 c h a p t e r 14 INFORMATION SYSTEMS SECURITY & CONTROL 14. 1 © 2002 by Prentice Hall
c h a p t e r 14 INFORMATION SYSTEMS SECURITY & CONTROL 14. 1 © 2002 by Prentice Hall
 LEARNING OBJECTIVES • DEMONSTRATE WHY INFO SYSTEMS ARE VULNERABLE TO DESTRUCTION, ERROR, ABUSE, QUALITY CONTROL PROBLEMS • COMPARE GENERAL AND APPLICATION CONTROLS * 14. 2 © 2002 by Prentice Hall
LEARNING OBJECTIVES • DEMONSTRATE WHY INFO SYSTEMS ARE VULNERABLE TO DESTRUCTION, ERROR, ABUSE, QUALITY CONTROL PROBLEMS • COMPARE GENERAL AND APPLICATION CONTROLS * 14. 2 © 2002 by Prentice Hall
 LEARNING OBJECTIVES • DESCRIBE MEASURES TO ENSURE RELIABILITY, AVAILABILITY, SECURITY OF E-COMMERCE, DIGITAL BUSINESS PROCESSES * 14. 3 © 2002 by Prentice Hall
LEARNING OBJECTIVES • DESCRIBE MEASURES TO ENSURE RELIABILITY, AVAILABILITY, SECURITY OF E-COMMERCE, DIGITAL BUSINESS PROCESSES * 14. 3 © 2002 by Prentice Hall
 LEARNING OBJECTIVES • DESCRIBE IMPORTANT SOFTWARE QUALITY- ASSURANCE TECHNIQUES • DEMONSTRATE IMPORTANCE OF AUDITING INFO SYSTEMS & SAFEGUARDING DATA QUALITY * 14. 4 © 2002 by Prentice Hall
LEARNING OBJECTIVES • DESCRIBE IMPORTANT SOFTWARE QUALITY- ASSURANCE TECHNIQUES • DEMONSTRATE IMPORTANCE OF AUDITING INFO SYSTEMS & SAFEGUARDING DATA QUALITY * 14. 4 © 2002 by Prentice Hall
 MANAGEMENT CHALLENGES • SYSTEM VULNERABILITY & ABUSE • CREATING A CONTROL ENVIRONMENT • ENSURING SYSTEM QUALITY * 14. 5 © 2002 by Prentice Hall
MANAGEMENT CHALLENGES • SYSTEM VULNERABILITY & ABUSE • CREATING A CONTROL ENVIRONMENT • ENSURING SYSTEM QUALITY * 14. 5 © 2002 by Prentice Hall
 SYSTEM VULNERABILITY & ABUSE • • • WHY SYSTEMS ARE VULNERABLE HACKERS & VIRUSES CONCERNS FOR BUILDERS & USERS • SYSTEM QUALITY PROBLEMS * 14. 6 © 2002 by Prentice Hall
SYSTEM VULNERABILITY & ABUSE • • • WHY SYSTEMS ARE VULNERABLE HACKERS & VIRUSES CONCERNS FOR BUILDERS & USERS • SYSTEM QUALITY PROBLEMS * 14. 6 © 2002 by Prentice Hall
 THREATS TO INFORMATION SYSTEMS HARDWARE FAILURE, FIRE SOFTWARE FAILURE, ELECTRICAL PROBLEMS PERSONNEL ACTIONS, USER ERRORS ACCESS PENETRATION, PROGRAM CHANGES THEFT OF DATA, SERVICES, EQUIPMENT TELECOMMUNICATIONS PROBLEMS * 14. 7 © 2002 by Prentice Hall
THREATS TO INFORMATION SYSTEMS HARDWARE FAILURE, FIRE SOFTWARE FAILURE, ELECTRICAL PROBLEMS PERSONNEL ACTIONS, USER ERRORS ACCESS PENETRATION, PROGRAM CHANGES THEFT OF DATA, SERVICES, EQUIPMENT TELECOMMUNICATIONS PROBLEMS * 14. 7 © 2002 by Prentice Hall
 WHY SYSTEMS ARE VULNERABLE • SYSTEM COMPLEXITY • COMPUTERIZED PROCEDURES NOT ALWAYS READ OR AUDITED • EXTENSIVE EFFECT OF DISASTER • UNAUTHORIZED ACCESS POSSIBLE * 14. 8 © 2002 by Prentice Hall
WHY SYSTEMS ARE VULNERABLE • SYSTEM COMPLEXITY • COMPUTERIZED PROCEDURES NOT ALWAYS READ OR AUDITED • EXTENSIVE EFFECT OF DISASTER • UNAUTHORIZED ACCESS POSSIBLE * 14. 8 © 2002 by Prentice Hall
 VULNERABILITIES 14. 9 • RADIATION: Allows recorders, bugs to tap system • CROSSTALK: Can garble data • HARDWARE: Improper connections, failure of protection circuits • SOFTWARE: Failure of protection features, access control, bounds control • FILES: Subject to theft, copying, unauthorized access * © 2002 by Prentice Hall
VULNERABILITIES 14. 9 • RADIATION: Allows recorders, bugs to tap system • CROSSTALK: Can garble data • HARDWARE: Improper connections, failure of protection circuits • SOFTWARE: Failure of protection features, access control, bounds control • FILES: Subject to theft, copying, unauthorized access * © 2002 by Prentice Hall
 VULNERABILITIES • USER: Identification, authentication, subtle software modification • PROGRAMMER: Disables protective features; reveals protective measures • MAINTENANCE STAFF: Disables hardware devices; uses stand-alone utilities • OPERATOR: Doesn’t notify supervisor, reveals protective measures * 14. 10 © 2002 by Prentice Hall
VULNERABILITIES • USER: Identification, authentication, subtle software modification • PROGRAMMER: Disables protective features; reveals protective measures • MAINTENANCE STAFF: Disables hardware devices; uses stand-alone utilities • OPERATOR: Doesn’t notify supervisor, reveals protective measures * 14. 10 © 2002 by Prentice Hall
 HACKERS & COMPUTER VIRUSES • HACKER: Person gains access to computer for profit, criminal mischief, personal pleasure • COMPUTER VIRUS: Rogue program; difficult to detect; spreads rapidly; destroys data; disrupts processing & memory * 14. 11 © 2002 by Prentice Hall
HACKERS & COMPUTER VIRUSES • HACKER: Person gains access to computer for profit, criminal mischief, personal pleasure • COMPUTER VIRUS: Rogue program; difficult to detect; spreads rapidly; destroys data; disrupts processing & memory * 14. 11 © 2002 by Prentice Hall
 COMMON COMPUTER VIRUSES • CONCEPT, MELISSA: Word documents, e -mail. Deletes files • FORM: Makes clicking sound, corrupts data • EXPLORE. EXE: Attached to e-mail, tries to e-mail to others, destroys files • MONKEY: Windows won’t run • CHERNOBYL: Erases hard drive, ROM BIOS • JUNKIE: Infects files, boot sector, memory conflicts * 14. 12 © 2002 by Prentice Hall
COMMON COMPUTER VIRUSES • CONCEPT, MELISSA: Word documents, e -mail. Deletes files • FORM: Makes clicking sound, corrupts data • EXPLORE. EXE: Attached to e-mail, tries to e-mail to others, destroys files • MONKEY: Windows won’t run • CHERNOBYL: Erases hard drive, ROM BIOS • JUNKIE: Infects files, boot sector, memory conflicts * 14. 12 © 2002 by Prentice Hall
 ANTIVIRUS SOFTWARE • • • 14. 13 SOFTWARE TO DETECT ELIMINATE VIRUSES ADVANCED VERSIONS RUN IN MEMORY TO PROTECT PROCESSING, GUARD AGAINST VIRUSES ON DISKS, AND ON INCOMING NETWORK FILES * © 2002 by Prentice Hall
ANTIVIRUS SOFTWARE • • • 14. 13 SOFTWARE TO DETECT ELIMINATE VIRUSES ADVANCED VERSIONS RUN IN MEMORY TO PROTECT PROCESSING, GUARD AGAINST VIRUSES ON DISKS, AND ON INCOMING NETWORK FILES * © 2002 by Prentice Hall
 CONCERNS FOR BUILDERS & USERS DISASTER BREACH OF SECURITY ERRORS * 14. 14 © 2002 by Prentice Hall
CONCERNS FOR BUILDERS & USERS DISASTER BREACH OF SECURITY ERRORS * 14. 14 © 2002 by Prentice Hall
 DISASTER LOSS OF HARDWARE, SOFTWARE, DATA BY FIRE, POWER FAILURE, FLOOD OR OTHER CALAMITY • FAULT-TOLERANT COMPUTER SYSTEMS: Backup systems to prevent system failure (particularly Online Transaction Processing) * 14. 15 © 2002 by Prentice Hall
DISASTER LOSS OF HARDWARE, SOFTWARE, DATA BY FIRE, POWER FAILURE, FLOOD OR OTHER CALAMITY • FAULT-TOLERANT COMPUTER SYSTEMS: Backup systems to prevent system failure (particularly Online Transaction Processing) * 14. 15 © 2002 by Prentice Hall
 SECURITY POLICIES, PROCEDURES, TECHNICAL MEASURES TO PREVENT UNAUTHORIZED ACCESS, ALTERATION, THEFT, PHYSICAL DAMAGE TO INFORMATION SYSTEMS * 14. 16 © 2002 by Prentice Hall
SECURITY POLICIES, PROCEDURES, TECHNICAL MEASURES TO PREVENT UNAUTHORIZED ACCESS, ALTERATION, THEFT, PHYSICAL DAMAGE TO INFORMATION SYSTEMS * 14. 16 © 2002 by Prentice Hall
 WHERE ERRORS OCCUR • • • 14. 17 DATA PREPARATION TRANSMISSION CONVERSION FORM COMPLETION ON-LINE DATA ENTRY KEYPUNCHING; SCANNING; OTHER INPUTS * © 2002 by Prentice Hall
WHERE ERRORS OCCUR • • • 14. 17 DATA PREPARATION TRANSMISSION CONVERSION FORM COMPLETION ON-LINE DATA ENTRY KEYPUNCHING; SCANNING; OTHER INPUTS * © 2002 by Prentice Hall
 WHERE ERRORS OCCUR • • • 14. 18 VALIDATION PROCESSING / FILE MAINTENANCE OUTPUT TRANSMISSION DISTRIBUTION * © 2002 by Prentice Hall
WHERE ERRORS OCCUR • • • 14. 18 VALIDATION PROCESSING / FILE MAINTENANCE OUTPUT TRANSMISSION DISTRIBUTION * © 2002 by Prentice Hall
 SYSTEM QUALITY PROBLEMS • • • SOFTWARE & DATA BUGS: Program code defects or errors MAINTENANCE: Modifying a system in production use; can take up to 50% of analysts’ time • DATA QUALITY PROBLEMS: Finding, correcting errors; costly; tedious * 14. 19 © 2002 by Prentice Hall
SYSTEM QUALITY PROBLEMS • • • SOFTWARE & DATA BUGS: Program code defects or errors MAINTENANCE: Modifying a system in production use; can take up to 50% of analysts’ time • DATA QUALITY PROBLEMS: Finding, correcting errors; costly; tedious * 14. 19 © 2002 by Prentice Hall
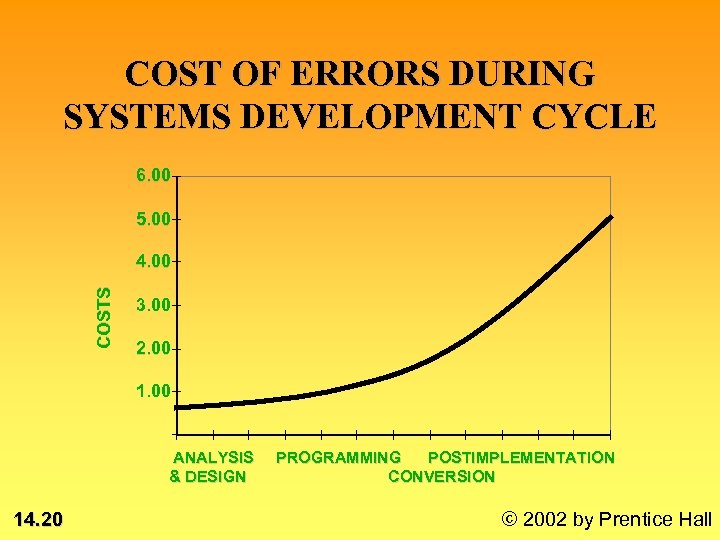 COST OF ERRORS DURING SYSTEMS DEVELOPMENT CYCLE 6. 00 5. 00 COSTS 4. 00 3. 00 2. 00 1. 00 ANALYSIS & DESIGN 14. 20 PROGRAMMING POSTIMPLEMENTATION CONVERSION © 2002 by Prentice Hall
COST OF ERRORS DURING SYSTEMS DEVELOPMENT CYCLE 6. 00 5. 00 COSTS 4. 00 3. 00 2. 00 1. 00 ANALYSIS & DESIGN 14. 20 PROGRAMMING POSTIMPLEMENTATION CONVERSION © 2002 by Prentice Hall
 CREATING A CONTROL ENVIRONMENT CONTROLS: Methods, policies, procedures to protect assets; accuracy & reliability of records; adherence to management standards • GENERAL CONTROLS • APPLICATION CONTROLS * 14. 21 © 2002 by Prentice Hall
CREATING A CONTROL ENVIRONMENT CONTROLS: Methods, policies, procedures to protect assets; accuracy & reliability of records; adherence to management standards • GENERAL CONTROLS • APPLICATION CONTROLS * 14. 21 © 2002 by Prentice Hall
 GENERAL CONTROLS • IMPLEMENTATION: Audit system development to assure proper control, management • SOFTWARE: Ensure security, reliability of software • PHYSICAL HARDWARE: Ensure physical security, performance of computer hardware * 14. 22 © 2002 by Prentice Hall
GENERAL CONTROLS • IMPLEMENTATION: Audit system development to assure proper control, management • SOFTWARE: Ensure security, reliability of software • PHYSICAL HARDWARE: Ensure physical security, performance of computer hardware * 14. 22 © 2002 by Prentice Hall
 GENERAL CONTROLS • COMPUTER OPERATIONS: Ensure procedures consistently, correctly applied to data storage, processing • DATA SECURITY: Ensure data disks, tapes protected from wrongful access, change, destruction • ADMINISTRATIVE: Ensure controls properly executed, enforced – SEGREGATION OF FUNCTIONS: Divide responsibility from tasks * 14. 23 © 2002 by Prentice Hall
GENERAL CONTROLS • COMPUTER OPERATIONS: Ensure procedures consistently, correctly applied to data storage, processing • DATA SECURITY: Ensure data disks, tapes protected from wrongful access, change, destruction • ADMINISTRATIVE: Ensure controls properly executed, enforced – SEGREGATION OF FUNCTIONS: Divide responsibility from tasks * 14. 23 © 2002 by Prentice Hall
 APPLICATION CONTROLS • INPUT • PROCESSING • OUTPUT * 14. 24 © 2002 by Prentice Hall
APPLICATION CONTROLS • INPUT • PROCESSING • OUTPUT * 14. 24 © 2002 by Prentice Hall
 INPUT CONTROLS • INPUT AUTHORIZATION: Record, monitor source documents • DATA CONVERSION: Transcribe data properly from one form to another • BATCH CONTROL TOTALS: Count transactions prior to and after processing • EDIT CHECKS: Verify input data, correct errors * 14. 25 © 2002 by Prentice Hall
INPUT CONTROLS • INPUT AUTHORIZATION: Record, monitor source documents • DATA CONVERSION: Transcribe data properly from one form to another • BATCH CONTROL TOTALS: Count transactions prior to and after processing • EDIT CHECKS: Verify input data, correct errors * 14. 25 © 2002 by Prentice Hall
 PROCESSING CONTROLS ESTABLISH THAT DATA IS COMPLETE, ACCURATE DURING PROCESSING • RUN CONTROL TOTALS: Generate control totals before & after processing • COMPUTER MATCHING: Match input data to master files * 14. 26 © 2002 by Prentice Hall
PROCESSING CONTROLS ESTABLISH THAT DATA IS COMPLETE, ACCURATE DURING PROCESSING • RUN CONTROL TOTALS: Generate control totals before & after processing • COMPUTER MATCHING: Match input data to master files * 14. 26 © 2002 by Prentice Hall
 OUTPUT CONTROLS ESTABLISH THAT RESULTS ARE ACCURATE, COMPLETE, PROPERLY DISTRIBUTED • BALANCE INPUT, PROCESSING, OUTPUT TOTALS • REVIEW PROCESSING LOGS • ENSURE ONLY AUTHORIZED RECIPIENTS GET RESULTS * 14. 27 © 2002 by Prentice Hall
OUTPUT CONTROLS ESTABLISH THAT RESULTS ARE ACCURATE, COMPLETE, PROPERLY DISTRIBUTED • BALANCE INPUT, PROCESSING, OUTPUT TOTALS • REVIEW PROCESSING LOGS • ENSURE ONLY AUTHORIZED RECIPIENTS GET RESULTS * 14. 27 © 2002 by Prentice Hall
 SECURITY AND THE INTERNET • ENCRYPTION: Coding & scrambling messages to deny unauthorized access • AUTHENTICATION: Ability to identify another party – MESSAGE INTEGRITY – DIGITAL SIGNATURE – DIGITAL CERTIFICATE * 14. 28 © 2002 by Prentice Hall
SECURITY AND THE INTERNET • ENCRYPTION: Coding & scrambling messages to deny unauthorized access • AUTHENTICATION: Ability to identify another party – MESSAGE INTEGRITY – DIGITAL SIGNATURE – DIGITAL CERTIFICATE * 14. 28 © 2002 by Prentice Hall
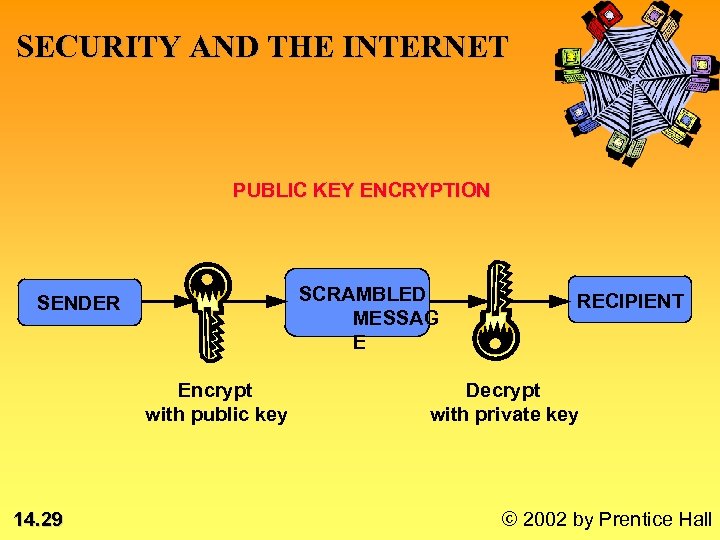 SECURITY AND THE INTERNET PUBLIC KEY ENCRYPTION SCRAMBLED MESSAG E SENDER Encrypt with public key 14. 29 RECIPIENT Decrypt with private key © 2002 by Prentice Hall
SECURITY AND THE INTERNET PUBLIC KEY ENCRYPTION SCRAMBLED MESSAG E SENDER Encrypt with public key 14. 29 RECIPIENT Decrypt with private key © 2002 by Prentice Hall
 SECURITY AND THE INTERNET • DIGITAL WALLET: Software stores credit card, electronic cash, owner ID, address for e-commerce transactions • SECURE ELECTRONIC TRANSACTION: Standard for securing credit card transactions on Internet * 14. 30 © 2002 by Prentice Hall
SECURITY AND THE INTERNET • DIGITAL WALLET: Software stores credit card, electronic cash, owner ID, address for e-commerce transactions • SECURE ELECTRONIC TRANSACTION: Standard for securing credit card transactions on Internet * 14. 30 © 2002 by Prentice Hall
 SECURITY AND THE INTERNET ELECTRONIC PAYMENT SYSTEMS • CREDIT CARD-SET: Protocol for payment security • ELECTRONIC CASH: Digital currency • ELECTRONIC CHECK: Encrypted digital signature • SMART CARD: Chip stores e-cash • ELECTRONIC BILL PAYMENT: Electronic funds transfer * 14. 31 © 2002 by Prentice Hall
SECURITY AND THE INTERNET ELECTRONIC PAYMENT SYSTEMS • CREDIT CARD-SET: Protocol for payment security • ELECTRONIC CASH: Digital currency • ELECTRONIC CHECK: Encrypted digital signature • SMART CARD: Chip stores e-cash • ELECTRONIC BILL PAYMENT: Electronic funds transfer * 14. 31 © 2002 by Prentice Hall
 DEVELOPING A CONTROL STRUCTURE • COSTS: Can be expensive to build; complicated to use • BENEFITS: Reduces expensive errors, loss of time, resources, good will RISK ASSESSMENT: Determine frequency of occurrence of problem, cost, damage if it were to occur * 14. 32 © 2002 by Prentice Hall
DEVELOPING A CONTROL STRUCTURE • COSTS: Can be expensive to build; complicated to use • BENEFITS: Reduces expensive errors, loss of time, resources, good will RISK ASSESSMENT: Determine frequency of occurrence of problem, cost, damage if it were to occur * 14. 32 © 2002 by Prentice Hall
 SYSTEM BUILDING APPROACHES • STRUCTURED METHODOLOGIES • COMPUTER AIDED SOFTWARE ENGINEERING (CASE) • SOFTWARE REENGINEERING * 14. 33 © 2002 by Prentice Hall
SYSTEM BUILDING APPROACHES • STRUCTURED METHODOLOGIES • COMPUTER AIDED SOFTWARE ENGINEERING (CASE) • SOFTWARE REENGINEERING * 14. 33 © 2002 by Prentice Hall
 STRUCTURED METHODOLOGIES TOP DOWN, STEP BY STEP, EACH STEP BUILDS ON PREVIOUS • STRUCTURED ANALYSIS • STRUCTURED DESIGN • STRUCTURED PROGRAMMING • FLOWCHARTS * 14. 34 © 2002 by Prentice Hall
STRUCTURED METHODOLOGIES TOP DOWN, STEP BY STEP, EACH STEP BUILDS ON PREVIOUS • STRUCTURED ANALYSIS • STRUCTURED DESIGN • STRUCTURED PROGRAMMING • FLOWCHARTS * 14. 34 © 2002 by Prentice Hall
 STRUCTURED ANALYSIS • DEFINES SYSTEM INPUTS, PROCESSES, OUTPUTS • PARTITIONS SYSTEM INTO SUBSYSTEMS OR MODULES • LOGICAL, GRAPHICAL MODEL OF INFORMATION FLOW • DATA FLOW DIAGRAM: Graphical display of component processes, flow of data * 14. 35 © 2002 by Prentice Hall
STRUCTURED ANALYSIS • DEFINES SYSTEM INPUTS, PROCESSES, OUTPUTS • PARTITIONS SYSTEM INTO SUBSYSTEMS OR MODULES • LOGICAL, GRAPHICAL MODEL OF INFORMATION FLOW • DATA FLOW DIAGRAM: Graphical display of component processes, flow of data * 14. 35 © 2002 by Prentice Hall
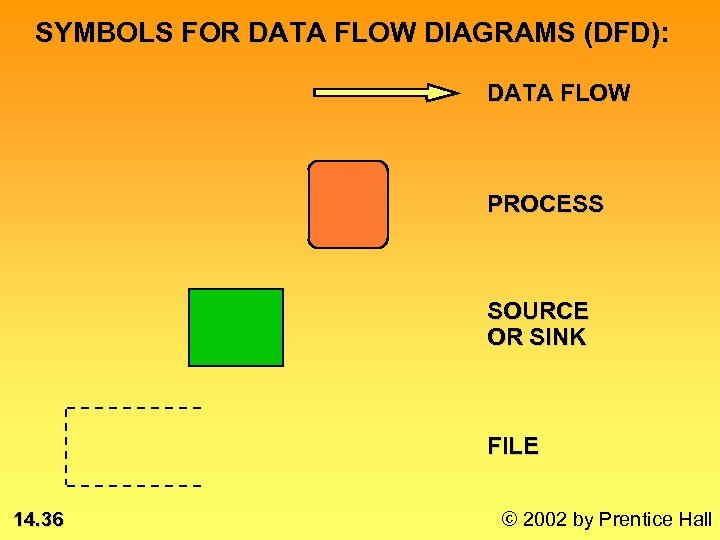 SYMBOLS FOR DATA FLOW DIAGRAMS (DFD): DATA FLOW PROCESS SOURCE OR SINK FILE 14. 36 © 2002 by Prentice Hall
SYMBOLS FOR DATA FLOW DIAGRAMS (DFD): DATA FLOW PROCESS SOURCE OR SINK FILE 14. 36 © 2002 by Prentice Hall
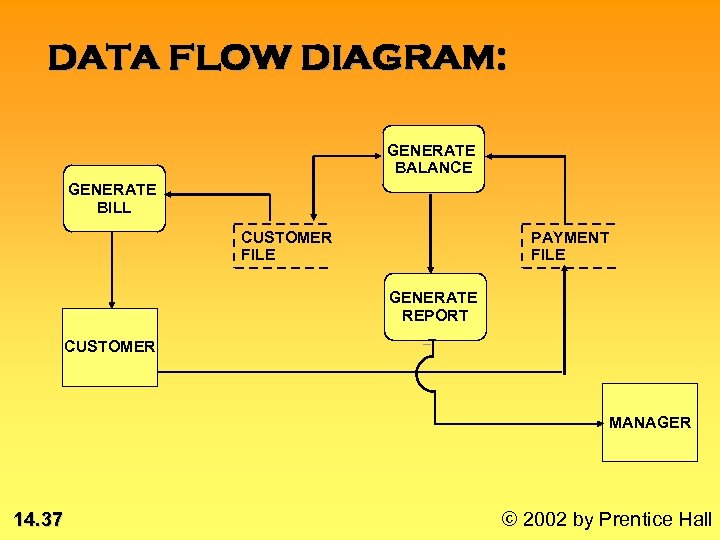 DATA FLOW DIAGRAM: GENERATE BALANCE GENERATE BILL CUSTOMER FILE PAYMENT FILE GENERATE REPORT CUSTOMER MANAGER 14. 37 © 2002 by Prentice Hall
DATA FLOW DIAGRAM: GENERATE BALANCE GENERATE BILL CUSTOMER FILE PAYMENT FILE GENERATE REPORT CUSTOMER MANAGER 14. 37 © 2002 by Prentice Hall
 STRUCTURED ANALYSIS • DATA DICTIONARY: Controlled definitions of descriptions of all data, such as variable names & types of data • PROCESS SPECIFICATIONS: Describes logic of processes at module level * 14. 38 © 2002 by Prentice Hall
STRUCTURED ANALYSIS • DATA DICTIONARY: Controlled definitions of descriptions of all data, such as variable names & types of data • PROCESS SPECIFICATIONS: Describes logic of processes at module level * 14. 38 © 2002 by Prentice Hall
 STRUCTURED DESIGN • • • 14. 39 DESIGN RULES / TECHNIQUES TO DESIGN SYSTEM, TOP DOWN IN HIERARCHICAL FASHION STRUCTURE CHART STRUCTURED PROGRAMMING MODULE SEQUENCE CONSTRUCT SELECTION CONSTRUCT * © 2002 by Prentice Hall
STRUCTURED DESIGN • • • 14. 39 DESIGN RULES / TECHNIQUES TO DESIGN SYSTEM, TOP DOWN IN HIERARCHICAL FASHION STRUCTURE CHART STRUCTURED PROGRAMMING MODULE SEQUENCE CONSTRUCT SELECTION CONSTRUCT * © 2002 by Prentice Hall
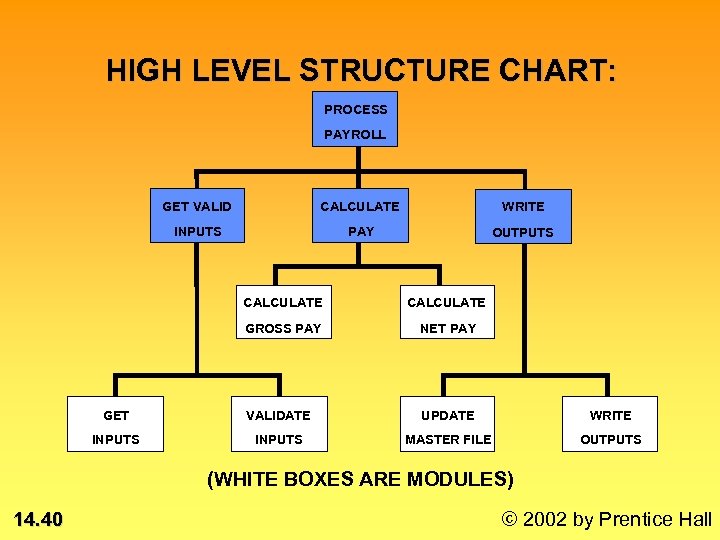 HIGH LEVEL STRUCTURE CHART: PROCESS PAYROLL GET VALID CALCULATE WRITE INPUTS PAY OUTPUTS CALCULATE GROSS PAY NET PAY GET VALIDATE UPDATE WRITE INPUTS MASTER FILE OUTPUTS (WHITE BOXES ARE MODULES) 14. 40 © 2002 by Prentice Hall
HIGH LEVEL STRUCTURE CHART: PROCESS PAYROLL GET VALID CALCULATE WRITE INPUTS PAY OUTPUTS CALCULATE GROSS PAY NET PAY GET VALIDATE UPDATE WRITE INPUTS MASTER FILE OUTPUTS (WHITE BOXES ARE MODULES) 14. 40 © 2002 by Prentice Hall
 STRUCTURED PROGRAMMING: • DISCIPLINE TO ORGANIZE, CODE PROGRAMS • SIMPLIFIES CONTROL PATHS • EASY TO UNDERSTAND, MODIFY • MODULE HAS ONE INPUT, ONE OUTPUT * 14. 41 © 2002 by Prentice Hall
STRUCTURED PROGRAMMING: • DISCIPLINE TO ORGANIZE, CODE PROGRAMS • SIMPLIFIES CONTROL PATHS • EASY TO UNDERSTAND, MODIFY • MODULE HAS ONE INPUT, ONE OUTPUT * 14. 41 © 2002 by Prentice Hall
 STRUCTURED PROGRAMMING: • MODULE: Logical unit of program. performs specific task(s) • SEQUENCE CONSTRUCT: Sequential steps or actions in program logic; streamlines flow • SELECTION CONSTRUCT: IF condition R is True THEN action C ELSE action D • ITERATION CONSTRUCT: WHILE Condition is True DO action E * 14. 42 © 2002 by Prentice Hall
STRUCTURED PROGRAMMING: • MODULE: Logical unit of program. performs specific task(s) • SEQUENCE CONSTRUCT: Sequential steps or actions in program logic; streamlines flow • SELECTION CONSTRUCT: IF condition R is True THEN action C ELSE action D • ITERATION CONSTRUCT: WHILE Condition is True DO action E * 14. 42 © 2002 by Prentice Hall
 PROGRAM FLOWCHART SYMBOLS: 14. 43 © 2002 by Prentice Hall
PROGRAM FLOWCHART SYMBOLS: 14. 43 © 2002 by Prentice Hall
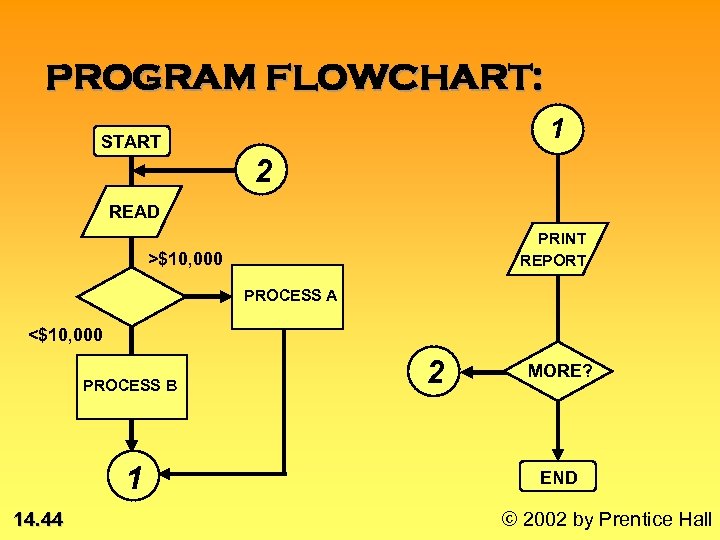 PROGRAM FLOWCHART: 1 START 2 READ PRINT REPORT >$10, 000 PROCESS A <$10, 000 PROCESS B 1 14. 44 2 MORE? END © 2002 by Prentice Hall
PROGRAM FLOWCHART: 1 START 2 READ PRINT REPORT >$10, 000 PROCESS A <$10, 000 PROCESS B 1 14. 44 2 MORE? END © 2002 by Prentice Hall
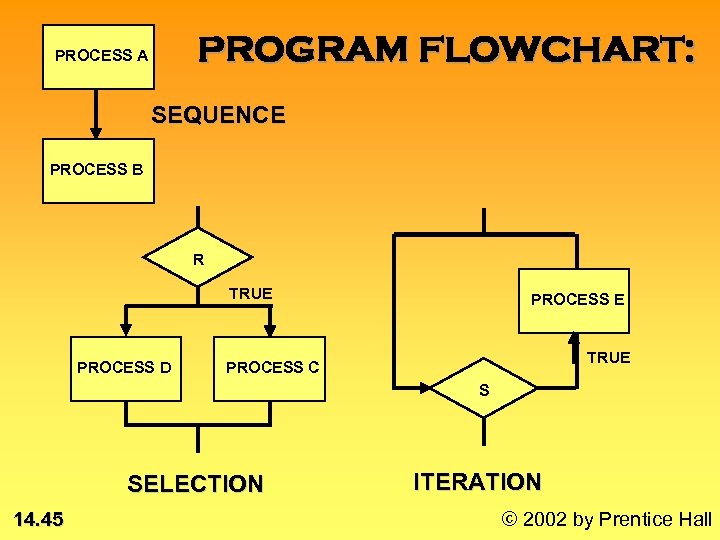 PROGRAM FLOWCHART: PROCESS A SEQUENCE PROCESS B R TRUE PROCESS D PROCESS E TRUE PROCESS C S SELECTION 14. 45 ITERATION © 2002 by Prentice Hall
PROGRAM FLOWCHART: PROCESS A SEQUENCE PROCESS B R TRUE PROCESS D PROCESS E TRUE PROCESS C S SELECTION 14. 45 ITERATION © 2002 by Prentice Hall
 SYSTEM FLOWCHART SYMBOLS: 14. 46 © 2002 by Prentice Hall
SYSTEM FLOWCHART SYMBOLS: 14. 46 © 2002 by Prentice Hall
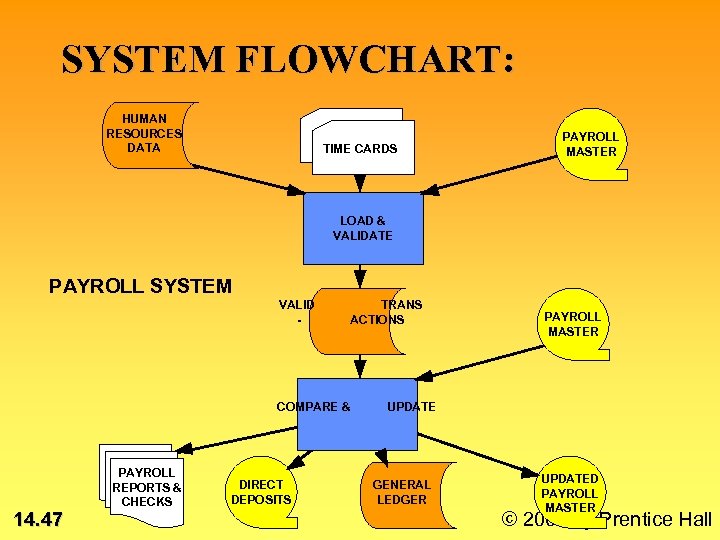 SYSTEM FLOWCHART: HUMAN RESOURCES DATA TIME CARDS PAYROLL MASTER LOAD & VALIDATE PAYROLL SYSTEM VALID - COMPARE & 14. 47 PAYROLL REPORTS & CHECKS DIRECT DEPOSITS TRANS ACTIONS PAYROLL MASTER UPDATE GENERAL LEDGER UPDATED PAYROLL MASTER © 2002 by Prentice Hall
SYSTEM FLOWCHART: HUMAN RESOURCES DATA TIME CARDS PAYROLL MASTER LOAD & VALIDATE PAYROLL SYSTEM VALID - COMPARE & 14. 47 PAYROLL REPORTS & CHECKS DIRECT DEPOSITS TRANS ACTIONS PAYROLL MASTER UPDATE GENERAL LEDGER UPDATED PAYROLL MASTER © 2002 by Prentice Hall
 COMPUTER AIDED SOFTWARE ENGINEERING (CASE) • AUTOMATION OF SOFTWARE METHODOLOGIES • PRODUCES CHARTS; DIAGRAMS; SCREEN & REPORT GENERATORS; DATA DICTIONARIES; PROGRESS REPORTS; ANALYSIS; CHECKING TOOLS; CODE; DOCUMENTATION * 14. 48 CASE © 2002 by Prentice Hall
COMPUTER AIDED SOFTWARE ENGINEERING (CASE) • AUTOMATION OF SOFTWARE METHODOLOGIES • PRODUCES CHARTS; DIAGRAMS; SCREEN & REPORT GENERATORS; DATA DICTIONARIES; PROGRESS REPORTS; ANALYSIS; CHECKING TOOLS; CODE; DOCUMENTATION * 14. 48 CASE © 2002 by Prentice Hall
 COMPUTER AIDED SOFTWARE ENGINEERING (CASE) INCREASES PRODUCTIVITY & QUALITY: • ENFORCES DEVELOPMENT DISCIPLINE • IMPROVES COMMUNICATION • DESIGN REPOSITORY FOR OBJECTS • AUTOMATES TEDIOUS TASKS • AUTOMATES TESTING & CONTROL • REQUIRES ORGANIZATIONAL DISCIPLINE * 14. 49 CASE © 2002 by Prentice Hall
COMPUTER AIDED SOFTWARE ENGINEERING (CASE) INCREASES PRODUCTIVITY & QUALITY: • ENFORCES DEVELOPMENT DISCIPLINE • IMPROVES COMMUNICATION • DESIGN REPOSITORY FOR OBJECTS • AUTOMATES TEDIOUS TASKS • AUTOMATES TESTING & CONTROL • REQUIRES ORGANIZATIONAL DISCIPLINE * 14. 49 CASE © 2002 by Prentice Hall
 MIS AUDIT IDENTIFIES CONTROLS OF INFORMATION SYSTEMS, ASSESSES THEIR EFFECTIVENESS • SOFTWARE METRICS: Objective measurements to assess system • TESTING: Early, regular controlled efforts to detect, reduce errors – WALKTHROUGH – DEBUGGING • DATA QUALITY AUDIT: Survey samples of files for accuracy, completeness * 14. 50 © 2002 by Prentice Hall
MIS AUDIT IDENTIFIES CONTROLS OF INFORMATION SYSTEMS, ASSESSES THEIR EFFECTIVENESS • SOFTWARE METRICS: Objective measurements to assess system • TESTING: Early, regular controlled efforts to detect, reduce errors – WALKTHROUGH – DEBUGGING • DATA QUALITY AUDIT: Survey samples of files for accuracy, completeness * 14. 50 © 2002 by Prentice Hall
 c h a p t e r 14 INFORMATION SYSTEMS SECURITY & CONTROL 14. 51 © 2002 by Prentice Hall
c h a p t e r 14 INFORMATION SYSTEMS SECURITY & CONTROL 14. 51 © 2002 by Prentice Hall


