a1770552b1a1f206aa57bef46b897137.ppt
- Количество слайдов: 46

CAP 6135: Malware and Software Vulnerability Analysis Spam and Phishing Cliff Zou Spring 2012

Acknowledgement q This lecture uses some contents from the lecture notes from: q q Dr. Dan Boneh (Stanford): CS 155: Computer and Network Security Jim Kurose, Keith Ross. Computer Networking: A Top Down Approach Featuring the Internet, 5 th edition. 2
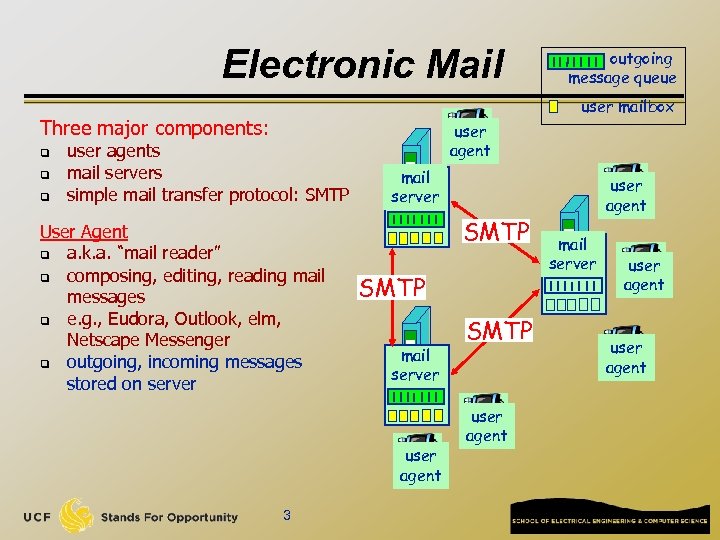
Electronic Mail user mailbox Three major components: q q q outgoing message queue user agents mail servers simple mail transfer protocol: SMTP User Agent q a. k. a. “mail reader” q composing, editing, reading mail messages q e. g. , Eudora, Outlook, elm, Netscape Messenger q outgoing, incoming messages stored on server user agent mail server SMTP mail server user agent 3 SMTP user agent mail server user agent
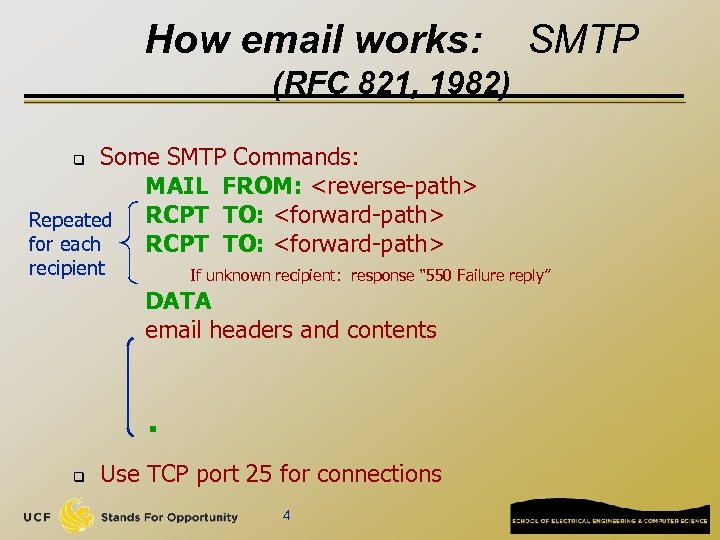
How email works: SMTP (RFC 821, 1982) Some SMTP Commands: MAIL FROM: <reverse-path> RCPT TO: <forward-path> Repeated for each RCPT TO: <forward-path> q recipient If unknown recipient: response “ 550 Failure reply” DATA email headers and contents . q Use TCP port 25 for connections 4
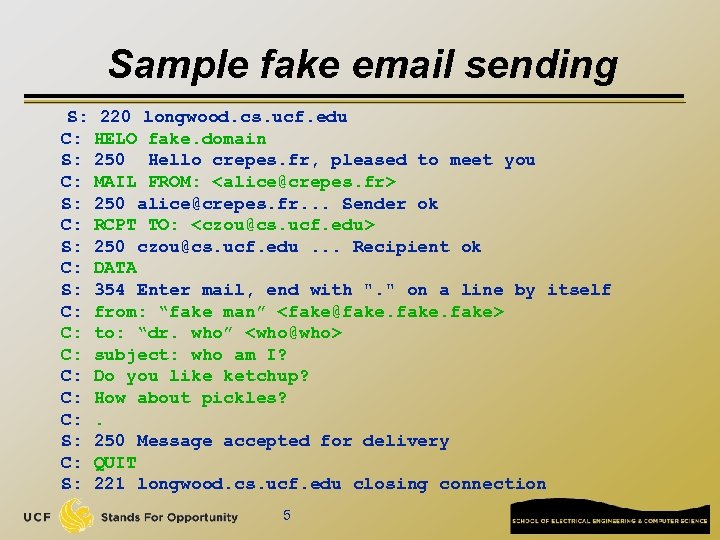
Sample fake email sending S: 220 longwood. cs. ucf. edu C: HELO fake. domain S: 250 Hello crepes. fr, pleased to meet you C: MAIL FROM: <alice@crepes. fr> S: 250 alice@crepes. fr. . . Sender ok C: RCPT TO: <czou@cs. ucf. edu> S: 250 czou@cs. ucf. edu. . . Recipient ok C: DATA S: 354 Enter mail, end with ". " on a line by itself C: from: “fake man” <fake@fake> C: to: “dr. who” <who@who> C: subject: who am I? C: Do you like ketchup? C: How about pickles? C: . S: 250 Message accepted for delivery C: QUIT S: 221 longwood. cs. ucf. edu closing connection 5
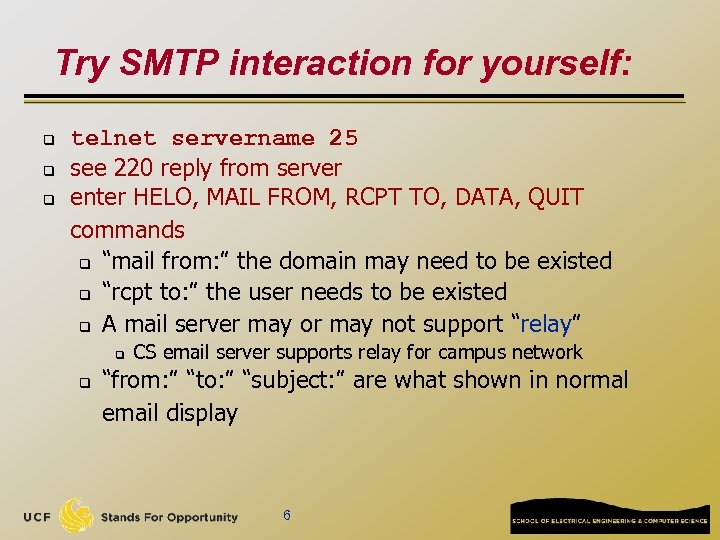
Try SMTP interaction for yourself: q q q telnet servername 25 see 220 reply from server enter HELO, MAIL FROM, RCPT TO, DATA, QUIT commands q “mail from: ” the domain may need to be existed q “rcpt to: ” the user needs to be existed q A mail server may or may not support “relay” q q CS email server supports relay for campus network “from: ” “to: ” “subject: ” are what shown in normal email display 6
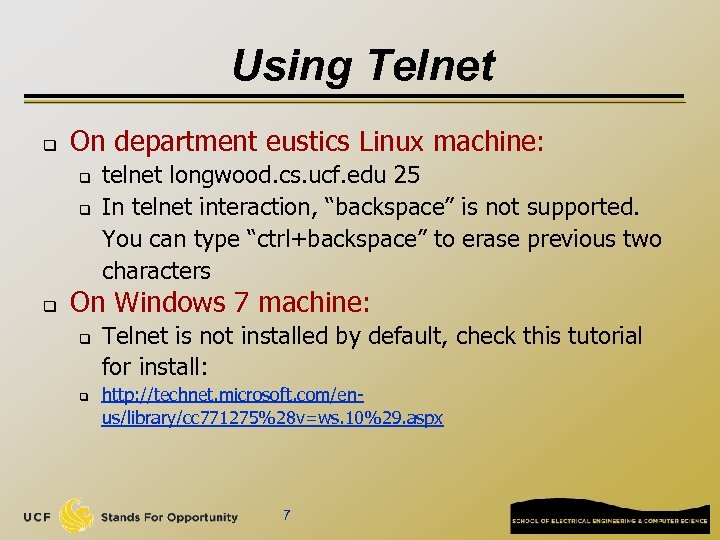
Using Telnet q On department eustics Linux machine: q q q telnet longwood. cs. ucf. edu 25 In telnet interaction, “backspace” is not supported. You can type “ctrl+backspace” to erase previous two characters On Windows 7 machine: q q Telnet is not installed by default, check this tutorial for install: http: //technet. microsoft. com/enus/library/cc 771275%28 v=ws. 10%29. aspx 7
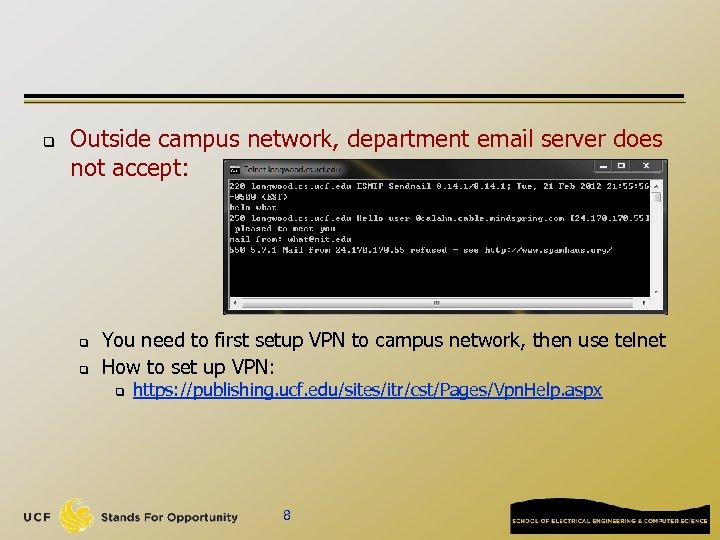
q Outside campus network, department email server does not accept: q q You need to first setup VPN to campus network, then use telnet How to set up VPN: q https: //publishing. ucf. edu/sites/itr/cst/Pages/Vpn. Help. aspx 8
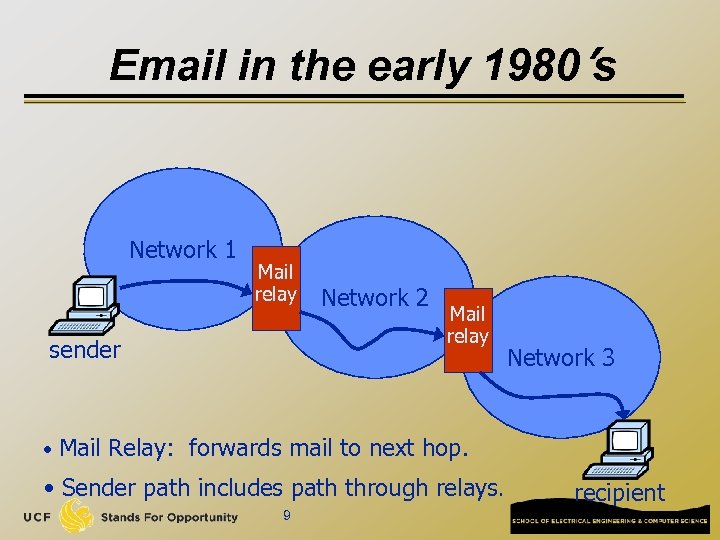
Email in the early 1980’s Network 1 Mail relay sender Network 2 Mail relay Network 3 • Mail Relay: forwards mail to next hop. • Sender path includes path through relays. 9 recipient
Why Email Server Support Relay? q Wiki tutorial: q q q Old days network constraint makes it necessary Email agent uses SMTP to send email on behalf of a user q q The user could choose which email address to use as the sender Email server supports email group list: q q http: //en. wikipedia. org/wiki/Open_mail_relay The “sender” shown in email is the group list address, but the real sender is a different person Closing Relay: q q Messages from local IP addresses to local mailboxes local IP addresses to non-local mailboxes non-local IP addresses to local mailboxes clients that are authenticated and authorized 10

Spoofed email q SMTP: designed for a trusting world … q Data in MAIL FROM totally under control of sender q q … an old example of improper input validation Recipient’s mail server: q q Only sees IP address of direct peer Recorded in the first From header 11
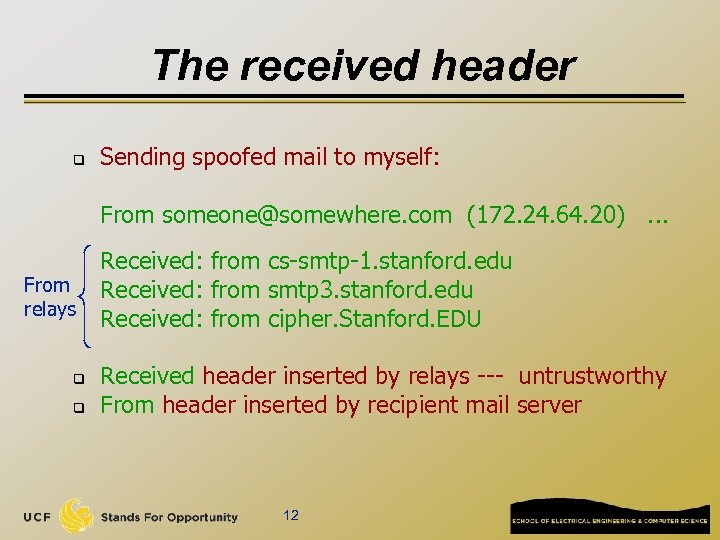
The received header q Sending spoofed mail to myself: From someone@somewhere. com (172. 24. 64. 20). . . From relays q q Received: from cs-smtp-1. stanford. edu Received: from smtp 3. stanford. edu Received: from cipher. Stanford. EDU Received header inserted by relays --- untrustworthy From header inserted by recipient mail server 12
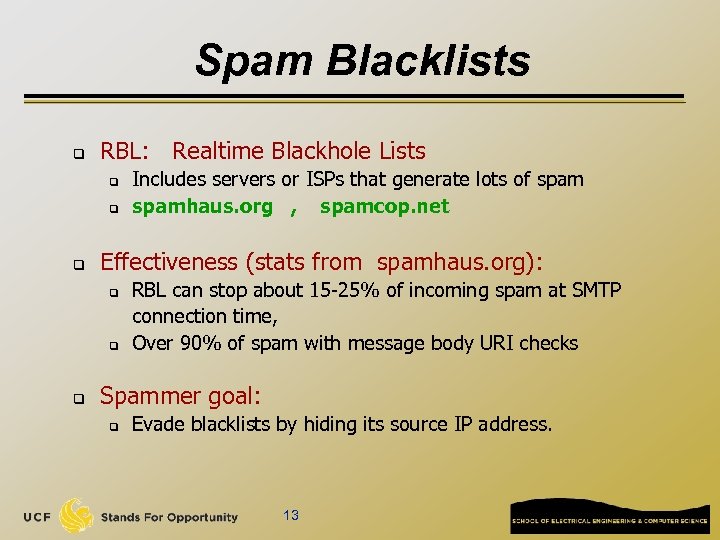
Spam Blacklists q RBL: Realtime Blackhole Lists q q q Effectiveness (stats from spamhaus. org): q q q Includes servers or ISPs that generate lots of spamhaus. org , spamcop. net RBL can stop about 15 -25% of incoming spam at SMTP connection time, Over 90% of spam with message body URI checks Spammer goal: q Evade blacklists by hiding its source IP address. 13

Spamming techniques
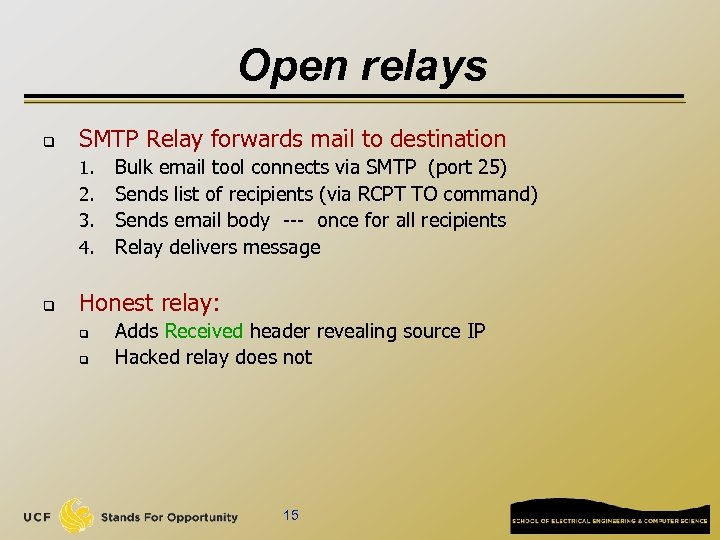
Open relays q SMTP Relay forwards mail to destination 1. 2. 3. 4. q Bulk email tool connects via SMTP (port 25) Sends list of recipients (via RCPT TO command) Sends email body --- once for all recipients Relay delivers message Honest relay: q q Adds Received header revealing source IP Hacked relay does not 15

Example: bobax worm q Infects machines with high bandwidth q q Slow spreading: q q q Exploits MS LSASS. exe buffer overflow vulnerability Spreads on manual command from operator Then randomly scans for vulnerable machines On infected machine: q q (spam zombie) Installs hacked open mail relay. Used for spam. Once spam zombie added to RBL: q Worm spreads to other machines 16
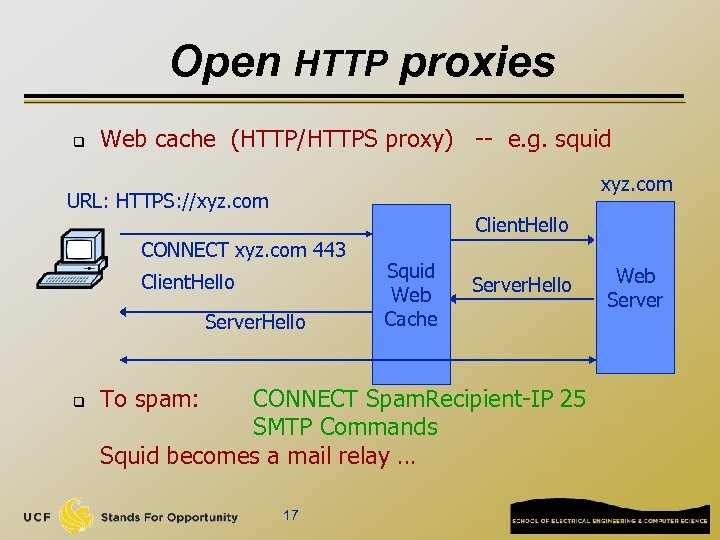
Open HTTP proxies q Web cache (HTTP/HTTPS proxy) -- e. g. squid xyz. com URL: HTTPS: //xyz. com Client. Hello CONNECT xyz. com 443 Client. Hello Server. Hello q To spam: Squid Web Cache Server. Hello CONNECT Spam. Recipient-IP 25 SMTP Commands Squid becomes a mail relay … 17 Web Server
Finding proxies q Squid manual: (squid. conf) acl Safe_ports port 80 443 http_access deny !Safe_ports q URLs for other ports will be denied q Similar problem with SOCKS proxies q Some open proxy and open relay listing services: q http: //www. multiproxy. org/ http: //www. stayinvisible. com/ http: //www. blackcode. com/proxy/ http: //www. openproxies. com/ (20$/month) 18
Open Relays vs. Open Proxies q HTTP proxy design problem: q Port 25 should have been blocked by default q q Otherwise, violates principal of least privilege Relay vs. proxy: q q Relay takes list of address and send msg to all Proxy: spammer must send msg body to each recipient through proxy. zombies typically provide hacked mail relays. 19
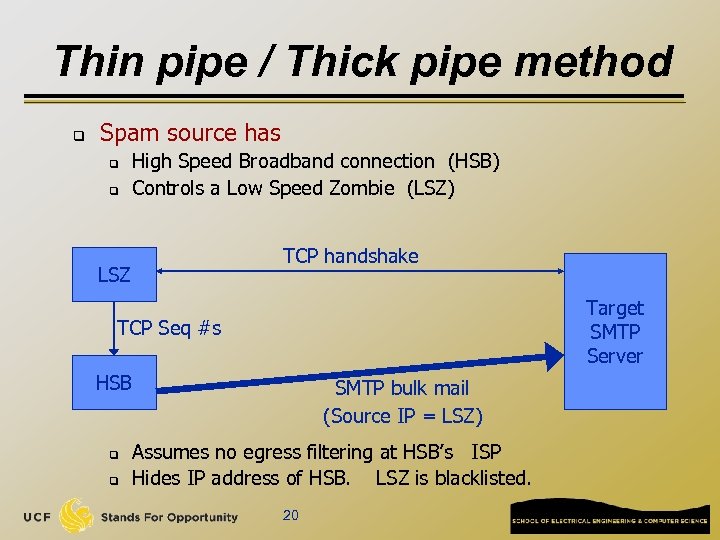
Thin pipe / Thick pipe method q Spam source has q q High Speed Broadband connection (HSB) Controls a Low Speed Zombie (LSZ) TCP handshake LSZ Target SMTP Server TCP Seq #s HSB q q SMTP bulk mail (Source IP = LSZ) Assumes no egress filtering at HSB’s ISP Hides IP address of HSB. LSZ is blacklisted. 20

Bulk email tools q (spamware) Automate: q Message personalization q q Also test against spam filters (e. g. spamassassin) Mailing list and proxy list management 21
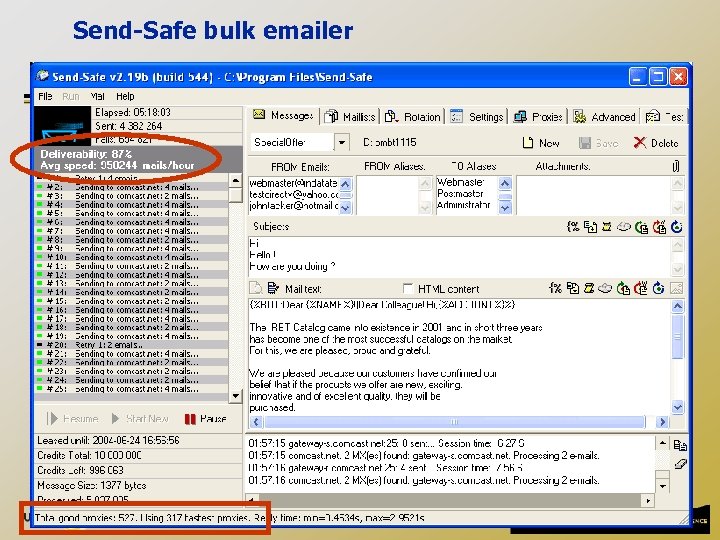
Send-Safe bulk emailer 22

Anti-spam methods

The law: CAN-SPAM act q (Jan. 2004) Bans false or misleading header information q To: and From: headers must be accurate q Prohibits deceptive subject lines q Requires an opt-out method q Requires that email be identified as advertisement q q . . . and include sender's physical postal address Also prohibits various forms of email harvesting and the use of proxies 24
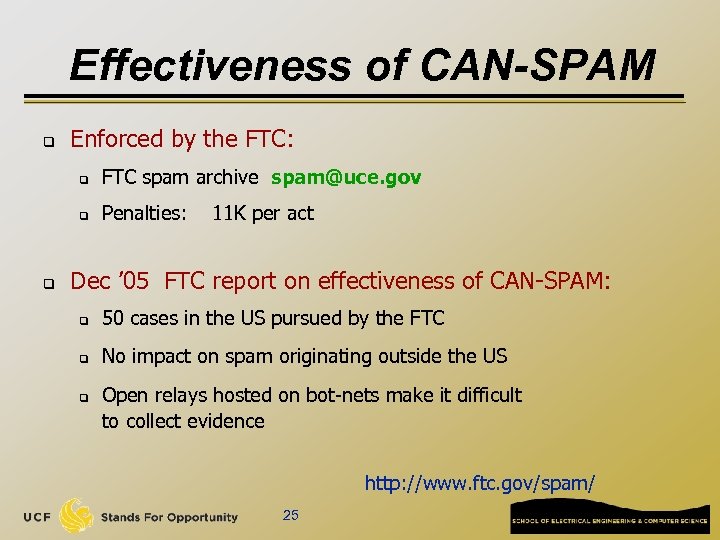
Effectiveness of CAN-SPAM q Enforced by the FTC: q q q FTC spam archive spam@uce. gov Penalties: 11 K per act Dec ’ 05 FTC report on effectiveness of CAN-SPAM: q 50 cases in the US pursued by the FTC q No impact on spam originating outside the US q Open relays hosted on bot-nets make it difficult to collect evidence http: //www. ftc. gov/spam/ 25
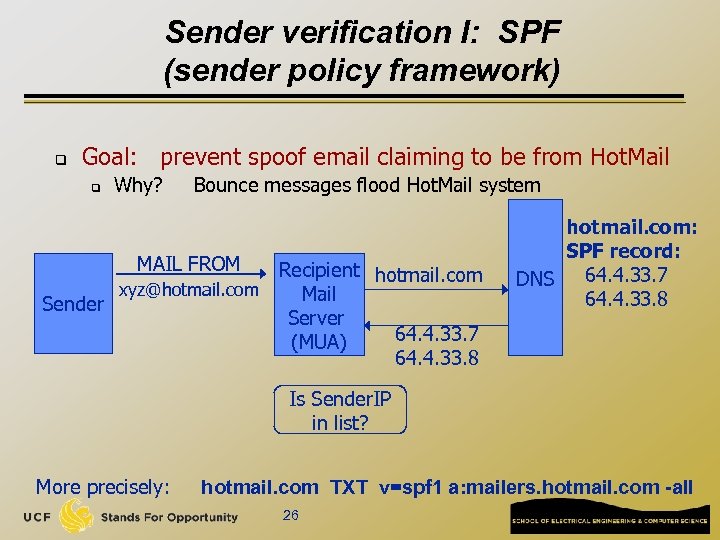
Sender verification I: SPF (sender policy framework) q Goal: prevent spoof email claiming to be from Hot. Mail q Why? Bounce messages flood Hot. Mail system MAIL FROM Sender xyz@hotmail. com Recipient hotmail. com Mail Server 64. 4. 33. 7 (MUA) 64. 4. 33. 8 hotmail. com: SPF record: 64. 4. 33. 7 DNS 64. 4. 33. 8 Is Sender. IP in list? More precisely: hotmail. com TXT v=spf 1 a: mailers. hotmail. com -all 26
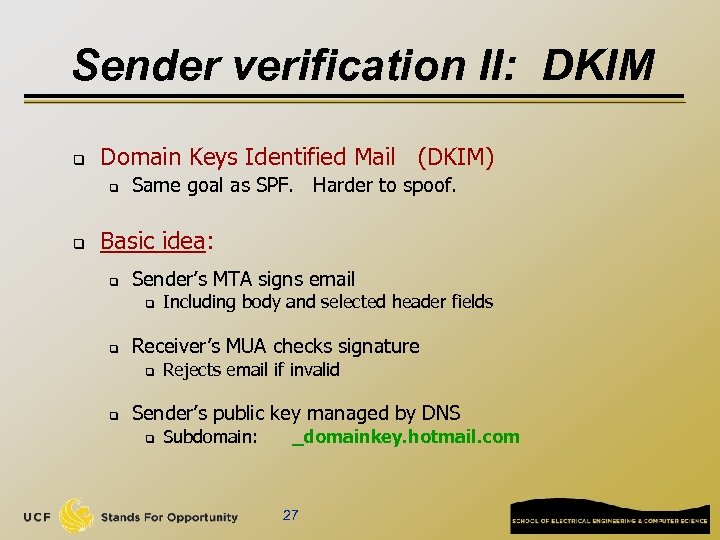
Sender verification II: DKIM q Domain Keys Identified Mail (DKIM) q q Same goal as SPF. Harder to spoof. Basic idea: q Sender’s MTA signs email q q Receiver’s MUA checks signature q q Including body and selected header fields Rejects email if invalid Sender’s public key managed by DNS q Subdomain: _domainkey. hotmail. com 27
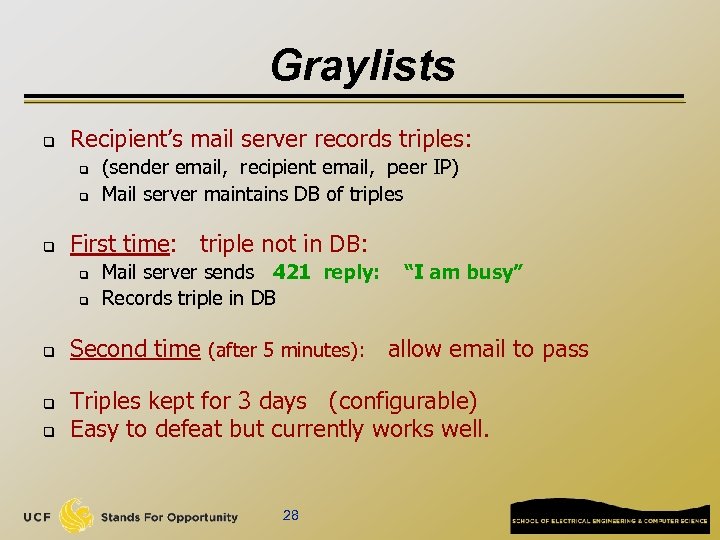
Graylists q Recipient’s mail server records triples: q q q First time: triple not in DB: q q q (sender email, recipient email, peer IP) Mail server maintains DB of triples Mail server sends 421 reply: Records triple in DB “I am busy” Second time (after 5 minutes): allow email to pass Triples kept for 3 days (configurable) Easy to defeat but currently works well. 28
Puzzles and CAPTCHA q General DDo. S defense techniques q Puzzles: slow down spam server q q Every email contains solution to puzzle where challenge = (sender, recipient, time) CAPTCHA: q q q Completely Automated Public Turing test to tell Computers and Humans Apart Every email contains a token Sender obtains tokens from a CAPTCHA server q q q Say: 100 tokens for solving a CAPTCHA server ensures tokens are not reused Either method is difficult to deploy. 29

Spam. Assasin q Wiki tutorial: q q http: //en. wikipedia. org/wiki/Spam. Assassin Mainly a rule-based spam filter q Many rules to give scores for all fields in an email q q Final decision is the combined score compared with a threshold Has false positive (treat normal as spam), and false negative (treat spam as normal) False positive is very damaging! q q Nobody wants to lose an important email! Also contains Bayesian filtering to match a user’s statistical profile q q Email header, special keywords in email, URLs in email, images in email, …. . Need known “ham” and “spam” email samples for training 30

Part II: Phishing & Pharming
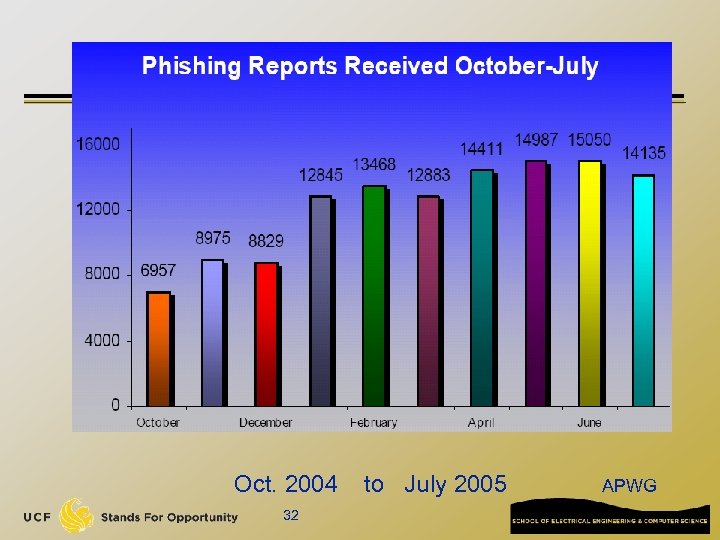
Oct. 2004 32 to July 2005 APWG
33
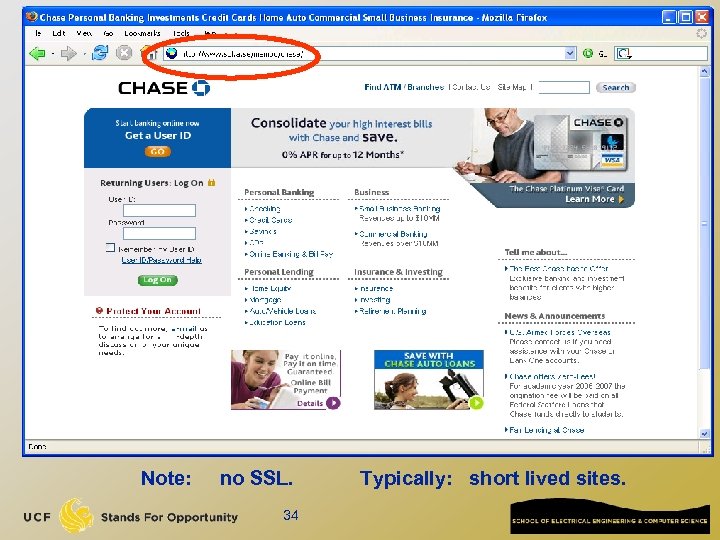
Note: no SSL. 34 Typically: short lived sites.
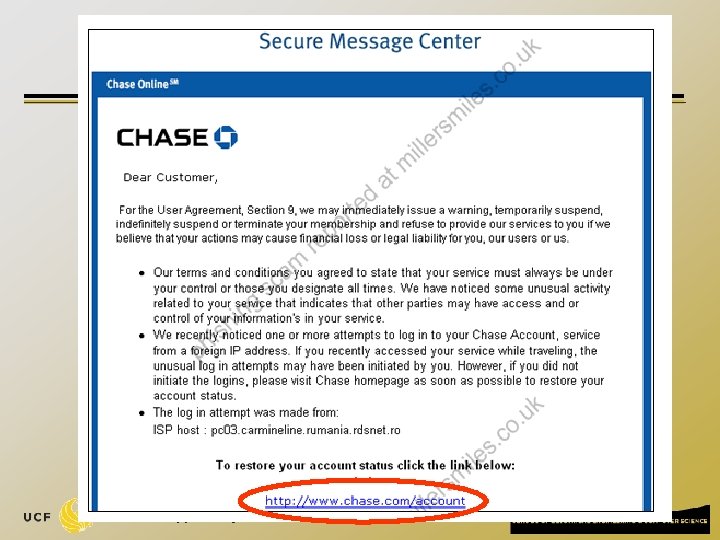
Common Phishing Methods q Often phishing sites hosted on bot-net drones. q q Move from bot to bot using dynamic DNS. Use domain names such as: www. ebay. com. badguy. com q Use URLs with multiple redirections: http: //www. chase. com/url. php? url=“http: //www. phish. com” q Use randomized links: q http: //www. some-poor-sap. com/823548 jd/ 35
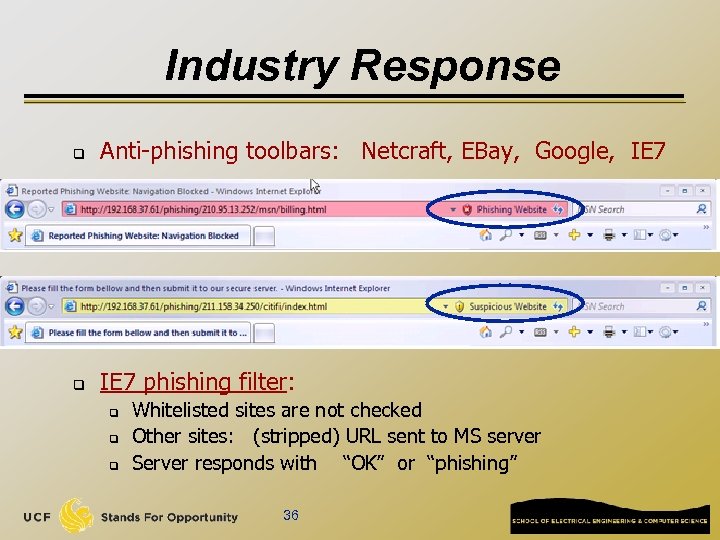
Industry Response q Anti-phishing toolbars: Netcraft, EBay, Google, IE 7 q IE 7 phishing filter: q q q Whitelisted sites are not checked Other sites: (stripped) URL sent to MS server Server responds with “OK” or “phishing” 36

Pharming q Cause DNS to point to phishing site q Examples: 1. 2. q DNS cache poisoning Write an entry into machine’s /etc/hosts file: “ Phisher-IP Victim-Name ” URL of phishing site is identical to victim’s URL q … will bypass all URL checks 37
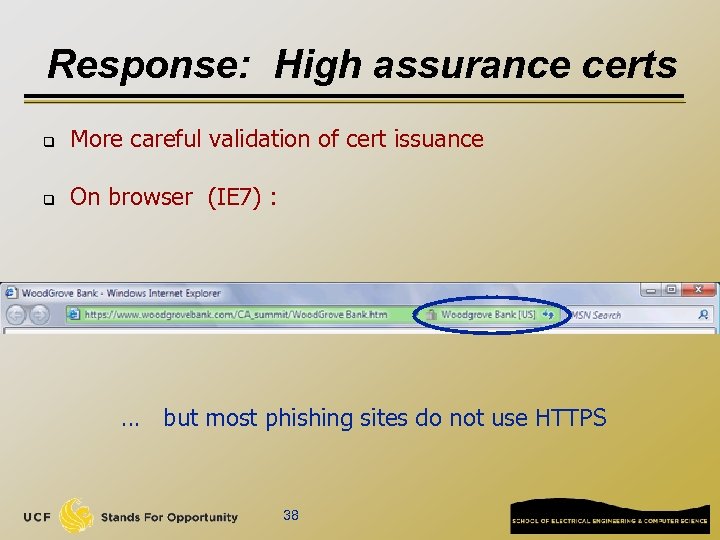
Response: High assurance certs q More careful validation of cert issuance q On browser (IE 7) : … but most phishing sites do not use HTTPS 38
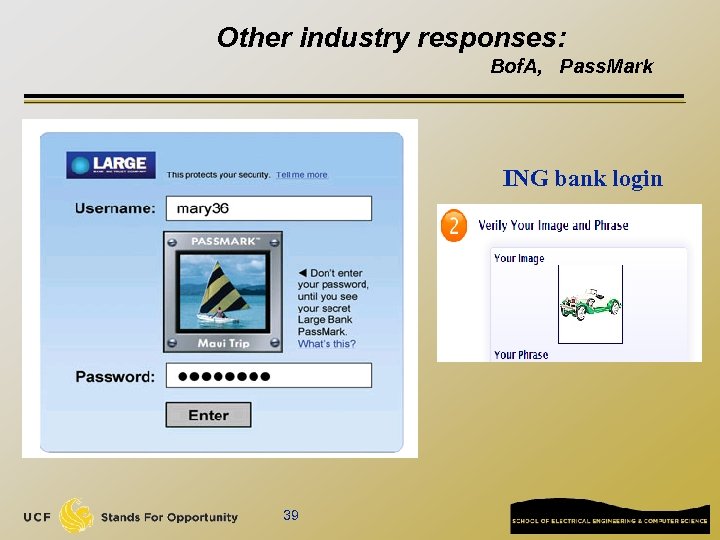
Other industry responses: Bof. A, Pass. Mark ING bank login 39
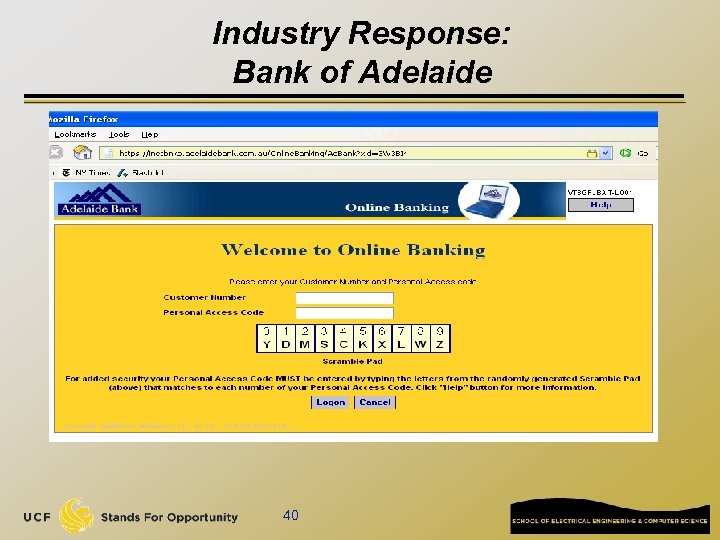
Industry Response: Bank of Adelaide 40
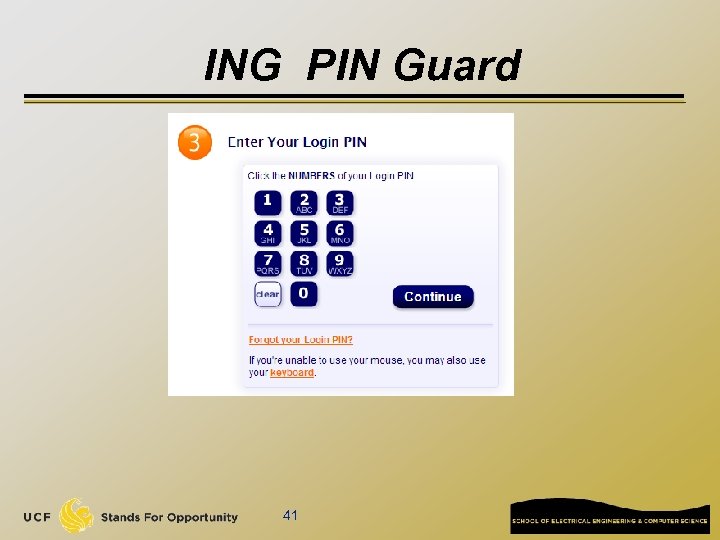
ING PIN Guard 41
T. G. s: The next phishing wave q Transaction generation malware: q q Wait for user to login to banking sites Issue money transfer requests on behalf of user. Reported malware in UK targeting all four major banks. Note: These are social engineering attacks. Not just a windows problem. 42

Some ID Protection Tools q Spoof. Guard: (NDSS ’ 04) q Alerts user when viewing a spoofed web page. q Uses variety of heuristics to identify spoof pages. q q Some Spoof. Guard heuristics used in e. Bay toolbar and Earthlink Scam. Blocker. Pwd. Hash: (Usenix Sec ’ 05) q Browser extension for strengthening pwd web auth. q Being integrated with RSA Secur. ID. 43
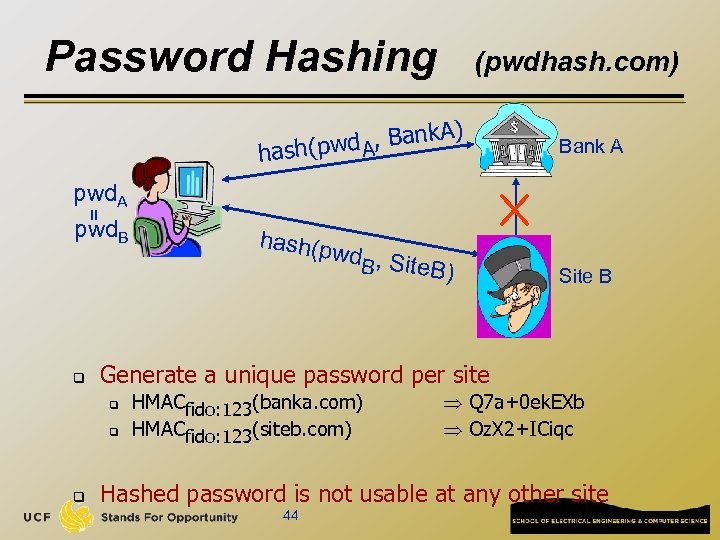
Password Hashing (pwdhash. com) ) d A, Bank. A hash(pw = pwd. A pwd. B Bank A q wd , S B ite. B) Site B Generate a unique password per site q q q hash(p HMACfido: 123(banka. com) HMACfido: 123(siteb. com) Q 7 a+0 ek. EXb Oz. X 2+ICiqc Hashed password is not usable at any other site 44
Our New Proposed Approach: Pwd. IP-Hash q Problem of Pwd. Hash: q q q Basic Idea: User password is first hashed with remote server’s IP address + domain name, then transmit to the remote server Reason: a remote server cannot lie about its IP address q q TCP connection has already set up, very hard to lie Result: The remote server receives a hashed password q q q cannot deal with Phishing attack The real server has the plain password and can verify The phishing server cannot use the hashed password for login See our prototype at: q q http: //www. cs. ucf. edu/~czou/Pwd. IP-Hash/ Paper published in conference IEEE NCA 2010. 45

Take home message q Deployed insecure services (proxies, relays) q q q Quickly exploited Cause trouble for everyone Current web user authentication is vulnerable to spoofing q Users are easily fooled into entering password in an insecure location 46
a1770552b1a1f206aa57bef46b897137.ppt