c52e556686089061a2f3c25725b2b228.ppt
- Количество слайдов: 45

Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems Vivek Pathak and Liviu Iftode Department of Computer Science Rutgers University 5/9/6

Outline n Introduction n Public key authentication n n Motivation for Peer-to-peer authentication n 5/9/6 Other solutions Byzantine fault tolerant authentication n n Existing models Security model Outline of correctness and performance Future work Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 2
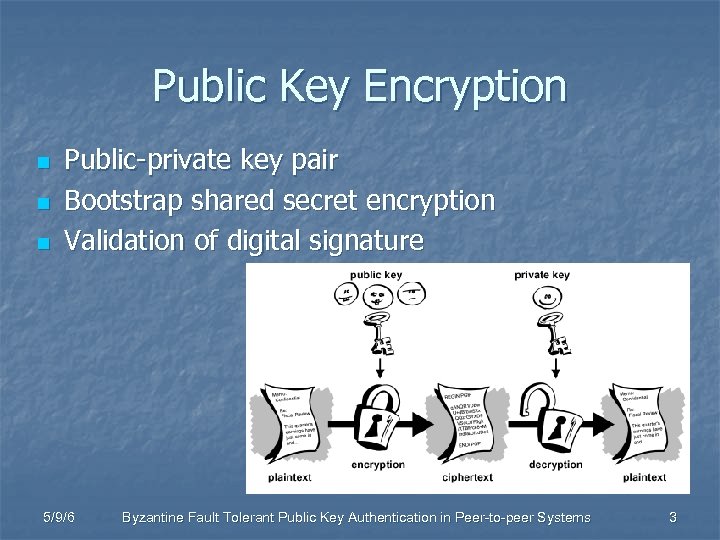
Public Key Encryption n Public-private key pair Bootstrap shared secret encryption Validation of digital signature 5/9/6 Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 3
Authentication of Public Keys n Mapping identities to public keys n Trusted third parties (TTP) n n Web of trust n 5/9/6 Certificate authority (CA) PGP Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 4

Authentication through CA n Provide public key certificate n 5/9/6 Use secure channel for bootstrapping Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 5
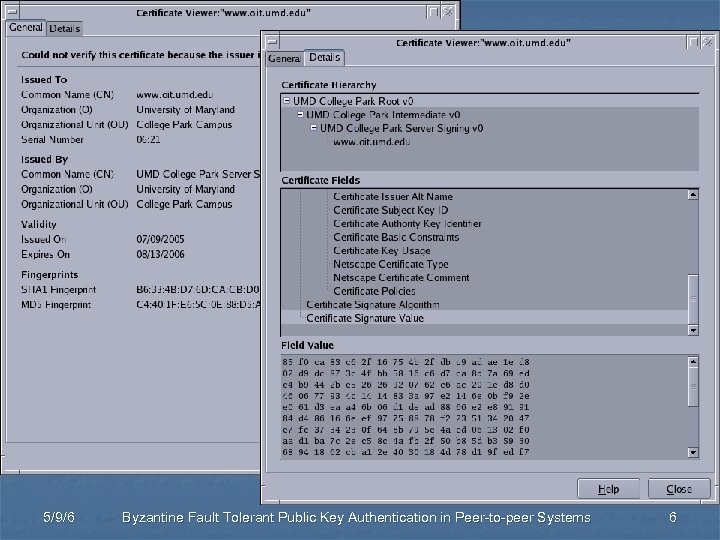
Authentication through CA 5/9/6 Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 6

Authentication through CA n Represent centralized aggregation of trust n n n Long lived CA keys Single point of failure Public key revocation n 5/9/6 Scalability with number of certified keys Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 7
Web of Trust n Informal human authentication n n 5/9/6 PGP key rings Levels of trust Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 8

Web of Trust n Peers take on the role of CA n Decentralized trust n n n No single point of failure Key authentication depends on human connections How to apply to autonomous systems n 5/9/6 Sophisticated users Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 9

Outline n Introduction n Public key authentication n n Motivation for Peer-to-peer authentication n 5/9/6 Other solutions Byzantine fault tolerant authentication n n Existing models Security model Outline of correctness and performance Future work Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 10

Characteristics of Peer-to-peer Systems n Heterogeneous peers n n n Lack of trusted third parties Hierarchical Certificate Authorities Large scale peer-to-peer systems n n n 5/9/6 Need decentralized solution Administrative burden on CA Scalability of key revocation Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 11

Characteristics of Peer-to-peer Systems n Autonomous operation n n Short lived public keys n n n Unsophisticated users Sensors and devices Web of trust depends on constant human feedback Peers may be attacked and recover Public key certificates require secure channel Malicious peers 5/9/6 Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 12
Other Solutions n Threshold encryption systems n Share the secret among a set of parties n n n Defend against a few compromised parties Secure initialization phase Crypto based network IDs n Choose network ID as function of public key n 5/9/6 Depends on the routing infrastructure Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 13

Outline n Introduction n Public key authentication n n Motivation for Peer-to-peer authentication n 5/9/6 Other solutions Byzantine fault tolerant authentication n n Existing models Security model Outline of correctness and performance Future work Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 14
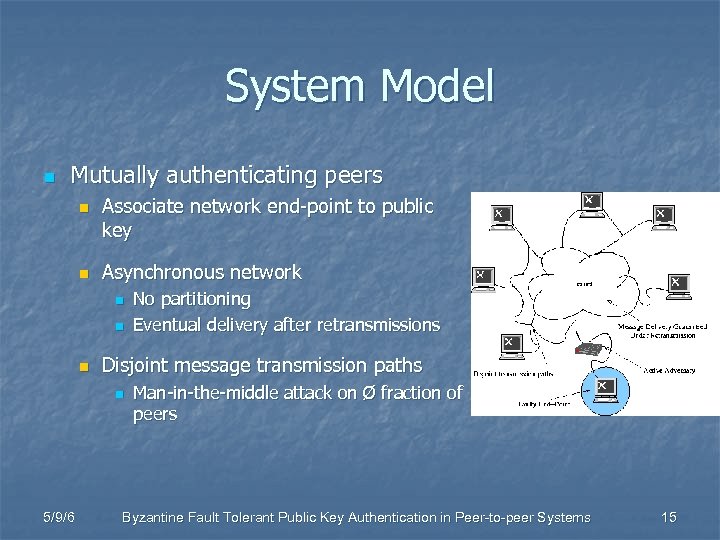
System Model n Mutually authenticating peers n n Associate network end-point to public key Asynchronous network n n n Disjoint message transmission paths n 5/9/6 No partitioning Eventual delivery after retransmissions Man-in-the-middle attack on Ø fraction of peers Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 15

Attack Model n Malicious peers n n Honest majority At most t of the n peers are faulty or malicious peers where t = 1 -6Ø/3 n n Passive adversaries n Active adversaries n Relax network-is-the-adversary model n n 5/9/6 Unlimited spoofing Limited power to prevent message delivery Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 16
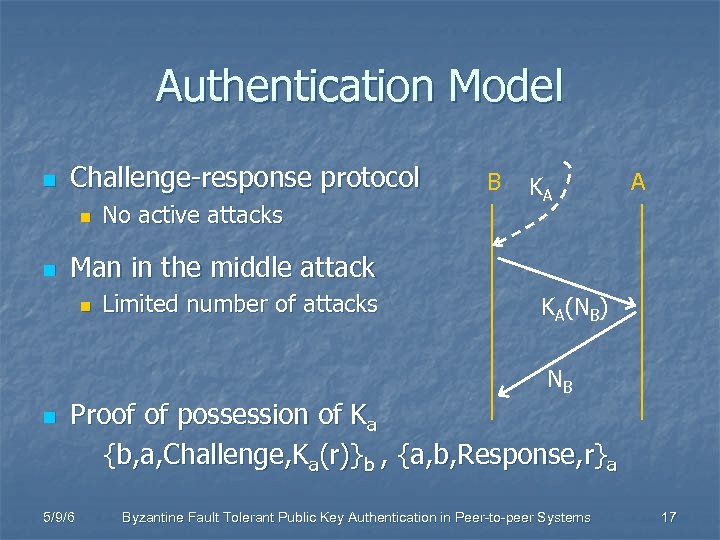
Authentication Model n Challenge-response protocol n n No active attacks B KA A Man in the middle attack n Limited number of attacks KA(NB) NB n Proof of possession of Ka {b, a, Challenge, Ka(r)}b , {a, b, Response, r}a 5/9/6 Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 17
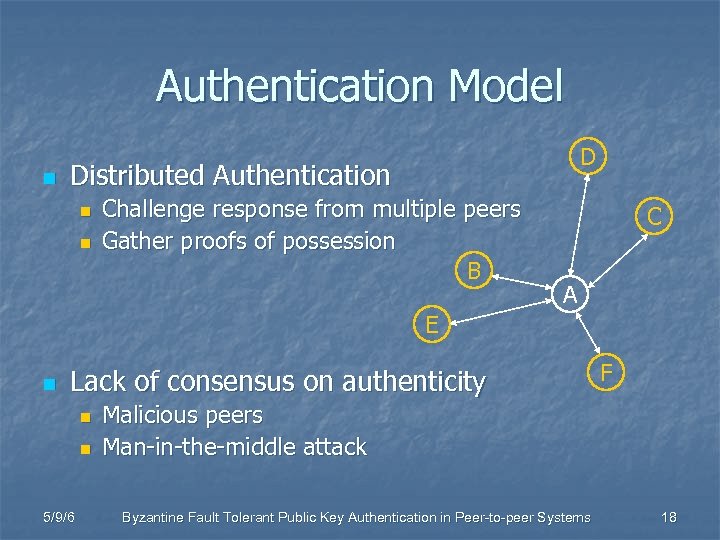
Authentication Model n D Distributed Authentication n n Challenge response from multiple peers Gather proofs of possession B C A E n Lack of consensus on authenticity n n 5/9/6 F Malicious peers Man-in-the-middle attack Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 18
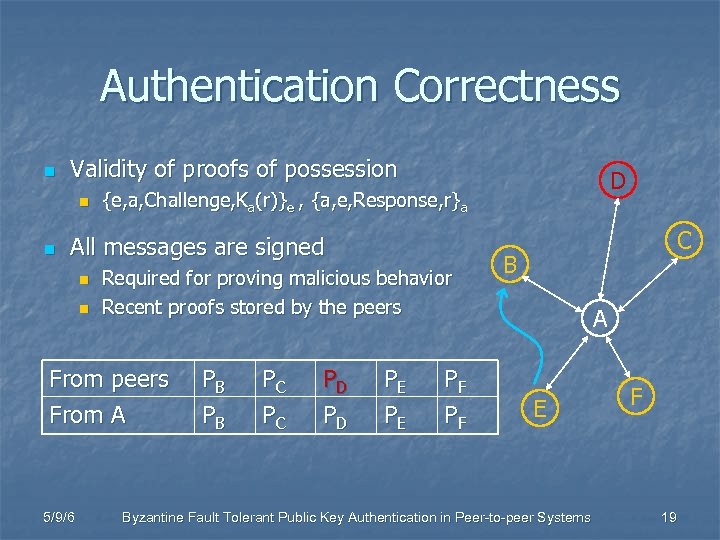
Authentication Correctness n Validity of proofs of possession n n {e, a, Challenge, Ka(r)}e , {a, e, Response, r}a All messages are signed n n Required for proving malicious behavior Recent proofs stored by the peers From A 5/9/6 D PB PB PC PC PD PD PE PE PF PF C B A E Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems F 19

Byzantine Agreement Overview n Publicize lack of consensus n n 1 1 0 1 1 From C 1 1 1 Each peer tries to authenticate A n n n Authenticating peer sends proofs of possession to peers From B Sends its proof-of-possession vector to From every peer Byzantine agreement on authenticity of KA From Majority decision at every peer n n 5/9/6 Identify malicious peers Complete authentication D 1 1 1 E 1 1 0 1 1 From F 1 1 0 1 1 Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 20
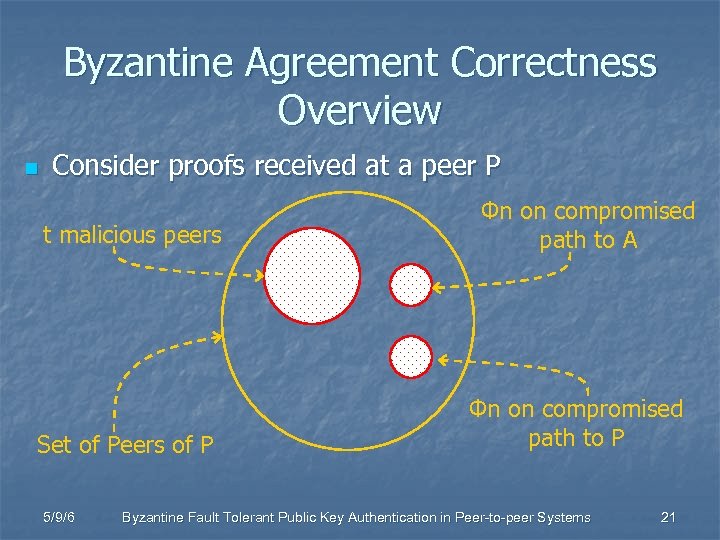
Byzantine Agreement Correctness Overview n Consider proofs received at a peer P t malicious peers Set of Peers of P 5/9/6 Φn on compromised path to A Φn on compromised path to P Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 21

Byzantine Agreement Correctness Overview n t + 2Øn may not arrive n n t + 2Øn may be faulty n n n P receives at least n-t-2Øn proofs P receives at least n-2 t-4Øn correct agreeing proofs P decides correctly by majority if n-2 t-4Øn > t + 2Øn Agreement is correct if t < 1 -6Ø/3 n 5/9/6 Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 22
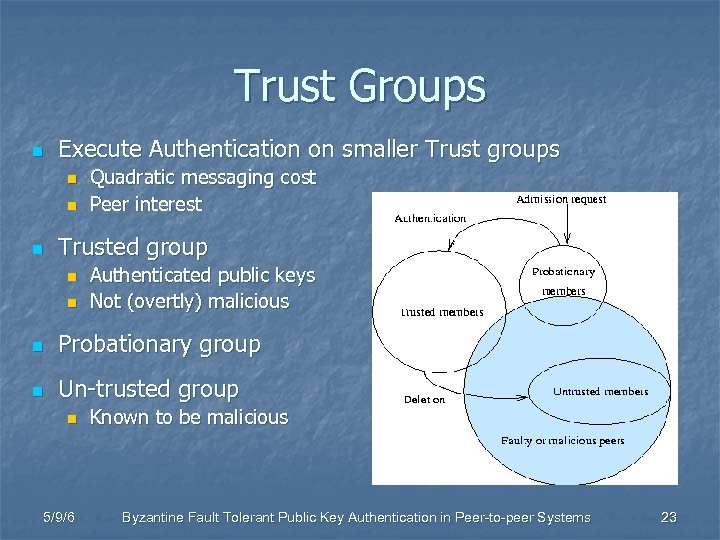
Trust Groups n Execute Authentication on smaller Trust groups n n n Quadratic messaging cost Peer interest Trusted group n n Authenticated public keys Not (overtly) malicious n Probationary group n Un-trusted group n 5/9/6 Known to be malicious Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 23
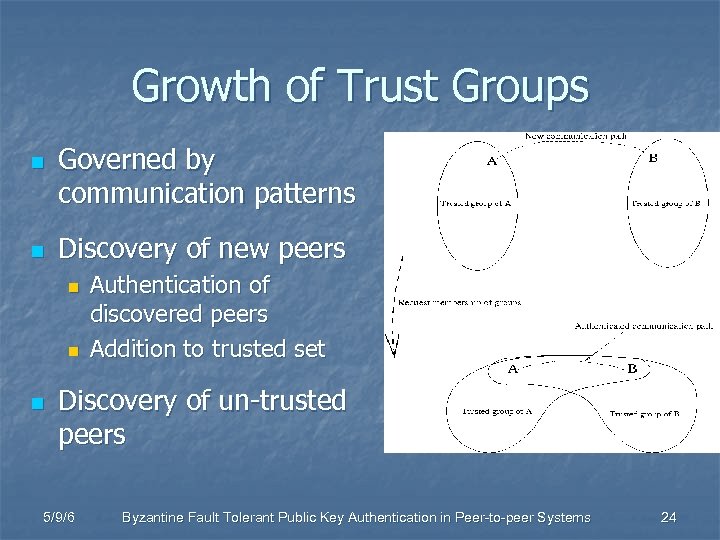
Growth of Trust Groups n n Governed by communication patterns Discovery of new peers n n n Authentication of discovered peers Addition to trusted set Discovery of un-trusted peers 5/9/6 Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 24

Evolution of Trust Groups n Covertly malicious peers n n n May wait until honest majority is violated Lead to incorrect authentication Periodic pruning of trusted group n n Unresponsive peers Remove older trusted peers from trust group n n Reduce messaging cost Randomize trusted group membership Group migration event Probability of violating honest majority 5/9/6 Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 25

Bootstrapping Trust Group n Authentication needs an honest trust group n n Initialize a Bootstrapping trust group Needed for cold start Authenticate each bootstrapping peer Size of bootstrapping trust group n 5/9/6 Recover from trusting a malicious peer n > 3/1 -6Ø Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 26

Public Key Infection n Optimistic trust n n n Lazy authentication Reduced messaging cost Cache of undelivered messages n n n 5/9/6 Use peers for epidemic propagation of messages Anti-entropy sessions eventually deliver messages Infect peers with new undelivered messages Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 27

Public Key Infection n Use logical and vector timestamps n n Determine messages to exchange for anti-entropy Detect message delivery Double exponential drop in number of uninfected peers with time Number of cached messages is in O(nlogn) 5/9/6 Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 28

Simulation n n Implemented Byzantine Fault Tolerant Authentication as a C++ library Simulation program n n Make library calls and keeps counters Study effects of n n 5/9/6 Group size Malicious peers Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 29
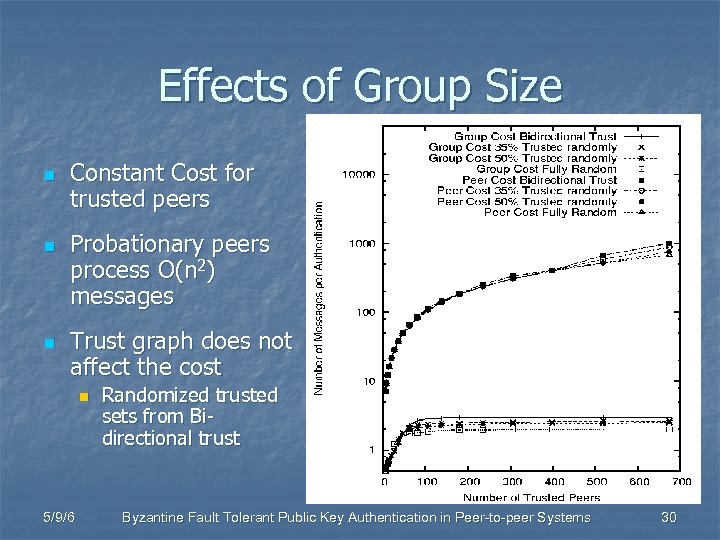
Effects of Group Size n n n Constant Cost for trusted peers Probationary peers process O(n 2) messages Trust graph does not affect the cost n 5/9/6 Randomized trusted sets from Bidirectional trust Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 30
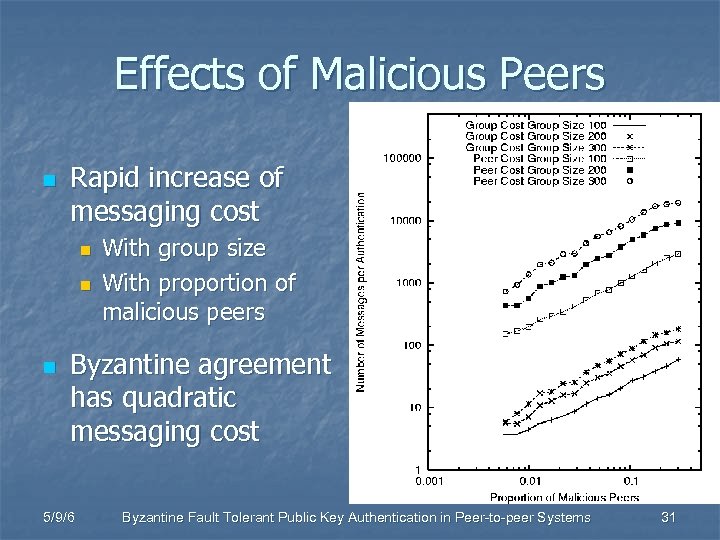
Effects of Malicious Peers n Rapid increase of messaging cost n n n With group size With proportion of malicious peers Byzantine agreement has quadratic messaging cost 5/9/6 Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 31

Conclusion n Autonomous authentication without trusted third party n n n Incremental approach to security Suited for low value peer-to-peer systems Tolerate malicious peers n Suited for applications spanning multiple administrative domains n Scalable to large peer-to-peer systems n Eliminate total trust and single point of failure n Made feasible by using stronger network assumptions n 5/9/6 Network adversary is not all powerful Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 32

Outline n Introduction n Public key authentication n n Motivation for Peer-to-peer authentication n 5/9/6 Other solutions Byzantine fault tolerant authentication n n Existing models Security model Outline of correctness and performance Future work Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 33
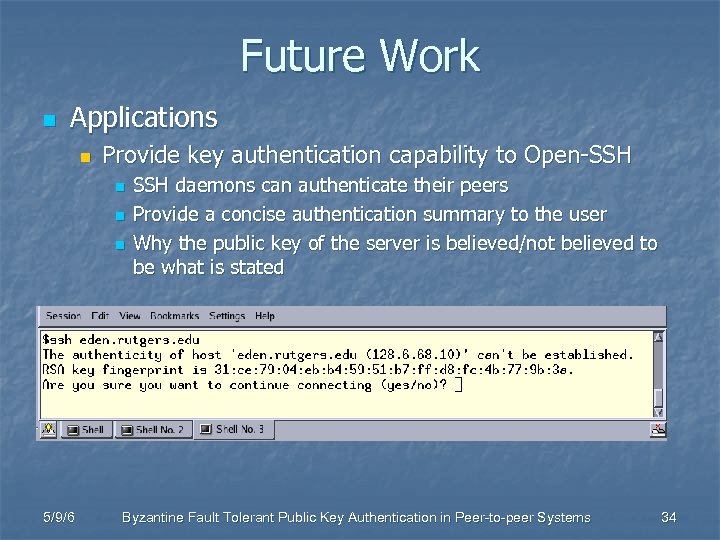
Future Work n Applications n Provide key authentication capability to Open-SSH n n n 5/9/6 SSH daemons can authenticate their peers Provide a concise authentication summary to the user Why the public key of the server is believed/not believed to be what is stated Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 34

Future Work n Applications contd. … n n Spam identification through public key authentication Existing solutions n Filtering: Machine learning to classify contents n n n Postage: Sender pays to send email n n End-to-end argument Safe sender lists n 5/9/6 Results in misspellings in spam messages False positive rate independent of sender importance Need to authenticate sender Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 35

Future Work n Sender Authentication n n Piggyback authentication protocol on email messages Messages are signed n n SMTP allows extension fields n n n Authenticate senders with existing infrastructure Incremental deployment Use digital signature to verify messages from authenticated senders n n 5/9/6 They can be delivered to peers indirectly Allow messages from safe senders pass through Eliminate false positives from spam filters Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 36

Future Work n Enhancements to the mechanism n Address denial of service n n Keep track of work done on behalf of any peer Peers are authenticated n n 5/9/6 Agreement on work done on behalf of peers Use authenticated load information to prevent denial of service Need economic model Avoid expensive public key cryptography Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 37

Future Work n Enhancements to the model n Authenticate public keys in Ad-hoc network n n Apply to vehicular computing n n n Does the public key belong to the car on GWB? Working on Geographical Authentication Study hybrid trust models n 5/9/6 Lack the network IDs assumed Hierarchical, peer-to-peer, web of trust Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 38

Q&A 5/9/6 Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 39
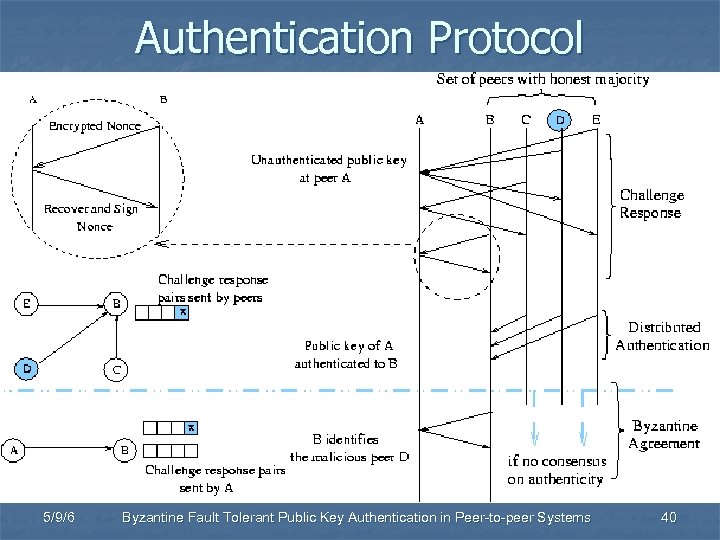
Authentication Protocol 5/9/6 Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 40

Objective n Security is an increasing concern n n n 5/9/6 Privacy Authenticity Fault tolerance Secure communication across the internet Distributed computation with semi-trusted principals : Smart messages Cost effective security Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 41

Privacy n Encryption n Our approach: nearly complete privacy n n n Computational cost Energy requirements Weakened keys, shortened key lifetime Tradeoff key lifetime for computational cost at constant security Cost effective encryption on commodity hardware 5/9/6 Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 42

Trust n Trusted third party model n n n Used in most security implementations Single-point of security failure Our model : distributed trust n n n 5/9/6 Authentication of public key is done by a vote of peers Addition of new participants Assumption: majority can not be corrupted Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 43

Performance n Lazy authentication protocol for updating the public keys to peers n n n Uses distributed trust to authenticate the new keys Allows admission of new peers Dynamical encryption in Linux kernel n n 5/9/6 Interrupt free processing Choose key lifetime based on system limitations Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 44

Status and Plan n Implemented encryption server on Linux n n Investigating security of distributed trust with dynamic membership n n 5/9/6 Preliminary point to point performance evaluation Paper in preparation Targeting active networks and mobile agents Byzantine Fault Tolerant Public Key Authentication in Peer-to-peer Systems 45
c52e556686089061a2f3c25725b2b228.ppt