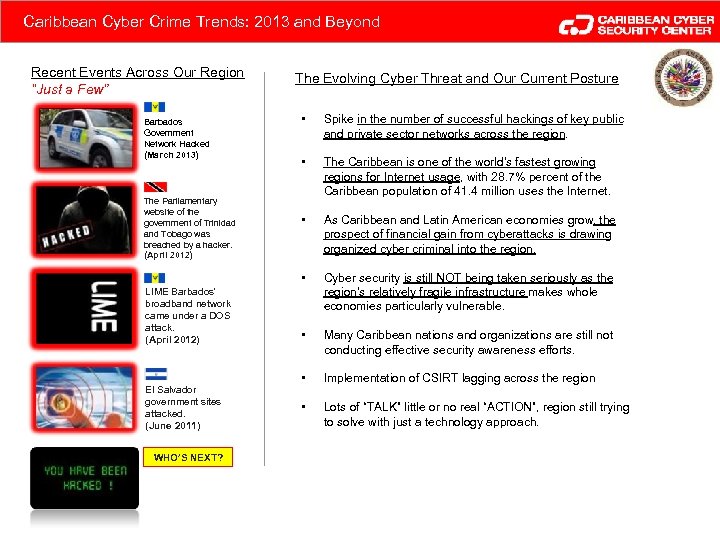
Caribbean Cyber Crime Trends: 2013 and Beyond Recent Events Across Our Region “Just a Few” The Evolving Cyber Threat and Our Current Posture The Parliamentary website of the government of Trinidad and Tobago was breached by a hacker. (April 2012) LIME Barbados' broadband network came under a DOS attack. (April 2012) El Salvador government sites attacked. (June 2011) WHO’S NEXT? • Spike in the number of successful hackings of key public and private sector networks across the region. • The Caribbean is one of the world's fastest growing regions for Internet usage, with 28. 7% percent of the Caribbean population of 41. 4 million uses the Internet. • As Caribbean and Latin American economies grow, the prospect of financial gain from cyberattacks is drawing organized cyber criminal into the region. • Barbados Government Network Hacked (March 2013) Cyber security is still NOT being taken seriously as the region's relatively fragile infrastructure makes whole economies particularly vulnerable. • Many Caribbean nations and organizations are still not conducting effective security awareness efforts. • Implementation of CSIRT lagging across the region • Lots of “TALK” little or no real “ACTION”, region still trying to solve with just a technology approach.
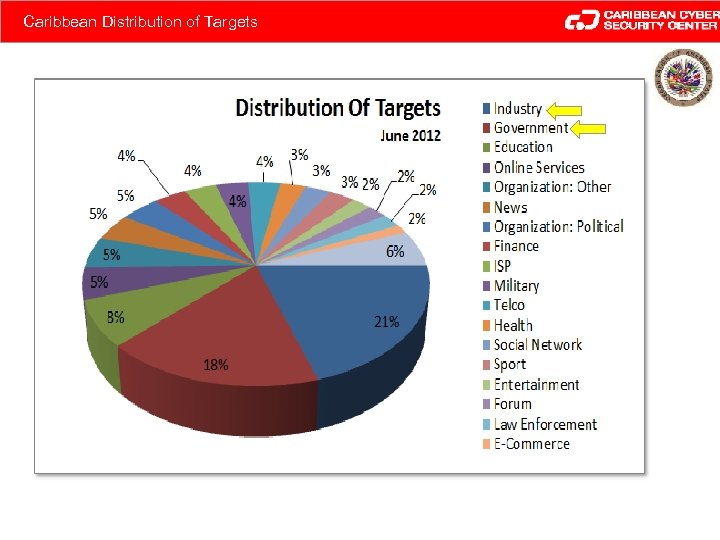
Caribbean Distribution of Targets
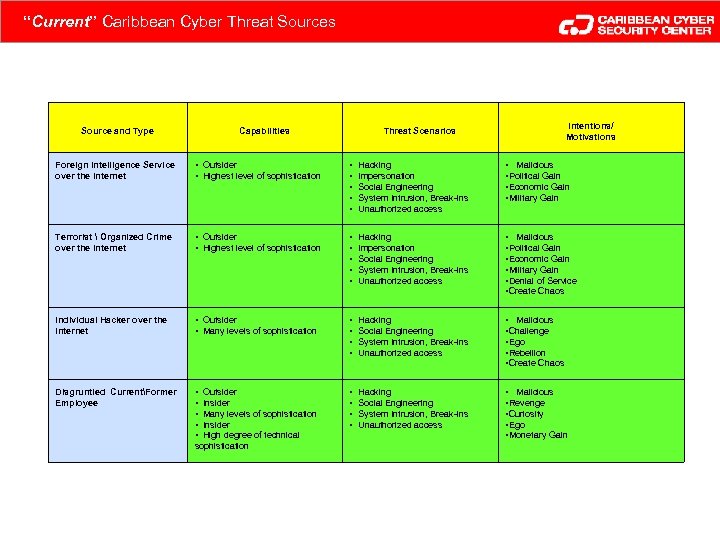
“Current” Caribbean Cyber Threat Sources Source and Type Capabilities Intentions/ Motivations Threat Scenarios Foreign Intelligence Service over the Internet • Outsider • Highest level of sophistication • • • Hacking Impersonation Social Engineering System Intrusion, Break-ins Unauthorized access • Malicious • Political Gain • Economic Gain • Military Gain Terrorist Organized Crime over the Internet • Outsider • Highest level of sophistication • • • Hacking Impersonation Social Engineering System Intrusion, Break-ins Unauthorized access • Malicious • Political Gain • Economic Gain • Military Gain • Denial of Service • Create Chaos Individual Hacker over the Internet • Outsider • Many levels of sophistication • • Hacking Social Engineering System Intrusion, Break-ins Unauthorized access • Malicious • Challenge • Ego • Rebellion • Create Chaos Disgruntled CurrentFormer Employee • Outsider • Insider • Many levels of sophistication • Insider • High degree of technical • • Hacking Social Engineering System Intrusion, Break-ins Unauthorized access • Malicious • Revenge • Curiosity • Ego • Monetary Gain sophistication

Understanding Our Regional Cyber Security Posture • Lack of readily available systems information and non-adherence to International Best Practices • Inability to effectively maintain the confidentiality, integrity and availability of systems. • With shrinking budgets in challenging economic times IT Security is placed on the back burner and hence cyber security is not viewed with the required sense of urgency by ICT leaders. • Consumerism – Departments have different buying practices with out consideration for software and hardware standards • Organizational difficulty obtaining management buy-in because cyber threats and cyber crime are seen as IT problems and not as critical business issues. • Cyber Crime is a global threat. Proceeds from Cyber Crime has out stripped the illegal drug trade. • No sense of urgency cause nothing catastrophic has happened “yet” • Overdependence on in-house ICT staff with no independent assessments being conducted.
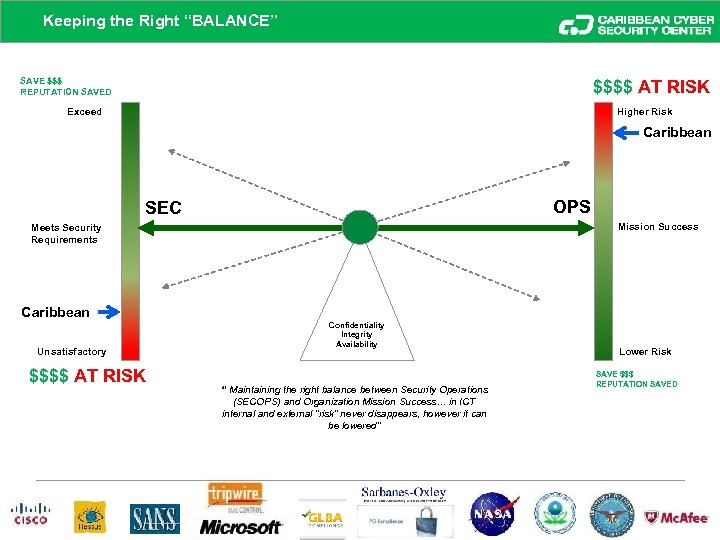
Keeping the Right “BALANCE” SAVE $$$ REPUTATION SAVED $$$$ AT RISK Exceed Higher Risk Caribbean OPS SEC Mission Success Meets Security Requirements Caribbean Unsatisfactory $$$$ AT RISK Confidentiality Integrity Availability “ Maintaining the right balance between Security Operations (SECOPS) and Organization Mission Success… in ICT internal and external “risk” never disappears, however it can be lowered” Lower Risk SAVE $$$ REPUTATION SAVED

The Global Cyber Security Response Developed Nations • The US, UK, Canada has recognized that is at a crossroads. The globally-interconnected digital information and communications infrastructure known as “cyberspace” underpins almost every facet of modern society and provides critical support for the U. S. economy, civil infrastructure, public safety, and national security. Caribbean Nations • • The status quo is no longer acceptable. The United States must signal to the world that it is serious about addressing this challenge with strong leadership and vision. The national dialogue on cyber security must begin today. The government, working with industry, should explain this challenge and discuss what the Nation can do to solve problems in a way that the American people can appreciate the need for action. The United States cannot succeed in securing cyberspace if it works in isolation. The Federal government should enhance its partnership with the private sector. There has been a lag in the implementation of effective national and regional cyber security legislation and policy frameworks which provides guidance to both the private and public sectors. • Political leaders in the region view cyber security as a “security” issue versus the “development” issue it is, noting our dependence on foreign reserves. • Current economic challenges has adversely impacted regional nations in allocating, or realigning ICT fiscal resources and support to cyber security efforts. • ICT leadership reluctant for independent assessment of their networks (culturalhuman factor). • • • We have not fully recognized that continued successful attack against a critical infrastructure in our region (like Banking) if publized globally can start a chain reaction and can adverse impact many regional economy’s.
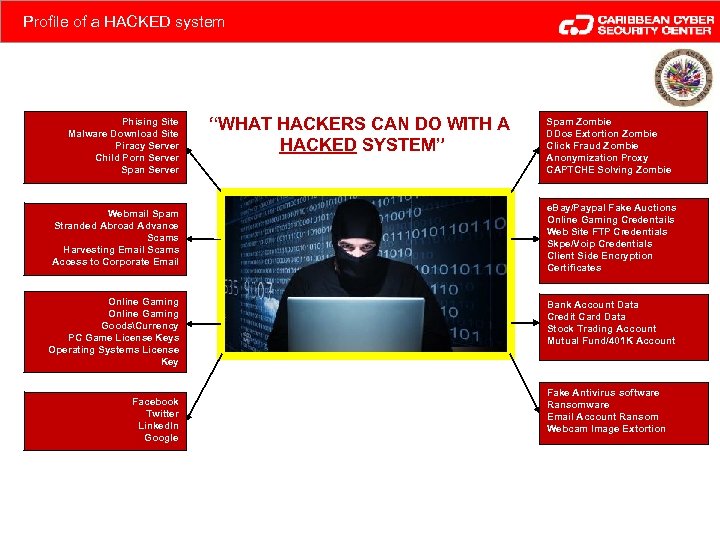
Profile of a HACKED system Phising Site Malware Download Site Piracy Server Child Porn Server Span Server Webmail Spam Stranded Abroad Advance Scams Harvesting Email Scams Access to Corporate Email Online Gaming GoodsCurrency PC Game License Keys Operating Systems License Key Facebook Twitter Linked. In Google “WHAT HACKERS CAN DO WITH A HACKED SYSTEM” Spam Zombie DDos Extortion Zombie Click Fraud Zombie Anonymization Proxy CAPTCHE Solving Zombie e. Bay/Paypal Fake Auctions Online Gaming Credentails Web Site FTP Credentials Skpe/Voip Credentials Client Side Encryption Certificates Bank Account Data Credit Card Data Stock Trading Account Mutual Fund/401 K Account Fake Antivirus software Ransomware Email Account Ransom Webcam Image Extortion
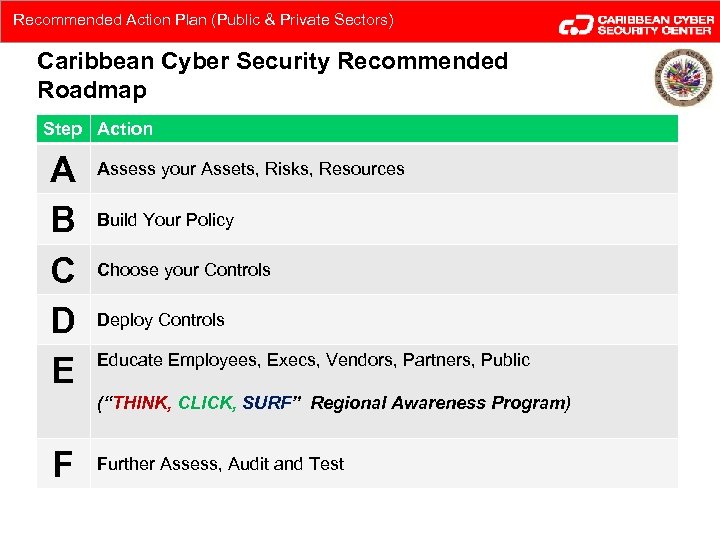
Recommended Action Plan (Public & Private Sectors) Caribbean Cyber Security Recommended Roadmap Step Action A B C D E Assess your Assets, Risks, Resources Build Your Policy Choose your Controls Deploy Controls Educate Employees, Execs, Vendors, Partners, Public (“THINK, CLICK, SURF” Regional Awareness Program) F Further Assess, Audit and Test
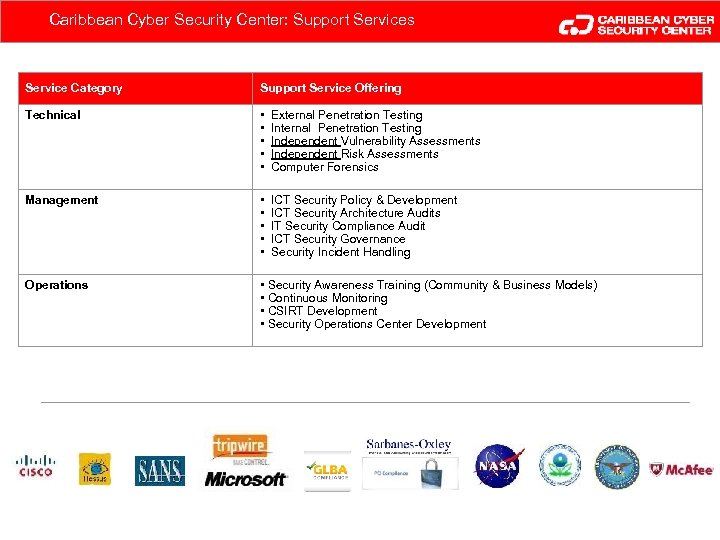
Caribbean Cyber Security Center: Support Services Service Category Support Service Offering Technical • External Penetration Testing • Independent Vulnerability Assessments • Independent Risk Assessments • Computer Forensics Management • ICT Security Policy & Development • ICT Security Architecture Audits • IT Security Compliance Audit • ICT Security Governance • Security Incident Handling Operations • Security Awareness Training (Community & Business Models) • Continuous Monitoring • CSIRT Development • Security Operations Center Development

VALUE In the rapidly evolving world of cyber threats and vulnerabilities our mission is the protection of Caribbean private and public ICT information systems and resources, as a regional development issue. To become a recognized “hands -on” regional cyber security and information assurance resource for ICT Penetration Testing, Vulnerability Assessment, Risk Assessments, Security Awareness Training and ICT Security Governance/Policy development support. We have harnessed a best of breed team of recognized and experienced cyber security and information assurance consultants and technology partners, who are well versed in global cyber security compliance standards and best practices.
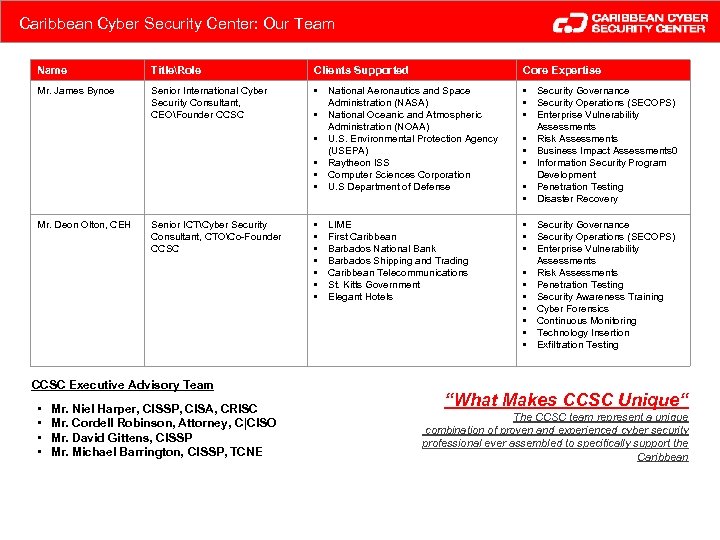
Caribbean Cyber Security Center: Our Team Name TitleRole Clients Supported Core Expertise Mr. James Bynoe Senior International Cyber Security Consultant, CEOFounder CCSC • National Aeronautics and Space Administration (NASA) • National Oceanic and Atmospheric Administration (NOAA) • U. S. Environmental Protection Agency (USEPA) • Raytheon ISS • Computer Sciences Corporation • U. S Department of Defense • Security Governance • Security Operations (SECOPS) • Enterprise Vulnerability Assessments • Risk Assessments • Business Impact Assessments 0 • Information Security Program Development • Penetration Testing • Disaster Recovery Mr. Deon Olton, CEH Senior ICTCyber Security Consultant, CTOCo-Founder CCSC • • Security Governance • Security Operations (SECOPS) • Enterprise Vulnerability Assessments • Risk Assessments • Penetration Testing • Security Awareness Training • Cyber Forensics • Continuous Monitoring • Technology Insertion • Exfiltration Testing CCSC Executive Advisory Team • • Mr. Niel Harper, CISSP, CISA, CRISC Mr. Cordell Robinson, Attorney, C|CISO Mr. David Gittens, CISSP Mr. Michael Barrington, CISSP, TCNE LIME First Caribbean Barbados National Bank Barbados Shipping and Trading Caribbean Telecommunications St. Kitts Government Elegant Hotels “What Makes CCSC Unique“ The CCSC team represent a unique combination of proven and experienced cyber security professional ever assembled to specifically support the Caribbean
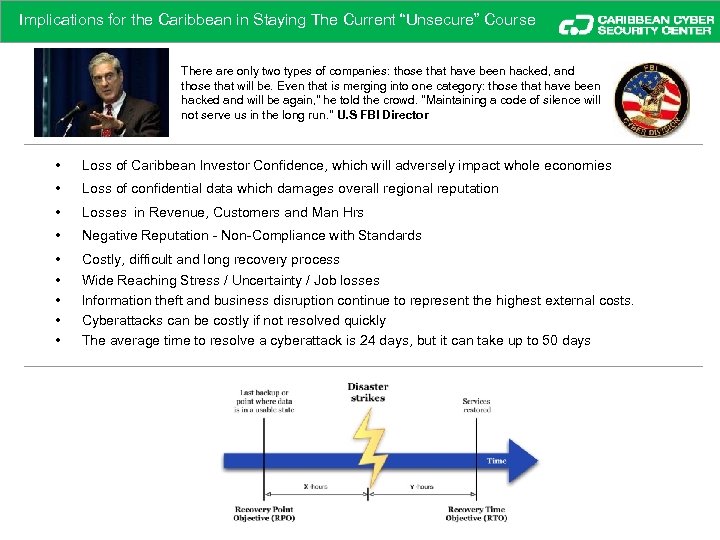
Implications for the Caribbean in Staying The Current “Unsecure” Course There are only two types of companies: those that have been hacked, and those that will be. Even that is merging into one category: those that have been hacked and will be again, " he told the crowd. "Maintaining a code of silence will not serve us in the long run. " U. S FBI Director • Loss of Caribbean Investor Confidence, which will adversely impact whole economies • Loss of confidential data which damages overall regional reputation • Losses in Revenue, Customers and Man Hrs • Negative Reputation - Non-Compliance with Standards • • • Costly, difficult and long recovery process Wide Reaching Stress / Uncertainty / Job losses Information theft and business disruption continue to represent the highest external costs. Cyberattacks can be costly if not resolved quickly The average time to resolve a cyberattack is 24 days, but it can take up to 50 days

our web presenceportal: www. caribbeancsc. com

contact Information James Bynoe james. bynoe@caribbeancsc. com 202 -640 -8085 Deon Olton deon. olton@caribbeancsc. com 246 -232 -9009 Michael Barrington michael. barrington@caribbeancsc. com 443 -854 -1573 WWW. CARIBBEANCSC. COM

Thank You For Attending!!
487878414a2fd4d14d34afc6c2b80756.ppt