f342921c3308f00760e13d59ac8ebc42.ppt
- Количество слайдов: 67
BUSS 909 Office Automation & Intranets Lecture 8 Internet, Intranets and Extranets: Implementation and Management Clarke, R. J (2000) L 909 -08: 1

Notices (1) n Students must organise themselves into Teams in readiness for Assignment 3: n Each team must have 5 students, and must nominate a Team Leader (if necessary a 6 th student may be allocated to a group) n Teams should, if possible, belong to the same Tutorial Class n Team membership must be emailed to me prior to Monday 7 th September 12: 30 (Week 9) Clarke, R. J (2000) L 909 -08: 2

Agenda n Web Servers n n Installation Performance Maintenance Security- Firewalls n Testing n Client-side Testing n Server-side Testing n Maintenance and Integration n Web Site Maintenance n Web Applications Clarke, R. J (2000) L 909 -08: 3

Web Server Installation Clarke, R. J (2000) L 909 -08: 4

Web Server Installation n set up of Web Servers may be nontrivial; the steps are likely to include: n installing a pre-compiled server- for example, HTTP Deamon Server (httpd) from NCSA n compilation of a server- to produce the required binaries n site specific configuration- for httpd you are required to adjust the contents of three files Clarke, R. J (2000) L 909 -08: 5

Web Server Installation n Installation of the Server- move the httpd server and its files and directories to the required locations before starting the Web Server n Starting the Server- often can run servers in a prototyping mode for testing (inetd) or in a standalone mode for production Clarke, R. J (2000) L 909 -08: 6

Web Server Installation n Mapping URLs to Documents- when a URL does not include a directory path or a filename, the web server: neither returns the contents of a file called index. html nor, the file does not exist and the web server automatically generates a directory index (similar to ls-1) n Testing the Web Server- exercise the server via a browser, should as a minimum provide an index. html Clarke, R. J (2000) L 909 -08: 7

Web Server Installation n Setting Up Home Pages- most often the entry point to a web server is a home pagehome. html. Can have one or many depending on the number of sites being hosted n Delegating Document Tree Managementndiscussion has assumed that a single user is using the web server nin reality content maintenance is the responsibility of an authoring community- rights to subdirectories etc Clarke, R. J (2000) L 909 -08: 8

Web Server Installation n Conventions for Public Accessnserver names should start with www nuse a CNAME alias record that maps the web server name to an actual system name nestablish a so called webmaster alias- an email alias that people can use to send comments, tips on broken pointers etc. nuse signatures on the bottom of HTML pages mounted on the web server- often implemented as Server Side Includes (SSIs) Clarke, R. J (2000) L 909 -08: 9

Web Server Installation n Announcing the Web Server: nthere are no formal procedures for this nbut there are well-established norms nsend announcement message to the mailing list at www-announce@www 0. cern. ch npost announcement message to www-request@info. cern. ch - a CERN moderated list of servers nsend an announcement message to whatz-new@nsca. uiuc. edu - an NCSA moderated list Clarke, R. J (2000) L 909 -08: 10
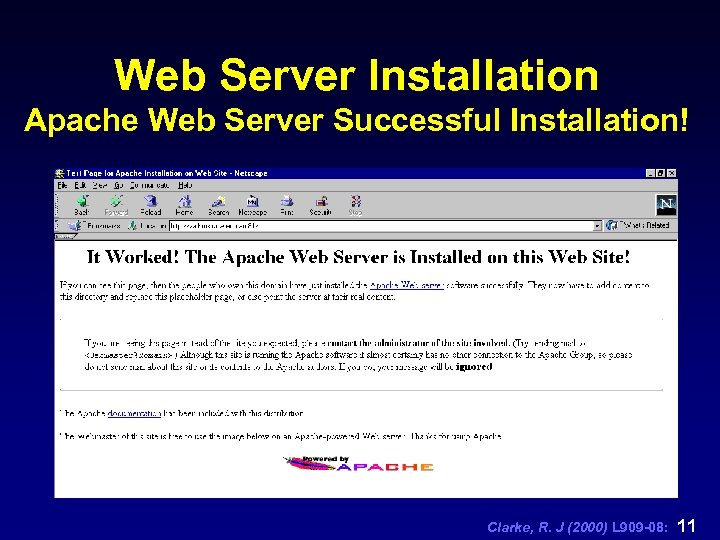
Web Server Installation Apache Web Server Successful Installation! Clarke, R. J (2000) L 909 -08: 11

Web Server Performance Source: Yeager & Mc. Grath (1996) Clarke, R. J (2000) L 909 -08: 12
Web Server Performance Document Distribution and Caching n each web server serves only one document tree (see L 909 -06. PPT) n web servers ‘expose’ a seamless view of information provided by the server, just as a web browser provides a seamless view of information on the web n the information provided by the server may actually be stored and organised in many different ways Clarke, R. J (2000) L 909 -08: 13
Web Server Performance Document Distribution and Caching n the web server acts as a translator between a simple logical view of a document tree and the physical view of files stored on the server n users do not want to know the complex details of physical storage but information providers must understand this n web servers can be configured to provide documents from a conceptually simpler ‘logical’ document tree rather than the complex ‘physical’ reality Clarke, R. J (2000) L 909 -08: 14
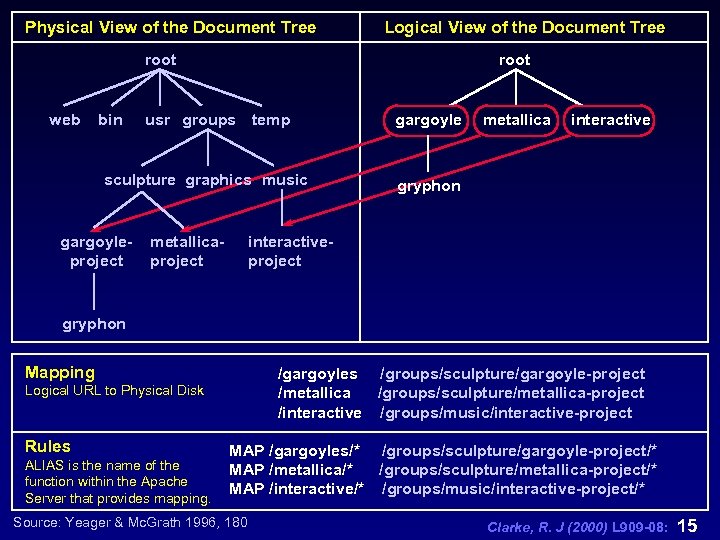
Physical View of the Document Tree Logical View of the Document Tree root web bin root usr groups temp sculpture graphics music gargoyleproject metallicaproject gargoyle metallica interactive gryphon interactiveproject gryphon Mapping /gargoyles /groups/sculpture/gargoyle-project /metallica /groups/sculpture/metallica-project /interactive /groups/music/interactive-project Logical URL to Physical Disk Rules ALIAS is the name of the function within the Apache Server that provides mapping. MAP /gargoyles/* /groups/sculpture/gargoyle-project/* MAP /metallica/* /groups/sculpture/metallica-project/* MAP /interactive/* /groups/music/interactive-project/* Source: Yeager & Mc. Grath 1996, 180 Clarke, R. J (2000) L 909 -08: 15

Web Server Performance Document Distribution and Caching n the information service provider may want the physical organisation as it is: n large servers may have thousands of documents to serve- more convenient to break documents into groups to store each separately n no single logical view will service all the needs of different users Clarke, R. J (2000) L 909 -08: 16

Web Server Performance Document Distribution and Caching n for high throughput systems it may be necessary to reduce the load on the server- two ways to do this: n allocate part of the document tree to another server Clarke, R. J (2000) L 909 -08: 17

Web Server Maintenance Clarke, R. J (2000) L 909 -08: 18
Web Server Maintenance n Depending on the type and state of the web server, it may be necessary to enhance its capabilities by: nproviding additional MIME types (Multimedia Extension) if necessary n. Enabling Server-side includes- similar to include files in programming languages- however, they can include not only files but variables n. Automatic Directory Indexing- insurance against users pointing to a directory URL rather than a file URL when no index. html exists Clarke, R. J (2000) L 909 -08: 19

Web Server Maintenance n Updating HTML Documents- don’t need to reboot the server, just lay the new documents over the existing ones n Managing/Analysing Log Files- on a daily/weekly basis the systems administrator should move or archive the log files to prevent them from growing to big- the process should be automated as part of standard backup procedures Clarke, R. J (2000) L 909 -08: 20
Web Server Maintenance n Moving Directory Structures- on occasion parts of the document tree need to be moved in order to cope with disk space constraints or changing system environment n Mirroring Documents and Servers- mirror (duplicate) part of another hosts directory tree in order to speed up your server (fetch slow graphics overnight), or in order to spread your server’s load across another Clarke, R. J (2000) L 909 -08: 21

Web Server Security Reading 24: Lodin & Scuba (1998) Clarke, R. J (2000) L 909 -08: 22

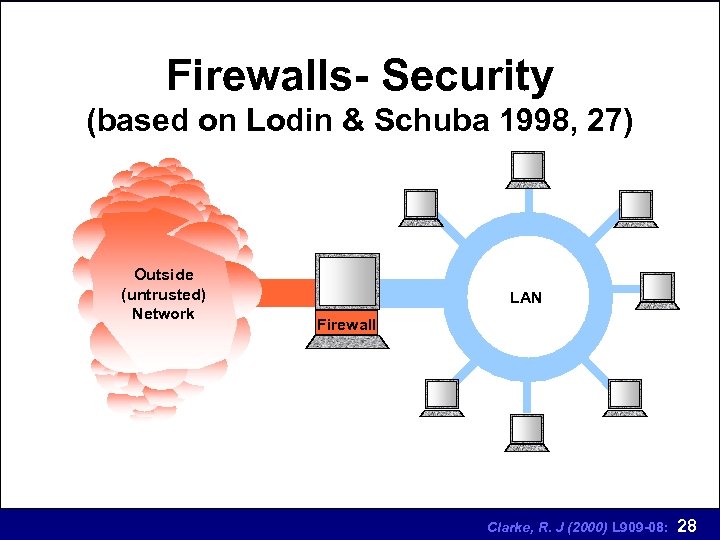
Web Server Security Firewalls (1) n each company that connects to WWW provides new opportunities for crackers n the general solution to secure internal networks is to construct a guarded gateway called a firewall Clarke, R. J (2000) L 909 -08: 23

Web Server Security Firewalls (2) n firewalls are the first defense against unwelcome visits to intranets and extranets n firewalls comprise software and or hardware which collectively form a set of mechanisms that enforce secure communications traffic entering or leaving a network domain Clarke, R. J (2000) L 909 -08: 24

Web Server Security Firewalls (3) n firewalls have several different topologies (as we will show shortly) n in general, firewalls are located between the internal network and the internet n an estimated one third of all Internet connected machines are located behind firewalls (Liu et al 1994, 497) Clarke, R. J (2000) L 909 -08: 25

Web Server Security n firewalls prevent unauthorised access between networks n it implies that decisions have been made about what is allowed and disallowed across the firewall n the decisions are based on the security policy for the site Clarke, R. J (2000) L 909 -08: 26

Web Server Security n firewalls work by examining the IP packets that travel between the server and the client n this approach enables the control of information flow for each of the possible internet services by n IP address n by port n in each direction Clarke, R. J (2000) L 909 -08: 27
Firewalls- Security (based on Lodin & Schuba 1998, 27) Outside (untrusted) Network LAN Firewall Clarke, R. J (2000) L 909 -08: 28

Firewalls- Security n attempt to maintain privacy by protecting data that its entering or leaving a domain, by preventing n passive wiretapping- data eavesdropping n active wiretapping- data change n traffic outside the firewall or internal to the domain is not affected Clarke, R. J (2000) L 909 -08: 29

Firewalls- Security n firewalls guard intranets and extranets from an outside and therefore untrusted network n they may also guard against parts of the internal intranet from other parts Clarke, R. J (2000) L 909 -08: 30
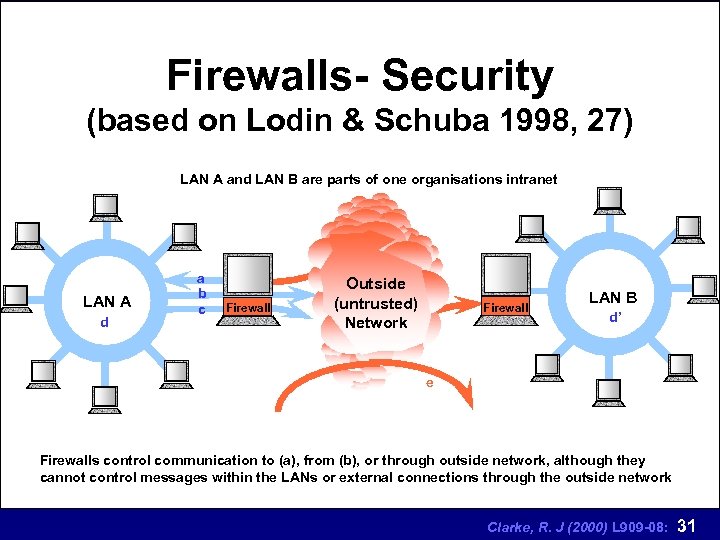
Firewalls- Security (based on Lodin & Schuba 1998, 27) LAN A and LAN B are parts of one organisations intranet LAN A d a b c Firewall Outside (untrusted) Network Firewall LAN B d’ e Firewalls control communication to (a), from (b), or through outside network, although they cannot control messages within the LANs or external connections through the outside network Clarke, R. J (2000) L 909 -08: 31

Firewalls- Security n can protect material within the domain- stored data, computational resources, and communication resources n can be guarded against unauthorised access, browsing, leaking, modification, insertion, and deletioncan protect against ‘denial of service type’ hacks Clarke, R. J (2000) L 909 -08: 32

Firewalls- Security n firewalls are generally applied to Transmission Control Protocol/Internet Protocol (TCP/IP) communications which are used in public Internet and private Intranets n controversies abound on the need for firewalls- even if they are deficient, they are a focus for computer security policy Clarke, R. J (2000) L 909 -08: 33

Firewalls- Security n security mechanisms employed by firewalls correspond to layers in the Open Systems Interconnection (OSI) model n OSI model views data communication in terms of movement through a series of layers (see L 909 -02. PPT) n 1 Physical Layer; 2 Data Link Layer; 3 Network Layer; 4 Transport Layer; 5 Session Layer; 6 Presentation Layer; 7 Application Layer Clarke, R. J (2000) L 909 -08: 34
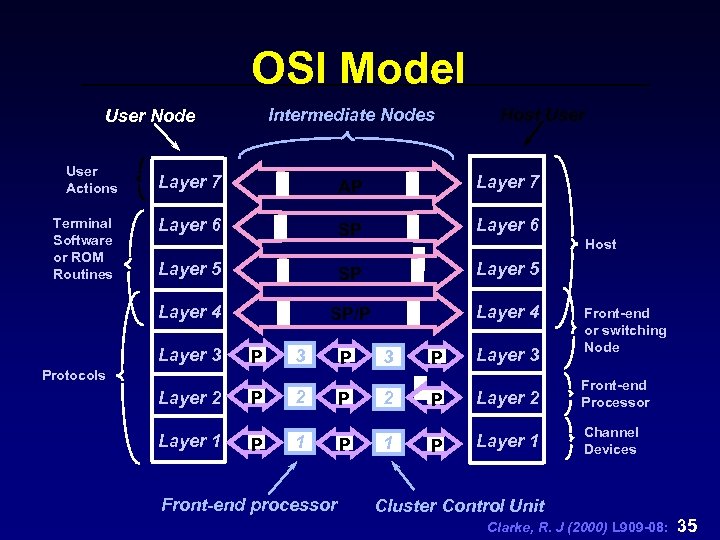
OSI Model Intermediate Nodes User Node User Actions Host User AP Layer 7 Layer 6 SP Layer 6 Layer 5 SP Layer 5 Layer 4 Terminal Software or ROM Routines Layer 7 SP/P Layer 4 Layer 3 Host P 3 Layer 2 P 2 Layer 1 P 1 P 3 Protocols Front-end processor P Layer 3 Front-end or switching Node P Layer 2 Front-end Processor P Layer 1 Channel Devices Cluster Control Unit Clarke, R. J (2000) L 909 -08: 35
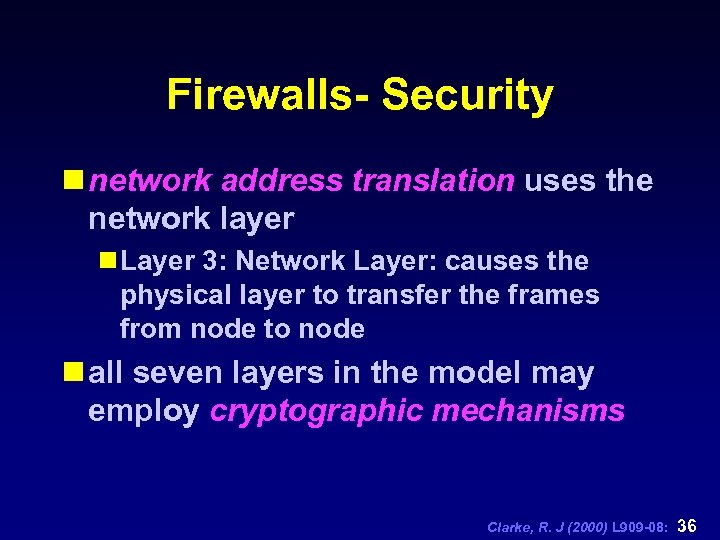
Firewalls- Security n network address translation uses the network layer n Layer 3: Network Layer: causes the physical layer to transfer the frames from node to node n all seven layers in the model may employ cryptographic mechanisms Clarke, R. J (2000) L 909 -08: 36

Firewalls- Security n packet filtering mechanism operates primarily on network and transport layers n Layer 4: Transport Layer: enables user and host nodes to communicate with each other; synchronizes fast- and slow - speed equipment as well as overburdened and idle units Clarke, R. J (2000) L 909 -08: 37

Firewalls- Security n can impose overheads especially performance limitations (delays) on the throughput of the intranet n this is becoming less of a concern due to speed improvements with hardware (higher processing speeds) and software optimisations Clarke, R. J (2000) L 909 -08: 38

Firewalls- Security n specific operations supported by firewalls include: n packet filtering- a router allows/denies the passage of data after checking its header and contents based on security rules n network address translation (NAT)hides internal addresses and network topology of the domain from outside users Clarke, R. J (2000) L 909 -08: 39

Firewalls- Security n circuit-level forwarding (low-level)- groups packets into connections. Inbound and outbound connections must connect to a proxy process before it can proceed. The proxy makes use of rules to determine whether the connection should be made. n application-level forwarding (higher-level)firewalls can interpret data in packets in accordance with protocols and security rules Clarke, R. J (2000) L 909 -08: 40

Firewalls- Security n crytographic mechanisms- enciphering or deciphering of messages using a secret code. There are many different types of crypographic meachanisms around. Internet Engineering Task Force for the IP security (IPsec) protocols Clarke, R. J (2000) L 909 -08: 41

Web Applications Clarke, R. J (2000) L 909 -08: 42

Web Applications n a number of companies are implementing ‘mission-critical’ web based applications n these applications generally utilise databases n attempt at developing closer alliances with customers, suppliers, partners, and employees Clarke, R. J (2000) L 909 -08: 43
Web Applications n sophisticated web applications must support complex Internet/intranet system configuration n systems level hardware/software, and networking products must work together n software elements: JAVA applets, Microsoft Active X controls, CGI scripts, SQL code Clarke, R. J (2000) L 909 -08: 44
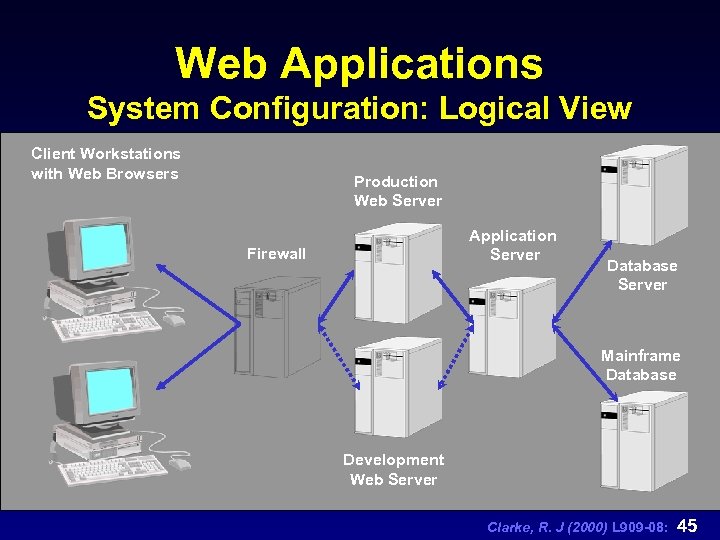
Web Applications System Configuration: Logical View Client Workstations with Web Browsers Production Web Server Application Server Firewall Database Server Mainframe Database Development Web Server Clarke, R. J (2000) L 909 -08: 45
Web Applications n In terms of complexity, complex web applications are therefore no different to traditional systems development projects n web-based application components must be thoroughly tested to ensure that they are reliable, defect-free, and meets its original design purposes Clarke, R. J (2000) L 909 -08: 46
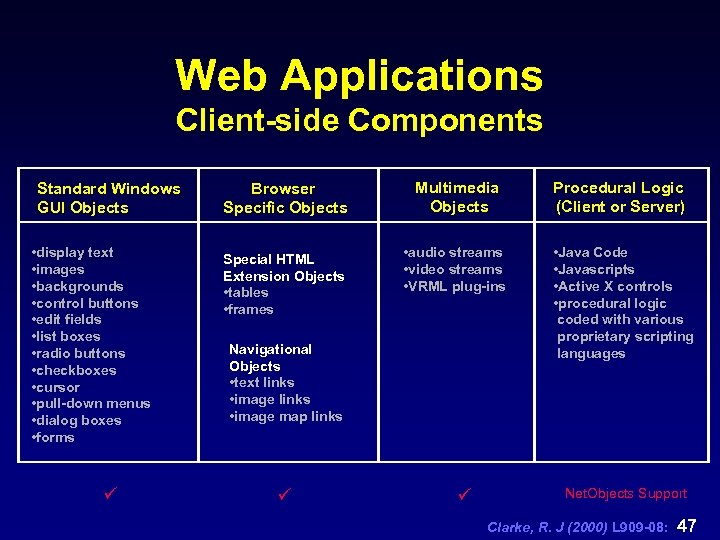
Web Applications Client-side Components Standard Windows GUI Objects • display text • images • backgrounds • control buttons • edit fields • list boxes • radio buttons • checkboxes • cursor • pull-down menus • dialog boxes • forms ü Browser Specific Objects Special HTML Extension Objects • tables • frames Multimedia Objects Procedural Logic (Client or Server) • audio streams • video streams • VRML plug-ins • Java Code • Javascripts • Active X controls • procedural logic coded with various proprietary scripting languages Navigational Objects • text links • image map links ü ü Net. Objects Support Clarke, R. J (2000) L 909 -08: 47
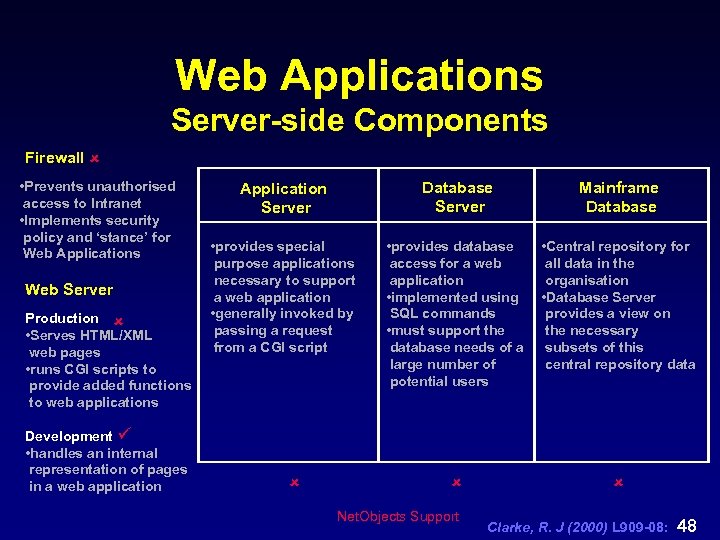
Web Applications Server-side Components Firewall û • Prevents unauthorised access to Intranet • Implements security policy and ‘stance’ for Web Applications Web Server Production û • Serves HTML/XML web pages • runs CGI scripts to provide added functions to web applications Development ü • handles an internal representation of pages in a web application Application Server Database Server Mainframe Database • provides special purpose applications necessary to support a web application • generally invoked by passing a request from a CGI script • provides database access for a web application • implemented using SQL commands • must support the database needs of a large number of potential users • Central repository for all data in the organisation • Database Server provides a view on the necessary subsets of this central repository data û û û Net. Objects Support Clarke, R. J (2000) L 909 -08: 48

Client-side Testing Clarke, R. J (2000) L 909 -08: 49
Client-side Testing Browser & Desktop n Browser compatibility testing n application operates correctly and consistently on different types of browsers (see Reading #22, Berghel 1996) n Desktop configuration testing n verifies that the client-side operates consistently on different client desktop machines with different configurations Clarke, R. J (2000) L 909 -08: 50
Client-side Testing Usability & Documentation n Usability testing n user-centric design of the user interface n with multimedia elements, establish that the user activity matches the users business task flows n Documentation testing n verifies the accuracy, relevance, userfriendliness, and completeness of written user guides and online help Clarke, R. J (2000) L 909 -08: 51

Client-side Testing Security n Security testing n verifies that the web application is immune from unauthorised access attempts n necessitates the regular determination of the accuracy of the information on the web site n determines that links have not been modified Clarke, R. J (2000) L 909 -08: 52

Client-side Testing Browser & Desktop n Error message testing n proper handling of known error conditions by the web application n Client load testing n verifies the scalability of the web application client-side while under different volumes of data Clarke, R. J (2000) L 909 -08: 53
Client-side Testing Portability & Applet Scripting n Cross-platform portability n verifies that the web application functional behaviour is consistent across different client platforms (eg. Windows, Mac, UNIX) n Applet/Script Testing n verifies applet/script behaviour of JAVA applets, scripts, plug-ins, or Active X components when downloaded and executed client-side Clarke, R. J (2000) L 909 -08: 54

Client-side Testing GUI Testing n verifies the overall functionality of the Web Application with respect to its Graphical User Interface environment Clarke, R. J (2000) L 909 -08: 55

Server-side Testing Clarke, R. J (2000) L 909 -08: 56
Server-Side Testing n Web-server Load testing n Network Load Testing n Application Server Testing n Database Server Load Testing Clarke, R. J (2000) L 909 -08: 57

Web Site Maintenance Link Verification Clarke, R. J (2000) L 909 -08: 58

Web Site Maintenance Link Types n web sites will have several link types n using Net. Objects naming conventions, web sites will have: n internal links that link pages in your site to other pages in your site, or n external links that link pages in your site to other web sites Clarke, R. J (2000) L 909 -08: 59

Web Site Maintenance Link Types n it is generally true that the same internal links get used repeatedly, for example links to home pages, and those used in navigation bars n this is not true of external links- may be used only once in the web site n even small web sites can have masses of external links Clarke, R. J (2000) L 909 -08: 60

Web Site Maintenance Need for Link Verification n the resources referenced by external links can be re/moved from the Internet n this leads to a bad link occurring in your web site over which you have no control n fortunately, there are link verification tools both freeware and commercial which can automatically test links in your web sites Clarke, R. J (2000) L 909 -08: 61

Web Site Maintenance Link Verification Tools n suitable characteristics for link verification tools include: n should be able to check weblets (that is parts of your website), not just the entire web hierarchy n should be able to cope with the situation where a valid URL points to a web site that is temporarily down, unresponsive, or slow n ability to restart if interrupted Clarke, R. J (2000) L 909 -08: 62

Further Reading n Liu, C. ; Peek, J. ; Jones, R. ; Buus, B. and A. Nye (1994) Managing Internet Information Services Chapter 18: Setting Up a Web Server, O’Reilly & Associates, Inc. 299 -324 n Liu, C. ; Peek, J. ; Jones, R. ; Buus, B. and A. Nye (1994) Managing Internet Information Services Chapter 20: Web: Gateways and Forms, O’Reilly & Associates, Inc. 357 -380 n Liu, C. ; Peek, J. ; Jones, R. ; Buus, B. and A. Nye (1994) Managing Internet Information Services Chapter 21: Web: Access Control and Security, O’Reilly & Associates, Inc. 381 -390 n Berghel, H. (1996) “HTML Compliance and the Return of the Test Pattern” Communications of the ACM February 39 (2) 19 -22 (Reading #22) Clarke, R. J (2000) L 909 -08: 63

n Luotonen, A. (1998) Web Proxy Servers Prentice Hall PTR Web Infrastructure Series NJ: Prentice Hall PTR n Fournier, R. (1999) A Methodology for Client/Server and Web Application Development Yourdon Press Computing Series, NJ: Yourdon Press, Prentice Hall n Lodin, S. W. and C. L. Schuba (1998) “Firewalls fend off invasions from the Net” IEEE Spectrum February 1998, 35 (2), 26 - 34 (Reading #24) n Oppliger, R. (1997) “Internet Security: Firewalls and Beyond” Communications of the ACM May 40 (5) 92 -102 (Reading #25) n Wood, D. (1998) “The Search for the Searcher: Use second-rate search engine software and your users will avoid your Web site in droves” Systems April 1998, 58 -67 (Reading #26) Clarke, R. J (2000) L 909 -08: 64

n Anonymous (1998) “Serving from the baseline: APC Labs checks out entry-level Web servers from small-to-medium businesses” APC Magazine April 1998, 115 -124 (Reading #27) n Schwartz, R. L. (1999) “Programming with Perl: Step-by Step Link Verification” Web Techniques 4 (3) March 1999, 30 -34 n Yeager, N. J. & R. E. Mc. Grath (1996) Web Server Technology: The Advanced Guide for World Wide Web Information Providers San Francisco, California: Morgan Kaufmann n Holden, G. and M. Keller (1999) Apache Server for Windows: Little Black Book Arizona: Coriolis Clarke, R. J (2000) L 909 -08: 65
Links Web Techniques www. webtechniques. co New. Apps Software Archive http: //www. newapps. com/appstopics/ Win_95_HTML_and_Link_Verification_Tools. html Viable Software Alternatives- Alert Link. Runner http: //viablesoftware. com/ Tetranet Software- Link. Bot Pro http: //www. tetranetsoftware. com/products/linkbot. htm Trellian- Site. Mapper http: //www. trellian. com/mapper/ Aman Software- Cyber. Spyder Link Test 2. 1. 5 http: //www. cyberspyder. com/cslnkts 1. html Hausherr, Tilman- Xenu's Link Sleuth http: //www. snafu. de/~tilman/xenulink. html comp. lang. tcl Frequently Asked Questions (1998) http: //www. cis. ohio-state. edu/hypertext/faq/usenet/tcl-faq/part 1/faq-doc-2. html Clarke, R. J (2000) L 909 -08: 66

Bourne Shell (1994) http: //garfield. ir. ucf. edu/manual/aix/bourne. html CGI Programming 101 (1997 -1998) http: //lightsphere. com/dev/class/ Comprehensive Perl Archive Network (1998) http: //ftp. digital. com/pub/plan/perl/CPAN. html IPSec Online (1998) http: //www. data. com/tutorials/bullet_online. html Clarke, R. J (2000) L 909 -08: 67
f342921c3308f00760e13d59ac8ebc42.ppt